| Oracle® Waveset 8.1.1 Connector Reference Release 8.1.1 E25959-06 |
|
|
PDF · Mobi · ePub |
| Oracle® Waveset 8.1.1 Connector Reference Release 8.1.1 E25959-06 |
|
|
PDF · Mobi · ePub |
This chapter includes the following information about the SAP User Management connector for Oracle Waveset:
The SAP User Management connector provides provisioning and reconciliation for SAP target systems. For the supported SAP target systems, see Certified Components for the SAP User Management Connector.
The SAP User Management connector uses the Business Application Programming Interface (BAPI) to send requests to the SAP target system. The BAPI is available in the SAP Java Connector (JCo) package.
This section provides the following additional information about the SAP User Management connector:
The following figure shows the SAP User Management connector architecture.
Figure 9-1 SAP User Management Connector Architecture
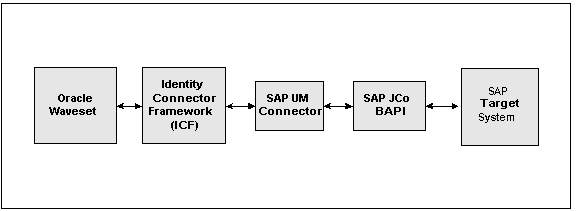
The SAP User Management connector architecture includes these components:
Oracle Waveset includes the connector integration files. These files are XML files that provide the configuration information necessary to transform data from a resource to Oracle Waveset. Integration files are sometimes called the connector "glue" code.
The Identity Connector Framework (ICF) provides basic provisioning, logging, and other functions that Oracle Waveset (and Oracle Identity Manager) connectors can use.
The SAP User Management connector uses the Business Application Programming Interface (BAPI) to send requests to the SAP target system. The BAPI is available in the SAP Java Connector (JCo) package.
If you are deploying the SAP User Management connector in the Connector Server, see also SAP User Management Connector Deployment Architecture With the Connector Server.
The SAP User Management connector supports the operations described in the following table.
Table 9-1 SAP User Management Connector Operations
| Operation | Description |
|---|---|
|
Provisioning |
Operations include:
|
|
Reconciliation |
Operations include:
|
If Logon Group is configured in the SAP target system, both failover and load balancing are supported. The SAP Message Server provides this support.
If Logon Group is configured for the SAP system, information about the Message Server is provided in the Resource.
For more information about the Message Server, see the SAP documentation for your specific SAP target system.
The SAP User Management connector resource configuration parameters are described in the following sections:
In the following tables, required parameters are noted in the description. Other attributes are optional.
The following table describes the SAP administrator credential parameters used by the SAP User Management connector.
Table 9-2 SAP Administrator Credentials Parameters
| Parameter | Type | Description |
|---|---|---|
|
SAP Destination Name |
String |
Unique resource name that defines the destination to be created. Required. |
|
Host |
String |
Host name of the resource. Required. |
|
System Number |
String |
SAP System Number. Required. |
|
SAP Client |
String |
SAP Client setting. Default is 000. Required. |
|
User |
String |
When using normal authentication, a user name that has permissions to create new accounts. Required for normal authentication. |
|
Password |
String |
When using normal authentication, password of the User account. Required for normal authentication. |
|
Language |
String |
Server language setting. Default is EN (English). |
The following table describes the SAP SNC parameters. Use these parameters to enable and configure SNC for secure communication between Oracle Waveset and the SAP target system.
See also Configuring Secure Network Communications (SNC) for the SAP User Management Connector.
Table 9-3 SAP Secure Network Communications (SNC) Parameters
| Parameter | Type | Description |
|---|---|---|
|
Enable SAP SNC |
Boolean |
Enable secure communication using SNC between Oracle Waveset and the SAP target system instead of regular authentication. |
|
SNC Library Path |
String |
When using SNC, the full path to the SNC cryptographic library file including the file extension (.so, .a, or .dll). |
|
SNC Partner Name |
String |
When using SNC, the name of the SAP system that is known to the SNC environment. This string value looks like a DN but is prepended with
|
|
SNC Protection Level |
String |
When using SNC, the level of privacy for this connection:
Both sides of the connection must specify the same level of protection. |
|
SNC Name |
String |
When using SNC, name for the client that is known to the SNC environment. This string value looks like a DN but is prepended with
|
|
SNC X500 Certificate |
String |
When using SNC, the X509 certificate. You must delete the BEGIN CERTIFICATE and END CERTIFICATE lines and remove all newline characters from the certificate. |
The following table describes the SAP destination connection tuning parameters used by the SAP User Management connector.
