| Oracle® Waveset 8.1.1 Connector Reference Release 8.1.1 E25959-06 |
|
|
PDF · Mobi · ePub |
| Oracle® Waveset 8.1.1 Connector Reference Release 8.1.1 E25959-06 |
|
|
PDF · Mobi · ePub |
This chapter includes the following information about the AS400 connector for Oracle Waveset:
The AS400 connector for Oracle Waveset supports provisioning to IBM AS400 resources.
The AS400 connector is implemented using the Identity Connector Framework (ICF). The ICF provides a container that separates the connector bundle from the application. The ICF also provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. For more information about the ICF, see Chapter 1, "Identity Connectors Overview".
The AS400 connector supersedes the OS/400 resource adapter. To migrate from a resource adapter deployment, see Migrating an AS400 Connector.
This section provides the following information about the AS400 connector:
The following figure shows the AS400 connector architecture.
The AS400 connector architecture includes these components:
Oracle Waveset includes the connector integration files. These files are XML files that provide the configuration information necessary to transform data from a resource to Oracle Waveset. Integration files are sometimes called the connector "glue" code.
The Identity Connector Framework (ICF) provides basic provisioning, logging, and other functions that Oracle Waveset (and Oracle Identity Manager) connectors can use.
The AS400 connector requires the JTOpen library (jt400.jar file) to access the OS/400 target system.
The AS400 connector supports these provisioning operations:
Create account
Update account
Delete account
Enable/disable account
Reset password
Before and after actions
The AS400 connector for Oracle Waveset supports the configuration parameters shown in the following table.
Table 3-1 Configuration Properties for the AS400 Connector
| Name | Type | Required | Description |
|---|---|---|---|
|
|
String |
Yes |
Administrator account name. This property was |
|
|
GuardedString |
Yes |
Administrator password. This property was |
|
|
String |
Yes |
Hostname or IP address of the AS400 resource to connect to. |
|
|
Boolean |
Yes |
Indicates whether to connect to the host using SSL. The default value is |
The AS400 connector supports the __ACCOUNT__ object class, which represents OS/400 user profiles. The AS400 connector can also list OS/400 group profiles, denoted by the __GROUP__ object class.
An AS400 connector resource supports additional new attributes compared to the OS/400 resource adapter, as listed in New Account Attributes for the AS400 Connector.
Those new attributes are stored in the OS/400 directory entry object associated with the account. If these new attributes are not required, you can build your own user form to skip these extra attributes. An alternative approach is to remove those attributes from the Resource Schema using the Resource Wizard.
The AS400 connector creates a directory entry if it is absent on the OS/400 target system, whenever attribute update is invoked on an OS/400 account.
This section provides the following security information for the AS400 connector:
The AS400 connector by default uses Secure Sockets Layer (SSL) to talk to the AS400 resource. The usage of SSL is controlled by the useSSL configuration property.
Note:
The AS400 connector uses an account with the administrative privileges described below. For increased security, it is recommended that you create a separate account, apart from QSECOFR (the OS/400 security officer account).
The following administrative privileges are required for the AS400 connector:
Create Account — CRT: To add an OS/400 user, the administrator must have all of the following:
*SECADM special authority
*USE authority to the initial program, initial menu, job description, message queue, output queue, and attention-key-handling program if specified
*CHANGE and object management authorities to the group profile and supplemental group profiles, if specified
Update Account — CHG: The user must have *SECADM special authority, and *OBJMGT and *USE authorities to the user profile being changed, to specify this command. *USE authority to the current library, program, menu, job description, message queue, print device, output queue, or ATTN key handling program is required to specify these parameters.
Delete Account — DLT: The user must have use (*USE) and object existence (*OBJEXIST) authority to the user profile. The user must have existence, use, and delete authorities to delete a message queue associated with and owned by the user profile. The user profile cannot be deleted if a user is currently running under the profile, or if it owns any objects and OWNOBJOPT(*NODLT) is specified.
