| Oracle® Waveset 8.1.1 Connector Reference Release 8.1.1 E25959-06 |
|
|
PDF · Mobi · ePub |
| Oracle® Waveset 8.1.1 Connector Reference Release 8.1.1 E25959-06 |
|
|
PDF · Mobi · ePub |
This chapter includes the following information about the Active Directory connector for Oracle Waveset:
The Oracle Waveset Active Directory connector is a .NET connector that supports provisioning to Microsoft Windows servers running:
Microsoft Active Directory Domain Services (AD DS)
Microsoft Active Directory Lightweight Directory Services (AD LDS), formerly called Active Directory Application Mode (ADAM)
For AD LDS, the Active Directory connector supports the same features that are supported for AD DS, except when explicitly noted otherwise in this chapter.
Oracle does not provide AD LDS specific integration artifacts (that is, glue) for Oracle Waveset. Therefore, to use AD LDS, you must manually configure the Oracle Waveset resource, user forms, and any related artifacts. (Or, you can use the LDAP resource adapter.) For more information, see Configuring the Active Directory Connector for AD LDS.
The Active Directory connector is implemented using the Identity Connector Framework (ICF). The ICF provides a container that separates the connector bundle from the application. The ICF also provides common features such as connection pooling, buffering, time outs, and filtering to simplify the usage of the connectors. For more information about the ICF, see Chapter 1, "Identity Connectors Overview".
Other considerations for the Active Directory connector are:
The Active Directory connector operates in the context of the .NET Connector Framework, which in turn requires an application to execute. Therefore, by default, Oracle provides (and recommends) the .NET Connector Server to run the Active Directory connector.
The Active Directory connector supports any scripting language that has a script executor in the ICF. Currently, there are two script executor implementations: a Windows shell script executor (batch scripts) and a Boo script executor. Although Visual Basic scripts are not directly supported, a Visual Basic script can be called via a shell script.
The Active Directory connector supports agentless target deployment; that is, an agent is not required.
The Active Directory connector supports various Active Directory Forest Topologies The connector supports Global Catalog Server based reconciliation to bring the objects from the nested (child) domain.
The connector also supports reconciliation and provisioning operations across domains. For example, you can assign a user in one domain to a group in another domain. You can also reconcile a user record even if the user and the user's manager belong to different domains. The connector supports provisioning of the accounts in the child domain by connecting to the parent domain and then using referrals for provisioning to the child domain.
The Active Directory connector supports a custom schema. You can create custom object classes and different object classes for different types of users. The connector supports provisioning and reconciliation for custom object classes.
The Active Directory connector supports fail-over. The backup domain controller URLs must be configured for handling fail-over. The connector will connect to the available backup domain controller if the primary domain controller is not reachable.
The Active Directory connector supersedes the Active Directory resource adapter. For migration information, see Migrating an Active Directory Resource Adapter.
This section provides the following additional information about the Active Directory connector:
The Active Directory connector supports the following operations:
Table 2-1 Active Directory Connector Operations
| Operation | Description |
|---|---|
|
Account provisioning |
|
|
Reconciliation |
Full and incremental reconciliation. See also Reconciliation for the Active Directory Connector. Data loading methods include:
|
Reconciliation compares the contents of the account index to what each resource currently contains. The Active Directory connector supports both full and incremental reconciliation. Reconciliation can perform the following functions:
Detect new and deleted accounts
Detect changes in account attribute values
Correlate accounts with Oracle Waveset users
Detect accounts that are not associated with Oracle Waveset users
Detect when a user has been moved from one container on a resource to another container on a resource
Active Sync listens or polls for changes to a resource, detecting incremental changes in real time. Active Sync must always connect to the same Active Directory server. If the Search Child Domains configuration property is not set, the Sync Domain Controller property must be configured to specify the hostname of a specific Sync Domain Controller because Active Sync must always connect to the same Domain Controller. If the Search Child Domains property is set, then the Sync Global Catalog Server property must be set to a specific Global Catalog server.
For information about limiting the number of repeated events that occur when you switch to a new domain controller, see Chapter 53, "Active Directory Synchronization Failover," in the Oracle Waveset 8.1.1 Resources Reference in the following library:
http://docs.oracle.com/cd/E19225-01/index.html
If the Active Directory connector is configured to sync from AD LDS, the Active Directory Domain Controller Hostname defines the server to contact. The Search Child Domain configuration property is ignored for AD LDS.
The Active Directory connector supports before and after actions, which use scripts (written in a supported scripting language) to perform activities on the Connector Server during a user create, update, or delete request.
For more information, see Chapter 51, "Adding Actions to Resources," in the Oracle Waveset 8.1.1 Resources Reference in the following library:
http://docs.oracle.com/cd/E19225-01/index.html
Before and after actions are mapped to the ScriptOnConnectorOp and ScriptOnResourceOp SPI operations in the ICF. The ScriptOnConnectorOp operation is supported by the default implementation of the framework.
See also Configuring Before and After Actions for the Active Directory Connector.
When a user's password is changed, to meet the password history requirements, the user might need to provide the previous password. The "User Provides Password On Change" option (WS_USER_PASSWORD attribute) is available in the Active Directory connector userForm.xml file. Several considerations are:
This attribute is ignored if the "PasswordNever Expires" option is set for the resource.
This attribute is not available in the Active Directory connector resource configuration page.
The BCDHostNames parameter provides support for failover of replicated target systems. If a target system goes down, operations can still be performed using a backup domain controller host. The target systems will have specific recovery methods (independent of the Active Directory connector), which will support the data synchronization for the replication of the terminals and hosts. The requirements for failover support include:
The target systems must be in the same domain.
The target systems must be SSO enabled (or have the same authorization credentials).
The Active Directory hierarchy must be the same (true copy).
For more information, see the BCDHostNames parameter in Table 2-2, "Active Directory Connector Resource Configuration Parameters".
The following table describes the configuration parameters that you specify when you configure a resource for the Windows target system. The resource contains connection information about the target system.