Table 9-4 SAP Destination Connection Tuning Parameters
| Parameter | Type | Description |
|---|---|---|
|
Configure Connection Tuning |
Boolean |
Allows the connection properties to be customized when the SAP Destination is configured. |
|
Max Active Connections |
Integer |
Maximum number of active connections that can be simultaneously created for a destination. |
|
Pool Capacity |
Integer |
Maximum number of idle connections that can be kept open by the destination. |
|
Connection Expire Time |
Integer |
Freed connections held by the destination that can be closed after this amount of time. Specified in milliseconds. |
|
Check Released Connections Period |
Integer |
Released connections are checked for expiration after waiting for this time period. Specified in milliseconds. |
|
Max Connection Wait Time |
Integer |
Maximum time to wait for a connection. Specified in milliseconds. |
|
JCO Trace Level |
Integer |
Level of SAP JCo tracing to enable. Enter 0 or any positive integer up to and including 10. |
|
JCO Trace Directory |
String |
Absolute path to the directory where the trace files will be created. |
The following table describes the CUA parameters used by the SAP User Management connector.
Table 9-5 SAP Central User Administration (CUA) Parameters
| Parameter | Type | Description |
|---|---|---|
|
Enable CUA |
Boolean |
If set to true, the connector can manage subsytems as well as roles and profiles on those subsystems. |
|
CUA Child Password Check Delay |
Integer |
Specifies the milliseconds to delay before checking the propagation of the initial password change to the child systems. This parameter is not used unless CUA is enabled. Default is 1000 milliseconds. |
|
CUA Child Initial Password Change Function Module |
String |
Name of the Remote Enabled function module that changes the initial password for a user on all CUA child systems. This parameter is not used unless CUA is enabled. If the value is not set, password changes will only applied to the CUA system. Setting productive passwords on CUA child systems will also automatically fail without this setting. |
|
CUA Child Password Change Function Module |
String |
Name of the Remote Enabled function module that changes the productive password for a user on a CUA child system. This parameter is not used unless CUA is enabled. |
|
CUA Child Password Check Function Module |
String |
Name of the Remote Enabled function module that checks the setting of the initial password on a child system. This parameter is not used unless CUA is enabled. Note: If the value is not set, no checks will be performed, which could cause failures when setting a productive password. |
The following table describes the SAP password change parameters used by the SAP User Management connector.
Table 9-6 SAP Password Change Parameters
| Parameter | Type | Description |
|---|---|---|
|
Return SAP Temporary Passwords on Failure |
Boolean |
Flag that determines whether the plain text temporary password is returned when an error occurs during user password changes. This flag is necessary because two separate password changes are required for a user password change. The first change is done as an admin with a temporary password. The second change is done with the new password to prevent the password from being expired. If the system fails after the first change but before the second change, the connector returns the temporary password in plain text so that the user can see their current password. |
|
Upper Case Passwords |
Boolean |
When selected, converts the password to uppercase format before sending to the resource. |
|
Use SAP Temporary Passwords |
Boolean |
Allow SAP to generate a password for use in setting a user's password as expired or unexpired. This option requires installation of SAP Note 832661. |
The following table describes miscellaneous optional parameters used by the SAP User Management connector.
