Managing Account Security and Privileges
This section discusses actions you can take to provide secure access for user accounts and to manage user privileges in Waveset.
Setting Password Policies
Resource password policies establish the limitations for passwords. Strong password policies provide added security to help protect resources from unauthorized login attempts. You can edit a password policy to set or select values for a range of characteristics.
To begin working with password policies, click Security on the main menu, and then click Policies.
To edit a password policy, click it in the Policies list. To create a password policy, select String Quality Policy from the New list of options.
Note –
For more information on policies, see Configuring Waveset Policies.
Creating a Policy
Password policies are the default type for string quality policies. After naming and providing an optional description for a new policy, select options and parameters for the rules that define that policy.
Length Rules
Length rules set the minimum and maximum required character length for a password. Select this option to enable the rule, and then enter a limit value for the rule.
Policy Type
Choose one of the policy type buttons . If you choose the Other option, you must enter the type in the text field provided.
Character Type Rules
Character type rules establish the minimum and maximum characters of certain types and number that can be included in a password.
These include:
-
Minimum and maximum alphabetic, numeric, uppercase, lowercase, and special characters
-
Minimum and maximum embedded numeric characters
-
Maximum repetitive and sequential characters
-
Minimum beginning alphabetic and numeric characters
Enter a numeric limit value for each character type rule; or enter All to indicate that all characters must be of that type.
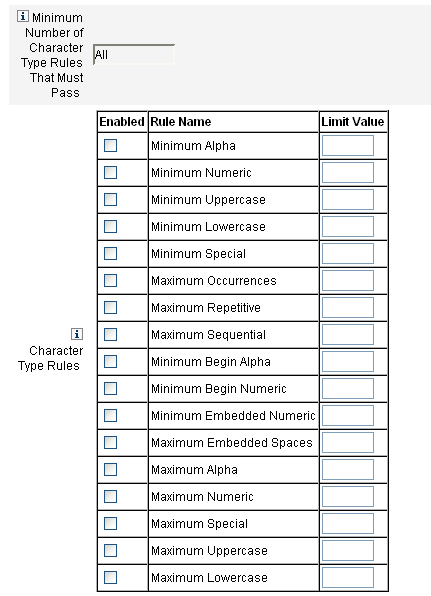
Minimum Number of Character Type Rules
You can also set the minimum number of character type rules that must pass validation, as illustrated in Figure 3–7. The minimum number that must pass is one. The maximum cannot exceed the number of character type rules that you have enabled.
Note –
To set the minimum number that must pass to the highest value, enter All.
Figure 3–7 Password Policy (Character Type) Rules
Dictionary Policy Selection
You can choose to check passwords against words in a dictionary to guard against simple dictionary attacks.
Before you can use this option, you must:
-
Configure the dictionary
-
Load dictionary words
You configure the dictionary from the Policies page. For more information about how to set up the dictionary, see What is a Dictionary Policy?.
Password History Policy
You can prohibit the reuse of passwords that were used immediately preceding a newly selected password.
In the Number of Previous Passwords that Cannot be Reused field, enter a numeric value greater than one to prohibit re-use of the current and preceding passwords. For example, if you enter a numeric value of 3, the new password cannot be the same as the current password or the two passwords used immediately before it.
You can also prohibit re-use of similar characters from passwords used previously. In the Maximum Number of Similar Characters from Previous Passwords that Cannot be Reused field, enter the number of consecutive characters from the previous password or passwords that cannot be repeated in the new password. For example, if you enter a value of 7, and the previous password was password1, then the new password cannot be password2 or password3.
If you enter a value of 0, then all characters must be different regardless of sequence. For example, if the previous password was abcd, then the new password cannot include the characters a, b, c, or d.
The rule can apply to one or more previous passwords. The number of previous passwords checked is the number specified in the Number of Previous Passwords that Cannot be Reused field.
Must Not Contain Words
You can enter one or more words that the password may not contain. In the entry box, enter one word on each line.
You can also exclude words by configuring and implementing the dictionary policy. For more information, see What is a Dictionary Policy?.
Must Not Contain Attributes
You can enter one or more attributes that the password may not contain.
You can specify the following attributes:
-
accountID
-
email
-
firstname
-
fullname
-
lastname
You can change the allowed set of “must not contain” attributes for passwords in the UserUIConfig configuration object. See Must Not Contain Attributes in Policies for more information.