Table 2-2 Active Directory Connector Resource Configuration Parameters
| Parameter Name | Type | Required | Description |
|---|---|---|---|
|
Directory Administrator's Account |
String |
Yes |
Administrator's user name with which the system should authenticate. Can be either a username or a combination of domain name and user name in the form of For example: Administrator |
|
Directory Administrator's Password |
String |
Yes |
Administrator's password that should be used when authenticating. |
|
Object Class for User Objects |
String |
No |
Active Directory object class for user objects that will be managed on the specified resource. The default is User (which for most situations should be sufficient). |
|
Container |
String |
Yes |
Base context for all searches. For example: |
|
Create Home Directory |
Boolean |
No |
Specifies whether or not the home directory for the user will be created. |
|
Active Directory Domain Controller Hostname |
String |
No |
Domain controller: hostname, IP address, or domain name of the LDAP server. If not supplied, a serverless bind is used. For example: If the Active Directory connector is configured to sync from AD LDS, this parameter defines the server to contact. |
|
Search Child Domains |
Boolean |
No |
Set if you want searches of Active Directory to include child domains. In addition, the Search Container and Sync Search Context (see the sync settings) attributes must be set to the top of the parent domain. For example: Note. The parameter is ignored for AD LDS. |
|
Domain Name |
String |
Yes |
Name of the Windows domain. For example: |
|
Search Context |
String |
No |
Not currently used. |
|
Use SSL |
Boolean |
No |
Select if the connection to the target system must be encrypted through an SSL channel. The default is No. If set to Yes, this parameter enables SSL between the .NET Connector Server where the Active Directory bundle is deployed and Active Directory or AD LDS. Note. Even if the value is set to No, communication between the .NET Connector Server Active Directory will be of "Secure type". |
|
Delete Leaf Nodes of User Objects |
Boolean |
No |
Select if the associated leaf nodes of a User object to delete are intended to be removed along with the object. If not selected and the User object to delete has leaf nodes, the operation will fail and an error message will be displayed. |
|
Page Size |
Integer |
No |
Indicates the page size returned from Active Directory queries to the connector in a paged search. The default is 1000. Paging splits the entire result set of a query into smaller subsets called, appropriately, pages. In general, it is recommended that you set this value to the maximum page size for simple searches. By setting the parameter to the maximum value, you can minimize the network round trips necessary to retrieve each page, which tends to be the more expensive operation for simple searches. While you can specify a Page Size value greater than the Active Directory system's MaxPageSize value, the Active Directory server will ignore the Page Size value and use the MaxPageSize value instead. No exception will be generated in this case. In some cases, you might need to specify a smaller Page Size value to avoid time outs or overtaxing the server. Some queries are especially expensive, so limiting the number of results in a single page can help avoid this problem. |
|
Lockout Threshold in AD LDS |
Integer |
No |
Specifies the configured number of failed logon attempts that causes a user account to be locked out in an AD LDS instance. |
|
AD LDS Port |
Integer |
No |
Specifies the port number on which the AD LDS instance is listening for connections. |
|
Target is an AD LDS (ADAM) instance |
Boolean |
No |
Select if the target system is an AD LDS instance. The default is No. |
|
BCDHostNames |
String |
No |
To set BCDHostNames, specify the Active Directory domain controller host names separated by a semicolon. For example:
|
Windows Active Directory is a hierarchically based resource. The Active Directory connector identity template provides the default location in the directory tree where a user is created. The default identity template is:
CN=$fullname$,cn=Users,dc=mydomain,dc=com
Note:
For a container name, you must specify ou, cn, and dc in lower case.
You must replace the default template with a valid template for your deployment.
On the Active Directory connector side, secure communication is ensured by the API. Any bind to the directory is secured by the Windows Security Support Provider Interface (SSPI). Because password management requires an SSL channel for AD LDS, the Active Directory connector can be configured to communicate with the target system via an SSL channel.
The communication between the .NET Connector Framework and Oracle Waveset is encrypted by the framework, but it is also recommended that you use an SSL connection.
The administrative account configured in the Active Directory resource must have the permissions in Active Directory as shown in the following table.
Table 2-3 Active Directory Administrative Account Permissions
| Oracle Waveset Functionality | Active Directory Administrative Account Permissions |
|---|---|
|
Create user |
Create User Objects To create the account enabled, you must have the ability to Read/Write the To create with the password expired, you must be able to Read/Write the |
|
Delete user |
Delete User Objects |
|
Update users |
Read All Properties, Write All Properties Note: If only a subset of the properties are to be managed from Waveset, then Read/Write access can be given to just those properties. |
|
Change/Reset passwords Unlock user accounts Expire Active Directory user accounts |
User Object permissions:
User Property permissions:
|
By default, the .NET Connector Server runs as the local system account. This option is configurable through the Services MMC Snap-in.
if you run the .NET Connector Server as an account other than Local System, the Connector Server service account requires the "Act As Operating System" and "Bypass Traverse Checking" user rights. It uses these rights for pass-through authentication and for changing and resetting passwords in certain situations.
Most of the management of Active Directory is done using the administrative account specified in the resource. However, some operations are done as the Connector Server service account. Thus, the Connector Server service account must have the appropriate permissions to perform these operations. Currently, these operations are:
Creating home directories
Running actions (including before and after actions)
When performing before and after action scripts, the .NET Connector Server might need the "Replace a process level token" right. For example, this right is required if the .NET Connector Server attempts to run the script subprocess as another user, such as the resource administrative user. in this case, the .NET Connector Server process needs the right to replace the default token associated with that subprocess.
if this right is missing, the following error can be returned during subprocess creation:
"Error creating process: A required privilege is not held by the client"
The "Replace a process level token" right is defined in the Default Domain Controller Group Policy object and in the local security policy of workstations and servers. To set this right on a system, open the Local Security Policies application within the Administrative Tools folder, then navigate to Local Policies, User Rights Assignment, and then Replace a process level token.
The Active Directory connector is certified with the following components:
Table 2-4 Active Directory Connector Certified Components
| Component | Requirement |
|---|---|
|
Oracle Waveset |
Oracle Waveset 8.1 Update 1 Bundle Patch 6 or later |
|
Identity Connector Framework (ICF) |
ICF 1.2 or later |
|
Microsoft .NET Framework |
Microsoft .NET Framework 3.5 or later Note: To prevent a memory leak problem with Microsoft .NET Framework 3.5, apply the hotfix described in the following article: |
|
Target Systems |
Microsoft Active Directory
|
|
Target Systems (continued) |
MicrosoftActive Directory Lightweight Directory Services (AD LDS) or MicrosoftActive Directory ApplicationMode (ADAM)
|
Note:
The migration XML covers most of the cases. However, if your resource is customized so that the default migration is not applicable, you must edit the XML file for the MigrationForm.Org.IdentityConnector.ActiveDirectory.ActiveDirectoryConnector form before starting the migration process.
Before You Get Started: Install and configure the latest version of the .NET Connector Server, as described in Installing, Configuring, and Enabling Logging on the .NET Connector Server.
To migrate a Active Directory resource adapter to the Active Directory connector, follow these steps:
Make sure you have installed Oracle Waveset with the patch shown in Certified Components for the Active Directory Connector.
Log in to the Oracle Waveset Administrator interface.
Go to the Migrate Adapters page.
Select the Resource you want to migrate from.
Select the type of the connector you want to convert to.