Table 9-7 Miscellaneous Optional Parameters
| Parameter | Type | Description |
|---|---|---|
|
Filtered Accounts |
String |
Listed accounts cannot be edited, created, or listed. |
|
SAP Retry Count |
Integer |
Number of times to retry a failed operation. A failure could occur due to a network outage or some other anomaly. Default is 5. |
|
SAP Retry Wait Time |
Integer |
Number of milliseconds to wait before attempting a new operation. Default is 1000 milliseconds. |
|
Temporary Password |
String |
Temporary password to use while doing password changes. |
|
User Provides Password On Change |
Boolean |
If selected, the user is required to specify their current SAP password when changing the password. |
|
Eat Non Update Create |
Boolean |
If set to true, the connector does not throw an exception when it sends an parameter that cannot be created or updated. Instead, the connector just processes the remaining parameters. If set to false, the connector throws an exception without processing. |
This section provides the following security considerations for the SAP User Management connector:
Secure communication between Oracle Waveset and the SAP target system is provided by SAP Secure Network Communications (SNC).
For more information about SNC, see the following sections:
For general information about SNC, see the following article:
http://help.sap.com/saphelp_nw73/helpdata/en/0a/0a2e0fef6211d3a6510000e835363f/content.htm
To manage the user accounts on the SAP target system, the SAP administrator must have account permissions to create and modify user accounts, including read, write, and delete permissions.
For information about configuring the SAP administrator, see SAP Administrator Credentials Parameters.
The SAP User Management connector is certified with the components shown in the following table.
Table 9-8 Certified Components for the SAP User Management Connector
| Component | Requirement |
|---|---|
|
Oracle Waveset |
Oracle Waveset 8.1 Update 1 Bundle Patch 8 or later |
|
SAP target systems |
The following SAP target systems are supported:
|
|
SAP target systems (continued) |
In general:
|
|
Identity Connector Framework (ICF) |
ICF 1.0 or later |
|
External Code |
SAP Java Connector (SAP JCo) 3.0.2 or later, including:
|
|
JDK |
JDK 1.5 or later |
The SAP User Management connector is localized in the following languages:
Arabic
Chinese (Simplified and Traditional)
Czech
Danish
Dutch
Finnish
French
German
Greek
Hebrew
Hungarian
Italian
Japanese
Korean
Norwegian
Polish
Portuguese (Brazilian)
Romanian
Russian
Slovak
Spanish
Swedish
Thai
Turkish
You can deploy the SAP User Management connector either locally in Oracle Waveset or remotely in the Connector Server, as described in the following sections:
Downloading and Installing the SAP Java Connector (JCo) Files
Installing the SAP User Management Connector in the Connector Server
Installing the SAP User Management Connector in Oracle Waveset
Postinstallation Tasks for the SAP User Management Connector
The SAP User Management connector requires the following SAP JCo files:
For all platforms: sapjco3.jar
For Microsoft Windows platforms: sapjco3.dll
For UNIX and Linux platforms: libsapjco3.so
These files are available in the SAP JCo.zip file. To download and install these files, perform the following steps on the Oracle Waveset host computer:
Download the JCo.zip file from the SAP site as follows:
Select Application Platform, Connectivity, Connectors, SAP Java Connector, and Tools & Services to open the SAP JAVA Connector page.
On the SAP JAVA Connector page, in the right pane, click the link for the SAP JCo release that you want to download.
In the dialog box that is displayed, specify the path to the directory in which you want to save the file and click Save.
For the versions of the SAP JCo that are supported, see Certified Components for the SAP User Management Connector.
Create a new directory and then extract the JCo.zip file in this new directory.
Depending on your platform, copy the SAP library files to the following directories:
For Windows platforms:
Copy sapjco3.dll to the winnt\system32 directory. Or, copy this file into any directory and then add the path to the directory to the PATH environment variable.
Ensure that the msvcr80.dll and msvcp80.dll files are in the C:\WINDOWS\system32 directory. If necessary, first download these files from various sources on the Internet.
For UNIX and Linux platforms:
Copy libsapjco3.so to the /usr/local/jco directory.
Add the path to the directory specified in the previous step to the LD_LIBRARY_PATH environment variable.
Stop the Oracle Waveset web application.
Copy the SAP User Management connector bundle JAR file (org.identityconnectors.sap-2.0.0.jar) to the WavesetInstallDirectory/WEB-INF/bundles directory of the Oracle Waveset web application.
