Part III NIS+ Administration
This part describes the administration and troubleshooting of the NIS+ naming service in the Solaris OS.
Chapter 10 NIS+ Tables and Information
This chapter describes the structure of NIS+ tables and provides a brief overview of how they can be set up.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
NIS+ Table Structure
NIS+ stores a wide variety of network information in tables. NIS+ tables provide several features not found in simple text files or maps. They have a column-entry structure, they accept search paths, they can be linked together, and they can be set up in several different ways. NIS+ provides 16 preconfigured system tables, and you can also create your own tables. Table 10–1 lists the preconfigured NIS+ tables.
Note –
As a naming service, NIS+ tables are designed to store references to objects, not the objects themselves. For this reason, NIS+ does not support tables with large entries. If a table contains excessively large entries, rpc.nisd may fail.
Table 10–1 List of NIS+ Tables
|
Table Name |
Information in the Table |
|---|---|
|
hosts |
Network address and host name of every machine in the domain |
|
bootparams |
Location of the root, swap, and dump partition of every diskless client in the domain |
|
passwd |
Password information about every user in the domain |
|
cred |
Credentials for principals who belong to the domain |
|
group |
The group name, group password, group ID, and members of every UNIX group in the domain |
|
netgroup |
The netgroups to which machines and users in the domain may belong |
|
mail_aliases |
Information about the mail aliases of users in the domain |
|
timezone |
The time zone of every machine in the domain |
|
networks |
The networks in the domain and their canonical names |
|
netmasks |
The networks in the domain and their associated netmasks |
|
ethers |
The Ethernet address of every machine in the domain |
|
services |
The names of IP services used in the domain and their port numbers |
|
protocols |
The list of IP protocols used in the domain |
|
RPC |
The RPC program numbers for RPC services available in the domain |
|
auto_home |
The location of all user's home directories in the domain |
|
auto_master |
Automounter map information |
Because it contains only information related to NIS+ security, the Cred table, is described in Chapter 12, Administering NIS+ Credentials.
These tables store a wide variety of information, ranging from user names to Internet services. Most of this information is generated during a setup or configuration procedure. For instance, an entry in the passwd table is created when a user account is set up. An entry in the hosts table is created when a machine is added to the network. And an entry in the networks table is created when a new network is set up.
Since this information is generated from such a wide field of operations, much of it is beyond the scope of this manual. However, as a convenience, Chapter 23, Information in NIS+ Tables summarizes the information contained in each column of the tables, providing details only when necessary to keep things from getting confusing, such as when distinguishing groups from NIS+ groups and netgroups. For thorough explanations of the information, consult Solaris system and network administration manuals.
Note –
You can create more automounter maps for a domain, but be sure to store them as NIS+ tables and list them in the auto_master table. When creating additional automount maps to supplement auto_master (which is created for you), the column names must include key and value. For more information about the automounter, consult books about the automounter or books that describe the NFS file system.
NIS+ Columns and Entries
Although NIS+ tables store different types of information, they all have the same underlying structure; they are each made up of rows and columns (the rows are called “entries” or “entry objects”):
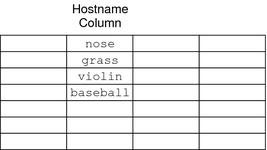
A client can access information by a key, or by any column that is searchable. For example, to find the network address of a machine named baseball, a client could look through the hostname column until it found baseball.

It then would move along the baseball entry to find its network address:

Because a client can access table information at any level, NIS+ provides security mechanisms for all three levels. For instance, an administrator could assign read rights to everyone for a table at the object level, modify rights to the owner at the column level, and modify rights to the group at the entry level. Details about table security are provided in Chapter 15, Administering NIS+ Access Rights.
NIS+ Search Paths
A table contains information only about its local domain. For instance, tables in the doc.com. domain contain information only about the users, clients, and services of the doc.com. domain. The tables in the sales.doc.com. domain store information only about the users, clients, and services of the sales.doc.com. domain. And so on.
If a client in one domain tries to find information that is stored in another domain, it has to provide a fully qualified name. As described in NIS+ NIS_PATH Environment Variable if the NIS_PATH environment variable is set up properly, the NIS+ service will do this automatically.
Every NIS+ table can also specify a search path that a server will follow when looking for information. The search path is an ordered list of NIS+ tables, separated by colons:
table:table:table... |
The table names in the search path don't have to be fully qualified; they can be expanded just like names entered at the command line. When a server cannot find information in its local table, it returns the table's search path to the client. The client uses that path to look for the information in every table named in the search path, in order, until it finds the information or runs out of names.
Here is an example that demonstrates the benefit of search paths. Assume the following domain hierarchy:
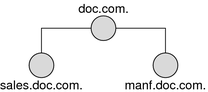
The hosts tables of the lower two domains contain the following information.
Table 10–2 Example NIS+ Hosts Table|
sales.doc.com. |
|
manf.doc.com. |
|
|---|---|---|---|
|
10.0.0.1 |
localhost |
172.18.0.1 |
localhost |
|
10.22.3.22 |
luna |
172.29.6.1 |
sirius |
|
10.22.3.24 |
phoebus |
172.29.6.112 |
rigel |
|
10.22.3.25 |
europa |
172.29.6.90 |
antares |
|
10.22.3.27 |
ganymede |
172.29.6.101 |
polaris |
|
10.22.3.28 |
mailhost |
172.29.6.79 |
mailhost |
Assume now that a user logged onto the luna machine in the sales.doc.com. domain wants to log in remotely to another client. Without providing a fully qualified name, that user can only remotely log in to five machines: localhost, phoebus, europa, ganymede, and the mailhost.
Now assume that the search path of the hosts table in the sales.doc.com. domain listed the hosts table from the manf.doc.com. domain:
hosts.org_dir.manf.doc.com. |
Now a user in the sales.doc.com. domain can enter something like rlogin sirius, and the NIS+ server will find it. It will first look for sirius in the local domain, but when it does not find a match, it will look in the manf.doc.com. domain. How does the client know how to find the manf.doc.com. domain? As described in Chapter 2, NIS+: An Introduction, the information is stored in its directory cache. If it is not stored in its directory cache, the client will obtain the information by following the process described in Chapter 2, NIS+: An Introduction.
There is a slight drawback, though, to specifying a search path. If the user were to enter an incorrect name, such as rlogin luba (rather than “luna”), the server would need to look through three tables – instead of just one – before returning an error message. If you set up search paths throughout the namespace, an operation may end up searching through the tables in 10 domains instead of just 2 or 3. Another drawback is a performance loss from having many clients contact more than one set of servers when they need to access NIS+ tables.
You should also be aware that since “mailhost” is often used as an alias, when trying to find information about a specific mailhost, you should use its fully qualified name (for example, mailhost.sales.doc.com.), or NIS+ will return all the mailhosts it finds in all the domains it searches through.
You can specify a table's search path by using the -p option to the nistbladm command, as described in Using the nistbladm Command With NIS+ Tables.
Ways to Set Up NIS+ Tables
-
Creating the org_dir directory
-
Creating the system tables
-
Creating non-system tables (optional)
-
Populating the tables with information
Setting up NIS+ tables involves three or four tasks:
As described in NIS+ Files and Directories, NIS+ system tables are stored under an org_dir directory. So, before you can create any tables, you must create the org_dir directory that will hold them. You can do this in three ways.
-
Use the nisserver script. The nisserver script creates the appropriate directories and a full set of system tables. Running the nisserver script is the recommended method.
-
Use the nismkdir command. The nismkdir command simply creates the directory.
-
Use the /usr/lib/nis/nissetup utility. The nissetup utility creates the org_dir and groups_dir directories and a full set of system tables.
The nisserver script and the nissetup and nismkdir utilities are described in nismkdir Command. Additional information on the nismkdir command can be found in nismkdir Command.
A benefit of the nissetup utility is its capability to assign the proper access rights to the tables of a domain whose servers are running in NIS-compatibility mode. When entered with the -Y flag, it assigns read permissions to the nobody class of the objects it creates, allowing NIS clients, who are unauthenticated, to get information from the domain's NIS+ tables.
The 16 NIS+ system tables and the type of information they store are described in Table 10–1. To create them, you could use one of the three ways mentioned above. The nistbladm utility also creates and modifies NIS+ tables. You could conceivably create all the tables in a namespace with the nistbladm command, but you would have to type much more and you would have to know the correct column names and access rights. A much easier way is to use the nisserver script.
To create a non-system table – that is, a table that has not been preconfigured by NIS+ – use the nistbladm command. (Note that if you are creating additional automount maps, the first column must be named key and the second column named value.)
You can populate NIS+ tables in three ways: from NIS maps, from ASCII files (such as /etc files), and manually.
If you are upgrading from the NIS service, you already have most of your network information stored in NIS maps. You don't have to re-enter this information manually into NIS+ tables. You can transfer it automatically with the nispopulate script or the nisaddent utility.
If you are not using another network information service, but maintain network data in a set of /etc files, you don't have to re-enter this information, either. You can transfer it automatically, also using the nispopulate script or the nisaddent utility.
If you are setting up a network for the first time, you may not have much network information stored anywhere. In that case, you'll need to first get the information and then enter it manually into the NIS+ tables. You can do this with the nistbladm command. You can also do it by entering all the information for a particular table into an input file& – is essentially the same as an /etc file – and then transferring the contents of the file with the nispopulate script or the nisaddent utility.
How NIS+ Tables Are Updated
When a domain is set up, its servers receive their first versions of the domain's NIS+ tables. These versions are stored on disk, but when a server begins operating, it loads them into memory. When a server receives an update to a table, it immediately updates its memory-based version of the table. When it receives a request for information, it uses the memory-based copy for its reply.
Of course, the server also needs to store its updates on disk. Since updating disk-based tables takes time, all NIS+ servers keep log files for their tables. The log files are designed to temporarily store changes made to the table, until they can be updated on disk. They use the table name as the prefix and append .log. For example:
hosts.org_dir.log bootparams.org_dir.log password.org_dir.log |
You should update disk-based copies of a table on a daily basis so that the log files don't grow too large and take up too much disk space. This process is called checkpointing. To do this, use the nisping -C command.
Chapter 11 NIS+ Security Overview
This chapter describes the NIS+ security system and how it affects the entire NIS+ namespace.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
Solaris Security and NIS+
In essence, Solaris security is provided by gates that users must pass through in order to enter the Solaris system, and permission matrixes that determine what they are able to do once inside. (See Figure 11–1 for a schematic representation of this system.)
Figure 11–1 Solaris Security Gates and Filters
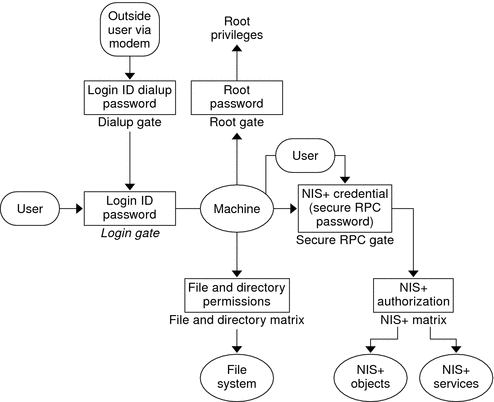
As you can see in the above figure, the overall system is composed of four gates and two permission matrixes:
-
Dialup gate. To access a given Solaris system from the outside through a modem and phone line, you must provide a valid login ID and dialup password.
-
Login gate. To enter a given Solaris system you must provide a valid login ID and user password.
-
File and Directory Matrix. Once you have gained access to a Solaris system, your ability to read, execute, modify, create, and destroy files and directories is governed by the applicable permissions matrix.
-
Root gate. To gain access to root privileges, you must provide a valid super user (root) password.
-
Secure RPC gate. In an NIS+ environment running at security level 2 (the default), when you try to use NIS+ services and gain access to NIS+ objects (servers, directories, tables, table entries, and so forth) your identity is confirmed by NIS+ using the Secure RPC process.
Consult your Solaris documentation for detailed descriptions of the Dialup, Login, and Root gates, and the File and Directory permissions matrix.
To enter the Secure RPC gate requires presentation of a Secure RPC password. (In some contexts Secure RPC passwords have been referred to as network passwords.) Your Secure RPC password and your login password normally are identical and when that is the case you are passed through the gate automatically without having to re-enter your password. (See Secure RPC Passwords and the Login Password Problem in NIS+ for information regarding cases where the two passwords are not the same.)
A set of credentials are used to automatically pass your requests through the Secure RPC gate. The process of generating, presenting, and validating your credentials is called authentication because it confirms who you are and that you have a valid Secure RPC password. This authentication process is automatically performed every time you request an NIS+ service.
In an NIS+ environment running in NIS-compatibility mode (also known as YP-compatibility mode), the protection provided by the Secure RPC gate is significantly weakened because everyone has read rights for all NIS+ objects and modify rights for those entries that apply to them regardless of whether or not they have a valid credential (that is, regardless of whether or not the authentication process has confirmed their identity and validated their Secure RPC password). Since that allows anyone to have read rights for all NIS+ objects and modify rights for those entries that apply to them, an NIS+ network running in compatibility mode is less secure than one running in normal mode.
For details on how to create and administer NIS+ authentication and credentials, see Chapter 12, Administering NIS+ Credentials.
-
NIS+ objects matrix. Once you have been properly authenticated to NIS+ your ability to read, modify, create, and destroy NIS+ objects is governed by the applicable permissions matrix. This process is called NIS+ authorization.
For details NIS+ permissions and authorization, see Chapter 15, Administering NIS+ Access Rights.
NIS+ Security Overview
NIS+ security is an integral part of the NIS+ namespace. You cannot set up security and the namespace independently. For this reason, instructions for setting up security are woven through the steps used to set up the other components of the namespace. Once an NIS+ security environment has been set up, you can add and remove users, change permissions, reassign group members, and all other routine administrative tasks needed to manage an evolving network.
The security features of NIS+ protect the information in the namespace, as well as the structure of the namespace itself, from unauthorized access. Without these security features, any NIS+ client could obtain and change information stored in the namespace or even damage it.
NIS+ security does two things:
-
Authentication. Authentication is used to identify NIS+ principals. Every time a principal (user or machine) tries to access an NIS+ object, the user's identity and Secure RPC password is confirmed and validated.
-
Authorization. Authorization is used to specify access rights. Every time NIS+ principals try to access NIS+ objects, they are placed in one of four authorization classes (owner, group, world, nobody). The NIS+ security system allows NIS+ administrators to specify different read, modify, create, or destroy rights to NIS+ objects for each class. Thus, for example, a given class could be permitted to modify a particular column in the passwd table but not read that column, or a different class could be allowed to read some entries of a table but not others.
-
Authentication. NIS+ uses credentials to confirm that you are who you claim to be.
-
Authorization. Once your identity is established by the authentication process, NIS+ determines your class. What you can do with a given NIS+ object or service depends on which class you belong to. This is similar in concept to the standard UNIX file and directory permissions system. (See NIS+ Authorization Classes for more information on classes.)
In essence, then, NIS+ security is a two-step process:
This process, for example, prevents someone with root privileges on machine A from using the su command to assume the identity of a second user and then accessing NIS+ objects with the second user's NIS+ access privileges.
Note, however, that NIS+ cannot prevent someone who knows another user's login password from assuming that other user's identity and NIS+ access privileges. Nor can NIS+ prevent a user with root privileges from assuming the identity of another user who is logged in from the same machine.
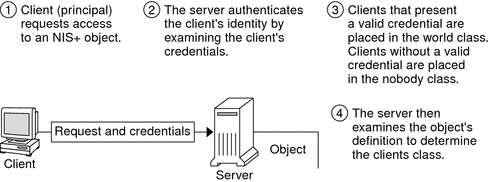
Figure 11–2 details this process.
Figure 11–2 Summary of the NIS+ Security Process
NIS+ Principals
NIS+ principals are the entities (clients) that submit requests for NIS+ services. An NIS+ principal may be someone who is logged in to a client machine as a regular user, someone who is logged in as superuser, or any process that runs with superuser permission on an NIS+ client machine. Thus, an NIS+ principal can be a client user or a client machine.
An NIS+ principal can also be the entity that supplies an NIS+ service from an NIS+ server. Since all NIS+ servers are also NIS+ clients, much of this discussion also applies to servers.
NIS+ Security Levels
NIS+ servers operate at one of two security levels. These levels determine the type of credential principals that must submit for their requests to be authenticated. NIS+ is designed to run at the most secure level, which is security level 2. Level 0 is provided only for testing, setup, and debugging purposes. These security levels are summarized in Table 11–1.
Table 11–1 List of NIS+ Security Levels|
Security Level |
Description |
|---|---|
|
0 |
Security level 0 is designed for testing and setting up the initial NIS+ namespace. An NIS+ server running at security level 0 grants any NIS+ principal full access rights to all NIS+ objects in the domain. Level 0 is for setup purposes only and should only be used by administrators for that purpose. Level 0 should not be used on networks in normal operation by regular users. |
|
1 |
Security level 1 uses AUTH_SYS security. This level is not supported by NIS+ and should not be used. |
|
2 |
Security level 2 is the default. It is the highest level of security currently provided by NIS+. It authenticates only requests that use DES credentials. Requests with no credentials are assigned to the nobody class and have whatever access rights that have been granted to that class. Requests that use invalid DES credentials are retried. After repeated failure to obtain a valid DES credential, requests with invalid credentials fail with an authentication error. (A credential might be invalid for a variety of reasons such as the principal making the request is not keylogged in on that machine, the clocks are out of synch, there is a key mismatch, and so forth.) |
NIS+ Security Levels and Password Commands
In Solaris releases 2.0 through 2.4, you used the nispasswd command to change your password. However, nispasswd could not function without credentials. (In other words, it could not function under security level 0 unless there were credentials existing from some previous higher level.) Starting with the Solaris 2.5 release, the passwd command must be used to change your own password regardless of security level or credential status.
NIS+ Authentication and Credentials
The purpose of NIS+ credentials is to authenticate (confirm) the identity of each principal requesting an NIS+ service or access to an NIS+ object. In essence, the NIS+ credential/authorization process is an implementation of the Secure RPC system.
The credential/authentication system prevents someone from assuming some other user's identity. That is, it prevents someone with root privileges on one machine from using the su command to assume the identity of a second user who is not logged in and then accessing NIS+ objects with the second user's NIS+ access privileges.
Once a server authenticates a principal, the principal is placed in one of four authorization classes. The server then checks the NIS+ object that the principal wants to access to see what activities that class of principal is authorized to perform. (See NIS+ Authorization and Access for further information on authorization.)
NIS+ User and Machine Credentials
There are two basic types of principal, users and machines, and thus two different types of credentials:
-
User credentials. When someone is logged in to an NIS+ client as a regular user, requests for NIS+ services include that person's user credentials.
-
Machine credentials. When a user is logged in to an NIS+ client as superuser, request for services use the client machine's credentials.
DES Credentials and LOCAL Credentials in NIS+
NIS+ principals can have two types of credential: DES and LOCAL.
DES Credentials in NIS+
Note –
DES credentials are only one method of achieving authentication. In the future, other methods may be available. Thus, do not equate DES credentials with NIS+ credentials.
In this document, the term DES credentials is used generically to denote a Diffie-Hellman key based authentication, regardless of key length. The system allows you to specify the key length from a pre-determined set. Use nisauthconf to set or display the Diffie-Hellman key length.
DES (Data Encryption Standard) credentials are the type of credential that provide secure authentication. When this guide refers to NIS+ checking a credential to authenticate an NIS+ principal, it is the DES credential that NIS+ is validating.
Each time a principal requests an NIS+ service or access to an NIS+ object, the software uses the credential information stored for that principal to generate a credential for that principal. DES credentials are generated from information created for each principal by an NIS+ administrator, as explained in Chapter 12, Administering NIS+ Credentials.
-
When the validity of a principal's DES credential is confirmed by NIS+, that principal is authenticated.
-
A principal must be authenticated in order to be placed in the owner, group, or world authorization classes. In other words, you must have a valid DES credential in order to be placed in one of those classes. (Principals who do not have a valid DES credential are automatically placed in the nobody class.)
-
DES credential information is always stored in the cred table of the principal's home domain, regardless of whether that principal is a client user or a client machine.
LOCAL Credentials in NIS+
LOCAL credentials are simply a map between a user's User ID number and NIS+ principal name which includes their home domain name. When users log in, the system looks up their LOCAL credential, which identifies their home domain where their DES credential is stored. The system uses that information to get the user's DES credential information.
When users log in to a remote domain, those requests use their LOCAL credential which points back to their home domain; NIS+ then queries the user's home domain for that user's DES credential information. This allows a user to be authenticated in a remote domain even though the user's DES credential information is not stored in that domain.
Figure 11–3 NIS+ Credentials and Domains
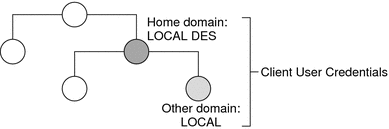
LOCAL credential information can be stored in any domain. In fact, in order to log into a remote domain and be authenticated, a client user must have a LOCAL credential in the cred table of the remote domain. If a user does not have a LOCAL credential in a remote domain the user is trying to access, NIS+ will be unable to locate the user's home domain to obtain the user's DES credential. In such a case the user would not be authenticated and would be placed in the nobody class.
NIS+ User Types and Credential Types
A user can have both types of credentials, but a machine can only have DES credentials.
Root cannot have NIS+ access, as root, to other machines because the root UID of every machine is always zero. If root (UID=0) of machine A tried to access machine B as root, that would conflict with machine B's already existing root (UID=0). Thus, a LOCAL credential doesn't make sense for a client machine; so it is allowed only for a client user.
Table 11–2 Types of NIS+ Credentials|
Type of Credential |
Client User |
Client machine |
|---|---|---|
|
DES |
Yes |
Yes |
|
LOCAL |
Yes |
No |
NIS+ Authorization and Access
The basic purpose of NIS+ authorization is to specify the access rights that each NIS+ principal has for each NIS+ object and service.
Once the principal making an NIS+ request is authenticated, NIS+ places them in an authorization class. The access rights (permissions) that specify which activities a principal may do with a given NIS+ object are assigned on a class basis. In other words, one authorization class may have certain access rights while a different class has different rights.
-
Authorization classes. There are four authorization classes: owner, group, world, and nobody. (See NIS+ Authorization Classes below for details.)
-
Access rights. There are four types of access rights (permissions): create, destroy, modify, and read. (See NIS+ Access Rights for details.)
NIS+ Authorization Classes
NIS+ objects do not grant access rights directly to NIS+ principals.
Instead, they grant access rights to four classes of principal:
-
Owner. The principal who happens to be the object's owner gets the rights granted to the owner class.
-
Group. Each NIS+ object has one group associated with it. The members of an object's group are specified by the NIS+ administrator. The principals who belong to the object's group class get the rights granted to the group class. (In this context, group refers to NIS+ groups, not UNIX or net groups.)
-
World. The world class encompasses all NIS+ principals that a server has been able to authenticate. (That is, everyone who has been authenticated but who is not in either the owner or group classes.)
-
Nobody. Everyone belongs to the nobody class even those who are not authenticated.
Figure 11–4 Authorization Classes in NIS+
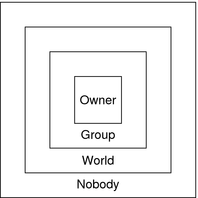
For any NIS+ request, the system determines which class the requesting principal belongs to and the principal then can use whatever access rights belonging to that class.
An object can grant any combination of access rights to each of these classes. Normally, however, a higher class is assigned the same rights as all the lower classes, plus possible additional rights.
For instance, an object could grant read access to the nobody and world classes; both read and modify access to the group class; and read, modify, create, and destroy access to the owner class.
The four classes are described in detail below.
NIS+ Owner Class
The owner is a single NIS+ principal.
A principal making a request for access to an NIS+ object must be authenticated (present a valid DES credential) before being granted owner access rights.
By default, an object's owner is the principal that created the object. However, an object's owner can cede ownership to another principal in two ways:
-
One way is for the principal to specify a different owner at the time the object is created (see Specifying NIS+ Access Rights in Commands).
-
A second way is for the principal to change the ownership of the object after it is created (see Changing Ownership of NIS+ Objects and Entries).
Once a principal gives up ownership, that principal gives up all owner's access rights to the object and keeps only the rights the object assigns to either the group, the world, or nobody.
NIS+ Group Class
The object's group is a single NIS+ group. (In this context, group refers to NIS+ groups, not UNIX or net groups.)
A principal making a request for access to an NIS+ object must be authenticated (present a valid DES credential) and belong to the group before being granted group access rights.
An NIS+ group is a collection of NIS+ principals, grouped together as a convenience for providing access to the namespace. The access rights granted to an NIS+ group apply to all the principals that are members of that group. (An object's owner, however, does not need to belong to the object's group.)
When an object is created it may be assigned a default group. A nondefault group can be specified for an object when it is created or after it is created. An object's group may be changed at any time.
Note –
Information about NIS+ groups is not stored in the NIS+ group table. The group table stores information about UNIX groups. Information about NIS+ groups is stored in the appropriate groups_dir directory object.
Information about NIS+ groups is stored in NIS+ group objects, under the groups_dir subdirectory of every NIS+ domain.
Figure 11–5 NIS+ Directory Structure
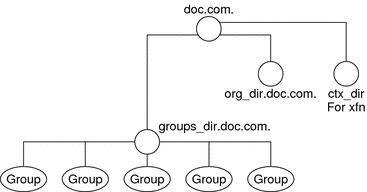
Instructions for administering NIS+ groups are provided in Chapter 17, Administering NIS+ Groups.
NIS+ World Class
The world class contains all NIS+ principals that are authenticated by NIS+. In other words, the world class includes everyone in the owner and group class, plus everyone else who presents a valid DES credential.
Access rights granted to the world class apply to all authenticated principals.
NIS+ Nobody Class
The nobody class is composed of anyone who is not properly authenticated. In other words, the nobody class includes everyone who does not present a valid DES credential.
Authorization Classes and the NIS+ Object Hierarchy
There is a hierarchy of NIS+ objects and authorization classes that can apply independently to each level.
The standard default NIS+ directory hierarchy is:
-
Directory level. In each NIS+ domain there are two NIS+ directory objects: groups_dir and org_dir. Each groups_dir directory object contains various groups. Each org_dir directory object contains various tables.
-
Group level or table level. Groups contain individual entries and possibly other groups. Tables contain both columns and individual entries.
-
Column level. A given table will have one or more columns.
-
Entry (row) level. A given group or table will have one or more entries.
The four authorization classes apply at each level. Thus, a directory object will have its own owner and group. The individual tables within a directory object will have their own individual owners and groups which may be different than the owner and group of the directory object. Within a table, an entry (row) may have its own individual owner or group which may be different than the owner and group of the table as a whole or the directory object as a whole. Within a table, individual columns have the same owner and group as the table as a whole.
NIS+ Access Rights
NIS+ objects specify their access rights as part of their object definitions. (You can examine these by using the niscat -o command.)
NIS+ objects specify access rights for NIS+ principals in the same way that UNIX files specify permissions for UNIX users. Access rights specify the types of operations that NIS+ principals are allowed to perform on NIS+ objects.
NIS+ operations vary among different types of objects, but they all fall into one of the four access rights categories: read, modify, create, and destroy.
-
Read A principal with read rights to an object can view the contents of that object.
-
Modify. A principal with modify rights to an object can change the contents of that object.
-
Destroy. A principal with destroy rights to an object can destroy or delete the object.
-
Create. A principal with create rights to a higher level object can create new objects within that level. In other words, if you have create rights to an NIS+ directory object, you can create new tables within that directory. If you have create rights to an NIS+ table, you can create new columns and entries within that table.
Every communication from an NIS+ client to an NIS+ server is, in effect, a request to perform one of these operations on a specific NIS+ object. For instance, when an NIS+ principal requests the IP address of another machine, it is requesting read access to the hosts table object, which stores that type of information. When a principal asks the server to add a directory to the NIS+ namespace, it is actually requesting modify access to the directory's parent object.
Keep in mind that these rights logically evolve down from directory to table to table column and entry levels. For example, to create a new table, you must have create rights for the NIS+ directory object where the table will be stored. When you create that table, you become its default owner. As owner, you can assign yourself create rights to the table which allows you to create new entries in the table. If you create new entries in a table, you become the default owner of those entries. As table owner, you can also grant table-level create rights to others. For example, you can give your table's group class table-level create rights. In that case, any member of the table's group can create new entries in the table. The individual member of the group who creates a new table entry becomes the default owner of that entry.
NIS+ Administrator
An NIS+ administrator is anyone who has administrative rights over an NIS+ object. For the purpose of this discussion, administrative rights are defined as create, destroy, and for some objects, modify rights. (See NIS+ Access Rights for a description of NIS+ access rights.)
Whoever creates an NIS+ object sets the initial access rights to that object. If the creator restricts administrative rights to the object's owner (initially the creator), than only the owner has administrative power over that object. On the other hand, if the creator grants administrative rights to the object's group, then everyone in that group has administrative power over that object.
Thus, who ever has administrative rights over an object is considered to be an NIS+ administrator for that object.
In other words, the NIS+ software does not enforce any requirement that there be a single NIS+ administrator.
Theoretically, you could grant administrative rights to the world class, or even the nobody class. The software allows you to do that. But granting administrative rights beyond the group class nullifies NIS+ security. Thus, if you grant administrative rights to either the World or the nobody class you are, in effect, defeating the purpose of NIS+ security.
NIS+ Password, Credential, and Key Commands
Note –
The NIS+ service is managed by the Service Management Facility. Administrative actions on this service, such as enabling, disabling, or restarting, can be performed by using the svcadm command. See NIS+ and the Service Management Facility for more information about using the Facility with NIS+. For an overview of the Facility, refer to Chapter 18, Managing Services (Overview), in System Administration Guide: Basic Administration. Also refer to the svcadm(1M) and svcs(1) man pages for more details.
Use the following commands to administer passwords, credentials, and keys (see the appropriate man pages for a full description of each command):
-
chkey. Changes a principal's Secure RPC key pair. Do not use chkey unless necessary, use passwd instead. See Changing Keys for an NIS+ Principal for more information.
-
keylogin. Decrypts and stores a principal's secret key with the keyserv.
-
keyserv. Enables the server for storing private encryption keys. See Keylogin With NIS+ for more information about keys. See NIS+ and the Service Management Facility for information about managing NIS+ by using the Service Management Facility.
-
nisaddcred. Creates credentials for NIS+ principals. See Creating NIS+ Credential Information and Administering NIS+ Credential Information for more information.
-
nisupdkeys. Updates public keys in directory objects. See Updating Public Keys for NIS+ for more information.
-
passwd. Changes and administers principal's password. See Chapter 16, Administering NIS+ Passwords for more information.
Chapter 12 Administering NIS+ Credentials
This chapter describes NIS+ credentials and how to administer them.
Tip –
Some NIS+ security tasks can be performed more easily with Solaris Management Console tools if you have them available.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
NIS+ Credentials
NIS+ credentials are used to identify NIS+ users. This chapter assumes that you have an adequate understanding of the NIS+ security system in general, and in particular of the role that credentials play in that system.
For a complete description of NIS+ credential-related commands and their syntax and options, see the NIS+ man pages.
Note –
The description of DES credentials in this chapter is applicable to 192-bit Diffie-Hellman DES credentials. While similar, authentication using other key lengths differs in details. When the command line interface is used to manipulate the keys, the differences are transparent to both the user and the system administrator. Use nisauthconf to display or set the prescribed key lengths.
How NIS+ Credentials Work
Note –
Some NIS+ security tasks can be performed more easily with Solaris Management Console tools, if you have them available.
The credential/authentication system prevents someone from assuming some other user's identity. That is, it prevents someone with root privileges on one machine from using the su command to assume the identity of a second user who is either not logged in at all or logged in on another machine and then accessing NIS+ objects with the second user's NIS+ access privileges.
NIS+ cannot prevent someone who knows another user's login password from assuming that other user's identity and the other user's NIS+ access privileges. Nor can NIS+ prevent a user with root privileges from assuming the identity of another user who is currently logged in on the same machine.
NIS+ Credentials and Credential Information
To understand how DES credentials are created and how they work, you need to distinguish between the credential itself and the information that is used to create and verify it.
-
Credential information: The data that is used to generate a DES credential and by the server to verify that credential.
-
DES credential: The bundle of numbers that is sent by the principal to the server to authenticate the principal. A principal's credential is generated and verified each time the principal makes an NIS+ request. See DES Credential in NIS+ for a detailed description of the DES credential.
NIS+ Authentication Components
In order for the credential/authentication process to work the following components must be in place:
-
Principal's DES credential information. This information is initially created by an NIS+ administrator for each principal. It is stored in the cred table of the principal's home domain. A principal's DES credential information consists of:
-
Principal name. This would be a user's fully qualified login ID or a machine's fully qualified host name.
-
Principal's Secure RPC netname. Each principal has a unique Secure RPC netname. (See DES Credential Secure RPC Netname for more information on Secure RPC netnames.)
-
Principal's public key.
-
Principal's encrypted private key.
-
-
Principal's LOCAL credential
-
Server's public keys. Each directory object stores copies of the public keys of all the servers in that domain. Note that each server's DES credentials are also stored in the cred table.
-
Keyserver copy of principal's private key. The keyserver has a copy of the private key of the principal that is currently logged in (user or machine).
How NIS+ Principals Are Authenticated
There are three phases to the authorization process:
-
Preparation phase. This consists of the setup work performed by an NIS+ administrator prior to the user logging in; for example, creating credential information for the user.
-
Login phase. This consists of the actions taken by the system when a user logs in.
-
Request phase. This consists of the actions taken by the software when an NIS+ principal makes a request for an NIS+ service or access to an NIS+ object.
These three phases are described in detail in the following subsections.
NIS+ Credentials Preparation Phase
The easiest way for an NIS+ administrator to create credential information for users is to use the nisclient script. This section describes how to create client information using the NIS+ command set.
Prior to an NIS+ principal logging in, an NIS+ administrator must create DES credential information for that principal (user or machine).
The administrator must:
-
Create a public key and an encrypted private key for each principal. These keys are stored in the principal's home domain cred table. This can be done with the nisaddcred command as described in Creating Credential Information for NIS+ Principals.
-
Create server public keys. (See Updating Public Keys for NIS+.)
NIS+ Login Phase – Detailed Description
-
The keylogin program is run for the principal. The keylogin program gets the principal's encrypted private key from the cred table and decrypts it using the principal's login password.
Note –When a principal's login password is different from his or her Secure RPC password, keylogin cannot decrypt it and the user starts getting “cannot decrypt” errors or the command fails without a message. For a discussion of this problem, see Secure RPC Passwords and the Login Password Problem in NIS+.
-
The principal's decrypted private key is passed to the keyserver which stores it for use during the request phase.
Note –The decrypted private key remains stored for use by the keyserver until the user does an explicit keylogout. If the user simply logs out (or goes home for the day without logging out), the decrypted private key remains stored in the server. If someone with root privileges on a user's machine switched to the user's login ID, that person would then have use of the user's decrypted private key and could access NIS+ objects using the user's access authorization. Thus, for added security, users should be cautioned to perform an explicit keylogout when they cease work. If they also log out of the system, all they need do is log back in when they return. If they do not explicitly log out, they will have to perform an explicit keylogin when they return to work.
When a principal logs into the system the following steps are automatically performed:
NIS+ Request Phase – Detailed Description
-
NIS+ checks the cred table of the object's domain.
-
If the principal has LOCAL credential information, NIS+ uses the domain information contained in the LOCAL credential to find the principal's home domain cred table where it obtains the information it needs.
-
If the principal has no credential information, the rest of the process is aborted and the principal is given the authorization access class of nobody.
-
-
NIS+ gets the user's DES credential from the cred table of the user's home domain. The encrypted private key is decrypted with the user's password and saved by the keyserver.
-
NIS+ obtains the server's public key from the NIS+ directory object.