On the next page, select the Active Directory connector version and the Connector Server to use.
Provide the Active Directory Domain Name.
Click Convert.
Note:
After you finish the migration, it is recommended that you test the configuration.
This section discusses the following topics:
Active Directory Connector Deployment Architecture With the .NET Connector Server
Enabling Reconciliation and Provisioning Operations Across Multiple Domains
The following figure shows the distributed deployment architecture with the Active Directory connector deployed in the .NET Connector Server.
Figure 2-1 Active Directory Connector Deployment Architecture with the .NET Connector Server
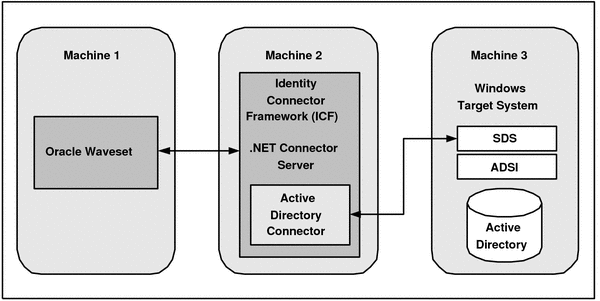
Machine 1 has Oracle Waveset deployed.
Machine 2 has the Active Directory connector bundle deployed in the .NET Connector Server. The .NET Connector Server is part of the Identity Connector Framework (ICF). The machine where the .NET Connector Server is installed must also have Microsoft .NET Framework 3.5 or later installed.
Machine 3 has the Windows target system deployed with either Active Directory or Active Directory Lightweight Directory Services (AD LDS).
Note:
In this scenario, Machine 2 and Machine 3 must be in the same domain.
If you prefer, you can also install the .NET Connector Server and the Active Directory connector bundle on the Windows target system. This machine must also have Microsoft .NET Framework 3.5 or later installed.
Oracle Waveset communicates directly with the Identity Connector Framework (ICF), which passes requests to the .NET Connector Server over the network.
The .NET Connector Server then serves as a proxy to provide access to the Active Directory connector, which is deployed within the .NET Connector Server. The results of operations performed on the connector are passed back to Oracle Waveset via the ICF.
Before you install the Active Directory connector, install and configure the .NET Connector Server, and configure the target system as follows:
Considering the .NET Connector Server Installation Locations
Installing, Configuring, and Enabling Logging on the .NET Connector Server
Delegating Control of Organizational Units and Custom Object Classes
The Active Directory connector is available on the Oracle Identity Manager Connector Downloads page:
http://www.oracle.com/technetwork/middleware/id-mgmt/downloads/connectors-101674.html
Note:
This section applies only when the Active Directory connector is configured to contact an Active Directory server and not for AD LDS.
Unless the Active Directory Domain Controller Hostname (LDAPHostName) resource attribute is set, the connector will perform a serverless bind to the directory. For the serverless bind to work, the .NET Connector Server must be installed on a system that is in a domain and that knows about the domain and directory to be managed. All Windows domains managed by a connector must be part of the same forest. Managing domains across forest boundaries is unsupported. If you have multiple forests, install at least one .NET Connector Server in each forest.
The Active Directory Domain Controller Hostname resource attribute tells the connector to bind to a particular DNS hostname or IP address. This is the opposite of a serverless bind. However, the Active Directory Domain Controller Hostname does not necessarily have to specify a specific domain controller. The DNS name of an Active Directory domain can be used. If the connector's DNS server is configured to return multiple IP addresses for that DNS name, then one of them will be used for the directory bind. This avoids having to rely on a single domain controller.
All operations require that the .NET Connector Server be a member of a domain.
Although the .NET Connector Server can be executed as a standalone Windows application, it is recommended that you install the .NET Connector Server using the installation package (ServiceInstall.msi). This package registers the .NET Connector Server as a Windows service and then automatically starts the service.
The machine where the .NET Connector Server is installed must also have Microsoft .NET Framework 3.5 or later installed.
This section discusses the following topics:
To install and configure the .NET Connector Server, follow these steps:
To install the .NET Connector Server, execute ServiceInstall.msi and follow the wizard. The wizard takes you through the installation process step-by-step. After completion, the .NET Connector Server is registered as a Windows service.
The ServiceInstall.msi file is included as part of the Oracle Waveset patch shown in Certified Components for the Active Directory Connector.
Start the Microsoft Services Console.
If the .NET Connector Server is running, stop it by stopping the Windows service.
To set a custom key for the .NET Connector Server, use the /setkey command-line argument, as follows:
Change to the directory where the .NET Connector Server was installed. The default directory is:
C:\Program Files\Identity Connectors\Connector Server
Execute the following command:
ConnectorServer.exe /setkey newkey
where newkey is the value for the new key.
This key is required by any client that connects to this .NET Connector Server.
Check the settings in the .NET Connector Server configuration file (ConnectorServer.exe.config). These settings are in the tag named AppSettings. For example:
<add key="connectorserver.port" value="8759" />
<add key="connectorserver.usessl" value="false" />
<add key="connectorserver.certificatestorename"
value="ConnectorServerSSLCertificate" />
<add key="connectorserver.ifaddress" value="0.0.0.0" />
The most common settings you might want to change are:
Port number: To change the port, set connectorserver.port to a value other than 8759.
SSL settings: To use SSL, set connectorserver.usessl to true and then set connectorserver.certificatestorename to your certificate store name.
Listening socket bind: To change the listening socket bind, set connectorserver.ifaddress to an address other than 0.0.0.0.
Trace settings: To set trace settings, see Enabling Logging for the Active Directory Connector.
Save the following configuration information from the .NET Connector Server installation for later use:
Host name or IP address
Connector Server port
Connector Server key values
Whether SSL is enabled
When you are finished configuring the .NET Connector Server, restart it by restarting the Windows service. Or, you can also restart the .NET Connector Server using the following command:
ConnectorServer.exe /run
The Active Directory connector uses the built-in logging mechanism of the .NET framework. Logging for the Active Directory connector is not integrated with Oracle Waveset. The logging level is set in the .NET Connector Server configuration file (ConnectorServer.exe.config).
To enable logging for the Active Directory connector, follow these steps:
Go to the directory where the ConnectorServer.exe file is installed. The default directory is C:\Program Files\Identity Connectors\Connector Server.
The ConnectorServer.exe.config file should be present in this directory.