In the JAR file name, 2.0.0 represents the connector bundle version.
Copy the sapjco3.jar file to the WavesetInstallDirectory/WEB-INF/lib directory.
Copy the sap-idmglue.jar file from the sap-idmglue-2.0.0/WEB-INF/lib directory to the WavesetInstallDirectory/WEB-INF/lib directory.
Start the Oracle Waveset web application.
Import the following XML files from the sap-idmglue-2.0.0/sample/connectors/sap-idmglue directory:
postProcess.xml
Resource Wizard SAPConnector Connector.xml
SAP Connector CUA User Form.xml
SAP Connector User Form.xml
This section describes the following subsections:
The following figure shows a distributed deployment architecture with the SAP User Management connector deployed in the Connector Server.
Figure 9-2 SAP User Management Connector Deployment Architecture With the Connector Server

A SAP User Management connector deployment with the Connector Server includes these components:
Machine 1 has Oracle Waveset deployed.
Machine 2 has the SAP User Management connector installed in the Connector Server. The Connector Server is part of the Identity Connector Framework (ICF).
The SAP User Management connector uses the Business Application Programming Interface (BAPI) to send requests to the SAP target system. The BAPI is available in the SAP Java Connector (JCo) package.
Machine 3 has the SAP target system deployed.
Note:
The Connector Server requires a JDK to run. For the requirements, see Certified Components for the SAP User Management Connector. If necessary, set your JAVA_HOME environment variable to point to your specific installation.
To install and configure the Connector Server:
Create a new directory on the machine where you want to install the Connector Server. In this section, CONNECTOR_SERVER_HOME represents this directory.
Unzip the Connector Server package in your new directory from Step 1. The Connector Server package is available with the Identity Connector Framework (ICF).
In the ConnectorServer.properties file, set the following properties, as required by your deployment. The ConnectorServer.properties file is located in the conf directory.
| Property | Description |
|---|---|
|
|
Port on which the Connector Server listens for requests. The default is 8759. |
|
|
Directory where the connector bundles are deployed. The default is |
|
|
Directory in which to place dependent libraries. The default is |
|
|
If set to If you specify
|
|
|
Bind address. To set this property, uncomment it in the file (if necessary). The bind address can be useful if there are more NICs installed on the machine. |
|
|
Connector Server key. |
Set the properties in the ConnectorServer.properties file, as follows:
To set connectorserver.key, run the Connector Server with the setKey option.
For all other properties, edit the ConnectorServer.properties file manually.
The conf directory also contains the logging.properties file, which you can edit if required by your deployment.
To run the Connector Server on Windows systems, use the ConnectorServer.bat script as follows:
Make sure that you have set the properties required by your deployment in the ConnectorServer.properties file, as described in Installing and Configuring the Connector Server.
Change to the CONNECTOR_SERVER_HOME\bin directory and find the ConnectorServer.bat script.
The ConnectorServer.bat script supports the following options:
| Option | Description |
|---|---|
/install [serviceName] ["-J java option"] |
Installs the Connector Server as a Windows service. Optionally, you can specify a service name and Java options. If you do not specify a service name, the default name is |
/run ["-J java option"]
|
Runs the Connector Server from the console. Optionally, you can specify Java options. For example, to run the Connector Server with SSL:
ConnectorServer.bat /run
"-J-Djavax.net.ssl.keyStore=mykeystore.jks"
"-J-Djavax.net.ssl.keyStorePassword=password"
|
/setkey [key]
|
Sets the Connector Server key. The |
/uninstall [serviceName]
|
Uninstalls the Connector Server. If you do not specify a service name, the script uninstalls the |
If you need to stop the Connector Server, stop the respective Windows service.
To run the Connector Server on UNIX and Linux systems, use the connectorserver.sh script, as follows:
Make sure that you have set the properties required by your deployment in the ConnectorServer.properties file, as described in Installing and Configuring the Connector Server.
Change to the CONNECTOR_SERVER_HOME/bin directory.
Use the chmod command to set the permissions to make the connectorserver.sh script executable.
