Chapter 13 Identity Auditing: Basic Concepts
This chapter introduces you to the concepts behind identity auditing and audit controls. Audit controls can be used to monitor and manage auditing and compliance across enterprise information systems and applications.
In this chapter, you will learn about the following concepts and tasks:
About Identity Auditing
Waveset defines auditing as the systematic capture, analysis, and response to identity data across an enterprise to ensure compliance with internal and external policies and regulations.
Compliance with accounting and data privacy legislation is not a simple task. Waveset’s auditing features offer a flexible approach, allowing you to implement a compliance solution that works for your enterprise.
In most environments, different groups are involved with compliance: internal and external auditing teams (for whom auditing is the primary focus); and non-auditing staff (who may see auditing as a distraction). IT often is involved with compliance as well, helping transition internal auditing team requirements to a chosen solution’s implementation. The key to successfully implementing an auditing solution is in accurately capturing the knowledge, controls, and processes of non-auditing staff, and then automating the application of that information.
Goals of Identity Auditing
Identity auditing improves audit performance as follows:
-
Identity auditing automatically detects compliance violations and facilitates swift remediation through immediate notification
Waveset audit policy features let you define rules (that is, criteria) for violations. Once defined, the system scans for conditions that violate established policies, such as unauthorized access changes or erroneous access privileges. Upon detection, the system notifies the appropriate persons according to a defined escalation chain. User-invoked tasks, or workflows that are automatically invoked by policy violations, can then remediate (correct) the violation.
-
Provides key information, on-demand, about the effectiveness of internal audit controls
The Auditor Reports provide summary status information about violations and exceptions for quick analysis of risk status. The Reports tab also provides graphical reports of violations. You can view violations by resource, organization, or policy, customizing each chart according to the report characteristics you define.
-
Automates certification reviews of identity controls to reduce operational risk
Workflow capabilities enable automated notification of policy and access violations to selected reviewers.
-
Prepares comprehensive reports that detail user activity and meet regulatory requirements
The Reports area lets you define detailed reports and charts that provide information on access history and privileges, and other policy violations. The system keeps a secure and comprehensive identity audit trail that can be mined, through reporting capabilities, for access data and user profile updates.
-
Streamlines the process of periodic reviews to maintain security and regulatory compliance
Periodic access reviews can be conducted to collect user entitlement records and determine which entitlements require review. The process then notifies designated attestors of pending requests for review and updates the status or pending requests when attestor actions on the requests are completed.
-
Identifies potential conflict-of-interest capabilities for user accounts
Waveset provides a Separation of Duties report that identifies users with specific capabilities or privileges that could be a potential conflict of interest.
Understanding Identity Auditing
Waveset provides a feature for auditing user account privileges and access rights, and a separate feature for maintaining and certifying compliance. These features are policy-based compliance and periodic access reviews.
Policy-Based Compliance
Waveset employs an audit policy system that allows administrators to maintain compliance of company-established requirements for all user accounts.
You can use audit policies to ensure compliance in two different and complementary ways: continuous compliance and periodic compliance.
These two techniques are particularly complementary in an environment in which provisioning operations may be performed outside of Waveset. When an account can be changed by a process that does not execute or honor existing audit policies, periodic compliance is necessary.
Continuous Compliance
Continuous compliance means that an audit policy is applied to all provisioning operations, such that an account cannot be modified in a way that does not comply with current policy.
You enable continuous compliance by assigning an audit policy to an organization, a user, or both. Any provisioning operations performed on a user will cause the user-assigned policies to be evaluated. Any resulting policy failure will interrupt the provisioning operation.
An organization-based policy set is defined hierarchically. There is only one organization policy set in effect for any user. The applied policy set is the one assigned to the lowest-level organization. For example:
|
Organization |
Directly Assigned Policy Set |
Effective Policy |
|---|---|---|
|
Austin |
Policies A1, A2 |
Policies A1, A2 |
|
Marketing |
Policies A1, A2 |
|
|
Development |
Policies B, C2 |
Policies B, C2 |
|
Support |
Policies B, C2 |
|
|
Test |
Policies D, E5 |
Policies D, E5 |
|
Finance |
Policies A1, A2 |
|
|
Houston |
<none> |
Periodic Compliance
Periodic compliance means that Waveset evaluates policy on-demand. Any noncompliant conditions are captured as compliance violations.
When executing periodic compliance scans, you can select which policies to use in the scan. The scan process blends directly-assigned policies (user-assigned and organization-assigned policies) and an arbitrary set of selected policies.
Waveset users with Auditor Administrator capabilities can create audit policies and monitor compliance with those policies through periodic execution of policy scans and reviews of policy violations. Violations can be managed through remediation and mitigation procedures.
