What Is Auditing?
Auditing is the collecting of data about the use of system resources. The audit data provides a record of security-related system events. This data can then be used to assign responsibility for actions that take place on a host. Successful auditing starts with two security features: identification and authentication. At each login, after a user supplies a user name and password, a unique audit session ID is generated and associated with the user's process. The audit session ID is inherited by every process that is started during the login session. Even if a user changes identity within a single session, all user actions are tracked with the same audit session ID. For more details about changing identity, see the su(1M) man page.
The audit service makes the following possible:
-
Monitoring security-relevant events that take place on the host
-
Recording the events in a network-wide audit trail
-
Detecting misuse or unauthorized activity
-
Reviewing patterns of access and the access histories of individuals and objects
-
Discovering attempts to bypass the protection mechanisms
-
Discovering extended use of privilege that occurs when a user changes identity
During system configuration, you preselect which classes of audit records to monitor. You can also fine-tune the degree of auditing that is done for individual users. The following figure shows details of the flow of Solaris auditing.
Figure 28–1 The Flow of Auditing
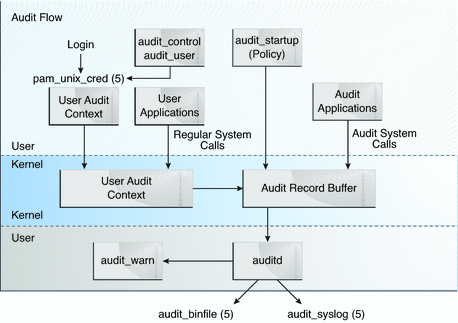
After audit data is collected in the kernel, plugins distribute the data to the appropriate locations. Then, postselection tools enable you to reduce and examine interesting parts of the audit trail. For example, you can choose to review audit records for individual users or specific groups. You can examine all records for a certain type of event on a specific day. Or, you can select records that were generated at a certain time of day.
Systems that install non-global zones can audit all zones identically from the global zone. These systems can also be configured to collect different records in the non-global zones. For more information, see Auditing and Solaris Zones.
- © 2010, Oracle Corporation and/or its affiliates