In the ConnectorServer.exe.config file, add the following snippet, shown in bold text:
<system.diagnostics>
<trace autoflush="true" indentsize="4">
<listeners>
<remove name="Default" />
<add name="myListener" type="System.Diagnostics.TextWriterTraceListener"
initializeData="c:\connectorserver2.log" traceOutputOptions="DateTime">
<filter type="System.Diagnostics.EventTypeFilter" initializeData="Information" />
</add>
</listeners>
</trace>
<switches>
<add name="ActiveDirectorySwitch" value="4" />
</switches>
</system.diagnostics>
The value="4" sets the logging level to Verbose. This value can be set as follows:
| Value | Logging Level |
|---|---|
|
|
Verbose level. Most granular. |
|
|
Information level. |
|
|
Warning level. |
|
|
Error level. |
|
|
No logging. |
However, remember that the logging level has a direct effect on the performance of the .NET Connector Server.
After you make the configuration change, stop and then restart the .NET Connector Server service. Or, you can also restart the .NET Connector Server using the following command:
ConnectorServer.exe /run
Information about events that occur during the course of reconciliation and provisioning operations are stored in a log file. As you use the connector over a period time, the amount of information written to a log file increases. If no rotation is performed, then log files become huge.
To avoid such a scenario, perform the procedure described in this section to configure rotation of the log file.
To configure rotation of a log file on a daily basis:
Log in to the computer that is hosting the connector server.
Stop the Connector Server.
Back up the ConnectorServer.exe.config file. The default location of this file is C:\Program Files\Identity Connectors\Connector Server.
In a text editor, open the ConnectorServer.exe.config file for editing.
Search for the <listeners> and </listeners> elements and replace the text between these elements with the following:
<remove name="Default" /> <add name="FileLog"type="Microsoft.VisualBasic.Logging.FileLogTraceListener,Microsoft.VisualBasic,Version=8.0.0.0,Culture=neutral,PublicKeyToken=b03f5f7f11d50a3a" initializeData="FileLogWriter" traceOutputOptions="DateTime" BaseFileName="ConnectorServerDaily" Location="Custom" CustomLocation="C:\ConnectorServerLog\" LogFileCreationSchedule="Daily"> <filter type="System.Diagnostics.EventTypeFilter" initializeData="Information"/> </add>
Save and close the file.
Start the Connector Server.
See Also:
The following URL for more information about configuring log file rotation:
http://msdn.microsoft.com/en-us/library/microsoft.visualbasic.logging.filelogtracelistener.aspx
By default, user accounts that belong to the Account Operators group can manage only user and group objects. To manage organizational units or custom object classes, you must assign the necessary permissions to a user account. In other words, you must delegate complete control for an organizational unit or custom object class to a user or group object. In addition, you need these permissions to successfully perform provisioning of custom object classes.
This is achieved by using the Delegation of Control Wizard. An example for managing organizational units is creating organizational units.
To delegate control for an organizational unit or custom object class to a user account:
Note:
In a parent-child deployment environment or forest topology, perform this procedure on all the child domains.
In the Active Directory Users and Computers window, in the navigation tree, right-click the organizational unit whose control you want to delegate, and then click Delegate Control.
The Delegation of Control Wizard is displayed.
Note:
If you want to delegate control for all organization units under the root context, then delegate control at the root context level.
On the Welcome to the Delegation of Control Wizard page, click Next.
On the Users or Groups page, to select either a user or group to whom you want to delegate control:
Click Add.
In the Select Users, Computers, or Groups dialog box, enter a user or group name. For example, enter OIMUser.
Click Check Names.
Click OK to close the dialog box.
Click Next.
On the Tasks to Delegate page, select the Create a custom task to delegate option, and then click Next.
On the Active Directory Object Type page, select Only the following objects in the folder, and then select Organization Unit Objects. If you are delegating control for custom object classes, then select the custom object class for which you want to delegate control.
Select the Create selected objects in the folder and Delete selected objects in the folder options, and then click Next.
On the Permissions page:
For Organizational Units, select Full Control, click Next, and then click Finish.
For custom object classes, select the required permissions, click Next, and then click Finish.
It is recommended that you install the Active Directory connector bundle in the .NET Connector Server, as follows:
Change to the directory where the .NET Connector Server was installed.
Unzip the Active Directory connector ZIP file in the directory from Step 1.
Restart the .NET Connector Server service. Or, you can also restart the .NET Connector Server using the following command:
ConnectorServer.exe /run
Adding Attributes to Active Directory Connector Resource Forms
Adding Byte[] Datatype Attribute to Active Directory Connector Resource Forms
Displaying Group Names for Active Directory LDS or ADAM Resources
Configuring Before and After Actions for the Active Directory Connector
To create an Active Directory connector resource, follow these steps:
Log in to the Oracle Waveset Administrator interface.
Create the Active Directory connector resource by following the Create Windows Active Directory Connector Resource wizard.
Select the Active Directory Connector Version as "1.1.0.6380".
Select the .NET Connector Server on which the Active Directory connector bundle is deployed.
Specify values for the Active Directory connector, depending on your deployment. For more information, see:
To enable checking the password history for an Active Directory account when end-users change their password, the WS_USER_PASSWORD attribute is available in the Active Directory connector userForm.xml file. This attribute is ignored if the PasswordNever Expires field is set for the resource.
The Active Directory connector Group, Organizational unit, and Container resource forms are customizable. You can add attributes to these forms, as required by your deployment.For example, when you provision an organizational unit, the Name, Short Name, and Description attributes are available for the organization. However, when you create a resource object of type Organization, by default you see only the Name attribute.Therefore, to add additional attributes to provision an organizational unit, edit the Windows Active Directory Create Organizational Unit Form, as follows:
Go to the Oracle Waveset debug page:
http://host_name:port/idm/debug
Select Resource Form from the drop-down box, which is adjacent to List Objects, and then click List Objects.
Select the Windows Active Directory Create Organizational Unit Form from the list and click Edit.
Add additional attributes to the form. For example:
<Field name='organizational unit.attributes.description'>
<Display class='Text'>
<Property name='title' value='Description:'/>
</Display>
</Field>
Add any other target attributes to the Windows Active Directory Create Organizational Unit Form by following these same steps.You can also add attributes to the Windows Active Directory Create Group Form and Windows Active Directory Create Container Form, as required by your deployment.
You can add attributes of Byte[] datatype to connector resource forms such as User and Group, depending on your requirement. For example, you can add the thumbnailPhoto attribute to the User resource form as follows:
In a text editor, open the owglue\sample\connectors\ActiveDirectoryConnector-idmglue\UserForm.xml file located in the installation media.
Add additional attributes to the form. For example:
<Field name='accounts[$(RESOURCE_NAME)].thumbnailPhoto'> <Expansion> <cond> <isnull> <ref>FileSource</ref> </isnull> <ref>accounts[$(RESOURCE_NAME)].thumbnailPhoto</ref> <new class='com.waveset.util.Binary'> <ref>FileSource</ref> </new> </cond> </Expansion> </Field> <Field name='FileSource'> <Display class='FileUpload'> <Property name='title' value='Thumbnail Photo'/> </Display> </Field>
Import the User form as follows:
Click the Configure tab.
