How the DES Credential in NIS+ Is Generated
To generate its DES credential, the principal depends on the keylogin command, which must have been executed before the principal tries to generate its credential. The keylogin command (often referred to simply as a keylogin) is executed automatically when an NIS+ principal logs in. See Figure 12–2.
Note –
Note that if the principal's login password is different from the principal's Secure RPC password, a successful keylogin cannot be performed. See Secure RPC Passwords and the Login Password Problem in NIS+ for a discussion of this situation.
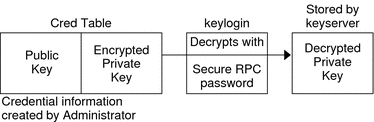
The purpose of the keylogin is to give the principal access to the principal's private key. keylogin fetches the principal's private key from the cred table, decrypts it with the principal's Secure RPC password (remember that the private key was originally encrypted with the principal's Secure RPC password), and stores it locally with the keyserver for future NIS+ requests.
Figure 12–1 keylogin Generates an NIS+ Principal's Private Key
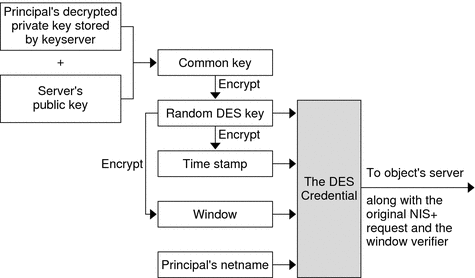
To generate its DES credential, the principal still needs the public key of the server to which it will send the request. This information is stored in the principal's directory object. Once the principal has this information, it can form the verification field of the credential.
First, the principal generates a random DES key for encrypting various credential information. The principal uses its own private key (stored in the keyserver) and the server's public key to generate a common key that is used to generate and encrypt the random DES key. It then generates a time stamp that is encrypted with the DES key and combines it with other credential-related information into the verification field.
Figure 12–2 Creating the DES Credential in NIS+
- © 2010, Oracle Corporation and/or its affiliates