Implementing Password Policies
Password policies are established for each resource. To put a password policy in place for a specific resource, select it from the Password Policy list of options, which is located in the Policy Configuration area of the Create or Edit Resource Wizard: Waveset Parameters pages.
Setting Account Authentication Policies
You must configure user authentication, and the rules that govern authentication, as part of an Waveset account policy. Unlike password policies, Waveset account policies are assigned directly to the user or through the organization assigned to the user (on the Create and Edit User pages). The user authentication methods you establish enables users to access Waveset when they forget their user ID or passwords, or when their passwords are reset.
You can configure the following authentication methods for an Waveset account policy:
-
Authentication questions. Require users to answer one or more account authentication questions to gain access to Waveset. The authentication question policy determines what happens when a user clicks on the Forgot Your Password? button on the login page or when accessing the Change My Answers page.
-
Login recovery. Resets the user's password, then emails both the login and password to the user's email address.
Instructions for configuring these methods from the Waveset Administrator interface follow.
To Establish Authentication Questions for an Account Policy
-
Select Security > Policies from the main menu.
-
Choose DefaultWaveset Account Policy from the list of policies.
Authentication selections are offered in the Secondary Authentication Policy Options area of the page. The following table describes each option.
Option
Description
All
Requires the user to answer all policy-defined and personalized questions.
Any
Waveset displays all policy-defined and personalized questions. You must specify how many questions the user must answer.
Next
Requires the user to answer all possible policy-defined questions the first time that user logs in.
If the user clicks the Forgot Your Password? button during login, Waveset displays the first question. If the user answers incorrectly, Waveset displays the next question, and so on until the user answers an authentication question correctly and logs in, or is locked out based on the specified failure attempts limit. User-generated questions are not supported for this policy.
Random
Allows the administrator to specify how many questions the user must answer. Waveset randomly selects and displays the specified number of questions from the list of questions defined in the policy as well as those the user has defined. The user must answer all questions displayed.
Round robin
Waveset selects the next question from the list of configured questions and assigns this question to the user. The first user is assigned the first question in the list of authentication questions, and the second user is assigned the second question. This pattern continues until the number of questions is exceeded. At that point, questions are assigned to users in sequential order. For example, if there are 10 questions, the 11th and 21st users are assigned the first question.
Only the selected question is displayed. If you want the user to answer a different question every time, use the Random policy and set the number of questions to 1.
Users cannot define their own authentication questions. See Using Personalized Authentication Questions for more information about this feature.
You can verify your authentication choices by logging in to the Waveset End User interface, clicking the Forgot Your Password? button, and answering the presented question or questions.
Note –
After you set up the authentication questions, users must log in to the End User interface and provide initial answers to their authentication questions. If the users do not set answers the first time they log in, they cannot successfully log in without a password.
The following figure shows an example of the User Account Authentication screen.
Figure 3–8 User Account Authentication

Using Personalized Authentication Questions
In the Waveset account policy, you can select an option to allow users to supply their own authentication questions in the End User and Administrator interfaces. You can additionally set the minimum number of questions that the user must provide and answer to be able to log in successfully by using personalized authentication questions.
-
Select the Security > Policies tabs.
-
On the Policies page, click Default Identity Manager Account Policy.
-
When the Policy page displays, scroll down to the Secondary Authentication Policy Options section.
Complete this section as follows:
-
For Login Interface. Select User Interface from the menu.
-
Maximum Number of Failed Login Attempts. Enter the maximum number of failed attempts you want to allow.
-
Enforce Answer Policy at Login. Deselect this option.
-
Authentication Questions Policy. Select Any from the menu.
-
Minimum Number of Questions User is Required to Answer. Enter the minimum number of questions you want the user to answer.
-
Answer Quality Policy. Select None from the menu.
Note –If you previously configured one or more Authentication Answer Quality Policies, they will be available for selection from the menu. Otherwise, the only option is None.
-
Allow User Supplied Questions. Select this option to allow user-supplied questions.
-
Minimum Number of User Supplied Questions. Enter the minimum number of questions you want the user to provide.
-
Supplied Question Quality Policy. Select None from the menu.
Note –If you previously configured one or more Authentication Question Quality Policies, they will be available for selection from the menu. Otherwise, the only option is None.
-
Organizations. Select one or more organizations to which this object will be available.
-
-
Click Save to save your changes.