All objects in the user profile must first either be transferred to new owners by using the Change Object Owner (CHGOBJOWN) command or be deleted from the system. This can also be accomplished by specifying OWNOBJOPT(*DLT) to delete the objects or OWNOBJOPT(*CHGOWN user-profile-name) to change the ownership.
Authority granted to the user does not have to be specifically revoked by the Revoke Object Authority (RVKOBJAUT) command; it is automatically revoked when the user profile is deleted.
Search or Reconcile Account — DSP: The user name can be specified as USRPRF(*ALL) or USRPRF(generic*-user-name) only when TYPE(*BASIC) and OUTPUT(*OUTFILE) are specified.
Note:
If the administrator requires additional rights, use the following commands from the OS/400 console:
CRTUSRPRF USRPRF (adminUserName) AUT (list-of-necessary-permissions) CHGUSRPRF USRPRF (adminUserName) SPCAUT (list-of-necessary-permissions)
The list-of-necessary-permissions can differ for each administrator and should be determined based on your deployment's requirements.
Also, *USE and *CHANGE are values for the GRPAUT (Group Authority) parameter of the CHGUSRPRF command. Group Authority specifies the authority given to the group profile for newly created objects.
The AS400 connector for Oracle Waveset is certified with the following components:
The AS400 connector is localized in the following languages:
Arabic
Chinese (Simplified)
Chinese (Traditional)
Danish
French
German
Italian
Japanese
Korean
Portuguese (Brazilian)
Spanish
To change the language, specify the lang and cntry URL parameters. For example, to access Oracle Waveset in the Japanese language:
http://domain:port/idm/?lang=ja&cntry=JP
If you currently have the OS/400 resource adapter installed, this section describes how to migrate to the AS400 connector.
Oracle Waveset provides the required connector glue code. The installation script places the connector bundle into the proper locations on the application server and loads the required upgrade XML files.
To migrate to an AS400 connector, follow these steps:
Make sure you have installed Oracle Waveset with the patch shown in Certified Components for the AS400 Connector.
Log in to the Oracle Waveset Administrator interface as an Administrator.
Select the Resources tab and then the Migrate Adapters tab.
Follow the Migration Wizard to complete the migration. A script runs in the background that updates the schema map.
The AS400 connector is backwards compatible with the OS/400 resource adapter. All forms, workflows, and tasks should work the same as before you migrate the adapter.
The AS400 connector supports the following new account attributes. These attributes were not supported by default in the OS/400 resource adapter.
Note:
These new attributes require a directory entry object to be created on the OS/400 target system. The directory entry has lazy initialization, so it is created only if the application explicitly provides any of these new attributes.
For a description of these new attributes, including the specific values allowed, see Table 3-4, "Account Attributes for the AS400 Connector".
PASSWORD_CHANGE_INTERVAL
ACCOUNTING_CODE
ADDRESS1
ADDRESS2
BUILDING
COMPANY
DEPARTMENT
FAX
FIRST_NAME
FULL_NAME
GROUP_AUTHORITY
GROUP_PROFILE_NAME
JOB_TITLE
LAST_NAME
LOCATION
MIDDLE_NAME
OFFICE
PREFERRED_NAME
STORAGE_USED
SUPGRPPRF
TELEPHONE
The following account attributes have been renamed for the AS400 connector:
Table 3-3 Renamed Account Attributes for the AS400 Connector
| Adapter Attribute Name | Connector Attribute Name | Connector Data Type |
|---|---|---|
|
|
|
String |
|
|
|
Long |
|
|
|
Boolean |
|
|
|
GuardedString |
|
|
|
Long |
|
|
|
Boolean |
The legacy OS/400 resource adapter supported a customized version of the Delete user operation, supported by the OS400Deprovision form included in the sample directory of the Waveset installation. The AS400 connector preserves this support, although the following account attributes used for this feature have been replaced with operation options:
GRPPRF
OWNOBJOPT
You can deploy the AS400 connector either locally in Oracle Waveset or remotely in the Connector Server, as described in the following sections:
Note:
In a production environment, it is recommended that you deploy the AS400 connector in the Connector Server.