Click Import Exchange File.
Select the User resource form and then click Import.
Add the thumbnailPhoto attribute as follows:
Click the Resource tab.
Click Edit Resource Page, to open the resource to which you want to add the attribute.
The Edit RESOURCE_NAME Resource Wizard page is displayed.
On the Resource Parameters page, click Next.
On the Account Attributes page, click Add Attribute.
In the new row that is added to the table, specify the following values:
In the Identity System User Attributes column, enter thumbnailPhoto in the text field.
In the Attribute Type column, from the drop-down list, select binary.
In the Resource User Attribute column, enter thumbnailPhoto.
Click Save.
If you create an Active Directory LDS (AD LDS) or ADAM resource, groups for the resource are shown in Oracle Waveset without the group name for both provisioning and reconciliation.
To get the group name to display for an AD LDS or ADAMresource, edit the resource forms, as follows:
In the Windows Active Directory Create Group Form, replace all occurrences of samAccountName with cn.
In all other Active Directory connector resource forms, including the Windows Active Directory Update Group Form, replace samAccountName with userPrincipalName. Any references to samAccountName in these forms can cause undesirable behavior for an AD LDS or ADAMresource.
This section describes how to configure a "create after action" for the Active Directory connector, but the steps apply to all types of actions as well.
To configure a "create after action" for the Active Directory connector, follow these steps:
Import a resource action similar to the following example:
<?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE Waveset PUBLIC 'waveset.dtd' 'waveset.dtd'>
<Waveset>
<ResourceAction name='ADAfterCreate'>
<ResTypeAction restype='Windows Active Directory' timeout='6000'
actionType='SHELL' execMode='resource'>
<act>
echo create>> C:\Temp\%WSUSER_accountId%.txt
exit
</act>
</ResTypeAction>
</ResourceAction>
</Waveset>
Note. execMode can be set to either resource or connector; however, only resource is supported by the Active Directory connector. If execMode is set to connector, it will be mapped to the generic ScriptOnConnector SPI operation provided by the Connector Framework.
In Oracle Waveset, add the create after action attribute to the Identity System User Attribute column on the Active Directory resource.
Type IGNORE_ATTR in the Resource User Attribute column and leave the other values as the defaults. Then save the changes.
Add a form field to the resource specific user form (probably the AD IdC User Form) with the name as create after action. For example:
<Field name='accounts[$(RESOURCE_NAME)].create after action'> <Expansion> <s>ADAfterCreate</s> </Expansion> </Field>
You can now test the script.
This section describes how you can pass Active Directory connector process form parameters to scripts during the execution of before and after scripts. Visual Basic (VB), batch, and Perl scripts function similarly and can execute any commands that can be executed on the target system command line or shell.
The following example shows a Visual Basic script that consumes data dynamically from the process form. This is an example procedure for an After Create action, which requires creating a user also in an organizational unit other than the organizational unit where the user is provisioned.
Create a script file on the Oracle Waveset machine. For example:
C:\arg.vbs %givenName%
Note: There is a space between C:\arg.vbs and %givenName%.
On the machine hosting the target system, create the arg.vbs file in the C:\ directory.
Include the following lines in the arg.vbs file:
Set args = WScript.Arguments
GivenNameFromArg = args.Item(0)
lengthGivenName = Len(GivenNameFromArg) - 2
GivenNameTrim = Mid(GivenNameFromArg, 2, lengthGivenName)
Set objOU = GetObject("LDAP://ldapserver.example.com:389/OU=org,dc=example,dc=com")
Set objUser = objOU.Create("User", "cn=scriptCreate" & GivenNameTrim )
objUser.Put "givenName", "scriptCreate" & GivenNameTrim
objUser.Put "sAMAccountName", "scriptCreate " & GivenNameTrim
objUser.Put "userPrincipalName", "scriptCreate" & GivenNameTrim
objUser.Put "displayName", "scriptCreate" & GivenNameTrim
objUser.Put "sn", "scriptCreate" & GivenNameTrim
objUser.SetInfo
Save and close the arg.vbs file.
Provision a user account on Oracle Waveset.
The Active Directory connector supportsMicrosoft Active Directory Lightweight Directory Services (AD LDS), formerly called Active Directory ApplicationMode (ADAM). To configure the Active Directory connector for AD LDS, follow these steps:
Go to the Oracle Waveset debug page:
http://host_name:port/idm/debug
Select Resource from the drop-down box adjacent to List Objects, and then click on List Objects.
Edit the AD LDS resource, as follows:
Modify the mapping of accountID to UserPrincipalName. The accountID is mapped to sAMAccountName. Because sAMAccountName is not present in AD LDS, update the following line by specifying mapName='UserPrincipalName':
<AccountAttributeType id='15' name='accountId' syntax='string' mapName='sAMAccountName' mapType='string'>
Modify the Group Object type by specifying cn as displayNameAttr instead of sAMAccountName. In the following lines, by replace samAccountName with cn:
<ObjectAttributes idAttr='distinguishedName' displayNameAttr='samAccountName' descriptionAttr='description' objectClassAttr='objectclass'> <ObjectAttribute name='samAccountName' type='string'/>
Edit the Resource Form (Windows Active Directory Create Group Form) by selecting the Resource Form from the drop-down adjacent to List Objects. Then, replace all references to sAMAccountName with cn.
The Active Directory connector supports reconciliation and provisioning operations across multiple domains in a single forest. Reconciliation runs are performed by using the Global Catalog Server and provisioning operations are performed by using LDAP referrals. If you want to enable reconciliation and provisioning across multiple domains, then perform the procedure described in the following sections:
To perform reconciliation across multiple domains, this connector uses both the domain controller and the Global Catalog Server for fetching records from the target system.
During reconciliation, records from the Global Catalog Server are fetched to the connector. After a record is fetched into the connector, the distinguishedName and uSNChanged attribute values are read. By using the distinguishedName, the connector performs an LDAP query on the domain controller that contains the actual data (referrals are used here). This approach is used for reconciliation because the Global Catalog Server has only partial set of records. Complete data can only be fetched from the domain controller.
After all records are fetched, Oracle Waveset keeps track of the maximum value of the uSNChanged attribute of a domain controller on which the Global Catalog Server is running. In incremental mode, only records whose uSNChanged attribute values are greater than current value in the Latest Token attribute are fetched from the Global Catalog Server.
Therefore, any updates made to a record on the target system must update the uSNChanged attribute of that record in the Global Catalog Server so that the connector can detect records that have been updated since the last reconciliation run and then fetch them into Oracle Waveset.