-
The keyserver takes the principal's decrypted private key and the public key of the object's server (the server where the object is stored) and uses them to create a common key.
-
The common key is then used to generate an encrypted DES key. To do this, Secure RPC generates a random number which is then encrypted using the common key. For this reason, the DES key is sometimes referred to as the random key or the random DES key.
-
NIS+ then takes the current time of the principal's server and creates a time stamp that is encrypted using the DES key.
-
NIS+ then creates a 15-second window, which is encrypted with the DES key. This window is the maximum amount of time that is permitted between the time stamp and the server's internal clock.
-
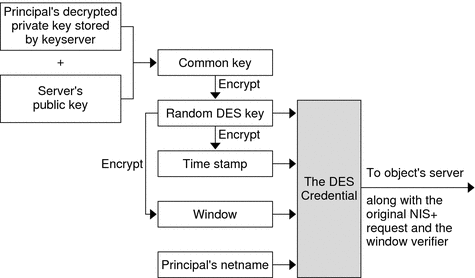
NIS+ then forms the principal's DES credential, which is composed of the following items.
-
NIS+ then passes the following information to the server where the NIS+ object is stored.
-
The access request (whatever it might be)
-
The principal's DES credential
-
Window verifier (encrypted), which is the encrypted window plus one
-
-
The object's server receives this information.
-
The object's server uses the Secure RPC netname portion of the credential to look up the principal's public key in the cred table of the principal's home domain.
-
The server then uses the principal's public key and the server's private key to regenerate the common key. This common key must match the common key that was generated by the principal's private key and the server's public key.
-
The common key is used to decrypt the DES key that arrived as part of the principal's credential.
-
The server decrypts the principal's time stamp with the newly decrypted DES key and verifies it with the window verifier.
-
The server then compares the decrypted and verified time stamp with the server's current time and proceeds as follows.
-
If the time difference at the server exceeds the window limit, the request is denied and the process aborts with an error message. For example, suppose the time stamp is 9:00am and the window is one minute. If the request is received and decrypted by the server after 9:01am, it is denied.
-
If the time stamp is within the window limit, the server checks to see if the time stamp is greater than the one previously received from the principal. This ensures that NIS+ requests are handled in the correct order.
-
Requests received out of order are rejected with an error message. For example, if the time stamp is 9:00am and the most recently received request from this principal had a time stamp of 9:02am, the request would be rejected.
-
Requests that have a time stamp equal to the previous one are rejected with an error message. This ensures that a replayed request is not acted on twice. For example, if the time stamp is 9:00am and the most recently received request from this principal also had a time stamp of 9:00am, this request would be rejected.
-
-
-
If the time stamp is within the window limit, and greater than the previous request from that principal, the server accepts the request.
-
The server then complies with the request and stores the time stamp from this principal as the most recently received and acted on request.
-
To confirm to the principal that the information received from the server in answer to the request comes from a trusted server, the server encrypts the time stamp with the principal's DES key and sends it back to the principal along with the data.
-
At the principal's end, the returned time stamp is decrypted with the principal's DES key.
-
If the decryption succeeds, the information from the server is returned to the requester.
-
If the decryption fails for some reason, an error message is displayed.
-
Every time an NIS+ principal requests access to an NIS+ object, the NIS+ software performs a multistage process to authenticate that principal:
DES Credential in NIS+
The DES credential consists of:
-
The principal's Secure RPC netname (see DES Credential Secure RPC Netname).
-
A verification field (see DES Credential Verification Field in NIS+).
DES Credential Secure RPC Netname
Secure RPC netname. This portion of the credential is used to identify the NIS+ principal. Every Secure RPC netname contains the following three components.
-
Prefix. The prefix is always the word unix.
-
Identifier. If the principal is a client user, the ID field is the user's UID. If the principal is a client machine, the ID field is the machine's hostname.
-
Domain name. The domain name is the name of the domain that contains the principal's DES credential (in other words, the principal's home domain).
Note –
Remember that an NIS+ principal name always has a trailing dot, and a Secure RPC netname never has a trailing dot.
Table 12–1 Secure RPC Netname Format
|
Principal |
Prefix |
Identifier |
Domain |
Example |
|---|---|---|---|---|
|
User |
unix |
UID |
Domain containing user's password entry and the DES credential itself |
unix.24601@sales.doc.com |
|
machine |
unix |
hostname |
The domain name returned by executing the domainname command on that machine |
unix.machine7@sales.doc.com |
DES Credential Verification Field in NIS+
The verification field is used to make sure the credential is not forged. It is generated from the credential information stored in the cred table.
The verification field is composed of:
-
The principal's encrypted DES key, generated from the principal's private key and the NIS+ server's public key as described in NIS+ Request Phase – Detailed Description
-
The encrypted time stamp
-
The time window
How the DES Credential in NIS+ Is Generated
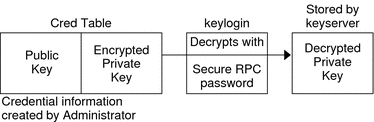
To generate its DES credential, the principal depends on the keylogin command, which must have been executed before the principal tries to generate its credential. The keylogin command (often referred to simply as a keylogin) is executed automatically when an NIS+ principal logs in. See Figure 12–2.
Note –
Note that if the principal's login password is different from the principal's Secure RPC password, a successful keylogin cannot be performed. See Secure RPC Passwords and the Login Password Problem in NIS+ for a discussion of this situation.
The purpose of the keylogin is to give the principal access to the principal's private key. keylogin fetches the principal's private key from the cred table, decrypts it with the principal's Secure RPC password (remember that the private key was originally encrypted with the principal's Secure RPC password), and stores it locally with the keyserver for future NIS+ requests.
Figure 12–1 keylogin Generates an NIS+ Principal's Private Key
To generate its DES credential, the principal still needs the public key of the server to which it will send the request. This information is stored in the principal's directory object. Once the principal has this information, it can form the verification field of the credential.
First, the principal generates a random DES key for encrypting various credential information. The principal uses its own private key (stored in the keyserver) and the server's public key to generate a common key that is used to generate and encrypt the random DES key. It then generates a time stamp that is encrypted with the DES key and combines it with other credential-related information into the verification field.
Figure 12–2 Creating the DES Credential in NIS+
Secure RPC Passwords and the Login Password Problem in NIS+
When a principal's login password is different from his or her Secure RPC password, keylogin cannot decrypt it at login time because keylogin defaults to using the principal's login password, and the private key was encrypted using the principal's Secure RPC password.
When this occurs, the principal can log in to the system, but for NIS+ purposes the principal is placed in the authorization class of nobody because the keyserver does not have a decrypted private key for that user. Since most NIS+ environments are set up to deny the nobody class create, destroy, and modify rights to most NIS+ objects, this results in “permission denied” errors when the user tries to access NIS+ objects.
Note –
In this context, network password is sometimes used as a synonym for Secure RPC password. When prompted for your “network password,” enter your Secure RPC password.
To be placed in one of the other authorization classes, a user in this situation must explicitly run the keylogin program and give the principal's Secure RPC password when keylogin prompts for a password. (See Keylogin With NIS+.)
But an explicit keylogin provides only a temporary solution that is good only for the current login session. The keyserver now has a decrypted private key for the user, but the private key in the user's cred table is still encrypted using the user's Secure RPC password, which is different than the user's login password. The next time the user logs in, the same problem recurs. To permanently solve the problem the user needs to re-encrypt the private key in the cred table to one based on the user's login ID rather than the user's Secure RPC password. To do this, the user needs to run chkey -p as described in Changing Keys for an NIS+ Principal.
-
Log in using the login password.
-
Run the keylogin program to temporarily get a decrypted private key stored in the keyserver and thus gain temporary NIS+ access privileges.
-
Run chkey -p to permanently change the encrypted private key in the cred table to one based on the user's login password.
-
When you are ready to finish this login session, run keylogout.
-
Log off the system with logout.
Thus, to permanently solve problems related to a difference in Secure RPC password and login password, the user (or an administrator acting for the user) must perform these steps:
Cached Public Keys Problems in NIS+
Occasionally, you might find that even though you have created the proper credentials and assigned the proper access rights, some principal requests still get denied. The most common cause of this problem is the existence of stale objects with old versions of a server's public key.
You can usually correct this problem by:
-
Running nisupdkeys on the domain you are trying to access. (See nisupdkeys Command for information on using the nisupdkeys command and Stale and Outdated NIS+ Credential Information for information on how to correct this type of problem.)
-
Stopping the NIS+ service on your machine by using the svcadm command, removing /var/nis/NIS_SHARED_DIRCACHE, and then restarting the NIS+ service.
Where Credential-Related Information Is Stored in NIS+
This section describes where credential-related information is stored throughout the NIS+ namespace.
Credential-related information, such as public keys, is stored in many locations throughout the namespace. NIS+ updates this information periodically, depending on the time-to-live values of the objects that store it, but sometimes, between updates, it gets out of sync. As a result, you may find that operations that should work, do not. lists all the objects, tables, and files that store credential-related information and how to reset it.
Note –
The NIS+ service is managed by the Service Management Facility (SMF). Enabling, disabling, or restarting NIS+ daemons such as rpc.nisd, keyserv, and nis_cachemgr, can be performed by using the svcadm command. See NIS+ and the Service Management Facility for more information about using SMF with NIS+. For an overview of SMF, refer to Chapter 18, Managing Services (Overview), in System Administration Guide: Basic Administration. Also refer to the svcadm(1M) and svcs(1) man pages for more details.
Table 12–2 Where NIS+ Credential-Related Information Is Stored
|
Item |
Stores |
To Reset or Change |
|---|---|---|
|
cred table |
NIS+ principal's public key and private key. These are the master copies of these keys. |
Use nisaddcred to create new credentials; it updates existing credentials. An alternative is chkey. |
|
directory object |
A copy of the public key of each server that supports it. |
Run the /usr/lib/nis/nisupdkeys command on the directory object. |
|
keyserver |
The secret key of the NIS+ principal that is currently logged in. |
Run keylogin for a principal user or keylogin -rfor a principal machine. |
|
NIS+ daemon |
Copies of directory objects, which in turn contain copies of their servers' public keys. |
Stop the rpc.nisd daemon and the cache manager by disabling the NIS+ service, and then remove NIS_SHARED_DIRCACHE from /var/nis. Then restart the NIS+ service. |
|
Directory cache |
A copy of directory objects, which in turn contain copies of their servers' public keys. |
Restart the NIS+ cache manager with the -i option |
|
cold-start file |
A copy of a directory object, which in turn contains copies of its servers' public keys. |
Stop the NIS+ service. Remove the NIS_COLD_START and NIS_SHARED_DIRCACHE files from /var/nis. Restart the NIS+ service. |
|
|
A user's password. |
Use the passwd -r nisplus command. It changes the password in the NIS+ passwd table and updates it in the cred table. |
|
passwd file |
A user's password or a machine's superuser password. |
Use the passwd -r nisplus command, whether logged in as super user or as yourself, whichever is appropriate. |
|
passwd map (NIS) |
A user's password |
Use the passwd -r nisplus command. |
NIS+ cred Table in Detail
Credential information for principals is stored in a cred table. The cred table is one of the 16 standard NIS+ tables. Each domain has one cred table, which stores the credential information of client machines that belong to that domain and client users who are allowed to log into them. (In other words, the principals of that domain.) The cred tables are located in their domains' org_dir subdirectory.
Never link a cred table. Each org_dir directory must have its own cred table. Never use a link to some other org_dir cred table.
For users, the cred table stores LOCAL credential information for all users who are allowed to log into any of the machines in the domain. The cred table also stores DES credential information for those users that have the domain as their home domain.
You can view the contents of a cred table with the niscat command, described in Chapter 19, Administering NIS+ Tables.
The cred table, as shown in Table 12–3, has five columns.
Table 12–3 NIS+ cred Table Credential Information|
NIS+ Principal Name |
Authentication Type |
Authentication Name |
Public Data |
Private Data |
|
|---|---|---|---|---|---|
|
Column Name |
cname |
auth_type |
auth_name |
public_data |
private_data |
|
User |
Fully qualified principal name |
LOCAL |
UID |
GID list |
|
|
Machine |
Fully qualified principal name |
DES |
Secure RPC netname |
Public key |
Encrypted Private key |
The Authentication Type column, determines the types of values found in the other four columns.
-
LOCAL. If the authentication type is LOCAL, the other columns contain a principal user's name, UID, and GID; the last column is empty.
-
DES. If the authentication type is DES, the other columns contain a principal's name, Secure RPC netname, public key, and encrypted private key. These keys are used in conjunction with other information to encrypt and decrypt a DES credential.
Creating NIS+ Credential Information
There are several methods of creating and administering credential information:
-
Use Solaris Management Console tools if you have them available. They provide easier methods of credential administration and are recommended for administering individual credentials.
-
Use the nisclient script. This is another easy method of creating or altering credentials for a single principal. Because of its convenience, this is a recommended method of administering individual credentials. gives step by step instructions on using the nisclient script to create credential information.
-
Use the nispopulate script. This is an easy method of creating or altering credentials for a one or more principals who already have information on them stored in NIS maps or /etc files. Because of its convenience, this is a recommended method of administering credentials for groups of NIS+ principals. For step by step instructions on using the nispopulate script to create credential information, see.Populating NIS+ Tables.
-
Use the nisaddcred command. The section below describes how credentials and credential information are created using nisaddcred.
nisaddcred Command
The command used to create credential information is nisaddcred.
Note –
You can also use the nispopulate and nisclient scripts to create credential information. They, in turn, use the nisaddcred command. These scripts are much easier to use, and more efficient, than the nisaddcred command. Unless your network requires special features, you should use the scripts.
The nisaddcred command creates, updates, and removes LOCAL and DES credential information. To create credential information, you must have create rights to the proper domain's cred table. To update a credential, you must have modify rights to the cred table or, at least, to that particular entry in the cred table. To delete a credential, you must have destroy rights to the cred table or the entry in the cred table.
-
To create or update credentials for another NIS+ principal, use:
For LOCAL credentials
nisaddcred -p uid -P principal-name local
For DES credentials
nisaddcred -p rpc-netname -P principal-name des
-
To update your own credentials, use:
For LOCAL credentials
nisaddcred -local
For DES credentials, use:
nisaddcred des
-
nisaddcred -r principal-name
NIS+ Credential-Related Commands
In addition to the nisaddcred command described in this chapter, two other commands can provide some useful information about credentials. The niscat and nismatch commands are described in the following table.
Table 12–4 Additional NIS+ Credential-Related Commands|
Command |
Description |
See |
|---|---|---|
|
niscat -o |
Lists a directory's properties. By looking in the public key field of the directory's server, you can tell whether the directory object is storing a public key. | |
|
nismatch- |
When run on the cred table, displays credential information for principal. |
How nisaddcred Creates NIS+ Credential Information
Use nisaddcred to create LOCAL and DES credential information.
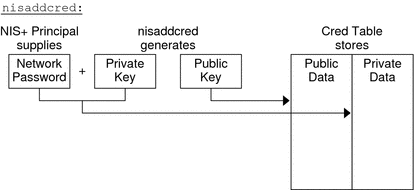
LOCAL NIS+ Credential Information
When used to create LOCAL credential information, nisaddcred simply extracts the principal user's UID (and GID) from the principal's login record and places it in the domain's cred table.
DES Credential Information in NIS+
-
Forming the principal's Secure RPC netname. A Secure RPC netname is formed by taking the principal's user ID number from the password record and combining it with the domain name (unix.1050@doc.com, for example).
-
Generating the principal's private and public keys.
When used to create DES credential information, nisaddcred goes through a two-part process:
To encrypt the private key, nisaddcred needs the principal's Secure RPC password. When the nisaddcred command is invoked with the -des argument, it prompts the principal for a Secure RPC password. Normally, this password is the same as the principal's login password. (If it is different, the user will have to perform additional steps when logging in, as described in Secure RPC Passwords and the Login Password Problem in NIS+.)
The nisaddcred command generates a pair of random, but mathematically related 192-bit authentication keys using the Diffie-Hellman cryptography scheme. These keys are called the Diffie-Hellman key-pair, or simply key-pair for short.
One of these is the private key, and the other is the public key. The public key is placed in the public data field of the cred table. The private key is placed in the private data field, but only after being encrypted with the principal's Secure RPC password.
Figure 12–3 How nisaddcred Creates an NIS+ Principal's Keys
The principal's private key is encrypted as a security precaution because the cred table, by default, is readable by all NIS+ principals, even unauthenticated ones.
Secure RPC Netname and NIS+ Principal Name
When creating credential information, you will often have to enter a principal's rpc-netname and principal-name.
Each has its own syntax:
-
Secure RPC netname. A Secure RPC netname is a name whose syntax is determined by the Secure RPC protocol. Therefore, it does not follow NIS+ naming conventions:
-
For users, the syntax is: unix.uid@domain
-
For machines, the syntax is: unix.hostname@domain
If a Secure RPC netname identifies a user, it requires the user's UID. If it identifies a machine, it requires the machine's host name. (When used with the nisaddcred command it is always preceded by the -p (lowercase) flag.)
A Secure RPC netname always begins with the unix (all lowercase) prefix and ends with a domain name. However, because it follows the Secure RPC protocol, the domain name does not contain a trailing dot.
-
-
Principal name. An NIS+ principal follows the normal NIS+ naming conventions, but it must always be fully qualified. the syntax is: principal.domain.
Whether it identifies a client user or a client machine, it begins with the principal's name, followed by a dot and the complete domain name, ending in a dot. (When used with nisaddcred to create credential information, it is always preceded by the -P (uppercase) flag. When used to remove credential information, it does not use the -P flag.)
Creating NIS+ Credential Information for the Administrator
When a namespace is first set up, credential information is created first for the administrators who will support the domain. Once they have credential information, they can create credential information for other administrators, client machines, and client users.
When you try to create your own credential information, you run into a problem of circularity: you cannot create your own credential information unless you have Create rights to your domain's cred table, but if the NIS+ environment is properly set up, you cannot have such rights until you have credentials. You have to step out of the loop somehow.
You can do this in one of two ways:
-
By creating your credential information while logged in as superuser to your domain's master server.
-
By having another administrator create your credential information using a dummy password, then changing your password with the chkey command.
In either case, your credential information is thus created by another NIS+ principal. To create your own credential information, follow the instructions in Creating Credential Information for NIS+ Principals.
Creating Credential Information for NIS+ Principals
Credential information for NIS+ principals can be created any time after their domain has been set up; in other words, once a cred table exists.
To create credential information for an NIS+ principal:
-
You must have Create rights to the cred table of the principal's home domain.
-
The principal must be recognized by the server. This means that:
-
If the principal is a user, the principal must have an entry either in the domain's NIS+ passwd table or in the server's /etc/passwd file.
-
If the principal is a machine, it must have an entry either in the domain's NIS+ Hosts table or in the server's.
-
Once those conditions are met, you can use the nisaddcred command with both the -p and -P options:
For LOCAL credentials
nisaddcred -p uid -P principal-name local |
For DES credentials
nisaddcred -p rpc.netname -P principal-name des |
Remember these principles:
-
You can create both LOCAL and DES credential information for a principal user.
-
You can only create DES credential information for a principal machine.
-
You can create DES credential information only in the principal's home domain (user or machine).
-
You can create LOCAL credential information for a user in both the user's home domain and in other domains.
For NIS+ User Principals – Example
This example creates both LOCAL and DES credential information for an NIS+ user named morena who has a UID of 11177. She belongs to the doc.com. domain, so this example enters her credential information from a principal machine of that domain:
client# nisaddcred -p 11177 -P morena.doc.com. local client# nisaddcred -p unix.11177@sales.doc.com \ -P morena.doc.com. des Adding key pair for unix.11177@sales.doc.com (morena.doc.com.). Enter login password: |
The proper response to the Enter login password: prompt is morena's login password. (If you don't know her login password, you can use a dummy password that she can later change using chkey, as described in the next example.)
Using a Dummy Password and chkey in NIS+ – Example
If you don't know the user's login password, you can use a dummy password as described below.
Table 12–5, shows how another administrator, whose credential information you create using a dummy password, can then use chkey to change his or her own password. In this example, you create credential information for an administrator named Eiji who has a UID of 119. Eiji, whose login ID is eiji, belongs to the root domain, so you would enter his credential information from the root master server which is named rootmaster.
Table 12–5 Creating NIS+ Administrator Credentials: Command Summary|
Tasks |
Commands |
|---|---|
|
Create LOCAL credential information for Eiji. |
rootmaster# nisaddcred -p 119 -P eiji.doc.com. local |
|
Create DES credential information for Eiji. |
rootmaster# nisaddcred -p unix.119@doc.com -P eiji.doc.com. des Adding key pair for unix.119@doc.com (eiji.doc.com.). |
|
Type dummy password for Eiji. |
Enter eiji's login password: nisaddcred: WARNING: password differs from login passwd |
|
Re-enter dummy password. |
Retype password: |
|
You tell Eiji the dummy password that you used. |
|
|
Eiji logs into rootmaster. |
rootmaster% login: eiji |
|
Eiji enters real login password. |
Password: |
|
Eiji gets error message but is allowed to log in anyway. |
Password does not decrypt secret key for unix.119@doc.com. |
|
Eiji runs keylogin. |
rootmaster% keylogin |
|
Eiji types dummy password. |
Password: dummy-password |
|
Eiji runs chkey. |
rootmaster% chkey -p Updating nisplus publickey database Generating new key for'unix.119@doc.com'. |
|
Eiji types real login password. |
Enter login password: |
|
Eiji re-types real login password. |
Retype password: Done. |
First, you would create Eiji's credential information in the usual way, but using a dummy login password. NIS+ would warn you and ask you to re-type it. When you did, the operation would be complete. The domain's cred table would contain Eiji's credential information based on the dummy password. The domain's passwd table (or /etc/passwd file), however, would still have his login password entry so that he can log in to the system.
Then, Eiji would log in to the domain's master server, typing his correct login password (since the login procedure checks the password entry in the passwd table or /etc/passwd file). From there, Eiji would first run keylogin, using the dummy password (since a keylogin checks the cred table), and then use the chkey -p command to change the cred entry to the real thing.
Creating Credential Information in Another NIS+ Domain – Example
The two previous examples created credential information for a principal user while the principal user was logged in to the master server of the principal's home domain. However, if you have the proper access rights, you can create credential information in another domain. Simply append the domain name to this syntax:
For LOCAL credentials
nisaddcred -p uid -P principal-name local domain-name |
For DES credentials
nisaddcred -p rpc-netname -P principal-name des domain-name |
The following example first creates LOCAL and DES credential information for an administrator named Chou in her home domain, which happens to be the root domain, then adds her LOCAL credential information to the doc.com domain. Chou's UID is 11155. This command is typed on from the root master server. For simplicity, it assumes you are entering Chou's correct login password.
rmaster# nisaddcred -p 11155 -P chou.doc.com. local rmaster# nisaddcred -p unix.11155@doc.com -P chou.doc.com. des Adding key pair for unix.11155@doc.com (chou.doc.com.). Enter login password: rootmaster# nisaddcred -p 11155 -P chou.doc.com. local doc.com. |
LOCAL credential information maps a UID to an NIS+ principal name. Although an NIS+ principal that is a client user can have different user IDs in different domains, it can have only one NIS+ principal name. So, if an NIS+ principal such as chou will be logging in from a domain other than her home domain, not only should she have a password entry in that domain, but also a LOCAL credential in that domain's cred table.
For NIS+ Machines – Example
This example creates credential information for a principal machine. Its host name is starshine1 and it belongs to the root domain. Therefore, its credential information is created from the root master server. In this example, you create them while logged in as root to the root master; however, if you already have valid credential information and the proper access rights, you could create them while logged in as yourself.
rootmaster# nisaddcred -p unix.starshine1@doc.com -P starshine1.doc.com. des Adding key pair for unix.starshine1@doc.com (starshine1.doc.com.). Enter starshine1.doc.com.'s root login password: Retype password: |
The proper response to the password prompt is the principal machine's superuser password. Of course, you could use a dummy password that would later be changed by someone logged in as superuser to that principal machine.
Administering NIS+ Credential Information
The following sections describe how to use the nisaddcred command to administer existing credential information. You must have create, modify, read, and destroy rights to the cred table to perform these operations.
Updating Your Own NIS+ Credential Information
Updating your own credential information is considerably easier than creating it. Just type the simple versions of the nisaddcred command while logged in as yourself:
# nisaddcred des # nisaddcred local |
To update credential information for someone else, you simply perform the same procedure that you would use to create that person's credential information.
Removing NIS+ Credential Information
The nisaddcred command removes a principal's credential information, but only from the local domain where the command is run.
Thus, to completely remove a principal from the entire system, you must explicitly remove that principal's credential information from the principal's home domain and all domains where the principal has LOCAL credential information.
To remove credential information, you must have modify rights to the local domain's cred table. Use the -r option and specify the principal with a full NIS+ principal name:
# nisaddcred -r principal-name |
The following two examples remove the LOCAL and DES credential information of the administrator Morena.doc.com. The first example removes both types of credential information from her home domain (doc.com.), the second removes her LOCAL credential information from the sales.doc.com. domain. Note how they are each entered from the appropriate domain's master servers.
rootmaster# nisaddcred -r morena.doc.com. salesmaster# nisaddcred -r morena.doc.com. |
To verify that the credential information was indeed removed, run nismatch on the cred table, as shown below. For more information about nismatch, see Chapter 19, Administering NIS+ Tables.
rootmaster# nismatch morena.doc.com. cred.org_dir salesmaster# nismatch morena.doc.com. cred.org_dir |
Chapter 13 Administering NIS+ Keys
This chapter describes NIS+ keys and how to administer them.
Tip –
Some NIS+ security tasks can be performed more easily with Solaris Management Console tools if you have them available.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
NIS+ Keys
NIS+ keys are used to encrypt NIS+ related information.
This chapter assumes that you have an adequate understanding of the NIS+ security system in general, and in particular of the role that keys play in that system. See Chapter 11, NIS+ Security Overview for more information.
For a complete description of NIS+ key-related commands and their syntax and options, see the NIS+ man pages. (The nisaddcred command also performs some key-related operations. See Chapter 12, Administering NIS+ Credentials for more information.)
Note –
The NIS+ service is managed by the Service Management Facility (SMF). Administrative actions on the NIS+ services, such as enabling, disabling, or restarting, can be performed by using the svcadm command. See NIS+ and the Service Management Facility for more information about using SMF with NIS+. For an overview of SMF, refer to Chapter 18, Managing Services (Overview), in System Administration Guide: Basic Administration. Also refer to the svcadm(1M) and svcs(1) man pages for more details.
Keylogin With NIS+
When a principal logs in, the login process prompts for a password. That password is used to pass the user through the login security gate and give the user access to the network. The login process also decrypts the user's private key stored in the user's home domain cred table and passes that private key to the keyserver. The keyserver then uses that decrypted private key to authenticate the user each time the user accesses an NIS+ object.
Normally, this is the only time the principal is asked to provide a password. However, if the principal's private key in the cred table was encrypted with a password that was different from the user's login password, login cannot decrypt it using the login password at login time, and thus cannot provide a decrypted private key to the keyserver. (This most often occurs when a user's private key in the cred table was encrypted with a Secure RPC password different from the user's login password.)
Note –
In this context, network password is sometimes used as a synonym for Secure RPC password.
To temporarily remedy this problem, the principal must perform a keylogin, using the keylogin command, after every login. (The -r flag is used to keylogin the superuser principal and to store the superuser's key in /etc/.rootkey on a host.)
For a principal user
keylogin |
For a principal machine (only once)
keylogin -r |
Note, however, that performing an explicit keylogin with the original password provides only a temporary solution good for the current login session only. The private key in the cred table is still encrypted with a password different than the user's login password so the next time the user logs in the problem will reoccur. To permanently solve this problem, the user must run chkey to change the password used to encrypt the private key to the user's login password (see Changing Keys for an NIS+ Principal).
Changing Keys for an NIS+ Principal
The chkey command changes an NIS+ principal's public and private keys that are stored in the cred table. It does not affect the principal's entry either in the passwd table or in the /etc/passwd file.
-
Generates new keys and encrypts the private key with the password. Run chkey with the -p option to re-encrypt the existing private key with a new password.
-
Generates a new Diffie-Hellman key pair and encrypts the private key with the password you provide. (Multiple Diffie-Hellman key pairs can exist for each principal.) In most cases, however, you do not want a new keypair, you want to re-encrypt your current existing private key with the new password. To do this, run chkey with the -p option.
See the man pages for more information on these subjects.
Note –
In an NIS+ environment, when you change your login password with any of the current administration tools or the passwd (or nispasswd) commands, your private key in the cred table is automatically re-encrypted with the new password for you. Thus, you do not need to explicitly run chkey after a change of login password.
The chkey command interacts with the keyserver, the cred table, and the passwd table.
In order to run chkey, you:
-
Must have an entry in the passwd table of your home domain. Failure to meet this requirement will result in an error message.
-
Must run keylogin to make sure that the keyserver has a decrypted private key for you.
-
Must have modify rights to the cred table. If you do not have modify rights you will get a “permission denied” type of error message.
-
Must know the original password with which the private key in the cred table was encrypted. (In most cases, this your Secure RPC password.)
To use the chkey command to re-encrypt your private key with your login password, you first run keylogin using the original password, and then use chkey -p, as shown in Table 13–1, which illustrates how to perform a keylogin and chkey for a principal user.
Table 13–1 Re-encrypting Your NIS+ Private Key: Command Summary|
Tasks |
Commands |
|---|---|
|
Log in. |
Sirius% login Login-name |
|
Provide login password. |
Password: |
|
If login password and Secure RPC password are different, perform a keylogin. |
Sirius% keylogin |
|
Provide the original password that was used to encrypt the private key. |
Password: Secure RPC password |
|
Run chkey. |
Sirius% chkey -p Updating nisplus publickey database Updating new key for 'unix.1199@Doc.com'. |
|
Enter login password. |
Enter login password: login-password |
|
Re-enter login password |
Retype password: |
Changing the NIS+ Keys
The following sections describe how to change the keys of an NIS+ principal.
Note –
Whenever you change a server's keys, you must also update the key information of all the clients in that domain as explained in Updating NIS+ Client Key Information.
Changing NIS+ Root Keys From Root
Table 13–2, shows how to change the keys for the root master server from the root master (as root).
Table 13–2 Changing an NIS+ Root Master's Keys: Command Summary|
Tasks |
Commands |
|---|---|
|
Create new DES credentials |
rootmaster# nisaddcred des |
|
Find the NIS+ service |
rootmaster# svcs \*nisplus\* |
|
Stop the NIS+ service |
rootmaster# svcadm disable -t /network/rpc/nisplus:default |
|
Remove the -S 0 security option |
Edit the /lib/svc/method/nisplus file to remove the -S 0 option |
|
Restart NIS+ service with no security |
# svcadm enable network/rpc/nisplus |
|
Perform a keylogout (previous keylogin is now out of date) |
rootmaster# keylogout -f |
|
Update the keys in the directories served by the master |
rootmaster# nisupdkeys dirs |
|
Find the NIS+ service |
rootmaster# svcs \*nisplus\* |
|
Stop the NIS+ service |
rootmaster# svcadm disable -t /network/rpc/nisplus:default |
|
Add the -S 0 security option |
Edit the /lib/svc/method/nisplus file to add the -S 0 option |
|
Restart NIS+ daemon with default security |
# svcadm enable network/rpc/nisplus |
|
Perform a keylogin |
rootmaster# keylogin |
Where:
dirs are the directory objects you wish to update. (That is, the directory objects that are served by rootmaster.)
In the first step of the process outlined in Table 13–2, nisaddcred updates the cred table for the root master, updates /etc/.rootkey and performs a keylogin for the root master. At this point the directory objects served by the master have not been updated and their credential information is now out of synch with the root master. The subsequent steps described in Table 13–2 are necessary to successfully update all the objects.
Note –
Whenever you change a server's keys, you must also update the key information of all the clients in that domain as explained in Updating NIS+ Client Key Information.
Changing Root Keys From Another NIS+ Machine
To change the keys for the root master server from some other machine you must have the required NIS+ credentials and authorization to do so.
Table 13–3 Remotely Changing NIS+ Root Master Keys: Command Summary|
Tasks |
Commands |
|---|---|
|
Create the new DES credentials |
othermachine% nisaddcred -p principal-P nisprincipal des |
|
Update the directory objects. |
othermachine% nisupdkeysdirs |
|
Update /etc.rootkey. |
othermachine% keylogin -r |
|
Reinitialize othermachine as client |
othermachine% nisinit -cH |
Where:
-
principal is the root machine's Secure RPC netname. For example:unix.rootmaster@doc.com (no dot at the end).
-
nis-principal is the root machine's NIS+ principal name. For example, rootmaster.doc.com. (a dot at the end).
-
dirs are the directory objects you want to update (that is, the directory objects that are served by rootmaster).
When running nisupdkeys be sure to update all relevant directory objects at the same time. In other words, do them all with one command. Separate updates may result in an authentication error.
Note –
Whenever you change a server's keys, you must also update the key information of all the clients in that domain as explained in Updating NIS+ Client Key Information.
Changing the Keys of an NIS+ Root Replica From the Replica
To change the keys of a root replica from the replica, use these commands:
replica# nisaddcred des replica# nisupdkeys dirs |
Where:
dirs are the directory objects you wish to update, (that is, the directory objects that are served by replica).
When running nisupdkeys be sure to update all relevant directory objects at the same time. In other words, do them all with one command. Separate updates may result in an authentication error.
Note –
Whenever you change a server's keys, you must also update the key information of all the clients in that domain as explained in Updating NIS+ Client Key Information.
Changing the Keys of an NIS+ Non-Root Server
To change the keys of a non-root server (master or replica) from the server, use these commands:
subreplica# nisaddcred des subreplica# nisupdkeys parentdir dirs |
Where:
-
parentdir is the non-root server's parent directory (that is, the directory containing subreplica's NIS+ server).
-
dirs are the directory objects you want to update (that is, the directory objects that are served by subreplica).
When running nisupdkeys be sure to update all relevant directory objects at the same time. In other words, do them all with one command. Separate updates may result in an authentication error.
Note –
Whenever you change a server's keys, you must also update the key information of all the clients in that domain, as explained in Updating NIS+ Client Key Information.
Updating Public Keys for NIS+
The public keys of NIS+ servers are stored in several locations throughout the namespace. When new credential information is created for the server, a new key pair is generated and stored in the cred table. However, namespace directory objects still have copies of the server's old public key. The nisupdkeys command is used to update those directory object copies.
nisupdkeys Command
If a new keypair is generated because the old key pair has been compromised or the password used to encrypt the private key is forgotten, the nisupdkeys can be used to update the old public key in the directory objects.
-
Update the key of one particular server
-
Update the keys of all the servers that support an NIS+ directory object
-
Remove a server's public key from the directory object
-
Update a server's IP address, if that has changed
However, nisupdkeys cannot update the NIS_COLD_START files on the principal machines. To update their copies of a server's keys, NIS+ clients should run the nisclient command. Or, if the NIS+ cache manager is running and more than one server is available in the cold-start file, the principals can wait until the time-to-live expires on the directory object. When that happens, the cache manager automatically updates the cold-start file. The default time-to-live is 12 hours.
To use the nisupdkeys command, you must have modify rights to the NIS+ directory object.
Updating Public Keys Arguments and Examples in NIS+
The nisupdkeys command is located in /usr/lib/nis. The nisupdkeys command uses the following arguments (for a complete description of the nisupdkeys command and a full list of all its arguments, see the nisupdkeys man page).
Table 13–4 nisupdkeys Arguments|
Argument |
Effect |
|---|---|
|
(no argument) |
Updates all keys of servers for current domain. |
|
directoryname |
Updates the keys of the directory object for the named directory. |
|
-H servername |
Updates the keys of the named server for the current domain directory object. A fully qualified host name can be used to update the keys of servers in other domains. |
|
-s -H servername |
Updates the keys of all the directory objects served by the named server. |
|
-C |
Clears the keys. |
Table 13–5 gives an example of updating a public key.