To install the AS400 connector, you must have access to the file system on the application server.
In the following procedure, WavesetInstallDir refers to the location where Oracle Waveset is deployed.
To install the AS400 connector in Oracle Waveset, follow these steps:
Download the JTOpen library from the following location:
Unzip the JTOpen library in a temporary directory and find the jt400.jar file.
Stop the Oracle Waveset web application.
If a previous version of thejt400.jar file does not already exist, copy the jt400.jar file to the WavesetInstallDir/WEB-INF/lib directory.
or
If a previous version of thejt400.jar file does already exist, copy the jt400.jar file inside the AS400 connector JAR, as follows:
Go to the WavesetInstallDir/WEB-INF/bundles directory, where the org.identityconnectors.as400 bundle resides.
Add the jt400.jar file to the /lib subdirectory of the AS400 connector JAR. The result is the following layout inside the AS400 connector JAR:
org.identityconnectors.as400-1.0.0.jar
/META-INF
/org
/lib
jt400.jar
Start the Oracle Waveset web application.
Log in to the Oracle Waveset Administrator interface.
Before you begin, consider these requirements. For the JDK requirements. see Certified Components for the AS400 Connector. If necessary, see your JAVA_HOME environment variable to point to your specific installation.
This section describes the following subsections:
If you install the AS400 connector in the Connector Server, the following figure shows the distributed deployment architecture.
Figure 3-2 AS400 Connector Deployment Architecture With the Connector Server
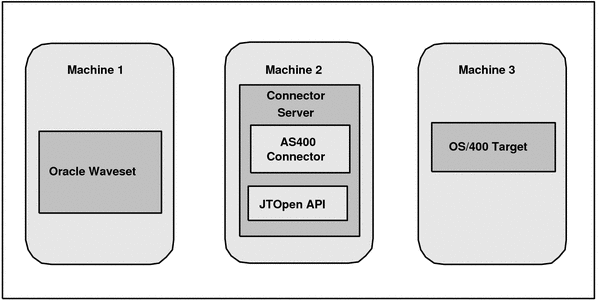
Machine 1 has Oracle Waveset deployed.
Machine 2 has the AS400 connector installed in the Connector Server. The Connector Server is part of the Identity Connector Framework (ICF).
The jt400.jar file from the JTOpen library must be installed in the CONNECTOR_SERVER_HOME/lib directory.
For detailed installation information, see Installing the AS400 Connector in the Connector Server.
Machine 3 has the OS/400 target deployed.
To install and configure the Connector Server, follow these steps:
Create a new directory on the machine where you want to install the Connector Server. In this section, CONNECTOR_SERVER_HOME represents this directory.
Unzip the Connector Server package in your new directory from Step 1. The Connector Server package is available with the Identity Connector Framework (ICF).
In the ConnectorServer.properties file, set the following properties, as required by your deployment. The ConnectorServer.properties file is located in the conf directory.
| Property | Description |
|---|---|
|
|
Port on which the Connector Server listens for requests. The default is 8759. |
|
|
Directory where the connector bundles are deployed. The default is |
|
|
Directory in which to place dependent libraries. The default is |
|
|
If set to If you specify
|
|
|
Bind address. To set this property, uncomment it in the file (if necessary). The bind address can be useful if there are more NICs installed on the machine. |
|
|
Connector Server key. |
Set the properties in the ConnectorServer.properties file, as follows:
To set connectorserver.key, run the Connector Server with the /setKey option.
For more information, see Running the Connector Server on Windows Systems or Running the Connector Server on UNIX and Linux Systems.
For all other properties, edit the ConnectorServer.properties file manually.
The conf directory also contains the logging.properties file, which you can edit if required by your deployment.