To enable reconciliation across domains, follow these steps:
Set the value of the Search Child Domains entry to yes.
Specify the name of the domain controller that is hosting the Global Catalog Server as the value of the SyncGlobalCatalogServer in the resource configuration.
Note:
While performing group reconciliation in a cross-domain environment, the connector fetches only those groups of the account that are visible to the domain controller on which the account is present.
In a parent-child deployment environment of the target system, before performing provisioning operations across multiple domains, it is expected that the target system resource is configured with the parent domain. In a replication environment of the target system, before performing provisioning operations across multiple domains, it is expected that the target system resource is configured with any of the domain controllers.
This scenario is illustrated by the following example.
Suppose a parent-child domain environment in which the parent domain is dc1 and child domain is dc2. The target system resource is configured to include dc1 as the value of the LDAPHostName parameter the name of the parent domain as the value of theDomainName parameter.
During provisioning, if you select an organization that belongs to the child domain, multiple groups that span across domains, and the manager from the parent domain, then LDAP referrals are internally used by ADSI (Active Directory Service Interfaces). This is because all connectors operations are leveraged to ADSI, which enables creation of an account in the child domain even without providing any details of the child domain in the Resource Configuration.
All this information is internally calculated depending upon the organization that is selected during the provisioning operation. In the connector, the referral chasing option is set to All, which means that all referrals are chased when any referral is provided by the domain controller. Therefore, no explicit configuration procedure is required to enable provisioning across multiple domains.
For more information, see the ADSI documentation about LDAP referrals.
To perform the procedure described in this section, all domain controllers in the forest must be running Microsoft Windows Server 2003 or later, and the forest functional mode must be Microsoft Windows Server 2003 or later. For more information on dynamic auxiliary object classes, see "Dynamically Linked Auxiliary Classes (Windows)" at the following Web site:
http://msdn.microsoft.com/en-us/library/windows/desktop/ms676289%28v=vs.85%29.aspx
The following is the procedure to add auxiliary classes to users:
Create an entry for the AccountObjectClass attribute in the owglue\sample\connectors\ActiveDirectoryConnector-idmglue\ResourceWizard.xml file that is located in the connector installation media.
If the auxiliary class has mandatory attributes, then create an entry for the ObjectClassMandatoryAttributes attribute and the mandatory attributes in the owglue\sample\connectors\ActiveDirectoryConnector-idmglue\ResourceWizard.xml file that is located in the connector installation media. Ensure to set the value of the Display class element to MultiSelect when you create this entry.
Save the file.
Import the ResourceWizard.xml file as follows:
Click the Configure tab.
Click Import Exchange File.
Select the ResourceWizard.xml file and then click Import.
To add the auxiliary class to the resource in Oracle Waveset:
Note:
To explain this procedure, it has been assumed that CustomAuxClass is an auxiliary class with the following attributes:
CustomAttribute1
This is a mandatory attribute.
CustomAttribute2
This is an optional attribute.
CustomAttribute3
This is a mandatory attribute.
Open an Active Directory resource.
Enter the name of the auxiliary class in the column corresponding to the AccountObjectClass attribute.
For example, enter CustomAuxClass.
From the list of attributes displayed in the colum corresponding to the ObjectClassMandatoryAttributes attribute, select the mandatory attributes of the auxiliary class, and then move it to the right column.
For example, select CustomAttribute1 and CustomAttribute3 and in the left column and move it to the right column.
Click Next.
In the Account Attributes tab, add all the attributes of the auxiliary class. For example, you must add the CustomAttribute1, CustomAttribute2, and CustomAttribute3 attributes.
Click Save.
To display the custom attributes on the user form in Oracle Waveset:
Go to the Oracle Waveset debug page:
http://host_name:port/idm/debug
In the column corresponding to List Objects, select User Form.
Click List Objects.
Click the edit button corresponding to the User Form (for example, AD IdC User Form).
Add the following lines for each custom attribute:
<Field name='accounts[$(RESOURCE_NAME)].<AttributeName>'>
<Display class='Text'>
<Property name='title' value="<AttributeName>"/>
<Property name='size' value='25'/>
</Display>
</Field>
The following is a sample of code that you must add for the CustomAuxClass auxiliary class:
<Field name='accounts[$(RESOURCE_NAME)].CustomAttribute1'>
<Display class='Text'>
<Property name='title' value=" CustomAttribute1"/>
<Property name='size' value='25'/>
</Display>
</Field>
<Field name='accounts[$(RESOURCE_NAME)].CustomAttribute2'>
<Display class='Text'>
<Property name='title' value=" CustomAttribute2"/>
<Property name='size' value='25'/>
</Display>
</Field>
Click Save.
This connector supports adding custom object classes to users. The custom object class has the attributes of the user and custom attributes.
The following is the procedure to include a custom object class:
Note:
To explain this procedure, it has been assumed that CustomObjectClass is a custom object class with the following attributes:
CustomStringAttr, CustomIntAttr
These are mandatory attributes.
SecondCustomStringAttr
This is an optional attribute.
If the custom object class has mandatory attributes, then create an entry for the ObjectClassMandatoryAttributes attribute in the owglue\sample\connectors\ActiveDirectoryConnector-idmglue\ResourceWizard.xml file that is located in the connector installation media. Ensure to set the value of the Display class element to MultiSelect when you create this entry.
The following is a sample of code to add the ObjectClassMandatoryAttributes attribute and set the Display class element to Multiselect:
<Field name="resourceAttributes[ObjectClassMandatoryAttributes].value" required="false">
<Display class="MultiSelect">
<Property name="title" value="ObjectClassMandatoryAttributes"/>
<Property name="allowedValues">
<List>
<String>CustomStringAttr</String>
<String>CustomIntAttr</String>
</List>
</Property>
</Display>
</Field>
Save the file.
Import the ResourceWizard.xml file as follows:
Click the Configure tab.
Click Import Exchange File.
Select the ResourceWizard.xml file and then click Import.
To add the custom object class to the resource in Oracle Waveset:
Note:
To explain this procedure, it has been assumed that CustomAuxClass is an auxiliary class with the following attributes:
CustomAttribute1
This is a mandatory attribute.
CustomAttribute2
This is an optional attribute.
CustomAttribute3
This is a mandatory attribute.
Open an Active Directory resource.
Enter the name of the custom object class in the column corresponding to the Object Class for User Objects attribute.
For example, enter CustomObjectClass.
Click Next.
In the Account Attributes tab, add all the attributes of the custom object class. For example, you must add the CustomStringAttr, CustomIntAttr and SecondCustomStringAttr attributes.
Click Save.