Table 13–5 Updating an NIS+ Public Key: Command Examples|
Tasks |
Commands |
|---|---|
|
Update all keys of all servers of the current domain (doc.com). |
rootmaster# /usr/lib/nis/nisupdkeys Fetch Public key for server rootmaster.doc.com. netname='unix.rootmaster@doc.com' Updating rootmaster.doc.com.'s public key. Public key: public-key |
|
Update keys of all servers supporting the sales.doc.com domain directory object. |
salesmaster# nisupdkeys sales.doc.com (Screen notices not shown) |
|
Update keys for a server named master7 in all the directories that store them. |
rootmaster# nisupdkeys -H master7 |
|
Clear the keys stored by the sales.doc.com directory object. |
rootmaster# nisupdkeys -C sales.doc.com |
|
Clear the keys for the current domain directory object for the server named master7. |
rootmaster# nisupdkeys -C -H master7 |
Updating IP Addresses in NIS+
If you change a server's IP address, or add additional addresses, you need to run nisupdkeys to update NIS+ address information.
To update the IP addresses of one or more servers, use the nisupdkeys command -a option.
To update the IP addresses of servers of a given domain
rootmaster# nisupdkeys -a domain |
To update the IP address of a particular server
rootmaster# nisupdkeys -a -H server |
Updating NIS+ Client Key Information
Whenever you change any server's keys, you must update all of the clients as well. Remember, that all NIS+ servers are also NIS+ clients, so if you update the keys on one server, you must update key information on all other machines in the domain regardless of whether or not they are NIS+ servers or ordinary clients.
There are three ways to update client key information:
-
The easiest way to update an individual client's key information is by running the nisclient script on the client.
-
Another way to update an individual client's key information is by running the nisinit command on the client as described in Three Methods to Initialize an NIS+ Client.
-
You can globally update client key information for all the machines in a domain by shortening the Time To Live value of the domain's directory object as explained in Globally Updating NIS+ Client Key Information.
Globally Updating NIS+ Client Key Information
After changing a server's keys, you can globally update client key information for all the machines in a domain by:
 How to Update Client Key Information
How to Update Client Key Information
-
Use the nischttl command to reduce the Time To Live (TTL) value of the domain's directory object so that the value expires almost immediately.
For example, if you have changed the keys for a server in the sales.doc.com. domain, to reduce the directory's TTL value to one minute you would enter:
client% nischttl 60 sales.doc.com.
-
When the directory's TTL value expires, the cache manager expires the entry and then obtains the new, updated information for clients.
-
Once the directory object's TTL value has expired, reset the directory object's TTL to its default value.
For example, to reset the TTL value to 12 hours for the sales.doc.com. domain's directory object, you would enter:
client% nischttl 12h sales.doc.com.
See nischttl Command for more information on working with TTL values.
Chapter 14 Administering Enhanced NIS+ Security Credentials
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
Diffie-Hellman Extended Key
NIS+ offers increased security at the RPC(3N) layer beyond 192 bit Diffie-Hellman (RPC(3N) security flavor AUTH_DH) using the RPCSEC_GSS RPC(3N) security flavor. See the nisauthconf command for a list of which security mechanisms are available on the system. Along with more stringent cryptographic strength, these security mechanisms also provide integrity for each NIS+ transaction. That is, the data for each NIS+ transaction is verified that it has not been modified.
System administraters can take advantage of the more stringent security mechanisms either by running nisauthconf before the NIS+ server environment is constructed or after, using the guidelines below.
Note –
AUTH_DH was formerly referred to as AUTH_DES.
Transitioning NIS+ to a New Public Key-Based Security Mechanism
The more stringent security mechanisms of the public key cryptography family such as Diffie-Hellman 640 bit (dh640-0) will require new credentials for each principal to be added to the existing cred table. The procedure outlined below is for a system currently running with Diffie-Hellman 192 bit (RPC security flavor AUTH_DH) security that will be converted to running with Diffie-Hellman 640 bit (RPC security flavor RPCSEC_GSS) security. Although this transition document highlights the most likely case, the principles are the same for converting from any one security mechanism type of the public key cryptography family to another security mechanism of the public key cryptography family.
Note –
The following example assumes that $PATH includes /usr/lib/nis.
Configuring NIS+ Security Mechanisms
NIS+ security configuration is done with the nisauthconf command. nisauthconf takes a list of security mechanisms in order of preference. A security mechanism may use one or more authentication flavors specified in secure_rpc(3N). If des is the only specified mechanism, then NIS+ only uses AUTH_DH (formerly AUTH_DES) for authentication with other NIS+ clients and servers. Any other security mechanisms after des will be ignored by NIS+, except for nisaddcred.
nisauthconf [-v] [mechanism, ...] |
Where mechanism is a RPC security mechanism that is available on the system. See nisauthconf for the list of mechanisms available. If no mechanisms are specified, then a list of currently configured mechanisms is printed.
Creating New NIS+ Security Mechanism Credentials
Credential information for the new mechanism must be created for each NIS+ user and host principal. In order to do this, on one of the machines running NIS+, the nisauthconf command must be run to allow the creation of new credentials while the system continues to authenticate with the current mechanism. Also see Creating Credential Information for NIS+ Principals for details on credential creation basics.
New NIS+ Security Mechanism Credentials – Example
Converting des to dh640-0; the nisauthconf should be run as root and the nisaddcred should be run as any principal that has Create rights in the principal's home directory. The server is named server1 and the user principal is named morena. User morena has UID 11177.
client# nisauthconf des dh640-0
client% nisaddcred -P server1.doc.com. -p unix.server1@doc.com dh640-0
(screen notices not shown)
client% nisaddcred -P morena.doc.com. -p unix.11177@doc.com -ldummy-password dh640-0
(screen notices not shown)
|
Adding New Keys to NIS+ Directory Objects
Once the new credentials have been generated for all the servers, run nisupdkeys(1m) to add the new public keys to all the directory objects served by these servers. To use the nisupdkeys(1m) command, you must have modify rights to the NIS+ directory object. See Updating Public Keys for NIS+ for more details.
All servers that serve these NIS+ directories and all clients that access these directories must be running at least the Solaris 7 release.
Adding New Public Keys to NIS+ Directory Objects – Example
In this example, the directories that are being served by the servers with new public keys are doc.com, org_dir.doc.com., groups_dir.doc.com.. The update will be done as the master server principal. Before running the new mechanism, nisupdkeys needs to be configured with nisauthconf. In this example, the current authentication mechanism is des and the new mechanism is dh640-0.
masterserver# nisauthconf dh640-0 des masterserver# nisupdkeys doc.com. (screen notices not shown) masterserver# nisupdkeys org_dir.doc.com. (screen notices not shown) masterserver# nisupdkeys groups_dir.doc.com. (screen notices not shown) |
Configuring NIS+ Servers to Accept New Security Mechanism Credentials
On each server, configure NIS+ authentication so that it accepts both the old and new credentials. This will require running nisauthconf(1m) and keylogin and restarting keyserv(1m). The keylogin command stores the keys for each mechanism in the /etc/.rootkey. See Keylogin With NIS+ for basic keylogin details.
Configuring NIS+ Servers to Accept New Security Mechanism Credentials – Example
In this example, the current authentication mechanism is des and the new mechanism is dh640-0. Note the ordering is significant here; any mechanisms after the des entry will be ignored for client and server NIS+ authentication.
server# nisauthconf dh640-0 des server# keylogin -r (screen notices not shown) server# /etc/reboot |
Configuring NIS+ Machines to Use New Security Mechanism Credentials
Now that the servers can accept the new credentials, the machines can be converted to authenticate by using the new credentials. To do this, run nisauthconf and keylogin as root and reboot.
Configuring NIS+ Machines to Use New Security Mechanism Credentials – Examples
In this example, the new mechanism is dh640-0 but the system will also attempt authentication with des credentials if the dh640-0 ones are not available or do not succeed.
workstation# nisauthconf dh640-0 des workstation# keylogin -r (screen notices not shown) workstation# /etc/reboot |
In the next example, the new mechanism is dh640-0 and authentication will only be attempted with this mechanism. Before configuring any system to authenticate by using the new mechanism exclusively, the cached directory objects must be refreshed to include the keys for the new mechanism. This can be verified with nisshowcache. An alternative to waiting for the cached directory objects to time out and be refreshed is the following: stop the NIS+ service, then construct a new NIS_COLD_START by using nisinit, and then restart the NIS+ service.
Manually Refresh NIS+ Directory Objects – Example NETNAMER
To manually refresh directory objects, use the svcadm command. See the svcadm(1M) man page for more information.
# svcadm disable -t /network/rpc/nisplus:default # nisinit -cH masterserver # svcadm enable /network/rpc/nisplus:default |
The machine principal and all users of this machine must have dh640-0 credentials in the cred table before the system can be configured to authenticate exclusively with dh640-0.
workstation# nisauthconf dh640-0 workstation# keylogin -r (screen notices not shown) workstation# /etc/reboot |
Changing the Password Protecting New NIS+ Credentials
For each user given new credentials with the dummy passwd, they need to run chkey to convert to their login password. For more information, see Changing Keys for an NIS+ Principal.
Change Password Protecting New NIS+ Credentials – Example
Run chkey to convert to your login password:
# chkey -p (screen notices not shown) |
Configuring NIS+ Servers to Accept Only New Security Mechanism Credentials
When converting from a lower grade security mechanism to a higher one, the maximum security benefit is achieved by configuring the NIS+ servers to only accept credentials of the new higher grade security mechanism type. Do this only after the servers have been successfully configured to authenticate by using the old and the new mechanism.
Before configuring any system to authenticate by using the new mechanism exclusively, the cached directory objects must be refreshed to include the keys for the new mechanism and verified with nisshowcache.
Configuring NIS+ Servers to Accept Only New Security Mechanism Credentials – Example
Run nisauthconf(1m) on each NIS+ server and reboot. In this example, the NIS+ server will be configured to only accept authentication of dh640-0 credentials.
server# nisauthconf dh640-0 server# /etc/reboot |
Optionally, the directory objects can now be updated to remove the old public keys. This should be done from the master server and nisupdkeys(1m) should be run once for each directory served by the servers authenticating only with the new security mechanism. In this example, the directories to be updated are doc.com, org_dir.doc.com., and groups_dir.doc.com.
masterserver# nisupdkeys doc.com. (screen notices not shown) masterserver# nisupdkeys org_dir.doc.com. (screen notices not shown) masterserver# nisupdkeys groups_dir.doc.com. |
Removing Old Credentials From the NIS+ cred Table
If desired, the credentials of the old security mechanism can be removed from the cred table. You must have modify rights to the local domain's cred table. See Removing NIS+ Credential Information for more details.
Removing Old Credentials From the NIS+ cred Table – Example
In this example, the principal morena.doc.com will have her des credentials removed from the cred table.
master# nisaddcred -r morena.doc.com. dh192-0 |
Chapter 15 Administering NIS+ Access Rights
This chapter describes NIS+ access rights and how to administer them.
Tip –
Some NIS+ security tasks can be performed more easily with Solaris Management Console tools if you have them available.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
About NIS+ Access Rights
NIS+ access rights determine what operations NIS+ users can perform and what information they have access to. This chapter assumes that you have an adequate understanding of the NIS+ security system in general, and in particular of the role that access rights play in that system (see Chapter 11, NIS+ Security Overview for this information).
For a complete description of NIS+ access-related commands and their syntax and options, see the NIS+ man pages.
Introduction to NIS+ Authorization and Access Rights
See NIS+ Authorization and Access for a description of how authorization and access rights work with NIS+ credentials and authentication to provide security for the NIS+ namespace.
NIS+ Authorization Classes – Review
As described more fully in NIS+ Authorization Classes, NIS+ access rights are assigned on a class basis.
There are four different NIS+ classes:
-
Owner. The owner class is a single NIS+ principal. By default, an object's owner is the principal that created the object. However, an object's owner can transfer ownership to another principal who then becomes the new owner.
-
Group. The group class is a collection of one or more NIS+ principals. An NIS+ object can have only one NIS+ group.
-
World. The world class contains all NIS+ principals that are authenticated by NIS+ (in other words, everyone in the owner and group class, plus everyone else who presents a valid DES credential).
-
Nobody. The nobody class is composed of anyone who is not properly authenticated (in other words, anyone who does not present a valid DES credential).
NIS+ Access Rights – Review
As described more fully in NIS+ Access Rights, there are four types of NIS+ access rights:
-
Read. A principal with read rights to an object can view the contents of that object.
-
Modify. A principal with modify rights to an object can change the contents of that object.
-
Destroy. A principal with Destroy rights to an object can delete the object.
-
Create. A principal with create rights to a higher level object can create new objects within that level. In other words, if you have create rights to an NIS+ directory object, you can create new tables within that directory. If you have create rights to an NIS+ table, you can create new columns and entries within that table.
Keep in mind that these rights logically evolve down from directory to table to table column and entry levels. For example, to create a new table, you must have create rights for the NIS+ directory object where the table will be stored. When you create that table, you become its default owner. As owner, you can assign yourself create rights to the table which allows you to create new entries in the table. If you create new entries in a table, you become the default owner of those entries. As table owner, you can also grant table level create rights to others. For example, you can give your table's group class table level create rights. In that case, any member of the table's group can create new entries in the table. The individual member of the group who creates a new table entry becomes the default owner of that entry.
Concatenation of NIS+ Access Rights
Authorization classes are concatenated. In other words, the higher class usually belongs to the lower class and automatically gets the rights assigned to the lower class.
The algorithm works like this:
-
Owner class. An object's owner may, or may not, belong to the object's group. If the owner does belong to the group, then the owner gets whatever rights are assigned to the group. The object's owner automatically belongs to the world and nobody classes, so the owner automatically gets whatever rights that object assigns to those two classes.
-
Group class. Members of the object's group automatically belong to the world and nobody classes, so the group members automatically get whatever rights that object assigns to world and nobody.
-
World class. The world class automatically gets the same rights to an object that are given to the nobody class.
-
Nobody class. The nobody class only gets those rights an object specifically assigns to the nobody class.
The basic principle that governs this is that access rights override the absence of access rights. In other words, a higher class can have more rights than a lower class, but not fewer rights. (The one exception to this rule is that if the owner is not a member of the group, it is possible to give rights to the group class that the owner does not have.)
How NIS+ Access Rights Are Assigned and Changed
When you create an NIS+ object, NIS+ assigns that object a default set of access rights for the owner and group classes. By default, the owner is the NIS+ principal who creates the object. The default group is the group named in the NIS_GROUP environment variable.
Specifying Different Default Rights in NIS+
NIS+ provides two different ways to change the default rights that are automatically assigned to an NIS+ object when it is created.
-
The NIS_DEFAULTS environment variable. NIS_DEFAULTS stores a set of security-related default values, one of which is access rights. These default access rights are the ones automatically assigned to an object when it is created. (See Displaying NIS+ Defaults With nisdefaults for details.)
If the value of the NIS_DEFAULTS environment variable is changed, objects created after the change are assigned the new values. However, previously created objects are not affected.
-
The -D option, which is available with several NIS+ commands. When you use the -D option as part of the command to create an NIS+ object, it overrides the default rights specified by the NIS_DEFAULTS environment variable and allows you to explicitly specify an initial set of rights for that object. (See Specifying Non-Default Security Values at Creation Time in NIS+ for details.)
Changing Access Rights to an Existing NIS+ Object
When an NIS+ object is created, it comes into existence with a default set of access rights (from either the NIS_DEFAULTS environment variable or as specified with the -D option). These default rights can be changed with the
NIS+ Table, Column, and Entry Security
NIS+ tables allow you to specify access rights on the table three ways:
-
You can specify access rights to the table as a whole.
-
You can specify access rights to each entry (row) by itself.
-
You can specify access rights to each table column individually.
A field is the intersection between a column and an entry (row). All data values are entered in fields.
These column-level and entry-level access rights allow you to specify additional access to individual rows and columns that override table level restrictions, but column and entry level rights cannot be more restrictive than the table as a whole:
-
Table. The table level is the base level. Access rights assigned at the table level apply to every piece of data in the table unless specifically modified by a column or entry exception. Thus, the table level rights should be the most restrictive.
Note –Remember that authorization classes concatenate. A higher class gets the rights assigned to lower classes. See Concatenation of NIS+ Access Rights.
-
Column. Column-level rights allow you to grant additional access rights on a column-by-column basis. For example, suppose the table level granted no access rights whatsoever to the world and nobody classes. In such a case, no one in those two classes could read, modify, create, or destroy any data in the table. You could use column-level rights to override that table level restriction and permit members of the world class the right to view data in a particular column.
On the other hand, if the table level grants table-wide read rights to the owner and group classes, you cannot use column-level rights to prevent the group class from having read rights to that column.
-
Entry (row). entry level rights allow you to grant additional access rights on a row-by-row basis. For example, this allows you to permit individual users to change entries that apply to them, but not entries that apply to anyone else.
Keep in mind that an entry's group does not have to be the same as the table's group. Tables and entries can have different groups. This means that you can permit members of a particular group to work with one set of entries while preventing them from affecting entries belonging to other groups.
NIS+ Table, Column, Entry Example
Column- or entry level access rights can provide additional access in two ways: by extending the rights to additional principals or by providing additional rights to the same principals. Of course, both ways can be combined. Following are some examples.
Assume a table object granted read rights to the table's owner.
Table 15–1 NIS+ Table, Column, Entry Example 1|
|
Nobody |
Owner |
Group |
World |
|---|---|---|---|---|
|
Table Access Rights: |
---- |
r--- |
---- |
---- |
This means that the table's owner could read the contents of the entire table but no one else could read anything. You could then specify that Entry-2 of the table grant read rights to the group class.
Table 15–2 NIS+ Table, Column, Entry Example 2|
|
Nobody |
Owner |
Group |
World |
|---|---|---|---|---|
|
Table Access Rights: |
---- |
r--- |
---- |
---- |
|
Entry-2 Access Rights: |
---- |
---- |
r--- |
---- |
Although only the owner could read all the contents of the table, any member of the table's group could read the contents of that particular entry. Now, assume that a particular column granted read rights to the world class.
Table 15–3 NIS+ Table, Column, Entry Example 3|
|
Nobody |
Owner |
Group |
World |
|---|---|---|---|---|
|
Table Access Rights: |
---- |
r--- |
---- |
---- |
|
Entry-2 Access Rights: |
---- |
---- |
r--- |
---- |
|
Column-1 Access Rights: |
---- |
---- |
---- |
r--- |
Members of the world class could now read that column for all entries in the table. Members of the group class could read everything in Column-1 (because members of the group class are also members of the world class) and also all columns of Entry-2. Neither the world nor the group classes could read any cells marked *NP* (for Nor Permitted).
Table 15–4 NIS+ Table, Column, Entry Example 4|
|
Col 1 |
Col 2 |
Col 2 |
|---|---|---|---|
|
Entry-1 |
contents |
*NP* |
*NP* |
|
Entry-2 |
contents |
contents |
contents |
|
Entry-3 |
contents |
*NP* |
*NP* |
|
Entry-4 |
contents |
*NP* |
*NP* |
|
Entry-5 |
contents |
*NP* |
*NP* |
NIS+ Rights at Different Levels
This section describes how the four different access rights (read, create, modify, and destroy) work at the four different access levels (directory, table, column, and entry).
The objects that these various rights and levels act on are summarized in Table 15–5.
Table 15–5 NIS+ Access Rights and Levels and the Objects They Act Upon|
|
Directory |
Table |
Column |
Entry |
|---|---|---|---|---|
|
Read |
List directory contents |
View table contents |
View column contents |
View entry (row) contents |
|
Create |
Create new directory or table objects |
Add new entries (rows) |
Enter new data values in a column |
Enter new data values in an entry (row) |
|
Modify |
Move objects and change object names |
Change data values anywhere in table |
Change data values in a column |
Change data values in an entry (row) |
|
Destroy |
Delete directory objects such as tables |
Delete entries (rows) |
Delete data values in a column |
Delete data values in an entry (row) |
NIS+ Read Rights
-
Directory. If you have read rights to a directory, you can list the contents of the directory.
-
Table. If you have read rights to a table, you can view all the data in that table.
-
Column. If you have read rights to a column, you can view all the data in that column.
-
Entry. If you have read rights to an entry, you can view all the data in that entry.
NIS+ Create Rights
-
Directory. If you have create rights at the directory level, you can create new objects in the directory such as new tables.
-
Table. If you have create rights at the table level, you can create new entries. (You cannot add new columns to an existing table regardless of what rights you have.)
-
Column. If you have create rights to a column, you can enter new data values in the fields of that column. You cannot create new columns.
-
Entry. If you have create rights to an entry, you can enter new data values in the fields of that row. (Entry level create rights do not permit you to create new rows.)
NIS+ Modify Rights
-
Directory. If you have modify rights at the directory level, you can move or rename directory objects.
-
Table. If you have modify rights at the table level, you can change any data values in the table. You can create (add) new rows, but you cannot create new columns. If an existing field is blank, you can enter new data in it.
-
Column. If you have modify rights to a column, you can change the data values in the fields of that column.
-
Entry. If you have modify rights to an entry, you can change the data values in the fields of that row.
NIS+ Destroy Rights
-
Directory. If you have destroy rights at the directory level, you can destroy existing objects in the directory such as tables.
-
Table. If you have destroy rights at the table level, you can destroy existing entries (rows) in the table but not columns. You cannot destroy existing columns in a table: you can only destroy entries.
-
Column. If you have destroy rights to a column, you can destroy existing data values in the fields of that column.
-
Entry. If you have destroy rights to an entry, you can destroy existing data values in the fields of that row.
Where NIS+ Access Rights Are Stored
An object's access rights are specified and stored as part of the object's definition. This information is not stored in an NIS+ table.
Viewing an NIS+ Object's Access Rights
The access rights can be viewed by using the niscat command:
niscat -o objectname |
Where objectname is the name of the object whose access rights you want to view.
This command returns the following information about an NIS+ object:
-
Owner. The single NIS+ principal who has ownership rights. This is usually the person who created the object, but it could be someone to whom the original owner transferred ownership rights.
-
Group. The object's NIS+ group.
-
Nobody class access rights. The access rights granted to everyone, whether they are authenticated (have a valid DES credential) or not.
-
Owner class access rights. The access rights granted to the object's owner.
-
Group class access rights. The access rights granted to the principals in the object's group.
-
World class access rights. The access rights granted to all authenticated NIS+ principals.
Access rights for the four authorization classes are displayed as a list of 16 characters, like this:
r---rmcdr---r--- |
Each character represents a type of access right:
-
r represents read rights.
-
m represents modify rights.
-
d represents destroy rights.
-
c represents create rights.
-
- represents no access rights.
The first four characters represent the access rights granted to nobody, the next four to the owner, the next four to the group, and the last four to the world.
Figure 15–1 NIS+ Access Rights Display
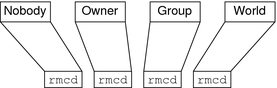
Note –
Unlike UNIX file systems, the first set of rights is for nobody, not for the owner.
Default NIS+ Access Rights
When you create an object, NIS+ assigns the object a default owner and group, and a default set of access rights for all four classes. The default owner is the NIS+ principal who creates the object. The default group is the group named in the NIS_GROUP environment variable. Table 15–6, shows the default access rights.
Table 15–6 NIS+ Default Access Rights|
Nobody |
Owner |
Group |
World |
|---|---|---|---|
|
- |
read |
read |
read |
|
- |
modify |
- |
- |
|
- |
create |
- |
- |
|
- |
destroy |
- |
- |
If you have the NIS_DEFAULTS environment variable set, the values specified in NIS_DEFAULTS will determine the defaults that are applied to new objects. When you create an object from the command line, you can use the -D flag to specify values other than the default values.
How an NIS+ Server Grants Access Rights to Tables
This section discusses how a server grants access to tables objects, entries, and columns during each type of operation: read, modify, destroy, and create.
Note –
At security level 0, a server enforces no NIS+ access rights and all clients are granted full access rights to the table object. Security level 0 is only for administrator setup and testing purposes. Do not use level 0 in any environment where ordinary users are performing their normal work.
The four factors that a server must consider when deciding whether to grant access are:
-
The type of operation requested by the principal
-
The table, entry, or column the principal is trying to access
-
The authorization class the principal belongs to for that particular object
-
The access rights that the table, entry, or column has assigned to the principal's authorization class
After authenticating the principal making the request by making sure the principal has a valid DES credential, an NIS+ server determines the type of operation and the object of the request.
-
Directory. If the object is a directory or group, the server examines the object's definition to see what rights are granted to the four authorization classes, determines which class the principal belongs to, and then grants or denies the request based on the principal's class and the rights assigned to that class.
-
Table. If the object is a table, the server examines the table's definition to see what table level rights are granted to the four authorization classes, and determines which class the principal belongs to. If the class to which the principal belongs does not have table level rights to perform the requested operation, the server then determines which row or column the operation concerns and determines if there are corresponding row-level or column-level access rights permitting the principal to perform the requested operation.
Specifying NIS+ Access Rights in Commands
This section assume an NIS+ environment running at security level 2 (the default level).
This section describes how to specify access rights, as well as owner, group owner, and object, when using any of the commands described in this chapter.
NIS+ Syntax for Access Rights
This subsection describes the access rights syntax used with the various NIS+ commands that deal with authorization and access rights.
NIS+ Class, Operator, and Rights Syntax
Access rights, whether specified in an environment variable or a command, are identified with three types of arguments: class, operator, and right.
-
Class. Class refers to the type of NIS+ principal (authorization class) to which the rights will apply.
Class
Description
n
Nobody: all unauthenticated requests
o
The owner of the object or table entry
g
The group owner of the object or table entry
w
World: all authenticated principals
a
All: shorthand for owner, group, and world (this is the default)
-
Operator. The operator indicates the kind of operation that will be performed with the rights.
Operator
Description
+
Adds the access rights specified by right
-
Revokes the access rights specified by right
=
Explicitly changes the access rights specified by right; in other words, revokes all existing rights and replaces them with the new access rights.
-
Rights. The rights are the access rights themselves. The accepted values for each are listed below.
Right
Description
r
Reads the object definition or table entry
m
Modifies the object definition or table entry
c
Creates a table entry or column
d
Destroys a table entry or column
You can combine operations on a single command line by separating each operation from the next with a comma (,).
Table 15–7 NIS+ Class, Operator, and Rights Syntax – Examples|
Operations |
Syntax |
|---|---|
|
Add read access rights to the owner class |
o+r |
|
Change owner. group, and world classes' access rights to modify only from whatever they were before |
a=m |
|
Add read and modify rights to the world and nobody classes |
wn+m |
|
Remove all four rights from the group, world, and nobody classes |
gwn-rmcd |
|
Add create and destroy rights to the owner class and add read and modify rights to the world and nobody classes |
o+cd,wn+rm |
NIS+ Syntax for Owner and Group
-
Owner. To specify an owner, use an NIS+ principal name.
-
Group. To specify an NIS+ group, use an NIS+ group name with the domain name appended.
Remember that principal names are fully qualified (principalname.domainname).
For owner
principalname |
For group
groupname.domainname |
NIS+ Syntax for Objects and Table Entries
Objects and table entries use different syntaxes.
-
Objects use simple object names.
-
Table entries use indexed names.
For objects
objectname |
For table entries
columnname=value],tablename |
Note –
In this case, the brackets are part of the syntax.
Indexed names can specify more than one column-value pair. If so, the operation applies only to the entries that match all the column-value pairs. The more column-value pairs you provide, the more stringent the search, as in the following.
Table 15–8 NIS+ Object and Table Entry – Examples|
Type |
Example |
|---|---|
|
Object |
hosts.org_dir.sales.doc.com. |
|
Table entry |
`[uid=33555],passwd.org_dir.Eng.doc.com.' |
|
Two-value table entry |
`[name=sales,gid=2],group.org_dir.doc.com.' |
Columns use a special version of indexed names. Because you can only work on columns with the nistbladm command, see Using the nistbladm Command With NIS+ Tables for more information.
Displaying NIS+ Defaults With nisdefaults
The nisdefaults command displays the seven default values currently active in the namespace. These default values are either
-
Preset values supplied by the NIS+ software
-
The defaults specified in the NIS_DEFAULTS environment variable (if you have NIS_DEFAULTS values set)
Any object that you create on this machine will automatically acquire these default values unless you override them with the -D option of the command you are using to create the object.
Table 15–9 NIS+ Default Values and nisdefaults Options|
Default |
Option |
From |
Description |
|---|---|---|---|
|
Domain |
-d |
/etc/defaultdomain |
Displays the home domain of the machine from which the command was entered. |
|
Group |
-g |
NIS_GROUP environment variable |
Displays the group that would be assigned to the next object created from this shell. |
|
Host |
-h |
uname -n |
Displays the machine's host name. |
|
Principal |
-p |
gethostbyname() |
Displays the fully qualified user name or host name of the NIS+ principal who entered the nisdefaults command. |
|
Access Rights |
-r |
NIS_DEFAULTS environment variable |
Displays the access rights that will be assigned to the next object or entry created from this shell. Format: ----rmcdr---r--- |
|
Search path |
-s |
NIS_PATH environment variable |
Displays the syntax of the search path, which indicate the domains that NIS+ will search through when looking for information. Displays the value of the NIS_PATH environment variable if it is set. |
|
Time-to-live |
-t |
NIS_DEFAULTS environment variable |
Displays the time-to-live that will be assigned to the next object created from this shell. The default is 12 hours. |
|
All (terse) |
-a |
|
Displays all seven defaults in terse format. |
|
Verbose |
-v |
Display specified values in verbose mode. |
|
You can use these options to display all default values or any subset of them:
-
To display all values in verbose format, type the nisdefaults command without arguments.
master% nisdefaults Principal Name : topadmin.doc.com. Domain Name : doc.com. Host Name : rootmaster.doc.com. Group Name : salesboss Access Rights : ----rmcdr---r--- Time to live : 12:00:00:00:00 Search Path : doc.com.
-
To display all values in terse format, add the -a option.
-
To display a subset of the values, use the appropriate options. The values are displayed in terse mode. For example, to display the rights and search path defaults in terse mode, type the following.
rootmaster% nisdefaults -rs ----rmcdr---r--- doc.com.
-
To display a subset of the values in verbose mode, add the -v flag.
Setting NIS+ Default Security Values
This section describes how to perform tasks related to the nisdefaults command, the NIS_DEFAULTS environment variable, and the -D option.
The NIS_DEFAULTS environment variable specifies the following default values:
-
Owner
-
Group
-
Access rights
-
Time-to-live
The values that you set in the NIS_DEFAULTS environment variable are the default values applied to all NIS+ objects that you create using that shell (unless overridden by using the -D option with the command that creates the object).
You can specify the default values (owner, group, access rights, and time-to-live) specified with the NIS_DEFAULTS environment variable. Once you set the value of NIS_DEFAULTS, every object you create from that shell will acquire those defaults, unless you override them by using the -D option when you invoke a command.
Displaying the Value of the NIS+ NIS_DEFAULTS Variable
You can check the setting of an environment variable by using the echo command, as shown below:
client% echo $NIS_DEFAULTS owner=butler:group=gamblers:access=o+rmcd |
You can also display a general list of the NIS+ defaults active in the namespace by using the nisdefaults command as described in Displaying NIS+ Defaults With nisdefaults.
Changing NIS+ Defaults
You can change the default access rights, owner, and group, by changing the value of the NIS_DEFAULTS environment variable.
Use the environment command that is appropriate for your shell (setenv for C-shell or $NIS_DEFAULTS=, export for Bourne and Korn shells) with the following arguments:
-
access=right, where right are the access rights using the formats described in Specifying NIS+ Access Rights in Commands.
-
owner=name, where name is the user name of the owner.
-
group=group, where group is the name of the default group.
You can combine two or more arguments into one line separated by colons:
-owner=principal-name:-group=group-name |
Table 15–10 shows some examples.
Table 15–10 Changing NIS+ Defaults – Examples|
Tasks |
Examples |
|---|---|
|
This command grants owner read access as the default access right. |
client% setenv NIS_DEFAULTS access=o+r |
|
This command sets the default owner to be the user abe whose home domain is doc.com. |
client% setenv NIS_DEFAULTS owner=abe.doc.com. |
|
This command combines the first two examples on one code line. |
client% setenv NIS_DEFAULTS access=o+r:owner=abe.doc.com. |
All objects and entries created from the shell in which you changed the defaults will have the new values you specified. You cannot specify default settings for a table column or entry; the columns and entries simply inherit the defaults of the table.
Resetting the Value of NIS_DEFAULTS
You can reset the NIS_DEFAULTS variable to
its original values, by typing the name of the variable without arguments,
using the format appropriate to your shell:
For C shell
client# unsetenv NIS_DEFAULTS |
For Bourne or Korn shell
client$ NIS_DEFAULTS=; export NIS_DEFAULTS |
Specifying Non-Default Security Values at Creation Time in NIS+
You can specify different (that is, nondefault) access rights, owner, and group, any time that you create an NIS+ object or table entry with any of the following NIS+ commands:
To specify security values other than the default values, insert the -D option into the syntax of those commands, as described in Specifying NIS+ Access Rights in Commands.
As when setting defaults, you can combine two or more arguments into one line. Remember that column and entry's owner and group are always the same as the table, so you cannot override them.
For example, to use the nismkdir command to create a sales.doc.com directory and override the default access right by granting the owner only read rights you would type:
client% nismkdir -D access=o+r sales.doc.com |
Changing NIS+ Object and Entry Access Rights
The nischmod command operates on the access rights of an NIS+ object or table entry. It does not operate on the access rights of a table column; for columns, use the nistbladm command with the -D option. For all nischmod operations, you must already have modify rights to the object or entry.
Using nischmod to Add NIS+ Rights
To add rights for an object or entry use:
For object
nischmod class+right object-name |
For table entry
nischmod class+right [column-name=value],table-name |
For example, to add read and modify rights to the group of the sales.doc.com. directory object you would type:
client% nischmod g+rm sales.doc.com. |
For example to add read and modify rights to group for the name=abe entry in the hosts.org_dir.doc.com. table you would type:
client% nischmod g+rm '[name=abe],hosts.org_dir.doc.com.' |
Using nischmod to Remove NIS+ Rights
To remove rights for an object or entry use:
For object
nischmod class-right object-name |
For entry
nischmod class-right [column-name=value],table-name |
For example, to remove create and destroy rights from the group of the sales.doc.com. directory object you would type:
client% nischmod g-cd sales.doc.com. |
For example to remove destroy rights from group for the name=abe entry in the hosts.org_dir.doc.com. table, you would type:
client% nischmod g-d '[name=abe],hosts.org_dir.doc.com.' |
Specifying Column Access Rights in NIS+
The nistbladm command performs a variety of operations on NIS+ tables. Most of these tasks are described in Using the nistbladm Command With NIS+ Tables.
However, two of its options, -c and -u, enable you to perform some security-related tasks:
-
The -c option. The -c option allows you to specify initial column access rights when creating a table with the nistbladm command.
-
The -u option. The -u option allows you to change column access rights with the nistbladm command.
Setting Column Rights When Creating an NIS+ Table
When a table is created, its columns are assigned the same rights as the table object. These table level, rights are derived from the NIS_DEFAULTS environment variable, or are specified as part of the command that creates the table. You can also use the nistbladm -c option to specify initial column access rights when creating a table with nistbladm. To use this option you must have create rights to the directory in which you will be creating the table. To set column rights when creating a table use:
nistbladm -c type `columname=[flags] [,access]... tablename' |
Where:
-
type is a character string identifying the kind of table. A table's type can be anything you want it to be.
-
columnname is the name of the column.