To run the Connector Server on Windows systems, use the ConnectorServer.bat script, as follows:
Make sure that you have set the properties required by your deployment in the ConnectorServer.properties file, as described in Installing and Configuring the Connector Server.
Change to the CONNECTOR_SERVER_HOME\bin directory and find the ConnectorServer.bat script.
The ConnectorServer.bat script supports the following options:
| Option | Description |
|---|---|
/install [serviceName] ["-J java option"] |
Installs the Connector Server as a Windows service. Optionally, you can specify a service name and Java options. If you do not specify a service name, the default name is |
/run ["-J java option"]
|
Runs the Connector Server from the console. Optionally, you can specify Java options. For example, to run the Connector Server with SSL:
ConnectorServer.bat /run
"-J-Djavax.net.ssl.keyStore=mykeystore.jks"
"-J-Djavax.net.ssl.keyStorePassword=password"
|
/setkey [key]
|
Sets the Connector Server key. The |
/uninstall [serviceName]
|
Uninstalls the Connector Server. If you do not specify a service name, the script uninstalls the |
If you need to stop the Connector Server, stop the respective Windows service.
To run the Connector Server on UNIX and Linux systems, use the connectorserver.sh script, as follows:
Make sure that you have set the properties required by your deployment in the ConnectorServer.properties file, as described in Installing and Configuring the Connector Server.
Change to the CONNECTOR_SERVER_HOME/bin directory.
Use the chmod command to set the permissions to make the connectorserver.sh script executable.
Run the connectorserver.sh script. The script supports the following options:
| Option | Description |
|---|---|
|
|
Runs the Connector Server in the console. Optionally, you can specify one or more Java options. For example, to run the Connector Server with SSL:
./connectorserver.sh /run
-J-Djavax.net.ssl.keyStore=mykeystore.jks
-J-Djavax.net.ssl.keyStorePassword=password
|
|
|
Runs the Connector Server in the background. Optionally, you can specify one or more Java options. |
/stop |
Stops the Connector Server, waiting up to 5 seconds for the process to end. |
/stop n
|
Stops the Connector Server, waiting up to |
/stop -force |
Stops the Connector Server. Waits up to 5 seconds and then uses the |
/stop n -force
|
Stops the Connector Server. Waits up to |
/setKey key
|
Sets the Connector Server key. The |
To install the AS400 connector for Oracle Waveset into the Connector Server, follow these steps:
Make sure you have installed Oracle Waveset with the patch shown in Certified Components for the AS400 Connector.
Stop the Connector Server.
Copy the AS400 connector bundle into the Connector Server CONNECTOR_SERVER_HOME/bundles directory.
Copy the jt400.jar file to the CONNECTOR_SERVER_HOME/lib directory.
Start the Connector Server.
For information about starting and stopping the Connector Server, see Running the Connector Server on Windows Systems or Running the Connector Server on UNIX and Linux Systems.
Oracle Waveset supports three options for handling OS/400 objects that are associated with an account on an OS/400 resource. To enable this specialized support, you must use the OS400Deprovision form, which is located in the Oracle Waveset sample directory.
You must also edit the system configuration object. The instructions for editing this object are included in the comments in the OS400Deprovision form. Once enabled, these options appear on the Delete Resource Accounts page when you choose to delete a user's OS/400 resource account.
The form field OWNOBJOPT can have one of the following values:
DLT. The user's resource account and associated objects are deleted.
NODLT. The dependent objects are reassigned to a default profile (QDEFOWN) instead of being deleted.
CHGOWN. The user's dependent objects are inherited by a specified custom OS/400 profile, which is specified by the value of the GRPPRF field.
The form field GRPPRF is the user profile name that inherits objects owned by the deleted OS/400 account. This field is optional. It is relevant only when the field OWNOBJOPT has the value of CHGOWN.
The AS400 connector supports special characters in passwords for OS/400 version 5.1 or later.