For more information about the Auditor Administrator capabilities, see Understanding and Managing Capabilities in Chapter 6, Administration.
Waveset auditing allows for regular scans of users. These scans execute audit policies to detect deviations from established account limits. When a violation is detected, remediation activities are initiated. The rules may be standard audit policy rules provided by Waveset, or customized, user-defined rules.
Logical Task Flow for Policy-Based Compliance
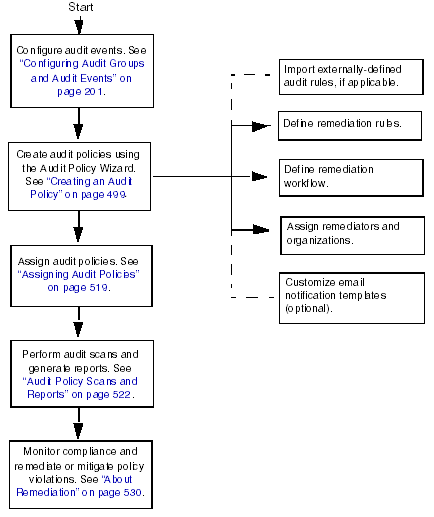
Figure 13–1 shows a logical task flow for establishing policy-based audit controls.
Periodic Access Reviews
Waveset provides for periodic access reviews that enable managers and other responsible parties to review and verify user access privileges on an ad-hoc or periodic basis. For more information about this feature, see Periodic Access Reviews and Attestation.
Figure 13–1 A Logical Task Flow for Establishing Policy-based Compliance
Working with Identity Auditing in the Administrator Interface
This section describes how to access Identity Auditing features in the Administrator Interface. Email notification templates used in identity auditing are also discussed.
Using the Compliance Section of the Interface
To create and manage audit policies, use the Compliance section of the Waveset Administrator interface.
 To Use the Compliance section to Create and Manage
Audit Policies
To Use the Compliance section to Create and Manage
Audit Policies
-
Log in to the Administrator interface (Logging in to the Waveset End-User Interface).
-
Click Compliance in the menu bar.
The following subtabs (or menu items) are available in the Compliance section:
-
Manage Policies
-
Manage Access Scans
-
Access Reviews
-
Manage Policies
The Manage Policies page lists the policies that you have permission to view and edit. You can also manage access scans from this area.
From the Manage Policies page, you can work with audit policies to accomplish these tasks:
-
Create an audit policy
-
Select a policy to view or edit
-
Delete a policy
Detailed information about these tasks follows in the section A Sample Audit Policy Scenario.
Manage Access Scans
Use the Manage Access Scans tab to create, modify, and delete access scans. Here you can define scans that you want to run or schedule for periodic access reviews. For more information about this feature, see Periodic Access Reviews and Attestation.
Access Reviews
The Access Reviews tab enables you to launch, terminate, delete, and monitor the progress of your access reviews. It displays a summary report of the scan results with information links that enable you to access more detailed information about the review status and pending activities.
For more information about this feature, see Managing Access Reviews.
Identity Auditing Tasks Interface Reference
To look up how to perform other identity auditing tasks in the Administrator interface, see Table B–8. This quick reference tells you where to go to start a variety of auditing tasks.
Email Templates
Identity Auditing uses email-based notification for a number of operations. For each of these notifications, an email template object is used. The email template allows the headers and body of email messages to be customized.
Table 13–1 Identity Auditing Email Templates|
Template Name |
Purpose |
|---|---|
|
Access Review Remediation Notice |
Sent to remediators by an access review when user entitlements are initially created in a remediating state. |
|
Bulk Attestation Notice |
Sent to attestors by an access review when they have pending attestations. |
|
Policy Violation Notice |
Sent to remediators by an audit policy scan when violations occur. |
|
Access Scan Begin Notice |
Sent to an access scan owner when an access review starts a scan. |
|
Access Scan End Notice |
Sent to an access scan owner when an access scan completes. |
Enabling Audit Logging
Before you can begin managing compliance and access reviews, the Waveset audit logging system must be enabled and configured to collect audit events. By default, the auditing system is enabled. An Waveset administrator with the Configure Audit capability can configure auditing.
Waveset provides the Compliance Management audit configuration group.
-
Log in to the Administrator interface (Logging in to the Waveset End-User Interface).
-
Select Configure from the menu bar, and then click Audit.
-
On the Audit Configuration page, select the Compliance Management audit group name.
Use the following steps to view or modify events stored by the Compliance Management group.
Note –
-
For more information about setting up audit configuration groups, see Configuring Audit Groups and Audit Events.
-
For information about how the audit system records events, see Chapter 10, Audit Logging.
- © 2010, Oracle Corporation and/or its affiliates