-
flags is the type of column. Valid flags are:
-
S for searchable
-
I for case insensitive
-
C for encrypted
-
B for binary data
-
X for XDR encoded data
-
-
access is the access rights for this column that you specify using the syntax described in Specifying NIS+ Access Rights in Commands.
-
... indicates that you can specify multiple columns each of the own type and with their own set of rights.
-
tablename is the fully qualified name of the table you are creating.
To assign a column its own set of rights at table creation time, append access rights to each column's equal sign after the column type and a comma. Separate the columns with a space:
column=type,rights column=type,rights column=type,rights |
The example below creates a table named depts in the doc.com directory, of type div, with three columns (Name, Site, and Manager), and adds modify rights for the group to the second and third columns:
rootmaster% nistbladm -c div Name=S Site=S,g+m Manager=S,g+m depts.doc.com. |
For more information about the nistbladm and the -c option, see Chapter 19, Administering NIS+ Tables.
Adding Rights to an Existing NIS+ Table Column
The nistbladm -u option allows you to add additional column access rights to an existing table column with the nistbladm command. To use this option you must have modify rights to the table column. To add additional column rights use:
nistbladm -u [column=access,...],tablename |
Where:
-
column is the name of the column.
-
access is the access rights for this column that you specify using the syntax described in Specifying NIS+ Access Rights in Commands.
-
... indicates that you can specify rights for multiple columns.
-
tablename is the fully qualified name of the table you are creating.
Use one column=access pair for each column whose rights you want to update. To update multiple columns, separate them with commas and enclose the entire set with square brackets:
[column=access, column=access, column=access] |
The full syntax of this option is described in Chapter 2, NIS+: An Introduction.
The example below adds read and modify rights to the group for the name and addr columns in the hosts.org_dir.doc.com. table.
client% nistbladm -u `[name=g+rm,addr=g+rm],hosts.org_dir..doc.com.' |
Removing Rights to an NIS+ Table Column
To remove access rights to a column in an NIS+ table, you use the -u option as described above in Adding Rights to an Existing NIS+ Table Column except that you subtract rights with a minus sign (rather than adding them with a plus sign).
The example below removes group's read and modify rights to the hostname column in the hosts.org_dir.doc.com. table.
client% nistbladm -u 'name=g-rm,hosts.org_dir.doc.com.' |
Changing Ownership of NIS+ Objects and Entries
The nischown command changes the owner of one or more objects or entries. To use it, you must have modify rights to the object or entry. The nischown command cannot change the owner of a column, since a table's columns belong the table's owner. To change a column's owner, you must change the table's owner.
Changing an NIS+ Object Owner With nischown
To change an object's owner, use the following syntax:
nischown new-owner object |
Where:
-
new-owner is the fully qualified user ID of the object's new owner.
-
object is the fully qualified name of the object.
Be sure to append the domain name to both the object name and new owner name.
The example below changes the owner of the hosts table in the doc.com. domain to the user named lincoln whose home domain is doc.com.:
client% nischown lincoln.doc.com. hosts.org_dir.doc.com. |
Changing an NIS+ Table Entry Owner With nischown
The syntax for changing a table entry's owner uses an indexed entry to identify the entry, as shown in the following, where:
-
new-owner is the fully qualified user ID of the object's new owner.
-
column is the name of the column whose value will identify the particular entry (row) whose owner is to be changed.
-
value is the data value that identified the particular entry (row) whose owner is to be changed.
-
... indicates that you can specify ownership changes for multiple entries.
-
tablename is the fully qualified name of the tables containing the entry whose owner is to be changed.
Be sure to append the domain name to both the new owner name and the table name.
The example below changes the owner of an entry in the hosts table of the doc.com. domain to takeda whose home domain is doc.com. The entry is the one whose value in the name column is virginia.
client% nischown takeda.doc.com. '[name=virginia],hosts.org_dir.doc.com.' |
Changing an NIS+ Object or Entry's Group
The nischgrp command changes the group of one or more objects or table entries. To use it, you must have modify rights to the object or entry. The nischgrp command cannot change the group of a column, since the group assigned to a table's columns is the same as the group assigned to the table. To change a column's group owner, you must change the table's group owner.
Changing an NIS+ Object's Group With nischgrp
To change an object's group, use the following syntax:
nischgrp group object |
Where:
-
group is the fully qualified name of the object's new group.
-
object is the fully qualified name of the object.
Be sure to append the domain name to both the object name and new group name.
The example below changes the group of the hosts table in the doc.com. domain to admins.doc.com.:
client% nischgrp admins.doc.com. hosts.org_dir.doc.com. |
Changing an NIS+ Table Entry's Group With nischgrp
The syntax for changing a table entry's group uses an indexed entry to identify the entry, as shown below (this syntax is fully described in NIS+ Syntax for Objects and Table Entries).
nischgrp new-group [column=value,...],tablename |
Where:
-
new-group is the fully qualified name of the object's new group.
-
column is the name of the column whose value will identify the particular entry (row) whose group is to be changed.
-
value is the data value that identified the particular entry (row) whose group is to be changed.
-
tablename is the fully qualified name of the tables containing the entry whose group is to be changed.
-
... indicates that you can specify group changes for multiple entries.
Be sure to append the domain name to both the new group name and the table name.
The example below changes the group of an entry in the hosts table of the doc.com. domain to sales.doc.com. The entry is the one whose value in the host name column is virginia.
client% nischgrp sales.doc.com. '[name=virginia],hosts.org_dir.doc.com.' |
Chapter 16 Administering NIS+ Passwords
This chapter describes how to use the passwd command from the point of view of an ordinary user (NIS+ principal) and how an NIS+ administrator manages the password system.
Tip –
Some NIS+ security tasks can be performed more easily with Solaris Management Console tools if you have them available.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
Using Passwords in NIS+
When logging in to a machine, users must enter both a user name (also known as a login ID) and a password. Although login IDs are publicly known, passwords must be kept secret by their owners.
Logging In to an NIS+ Domain
Logging in to a system is a two-step process.
 How to Use Passwords
How to Use Passwords
-
Type your login ID at the Login: prompt.
-
Type your password at the Password: prompt.
(To maintain password secrecy, your password is not displayed on your screen when you type it.)
If your login is successful you will see your system's message of the day (if any) and then your command-line prompt, windowing system, or normal application.
Login incorrect Message
The Login incorrect message indicates that:
-
You have entered the wrong login ID or the wrong password. This is the most common cause of the Login incorrect message. Check your spelling and repeat the process. Note that most systems limit to five the number of unsuccessful login tries you can make:
-
If you exceed a number of tries limit, you will get a Too many failures - try later message and not be allowed to try again until a designated time span has passed.
-
If you fail to successfully log in within a specified amount of time you will receive a Too many tries; try again later message, and not be allowed to try again until a designated time span has passed.
-
-
Another possible cause of the Login incorrect message is that an administrator has locked your password and you cannot use it until it is unlocked. If you are sure that you are entering your login ID and password correctly, and you still get a Login incorrect message, contact your system administrator.
-
Another possible cause of the Login incorrect message is that an administrator has expired your password privileges and you cannot use your password until your privileges are restored. If you are sure that you are entering your login ID and password correctly, and you still get a Login incorrect message, contact your system administrator.
Password will expire Message
If you receive a Your password will expire in N days message (where N is a number of days), or a Your password will expire within 24 hours message, it means that your password will reach its age limit and expire in that number of days (or hours).
In essence, this message is telling you to change your password now. (See Changing Your NIS+ Password.)
Permission denied Message at Login
After entering your login ID and password, you may get a Permission denied message and be returned to the login: prompt. This means that your login attempt has failed because an administrator has either locked your password, or terminated your account, or your password privileges have expired. In these situations you cannot log in until an administrator unlocks your password or reactivates your account or privileges. Consult your system administrator.
Changing Your NIS+ Password
To maintain security, you should change your password regularly. (See Choosing a Password for password requirements and criteria.)
Note –
The passwd command now performs all functions previously performed by nispasswd. For operations specific to an NIS+ name space, use passwd -r nisplus.
Changing your password is a four-step process:
 How to Change Your NIS+ Password
How to Change Your NIS+ Password
-
Run the passwd command at a system prompt.
-
Type your old password at the Enter login password (or similar) prompt.
Your keystrokes are not shown on your screen.
-
If you receive a Sorry: less than N days since the last change message, it means that your old password has not been in use long enough and you will not be allowed to change it at this time. You are returned to your system prompt. Consult your system administrator to find out the minimum number of days a password must be in use before it can be changed.
-
If you receive a You may not change this password message, it means that your network administrator has blocked any change.
-
-
Type your new password at the Enter new password prompt.
Your keystrokes are not shown on your screen.
At this point the system checks to make sure that your new password meets the requirements:
-
If it does meet the requirements, you are asked to enter it again.
-
If your new password does not meet the system requirements, a message is displayed informing you of the problem. You must then enter a new password that does meet the requirements.
See Password Requirements for the requirements a password must meet.
-
-
Type your new password again at the Re-enter new password prompt.
Your keystrokes are not shown on your screen.
If your second entry of the new password is not identical to your first entry, you are prompted to repeat the process.
Note –When changing root's password, you must always run chkey -p immediately after changing the password. (See Changing NIS+ Root Keys From Root and Changing Root Keys From Another NIS+ Machine for information on using chkey -p to change root's keys.) Failure to run chkey -p after changing root's password will result in root being unable to properly log in.
If you receive a Your password has expired message it means that your password has reached its age limit and expired. In other words, the password has been in use for too long and you must choose a new password at this time. (See Choosing a Password, for criteria that a new password must meet.)
In this case, choosing a new password is a three-step process:
-
Type your old password at the Enter login password (or similar) prompt.
Your keystrokes are not shown on your screen.
-
Type your new password at the Enter new password prompt.
Your keystrokes are not shown on your screen.
-
Type your new password again at the Re-enter new password prompt.
Your keystrokes are not shown on your screen.
-
NIS+ Password Change Failures
Some systems limit either the number of failed attempts you can make in changing your password or the total amount of time you can take to make a successful change. (These limits are implemented to prevent someone else from changing your password by guessing your current password.)
If you (or someone posing as you) fails to successfully log in or change your password within the specified number of tries or time limit, you will get a Too many failures - try later or Too many tries: try again later message. You will not be allowed to make any more attempts until a certain amount of time has passed. (That amount of time is set by your administrator.)
Choosing a Password
Many breaches of computer security involve guessing another user's password. While the passwd command enforces some criteria for making sure the password is hard to guess, a clever person can sometimes figure out a password just by knowing something about the user. Thus, a good password is one that is easy for you to remember but hard for someone else to guess. A bad password is one that is so hard for you to remember that you have to write it down (which you are not supposed to do), or that is easy for someone who knows about you to guess.
Password Requirements
A password must meet the following requirements:
-
Length. By default, a password must have at least six characters. Only the first eight characters are significant. (In other words, you can have a password that is longer than eight characters, but the system only checks the first eight.) Because the minimum length of a password can be changed by a system administrator, it may be different on your system.
-
Characters. A password must contain at least two letters (either uppercase or lowercase) and at least one numeral or symbol such as @,#,%. For example, you can use dog#food or dog2food as a password, but you cannot use dogfood.
-
Not your login ID. A password cannot be the same as your login ID, nor can it be a rearrangement of the letters and characters of your login ID. (For the purpose of this criteria, upper and lower case letters are considered to be the same.) For example, if your login ID is Claire2 you cannot have e2clair as your password.
-
Different from old password. Your new password must differ from your old one by at least three characters. (For the purpose of this criterion, uppercase and lowercase letters are considered to be the same.) For example, if your current password is Dog#fooD you can change it to dog#Meat but you cannot change it to daT#Food.
Bad Choices for Passwords
Bad choices for passwords include:
-
Any password based on your name
-
Names of family members or pets
-
Car license numbers
-
Telephone numbers
-
Social Security numbers
-
Employee numbers
-
Names related to a hobby or interest
-
Seasonal themes, such as Santa in December
-
Any word that is in a standard dictionary
Good Choices for Passwords
Good choices for passwords include:
-
Phrases plus numbers or symbols (beam#meup)
-
Nonsense words made up of the first letters of every word in a phrase plus a number or symbol (swotrb7 for SomeWhere Over The RainBow)
-
Words with numbers, or symbols substituted for letters (sn00py for snoopy)
Administering NIS+ Passwords
This section describes how to administer passwords in an NIS+ namespace. This section assumes that you have an adequate understanding of the NIS+ security system in general, and in particular of the role that login passwords play in that system (see Chapter 11, NIS+ Security Overview, for this information).
Note –
The passwd command now performs all functions previously performed by nispasswd. For operations specific to an NIS+ namespace, use passwd -r nisplus.
nsswitch.conf File Requirements for Passwords
In order to properly implement the passwd command and password aging on your network, the passwd entry of the nsswitch.conf file on every machine must be correct. This entry determines where the passwd command will go for password information and where it will update password information.
Only five passwd configurations are permitted:
-
passwd: files
-
passwd: files nis
-
passwd: files nisplus
-
passwd: compat
-
passwd: compat passwd_compat: nisplus
All of the nsswitch.conf files on all of your network's machines must use one of the passwd configurations shown above. If you configure the passwd entry in any other way, users may not be able to log in.
nispasswd Command
All functions previously performed by the nispasswd command are now performed by the passwd command. When issuing commands from the command line, you should use passwd, not nispasswd.
(The nispasswd command is still retained with all of its functionality for the purpose of backward compatibility.)
yppasswd Command
All functions previously performed by the yppasswd command are now performed by the passwd command. When issuing commands from the command line, you should use passwd, not yppasswd.
(The yppasswd is still retained with all of its functionality for the purpose of backward compatibility.)
passwd Command
The passwd command performs various operations regarding passwords. The passwd command replaces the nispasswd command. You should use the passwd command for all activities which used to be performed with the nispasswd command. (See the passwd command man page for a complete description of all passwd flags, options, and arguments.)
The passwd command allows users to perform the following operations:
-
Change their passwords
-
List their password information
Administrators can use the passwd command to perform the following operations:
-
Force users to change their passwords the next time the log in
-
Lock a user's password (prevent it from being used)
-
Set a minimum number of days before a user can change passwords
-
Specified when a user is warned to change passwords
-
Set a maximum number of days a password can be used without being changed
passwd and the nsswitch.conf Files
The name service switch determines where the passwd command (and other commands) obtains and stores password information.
If the passwd entry of the applicable nsswitch.conf file points to:
-
nisplus. Password information will be obtained, modified, and stored in the passwd and cred tables of the appropriate domain.
-
nis. Password information will be obtained, modified, and stored in passwd maps.
-
files. Password information will be obtained, modified, and stored in the /etc/passwd and /etc/shadow files.
passwd -r Option
When you run the passwd command with the -r nisplus, -r nis, or -r files arguments, those options override the nsswitch.conf file setting. You will be warned that this is the case. If you continue, the -r option will cause the passwd command to ignore the nsswitch.conf file sequence and update the information in the password information storage location pointed to by the -r flag.
For example, if the passwd entry in the applicable nsswitch.conf file reads:
passwd: files nisplus |
files is the first (primary) source, and passwd run without the -r option will get its password information from the /etc/passwd file. If you run the command with the -r nisplus option, passwd will get its information from the appropriate NIS+ passwd table and make its changes to that table, not to the /etc/passwd file.
The -r option should only be used when you cannot use the nsswitch.conf file because the search sequence is wrong. For example, when you need to update password information that is stored in two places, you can use the order specified in the nsswitch.conf file for the first one, but for the second one you have to force the use of the secondary or tertiary source.
The message:
Your specified repository is not defined in the nsswitch file! |
indicates that your change will be made to the password information in the repository specified by the -r option, but that change will not affect anyone until the nsswitch.conf file is changed to point to that repository. For example, suppose the nsswitch.conf file reads passwd: files nis and you use the -r nisplus option to establish password-aging limits in an NIS+ passwd table. Those password-aging rules will sit in that table unused because the nsswitch.conf file is directing everyone to other places for their password information.
passwd Command and “NIS+ Environment”
In this chapter, the phrase NIS+ environment refers to situations where the passwd entry of the applicable nsswitch.conf file is set to nisplus, or the passwd command is run with the -r nisplus argument.
passwd Command and Credentials
When run in an NIS+ environment (see above), the passwd command is designed to function with or without credentials. Users without credentials are limited to changing their own password. Other password operations can only be performed by users who have credentials (are authenticated) and who have the necessary access rights (are authorized).
passwd Command and NIS+ Permissions
In this discussion of authorization and permissions, it is assumed that everyone referred to has the proper credentials.
By default, in a normal NIS+ environment the owner of the passwd table can change password information at any time and without constraints. In other words, the owner of the passwd table is normally granted full read, modify, create, and destroy authorization (permission) for that table.
An owner can also:
-
Assign table ownership to someone else with the nischown command.
-
Grant some or all of read, modify, create, and destroy rights to the table's group, or even to the world or nobody class. (Of course, granting such rights to world or nobody seriously weakens NIS+ security.)
-
Change the permissions granted to any class with the nisdefaults, nischmod, or nistbladm commands.
Note –
Regardless of what permissions they have, everyone in the world, and nobody classes are forced to comply with password-aging constraints. In other words, they cannot change a password for themselves or anyone else unless that password has aged past its minimum. Nor can members of the group, world, and nobody classes avoid having to change their own passwords when the age limit has been reached. However, age constraints do not apply to the owner of the passwd table.
To use the passwd command in an NIS+ environment, you must have the required authorization (access rights) for the operation.
Table 16–1 NIS+ Access Rights for passwd Command|
This Operation |
Requires These Rights |
To This Object |
|---|---|---|
|
Displaying information |
read |
passwd table entry |
|
Changing Information |
modify |
passwd table entry |
|
Adding New Information |
modify |
passwd table |
passwd Command and NIS+ Keys
If you use passwd in an NIS+ environment to change a principal's password, it tries to update the principal's private (secret) key in the cred table.
-
If you have modify rights to the DES entry in the cred table and if the principal's login and Secure RPC passwords are the same, passwd will update the private key in the cred table.
-
If you do not have modify rights to the DES entry in the cred table or if the principal's login and Secure RPC passwords are not the same, the passwd command will change the password, but not change the private key.
If you do not have modify rights to the DES entry, it means that the private key in the cred table will have been formed with a password that is now different from the one stored in the passwd table. In this case, the user will have to change keys with the chkey command or run keylogin after each login.
passwd Command and Other NIS+ Domains
To operate on the passwd table of another domain, use:
passwd [options] -D domainname |
nistbladm Command
The nistbladm command allows you to create, change, and display information about any NIS+ table, including the passwd table.
To perform password operations using the nistbladm command you must apply nistbladm to the shadow column of the passwd table. Applying nistbladm to the shadow column is complex and tricky. Therefore, you should not use the nistbladm command for any operation that can more easily be performed by the passwd command or by using the Solaris Management Console tools.
Use the passwd command or Solaris Management Console tools to perform the following operations:
-
Changing a password
-
Setting the maximum period that a password can be used (password aging)
-
Setting the minimum period that a password must be used
-
Setting the password warning period
-
Turning off password aging
It is possible to use the nistbladm command to:
-
Create new passwd table entries
-
Delete an existing entry
-
Change the UID and GID fields in the passwd table
-
Change access rights and other security-related attributes of the passwd table
-
Set expiration and inactivity periods for a user's account (see Password Privilege Expiration in NIS+ and Specifying Maximum Number of Inactive Days for Users in NIS+)
nistbladm and NIS+ Shadow Column Fields
You use the nistbladm command to set password parameters by specifying the values of the different fields in the shadow column. These fields are entered in the format:
Where:
-
N1 Lastchange. The date of the last password change expressed as a number of days since January 1, 1970. The value in this field is automatically updated each time the user changes passwords. (See nistbladm and the Number of Days Password Parameter in NIS+ for important information regarding the number of days.) If the field is blank, or contains a zero, it indicates that there has not been any change in the past.
Note that the number of days in the lastchange field is the base from which other fields and operations are calculated. Thus, an incorrect change in this field could have unintended consequence in regards to minimum, maximum, warning, and inactive time periods.
-
N2 Min. The minimum number of days that must pass since the last time the password was changed before the user can change passwords again. For example, if the value in the lastchange field is 9201 (that is, 9201 days since 1/1/70) and the value in the min field is 8, the user is unable to change passwords until after day 9209. See Setting Minimum Password Life in NIS+ for additional information on password minimums.
Where min is one of the following values:
-
Zero (0). A value of zero in this field (or a blank space) means that there is no minimum period.
-
Greater than zero. Any number greater than zero sets that number of days as the minimum password life.
-
Greater than max. A value in this field that is greater than the value in the max field prevents the user from ever changing passwords. The message: You may not change this password is displayed when the user attempts to change passwords.
-
-
N3 Max. The maximum number of days that can pass since the last time the password was changed. Once this maximum number of days is exceeded, the user is forced to choose a new password the next time the user logs in. For example, if the value in the lastchange field is 9201 and the value in the max field is 30, after day 9231 (figured 9201+30=9231), the user is forced to choose a new password at the next login. See Setting a Password Age Limit in NIS+ for additional information on password maximums.
Where max is one of the following values:
-
Zero (0). A value of zero (0) forces the user to change passwords the next time the user logs in, and it then turns off password aging.
-
Greater than zero. Any number greater than zero sets that number of days before the password must be changed.
-
Minus one (-1). A value of minus one (-1) turns off password aging. In other words, entering passwd -x -1 username cancels any previous password aging applied to that user. A blank space in the field is treated as if it were a minus one.
-
-
N4 Warn. The number of days before a password reaches its maximum that the user is warned to change passwords. For example, suppose the value in the lastchange field is 9201, the value in the max field is 30, and the value in the warn field is 5. Then after day 9226 (figured 9201+30-5=9226) the user starts receiving “change your password” type warnings at each longing time. See Establishing a Password Warning Period in NIS+ for additional information on password warning times.
Where warn is one of the following values:
-
Zero (0). No warning period.
-
Greater than zero. A value of zero (0) sets the warning period to that number of days.
-
-
N5 Inactive. The maximum number of days between logins. If this maximum is exceeded, the user is not allowed to log in. For example, if the value of this field is 6, and the user does not log in for six days, on the seventh day the user is no longer allowed to log in. See Specifying Maximum Number of Inactive Days for Users in NIS+ for additional information on account inactivity.
Where inactive is one of the following values:
-
Minus one (-1). A value of minus one (-1) turns off the inactivity feature. The user can be inactive for any number of days without losing login privileges. This is the default.
-
Greater than zero. A value greater than zero sets the maximum inactive period to that number of days.
-
-
N6 Expire. The date on which a password expires, expressed as a number of days since January 1, 1970. After this date, the user can no longer log in. For example, if this field is set to 9739 (September 1, 1995) on September 2, 1995 GMT, the user will not be able to login and will receive a Login incorrect message after each try. See Password Privilege Expiration in NIS+ for additional information on password expiration.
Where expire is one of the following values:
-
Minus one (-1). A value of minus one (-1) turns off the expiration feature. If a user's password has already expired, changing this value to -1 restores it. If you do not want to set any expiration date, type a -1 in this field.
-
Greater than zero. A value greater than zero sets the expiration date to that number of days since 1/1/70. If you enter today's date or an earlier date, you immediately deactivate the users password.
-
-
N7 Unused. This field is not currently used. Values entered in this field will be ignored.
-
Login is the user's login ID.
When using nistbladm on the shadow column of the password table, all of the numeric fields must contain appropriate values. You cannot leave a field blank, or enter a zero, as a no change placeholder.
For example, to specify that the user amy last changed her password on day 9246 (May 1, 1995), cannot change her password until it has been in use for 7 days, must change her password after 30 days, will be warned to change her password after 25 days, must not remain inactive more than 15 days, and has an account that will expire on day number 9285, you would type:
nistbladm -m shadow=9246:7:30:5:15:9285 [name=amy], passwd.org.dir |
nistbladm and the Number of Days Password Parameter in NIS+
Most password aging parameters are expressed in number of days.
The following principles and rules apply:
-
Days are counted from January 1, 1970. That is day zero. January 2, 1970, is day 1.
-
NIS+ uses Greenwich mean time (GMT) in figuring and counting days. In other words, the day count changes at midnight GMT.
-
When you specify a number of days, you must use a whole number. You cannot use fractions of days.
-
When the number of days is used to specify some action, such as locking a password, the change takes effect on the day. For example, if you specify that a user's password privilege expires on day 9125 (January 2, 1995), that is the last day that the user can use the password. On the next day, the user can no longer use the password.
Values are entered in both the Lastchange and the Expire fields as a number of days since January 1, 1970, as in the following.
Table 16–2 Number of Days Since 1/1/70 Password Parameter in NIS+|
Date |
Day Number |
|---|---|
|
January 1, 1970 |
0 |
|
January 2, 1970 |
1 |
|
January 2, 1971 |
365 |
|
January 1, 1997 |
9863 |
Password-Related Commands in NIS+
The passwd and nistbladm commands provide capabilities that are similar to those offered by other commands. Table 16–3 summarizes their differences.
Table 16–3 NIS+ Commands Related to Passwords|
Command |
Description |
|---|---|
|
yppasswd |
Is now linked to the passwd command. Using yppasswd simply invokes the passwd command. |
|
nispasswd |
Is now linked to the passwd command. Using nispasswd simply invokes the passwd command. |
|
niscat |
Can be used to display the contents of the passwd table. |
Displaying Password Information in NIS+
You can use the passwd command to display password information about all users in a domain or about one particular user:
For your password information
passwd -s |
For all users in current domain
passwd -s -a |
For a particular user
passwd -s username |
Only the entries and columns for which you have read permission will be displayed.
Entries are displayed with the following format:
-
Without password aging: username status
-
With password aging: username status mm/dd/yy min max warn expire inactive
|
Field |
Description |
For Further Information |
|---|---|---|
|
username |
The user's login name. |
|
|
status |
The user's password status. PS indicates the account has a password. LK indicates the password is locked. NP indicates the account has no password. | |
|
mm/dd/yy |
The date, based on Greenwich mean time, that the user's password was last changed. |
|
|
min |
The minimum number of days since the last change that must pass before the password can be changed again. | |
|
max |
The maximum number of days the password can be used without having to change it. | |
|
warn |
The number of days' notice that users are given before their passwords have to be changed. | |
|
expire |
A date on which users loose the ability to log in to their accounts. | |
|
inactive |
A limit on the number of days that an account can go without being logged in to. Once that limit is passed without a log in users can no longer access their accounts. |
See Specifying Maximum Number of Inactive Days for Users in NIS+. |
To display entries from a passwd table in another domain, use the -D option:
For all users in another domain
passwd -s -a -D domainname |
For a particular user
passwd -s -D domainname username |
Changing Passwords in NIS+
New passwords must meet the criteria described in Password Requirements.
Changing Your Own Password
To change your password, type
station1% passwd |
You will be prompted for your old password and then the new password and then the new password a second time to confirm it.
Changing Someone Else's Password in NIS+
To change another user's password in the same domain, use:
passwd username |
To change another user's password in a different domain, use:
passwd -D domainname username |
When using the passwd command in an NIS+ environment (see passwd Command and “NIS+ Environment”) to change someone else's password you must have modify rights to that user's entry in the passwd table (this usually means that you are a member of the group for the passwd table and the group has modify rights). You do not have to enter either the user's old password or your password. You will be prompted to enter the new password twice to make sure that they match. If they do not match, you will be prompted to enter them again.
Changing Root's Password in NIS+
When changing root's password, you must always run chkey -p immediately after changing the password with the passwd command. Failure to run chkey -p after changing root's password will result in root being unable to properly log in.
To change a root password, follow these steps:
 How to Change root's Password
How to Change root's Password
-
Log in as root.
-
Change root's password using passwd.
Do not use nispasswd.
-
Run chkey -p.
You must use the -p option.
Locking a Password in NIS+
When operating in an NIS+ environment (see passwd Command and “NIS+ Environment”), an administrator (a group member) with modify rights to a user's entry in the passwd table can use the passwd command to lock a password. An account with a locked password cannot be used. When a password is locked, the user will receive a Login incorrect message after each login attempt.
Keep in mind that locked passwords have no effect on users who are already logged in. A locked password only prevents users from performing those operations that require giving a password such as login, rlogin, ftp, or telnet.
Note also that if a user with a locked password is already logged in, and that user uses the passwd command to change passwords, the lock is broken.
You can use this feature to:
-
Temporarily lock a user's password while that user is on vacation or leave. This prevents anyone from logging in as the absent user.
-
Immediately lock one or more user passwords in the case of suspected security problem.
-
Quickly lock a dismissed employee out of the system. This is quicker and easier than eliminating that user's account and is an easy way of preserving any data stored in that account.
-
If you have assigned passwords to UNIX processes, you can lock those passwords. This allows the process to run, but prevents anyone from logging in as those processes even if they know the process password. (In most cases, processes would not be set up as NIS+ principals, but would maintain their password information in /etc files. In such a case you would have to run the passwd command in files mode to lock /etc stored passwords.)
To lock a password, use:
passwd -l username |
Unlocking a Password in NIS+
To unlock a user's password, you simply change it. You can “change” it back to the exact same password that it was when it was locked. Or you can change it to something new.
For example, to unlock jody's password, you would enter:
station1% passwd jody |
Managing Password Aging in NIS+
Password aging is a mechanism you can use to force users to periodically change their passwords. Password aging allows you to:
-
Force a user to choose a new password the next time the user logs in. (See Forcing Users to Change Passwords in NIS+ for details.)
-
Specify a maximum number of days that a password can be used before it has to be changed. (See Setting a Password Age Limit in NIS+ for details.)
-
Specify a minimum number of days that a password has to be in existence before it can be changed. (See Setting Minimum Password Life in NIS+ for details.)
-
Specify that a warning message be displayed whenever a user logs in a specified number of days before the user's password time limit is reached. (See Establishing a Password Warning Period in NIS+ for details.)
-
Specify a maximum number of days that an account can be inactive. If that number of days pass without the user logging in to the account, the user's password will be locked. (See Specifying Maximum Number of Inactive Days for Users in NIS+ for details.)
-
Specify an absolute date after which a user's password cannot be used, thus denying the user the ability to log in to the system. (See Password Privilege Expiration in NIS+ for details.)
Keep in mind that users who are already logged in when the various maximums or dates are reached are not affected by the preceding features. They can continue to work as normal.
Password aging limitations and activities are only activated when a user logs in or performs one of the following operations:
-
login
-
rlogin
-
telnet
-
ftp
These password aging parameters are applied on user-by-user basis. You can have different password aging requirements for different users. (You can also set general default password aging parameters as described in Managing Password Aging in NIS+.)
Forcing Users to Change Passwords in NIS+
There are two ways to force a user to change passwords the next time the user logs in:
Force change keeping password aging rules in effect
passwd -f username |
Force change and turn off password aging rules
passwd -x 0 username |
Setting a Password Age Limit in NIS+
The -max argument to the passwd command sets an age limit for the current password. In other words, it specifies the number of days that a password remains valid. After that number of days, a new password must be chosen by the user. Once the maximum number of days have passed, the next time the user tries to login with the old password a Your password has been expired for too long message is displayed and the user is forced to choose a new password in order to finish logging in to the system.
The max argument uses the following format:
passwd -x max username |
Where:
-
username is the login ID of the user
-
max is one of the following values:
-
Greater than zero. Any number greater than zero sets that number of days before the password must be changed.
-
Zero (0). A value of zero (0) forces the user to change passwords the next time the user logs in, and it then turns off password aging.
-
Minus one (-1). A value of minus one (-1) turns off password aging. In other words, entering passwd -x -1 username cancels any previous password aging applied to that user.
-
For example, to force the user schweik to change passwords every 45 days, you would type the command:
station1% passwd -x 45 schweik |
Setting Minimum Password Life in NIS+
The min argument to the passwd command specifies the number of days that must pass before a user can change passwords. If a user tries to change passwords before the minimum number of days has passed, a Sorry less than N days since the last change message is displayed.
The min argument uses the following format:
passwd -x max -n min username |
Where:
-
username is the login ID of the user
-
max is the maximum number of days a password is valid as described in the section above
-
min is the minimum number of days that must pass before the password can be changed
For example, to force the user eponine to change passwords every 45 days, and prevent him from changing it for the first 7 days you would type the command:
station1% passwd -x 45 -n 7 eponine |
The following rules apply to the min argument:
-
You do not have to use a min argument or specify a minimum number of days before a password can be changed.
-
If you do use the min argument, it must always be used in conjunction with the -max argument. In other words, in order to set a minimum value you must also set a maximum value.
-
If you set min to be greater than max, the user is unable to change passwords at all. For example, the command passwd -x 7 -n 8 prevents the user from changing passwords. If the user tries to change passwords, the You may not change this password message is displayed. Setting the min value greater than the max value has two effects:
-
The user is unable to change password. In this case, only someone with administer privileges could change the password. For example, in situations where multiple users share a common group password, setting the min value for that password greater than the max value would prevent any individual user from changing the group password.
-
The password is only valid for the length of time set by the max value, but the user cannot change it because the min value is greater than the max value. Thus, there is no way for the user to prevent the password from becoming invalid at the expiration of the max time period. In effect, this prevents the user from logging in after the max time period unless an administrator intervenes.
-
Establishing a Password Warning Period in NIS+
The warn argument to the passwd command specifies the number of days before a password reaches its age limit that users will start to seeing a Your password will expire in N days message (where N is the number of days) when they log in.
For example, if a user's password has a maximum life of 30 days (set with the -max argument) and the warn value is set to 7 days, when the user logs in on day 24 (one day past the warn value) the warning message Your password will expire in 7 days is displayed. When the user logs in on day 25, the warning message Your password will expire in 6 days is displayed.
Keep in mind that the warning message is not sent by Email or displayed in a user's console window. It is displayed only when the user logs in. If the user does not log in during this period, no warning message is given.
Keep in mind that the warn value is relative to the max value. In other words, it is figured backwards from the deadline set by the max value. Thus, if the warn value is set to 14 days, the Your password will expire in N days message will begin to be displayed two weeks before the password reaches its age limit and must be changed.
Because the warn value is figured relative to the max value, it only works if a max value is in place. If there is no max value, warn values are meaningless and are ignored by the system.
The warn argument uses the following format:
passwd -x max -w warn username |
Where:
-
username is the login ID of the user.
-
max is the maximum number of days a password is valid as described on Setting a Password Age Limit in NIS+.
-
warn is the number of days before the password reaches its age limit that the warning message will begin to be displayed.
For example, to force the user nilovna to change passwords every 45 days, and display a warning message 5 days before the password reaches its age limit you would type the command:
station1% passwd -x 45 -w 5 nilovna |
The following rules apply to the warn argument:
-
You do not have to use the warn argument or specify a warning message. If no warn value is set, no warning message is displayed prior to a password reaching its age limit.
-
If you do use the warn argument, it must always be used in conjunction with the max argument. In other words, in order to set a warning value you must also set a maximum value.
Note –
You can also use Solaris Management Console to set a warn value for a user's password.
Turning Off Password Aging in NIS+
There are two ways to turn off password aging for a given user:
Turn off aging while allowing user to retain current password
passwd -x -1 username |
Force user to change password at next login, and then turn off aging
passwd -x 0 username |
This sets the max value to either zero or -1 (see Setting a Password Age Limit in NIS+ for more information on this value).
For example, to force the user mendez to change passwords the next time he logs in and then turn off password aging you would type the command:
station% passwd -x 0 mendez |
Note –
You can also use Solaris Management Console to set this parameter for a user's password.
You can also use the nistbladm command to set this value. For example, to turn off password aging for the user otsu and allow her to continue using her current password, you would type:
station1% nistbladm -m `shadow=0:0:-1:0:0:0:0' [name=otsu],passwd.org_dir |
For additional information on using the nistbladm command, see nistbladm Command.