A password must begin with an uppercase alphabetic character (A-Z) or the special characters @, $, #, or _, followed by uppercase alphabetic characters A-Z, numbers 0-9, and the special characters @, $, #, and _. The maximum length of a password is 10 characters.
The AS400 connector attributes naming follows the standard OS/400 conventions. For more information about OS/400 attributes, see the Create User Profile (CRTUSRPRF) and Change Directory Entry (CHGDIRE) OS/400 commands at the following site:
http://publib.boulder.ibm.com/infocenter/iseries/v5r4/index.jsp
The following table describes the account attributes for the AS400 connector. All attributes are strings, unless indicated otherwise. Also, unless indicated, the default properties for each attribute are not required, creatable, updatable, readable, and returned by default.
Table 3-4 Account Attributes for the AS400 Connector
| AS400 Connector Attribute | Native OS/400 Attribute | Description |
|---|---|---|
|
|
None |
Boolean. Indicates whether the account is enabled and logins are allowed. This attribute was |
|
|
None |
Long. Read-only. Last login date. This attribute was |
|
|
None |
Long. Read-only. Date and time the password was last updated. This attribute was |
|
|
User profile name |
Required. Not updatable. OS/400 user profile name. This attribute was The user profile name can be a maximum of 10 characters, including any letter (A-Z), a number (0-9), and the following special characters: pound ( |
|
|
User password |
Required. Guarded string. OS/400 user password. Value is encrypted. This attribute was |
|
|
None |
Integer. Number of days between the date when the password is changed and the date when the password expires. Values can be -1 through 366:
|
|
|
None |
Boolean. Indicates whether the password has expired. This attribute was |
|
|
|
Accounting code associated with the user. Values can be a character value (15 characters, padded with blanks if fewer that 15 characters), *SAME, or *BLANK. |
|
|
Directory entry attribute |
First line of the user's address. |
|
|
Directory entry attribute |
Second line of the user's address. |
|
|
|
Assistance level. Sets which interface to use. |
|
|
|
Attention-key-handling program for this user. |
|
|
Directory entry attribute |
Building name or number. |
|
|
|
Coded character set identifier. |
|
|
|
Country or region identifier. |
|
|
Directory entry attribute |
Company name. |
|
|
|
Current library for jobs initiated by this user profile. |
|
|
None |
Integer. Read-only. Number of days until the password expires. |
|
|
Directory entry attribute |
Department name or code. |
|
|
|
Delivery mode that specifies how messages sent to the message queue for this user are to be delivered. |
|
|
Directory entry attribute |
Fax telephone number. |
|
|
Directory entry attribute |
User's first name. A maximum of 20 characters is allowed. |
|
|
Directory entry attribute |
User's full name. |
|
|
|
Long. Group identification number for this user profile. You can assign the GID to a user who does not have an associated group profile. |
|
|
|
Authority given to the group profile for newly created objects. Values can be *SAME, *NONE, *ALL, *CHANGE, *USE, or *EXCLUDE. |
|
|
|
User's group profile name whose authority is used if no specific authority is given for the user or |
|
|
|
Integer. highest scheduling priority the user is allowed to have for each job submitted to the system. Values can be 0 (highest) through 9 (lowest). |
|
|
|
Pathname of the user's home directory. |
|
|
|
Initial menu displayed when the user signs on the system if the user's routing program is the command processor. |
|
|
|
For an interactive job, the program called whenever a new routing step is started that has QCMD as the request processing program. |
|
|
|
Fully qualified integrated file-system path name of the job description used for jobs that start through subsystem work station entries. |
|
|
Directory entry attribute |
Job title for this user. |
|
|
|
Keyboard buffering used when a job is initiated for this user. |
|
|
|
Language identifier for the user. |
|
|
Directory entry attribute |
User's last name. A maximum of 40 characters is allowed. |
|
|
|
Limit capabilities for this user. |
|
|
|
Limit for number of device sessions for this user. |
|
|
Directory entry attribute |