Run the connectorserver.sh script. The script supports the following options:
| Option | Description |
|---|---|
|
|
Runs the Connector Server in the console. Optionally, you can specify one or more Java options. For example, to run the Connector Server with SSL:
./connectorserver.sh /run
-J-Djavax.net.ssl.keyStore=mykeystore.jks
-J-Djavax.net.ssl.keyStorePassword=password
|
|
|
Runs the Connector Server in the background. Optionally, you can specify one or more Java options. |
/stop |
Stops the Connector Server, waiting up to 5 seconds for the process to end. |
/stop n
|
Stops the Connector Server, waiting up to |
/stop -force |
Stops the Connector Server. Waits up to 5 seconds and then uses the |
/stop n -force
|
Stops the Connector Server. Waits up to |
/setKey key
|
Sets the Connector Server key. The |
To install the SAP User Management connector in the Connector Server:
Make sure you have installed Oracle Waveset with the patch shown in Certified Components for the SAP User Management Connector.
Make sure you have performed the Downloading and Installing the SAP Java Connector (JCo) Files.
Stop the Connector Server.
Copy the SAP User Management connector bundle to the CONNECTOR_SERVER_HOME/bundles directory.
Copy the sapjco3.jar file to the CONNECTOR_SERVER_HOME/lib directory.
Start the Connector Server.
For information about starting and stopping the Connector Server, see Running the Connector Server on Windows Systems or Running the Connector Server on UNIX and Linux Systems.
Continue with Postinstallation Tasks for the SAP User Management Connector.
To install the SAP User Management connector in Oracle Waveset:
Make sure you have installed Oracle Waveset with the patch shown in Certified Components for the SAP User Management Connector.
Make sure you have performed the Downloading and Installing the SAP Java Connector (JCo) Files.
Stop the Oracle Waveset web application.
Copy the SAP User Management bundle JAR file to the WavesetInstallDirectory/WEB-INF/bundles directory.
Copy the sapjco3.jar file to the WavesetInstallDirectory/WEB-INF/lib directory.
Start the Oracle Waveset web application.
Continue with Postinstallation Tasks for the SAP User Management Connector.
After you install the SAP User Management connector, perform the following tasks:
Configuring Secure Network Communications (SNC) for the SAP User Management Connector
Enabling the Use of a Logon Group for the SAP User Management Connector
Enabling SAP JCo Connectivity for the SAP User Management Connector
To create an SAP User Management connector resource:
Log in to the Oracle Waveset Administrator interface.
Create the SAP User Management connector resource by following the Create SAP User Management Connector Resource wizard.
Select the SAP User Management Connector Version as "2.0.0".
If the SAP User Management connector is deployed in the Connector Server, select the Connector Server on which the connector bundle is deployed.
Or, if the SAP User Management connector is deployed in Oracle Waveset, specify the value for the Java Connector Server as Local.
Specify values for the SAP User Management connector, depending on your deployment. For more information, see:
Oracle Waveset uses a Java application server. To connect to the SAP system application server, this Java application server uses the SAP Java connector (JCo). If required, you can use Secure Network Communication (SNC) to secure communication between Oracle Waveset and the SAP target system.
This section describes the following topics:
The following are prerequisites for configuring the SAP User Management connector to use SNC:
SNC must be activated on the SAP application server.
You must be familiar with the SNC infrastructure. You must know which Personal Security Environment (PSE) the application server uses for SNC.
To install the security package on the Java application server used by Oracle Waveset:
Extract the contents of the SAP Cryptographic Library installation package.
The SAP Cryptographic Library installation package can be ordered from SAP official software partners listed on the SAP site.
The security package contains the following files:
SAP Cryptographic Library:
Microsoft Windows platforms: sapcrypto.dll
UNIX and Linux platforms: libsapcrypto.so
A corresponding license ticket (ticket)
The configuration tool:
Microsoft Windows platforms: sapgenpse.exe
UNIX and Linux platforms: sapgenpse
Copy the library and the sapgenpse.exe or sapgenpse file to a local directory. For example, on Windows:
C:/usr/sap
Check the file permissions. Ensure that the user under which the Java application server runs is able to run the library functions in the directory into which you copied the library and the sapgenpse.exe file.