Password Privilege Expiration in NIS+
You can set a specific date on which a user's password privileges expires. When a user's password privilege expires, that user can no longer have a valid password at all. In effect, this locks the user out of the system after the given date because after that date the user can no longer log in.
For example, if you specify an expire date of December 31, 1997, for a user named pete, on January 1, 1998 he will not be able to log in under that user ID regardless of what password he uses. After each login attempt he will receive a Login incorrect message.
Password Aging and Password Expiration in NIS+
Expiration of a user's password privilege is not the same as password aging.
-
Password aging. A password that has not been changed for longer than the aging time limit is sometimes referred to as an expired password. But that password can still be used to log in one more time. As part of that last login process the user is forced to choose a new password.
-
Expiration of password privilege. When a user's password privilege expires, the user cannot log in at all with any password. In other words, it is the user's permission to log in to the network that has expired.
Setting a Password Expiration Date in NIS+
Password privilege expiration dates only take effect when the user logs in. If a user is already logged in, the expiration date has no effect until the user logs out or tries to use rlogin or telnet to connect to another machine at which time the user will not be able to log in again. Thus, if you are going to implement password privilege expiration dates, you should require your users to log out at the end of each day's work session.
Note –
If you have Solaris Management Console tools available, do not use nistbladm to set an expiration date. Use Solaris Management Console tools because they are easier to use and provide less chance for error.
To set an expiration date with the nistbladm command:
nistbladm -m `shadow=n:n:n:n:n:n6:n' [name=login],passwd.org_dir |
Where:
-
login is the user's login ID
-
n indicates the values in the other fields of the shadow column
-
n6 is the date on which the user's password privilege expires This date is entered as a number of days since January 1, 1970 (see Table 16–2). n6 can be one of the following values:
-
Minus one (-1). A value of minus one (-1) turns off the expiration feature. If a user's password has already expired, changing this value to -1 restores the password. If you do not want to set any expiration date, type -1 in this field.
-
Greater than zero. A value greater than zero sets the expiration date to that number of days since 1/1/70. If you enter today's date or an earlier date, you immediately expire the user's password.
-
For example, to specify an expiration date for the user pete of December 31, 1995 you would type:
station1% nistbladm -m `shadow=n:n:n:n:n:9493:n' [name=pete],passwd.org_dir |
All of the fields must be filled in with valid values.
Turning Off Password Privilege Expiration in NIS+
To turn off or deactivate password privilege expiration, you must use the nistbladm command to place a -1 in this field. For example, to turn off privilege expiration for the user huck, you would type:
station1% nistbladm -m `shadow=n:n:n:n:n:-1:n' [name=huck],passwd.org_dir |
Or you can use the nistbladm command reset the expiration date to some day in the future by entering a new number of days in the n6 field.
Specifying Maximum Number of Inactive Days for Users in NIS+
You can set a maximum number of days that a user can go without logging in on a given machine. Once that number of days passes without the user logging in, that machine will no longer allow that user to log in. In this situation, the user will receive a Login incorrect message after each login attempt.
This feature is tracked on a machine-by-machine basis, not a network-wide basis. That is, in an NIS+ environment, you specify the number of days a user can go without logging in by placing an entry for that user in the passwd table of the user's home domain. That number applies for that user on all machines on the network.
For example, suppose you specify a maximum inactivity period of 10 days for the user sam. On January 1, sam logs in to both machine-A and machine-B, and then logs off both machines. Four days later on January 4, sam logs in on machine-B and then logs out. Nine days after that on January 13, sam can still log in to machine-B because only 9 days have elapsed since the last time he logged in on that machine, but he can no longer log in to machine-A because thirteen days have passed since his last log in on that machine.
Keep in mind that an inactivity maximum cannot apply to a machine the user has never logged in to. No matter what inactivity maximum has been specified or how long it has been since the user has logged in to some other machine, the user can always log in to a machine that the user has never logged in to before.
Do not set inactivity maximums unless your users are instructed to log out at the end of each workday. The inactivity feature only relates to logins; it does not check for any other type of system use. If a user logs in and then leaves the system up and running at the end of each day, that user will soon pass the inactivity maximum because there has been no login for many days. When that user finally does reboot or log out, he or she won't be able to log in.
Note –
If you have Solaris Management Console tools available, do not use nistbladm to set an inactivity maximum. Use Solaris Management Console tools because they are easier to use and provide less chance for error.
To set a login inactivity maximum, you must use the nistbladm command in the format:
nistbladm -m `shadow=n:n:n:n:n5:n:n' [name=login],passwd.org_dir |
Where:
-
login is the user's login ID
-
n indicates the values in the other fields of the shadow column
-
n5 is the number of days the user is allowed to go between logins. Inactive can be one of the following values:
-
Minus one (-1). A value of minus one (-1) turns off the inactivity feature. The user can be inactive for any number of days without losing login privileges. This is the default.
-
Greater than zero. A value greater than zero sets the maximum inactive period to that number of days.
-
For example, to specify that the user sam must log in at least once every seven days, you would type:
station1% nistbladm -m `shadow=n:n:n:n:n:7:n:n' [name=sam],passwd.org_dir |
To clear an inactivity maximum and allow a user who has been prevented from logging in to log in again, use nistbladm to set the inactivity value to -1.
Specifying Password Criteria and Defaults in NIS+
The following subsections describe various password-related defaults and general criteria that you can specify.
/etc/defaults/passwd File
The /etc/defaults/passwd file is used to set four general password defaults for users whose nsswitch.conf file points to files. The defaults set by the /etc/defaults/passwd file apply only to those users whose operative password information is taken from /etc files; they do not apply to anyone using either NIS maps or NIS+ tables. An /etc/defaults/passwd file on an NIS+ server only affects local users who happen to be obtaining their password information from those local files. An /etc/defaults/passwd file on an NIS+ server has no effect on the NIS+ environment or users whose nsswitch.conf file points to either nis or nisplus.
The four general password defaults governed by the /etc/defaults/passwd file are:
-
Maximum number of weeks the password is valid
-
Minimum number of weeks the password is valid
-
The number of weeks before the password becomes invalid that the user is warned
-
The minimum number of characters that a password must contain
The following principles apply to defaults set with an /etc/defaults/passwd file:
-
For users who obtain password information from local /etc files, individual password aging maximums, minimums and warnings set by the password command or Solaris Management Console override any /etc/defaults/passwd defaults. In other words, defaults set in the /etc/defaults/passwd file are not only applied to those users who do not have corresponding individual settings in their entries in their passwd table.
-
Except for password length, all the /etc/defaults/passwd file defaults are expressed as a number of weeks. (Remember that individual password aging times are expressed as a number of days.)
-
The MAXWEEKS, MINWEEKS, and WARNWEEKS defaults are all counted forward from the date of the user's last password change. (Remember that individual warn values are counted backwards from the maximum date.)
By default, /etc/defaults/passwd files already contain the entries:
MAXWEEKS= MINWEEKS= PASSLENGTH= |
To implement an entry, simply type the appropriate number after the equal sign. Entries that do not have a number after the equal sign are inactive and have no effect on any user. Thus, to set a MAXWEEKS default of 4, you would change the /etc/defaults/passwd file to read:
MAXWEEKS=4 MINWEEKS= PASSLENGTH= |
Maximum Weeks
You can use the MAXWEEKS default in the /etc/defaults/passwd file to set the maximum number of weeks that a user's password is valid. To set a default maximum time period, type the appropriate number of weeks after the equal sign in the MAXWEEKS= line:
MAXWEEKS=N |
Where N is a number of weeks. For example, MAXWEEKS=9.
Minimum Weeks
You can use the MINWEEKS default in the /etc/defaults/passwd file to set the minimum number of weeks that must pass before a user can change passwords. To set a default minimum time period, type the appropriate number of weeks after the equal sign on the MINWEEKS= line:
MINWEEKS=N |
Where N is a number of weeks. For example, MINWEEKS=2.
Warning Weeks
You can add a WARNWEEKS default to the /etc/defaults/passwd file set the number of weeks prior to a password becoming invalid due to aging that user is warned. for example, if you have set the MAXWEEKS default to 9, and you want users to be warned two weeks before their passwords become invalid, you would set the MAXWEEKS default to 7.
There is no point in setting the WARNWEEKS default unless you also set a MAXWEEKS default.
Remember that WARNWEEKS are counted forward from the date of the user's last password change, not backwards from the MAXWEEKS expiration date. Thus, WARNWEEKS must always be less than MAXWEEKS and cannot be equal to or greater than MAXWEEKS.
A WARNWEEKS default will not work unless there is also a MAXWEEKS default.
To set the warning time period, type the appropriate number of weeks after the equal sign on the WARNWEEKS= line.
WARNWEEKS=N |
Where Nis the number of weeks. For example, WARNWEEKS=1.
Minimum Password Length
By default, the passwd command assumes a minimum length of six characters. You can use the PASSLENGTH default in the /etc/defaults/passwd files to change that by setting the minimum number of characters that a user's password must contain to some other number.
To set the minimum number of characters to something other than six, type the appropriate number of characters after the equal sign in the PASSLENGTH= line:
PASSLENGTH=N |
Where Nis the number of characters. For example, PASSLENGTH=7.
Password Failure Limits
You can specify a number-of-tries limit or an amount-of-time limit (or both) for a user's attempt to change passwords. These limits are specified by adding arguments when starting the rpc.nispasswdd daemon.
Limiting the number of attempts or setting a time frame provides a limited (but not foolproof) defense against unauthorized persons attempting to change a valid password to one that they discover through trial and error.
Maximum Number of Tries
To set the maximum number of times a user can try to change a password without succeeding, use the -a number argument with rpc.nispasswdd, where number is the number of allowed tries. (You must have superuser privileges on the NIS+ master server to run rpc.nispasswdd.)
For example, to limit users to no more than four attempts (the default is 3), you would type:
station1# rpc.nispasswdd -a 4 |
In this case, if a user's fourth attempt at logging in is unsuccessful, the message Too many failures - try later is displayed. No further attempts are permitted for that user ID until a specified period of time has passed.
Maximum Login Time Period
To set the maximum amount a time a user can take to successfully change a password, use the -c minutes argument with rpc.nispasswdd, where minutes is the number of minutes a user has to log in. (You must have superuser privileges on the NIS+ master server to run rpc.nispasswdd.)
For example, to specify that users must successfully log in within 2 minutes, you would type:
station1# rpc.nispasswdd -c 2 |
In this case, if a user is unable to successfully change a password within 2 minutes, the message is displayed at the end of the two-minute period. No further attempts are permitted for that user ID until a specified period of time has passed.
Chapter 17 Administering NIS+ Groups
This chapter describes NIS+ groups and how to administer them.
Tip –
Some NIS+ security group tasks can be performed more easily with Solaris Management Console tools if you have them available.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
Solaris Groups and NIS+ Groups
The Solaris NIS+ environment defines three kinds of groups: UNIX groups, net groups, and NIS+ groups.
-
UNIX groups. A UNIX group is simply a collection of users who are given additional UNIX access permissions. In an NIS+ namespace, UNIX group information is stored in the group table located in the org_dir directory object (group.org_dir). See Chapter 19, Administering NIS+ Tables for information on how to add, modify, or delete members of a UNIX group.
-
Net groups. A net group is a group of machines and users that have permission to perform remote operations on other machines. In an NIS+ namespace, net groups information is stored in the netgroup table located in the org_dir directory object (netgroup.org_dir). See Chapter 19, Administering NIS+ Tables for information on how to add, modify, or delete members of a net groups.
-
NIS+ groups. An NIS+ group is a set of NIS+ users that are assigned specific access rights to NIS+ objects, usually for the purpose of administering the namespace. NIS+ group information is stored in tables located in the groups_dir directory object.
NIS+ Groups
NIS+ groups are used to assign access rights to NIS+ objects to one or more NIS+ principles. These access rights are described in Chapter 11, NIS+ Security Overview. Information about NIS+ groups is stored in tables located in the NIS+ groups_dir directory object. Information about each group is stored in a table of the same name. For example, information about the admin group is stored in admin.groups_dir.
It is recommended practice to create at least one NIS+ group called admin. The admin NIS+ group is normally used to designate those users who are to have NIS+ access rights. You can name this group anything you want, but the NIS+ manual set assumes that the group with NIS+ administrator privileges is named admin. You can also create multiple NIS+ groups with different sets of users and different sets of rights.
Note –
Always use the nisgrpadm command to work with NIS+ group membership. You can also use the nisls and nischgrp commands on the group table. Do not use the nistbladm command on the group table.
For a complete description of NIS+ group-related commands and their syntax and options, see the NIS+ man pages.
Related NIS+ Administration Commands for Groups
The nisgrpadm command performs most group administration tasks but several other commands affect groups as well,
Table 17–1 NIS+ Commands That Affect Groups|
Command |
Description |
See |
|---|---|---|
|
nissetup |
Creates, among other things, the directory in which a domain's groups are stored: groups_dir. |
|
|
nisls |
Lists the contents of the groups_dir directory; in other words, all the groups in a domain. For each named groups there will be a table of that name in groups_dir. | |
|
nischgrp |
Changes or assigns a group to any NIS+ object. | |
|
niscat |
Lists the object properties and membership of an NIS+ group. | |
|
nisdefaults |
Lists, among other things, the group that will be assigned to any new NIS+ object. |
For a complete description of these commands and their syntax, and options, see the NIS+ man pages.
Note –
Do not use the nistbladm command to work with the NIS+ groups table.
NIS+ Group Member Types
NIS+ groups can have three types of members: explicit, implicit, and recursive; and three types of nonmembers, also explicit, implicit, and recursive. These member types are used when adding or removing members of a group as described in nisgrpadm Command.
NIS+ Member Types
-
Explicit. An individual principal. Identified by principal name. The name does not have to be fully qualified if entered from its default domain.
-
Implicit. All the NIS+ principals who belong to an NIS+ domain. They are identified by their domain name, preceded by the * symbol and a dot. The operation you select applies to all the members in the group.
-
Recursive. All the NIS+ principals that are members of another NIS+ group. They are identified by their NIS+ group name, preceded by the @ symbol. The operation you select applies to all the members in the group.
NIS+ groups also accept nonmembers in all three categories: explicit, implicit, and recursive. Nonmembers are principals specifically excluded from a group that they otherwise would be part of.
NIS+ Nonmember Types
Nonmembers are identified by a minus sign in front of their name:
-
Explicit-nonmember. Identified by a minus sign in front of the principal name.
-
Implicit-nonmember. Identified by a minus sign, * symbol, and dot in front of the domain name.
-
Recursive nonmember. Identified by a minus sign and @ symbol in front of the group name.
NIS+ Group Syntax
The order in which inclusions and exclusions are entered does not matter. Exclusions always take precedence over inclusions. Thus, if a principal is a member of an included implicit domain and also a member of an excluded recursive group, then that principal is not included.
Thus, when using the nisgrpadm command, you can specify group members and nonmembers as shown in Table 17–2.
Table 17–2 Specifying NIS+ Group Members and Nonmembers|
Type of member |
Syntax |
|---|---|
|
Explicit member |
username.domain |
|
Implicit member |
*.domain |
|
Recursive member |
@groupname.domain |
|
Explicit nonmember |
-username.domain |
|
Implicit nonmember |
-*.domain |
|
Recursive nonmember |
@groupname.domain |
Using niscat With NIS+ Groups
The niscat -ocommand can be used to list the object properties and membership of an NIS+ group.
Listing the Object Properties of an NIS+ Group
To list the object properties of a group, you must have read access to the groups_dir directory in which the group is stored. Use niscat -o and the group's fully qualified name, which must include its groups_dir subdirectory:
niscat -o group-name.groups_dir.domain-name |
For example:
rootmaster# niscat -o sales.groups_dir.doc.com. Object Name : sales Owner : rootmaster.doc.com. Group : sales.doc.com. Domain : groups_dir.doc.com. Access Rights : ----rmcdr---r--- Time to Live : 1:0:0 Object Type : GROUP Group Flags : Group Members : rootmaster.doc.com. topadmin.doc.com. @.admin.doc.com. *.sales.doc.com. |
Note –
A better list of members is provided by the nisgrpadm -l command.
Several of the group's properties are inherited from the NIS_DEFAULTS environment variable, unless they were overridden when the group was created. The group flags field is currently unused. In the list of group members, the * symbol identifies member domains and the @ symbol identifies member groups.
nisgrpadm Command
The nisgrpadm command creates, deletes, and performs miscellaneous administration operations on NIS+ groups. To use nisgrpadm, you must have access rights appropriate for the operation.
Table 17–3 NIS+ Rights Required for nisgrpadm Command|
This Operation |
Requires This Access Right |
To This Object |
|---|---|---|
|
Create a group |
Create |
groups_dir directory |
|
Destroy a group |
Destroy |
groups_dir directory |
|
List the Members |
Read |
the group object |
|
Add Members |
Modify |
the group object |
|
Remove Members |
Modify |
the group object |
The nisgrpadm has two main forms, one for working with groups and one for working with group members.
To create or delete a group, or to lists its members use these forms:
nisgrpadm -c group-name.domain-name nisgrpadm -d group-name nisgrpadm -l group-name |
To add or remove members, or determine if they belong to the group use this form (where member... can be any combination of the six membership types listed in Table 17–2):
nisgrpadm -a group-name member... nisgrpadm -r group-name member... nisgrpadm -t group-name member... |
All operations except create (-c) accept a partially qualified group-name. However, even for the -c option, nisgrpadm does not require the use of groups_dir in the group-name argument. In fact, it won't accept it.
Creating an NIS+ Group
To create an NIS+ group, you must have create rights to the groups_dir directory of the group's domain. Use the -c option and a fully qualified group name:
nisgrpadm -c group-name. domainname |
When you create a group, an NIS+ groups table with the name you have given is created in groups_dir. You can use nisls to confirm that the new group table now exists in groups_dir, and niscat to list the groups members listed in the table.
A newly created group contains no members. See Adding Members to an NIS+ Group for information on how to specify who belongs to a group.
The example below creates three groups named admin. The first is in the doc.com. domain, the second in sales.doc.com., and the third in manf.doc.com. All three are created on the master server of their respective domains.
rootmaster# nisgrpadm -c admin.doc.com. Group admin.doc.com. created. salesmaster# nisgrpadm -c admin.sales.doc.com. Group admin.sales.doc.com. created. manfmaster# nisgrpadm -c admin.manf.doc.com. Group admin.manf.doc.com. created. |
The group you create will inherit all the object properties specified in the NIS_DEFAULTS variable; that is, its owner, owning group, access rights, time-to-live, and search path. You can view these defaults by using the nisdefaults command (described in Chapter 15, Administering NIS+ Access Rights). Used without options, it provides this output:
rootmaster# nisdefaults Principal Name : rootmaster.doc.com. Domain Name : doc.com. Host Name : rootmaster.doc.com. Group Name : Access Rights : ----rmcdr---r--- Time to live : 12:0:0 Search Path : doc.com. |
The owner is listed in the Principal Name field. The Group Name of the owning group is listed only if you have set the NIS_GROUP environment variable. For example, assuming a C-shell, to set NIS_GROUP to net_admins.doc.com:
rootmaster# setenv NIS_GROUP net_admins.doc.com |
You can override any of these defaults at the time you create the group by using the -D option:
salesmaster# nisgrpadm -D group=special.sales.doc.com.-c admin.sales.doc.com. Group admin.sales.doc.com. created. |
Deleting an NIS+ Group
To delete an NIS+ group, you must have destroy rights to the groups_dir directory in the group's domain. Use the -d option:
nisgrpadm -d group-name |
If the default domain is set properly, you don't have to fully-qualify the group name. However, you should check first (use nisdefaults), because you could unintentionally delete a group in another domain. The example below deletes the test.sales.doc.com. group.
salesmaster% nisgrpadm -d test.sales.doc.com. Group `test.sales.doc.com.' destroyed. |
Adding Members to an NIS+ Group
To add members to an NIS+ group you must have modify rights to the group object. Use the -a option:
nisgrpadm -a group-name members. . . |
As described in NIS+ Group Member Types, you can add principals (explicit members), domains (implicit members), and groups (recursive members). You don't have to fully qualify the name of the group or the name of the members who belong to the default domain. This example adds the NIS+ principals panza and valjean, both from the default domain, sales.doc.com., and the principal makeba, from the manf.doc.com. domain, to the group top-team.sales.doc.com.
client% nisgrpadm -a Ateam panza valjean makeba.manf.doc.com. Added panza.sales.doc.com to group Ateam.sales.doc.com Added valjean.sales.doc.com to group Ateam.sales.doc.com Added makeba.manf.doc.com to group Ateam.sales.doc.com |
To verify the operation, use the nisgrpadm -l option. Look for the members under the Explicit members heading.
This example adds all the NIS+ principals in the doc.com. domain to the staff.doc.com. group. It is entered from a client in the doc.com. domain. Note the * symbol and the dot in front of the domain name.
client% nisgrpadm -a Staff *.doc.com. Added *.doc.com. to group Staff.manf.doc.com. |
This example adds the NIS+ group admin.doc.com. to the admin.manf.doc.com. group. It is entered from a client of the manf.doc.com. domain. Note the @ symbol in front of the group name.
client% nisgrpadm -a admin @admin.doc.com. Added @admin.doc.com. to group admin.manf.doc.com. |
Listing the Members of an NIS+ Group
To list the members of an NIS+ group, you must have read rights to the group object. Use the -l option:
nisgrpadm -l group-name |
This example lists the members of the admin.manf.doc.com. group. It is entered from a client in the manf.doc.com. group:
client% nisgrpadm -l admin Group entry for admin.manf.doc.com. group: No explicit members No implicit members: Recursive members: @admin.doc.com. No explicit nonmembers No implicit nonmembers No recursive nonmembers |
Removing Members From an NIS+ Group
To remove members from an NIS+ group, you must have modify rights to the group object. Use the -r option:
nisgrpadm -r group-name members. . . |
This example removes the NIS+ principals allende and hugo.manf.doc.com. from the Ateam.sales.doc.com group. It is entered from a client in the sales.doc.com. domain:
client% nisgrpadm -r Ateam allende hugo.manf.doc.com. Removed allende.sales.doc.com. from group Ateam.sales.doc.com. Removed hugo.manf.doc.com. from group Ateam.sales.doc.com. |
This example removes the admin.doc.com. group from the admin.manf.doc.com. group. It is entered from a client in the manf.doc.com. domain:
client% nisgrpadm -r admin @admin.doc.com. Removed @admin.doc.com. from group admin.manf.doc.com. |
Testing for Membership in an NIS+ Group
To find out whether an NIS+ principal is a member of a particular NIS+ group you must have read access to the group object. Use the -t option:
nisgrpadm -t group-name members. . . |
This example tests whether the NIS+ principal topadmin belongs to the admin.doc.com. group. It is entered from a client in the doc.com. domain.
client% nisgrpadm -t admin topadmin topadmin.doc.com. is a member of group admin.doc.com. |
This example tests whether the NIS+ principal jo, from the sales.doc.com. domain, belongs to the admin.sales.doc.com. group. It is entered from a client in the doc.com. domain.
client% nisgrpadm -t admin.sales.doc.com. jo.sales.doc.com. jo.sales.doc.com. is a member of group admin.sales.doc.com. |
Chapter 18 Administering NIS+ Directories
This chapter describes NIS+ directory objects and how to administer them.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
NIS+ Directories
NIS+ directory objects are used to store information related to an NIS+ domain. For each NIS+ domain, there is a corresponding NIS+ directory structure. See Chapter 2, NIS+: An Introduction, for more information about NIS+ directories.
For a complete description of NIS+ directory-related commands and their syntax and options, see the NIS+ man pages.
Using the niscat Command With NIS+ Directories
The niscat -o command can be used to list the object properties of an NIS+ directory. To use it, you must have read access to the directory object itself.
Listing the Object Properties of an NIS+ Directory
To list the object properties of a directory, use niscat -o and the directory's name:
niscat -o directory-name |
For example:
rootmaster# niscat -o doc.com. Object Name : doc Owner : rootmaster.doc.com. Group : Domain : Com. Access Rights : r---rmcdr---r--- Time to Live : 24:0:0 Object Type : DIRECTORY . . |
Using the nisls Command With Directories
The nisls command lists the contents of an NIS+ directory. To use it, you must have read rights to the directory object.
To display in terse format, use:
nisls [-dgLmMR] directory-name |
To display in verbose format, use:
nisls -l [-gm] [-dLMR] directory-name |
|
Option |
Purpose |
|---|---|
|
-d |
Directory object. Instead of listing a directory's contents, treat it like another object. |
|
-L |
Links. If the directory name is actually a link, the command follows the link and displays information about the linked directory. |
|
-M |
Master. Get the information from the master server only. Although this provides the most up-to-date information, it may take longer if the master server is busy. |
|
-R |
Recursive. List directories recursively. That is, if a directory contains other directories, their contents are displayed as well. |
|
-l |
Long. Display information in long format. Long format displays an object's type, creation time, owner, and access rights. |
|
-g |
Group. When displaying information in long format, display the directory's group owner instead of its owner. |
|
-m |
Modification time. When displaying information in long format, display the directory's modification time instead of its creation time. |
Listing the Contents of an NIS+ Directory – Terse
To list the contents of a directory in the default short format, use one or more of the options listed below and a directory name. If you don't supply a directory name, NIS+ will use the default directory.
nisls [-dLMR] directory-name |
or
nisls [-dLMR] |
For example, this instance of nisls is entered from the root master server of the root domain doc.com.:
rootmaster% nisls doc.com.: org_dir groups_dir |
Here is another example entered from the root master server:
rootmaster% nisls -R sales.doc.com. sales.doc.com.: org_dir groups_dir groups_dir.sales.doc.com.: admin org_dir.sales.doc.com.: auto_master auto_home bootparams cred . |
Listing the Contents of an NIS+ Directory – Verbose
To list the contents of a directory in the verbose format, use the -l option and one or more of the options listed below. The -g and -m options modify the attributes that are displayed. If you don't supply a directory name, NIS+ will use the default directory.
nisls -l [-gm] [-dLMR] directory-name |
or
nisls -l [-gm] [-dLMR] |
Here is an example, entered from the master server of the root domain doc.com.:
rootmaster% nisls -l doc.com. D r---rmcdr---r--- rootmaster.doc.com. date org_dir D r---rmcdr---r--- rootmaster.doc.com. date groups_dir |
nismkdir Command
Note –
This section describes how to add a non-root server to an existing domain using the nismkdir command. An easier way to do this is with the nisserver script as described in Chapter 4, Configuring NIS+ With Scripts
The nismkdir command creates a non-root NIS+ directory and associates it with a master server. (To create a root directory, use the nisinit -r command, described in nisinit Command. The nismkdir command can also be used to add a replica to an existing directory.
There are several prerequisites to creating an NIS+ directory, as well as several related tasks.
To create a directory, use:
nismkdir [-m master-server] \ directory-name |
To add a replica to an existing directory, use:
nismkdir -s replica-server \ directory-name nismkdir -s replica-server \ org_dir.directory-name nismkdir -s replica-server \ groups_dir.directory-name |
Creating an NIS+ Directory
To create a directory, you must have create rights to its parent directory on the domain master server. First use the -m option to identify the master server and then the -s option to identify the replica, use:
nismkdir -m master directory nismkdir -s replica directory |
Always run nismkdir on the master server. Never run nismkdir on the replica machine. Running nismkdir on a replica creates communications problems between the master and the replica.
This example creates the sales.doc.com. directory and specifies its master server, smaster.doc.com. and its replica, rep1.doc.com.. It is entered from the root master server.
rootmaster% nismkdir -m smaster.doc.com. sales.doc.com. rootmaster% nismkdir -m smaster.doc.com. org_dir.sales.doc.com. rootmaster% nismkdir -m smaster.doc.com. groups_dir.sales.doc.com. rootmaster% nismkdir -s rep1.doc.com. sales.doc.com. rootmaster% nismkdir -s rep1.doc.com. org_dir.sales.doc.com. rootmaster% nismkdir -s rep1.doc.com. groups_dir.sales.doc.com. |
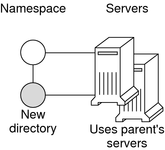
The nismkdir command allows you to use the parent directory's servers for the new directory instead of specifying its own. However, this should not be done except in the case of small networks. Here are two examples:
The first example creates the sales.doc.com. directory and associates it with its parent directory's master and replica servers.
rootmaster% nismkdir sales.doc.com |
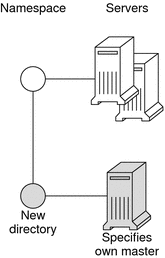
The second example creates the sales.doc.com. directory and specifies its own master server, smaster.doc.com.
rootmaster% nismkdir -m smaster.doc.com. sales.doc.com. |
Since no replica server is specified, the new directory will have only a master server until you use nismkdir again to assign it a replica. If the sales.doc.com. domain already existed, the nismkdir command as shown above would have made salesmaster.doc.com. its new master server and would have relegated its old master server to a replica.
Adding an NIS+ Replica to an Existing Directory
This section describes how to add a replica server to an existing system using the nismkdir command. An easier way to do this is with the nisserver script.
Keep in mind the following principles:
-
Root domain servers reside in (are part of) the root domain.
-
Subdomain servers reside in (are part of) the parent domain immediately above the subdomain in the hierarchy. For example, if a namespace has one root domain named prime and a subdomain named sub1:
-
The master and replica servers that serve the prime domain are themselves part of the prime domain because prime is the root domain.
-
The master and replica servers that serve the sub1 subdomain are also part of the prime domain because prime is the parent of sub1.
-
-
While it is possible for a master or replica server to serve more than one domain, doing so is not recommended.
To assign a new replica server to an existing directory, use nismkdir on the master server with the -s option and the name of the existing directory, org_dir, and groups_dir:
nismkdir -s replica-server existing-directory-name nismkdir -s replica-server org_dir. existing-directory-name nismkdir -s replica-server groups_dir. existing-directory-name |
The nismkdir command realizes that the directory already exists, so it does not recreate it. It only assigns it the additional replica. Here is an example with rep1 being the name of the new replica machine:
rootmaster% nismkdir -s rep1.doc.com. doc.com. rootmaster% nismkdir -s rep1.doc.com. org_dir.doc.com. rootmaster% nismkdir -s rep1.doc.com. groups_dir.doc.com. |
Always run nismkdir on the master server. Never run nismkdir on the replica machine. Running nismkdir on a replica creates communications problems between the master and the replica.
After running the three iterations of nismkdir as shown above, you need to run nisping from the master server on the three directories:
rootmaster# nisping doc.com. rootmaster# nisping org_dir.doc.com. rootmaster# nisping group_dir.doc.com. |
You should see results similar to these:
rootmaster# nisping doc.com. Pinging replicas serving directory doc.com. : Master server is rootmaster.doc.com. Last update occurred at Wed Nov 18 19:54:38 1995 Replica server is rep1.doc.com. Last update seen was Wed Nov 18 11:24:32 1995 Pinging ... rep1.doc.com |
It is good practice to include nisping commands for each of these three directories in the master server's cron file so that each directory is “pinged” at least once every 24 hours after being updated.
nisrmdir Command
The nisrmdir command can remove a directory or simply dissociate a replica server from a directory. (When a directory is removed or disassociated from a replica server, that machine no longer functions as an NIS+ replica server for that NIS+ domain.)
When it removes a directory, NIS+ first disassociates the master and replica servers from the directory, and then removes the directory.
-
To remove the directory, you must have destroy rights to its parent directory.
-
To dissociate a replica server from a directory, you must have modify rights to the directory.
If problems occur, see Removal or Dissociation of NIS+ Directory From Replica Fails.
Removing an NIS+ Directory
To remove an entire directory and dissociate its master and replica servers, use the nisrmdir command without any options:
nisrmdir directory-name nisping domain |
This example removes the manf.doc.com. directory from beneath the doc.com. directory:
rootmaster% nisrmdir manf.doc.com. rootmaster% nisping doc.com. |
Disassociating a Replica From an NIS+ Directory
To disassociate a replica server from a directory, you must first remove the directory's org_dir and groups_dir subdirectories. To do this, use the nisrmdir command with the -s option. After each of the subdirectories are removed, you must run nisping on parent domain.
nisrmdir -s replicanameorg_dir.domain nisrmdir -s replicanamegroups_dir.domain nisrmdir -s replicaname domain nisping domain |
This example disassociates the manfreplica1 server from the manf.doc.com. directory:
rootmaster% nisrmdir -s manfreplica1 org_dir.manf.doc.com. rootmaster% nisrmdir -s manfreplica1 groups_dir.manf.doc.com. rootmaster% nisrmdir -s manfreplica1 manf.doc.com. rootmaster% nisping manf.doc.com. |
If the replica server you are trying to dissociate is down or out of communication, the nisrmdir -s command returns a Cannot remove replicaname: attempt to remove a non-empty table error message. In such cases, you can run nisrmdir -f -s replicaname on the master to force the dissociation. Note, however, that if you use nisrmdir -f -s to dissociate an out-of-communication replica, you must run nisrmdir -f -s again as soon as the replica is back on line in order to clean up the replica's /var/nis file system. If you fail to rerun nisrmdir -f -s replicaname when the replica is back in service, the old out-of-date information left on the replica could cause problems.
nisrm Command
The nisrm command is similar to the standard rm system command. It removes any NIS+ object from the namespace, except directories and nonempty tables. To use the nisrm command, you must have destroy rights to the object. However, if you don't, you can use the -f option, which tries to force the operation in spite of permissions.
You can remove group objects with the nisgrpadm -d command (see Deleting an NIS+ Group), and you can empty tables with nistbladm -r or nistbladm -R (see Deleting an NIS+ Table).
To remove a nondirectory object, use:
nisrm [-if] object-name |
|
Option |
Purpose |
|---|---|
|
-i |
Inquire. Asks for confirmation prior to removing an object. If the object-name you provide is not fully qualified, this option is used automatically. |
|
-f |
Force. Attempts to force a removal even if you don't have the proper permissions. It attempts to change the permission by using the nischmod command, and then tries to remove the object again. |
Removing NIS+ Nondirectory Objects
To remove nondirectory objects, use the nisrm command and provide the object names:
nisrm object-name... |
This example removes a group and a table from the namespace:
rootmaster% nisrm -i admins.doc.com. groups.org_dir.doc.com. Remove admins.doc.com.? y Remove groups.org_dir.doc.com.? y |
rpc.nisd Daemon
When you enable the NIS+ service, the rpc.nisd daemon starts. You don't need any access rights to start the NIS+ daemon, but you should be aware of all its prerequisites and related tasks. They are described in Setting Up NIS+ Root Servers.
Note –
The NIS+ service is managed by the Service Management Facility (SMF). Administrative actions on this service, such as enabling, disabling, or restarting, can be performed by using the svcadm command. See NIS+ and the Service Management Facility for more information about using SMF with NIS+. For an overview of the SMF, refer to Chapter 18, Managing Services (Overview), in System Administration Guide: Basic Administration. Also refer to the svcadm(1M) and svcs(1) man pages for more details.
Starting the rpc.nisd Daemon
When you enable the NIS+ service, the rpc.nisd daemon starts. Use the svcadm enable command to start the service.
rootmaster# svcadm enable /network/rpc/nisplus:default |
Stopping the rpc.nisd Daemon
When you disable the NIS+ service, the rpc.nisd daemon stops. Use the svcs command to determine the FMRI and the state of the service. Then use the svcadm disable command to stop the service, whether the service is running in normal or NIS-compatibility mode.
rootmaster# svcs \*nisplus\* STATE STIME FMRI online Oct_07 svc:/network/rpc/nisplus:default rootmaster# svcadm disable /network/rpc/nisplus:default |
Changing rpc.nisd Syntax Options
By default, the NIS+ daemon starts with security level 2 and runs in normal mode. If you want to include specific options when you invoke the rpc.nisd daemon with the Service Management Facility, modify the /lib/svc/method/nisplus file to include the desired options. See NIS+ and the Service Management Facility for more information.