To display the custom attributes on the user form in Oracle Waveset:
Go to the Oracle Waveset debug page:
http://host_name:port/idm/debug
In the column corresponding to List Objects, select User Form.
Click List Objects.
Click the edit button corresponding to the user form (for example, AD IdC User Form).
Add the following lines for each custom attribute:
<Field name='accounts[$(RESOURCE_NAME)].<AttributeName>'>
<Display class='Text'>
<Property name='title' value="<AttributeName>"/>
<Property name='size' value='25'/>
</Display>
</Field>
The following is a sample of code that you must add for the CustomObjectClass auxiliary class:
<Field name='accounts[$(RESOURCE_NAME)].CustomStringAttr'>
<Display class='Text'>
<Property name='title' value="CustomStringAttr"/>
<Property name='size' value='25'/>
</Display>
</Field>
<Field name='accounts[$(RESOURCE_NAME)].SecondCustomStringAttr'>
<Display class='Text'>
<Property name='title' value="SecondCustomStringAttr"/>
<Property name='size' value='25'/>
</Display>
</Field>
<Field name='accounts[$(RESOURCE_NAME)].CustomIntAttr'>
<Display class='Text'>
<Property name='title' value="CustomIntAttr"/>
<Property name='size' value='25'/>
</Display>
</Field>
Click Save.
This section lists dependencies and limitations related to using the Active Directory connector, including the following section:
Note:
This section applies only when the Active Directory connector is configured to contact an Active Directory server and not for AD LDS.
In a default configuration, pass-through authentication is accomplished by sending the user ID and password only. These two attributes are configured in the AuthnProperties element in the resource object's XML as w2k_user and w2k_password. Without a domain specification, the Active Directory connector searches all known domains and tries to authenticate the user in the domain that contains the user.
In a trusted multi-domain environment, there can be two possible situations:
All domains contain a synchronized user and password combination.
The user/password combination is domain dependent.
When the user/password combination is synchronized, configure your Active Directory resources so that they are common resources.
For more information about setting up a common resource, see the Oracle Waveset 8.1.1 Business Administrator's Guide in the following library:
http://docs.oracle.com/cd/E19225-01/index.html
In an environment with multiple trusted domains and Active Directory forests, the authentication can fail using any of these configurations because the Global Catalog does not contain cross-forest information. If a user supplies a wrong password, it could also lead to account lockout in the user's domain if the number of false attempts is greater than the lockout threshold.
Login failures will occur in domains if the user exists in the domain and the password is not synchronized.
It is not possible to use multiple data sources for the domain information in one Login Module Group.
This section provides the following information about the object classes and attributes supported by the Active Directory connector:
__GROUP__ (Group) Object Class for the Active Directory Connector
organizationalUnit Object Class for the Active Directory Connector
Note:
If you wish, you can change the provisioning or reconciliation attribute map by adding arbitrary attributes (using the supported attribute types) defined in the Active Directory schema on the object class. You can also remove non-operational attributes.
The Active Directory connector also supports custom object classes and different object classes for different types of users. The connector supports the provisioning and reconciliation for custom object classes. For example, you might create a custom object class such as ObjectClass1, extending the USER.
__ACCOUNT__ Object Class for the Active Directory ConnectorUnless noted otherwise, an attribute is single-valued and optional, and can be created, updated, and read.
Note:
When you perform group reconciliation for the first time, the connector fetches all groups from the target system and stores it in Oracle Waveset cache. From this point onward, whenever you open the user form, all groups are loaded from the cache. Whenever you add a new group in the target system, then you must clear cache for the new group to reflect in Oracle Waveset. Similarly, everytime you create a new resource, you must clear cache. To clear the cache, navigate to debug page and click Clear Resource Object List Cache.
Table 2-5 __ACCOUNT__ Object Class Attributes for the Active Directory Connector
| Attribute Name | Type | Description |
|---|---|---|
|
|
String |
For AD DS only; not for AD LDS. |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
Multi-valued. |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
- |
|
|
String |
For AD DS only; not for AD LDS. |
|
|
String |
For AD DS only; not for AD LDS. |
|
|
Integer |
For AD DS only; not for AD LDS. |
|
|
Integer |
For AD DS only; not for AD LDS. |
|
|
Integer |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
Integer |
For AD DS only; not for AD LDS. |
|
|
Integer |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
Integer |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
Integer |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
Integer |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
Integer |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
Integer |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
String |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
String |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
String |
Cannot be created or updated. For AD DS only; not for AD LDS. |
|
|
String |
Cannot be created or updated. |
|
|
String |
Cannot be created or updated. |
|
|
String |
Multi-valued. |
|
|
String |
Cannot be created or updated. |
|
|
String |
Cannot be created or updated. |
|
|
String |
For AD DS only; not for AD LDS. |
|
|
Boolean |
- |
|
|
String |
Multi-valued. Not readable and not returned by default. Can be created only. |
|
|
Boolean |
- |
|
|
Boolean |
- |
|
|
Boolean |
- |
|
|
GuardedString |
- |
|
|
GuardedString |
Multi-valued. Not readable and not returned by default. |
|
|
String |
Multi-valued. |
|
|
String |
- |
|
|
String |
- |
|
|
String |
Required. |
|
|
Boolean |
Cannot be read. |
|
|
Long |
Cannot be created or updated. |
|
|
String |
Cannot be created or updated and not returned by default. |
|
|
String |
Cannot be created or updated and not returned by default. |
__GROUP__ (Group) Object Class for the Active Directory ConnectorThe Active Directory connector supports the attributes shown in the following table by default. Support for other attributes is also provided by the Active Directory connector. To include additional attributes, add the desired attributes to the ADgroupcreate.xml form and then import the revised form into Oracle Waveset. For more information see "Adding Attributes to Active Directory Connector Resource Forms".
Unless noted otherwise, an attribute is single-valued and optional, and can be created, updated, and read.
Table 2-6 __GROUP__ (Group) Object Class Attributes for the Active Directory Connector
| Attribute Name | Type | Description |
|---|---|---|
|
|
String |
For AD DS only; not for AD LDS. |
|
|
String |
- |
|
|
String |
- |
|
|
String |
For AD DS only; not for AD LDS. |
|
|
Integer |
- |
|
|
String |
Multi-valued. Not readable and not returned by default. |
organizationalUnit Object Class for the Active Directory ConnectorThe Active Directory connector supports the attributes shown in the following table by default. Support for other attributes is also provided by the Active Directory connector. To include additional attributes, add the desired attributes to the ADorganizationalunitcreate.xml form and then import the revised form into Oracle Waveset. For more information see Adding Attributes to Active Directory Connector Resource Forms.