Location for this user. |
|
|
|
Maximum amount of auxiliary storage in kilobytes. The value *NOMAX on the OS/400 target system is mapped to -1 on Oracle Waveset. |
|
|
Directory entry attribute |
User's middle name. |
|
|
|
Message queue where messages are sent for this user. |
|
|
Directory entry attribute |
Office name or number. |
|
|
|
Output queue for this user profile. |
|
|
|
Owner of new objects created by this user. |
|
|
Directory entry attribute |
User's preferred name. |
|
|
|
Default print device for this user. |
|
|
None |
Integer. Read-only. Number of invalid login attempts since the last successful login. |
|
|
|
List of special authorities for this user. Can have multiple values. |
|
|
|
Special environment for this user. |
|
|
|
Sort sequence table used for string comparisons for this user. |
|
|
None |
Integer. Read-only. Amount of auxiliary storage in kilobytes occupied by this user's owned objects. Default is 12 kilobytes. |
|
|
|
List of the user's supplemental group profiles. Can have multiple values. Note. To update the supplemental group ( |
|
|
Directory entry attribute |
Telephone number. |
|
|
|
Text up to 40 characters describing the object (OS/400 account). |
|
|
|
Long. User identification number that identifies a user on the OS/400 target system. Range is 1 to 4294967294. The UID must not already be assigned to another user profile. Note. The UID is read-only (that is, non creatable and non-updatable). See also Bug 11671704: UID Attribute is Read-Only. |
|
|
|
Type of user associated with this user profile: security officer, security administrator, programmer, system operator, or user. |
|
|
|
Level of help information detail to be shown and the function of the Page Up and Page Down keys by default. |
Note:
The OWNOBJOPT (owned object option) attribute and OWNOBJOPT (group profile) attribute have been superseded by the respective OS/400 operation.
The following forms are supplied with the AS400 connector:
OS400UserForm.xml provides a more user-friendly OS/400 form.
OS400Deprovision.xml enables more refined control for a delete user operation.
The AS400 connector supports Before and After actions written in the OS/400 Command Language. The following example shows a sample After action that sets the value of the TEXT attribute to the text specified by 'new text description' for a recently created account:
<?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE Waveset PUBLIC 'waveset.dtd' 'waveset.dtd'>
<Waveset>
<ResourceAction name='AfterCreateOS400'>
<ResTypeAction restype='OS/400' timeout='7000'
execMode='resource' actionType='OS/400 CL'>
<act>
CHGUSRPRF USRPRF($__NAME__$) TEXT('new text description')
</act>
</ResTypeAction>
</ResourceAction>
</Waveset>
For more information, see Chapter 51, "Adding Actions to Resources" in the Oracle Waveset 8.1.1 Resources Reference.
Connection pooling involves the management of AS400 connector instances, so that an OS/400 connection does not have to be created each time an operation is executed. For most applications, the default connection pooling setup should be sufficient. However, the fine-tuning of connection pooling can help to increase throughput, if maximum performance is a concern.
The AS400 connector uses Identity Connector Framework (ICF) connection pooling. For more information, see Editing Connection Pooling Parameters.
This section describes how to configure Secure Sockets Layer (SSL) for the AS400 connector. In summary, you must fetch the SSL certificate from the OS/400 resource and then import the certificate in the application server you are using.
Before you begin, consider these requirements:
For the JDK requirements. see Certified Components for the AS400 Connector. If necessary, set your JAVA_HOME environment variable to point to your specific installation.
SSL must be enabled on the OS/400 server, and the Digital Certificate Manager must be started. For more information, refer to the following document:
To configure SSL for the AS400 connector, follow these steps:
Fetch the certificate from the target OS/400 system:
In a web browser, go to the Digital Certificate Manager on http://OS400domain:2001, where OS400domain is the target OS/400 system. Use the same user account and password that you use to access the target OS/400 system.
In the left panel, select Create Certificate Authority.