Descriptions of some common rpc.nisd syntax options are included in Table 18–3.
Table 18–3 Common rpc.nisd Syntax Options|
Option |
Purpose |
|---|---|
|
-Y |
Specifies that the daemon run in NIS-compatibility mode, which enables it to answer requests from NIS clients. You can start the NIS+ daemon in NIS-compatibility mode in any server, including the root master. |
|
-B |
Adds DNS forwarding capabilities to an NIS+ daemon running in NIS-compatibility mode. This option requires that the /etc/resolv.conf file be set up for communication with a DNS nameserver. |
|
-S security-level |
Specifies a security level, where 0 means no NIS+ security and 2 provides full NIS+ security. (Level 1 is not supported.) |
|
-F |
Forces a checkpoint of the directory served by the daemon. This has the side effect of emptying the directory's transaction log and freeing disk space. |
nisinit Command
This section describes how to initialize a machine client using the nisinit command. An easier way to do this is with the nisclient script as described in Setting Up NIS+ Client Machines.
The nisinit command initializes a machine to be an NIS+ client or server. As with the rpc.nisd command, you don't need any access rights to use the nisinit command, but you should be aware of its prerequisites and related tasks. These are described in Initializing an NIS+ Client.
Three Methods to Initialize an NIS+ Client
You can initialize a client in three different ways:
-
By host name
-
By broadcast
-
By cold-start file
Each way has different prerequisites and associated tasks. For instance, before you can initialize a client by host name, the client's /etc/hosts file must list the host name you will use and the nsswitch.conf file must have files as the first choice on the hosts line.
Note –
Prior to the Solaris 10 7/07 release, before you can initialize an IPv6 client by host name, the client's /etc/inet/ipnodes file must list the host name you will use. For IPv6 addresses, specify ipnodes as the first choice on the hosts line of the nsswitch.conf file.
Following is a summary of the steps that use the nisinit command.
To initialize a client by host name, use the -c and -H options, and include the name of the server from which the client will obtain its cold-start file:
nisinit -c -H hostname |
To initialize a client by cold-start file, use the -c and -C options, and provide the name of the cold-start file:
nisinit -c -C filename |
To initialize a client by broadcast, use the -c and -B options:
nisinit -c -B |
Initializing the NIS+ Root Master Server
To initialize the root master server, use the nisinit -rcommand:
nisinit -r |
You will need the following information
-
The superuser password of the machine that will become the root master server.
-
The name of the new root domain. The root domain name must have at least two elements (labels) and end in a dot (for example, something.com.). The last element must be either an Internet organizational name (as shown in Table 18–4), or a two or three character geographic identifier such as .jp. for Japan.
|
Domain |
Purpose |
|---|---|
|
com |
Commercial organizations |
|
edu |
Educational institutions |
|
gov |
Government institutions |
|
mil |
Military groups |
|
net |
Major network support centers |
|
org |
Nonprofit organizations and others |
|
int |
International organizations |
nis_cachemgr Daemon
The nis_cachemgr should run on all NIS+ clients. The cache manager maintains a cache of location information about the NIS+ servers that support the most frequently used directories in the namespace, including transport addresses, authentication information, and a time-to-live value.
At startup, the cache manager obtains its initial information from the client's cold-start file, and downloads it into the /var/nis/NIS_SHARED_DIRCACHE file.
The cache manager makes requests as a client machine. Make sure the client machine has the proper credentials, or instead of improving performance, the cache manager will degrade it.
Starting and Stopping the NIS+ Cache Manager
When using the Service Management Facility (SMF), the cache manager has a dependency on the NIS+ service, so cache manager starts and stops along with the NIS+ service. Use the svcadm command to start, stop, or restart the NIS+ service.
client% svcadm enable /network/rpc/nisplus:default client% svcadm disable /network/rpc/nisplus:default client% svcadm restart /network/rpc/nisplus:default |
When you stop and start the NIS+ service, the cache manager is restarted but it retains the information in the /var/nis/NIS_SHARED_DIRCACHE file. The information in the cold-start file is simply appended to the existing information in the cache file. Use the -i option to clear the cache file and re-initialize it from the contents of the client's cold-start file.
nisshowcache Command
The nisshowcache command displays the contents of a client's directory cache.
Displaying the Contents of the NIS+ Cache
The nisshowcache command is located in /usr/lib/nis. It displays only the cache header and the directory names. Here is an example entered from the root master server:
rootmaster# /usr/lib/nis/nisshowcache -v Cold Start directory: Name : doc.com. Type : NIS Master Server : Name : rootmaster.doc.com. Public Key : Diffie-Hellman (192 bits) Universal addresses (3) . . Replicate: Name : rootreplica1.doc.com. Public Key : Diffie-Hellman (192 bits) Universal addresses (3) . . . Time to live : 12:0:0 Default Access Rights : |
Pinging and Checkpointing in NIS+
When a change is made to the NIS+ data set, that change is made in the memory of the master server for the NIS+ domain (or subdomain). A record of the change is also logged in the master server's transaction log (/var/nis/data/trans.log).
Normally, the master server transfers a change in the NIS+ data set to the domain's replica servers 120 seconds (2 minutes) after the change was made. This transfer process is called pinging. When the master server pings a replica, it updates the replica's data set with the change. The changed NIS+ data now resides in memory of the master and replica servers.
If the automatic ping process fails to update one or more replica servers, you need to manually force a ping as described in Forcing a Ping in NIS+. If you suspect that a replica has not been correctly updated with the most current NIS+ data, you can check when the replica was last updated as described in Displaying When NIS+ Replicas Were Last Updated.
Changes to the NIS+ data set stored in server memory and recorded in the transaction log need to be written into the NIS+ tables stored on disk. The process of updating the NIS+ tables is called checkpointing.
Checkpointing is not an automatic process. You must issue the checkpoint command as described in Checkpointing an NIS+ Directory.
nisping Command
The nisping command is used to:
-
Display when a replica was last pinged as described in Displaying When NIS+ Replicas Were Last Updated.
-
Force the master server to ping a replica if the automatic ping cycle has not been successful as described in Forcing a Ping in NIS+.
-
Checkpoint servers as described in Checkpointing an NIS+ Directory.
Displaying When NIS+ Replicas Were Last Updated
When used with the -u option, the nisping command displays the update times for the master and replicas of the local domain.
/usr/lib/nis/nisping -u [domain] |
To display the last updates in some other domain, specify the domain name in the command line. Note that when used with the -u option, the nisping command does not actually ping any replicas.
For example, to display the most recent replica update times for the local doc.com. domain, you would enter:
rootmaster# /usr/lib/nisping -u Last updates for directory doc.com.: Master server is rootmaster.doc.com. Last update occurred at Wed Nov 25 10:53:37 1992 Replica server is rootreplica1.doc.com. Last update seen was Wed Nov 25 10:53:37 1992 |
Forcing a Ping in NIS+
If the nisping -u command reveals that a replica has not been properly updated, you can use the nisping command to force the master server to ping all the replicas in a domain, or one replica in particular.
To ping all the replicas, use the nisping command without options:
/usr/lib/nis/nisping |
This forces the master server to ping all the replicas in the domain. Here is an example that pings all the replicas of the local doc.com. domain:
rootmaster# /usr/lib/nis/nisping Pinging replicas serving directory doc.com.: Master server is rootmaster.doc.com. Last update occurred at Wed Nov 25 10:53:37 1992 Replica server is rootreplica1.doc.com. Last update seen was Wed Nov 18 11:24:32 1992 Pinging ... rootreplica1.doc.com. |
To ping all the replicas in a domain other than the local domain, append a domain name:
/usr/lib/nis/nisping domainname |
You can also ping all the tables in all the directories on a single specified host. To ping all the tables in all the directories of a particular host, use the -a option:
/usr/lib/nis/nisping -a hostname |
Checkpointing an NIS+ Directory
Each domain and subdomain should be checkpointed at least once every 24 hour, or more often if the transaction log grows too large in relationship to swap space or total disk space.
Note –
Checkpointing large domains, or any domain with a large transaction log, is a time-consuming process which ties up NIS+ servers and slows NIS+ service. While a server is checkpointing, it will still answer requests for service, but it will be unavailable for updates. If possible, checkpoint operations should be scheduled for times when system use is low. You can use the cron file to schedule checkpoint operations.
To perform a checkpoint operation, run nisping -C on the domain's master server. It is good practice to first ping all replicas before checkpointing. This ensures that the replicas are checkpointing data that is current and up to date.
-
To checkpoint a particular directory, run the nisping command with the -C directoryname option. For example,
rootmaster# /usr/lib/nis/nisping rootmaster# /usr/lib/nis/nisping -C org_dir
-
To checkpoint all the directories in the local domain, run the nisping command with the -C -a options. For example,
rootmaster# /usr/lib/nis/nisping rootmaster# /usr/lib/nis/nisping -C -a
Once a server has transferred information from the server's transaction log to the appropriate NIS+ tables, the transactions in the log file are erased to conserve disk space.
For example, to checkpoint all of the directories in the doc.com. domain, you would enter:
rootmaster# /usr/lib/nis/nisping -C -a Checkpointing replicas serving directory doc.com. : Master server is rootmaster.doc.com. Last update occurred at Wed May 25 10:53:37 1995 Master server is rootmaster.doc.com. checkpoint has been scheduled with rootmaster.doc.com. Replica server is rootreplica1.doc.com. Last update seen was Wed May 25 10:53:37 1995 Replica server is rootreplica1.doc.com. checkpoint has been scheduled with rootmaster.doc.com. |
nislog Command
The nislog command displays the contents of the transaction log.
/usr/sbin/nislog /usr/sbin/nislog -h [number] /usr/sbin/nislog -t [number] |
|
Option |
Purpose |
|---|---|
|
-h [num] |
Display transactions starting with the head (beginning) of the log. If the number is omitted, the display begins with the first transaction. If the number 0 is entered, only the log header is displayed. |
|
-t [num] |
Display transactions starting backward from the end (tail) of the log. If the number is omitted, the display begins with the last transaction. If the number 0 is entered, only the log header is displayed. |
|
-v |
Verbose mode. |
Displaying the Contents of the NIS+ Transaction Log
Each transaction consists of two parts: the particulars of the transaction and a copy of an object definition.
Here is an example that shows the transaction log entry that was made when the doc.com. directory was first created. “XID” refers to the transaction ID.
rootmaster# /usr/sbin/nislog -h 1 NIS Log printing facility. NIS Log dump: Log state : STABLE Number of updates : 48 Current XID : 39 Size of log in bytes : 18432 ***UPDATES*** @@@@@@@@@@@@@@TRANSACTION@@@@@@@@@@@@@@ #00000, XID : 1 Time : Wed Nov 25 10:50:59 1992 Directory : doc.com. Entry type : ADD Name Entry timestamp : Wed Nov 25 10:50:59 1992 Principal : rootmaster.doc.com. Object name : org_dir.doc.com. ...................Object...................... Object Name : org_dir Owner : rootmaster.doc.com. Group : admin.doc.com. Domain : doc.com. Access Rights : r---rmcdr---r--- Time to Live : 24:0:0 Object Type : DIRECTORY Name : `org_dir.doc.com.' Type: NIS Master Server : rootmaster.doc.com. . . ................................................ @@@@@@@@@@@@@@TRANSACTION@@@@@@@@@@@@@@ #00000, XID : 2 |
nischttl Command
The nischttl command changes the time-to-live value of objects or entries in the namespace. This time-to-live value is used by the cache manager to determine when to expire a cache entry. You can specify the time-to-live in total number of seconds or in a combination of days, hours, minutes, and seconds.
The time-to-live values you assign objects or entries should depend on the stability of the object. If an object is prone to frequent change, give it a low time-to-live value. If it is steady, give it a high one. A high time-to-live is a week; a low one is less than a minute. Password entries should have time-to-live values of about 12 hours to accommodate one password change per day. Entries in tables that don't change much, such as those in the RPC table, can have values of several weeks.
To change the time-to-live of an object, you must have modify rights to that object. To change the time-to-live of a table entry, you must have modify rights to the table, entry, or columns you wish to modify.
To display the current time-to-live value of an object or table entry, use the nisdefaults -t command, described in Chapter 15, Administering NIS+ Access Rights.
To change the time-to-live value of objects, use:
nischttl time-to-live object-name |
or
nischttl [-L] time-to-live object-name |
To change the time-to-live value of entries, use:
nischttl time-to-live \ [column=value,...], \ table-name |
or
nischttl [-ALP] time-to-live \ [column=value,...], \ table-name |
Where time-to-live is expressed as:
-
Number of seconds. A number with no letter is interpreted as a number of seconds. Thus, 1234 for TTL would be interpreted as 1,234 seconds. A number followed by the letter s is also interpreted as a number of seconds. Thus, 987s for TTL would be interpreted as 987 seconds. When seconds are specified in combination with days, hours, or minutes, you must use the letter s to identify the seconds value.
-
Number of minutes. A number followed by the letter m is interpreted as a number of minutes. Thus, 90m for TTL would be interpreted as 90 minutes.
-
Number of hours. A number followed by the letter h is interpreted as a number of hours. Thus, 9h for TTL would be interpreted as 9 hours.
-
Number of days. A number followed by the letter d is interpreted as a number of days. Thus, 7d for TTL would be interpreted as 7 days.
These values may be used in combination. For example, a TTL value of 4d3h2m1s would specify a time to live of four days, three hours, two minutes, and one second.
The following flags may also be used with the nischttl command.
Table 18–6 nischttl Syntax Options|
Option |
Purpose |
|---|---|
|
A |
All. Apply the change to all the entries that match the column=value specifications that you supply. |
|
L |
Links. Follow links and apply the change to the linked object rather than the link itself. |
|
P |
Path. Follow the path until there is one entry that satisfies the condition. |
Changing the Time-to-Live of an NIS+ Object
To change the time-to-live of an object, type the nischttl command with the time-to-live value and the object-name. You can add the -L command to extend the change to linked objects.
nischttl -L time-to-live object-name |
You can specify the time-to-live in seconds by typing the number of seconds. Or you can specify a combination of days, hours, minutes, and seconds by using the suffixes s, m, h, and d to indicate the number of seconds, minutes, days, and hours. For example:
client% nischttl 86400 sales.doc.com. client% nischttl 24h sales.doc.com. client% nischttl 2d1h1m1s sales.doc.com. |
The first two commands change the time-to-live of the sales.doc.com. directory to 86,400 seconds, or 24 hours. The third command changes the time-to-live of all the entries in a hosts table to 2 days, 1 hour, 1 minute, and 1 second.
Changing the Time-to-Live of an NIS+ Table Entry
To change the time-to-live of entries, use the indexed entry format. You can use any of the options, -A, -L, or -P.
nischttl [-ALP] time-to-live \ [column=value,...], \ table-name |
Note –
C-shell users should use quotes to prevent the shell from interpreting the square brackets ([]) around the column value as a meta character.
These examples are similar to those above, but they change the value of table entries instead of objects:
client% nischttl 86400 '[uid=99],passwd.org_dir.doc.com.' client% nischttl 24h `[uid=99],passwd.org_dir.doc.com.' client% nischttl 2d1h1m1s `[name=fred],hosts.org_dir.doc.com.' |
Chapter 19 Administering NIS+ Tables
This chapter describes NIS+ tables and how to administer them. (See Table 10–1, for detailed descriptions of the default NIS+ tables.)
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
NIS+ Table Administration
Information used by NIS+ is stored in NIS+ tables. (See Chapter 23, Information in NIS+ Tables for a description of each default NIS+ system tables supplied in the Solaris software.)
For a complete description of NIS+ table-related commands and their syntax and options, see the NIS+ man pages.
Using the nistbladm Command With NIS+ Tables
Note –
Some NIS+ table administration tasks can be performed more easily with Solaris Management Console tools if you have them available.
The nistbladm command is the primary NIS+ table administration command. The nistbladm command is for use on NIS+ tables stored in an NIS+ directory object. With it, you can create, modify, and delete NIS+ tables and entries. To create a table, its directory must already exist. To add entries to the table, the table and columns must already be defined.
To create a table, you must have create rights to the directory under which you will create it. To delete a table, you must have destroy rights to the directory. To modify the contents of a table, whether to add, change, or delete entries, you must have modify rights to the table or the entries.
nistbladm Syntax Summary
The general syntax of the nistbladm command is:
nistbladm options \ [columspec | columnvalue] \ [tablename | indexedname] |
Where:
-
columnspec is a specification defining a column to be created in a table as described in Specifying NIS+ Table Columns.
-
columnvalue identifies a particular cell value in the table identified by tablename as described in nistbladm and NIS+ Column Values.
-
tablename is the name of the table. For example, hosts.org_dir.doc.com.
-
indexedname identifies a particular cell value in a certain table as described in nistbladm and NIS+ Column Values. In essence indexedname is the equivalent of columnvalue plus tablename.
|
Option |
Description |
|---|---|
|
-a | -A |
Add an entry to an existing NIS+ table. The -a option returns an error if execution of the command would result in overwritting any existing entry. The -A option forces execution of the command even if it results in overwriting an existing entry. (See Adding Entries to an NIS+ Table.) |
|
-D defaults |
Specify a different set of default properties when creating an object. (See the nistbladm man page for details.) |
|
-d |
Destroy a table. (See Deleting an NIS+ Table.) |
|
-c |
Create a table. (See Creating a New NIS+ Table.) |
|
-r | -R |
Remove one or more entries from an existing NIS+ table. The -r option returns an error if execution of the command would result in removal of more than one entry. The -R option forces execution of the command even if it results in removing multiple entries. (See Removing NIS+ Table Entries.) |
|
-m |
An obsoleted option for modifying table entries that is still supported for backwards compatibility. The -e and -E options are the preferred method for editing entries. |
|
-e | -E |
Edit an entry in an existing NIS+ table. The -e option returns an error if execution of the command would affect more than one entry. The -A option forces execution of the command even if it results in changing an existing entry in such a way as to overwrite a different entry. (See Modifying NIS+ Table Entries.) |
nistbladm and NIS+ Column Values
Column values are used to identify individual entries in tables using the format:
columname="value", \ columnname="value", ... |
Where:
-
columname is the name of a table column.
-
value is the contents of a particular cell within a column. That value is what identifies a table row. (When using column=value to create or modify table data, always enclose the value element in quotes.)
For example, suppose you had a hosts table that listed machine names and IP addresses.
Table 19–2 Example NIS+ Hosts Table|
IP address |
name |
aliases |
|---|---|---|
|
172.22.168.4 |
altair | |
|
172.22.168.119 |
deneb |
|
|
172.22.168.120 |
regulus |
dnsmaster |
|
172.22.168.121 |
regulus |
dnsmaster |
|
172.22.168.11 |
sirius |
In this example, your could identify the altair entry (row) in three different ways using the column=value of:
-
name=altair
-
address=172.22.168.4
-
name=altair,address=172.22.168.4
But notice in the table above that the machine regulus is multi-homed and has two IP addresses. In that case, the column=value of host=regulus identifies two rows.
To identify just the first regulus row, you would enter either:
-
address=172.22.168.120 or
-
address=172.22.168.120.,name=regulus,dnsmaster
Note –
Some nistbladm operations require that you enter a column=value pair for every column in the table.
nistbladm, Searchable NIS+ Columns, Keys, and Column Values
When an NIS+ table is created, one or more columns are designated searchable with either the S or the I flags as described in Specifying NIS+ Table Columns. You can use the niscat -o tablename command to display a list of a table's columns and their characteristics.
A table is keyed on its searchable columns. This means that each row in the table must have a unique combination of values in the searchable columns. For example, if a table has one searchable column, each table row must have a unique value in that column, no two rows can contain the same value.
For example, suppose you had a table containing one searchable column named city and a non-searchable column named country. The following rows would all be permitted:
|
City |
Country |
|---|---|
|
San Francisco |
United States |
|
Santa Fe |
United States |
|
Santiago |
Chile |
But you could not have two rows like:
|
City |
Country |
|---|---|
|
London |
Canada |
|
London |
England |
If a table has multiple searchable columns, it is the combination of values that must be unique. For example, suppose you had a table containing two searchable columns, Lastname, Firstname and a non-searchable column named city. The following rows would all be permitted:
|
Lastname |
Firstname |
City |
|---|---|---|
|
Kuznetsov |
Sergei |
Odessa |
|
Kuznetsov |
Rima |
Odessa |
|
Sergei |
Alex |
Odessa |
But you could not have two rows like this:
|
Lastname |
Firstname |
City |
|---|---|---|
|
Kuznetsov |
Rima |
Odessa |
|
Kuznetsov |
Rima |
Chelm |
NIS+ commands use the values in the searchable columns to identify specific table rows.
nistbladm and Indexed NIS+ Names
In the context of table administration, an NIS+ indexed name is a name that combines a table name with column value search criteria to identify and select particular entries in a table. Indexed names use the format:
[search_criteria],tablename.directory |
Note that search_criteria must be enclosed in square brackets [ ]. The search_criteria use the format:
columname=value, \ columname=value,... |
Where columname=value pairs are column values from the table's searchable columns as described in nistbladm and NIS+ Column Values.
For example, to identify the altair entry in Table 19–2 you could use the indexed name:
[addr=172.22.168.4,cname=altair],hosts.org_dir.doc.com. |
The nistbladm -R command allows you to remove all the entries in a table by using the two square brackets with nothing between them [ ] as a wildcard specifying all table rows.
nistbladm and NIS+ Groups
In a Solaris-NIS+ environment, there are three types of groups:
-
UNIX groups. Information about UNIX groups is stored in the groups.org_dir table. Use nistbladm to administer UNIX group information.
-
Netgroups. Information about net groups is stored in the netgroups.org_dir table. Use nistbladm to administer net group information.
-
NIS+ groups. Information about NIS+ groups is stored in one or more tables in the groups_dir directory object. Use nisgrpadm to administer NIS+ group information.
Note –
Do not use nistbladm to administer NIS+ groups.
(See Solaris Groups and NIS+ Groups for more information on the different types of groups and how to work with them.)
Creating a New NIS+ Table
An NIS+ table must have at least one column and at least one of its columns must be searchable. To create an NIS+ table, use the nistbladm command with the -c option:
nistbladm -c tabletype columnspec \ ... tablename |
Where:
-
Tabletype is simply a name that identifies a class of tables to which this table belongs. You can use any name you choose.
-
A columnspec specifies the name and characteristics of each column in a new table. Enter one columnspec for each column you want in your new table. Separate the columnspecs with spaces, as shown in the following example.
nistbladm -c tabletype columnspec columnspec \ columnspec tablename |
Columnspec formats are described in Specifying NIS+ Table Columns, below.
Specifying NIS+ Table Columns
Each columnspec entry has two to four components in the format:
name=type,rights: |
|
Component |
Description |
|---|---|
|
name |
Name of the column |
|
= |
An equal sign which is required. |
|
type |
[Optional] The type of column specified by the letters S, I or C (see Table 19–4). This component is optional. If no type is specified, the column becomes the default type. |
|
rights |
[Optional] Access rights. These access rights are over and above those granted to the table as a whole or to specific entries. If no access is specified, the column's access rights are those granted to the table as a whole, or to the entry. The syntax for access rights is described in Specifying NIS+ Access Rights in Commands. |
A column can be one of the following types.
Table 19–4 NIS+ Table Column Types|
Type |
Description |
|---|---|
|
|
No column type specified after the = sign. The column is neither searchable nor encrypted. |
|
-S |
Searchable. |
|
-I |
Searchable, but case-insensitive. When NIS+ commands search through the column, they will ignore case. |
|
-C |
Encrypted. |
NIS+ commands search through the column and identify individual table rows based on the contents of the searchable columns. Searchable columns are designated with either the S or the I option. In database terminology, a searchable column is a key. The first column in each table must be searchable. The remaining columns do not have to be searchable. Because the table is keyed on the searchable columns, if you have more than one searchable column, they must be the first and subsequent columns and not skip any columns. For example, if only one column in a table is searchable, it has to be the first column. If two columns are searchable, they must be the first two columns. (See nistbladm, Searchable NIS+ Columns, Keys, and Column Values for more information on searchable columns.)
If you specify only access rights, you don't need to use a comma. If you include one or more of the -S, -I, or -C flags, add a comma before the access rights.
In the example below, a table is created with the addition of column-specific access rights applied to the first two columns:
master% nistbladm -c depts Name=I,w+m Site=w+m Name=C \ divs.mydir.doc.com. |
For more information about specifying column access rights when creating a table, see Setting Column Rights When Creating an NIS+ Table.
Note –
NIS+ assumes that all column entries are null terminated. Applications and routines that write information to NIS+ tables must be configured to null terminate each column entry.
Creating Additional NIS+ Automount Tables
If you are creating an automount table, the table can have only two columns. The first column must be named key and the second column must be named value. For example, to create an automount table named auto1, you would enter:
master% nistbladm -c key-value key=S value= auto1.org_dir.doc.com. |
Deleting an NIS+ Table
To delete a table, use the -d option and enter the table name:
nistbladm -d tablename |
The table must be empty before you can delete it (see Removing NIS+ Table Entries). This example deletes the divs table from the doc.com. directory:
rootmaster% nistbladm -d divs.doc.com. |
Adding Entries to an NIS+ Table
To add new entries (rows) to a table, use nistbladm with either the -a or -A options followed by either one or more column=value pairs and the table name or an indexed name as described in nistbladm and Indexed NIS+ Names.
nistbladm [-a | -A] indexedname nistbladm [-a | -A] column="value" \ column="value" \ ... tablename |
When adding new entry rows to a table with either -a or -A:
-
Always enclose the value element in quotes. For example, to add an entry where the value of the cname column is deneb, the column=value pair would look like: cname="deneb".
-
You must specify a value for every column in the table.
-
To specify that a column in the entry row you are adding is empty use column=" ". In other words, for the value, enclose a space between the quote marks.
Note –
NIS+ is a naming service and its tables are designed to store references to objects, not the objects themselves. NIS+ is optimized to support 10,000 objects with a combined total size of all tables not more than 10M bytes. NIS+ does not support individual tables where the sum of field sizes in a single column are greater than approximately 7k. If a table is too large, rpc.nisd may fail.
Adding an NIS+ Table Entry With the -a Option
The -a option adds an entry to a table unless the entry already exists, in which case it returns an error. An entry is defined as existing if its values in the searchable columns exactly match the values in the new entry's searchable columns. (The values in non-searchable columns are not taken into account.)
To use the -a option, you must specify a value for every column in the table:
nistbladm -a column="value" \ column="value" \ ... tablename nistbladm -a indexedname |
(To list the names and characteristics of table columns, use the niscat -o tablename command.)
For example, to add a new row to a table named depts using column=value pairs, you would enter:
rootmaster% nistbladm -a Name='R&D' Site='SanFran' \ Name='vattel' depts.doc.com. |
To add the same entry using an indexed name, you would enter:
rootmaster% nistbladm -a [Name='R&D',Site='SanFran',\ Name='vattel'],depts.doc.com. |
Both examples would produce a table row that looked like this:
|
Dept |
Site |
Name |
|---|---|---|
|
R&D |
SanFran |
vattel |
C-shell users should also use quotes to set off expressions using square brackets.
You can only add one entry with each instance of the nistbladm command. You must run nistbladm once for each entry row you want to add.
If a table row already exists with values in each column that are identical to the entry you are trying to create, nistbladm -a will return an error. You cannot have two identical entry rows in a table. In this context, rows are considered identical if the values in the searchable columns are identical, the values in none search able columns are not considered.
For example, if the Dept and Site columns are searchable, and the Name column is not searchable, nistbladm considers the following two rows to be identical:
|
Dept (searchable) |
Site (searchable) |
Name (not searchable) |
|---|---|---|
|
Sales |
Vancouver |
Hosteen |
|
Sales |
Vancouver |
Lincoln |
In this example, nistbladm -a would not allow you to create the Sales Vancouver Lincoln row.
However if just some of the searchable columns have values identical to the entry you are trying to create, nistbladm -a will create a new entry as specified. For example, you could run the following commands to create two similar, but not identical, rows in a depts table:
rootmaster% nistbladm -a Dept='Sales' \ Site='Vancouver' Name='hosteen' staff.doc.com. rootmaster% nistbladm -a Dept='Sales' \ Site='SanFran' Name='lincoln' staff.doc.com. |
Which would produce rows that had some, but not all identical values in the searchable columns:
|
Dept |
Site |
Name |
|---|---|---|
|
Sales |
Vancouver |
hosteen |
|
Sales |
SanFran |
lincoln |
Adding an NIS+ Table Entry With the -A Option
The -A option is designed for applications where you need to force nistbladm to overwrite an existing entry. Like the -a option, -A adds a new entry to a table. However, if the entry already exists, instead of exiting with an error, it overwrites the existing entry row.
When using the -A option, you must specify all columns in the entry.
For example, suppose the following table exists and the Dept and Site columns are searchable:
|
Dept (searchable) |
Site (searchable) |
Name |
|---|---|---|
|
Sales |
SanFran |
Lincoln |
Now you run the following command:
rootmaster% nistbladm -A Name=Sales Site=SanFran \ Name=Tsosulu depts.doc.com. |
The -a option would have returned an error, since the entry specified by Name=Sales Site=SanFran already exists. But the -A option allows you to overwrite the existing row.
|
Dept |
Site |
Name |
|---|---|---|
|
Sales |
SanFran |
Tsosulu |
Modifying NIS+ Table Entries
Existing table entries are edited (modified) using either the -e or -E options. The Solaris release also supports use of the -m option for backwards compatibility with earlier releases. (All new applications and command line operations should use either the -e or -E options.)
To edit an existing entry (row) in a table, use nistbladm with either the -e or -E options followed by one or more column=value pairs that specify the new values and ending with an indexed name that identifies a particular row in a table as described in nistbladm and Indexed NIS+ Names.
nistbladm [-e | -E] column="value" \ column="value" \ ... indexedname |
When adding new entry rows to a table with either -e or -E:
-
Always enclose the value element in quotes. For example, to change the value of the cname column to deneb, the column=value pair would look like: cname="deneb".
-
You can only edit values in searchable columns one entry (row) at a time.
-
To specify that a column in the entry row that you are editing be empty, use column=" ". In other words, for the value, enclose a space between the quote marks.
Editing an NIS+ Table Entry With the -e Option
The -e option edits an entry in a table unless doing so would result in changing values in searchable columns in more than one entry row, in which case it returns an error. (The values in non-searchable columns are not taken into account.)
nistbladm column="value" \ column="value" \ ... indexedname |
To use the -e option, you only need to specify the column values you are changing.
For example, suppose you had the table:
|
Dept |
Site |
Name |
|---|---|---|
|
Sales |
SanFran |
Tsosulu |
To change the value of the Name column to Chandar, you would enter:
master% nistbladm -e Name="Chandar" [Dept='Sales',Site='SanFran'],\ depts.doc.com. |
Now the table looks like this:
|
Dept |
Site |
Name |
|---|---|---|
|
Sales |
SanFran |
Chandar |
(Note that in the example above, the indexed name did not need to include the Name column because in these examples that column is not searchable.)
C-shell users should also use quotes to set off expressions using square brackets.
You can use the -e option to edit the values in searchable columns so long as the new values you specify affect only the single row identified by the indexed name. For example, to change the department to Manf, you would enter:
master% nistbladm -e Dept="Manf" [Dept='Sales',Site='SanFran'],\ depts.doc.com. |
|
Dept (searchable) |
Site (searchable) |
Name |
|---|---|---|
|
Manf |
SanFran |
Chandar |
However, if an entry row already existed with Manf and SanFran in the searchable columns, the -e option would return an error.
You can specify changes to multiple columns so long as they all apply to a single entry row. For example, to change both the Dept and Name values, you would enter:
master% nistbladm -e Dept="Manf" Name=”Thi” \ [Dept='Sales',Site='SanFran'],depts.doc.com. |
|
Dept (searchable) |
Site (searchable) |
Name |
|---|---|---|
|
Manf |
SanFran |
Thi |
Editing an NIS+ Table Entry With the -E Option
The -E option is designed for applications where you need to force nistbladm to overwrite an existing entry even if doing so will affect more than one entry.
For example, suppose your table had the following rows:
|
Dept (searchable) |
Site (searchable) |
Name |
|---|---|---|
|
Sales |
SanFran |
Chandar |
|
Sales |
Alameda |
Achmed |
Now you run the following command:
master% nistbladm -E Site="Alameda” Mgr="Chu" \ [Div='Sales',Site='SanFran'],depts.doc.com. |
Which would change the Sales SanFran Chandar row to Sales Alameda Chu. But Sales Alameda are the key values identifying the Sales Alameda Achmed row, so that row would also be changed. The result would be a single row where once there had been two rows:
|
Dept (searchable) |
Site (searchable) |
Name |
|---|---|---|
|
Sales |
Alameda |
Chu |
The -e option would have returned an error, since the edit would affect more than one row. But the -E option allows you to affect more than one entry row.
Removing NIS+ Table Entries
-
To remove a single entry from a table, use the -r option as described in Removing NIS+ Single Table Entries.
-
To remove multiple entries from a table, use the -R option as described in Removing Multiple Entries From an NIS+ Table.
Removing NIS+ Single Table Entries
To remove a single entry from a table, use the -r option:
nistbladm -r indexed-name |
This example removes the Manf-1 entry from the depts table:
rootmaster% nistbladm -r [Dept=Manf-1,Site=Emeryville,Name=hosteen],\ depts.doc.com. |
You can specify as few column values as you wish. If NIS+ finds duplicates, it does not remove any entry and returns an error message instead. Thus, you could have removed the Manf-1 by specifying only the Site column value, as in this example:
rootmaster% nistbladm -r [Site=Emeryville],depts.doc.com. |
However, you could not have removed the Sales entry by specifying only the Site column value (SanFran), because two entries have that same value (R&D and Sales):
|
Dept |
Site |
Name |
|---|---|---|
|
R&D |
SanFran |
kuznetsov |
|
Sales |
SanFran |
jhill |
|
Manf-1 |
Emeryville |
hosteen |
|
Manf-2 |
Sausalito |
lincoln |
Removing Multiple Entries From an NIS+ Table
To remove multiple entries from a table, use the -R option:
nistbladm -R indexedname |
As with the -r option, you can specify as few column values as you wish. Unlike the -r option, however, if NIS+ finds duplicates, it removes all of them. You can find the name of a table's column by using the niscat -o command. This example removes all entries in which the Site is SanFran:
rootmaster% nistbladm -R [Site=SanFran],depts.doc.com. |
|
Dept |
Site |
Name |
|---|---|---|
|
Manf-1 |
Emeryville |
hosteen |
|
Manf-2 |
Sausalito |
lincoln |
You can use the -R option to remove all the entries from a table. Simply do not specify any column values between the square brackets, as in this example:
rootmaster% nistbladm -R [],depts.doc.com. |
When used with the nistbladm -R command, an empty set of square brackets is interpreted as a wildcard specifying all table rows.
niscat Command
The niscat command displays the contents of an NIS+ table. However, you can also use it to display the object properties of the table. You must have read rights to the table, entries, or columns that you wish to display.
niscat Command Syntax
To display the contents of a table, use:
niscat [-hM] tablename |
To display the object properties of a table, use:
niscat -o tablename niscat -o entry |
|
Option |
Description |
|---|---|
|
-h |
Header. Displays a header line above the table entries, listing the name of each column. |
|
-M |
Master. Displays only the entries of the table stored on the Master server. This ensures you get the most up-to-date information and should be used only for debugging. |
|
-o |
Object. Displays object information about the table, such as column names, properties, and servers. |
Displaying the Contents of an NIS+ Table
To display the contents of a table, use niscat with a table name:
niscat tablename |
This example displays the contents of the table named depts.
rootmaster% niscat -h depts.doc.com. #Name:Site:Name R&D:SanFran:kuznetsov Sales:SanFran:jhill Manf-1:Emeryville:hosteen Manf-2:Sausalito:lincoln |
Note –
The symbol *NP* indicates that you do not have permission to view that entry. Permissions are granted on a table, column, or entry (row) basis. For more on access permissions, see Chapter 15, Administering NIS+ Access Rights.