To configure Waveset to allow user-supplied questions, perform the following steps:
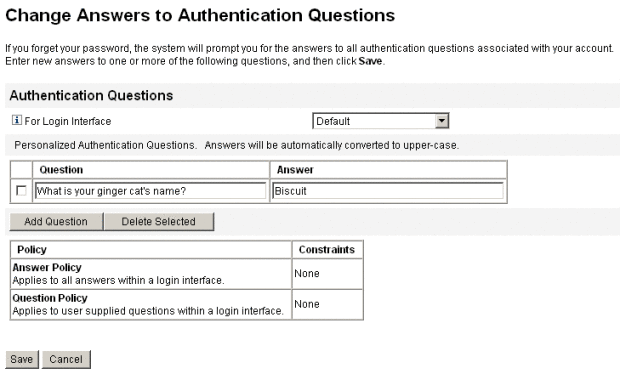
Users can add and change questions from the Change Answers to Authentication Questions page. An example of this page is shown in Figure 3–9.
Figure 3–9 Change Answers: Personalized Authentication Questions
Bypassing the Change Password Challenge after Authentication
When users successfully authenticate by answering one or more questions, by default they are challenged by the system to provide a new password. You can configure Waveset to bypass the change password challenge, however, by setting the bypassChangePassword system configuration property for one or more Waveset applications.
For instructions on editing the system configuration object, see Editing Waveset Configuration Objects.
To bypass the change password challenge for all applications following successful authentication, set the bypassChangePassword property as follows in the system configuration object.
Example 3–2 Setting the Attribute to Bypass the Change Password Challenge
<Attribute name="ui"
<Object>
<Attribute name="web">
<Object>
<Attribute name=’questionLogin’>
<Object>
<Attribute name=’bypassChangePassword’>
<Boolean>true</Boolean>
</Attribute>
</Object>
</Attribute>
...
</Object>
...
To disable this password challenge for a specific application, set it as follows.
Example 3–3 Setting the attribute to Disable the Change Password Challenge
<Attribute name="ui">
<Object>
<Attribute name="web">
<Object>
<Attribute name=’user’>
<Object>
<Attribute name=’questionLogin’>
<Object>
<Attribute name=’bypassChangePassword’>
<Boolean>true</Boolean>
</Attribute>
</Object>
</Attribute>
</Object>
</Attribute>
...
</Object>
...
|
To Establish Login Recovery for an Account Policy
Configuring Login Recovery as an alternative to the security questions-based login implements a message obfuscation option that renders the same generic result message for all errors and successes. This method helps prevent account harvesting.
Note –
The obfuscate messages option is enabled by default in the loginRecovery.jsp file. You can set this same option in the lookupUserId.jsp files.
Functionally, Login Recovery uses the same system as the Forgot Your User ID? method and both methods share the same configuration attributes. The main difference between these two methods is that Login Recovery also resets the user's password and then emails both the login and the password to the user's email address.
You can replace the security questions-based log-in method with the Login Recovery method by redirecting the Forgot Your Password? button or by creating a new Login Recovery button on the Log In pages. You configure either option in the System Configuration file, as follows:
-
To redirect Forgot Password to Login Recovery, specify
ui.web.user.questionLogin.forceLoginRecovery = true ui.web.admin.questionLogin.forceLoginRecovery = true
-
To use a Login Recovery button instead of Forgot Password/Lookup, specify
ui.web.user.disableLoginRecovery = false ui.web.admin.disableLoginRecovery = false ui.web.user.disableForgotPassword = true ui.web.admin.disableForgotPassword = true ui.web.user.disableForgotUserId = true ui.web.admin.disableForgotUserId = true
Assigning Administrative Privileges
You can assign Waveset administrative privileges, or capabilities, to users as follows:
-
Admin Roles. Users assigned an Admin Role inherit the capabilities and controlled organizations defined by the role. By default, all Waveset user accounts are assigned the User Admin Role when created. For detailed information about Admin Roles and creating an Admin Role, see Understanding and Managing Admin Roles in Chapter 6, Administration.
-
Capabilities. Capabilities are defined by rules. Waveset provides sets of capabilities grouped into functional capabilities that you can select from. Assigning capabilities allows for more granularity in assigning administrative privileges. For information about capabilities and creating capabilities, seeUnderstanding and Managing Capabilities in Chapter 6, Administration.
-
Controlled organizations. Controlled organizations grant administrative control privileges over specified organizations. For more information, see Understanding Waveset Organizations in Chapter 6, Administration.
For more information about Waveset Administrators and administrative duties, see Chapter 6, Administration
- © 2010, Oracle Corporation and/or its affiliates