Create the sec directory inside the directory into which you copied the library and the sapgenpse.exe file.
You can use any names for the directories that you create. However, creating the C:\usr\sap\sec or /usr/sap/sec directory is the SAP recommendation.
Copy the ticket file into the sec directory. This is also the directory in which the Personal Security Environment (PSE) and credentials of the Java application server are generated.
Set the SECUDIR environment variable for the Java application server user to the sec directory.
From this point onward, the term SECUDIR directory is used to refer to the directory whose path is defined in SECUDIR environment variable.
Set the SNC_LIB and PATH environment variables for the user of the Java application server to the cryptographic library directory, which is the parent directory of the sec directory.
To configure SNC for the SAP User Management connector:
Either create a PSE or copy the SNC PSE of the SAP application server to the SECUDIR directory. To create the SNC PSE for the Java application server, use the sapgenpse.exe command-line tool as follows:
To determine the location of the SECUDIR directory, run the sapgenpse command without specifying any command options. The program displays information such as the library version and the location of the SECUDIR directory.
Enter a command similar to the following to create the PSE:
sapgenpse get_pse -p PSE_Name -x PIN Distinguished_Name
The following is a sample distinguished name:
CN=SAPJ2EE, O=MyCompany, C=US
The sapgenpse command creates a PSE in the SECUDIR directory.
Create credentials for the Java application server.
The Java application server must have active credentials at run time to be able to access its PSE. To check whether or not this condition is met, enter the following command in the parent directory of the SECUDIR directory:
sapgenpse seclogin
Then, enter the following command to open the PSE of the server and create the credentials.sapgenpse file:
seclogin -p PSE_Name -x PIN -O [NT_Domain\]user_ID
The user_ID that you specify must have administrator rights. PSE_NAME is the name of the PSE file.
The credentials file, cred_v2, for the user specified with the -O option is created in the SECUDIR directory.
Exchange the public key certificates of the two servers as follows:
Export the Oracle Waveset certificate by entering the following command:
sapgenpse export_own_cert -o filename.crt -p PSE_Name -x PIN
Import the Oracle Waveset certificate into the SAP application server. You might require the SAP administrator's assistance to perform this step.
Export the certificate of the SAP application server. You may require the SAP administrator's assistance to perform this step.
Import the SAP application server certificate into Oracle Waveset by entering the following command:
sapgenpse maintain_pk -a serverCertificatefile.crt -p PSE_Name -x PIN
Configure the following parameters:
Enable SAP SNC
SNC Protection Level
SNC Name
SNC Partner Name
SNC X509 Certificate
SNC Library Path
For a description of these parameters, see SAP Secure Network Communications (SNC) Parameters.
In SAP, a logon group is used for failover and as a load-sharing mechanism. When a user logs in to a logon group, the system internally routes the connection request to the logon group member with the least load.
To enable the use of a logon group, set the following SAP User Management connector resource configuration parameters:
App server host
Logon group name
Message server
R3 name
Perform the following steps either on the Oracle Waveset host computer or the Connector Server, depending on where you deployed the SAP User Management connector.
To enable SAP JCo connectivity:
Open the following file in a text editor:
For Microsoft Windows platforms:
C:\WINDOWS\system32\drivers\etc\services
For UNIX or Linux platforms:
/etc/services
Add an entry to the file from the previous step in the following format:
sapmsSYSTEM_ID 36SYSTEM_NUMBER/tcp
For example, the new entry is shown in bold text:
...
ipx 213/udp #IPX over IP
ldap 389/tcp #Lightweight Directory Access Protocol
sapmsE60 3600/tcp
Save and close the file.
Create the sapmsg.ini file and add the following lines in the file:
[Message Server] o01=oss001.wdf.sap-ag.de SYSTEM_ID=HOST_NAME
For example:
[Message Server] o01=oss001.wdf.sap-ag.de E60=mysap08.corp.example.com
Save and close the file.