Displaying the Object Properties of an NIS+ Table or Entry
To list the object properties of a table, use niscat -o and the table's name:
niscat -o tablename.org_dir |
To display the object properties of a table entry, use niscat -o and specify the entry with an indexed name:
entry ::=column=value \ ... tablename | \ [column=value,...],\ tablename |
Here are two examples, one for a table and one for a table entry:
Table
rootmaster# niscat -o hosts.org_dir.doc.com. Object Name : hosts Owner : rootmaster.doc.com. Group : admin.doc.com. Domain : org_dir.doc.com. Access Rights : ----rmcdr---r--- Time to Live : 12:0:0 Object Type : TABLE Table Type : hosts_tbl Number of Columns : 4 Character Separator : Search Path : Columns : [0] Name : cname Attributes : (SEARCHABLE, TEXTUAL DATA, CASE INS Access Rights: ---------------- [1] Name : name Attributes : (SEARCHABLE, TEXTUAL DATA, CASE INS Access Rights: ---------------- [2] Name : addr Attributes : (SEARCHABLE, TEXTUAL DATA, CASE INS Access Rights: ---------------- [3] Name : comment Attributes : (TEXTUAL DATA) Access Rights: ---------------- |
Table entry
rootmaster# niscat -o [name=rootmaster],hosts.org_dir.doc.com. Object Name : hosts Owner : rootmaster.doc.com. Group : admin.doc.com. Domain : org_dir.doc.com. Access Rights : ----rmcdr---r--- Time to Live : 12:0:0 Object Type : ENTRY Entry data of type hosts_tbl Entry has 4 columns. . # |
nismatch and nisgrep Commands
The nismatch and nisgrep commands search through NIS+ tables for entries that match a particular string or regular expression, respectively. They display either the entries themselves or a count of how many entries matched. The differences between the nismatch and nisgrep commands are highlighted in Table 19–6 below.
Table 19–6 Characteristics of nismatch and nisgrep|
Characteristics |
nismatch |
nisgrep |
|---|---|---|
|
Search criteria |
Accepts text only |
Accepts regular expressions |
|
Speed |
Faster |
Slower |
|
Searches through |
Searchable columns only |
All columns, whether searchable or not |
|
Syntax of search criteria |
column=string ... tablename[ column= string,...], tablename |
column=exp ... tablename |
The tasks and examples in this section describe the syntax for both commands.
To use either command, you must have read access to the table you are searching through.
The examples in this section are based on the values in the following table, named depts.doc.com. Only the first two columns are searchable.
|
Name (S) |
Site (S) |
Name |
|---|---|---|
|
R&D |
SanFran |
kuznetsov |
|
Sales |
SanFran |
jhill |
|
Manf-1 |
Emeryville |
hosteen |
|
Manf-2 |
Sausalito |
lincoln |
|
Shipping-1 |
Emeryville |
tsosulu |
|
Shipping-2 |
Sausalito |
katabami |
|
Service |
Sparks |
franklin |
About Regular Expressions in NIS+
Regular expressions are combinations of text and symbols that you can use to search for special configurations of column values. For example, the regular expression `Hello' searches for a value that begins with Hello. When using a regular expression in the command line, be sure to enclose it in quotes, since many of the regular expression symbols have special meaning to the Bourne and C shells. For example:
rootmaster% nisgrep -h greeting='Hello' phrases.doc.com. |
The regular expression symbols are summarized in Table 19–7, below.
Table 19–7 Regular Expression Symbols in NIS+|
Symbol |
Description |
|---|---|
|
^string |
Find a value that begins with string. |
|
string $ |
Find a value that ends with string. |
|
. |
Find a value that has a number characters equal to the number of periods. |
|
[chars] |
Find a value that contains any of the characters in the brackets. |
|
*expr |
Find a value that has zero or more matches of the expr. |
|
+ |
Find something that appears one or more times. |
|
? |
Find any value. |
|
\'s-char' |
Find a special character, such as ? or $. |
|
x | y |
Find a character that is either x or y. |
nismatch and nisgrep Command Syntax
To search through the first column, use:
nismatch string tablename nisgrep reg-exp tablename |
To search through a particular column, use:
nismatch column=string tablename nisgrep column=reg-exp tablename |
To search through multiple columns, use:
nismatch column=string tablename ...\ nismatch [column=string,...],tablename nisgrep column=reg-exp ... \ tablename |
|
Option |
Description |
|---|---|
|
-c |
Count. Instead of the entries themselves, displays a count of the entries that matched the search criteria. |
|
-h |
Header. Displays a header line above the entries, listing the name of each column. |
|
-M |
Master. Displays only the entries of the table stored on the master server. This ensures you get the most up-to-date information and should be used only for debugging. |
Searching the First Column in NIS+
To search for a particular value in the first column of a table, simply enter the first column value and a tablename. In nismatch, the value must be a string. In nisgrep, the value must be a regular expression.
nismatch [-h] string tablename nisgrep [-h] reg-expression tablename |
This example searches through the depts table for all the entries whose first column has a value of R&D:
rootmaster% nismatch -h `R&D' depts.doc.com. rootmaster% nisgrep -h `R&D' depts.doc.com. |
Note –
Quotes are used in the 'R&D' expression above to prevent the shell from interpreting the ampersand (&) as a metacharacter.
Searching a Particular Column in NIS+
To search through a particular column other than the first, use the following syntax:
nismatch column=string tablename nisgrep column=reg-expression tablename |
This example searches through the depts table for all the entries whose second column has a value of SanFran:
rootmaster% nismatch -h Site=SanFran depts.doc.com. rootmaster% nisgrep -h Site=SanFran depts.doc.com. |
Searching Multiple Columns in NIS+
To search for entries with matches in two or more columns, use the following syntax:
nismatch [-h] [column=string, ... \ column=string,...],tablename nisgrep [-h] column=reg-exp ... \ tablename |
This example searches for entries whose second column has a value of SanFran and whose third column has a value of jhill:
rootmaster% nismatch -h [Site=SanFran,Name=jhill], depts.doc.com. rootmaster% nisgrep -h Site=SanFran Name=jhill depts.doc.com. |
nisln Command
The nisln command creates symbolic links between NIS+ objects such as tables and directories. All NIS+ administration commands accept the -L flag, which directs them to follow links between NIS+ objects.
Note –
Do not link table entries. Tables may be linked to other tables, but do not link an entry in one table to an entry in another table.
To create a link to another object (table or directory), you must have modify rights to the source object; that is, the one that will point to the other object or entry.
Never
link a cred table. Each org_dir directory should have its own cred table.
Do not use a link to some other org_dir cred table.
nisln Command Syntax
To create a link, use:
nisln source target |
|
Option |
Description |
|---|---|
|
-L |
Follow links. If the source is itself a link, the new link will not be linked to it, but to that link's original source. |
|
-D |
Defaults. Specify a different set of defaults for the linked object. Defaults are described in Specifying Non-Default Security Values at Creation Time in NIS+. |
Creating a Link in NIS+
To create a link between objects such as tables and directories, specify both object names: first the source, and then the target. Do not link table entries.
nisln source-object target-object |
nissetup Command
The nissetup command expands an existing NIS+ directory object into a domain by creating the org_dir and groups_dir directories, and a full set of NIS+ tables. It does not, however, populate the tables with data. For that, you will need the nisaddent command, described in nisaddent Command. Expanding a directory into a domain is part of the process of setting up a domain.
Note –
When setting up a new NIS+ domain, the nisserverscript is easier to use than the nissetup command. See Setting Up NIS+ Root Servers for a full description of using nisserver.
The nissetup command can expand a directory into a domain that supports NIS clients as well.
To use nissetup, you must have modify rights to the directory under which you'll store the tables.
Expanding a Directory Into an NIS+ Domain
You can use the nissetup command with or without a directory name. If you don't supply the directory name, it uses the default directory. Each object that is added is listed in the output.
rootmaster# /usr/lib/nis/nissetup doc.com. org_dir.doc.com. created groups_dir.doc.com. created auto_master.org_dir.doc.com. created auto_home.org_dir.doc.com. created bootparams.org_dir.doc.com. created cred.org_dir.doc.com. created ethers.org_dir.doc.com. created group.org_dir.doc.com. created hosts.org_dir.doc.com. created mail_aliases.org_dir.doc.com. created sendmailvars.org_dir.doc.com. created netmasks.org_dir.doc.com. created netgroup.org_dir.doc.com. created networks.org_dir.doc.com. created passwd.org_dir.doc.com. created protocols.org_dir.doc.com. created rpc.org_dir.doc.com. created services.org_dir.doc.com. created timezone.org_dir.doc.com. created |
Expanding a Directory Into an NIS-Compatible Domain
To expand a directory into a domain that supports NIS+ and NIS client requests, use the -Y flag. The tables are created with read rights for the nobody class so that NIS clients requests can access them.
rootmaster# /usr/lib/nis/nissetup -Y Test.doc.com. |
nisaddent Command
The nisaddent command loads information from text files or NIS maps into NIS+ tables. It can also dump the contents of NIS+ tables back into text files. If you are populating NIS+ tables for the first time, see the instructions in Populating NIS+ Tables. It describes all the prerequisites and related tasks.
You can use nisaddent to transfer information from one NIS+ table to another (for example, to the same type of table in another domain), but not directly. First, you need to dump the contents of the table into a file, and then load the file into the other table. Be sure, though, that the information in the file is formatted properly. Chapter 10, NIS+ Tables and Information describes the format required for each table.
When you load information into a table, you can use any of three options: replace, append, or merge. The append option simply adds the source entries to the NIS+ table. With the replace option, NIS+ first deletes all existing entries in the table and then adds the entries from the source. In a large table, this adds a large set of entries into the table's .log file (one set for removing the existing entries, another for adding the new ones), taking up space in /var/nis and making propagation to replicas time consuming.
The merge option produces the same result as the replace option but uses a different process, one that can greatly reduce the number of operations that must be sent to the replicas.
With the merge option, NIS+ handles three types of entries differently:
-
Entries that exist only in the source are added to the table
-
Entries that exist in both the source and the table are updated in the table
-
Entries that exist only in the NIS+ table are deleted from the table
When updating a large table with a file or map whose contents are not greatly different from those of the table, the merge option can spare the server a great many operations. Because the merge option deletes only the entries that are not duplicated in the source (the replace option deletes all entries, indiscriminately), it saves one delete and one add operation for every duplicate entry.
If you are loading information into the tables for the first time, you must have create rights to the table object. If you are overwriting information in the tables, you must have modify rights to the tables.
nisaddent Command Syntax
To load information from text files, use:
/usr/lib/nis/nisaddent -f filename table-type\[domain] /usr/lib/nis/nisaddent -f filename \ -t tablename table-type [domain] |
To load information from NIS maps, use:
/usr/lib/nis/nisaddent -y NISdomain table-type\ [domain] /usr/lib/nis/nisaddent -y NISdomain -t tablename table-type [domain] /usr/lib/nis/nisaddent -Y map table-type [domain] /usr/lib/nis/nisaddent -Y map -t tablename table-type [domain] |
To dump information from an NIS+ table to a file, use:
/usr/lib/nis/nisaddent -d [-t tablename tabletype] \ > filename |
Loading Information Into NIS+ From a File
You can transfer the contents of a file into an NIS+ table in several different ways:
-
The -f option with no other option replaces the contents of table-type in the local domain with the contents of filename.
nisaddent -f filename table-type
-
With the -a option, -f appends the contents of filename to table-type.
nisaddent -a -f filename table-type
-
With the -m option, -f merges the contents of filename into the contents of table-type.
nisaddent -m -f filename table-type
The following two examples load the contents of a text file named /etc/passwd.xfr into the NIS+ Passwd table. The first is into a table in the local domain, the second into a table in another domain:
rootmaster# /usr/lib/nis/nisaddent -f /etc/passwd.xfr passwd rootmaster# /usr/lib/nis/nisaddent -f /etc/shadow.xfr shadow rootmaster# /usr/lib/nis/nisaddent -f /etc/passwd.xfr passwd sales.doc.com. rootmaster# /usr/lib/nis/nisaddent -f /etc/shadow.xfr shadow sales.doc.com. |
Note –
When creating an NIS+ passwd table from /etc files, you must run nisaddent twice. You run the command once on the /etc/passwd file and once on the /etc/shadow file.
Note –
On a system that is running a release prior to the Solaris 10 7/07 release, you must place IPv6 addresses into NIS+. To merge entries from the /etc/inet/ipnodes file (IPv6 addresses) into the ipnodes.org_dir table, use the -v and -f options.
rootmaster# /usr/lib/nis/nisaddent -mv -f /etc/inet/ipnodes ipnodes |
Another way is to use stdin as the source. However, you cannot use the -m option with stdin. You can use redirect (->) or pipe (-|), but you cannot pipe into another domain.
|
Task |
Command |
|---|---|
|
Redirect |
cat filename > nisaddent table-type |
|
Redirect with append option |
cat filename > nisaddent -a table-type |
|
Redirect with append into another domain |
cat filename > nisaddent -a table-type NIS+ domain |
|
Pipe |
cat filename | nisaddent table-type |
|
Pipe with append option |
cat filename | nisaddent -a table-type |
If the NIS+ table is an automounter table or a nonstandard table, add the -t option and the complete name of the NIS+ table.
master# nisaddent -f /etc/auto_home.xfr \ -t auto_home.org_dir.doc.com.key-value master# nisaddent -f /etc/auto_home.xfr \ -t auto_home.org_dir.doc.com. key-value sales.doc.com. |
Loading Data From an NIS Map Into NIS+
You can transfer information from an NIS map in two different ways; either by specifying the NIS domain or by specifying the actual NIS map. If you specify the domain, NIS+ will figure out which map file in /var/yp/nisdomain to use as the source, based on the table-type. Note that /var/yp/nisdomain must be local files.
|
NIS+ Table Type |
NIS Map Name |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Protocols |
|
|
|
|
|
|
|
To transfer by specifying the NIS domain, use the -y (lowercase) option and provide the NIS domain in addition to the NIS+ table type.
Table replacement
nisaddent -y nisdomain table-type |
Table append
nisaddent -a -y nisdomain table-type |
Table merge
nisaddent -m -y nisdomain table-type |
By default, nisaddent replaces the contents of the
NIS+ table with the contents of the NIS map. Use the -a and -m options to append or merge. Here is an example that loads the NIS+
passwd table from its corresponding NIS map (passwd.byname) in the old-doc domain:
rootmaster# /usr/lib/nis/nisaddent -y old-doc passwd |
This example does the same thing, but for the sales.doc.com. domain instead of the local domain, doc.com.
rootmaster# /usr/lib/nis/nisaddent -y old-doc passwd sales.doc.com. |
If the NIS+ table is an automounter table or a nonstandard table, add the -t option and the complete name of the NIS table, just as you would if the source were a file.
rootmaster# nisaddent -y old-doc \ -t auto_home.org_dir.doc.com. key-value rootmaster# nisaddent -y old-doc \ -t auto_home.org_dir.doc.com. key-value sales.doc.com. |
If instead of using the map files for a domain, you prefer to specify a particular NIS map, use the -Y (uppercase) option and specify the map name.
rootmaster# nisaddent -Y hosts.byname hosts rootmaster# nisaddent -Y hosts.byname hosts sales.doc.com. |
If the NIS map is an automounter map or a non standard map, combine the -Y option with the -t option:
rootmaster# nisaddent -Y auto_home -t auto_home.org_dir.doc.com. key-value rootmaster# nisaddent -Y auto_home -t auto_home.org_dir.doc.com. key-value sales.doc.com. |
Dumping the Contents of an NIS+ Table to a File
To dump the contents of an NIS+ table into a file, use the -d and -t options. The -d options tells the command to dump, and the -t option specifies the NIS+ table:
rootmaster# nisaddent -d auto_home -t auto_home.org_dir.doc.com. key-value rootmaster# nisaddent -d auto_home -t auto_home.org_dir.doc.com. key-value sales.doc.com. |
Chapter 20 NIS+ Server Use Customization
This chapter describes how to customize and control which servers NIS+ clients use.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
NIS+ Servers and Clients
When client machines, users, applications, or processes need NIS+ information, they seek an active NIS+ server (master or replica) from which to get the needed data. On large networks, networks with many subnets, and networks that span wide-area links, you may be able to improve NIS+ performance by customizing server usage.
Default NIS+ Client Search Behavior
By default, if no server preferences have been set with the nisprefadm command, a client will first try to obtain the information it needs from an NIS+ server on the client's local subnet. If the client finds an active server on the local subnet, it obtains the information it needs from the first local server that responds. If no server is available on the local subnet, the client searches outside the local subnet, and obtains the NIS+ information it needs from the first remote server that responds.
On large, busy networks, this default search behavior may reduce NIS+ performance for one of two reasons:
-
When multiple servers on a subnet are serving a large number of clients, the random nature of the client's default search pattern may result in some servers being over worked while others are under used.
-
When a client has to seek an NIS+ server beyond the local subnet, it will obtain its information from the first server that responds even if that server is overworked, or linked to the client's subnet by a slower Wide Area Network connection such as a modem or a dedicated line that is already carrying heavy traffic.
Designating NIS+ Preferred Servers
The Solaris release contains a new feature – server-use customization – that allows you to control the order in which clients search for NIS+ servers.
With this new feature you can balance and customize server usage by:
-
Specifying that clients prefer (search for) certain servers over others.
-
Specify whether or not clients are permitted to use remote servers if no local servers are available.
The search criteria that you specify can be applied to all clients within a domain, all clients on a subnet, or to individual clients on a machine-by-machine basis.
Note –
When server-use preferences are set for a particular machine, those preferences apply to all users, applications, processes, or other clients running on that machine. You cannot set different server-use patterns for different clients on the same machine.
NIS+ Over Wide Area Networks
Server-use customization is particularly valuable for large networks with many subnets and networks that span multiple geographic sites connected by modems or leased lines. To maximize network performance, you want to minimize network traffic between subnets, and between sites linked by slower connections. You can do that by specifying which NIS+ servers the clients can use, and their order of server preference. In this way you confine as much NIS+ network traffic as possible to the local subnet.
Optimizing NIS+ Server Use
This section provides an overview of server-use customization.
nis_cachemgr Is Required
Server-use customization requires that a client be running nis_cachemgr. If a client machine is not running nis_cachemgr, it cannot make use of server-use customization. If there is no nis_cachemgr running on a client machine, that client will use the first server it identifies as described in Default NIS+ Client Search Behavior.
NIS+ Global Table or Local File
Depending on how you use the nisprefadm command, it creates either a local client_info file or a domain client_info table:
-
File. You can use nisprefadm to create a local, machine-specific client_info file that is stored in the machine's /var/nis directory. A local file specifies server preferences for that machine only. When a machine has a local /var/nis/client_info file, it ignores any server preferences contained in a domain client_info.org_dir table. To create a local client_info file, you run nisprefadm with the -L option.
-
Table. You can use nisprefadm to create an NIS+ client_info table which is stored in each domain's org_dir NIS+ directory object. This table can specify server preferences for:
-
Individual machines. (If a machine has a local /var/nis/client_info file, any preferences for that machine that happen to be in the domain client_info table are ignored.)
-
All the machines on a particular subnet. (If a machine on the subnet has a local /var/nis/client_info file or individual preferences set for it in the table it ignores subnet preferences.)
To create a global client_info table that applies to all machine on a subnet, you run nisprefadm with the -G and -C options as described in Specifying NIS+ Global Server Preferences.
Note that if a machine has its own local client_info file as described below, it will ignore all server preferences set for it in a global client_info table. If a machine has either a local client_info file or a machine-specific entry for it in the global client_info table, it will ignore preferences set for its subnet.
-
Use only the nisprefadm command to make changes to client_info files and tables. Never use other NIS+ commands such as nistbladm.
When working with client_info tables or files, you must use either the -G or the -L option to specify that your command apply to either the global table (-G) or local file (-L) of the machine you are running the command on.
NIS+ Preference Rank Numbers
Server preferences are controlled by giving each server a preference rank number. Clients search for NIS+ servers in order of numeric preference, querying servers with lower preference rank numbers before seeking servers with higher numbers.
Thus, a client will first try to obtain namespace information from NIS+ servers with a preference of zero. If there are no preference=0 servers available, then the client will query servers whose preference=1. If no 1's are available, it will try to find a 2, and then a 3, and so on until it either gets the information it needs or runs out of servers.
Preference rank numbers are assigned to servers with the nisprefadm command as described in Specifying NIS+ Global Server Preferences.
Server preference numbers are stored in client_info tables and files. If a machine has its own /var/nis/client_info file, it uses the preference numbers stored in that file. If a machine does not have its own client_info file, it uses the preference numbers stored in the domain's client_info.org_dir table. These client_info tables and files are called “preferred server lists” or simply server lists.
You customize server usage by controlling the server preferences of each client. For example, suppose a domain has a client machine named mailer that makes heavy use of namespace information and the domain has both a master server (nismaster) and a replica server (replica1). You could assign a preference number of 1 to nismaster and a number of 0 to replica1 for the mailer machine. The mailer machine would then always try to obtain namespace information from replica1 before trying nismaster. You could then specify that for all the other machines on the subnet the nismaster server had a preference number of zero and replica1 the number 1. This would cause the other machine to always try nismaster first.
You can give the same preference number to more than one server in a domain. For example, you could assign both nismaster1 and replica2 a preference number of 0, and assign replica3, replica4, and replica5 a preference number of 1.
Default NIS+ Server Preferences
If there is no client_info file or table, the cache manager automatically assigns all servers on the local subnet a default preference number of zero (0) and all servers outside the local subnet a preference of infinite. The purpose of nisprefadm is to change these default preference numbers to what you want them to be.
Efficiency and NIS+ Server Preference Numbers
A client must seek all servers with a given preference number before searching for servers with the next higher number. It requires 5 or more seconds for a client to search for all the servers with a given preference number. This means that if you have a master server and 4 replicas in a domain, and you give each one a different preference number from 0 to 4, it could take a client more than 25 seconds to run through all of those preference levels.
To maximize performance, you should not use more than two or three levels of server preference. For example, in the case described above, it is better to give one of those five servers a preference=0 and all the others a preference of 1, or give two of them a preference of 1 and the remaining three a preference of 2.
Preferred-Only NIS+ Servers and All Servers
Server lists also specify what a client does if it cannot find any preferred servers. A preferred server is any server with a preference of zero, or any server that you have assigned a preference number with nisprefadm.
By default, if a client fails to reach a preferred server, it will then seek out any server it can find anywhere on the network using the search mode described in Default NIS+ Client Search Behavior. You can change this default behavior with the nisprefadm -o option to specify that a client can only use preferred servers and if no servers are available it cannot go to non-preferred servers. See Specifying Preferred-Only Servers in NIS+ for details.
Note –
This option is ignored when the machine's domain is not served by any preferred servers.
Viewing NIS+ Preferences
To view the server preferences currently in effect for a particular client machine, you run nisprefadm with the -l option as described in Viewing NIS+ Machine Preferences.
NIS+ Server and Client Names
When specifying server or client machines, keep in mind the following points:
-
Server and client names do not need to be fully qualified so long as they are in the same NIS+ domain and uniquely identify the object. You can simply use the machine name by itself.
-
If a server or subnet is in another NIS+ domain, you need to include enough of the domain name to uniquely identify that machine. For example, if you are in the sales.doc.com domain and you need to specify the nismaster2 machine in the manf.doc.com domain, you need only enter nismaster2.manf.
NIS+ Server Preferences
To specify a server preference for:
-
Individual client machine, use the -L option to create a local client_info file for the machine you are running the nisprefadm on. Use the -G -C machine options to create machine-specific preferences in the global client_info table.
-
All machines on a subnet, use the -G -C subnetnumber option.
-
All machines in the current domain that do not have machine-specific or subnet-specific preferences, use the -G option.
When NIS+ Server Preferences Take Effect
Changes you make to a machine or subnet's server preferences normally do not take effect on a given machine until that machine updates it nis_cachemgr data. When the nis_cachemgr of a machine updates its server-use information depends on whether the machine is obtaining its server preferences from a global client_info table or a local /var/nis/client_info file (see NIS+ Global Table or Local File).
-
Global table. The cache managers of machines obtaining their server preferences from global tables update their server preferences whenever the machine is booted or whenever the Time-to-live (TTL) value expires for the client_info table. By default, this TTL value is 12 hours, but you can change that as described in Changing the Time-to-Live of an NIS+ Object.
-
Local file. The cache managers of machines obtaining their server preferences from local files update their server preferences every 12 hours or whenever you run nisprefadm to change a server preference. (Rebooting the machine does not update the cache manager's server preference information.)
However, you can force server preference changes to take effect immediately by running nisprefadm with the -F option. The -F option forces nis_cachemgr to immediately update its information. See Putting NIS+ Server Preferences Into Immediate Effect for details.
Using the nisprefadm Command
The following sections describe how to use the nisprefadm command to set, modify, and delete server preferences.
The nisprefadm command is used to specify the servers that clients are to prefer. The nisprefadm command has the following syntax:
nisprefadm -a|-m|-r|-u|-x|-l -L|-G [-o type] \ [-d domain] [-C machine] \ servers nisprefadm -F |
|
Option |
Description |
|---|---|
|
-G |
Create a global client_info table stored in the domain's org_dir directory. In other words, create a global preferred server list. This option must be used with either -C subnet to specify preferences for all the machines on a given subnet, or -C machine to specify preferences for an individual machine. |
|
-L |
Create a local client_info file stored in the local machine's /var/nis directory. In other words, create a preferred server list that applies only to the machine you are running the command on. |
|
-o type |
Specify an option. The valid options are: pref_type=all, which specifies that clients can use non-preferred servers if no preferred servers can be contacted, and pref_type=pref_only, which specifies that clients may only use the designated preferred servers. |
|
-d domain |
Create a global preferred server client_info table for the specified domain or subdomain. |
|
-C subnet |
The number of a subnet to which the preferences will apply. |
|
-C machine |
The name of a client machine. |
|
servers |
One or more NIS+ servers. These are the servers that are to be preferred. |
|
-a |
Add the specified servers to the server list. |
|
-m |
Modify the server list. For example, you can use the -m option to change the preference number given to one or more servers. |
|
-r |
Remove the specified servers from the server list. |
|
-u |
Clear the server list, and then add the specified servers. (In other words, replace the current server list with a new list of preferred servers.) |
|
-x |
Remove the server list completely. |
|
-l |
List (display) the current preferred server information. |
|
-F |
Force changes to a preferred server list to take effect immediately. |
Note –
The -C machine option should not be used with the -L (local) flag because it has no effect. For example, suppose you are running nisprefadm on the altair machine. You use the -L flag to specify that the preferences you are specifying be written into altair's local client_info file. You also use a -C vega option to specify that the preferences you are creating be applied to the vega machine. The nisprefadmcommand then write your preferences for vega into altair's file. But vega will never see them because vega will always get its server preferences from either its own local client_info file or the domain's global client_info table. Thus, it only makes sense to use the -C option when running nisprefadm with the -G (global) flag.
Viewing NIS+ Machine Preferences
 How to View Preferences for an NIS+ Server
How to View Preferences for an NIS+ Server
To view current server preferences, run nisprefadm with the -l option.
 How to View Preferences for an NIS+ Machine
How to View Preferences for an NIS+ Machine
-
Run nisprefadm with the -L and -l options on the machine.
sirius# nisprefadm -L -l
This displays any server preferences defined in the machine's local /var/nis/client_info file. If there is no local file, no information is displayed and you are returned to your shell prompt.
 How to View Global Preferences for an NIS+
Machine
How to View Global Preferences for an NIS+
Machine
-
Run nisprefadm with the -l, -G and -C machinename options.
sirius# nisprefadm -G -l -C machinename
Where machinename is the IP address (number) of the machine.
This displays the preferences set in the domain's global client_info table for that machine.
 How to View Global Preferences for an NIS+
Subnet
How to View Global Preferences for an NIS+
Subnet
-
Run nisprefadm with the -l, -G and -C subnet options.
sirius# nisprefadm -G -l -C subnet
Where subnet is the IP address (number) of the subnet.
This displays the preferences set in the domain's global client_info table for that machine.
Specifying NIS+ Preference Rank Numbers
By default, all servers listed after the -a option are given a preference number of zero. To specify a different preference number, enclose the number in parentheses immediately after the server name like this: -a name(n). Where name is the name of the server and n is the preference number.
For example, assign the replica2 server a preference number of 3:
# nisprefadm -G -a replica2(3) |
Note –
With some shells you may have to enclose the element in quotes like this: "name(n)".
See NIS+ Preference Rank Numbers for background information on the server preference rank numbers.
Specifying NIS+ Global Server Preferences
You can set global server preferences for a local or remote domain. Preferences may be set for individual machines and all the machines on a subnet.
The procedures in this section describe how to specify server preferences in a global client_info table residing on the NIS+ domain's master server. Once the table exists on the master server, NIS+ replicates it on to any existing replica servers for the domain.
-
See Specifying Local NIS+ Server Preference for information on how to create a local client_info file on an individual machine.
-
See NIS+ Global Table or Local File for an explanation of the difference between a global client_info table and a local client_info file.
To assign server preference numbers, run nisprefadm with either the:
-
-a option to add new or additional preferred servers.
-
-u option to delete existing server preferences and create new ones.
 How to Set Global Preferences for an NIS+
Subnet
How to Set Global Preferences for an NIS+
Subnet
To assign server preferences in the global table for all the machines on a subnet:
-
Run nisprefadm with the -G and -C subnet options.
#nisprefadm -G -a -C subnet servers (preferences)
Where:
-
-C subnet identifies the IP number of the subnet the preferences will apply to.
-
servers(preferences) are one or more servers with optional preference ranking numbers.
For example, to specify that the subnet 172.22.123.123 uses the nismaster and replica3 servers with a default preference number of zero and the manf.replica6 server with a preference number of 1, type the following.
polaris# nisprefadm -a -G -C 172.22.123.123 nismaster1 \ replica3 "manf.replica6(1)"
-
 How to Set Global Preferences for an Individual
NIS+ Machine
How to Set Global Preferences for an Individual
NIS+ Machine
-
Run nisprefadm with the -G, and -C machine options.
#nisprefadm -G -a -C machine servers (preferences)
Where:
-
-C machine identifies the machine the preferences will apply to. (Depending on the shell you are using, you may need to enclose machine in quotes.)
-
servers(preferences) are one or more servers with optional preference ranking numbers.
For example, to replace the current preferences for the machine cygnus with replica7 and replica9 both with a default preference number of zero, type the following.
polaris# nisprefadm -u -G -C cygnus replica7 replica9
-
 How to Set Global Preferences for a Remote
NIS+ Domain
How to Set Global Preferences for a Remote
NIS+ Domain
To assign server preferences for an individual machine in a remote domain or all the machines on a subnet in a remote domain:
-
Run nisprefadm with the -C, -G, and -d options.
#nisprefadm -a -G -C name \ -d domain servers(preferences)
Where:
-
name is the IP number of a subnet or the name of a machine. The modifications you make with this command apply to the subnet or machine that you name.
-
domainname is the name of the remote domain.
-
servers(preferences) are one or more servers with optional preference ranking numbers.
For example, to add the nismaster2 server with a default preference number of zero to the preferred server list of the 10.10.111.11 subnet in the remote sales.doc.com domain:
polaris# nisprefadm -a -G -C 10.10.111.11 -d sales.doc.com. nismaster2
-
Specifying Local NIS+ Server Preference
These procedures explain how to create or change a local client_info file that specifies server preferences for the machine on which it resides.
If a machine has a local /var/nis/client_info file, that machine takes its server preferences from its local file rather than the global client_info tables on NIS+ servers. In other words, a local file overrides any global table.
-
See Specifying NIS+ Global Server Preferences for information on how to create a global client_info tables for NIS+ servers.
-
See NIS+ Global Table or Local File for an explanation of the difference between a global client_info table and a local client_info file.
To assign server preferences, run nisprefadm with either the:
-
-a option to add new or additional preferred servers.
-
-u option to delete existing server preferences and create new ones.
 How to Set Preferences on a Local NIS+ Machine
How to Set Preferences on a Local NIS+ Machine
To assign server preferences for the local machine that you are running the nisprefadm command on:
-
Run nisprefadm with the -L option and either the -a or -u options.
#nisprefadm -a -L servers(preferences)
Where servers(preferences) are one or more servers with optional preference ranking numbers.
For example, to specify that the deneb machine first seek NIS+ information from the replica3 server with a default preference number of zero and then from the replica6 server (with a preference number of 1) in the manf.doc.com domain:
deneb# nisprefadm -a -L replica3 replica6.manf(1)
Modifying NIS+ Server Preferences
You can change a server's preference number and switch (replace) the preference numbers assigned to different servers.
To change preferred servers or the preference number assigned to a server, run nisprefadm with the -m oldserver-=newserver(n) option.
 How to Change an NIS+ Server's
Preference Number
How to Change an NIS+ Server's
Preference Number
-
Run nisprefadm with the -m server=server(new) option.
#nisprefadm -L|-G -C name -m oldserver=newserver(n)
Where:
-
-L|-G determines whether you are modifying a local file or a global table.
-
-C name is the IP number of a subnet or the name of a machine. This option is only used when you are also using the -G option. The modifications you make with this command apply to the subnet or machine that you name.
-
-m is the modify server list option.
-
old server is the name of the server whose preference number you want to change.
-
new server(n) is the server name and its new preference number.
For example, on the deneb machine, to change the number given to the replica6.manf server to 2 in deneb's local client_info file:
deneb# nisprefadm -L -m replica6.manf=replica6.manf(2)
-
 How to Replace One NIS+ Server With Another
in a Preference List
How to Replace One NIS+ Server With Another
in a Preference List
To change one server for another in a preference list:
-
Run nisprefadm with the -m oldserver=newserver option.
#nisprefadm -L|-G -C name -m \ oldserver=newserver(prefnumber)
Where:
-
-L|-G determine whether you are modifying a local or a domain-wide server list.
-
-C name is the IP number of a subnet or the name of a machine. This option is only used in when you are also using the -G option. The modifications you make with this command apply to the subnet or machine that you name.
-
-m is the modify-server-list option.
-
oldserver is the old server you are replacing.
-
newserver(prefnumber) is the new server (with an optional preference number) that is taking the old server's place in the preferred server list.
Keep in mind that when you replace a server in a global client_info table using the -G option, the replacement only applies to the subnet or machine identified by the -C option. Other listings of the replaced server are not affected.
For example, suppose you have a domain with three subnets, and the replica1 server is listed as a preferred server for two of those subnets. If replica1 is obsolete and you take it out of service, you then run nisprefadm -m to replace it with the new server for the first subnet. Until you do the same for the second subnet, replica1 is still listed as a preferred server for that subnet. The same principle applies to preferred servers for individual machines.
For example, to replace the replica3 server with the replica6 server for subnet 172.21.123.12 in the domain's global client_info table and assign replica6 a preference number of 1:
nismaster# nisprefadm -G -C 172.21.123.12 -m replica3 replica6(1)
-
 How to Remove NIS+ Servers From Preference
Lists
How to Remove NIS+ Servers From Preference
Lists
To remove one or more servers from a preference list:
-
Run nisprefadm with the -r option.
#nisprefadm -L|-G -C name -r servers
Where:
-
-L|-G determines whether you are modifying a local or a domain-wide server list.
-
-C name is the IP number of a subnet or the name of a machine. This option is only used when you are also using the -G option. The preferred servers you remove with this command apply to the subnet or machine that you name.
-
-r removes the named servers from the list.
For example, in the domain's global client_info table, to remove the replica3 and replica6.manf servers for the machine polaris:
polaris# nisprefadm -G -C polaris -r replica3 replica6.manf
-
Replacing an Entire Preferred Server List in NIS+
To replace an entire list of preferred servers for a subnet or machine in either a global client_info table or a machine in its local client_info file, run nisprefadm with the -u option.