Note:
For the Active Directory connector to provision an organizational unit, an organization must already exist in the Active Directory or AD LDS target resource. Otherwise, the Active Directory connector supports the provisioning of sub-organizational units only.
Unless noted otherwise, an attribute is single-valued and optional, and can be created, updated, and read.
The syntax (or type) of an attribute usually determines whether an attribute is supported. In general, Oracle Waveset supports Boolean, string, and integer syntaxes. Binary strings and similar syntaxes are not supported. This section provides the following information:
The following table lists the Active Directory syntaxes supported by Oracle Waveset:
Table 2-8 Active Directory Syntaxes Supported by Oracle Waveset
| Active Directory Syntax | Waveset Syntax | Syntax ID | OM ID | ADS Type |
|---|---|---|---|---|
|
|
Boolean |
2.5.5.8 |
1 |
|
|
|
String |
2.5.5.9 |
10 |
|
|
|
Integer |
2.5.5.9 |
2 |
|
|
|
String |
2.5.5.1 |
127 |
|
|
|
String |
2.5.5.13 |
127 |
|
|
|
String |
2.5.5.5 |
22 |
|
|
|
String |
2.5.5.5 |
19 |
|
|
|
String |
2.5.5.6 |
18 |
|
|
|
String |
2.5.5.2 |
6 |
|
|
|
String |
2.5.5.4 |
20 |
|
|
|
String |
2.5.5.12 |
64 |
|
|
|
String |
2.5.5.16 |
65 |
|
|
|
String |
2.5.5.16 |
65 |
|
The following table lists the Active Directory syntaxes that are not supported by Oracle Waveset:
Table 2-9 Active Directory Syntaxes Not Supported by Oracle Waveset
| Syntax | Syntax ID | OM ID | ADS Type |
|---|---|---|---|
|
DN with Unicode string |
2.5.5.14 |
127 |
|
|
DN with binary |
2.5.5.7 |
127 |
|
|
OR-Name |
2.5.5.7 |
127 |
|
|
Replica Link |
2.5.5.10 |
127 |
|
|
NT Security Descriptor |
2.5.5.15 |
66 |
|
|
Octet String |
2.5.5.10 |
4 |
|
|
SID String |
2.5.5.17 |
4 |
|
|
UTC Time String |
2.5.5.11 |
23 |
|
|
Object(Access-Point) |
2.5.5.14 |
127 |
N/A |
Oracle Waveset also supports the jpegPhoto and thumbnailPhoto account attributes, which use the Replica Link syntax. These attributes are write-only fields. This means that Oracle Waveset does not display the value of these attributes after reconciliation. The jpegPhoto and thumbnailPhoto attributes can be provisioned only if the account performing the provisioning operation has Admin privileges. Note that the size limit for the jpegPhoto and thumbnailPhoto attributes is 100 KB, but it is recommended to keep the size below 10K. Similarly, recommended thumbnail photo size in pixels is 96x96. See Adding Byte[] Datatype Attribute to Active Directory Connector Resource Forms for more information about adding these attributes to the user form.
The following sample forms are provided with the Active Directory connector:
Windows Active Directory Create Container Form (ADcontainercreate.xml)
Windows Active Directory Create Group Form (ADgroupcreate.xml)
Windows Active Directory Create Organizational Unit Form (ADorganizationalunitcreate.xml)
Windows Active Directory Update Container Form (ADcontainerupdate.xml)
Windows Active Directory Update Group Form (ADgroupupdate.xml)
Windows Active Directory Update Organizational Unit Form (ADorganizationalunitupdate.xml)
In addition, the following forms are also provided: migration.xml, resourceWizard.xml, postProcess.xml, and userForm.xml.
Waveset supports the following Active Directory objects:
Table 2-10 Supported Active Directory Objects
| Resource Object | Supported Features | Attributes Managed |
|---|---|---|
|
Group |
Create, update, delete |
|
|
DNS Domain |
Find |
|
|
Organizational Unit |
Create, delete, find |
|
|
Container |
Create, delete, find |
|
The attributes that can be managed on resource objects are also generally dictated by the attribute syntaxes. The attributes for these object types are similar as those for user accounts and are supported accordingly.
To check the password history for an Active Directory account when a user changes the password, the user must provide an AD password. To enable this feature, you must pass the current password value to the __CURRENT_PASSWORD__ attribute, and then add this attribute to the End User Change Password form.
Go to the Oracle Waveset debug page:
http://host_name:port/idm/debug
In the column corresponding to List Objects, select User Form.
Click List Objects.
Click the edit button corresponding to the End User Change Password Form.
Add the following code snippet:
<Field name='resourceAccounts.currentResourceAccounts[RESOURCE_NAME].attributes.CURRENT_PASSWORD'>
<Display class='Text'>
<Property name='title' value='CurrentPassword'/>
<Property name='secret' value='true'/>
</Display>
</Field>
Click Save.
Add the __CURRENT_PASSWORD__ attribute as follows:
Click the Resource tab.
Click Edit Resource Page, to open the resource to which you want to add the attribute.
The Edit RESOURCE_NAME Resource Wizard page is displayed.
On the Resource Parameters page, click Next.
On the Account Attributes page, click Add Attribute.
In the new row that is added to the table, specify the following values:
In the Identity System User Attributes column, enter CURRENT_PASSWORD in the text field.
In the Resource User Attribute column, enter __CURRENT_PASSWORD__.
Click Save.
Go to the Oracle Waveset debug page:
http://host_name:port/idm/debug
Open the resource, search for the CURRENT_PASSWORD attribute, and then add the view as follows:
<AccountAttributeType id='60' name='CURRENT_PASSWORD' syntax='encrypted' mapName='__CURRENT_PASSWORD__' mapType='string' writeOnly='true'>
<Views>
<String>Password</String>
<String>LoginChange</String>
</Views>
</AccountAttributeType>
Click Save.
From now onward, whenever an attempt to change the account password is made, the user is prompted to enter the current password. The password history is checked before completing the password change operation.
This section provides solutions to problems you might encounter after you deploy or while using the Active Directory connector.
Table 2-11 provides solutions to problems you might encounter with the Microsoft Active Directory User Management connector.
Table 2-11 Troubleshooting the Active Directory Connector
| Problem | Solution |
|---|---|
|
The following error is encountered while updating a user: Account not found in Resource |
This error is encountered if there are multiple domain controllers configured for the domain. To fix this issue, add a field to ResourceWizard.xml as follows:
<Field name="resourceAttributes[SyncDomainController].value" required="false">
<Display class="Text">
<Property name="title" value="SyncDomainController"/>
<Property name="help" value="SyncDomainController"/>
</Display>
</Field>
Reimport the xml file and provide the domain controller (Host) value for the same in the resource form. |