Copy the sapmsg.ini file to the C:\ directory for Windows systems or the root directory for UNIX and Linux systems.
This section provides the following information:
The following table lists the SAP User Management connector account attributes. These attributes are in the User object class. The only required attributes are accoundId and lastname.
Table 9-9 SAP User Management Connector Account Attributes
| Account Attribute | Description |
|---|---|
|
accountId |
User's account ID. Required. |
|
firstname |
User's first name. |
|
fullname |
User's full name. |
|
|
User's email address. |
|
lastname |
User's last name. Required. |
|
groups |
Provisions to the SAP GROUPS table. |
|
accountLockedNoPwd |
Boolean attribute that indicates whether the account is locked because the user has no password. |
|
accountLockedWrngPwd |
Boolean attribute that indicates whether the account is locked because of failed login attempts. |
|
personNumber |
Internal key for identifying a person. |
|
addressNumber |
Internal key for identifying an address for central address management. |
|
birthName |
Maiden name or name given at birth. |
|
middleName |
User's middle name. |
|
secondLastName |
User's second last name. |
|
academicTitle |
User's academic title, such as Dr. or Prof. |
|
academicTitle2 |
Second academic title for the user. |
|
namePrefix |
User's prefix to a last name, such as von, van der, or de la. |
|
namePrefix2 |
Second prefix to the user's last name. |
|
titleSupplement |
Name supplement, for the user. For example, a noble title, such as Lord or Lady. |
|
nickname |
User's nickname. |
|
initials |
User's middle initial or initials. |
|
nameFormat |
Sequence in which name components are assembled to present the name of a person in a complete form. The sequence can vary for each country. |
|
nameFormatCountry |
Country used to determine the name format. |
|
languageKey |
Language used to enter and display text. |
|
iso639Language |
ISO 639 language code. |
|
sortKey1 |
Search term. |
|
sortKey2 |
Secondary search term. |
|
department |
Department in a company as part of the company address |
|
function |
User's job functionality. |
|
buildingNumber |
Building number where the user's office is located. |
|
buildingFloor |
Floor where the user's office is located. |
|
correspondenceCode |
Correspondence code. |
|
inhouseMailCode |
Internal mail code. |
|
communicationType |
States how the user wants to exchange documents and messages with a business partner. |
|
title |
Title such as Mr. or Mrs. |
|
titleP |
Title such as Mr. or Mrs. |
|
addressName |
Name of an address. |
|
addressName2 |
Second line in the name of an address. |
|
addressName3 |
Third line in the name of an address. |
|
addressName4 |
Fourth line in the name of an address. |
|
careOfName |
Part of the address if the recipient is different from the occupant (c/o = care of) . |
|
city |
User's city |
|
district |
City or district supplement. |
|
cityNumber |
City code. |
|
districtNumber |
District code. |
|
cityPostalCode |
User's postal code. |
|
poBoxPostalCode |
Postal code required for unique assignment of the Post Office box. |
|
companyPostalCode |
Postal code that is assigned directly to a company. |
|
poBox |
User's post office box. |
|
poBoxCity |
Post office box city. |
|
poBoxCityCode |
Post Office box city, if it is different from the address city. |
|
postalDeliveryDistricy |
Postal delivery district. |
|
transportZone |
Regional zone of a goods recipient or supplier. |
|
street |
User's street. |
|
streetNumber |
User's street code. |
|
streetAbbreviation |
User's street abbreviation. |
|
houseNumber |
Number portion of a street address. |
|
houseNumber2 |
Secondary addess number |
|
street2 |
Additional address field printed above the street line. |
|
street3 |
Additional address field printed above the street line. |
|
street4 |
Additional address field printed above the street line. |
|
street5 |
Additional address field printed above the street line. |
|
oldBuilding |
Number or ID for the building in a contact person address. |
|
floor |
Floor number of an address. |
|
roomNumber |
Room number in an address. |
|
countryCode |
Country in an address. |
|
countryCodeISO |
Two-letter ISO code for the country in an address. |
|
languageKey |
Language used to enter and display text. |
|
languageKeyISO |
ISO 639 language code. |
|
region |
State or province. |
|
sort2 |
Secondary search term. |
|
timeZone |
Time difference of the time zone in hours/minutes relative to the UTC. |
|
taxJurisdictionCode |
Tax authority to which taxes must be paid. It is always the city to which the goods were delivered. |
|
telephoneNumber |
Telephone number, including the area code, but no country code. |
|
telephoneExtension |
Telephone number extension. |
|
faxNumber |
Fax number, including the area code, but no country code. |
|
faxExtension |
Fax number extension. |
|
cuaSystems |
Central User Administration system names. |
|
profiles |
Profiles assigned to the user. |
|
activityGroups |
Roles assigned to the user. |
|
lastLoginTime |
Read-only attribute that lists the most recent login time. |
Use the Oracle Waveset debug pages to set trace options on the following class:
org.identityconnectors.sap
This class returns the available error messages from the SAP target resource.