Or, if the Create Certificate Authority is not an option, select Install Local CA Certificate on Your PC.
Select Install Certificate, and copy the certificate to a text file. For example: cert.txt
Determine the SSL keystore location on the application server you are using.
For example, for Oracle WebLogic Server:
Open the WebLogic Server Administration Console (http://WeblogicDomain:port/console).
Look for SSL configuration settings and specifically the name of the keystore. Sometimes, you will see the full path to the keystore, but other times you will see a name such as "DemoTrust" keystore with a path such as WEBLOGIC_HOME/server/lib/DemoTrust.jks.
Use the keytool -importcert command to add the certificate from Step 1 to the keystore for the specific application server. For example, for WebLogic Server:
keytool -importcert -file path-to-certificate -alias arbitrary-alias -keystore WEBLOGIC_HOME/server/lib/DemoTrust.jks
where:
path-to-certificate is the path to the certificate file you obtained in Step 1.
arbitrary-alias is a user-defined alias for identification of the certificate in the certificate store.
To verify presence of the certificate in the certificate store, use the keytool -list -keystore command.
Follow these steps to communicate with a Connector Server using SSL:
Deploy an SSL certificate to the Connector Server's system.
Configure your Connector Server to provide SSL sockets.
Configure your application to communicate with the Connector Server using SSL.
Refer to the target system's manual for specific information about configuring connections to identity Connector Servers. You should indicate to your application that an SSL connection is required when establishing a connection for each SSL-enabled Connector Server. Additionally, if any of the SSL certificates used by your Connector Servers are issued by a non-standard certificate authority, your application must be configured to respect the additional authorities. Refer to your target system's manual for notes regarding certificate authorities.
Note:
Java applications can solve the issue of non-standard certificate authorities by expecting the following Java system properties to be passed when launching the application:
javax.net.ssl.trustStorePassword
For example: -Djavax.net.ssl.trustStorePassword=changeit
javax.net.ssl.trustStore
For example: -Djavax.net.ssl.trustStore=/usr/myApp_cacerts
Alternately, non-standard certificate authorities can be imported to the standard ${JAVA_HOME}/lib/security/cacerts directory.
Use the Oracle Waveset debug pages to set trace options on the following class:
org.identityconnectors.as400.AS400Connector
This class returns all available error messages from the OS/400 resource.
Bug 12636537: Multi-Valued SPCAUT Attribute Does Not Allow Adding Multiple Values
Bug 12635601: Provisioning User with Values for MSGQ and JOBD Fails
The UID attribute is a unique number that identifies a user on the OS/400 target system. In Oracle Waveset, the UID attribute is part of the default user form. However, if you try to update the UID attribute in Oracle Waveset, an error message is displayed.
Workaround. To update the UID attribute, use the OS/400 Command Language (CHGUSRPRF command).
The SPCAUT attribute is multi-valued, but the user form does not have an Add/Remove button like other multi-valued attributes.
Workaround. Use a space to delimit multiple values for the SPCAUT attribute. For example, in order to set the security administrator and auditor special authorities, specify: *SECADM *AUDIT.
You must explicitly include all the required special authorities, including previous special authorities you want to preserve.
This problem occurs as follows:
Create an AS400 connector resource in Oracle Waveset.
Create an Oracle Waveset user.
Create an OS/400 account for the Oracle Waveset user from Step 2 with the JOBD (job description) attribute set to the value QGPL/QDFTJOBD.
Oracle Waveset returns an error. This problem can occur for these attributes: INLMNU, INLPGM, JOBD, MSGQ, ATNPGM, OUTQ, and SRTSEQ. This problem also occurs if you assign an Oracle Waveset user to multiple OS/400 accounts on different OS/400 hosts.
Workaround. When you create the OS/400 account for the Oracle Waveset user, specify the fully-qualified path for these attributes. For example, for the job description attribute:
/QSYS.LIB/QGPL.LIB/QDFTJOBD.JOBD