The SAP User Management connector has the following known issue.
SAP Resource Adapter supports Role, Profile, Group, and Parameter multi-valued attributes. However, it does not support multi-valued attributes prefixed with underscore ("_").
In Oracle Waveset 8.1.1.7, some functions and constants have been deprecated in the SAPResourceAdapter class. The PARAMETER->PARAMOBJ multivalued attribute is of the type complex and is not a simple string. Therefore, multi-valued attributes prefixed with underscore ("_") are not supported in SAP Resource Adapters.
The SAP JCo must register the data provider with the JCo Environment class with a destination name. Any number of destination names can be added to the provider. The Identity Connector Framework (ICF) uses a different class loader for each bundle, so if two SAP connector bundles (such as SAP User Management and SAP HR) are installed, then the connector bundle that creates a connection first will work.
However, if a second SAP connector bundle tries to create a connection, it tries to register the data provider, which is already registered by the first SAP connector bundle. It then throws the "DestinationDataProvider already registered" error.
Consider the following scenarios:
Scenario 1 - Two connectors: SAP User Management connector and SAP HR connector
A different class loader is used for the SAP User Management connector and the SAP HR connector. For example:
Create Resource 1 for the SAP User Management connector. The resource will create successfully.
Create Resource 2 for the SAP User Management connector. Because the provider is static, it is already created for Resource 1. Therefore, this step will not register the provider again. It will add the destination to the existing provider, and the resource creation will be successful.
Create Resource 1 for the SAP HR connector. Because this connector uses a different class loader, this step will try to register a new provider because the provider instance will not be available in the new class loader. It will then throw the exception "Provider is already registered" because only one provider can be registered in the JCo Environment.
The JCODestinationManager will try to get the destination of the SAP HR connector from the Environment. In the Environment, destinations of the SAP User Management connector will be available. Therefore, it will throw the exception "Destination does not exist", and the Resource creation will fail.
In this scenario, you can create any number of resources for the SAP User Management connector, but any attempts at resource creation for the SAP HR connector will fail.
However, if you create a resource for the SAP HR connector first after starting the application server, then any number of resources for the SAP HR connector will work. But resource creation for the SAP User Management connector will fail.
Scenario 2 - One connector and one Resource Adapter: SAP connector and SAPJco3HRActiveSyncAdapter
When the SAP connector is used, it will have a different class loader. Therefore, the behavior will be similar to Scenario 1.
Scenario 3 - Two Resource Adapters: SAPBasisResourceAdapter and SAPJco3HRActiveSyncAdapter
The same class loader is used for both Resource Adapters. It will create a new DestinationDataProvider when the first resource is created (either SAP User Management or SAP HR). It will use the same provider for all subsequent resource creations whether it is the SAP User Management Resource Adapter or SAP HR Resource Adapter. Therefore, all resource creations will be successful.
The issue occurs only if a connector is used because each connector uses a different class loader. Resource Adapters do not have this issue because they use the same class loader.
To use the SAP User Management connector and a Resource Adapter, deploy the SAP User Management connector in the Connector Server and the Resource Adapter in Oracle Waveset.