The -u option operates the same way as the -a option, except that -u first deletes any existing server preferences for the machine or subnet before adding the new ones that you specify. (If there are existing preferences, the -a option adds the new ones to the old list.)
See How to Set Global Preferences for an Individual NIS+ Machine for an example using the -u option.
Specifying Preferred-Only Servers in NIS+
You can specify what clients do when no preferred servers are available.
By default, if a client cannot reach a preferred server, it uses whatever other server it can find. You can specify that clients may only use preferred servers by setting the preferred-only option. See Preferred-Only NIS+ Servers and All Servers for background information on the preferred-only and all servers options.
To specify what clients do when no preferred servers are available, run nisprefadm with the -o value option.
 How to Specify Preferred-Only
Servers in NIS+
How to Specify Preferred-Only
Servers in NIS+
To specify that clients using a server list may only obtain NIS+ information from servers named in the list:
-
Run nisprefadm with the -o pref_only option.
#nisprefadm -L|-G -o pref_only
Where:
-
-L|-G determines whether you are modifying a local or a domain-wide server list.
-
-o -pref_only specifies that clients can only obtain NIS+ information from servers on the list.
Note –This option is ignored for domains that are not served by any preferred servers.
For example, to specify in altair's local client_info file that altair must always use preferred servers and cannot use any server not on altair's preferred server list:
altair# nisprefadm -L -o pref_only
-
 How to Revert to Using Non-Preferred
Servers in NIS+
How to Revert to Using Non-Preferred
Servers in NIS+
To specify that clients using a server list may obtain NIS+ information from servers not named in the list if no preferred servers are available:
-
Run nisprefadm with the -o all option.
#nisprefadm -L|-G -o all
Where:
-
-L|-G determines whether you are modifying a local or a domain-wide server list.
-
-o -all specifies that clients may obtain NIS+ information from servers not on the list if no preferred servers are available.
Note –This is the default behavior. You only need to use the -o all option if you have previously specified preferred-only servers with the -o pref_only option.
For example, to specify in altair's local client_info file that altair can now use non-preferred servers if no preferred servers can be reached:
altair# nisprefadm -L -o all
-
Ending Use of Server Preferences in NIS+
You can stop using server-use customization and revert to the obtaining NIS+ information as described in Default NIS+ Client Search Behavior.
To end server preferences, run nisprefadm with the -x option.
# nisprefadm -G -x |
-
Client machines that do not have local server preferences will obtain NIS+ information as described in Default NIS+ Client Search Behavior.
-
Client machines that do have local server preferences set by a local /var/nis/client_info file will continue to use servers as specified in that file.
Note –
When you end server preferences, clients do not stop using server preferences until the normal course of events as described When NIS+ Server Preferences Take Effect. You can force an immediate end to server preferences as described in Putting NIS+ Server Preferences Into Immediate Effect.
Eliminating Local Server Preferences in NIS+
Ending local preferences can mean one of three different things:
-
That you want the machine to stop using its local client_info file for its server preferences and start using the preferences set for its subnet in the domain's global client_info table.
-
That you want this machine to stop using its local client_info file for its server preferences and start using the preferences set for it specifically in the domain's global client_info table.
-
That you do not want the machine to use server preferences at all. When a machine does not use server preferences, it obtains NIS+ information as described in Default NIS+ Client Search Behavior.
 How to Switch From Local to Global Subnet
Preferences in NIS+
How to Switch From Local to Global Subnet
Preferences in NIS+
-
Remove the machine's /var/nis/client_info file.
# rm /var/nis/client_info
This causes the machine to use the preferences specified for the machine's subnet in the domain's global client_info table.
 How to Switch From Local to Machine-Specific
Global Preferences in NIS+
How to Switch From Local to Machine-Specific
Global Preferences in NIS+
-
Remove the machine's /var/nis/client_info file.
# rm /var/nis/client_info
-
Specify preferences for the machine in the global table using the -G and -C options.
See How to Set Global Preferences for an Individual NIS+ Machine.
 How to Stop a Machine From Using Any Server
Preferences in NIS+
How to Stop a Machine From Using Any Server
Preferences in NIS+
-
Remove the machine's /var/nis/client_info file.
# rm /var/nis/client_info
If the machine's domain does not have a global client_info table, this step is all you have to do. If the domain does have a client_info table, continue on to the next step.
-
Create an empty /var/nis/client_info file.
# touch /var/nis/client_info
When a machine has its own /var/nis/client_info file, it does not use global preferences from any client_info table. If the machine has an empty /var/nis/client_info file, it will not use any preferences at all and will obtain NIS+ information, as described in Default NIS+ Client Search Behavior.
Putting NIS+ Server Preferences Into Immediate Effect
Server-use changes normally go into effect whenever the client machine is rebooted or updates its cache manager.
When you use nisprefadm to set or change server preferences on a local machine using a local client_info file (the -L option), your changes go into effect immediately.
For machines obtaining their server preferences from a global client_info table (the -G option) you can force server preference changes into immediate effect by running nisprefadm a particular with the -F option.
# nisprefadm -F |
For example, to force immediate implementation of changes to vega's preferred server list (whether local or global):
vega# nisprefadm -F |
The -F option forces the machine's cache manager to immediately update its server preference information from the domain's global client_info table. If the machine on which you run nisprefadm -F has its own local client_info file in /var/nis, running this command will have no effect.
Note –
You cannot use the -F option with any other nisprefadm options. The nisprefadm -F command must always be run by itself on the machine you want it to apply to. You cannot use the -G option to update the cache managers of all machines in a domain. The nisprefadm -F command must be run on each machine individually.
Chapter 21 NIS+ Backup and Restore
This chapter describes how to back up and restore an NIS+ namespace.
The NIS+ backup and restore capabilities provide a quick and easy method of preserving and reinstalling your NIS+ namespace. These features can also be used to simplify creation of new replica servers and reduce the time it takes to bring them online.
These tasks are performed by two commands:
-
nisbackup. Backs up NIS+ directory objects.
-
nisrestore. Restores NIS+ directory objects.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
Backing Up Your NIS+ Namespace With nisbackup
The nisbackup command backs up one or more NIS+ directory objects or an entire namespace to a specified UNIX file system directory.
Note –
The nisbackup command is always run on a master server. Never run it on a replica server.
The nisbackup command copies the NIS+ namespace data set as of the time the backup command is run. This recording includes all current NIS+ data and also any changes entered into the NIS+ namespace by an authorized network administrator but not yet checkpointed (posted) to the NIS+ tables. The backup operation does not check or correct NIS+ data. If data in a table is corrupt, the corrupt data is backed up as if it were valid data.
The nisbackup command only backs up those directory objects that the machine is master server for. In other words, you can only use nisbackup on a master server. You cannot use nisbackup on a replica server.
-
If a machine is a master server for both a domain and a subdomain's NIS+ directory objects, you can run nisbackup on that machine to back up both domain and subdomain directory objects.
-
However, if a machine is a master server for one directory object, and a replica server for a different directory object, you can run nisbackup to back up the directory object that the machine is master server for, but it will not back up any objects that the machine is only a replica server for.
If the backup process is interrupted or unable to successfully complete its operation, it halts and restores all previous backup files that were stored in the target directory.
nisbackup Syntax
The nisbackup command uses the following syntax:
nisbackup [-v][-a] backupdir objects |
Where:
-
Backupdir is the target directory where the backup files are to be stored. For example, /var/master1_bakup.
-
Objects are the NIS+ directory objects that you want to back up. For example, org_dir.doc.com. Multiple NIS+ directory objects can be listed separated by spaces.
The nisbackup command takes the following options.
Table 21–1 Options for the nisbackup Command|
Option |
Purpose |
|---|---|
|
-v |
Verbose mode. This mode provides additional information |
|
-a |
All. Backs up all NIS+ directory objects that the server is master of. This includes any sub-domain directory objects that this server is the master for. Note that directory objects of subdomains that have their own master servers will not be backed up. |
The nisbackup command must be run on the master server for the NIS+ directory objects you are backing up.
When specifying NIS+ directory objects to be backed up, you can use full or partially qualified directory names.
When you back up multi-level directories, the backup files for lower level directories are automatically placed in subdirectories of the target backup directory.
What nisbackup Backs Up
When using nisbackup, keep in mind that nisbackup is server specific. Regardless of whether or not you use the -a option, nisbackup only backs up those directories that the server you are running it on is master of. NIS+ directory objects that have some other master server will not be backed up.
For example, suppose the submaster1 server is master server for the sales.doc.com. directory objects and also a replica for the west.sales.doc.com. directory objects. When you run nisbackup on submaster1, only the sales.doc.com. directory objects will be backed up.
Some of the implications of this server-specific principle are:
-
Entire NIS+ namespace. If you want to perform an NIS+ back up for an entire multi-domain namespace, and your root master server is also the master server of all subdomains, you can run nisbackup on the root master with the -a option. However, if the root master server is not the master server of all subdomains, you must also run nisbackup on each of the other master servers in order to obtain a complete back up of your entire namespace.
-
Sub-domains. If you are performing an NIS+ back up for one or more sub-domains, you must run nisbackup on the subdomain's master server. If one machine, such as the root master, is also master of one or more subdomains, you can run nisbackup on that machine with the -a option.
NIS+ Backup Target Directory
While the backup target directory must be available to the server being backed up, it is good practice to use a target directory that is not physically mounted on the server. That way you ensure that if the server is damaged the backup directory is still available.
A separate target directory must be used for each master server being backed up. It is good practice to avoid confusion by including the master server's machine name in the target directory name. For example, the target directory for a nisbackup run on the master1 machine might be named /var/master1_bakup.
Never back up more than one master server to a given target directory. Always use different target directories for different master servers. This is because each time you backup one or more NIS+ directory objects to a given target directory, previous backup files for those NIS+ directory objects in that directory are overwritten.
Maintaining a Chronological Sequence of NIS+ Backups
There are at least two ways to maintain an historic sequence of backup files:
-
Different target directoriess. You can maintain separate target directories for each date's backup. For example, /var/master1_bakup/July14, and /var/master1_bakup/July15, and so on. While this method is simple it wastes disk storage space.
-
File system backup. The most common method of maintaining an historical sequence of NIS+ backups is to simply include the backup target directory in whatever regular file system backup method that you use. To facilitate this, the nisbackup command can be run from a crontab file, or from within the Solstice backup routine. See your Solstice documentation for information on how to specify that commands like nisbackup be automatically run as part of the system backup procedure.
Backing Up Specific NIS+ Directories
To back up specific NIS+ directory objects, you list those directories after the target backup directory.
For example, to backup the three org_dir directory objects for the root, sales, and manf domains to a /master1_bakup directory, you would run nisbackup on the master1 machine as follows:
master1# nisbackup /var/master1_bakup org_dir org_dir.sales org_dir.manf |
Backing Up an Entire NIS+ Namespace
To back up an entire NIS+ namespace you run the nisbackup command on the root master server with the -a option.
When you use the -a option, you do not specify the NIS+ directory objects to be backed up. All NIS+ directory objects on the server and all those of subdomains below it will be automatically backed up.
For example, to backup the doc.com. namespace to a /master1_bakup directory, you would run nisbackup on the root master as follows:
rootmaster# nisbackup -a /var/master1_bakup |
NIS+ Backup Directory Structure
When you perform a back up on a domain, a subdirectory for each NIS+ directory object is created in the backup target directory. The names of these subdirectories match the fully qualified NIS+ directory object name including the trailing period.
If you perform a full backup of an entire NIS+ object using the -a option, then all three of the associated directory objects (domain. org_dir.domain., and groups_dir.domain.) are backed up and three target subdirectories are created. If you are backing up multiple objects, subdirectories are created for every object that you are backing up.
Note that the backup subdirectories for multiple NIS+ directory object are all subdirectories of the parent target backup directory regardless of whether or not they are subdomains. In other words, nisbackup does not reproduce a domain hierarchy under the parent backup target directory, instead all of the back up subdirectories are simple subdirectories of the target directory.
For example, if you backed up the root, sales, and manf directory objects of doc.com. to a /var/master1_bakup directory, nine subdirectories would be created in the /var/master1_bakup directory as shown in Figure 21–1.
Figure 21–1 Example Directories Created by nisbackup
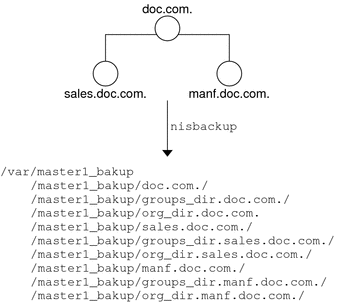
NIS+ Backup Files
The backup target directory contains a backup_list file that lists the NIS+ directory objects most recently backed up to this target directory.
Each of the subdirectories contain two files and a /data subdirectory.
The three files are:
-
data.dict. An XDR encoded file containing an NIS+ data dictionary for the NIS+ directory objects backed up to this directory.
-
last.upd. A binary file containing time-stamp information about the NIS+ directory object backed up to this directory.
Each of the /data subdirectories contain one or more of the following files:
-
root.object. An XDR encoded data file containing a description of the NIS+ root directory object. For example, /master1_bakup/doc.com/data/root.object.
-
root_dir. An XDR encoded file containing a description of NIS+ objects contained in the root directory and server information for those objects. For example, /master1_bakup/doc.com/data/root_dir.
-
table.directory. An XDR encoded file containing the data that was present in an NIS+ table at the time the backup was performed and also any data contained in any associated NIS+ log files. If there is an NIS+ table in the NIS+ directory object being backed up, a corresponding table.directory backup file will be created in the /data subdirectory for that directory object.
For example, every NIS+ org_dir directory contains a hosts table so there will be a hosts.org_dir file in each target/org_dir.domain/data subdirectory. For example, /master1_bakup/org_dir.doc.com./data/hosts.org_dir
User-created NIS+ tables present in a given directory object are backed up in the same way as the standard NIS+ tables.
-
groups_dir. An XDR encoded file containing NIS+ groups information. This file is stored in the corresponding NIS+ groups_dir target directory.
Restoring Your NIS+ Namespace With nisrestore
The nisrestore command recreates NIS+ directory objects to match the data stored in backup files created with the nisbackup command. This command can be used to restore NIS+ servers, replace directory objects that have become corrupted, or down load NIS+ data on to a new NIS+ server.
Prerequisites to Running nisrestore
In order to use nisrestore the target machine that will be receiving the NIS+ data from nisrestore must have already been set up as an NIS+ server. For a detailed description of setting up NIS+ servers, see Chapter 4, Configuring NIS+ With Scripts.
The prerequisites to using nisrestore are:
-
The machine must have already been initialized as an NIS+ client.
-
If the machine will be running in NIS-compatibility mode and support DNS forwarding, it must have a properly configured /etc/resolv.conf file.
-
If you are using nisrestore on a server while other servers in the namespace are up and running, nisrestore will verify with those other servers that this server is configured to serve the backed up NIS+ objects that you are restoring to it. If no other servers are up and running in your namespace, then you must run nisrestore with the -f option. In other words, if there are other servers that nisrestore can check with, you do not need to use the -f option. If no other servers are available, for example if you are restoring a single master server and there are no functioning replica servers, then you must use the -f option.
In addition to the preceding three prerequisites, the rpc.nisd daemon must not be running on the machine. If necessary, you must kill rpc.nisd, by stopping the NIS+ service, before running nisrestore.
nisrestore Syntax
The nisrestore command uses the following syntax:
nisrestore [-fv][-a][-t] backupdir [directory_objects] |
Where:
-
Backupdir is the directory containing the backup files to be used to restore the NIS+ objects. For example, /var/master1_bakup.
-
Directory_objects are the NIS+ directory objects that you want to restore. For example, org_dir.doc.com. Multiple NIS+ directory objects can be listed separated by spaces. (If you run nisrestore with the -a option, you do not specify specific directory objects.)
The nisrestore command takes the following options.
Table 21–2 Options for the nisrestore Command|
Option |
Purpose |
|---|---|
|
-a |
All. Restores all of the NIS+ directory objects contained in the backup directory. |
|
-f |
Forces the restoration without validating that the server is listed in the directory object's serving list. This option must be used when restoring a root master server or if you get an “unable to lookup object” type of error. |
|
-v |
Verbose mode. This mode provides additional information |
|
-t |
This option lists all of the NIS+ directory objects stored in the backup directory. No restoration of objects takes place. |
Using nisrestore
To restore NIS+ data from NIS+ backup files, use the nisrestore command.
For example, to restore the org_dir.doc.com. directory object on the replica1 server, you would log in as root on replica1, make sure that the prerequisites described in Prerequisites to Running nisrestore have been met and then run nisrestore as shown below:
replica1# nisrestore /var/master1_bakup org_dir.doc.com. |
The following points apply to nisrestore:
-
Damaged namespace. To restore a damaged or corrupted NIS+ namespace, the nisrestore command must be run on all of the servers for the NIS+ directory objects you are restoring.
-
Lookup error. If you get an error message telling you that nisrestore cannot verify or look up needed data, then you must use the -f option.
For example, to reload NIS+ data on a root master server named master1, you would enter the following.
master1# nisrestore -f -a /var/master1_bakup
-
Directory names. When specifying the NIS+ directory objects to be restored, you can use full or partially qualified directory names.
Using NIS+ Backup/Restore to Set Up Replicas
The NIS+ backup and restore features can be used to quickly down load NIS+ data on to a new replica server. For large namespaces this is much faster than nisping to obtain data from the master server.
To use nisbackup and nisrestore to set up a new replica, perform the following:
 How to Use NIS+ Backup/Restore
to Set Up Replicas
How to Use NIS+ Backup/Restore
to Set Up Replicas
-
Stop the NIS+ service on the new replica server.
Use svcadm disable. This interrupts the automatic transfer for namespace data from the master to the replica using the nisping command.
-
Run nisbackup on the master server.
-
Run nisrestore on the new replica to down load the NIS+ data.
-
Restart the NIS+ service on the new replica.
Replacing NIS+ Server Machines
You can use nisbackup and nisrestore to quickly replace a machine that you are using as a server with another machine. For example, you want to improve network performance by replacing an older server with a newer, faster machine.
To replace a machine being used as an NIS+ server with another machine, you must:
-
Assign the new machine the same IP address as the older machine it is replacing.
-
Assign the new machine the same machine name as the older machine it is replacing.
-
Connect the new machine to the same subnet as the older machine it is replacing.
To replace a server machine, follow these steps:
 How to Replace NIS+ Server Machines
How to Replace NIS+ Server Machines
-
Run nisbackup on the master server for the domain that the old server serves.
See Backing Up an Entire NIS+ Namespace. (Note that the old server you are replacing could be the master server for the domain, in which case you would run nisbackup on this old master server.)
-
Copy the old server's /var/nis/NIS_COLD_START file to the backup directory.
-
Copy the old server's /etc/.rootkey file to the backup directory.
-
Disconnect the old server from the network.
-
Connect the new server to the network.
-
Assign the new server the same IP address (number) as the old server.
-
Assign the new server the same machine name as the old server.
-
If necessary, stop the NIS+ service on the new server.
-
Run nisrestore on the new server to down load the NIS+ data.
-
Copy the .rootkey file from the backup directory to /etc on the new server.
-
Copy the NIS_COLD_START file from the backup directory to /var/nis on the new server.
-
Reboot the new server.
Chapter 22 Removing NIS+
This chapter describes how to use the NIS+ directory administration commands to remove NIS+ from clients, servers, and the namespace as a whole.
For information on disassociating an NIS+ replica server from a directory so that it no longer acts as a replica for that domain, see nisrmdir Command.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
The NIS+ service is managed by the Service Management Facility. Administrative actions on this service, such as enabling, disabling, or restarting, can be performed by using the svcadm command. See NIS+ and the Service Management Facility for more information about using SMF with NIS+. For an overview of SMF, refer to Chapter 18, Managing Services (Overview), in System Administration Guide: Basic Administration. Also refer to the svcadm(1M) and svcs(1) man pages for more details.
Removing NIS+ From a Client Machine
This section described how to remove NIS+ from a client machine. Keep in mind that removing NIS+ from a client machine does not remove the NIS+ name service from your network. See Removing the NIS+ Namespace for information on removing the NIS+ name service from a network and returning to either NIS or /etc files for name purposes.
Removing NIS+ That Was Installed Using nisclient
To remove NIS+ from a client machine that was set up as an NIS+ client using the nisclient -i script as described in Chapter 4, Configuring NIS+ With Scripts, run nisclient with the -r option:
client# nisclient -r |
nisclient -r simply undoes the most recent iteration of nisclient -i; it restores the previous naming system used by the client, such as NIS or /etc files.
Removing NIS+ That Was Installed Using NIS+ Commands
To remove NIS+ from a client machine that was set up as an NIS+ client using the nisaddcred, domainname, and nisinit commands as described in Chapter 4, Configuring NIS+ With Scripts, perform the following steps:
 How to Remove NIS+ That Was Installed Using NIS+ Commands
How to Remove NIS+ That Was Installed Using NIS+ Commands
-
client# rm -f /etc/.rootkey
-
Stop the keyserver.
client# svcadm disable /network/rpc/keyserv
-
Stop the NIS+ service.
This stops the rpc.nisd daemon and the nis_cachemgr.
client# svcadm disable /network/rpc/nisplus:default
-
Stop the name service cache (nscd).
client# svcadm disable /system/name-service-cache:default
-
Remove the /var/nis directory and files.
clientmachine# rm -rf /var/nis/*
Removing NIS+ From a Server
This section describes how to remove NIS+ from an NIS+ server.
Keep in mind that removing NIS+ from a server does not remove the NIS+ name service from your network. See Removing the NIS+ Namespace for information on removing the NIS+ name service from a network and returning to either NIS or /etc files for naming purposes.
Note –
You can replace a machine that you are using as an NIS+ server with another machine. See Replacing NIS+ Server Machines.
To remove NIS+ from a server, follow these steps:
 How to Remove NIS+ From a Server
How to Remove NIS+ From a Server
-
Perform the steps necessary to remove NIS+ from a client.
An NIS+ server is also an NIS+ client. This means that you must first remove the client-related part of NIS+. You can use nisclient -r as described in Removing NIS+ That Was Installed Using nisclient or the NIS+ command set as described in Removing NIS+ That Was Installed Using NIS+ Commands.
-
Remove the server's groups_dir and org_dir directories.
server# nisrmdir -f groups_dir.domainname server# nisrmdir -f org_dir.domainname
-
Stop the keyserver.
client# svcadm disable /network/rpc/keyserv
-
Stop the NIS+ service.
This kills the rpc.nisd daemon and the nis_cachemgr.
server# svcadm disable /network/rpc/nisplus:default
-
Stop the name service cache (nscd).
server# svcadm disable /system/name-service-cache:default
-
Remove the /var/nis directory and files.
rootmaster# rm -rf /var/nis/*
Removing the NIS+ Namespace
To remove the NIS+ namespace and return to using either NIS or /etc files for name services, follow these steps:
 How to Remove the NIS+ Namespace
How to Remove the NIS+ Namespace
-
Remove the .rootkey file from the root master.
rootmaster# rm -f /etc/.rootkey
-
Remove the groups_dir and org_dir subdirectories from the root master root domain.
rootmaster# nisrmdir -f groups_dir.domainname rootmaster# nisrmdir -f org_dir.domainname
Where domainname is the name of the root domain, for example, doc.com.
-
Remove the root domain.
rootmaster# nisrmdir -f domainname
Where domainname is the name of the root domain, for example, doc.com.
-
Stop the keyserver.
client# svcadm disable /network/rpc/keyserv
-
Stop the NIS+ service.
This kills the rpc.nisd daemon and the nis_cachemgr.
rootmaster# svcadm disable -t /network/rpc/nisplus:default
-
Stop the name service cache (nscd).
rootmaster# svcadm disable -t /system/name-service-cache:default
-
Create a new domain.
rootmaster# domainname name
Where name is the name of the new domain; for example, the name of the domain before you installed NIS+.
-
Remove the existing /etc/defaultdomain file.
rootmaster# rm /etc/defaultdomain
-
Recreate the /etc/defaultdomain file with the new domain name.
rootmaster# domainname > /etc/defaultdomain
-
Replace the original nsswitch.conf file.
If you set up this server with nisserver -r, you can use:
rootmaster# cp /etc/nsswitch.conf.no_nisplus /etc/nsswitch.conf
Alternatively, you can copy over one of the default switch template files. To use the default NIS switch file template, you would type:
rootmaster# cp /etc/nsswitch.nis etc/nsswitch.conf
To use the default /etc files switch file template, you would type:
rootmaster# cp /etc/nsswitch.files etc/nsswitch.conf
-
Remove the /var/nis directory and files.
rootmaster# rm -rf /var/nis/*
-
Start the NIS+ service.
rootmaster# svcadm enable /network/rpc/nisplus:default
Chapter 23 Information in NIS+ Tables
This chapter summarizes the information stored in the default NIS+ tables supplied in the Solaris software. This information is also documented in the corresponding man pages.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
NIS+ Tables
In an NIS+ environment, most namespace information is stored in NIS+ tables.
Without a naming service, most network information would be stored in /etc files and almost all NIS+ tables have corresponding /etc files. With the NIS service, you stored network information in NIS maps that also mostly corresponded with /etc files.
Note –
This chapter describes only those that are distributed as part of NIS+. Users and application developers frequently create NIS+ compatible tables for their own purposes. For information about tables created by users and developers, you must consult the documentation that they provide.
All NIS+ tables are stored in the domain's org_dir NIS+ directory object except the admin and groups tables that are stored in the groups_dir directory object.
Note –
Do not link table entries. Tables can be linked to other tables, but do not link an entry in one table to an entry in another table.
NIS+ Tables and Other Name Services
In the Solaris system the name service switch file (nsswitch.conf) allows you to specify one or more sources for different types of namespace information. In addition to NIS+ tables, sources can be NIS maps, DNS zone files, or /etc tables. The order in which you specify them in the switch file determines how the information from different sources is combined. (See Chapter 1, Name Service Switch for more information on the switch file.)
NIS+ Table Input File Format
If you are creating input files for any of these tables, most tables share two formatting requirements:
-
You must use one line per entry.
-
You must separate columns with one or more spaces or Tabs.
If a particular table has different or additional format requirements, they are described under the heading, “Input File Format.”
auto_home NIS+ Table
The auto_home table is an indirect automounter map that enables an NIS+ client to mount the home directory of any user in the domain. It does this by specifying a mount point for each user's home directory, the location of each home directory, and mount options, if any. Because it is an indirect map, the first part of the mount point is specified in the auto_master table, which is, by default, /home. The second part of the mount point (that is, the subdirectory under /home) is specified by the entries in the auto_home map, and is different for each user.
The auto_home table has two columns.
Table 23–1 auto_home Table|
Column |
Content |
Description |
|---|---|---|
|
Key |
Mount point |
The login name of every user in the domain |
|
Value
|
Options & location |
The mount options for every user, if any, and the location of the user's home directory |
For example:
costas barcelona:/export/partition2/costas |
The home directory of the user costas, which is located on the server barcelona, in the directory /export/partition2/costas, would be mounted under a client's /home/costas directory. No mount options were provided in the entry.
auto_master NIS+ Table
The auto_master table lists all the automounter maps in a domain. For direct maps, the auto_master table provides a map name. For indirect maps, it provides both a map name and the top directory of its mount point. The auto_master table has two columns.
Table 23–2 auto_master Table|
Column |
Content |
Description |
|---|---|---|
|
Key |
Mount point |
The top directory into which the map will be mounted. If the map is a direct map, this is a dummy directory, represented with /-. |
|
Value |
Map name |
The name of the automounter map |
For example, assume these entries in the auto_master table:
/home auto_home /-auto_man /programs auto_programs |
The first entry names the auto_home map. It specifies the top directory of the mount point for all entries in the auto_home map: /home. (The auto_home map is an indirect map.) The second entry names theauto_man map. Because that map is a direct map, the entry provides only the map name. The auto_man map will itself provide the topmost directory, as well as the full path name, of the mount points for each of its entries. The third entry names the auto_programs map and, since it provides the top directory of the mount point, the auto_programs map is an indirect map.
All automounter maps are stored as NIS+ tables. By default, the Solaris system provides the auto_master map, which is mandatory, and the auto_home map, which is a great convenience.
You can create more automounter maps for a domain, but be sure to store them as NIS+ tables and list them in the auto_master table. When creating additional automount maps to supplement auto_master (which is created for you), the column names must be key and value. For more information about the automounter consult your automounter or NFS file system documentation.
bootparams NIS+ Table
The bootparams table stores configuration information about every diskless machine in a domain. A diskless machine is a machine that is connected to a network, but has no hard disk. Since it has no internal storage capacity, a diskless machine stores its files and programs in the file system of a server on the network. It also stores its configuration information – or boot parameters – on a server.
Because of this arrangement, every diskless machine has an initialization program that knows where this information is stored. If the network has no name service, the program looks for this information in the server's /etc/bootparams file. If the network uses the NIS+ name service, the program looks for it in the bootparams table, instead.
The bootparams table can store any configuration information about diskless machines. It has two columns: one for the configuration key, another for its value. By default, it is set up to store the location of each machine's root, swap, and dump partitions.
The default bootparams table has only two columns that provide the following items of information.
Table 23–3 bootparams Table|
Column |
Content |
Description |
|---|---|---|
|
Key |
Hostname |
The diskless machine's official host name, as specified in the hosts table |
|
Value |
Configuration |
Root partition: the location (server name and path) of the machine's root partition |
|
|
|
Swap partition: the location (server name and path) of the machine's swap partition |
|
|
|
Dump partition: the location (server name and path) of the machine's dump partition |
|
|
|
Install partition. |
|
|
|
Domain. |
The columns are separated with a TAB character. Backslashes (\) are used to break a line within an entry. The entries for root, swap, and dump partitions have the following format:
client-name root=server:path \ swap=server:path \ dump=server:path \ install=server:path \ domain=domainname |
Here is an example:
buckarooroot=bigriver:/export/root1/buckaroo \ swap=bigriver:/export/swap1/buckaroo \ dump=bigriver:/export/dump/buckaroo \ install=bigriver:/export/install/buckaroo \ domain=sales.doc.com |
Additional parameters are available for x86-based machines. See the bootparams man page for additional information.
client_info NIS+ Table
The client_info table is an optional internal NIS+ table used to store server preferences for the domain in which it resides. This table is created and maintained with the nisprefadm command.
Only use nisprefadm to work with this table. Do not use any other NIS+ commands on this table.
cred NIS+ Table
The cred table stores credential information about NIS+ principals. Each domain has one cred table, which stores the credential information of client machines that belong to that domain and client users who are allowed to log into them. (In other words, the principals of that domain.) The cred tables are located in their domains' org_dir subdirectory.
Note –
Do not link a cred table. Each org_dir directory should have its own cred table. Do not use a link to some other org_dir cred table.
The cred table has five columns.
Table 23–4 cred Table|
NIS+ Principal Name |
Authentication Type |
Authentication Name |
Public Data |
Private Data |
|---|---|---|---|---|
|
Principal name of a principal user |
LOCAL |
UID |
GID list |
|
|
Principal name of a principal user or machine |
DES |
Secure RPC netname |
Public key |
Encrypted private key |
The second column, authentication type, determines the types of values found in the other four columns.
-
LOCAL. If the authentication type is LOCAL, the other columns contain a principal user's name, UID, and GID; the last column is empty.
-
DES. If the authentication type is DES, the other columns contain a principal's name, Secure RPC netname, public key, and encrypted private key. These keys are used in conjunction with other information to encrypt and decrypt a DES credential.
See Chapter 12, Administering NIS+ Credentials for additional information on credentials and the cred table.
ethers NIS+ Table
The ethers table stores information about the 48-bit Ethernet addresses of machines on the Internet. It has three columns.
Table 23–5 ethers Table|
Column |
Content |
Description |
|---|---|---|
|
Addr |
Ethernet-address |
The 48-bit Ethernet address of the machine |
|
Name |
Official-host-name |
The name of the machine, as specified in the hosts table |
|
Comment |
Comment |
An optional comment about the entry |
An Ethernet address has the form:
n:n:n:n:n:n hostname
where n is a hexadecimal number between 0 and FF, representing one byte. The address bytes are always in network order (most significant byte first).
group NIS+ Table
The group table stores information about UNIX user groups. The group table has four columns.
Table 23–6 group Table|
Column |
Description |
|---|---|
|
Name |
The group's name |
|
Passwd |
The group's password |
|
GID |
The group's numerical ID |
|
Members |
The names of the group members, separated by commas |
Earlier Solaris releases used a +/- syntax in local /etc/group files to incorporate or overwrite entries in the NIS group maps. Since the Solaris system uses the name service switch file to specify a machine's sources of information, this is no longer necessary. All you have to do in Solaris Release 2x systems is edit a client's /etc/nsswitch.conf file to specify files, followed by nisplus as the sources for the group information. This effectively adds the contents of the group table to the contents of the client's /etc/group file.
hosts NIS+ Table
The hosts table associates the names of all the machines in a domain with their IP addresses. The machines are usually also NIS+ clients, but they don't have to be. Other tables, such as bootparams, group, and netgroup, rely on the network names stored in this table. They use them to assign other attributes, such as home directories and group memberships, to individual machines. The hosts table has four columns.
Table 23–7 hosts Table|
Column |
Description |
|---|---|
|
Addr |
The machine's IP address (network number plus machine ID number) |
|
Cname |
The machine's official name |
|
Name |
A name used in place of the host name to identify the machine |
|
Comment |
An optional comment about the entry |
mail_aliases NIS+ Table
The mail_aliases table lists the domain's mail aliases recognized by sendmail. It has four columns.
Table 23–8 mail_aliases Table|
Column |
Description |
|---|---|
|
Alias |
The name of the alias |
|
Expansion |
A list containing the members that receive mail sent to this alias; members can be users, machines, or other aliases |
|
Comment |
An optional comment about the entry |
|
Options |
(See man page for options) |
Each entry has the following format:
alias-name:member[,member]... |
To extend an entry over several lines, use a backslash.
netgroup NIS+ Table
The netgroup table defines network wide groups used to check permissions for remote mounts, logins, and shells. The members of net groups used for remote mounts are machines; for remote logins and shells, they are users.
Note –
Users working on a client machine being served by an NIS+ server running in compatibility mode cannot run ypcat on the netgroup table. Doing so will give you results as if the table were empty even if it has entries.
The netgroup table has six columns.
Table 23–9 netgroup Table|
Column |
Content |
Description |
|---|---|---|
|
Name |
groupname |
The name of the network group |
|
Group |
groupname |
Another group that is part of this group |
|
Host |
hostname |
The name of a host |
|
User |
username |
A user's login name |
|
Domain |
domainname |
A domain name |
|
Comment |
Comment |
An optional comment about the entry |
The input file consists of a group name and any number of members:
groupname member-list... |
The member list can contain the names of other net groups or an ordered member list with three fields or both:
member-list::=groupname | (hostname, username, domainname) |
The first field of the member list specifies the name of a machine that belongs to the group. The second field specifies the name of a user that belongs to the group. The third field specifies the domain in which the member specification is valid.
A missing field indicates a wildcard. For example, the netgroup specification shown below includes all machines and users in all domains:
everybody ( , , ) |
A dash in a field is the opposite of a wildcard; it indicates that no machines or users belong to the group. Here are two examples:
(host1, -,doc.com.) (-,joe,doc.com.) |
The first specification includes one machine, host1, in the doc.com. domain, but excludes all users. The second specification includes one user in the doc.com. domain, but excludes all machines.
netmasks NIS+ Table
The netmasks table contains the network masks used to implement standard Internet subnetting. The table has three columns.
Table 23–10 netmasks Table|
Column |
Description |
|---|---|
|
Addr |
The IP number of the network |
|
Mask |
The network mask to use on the network |
|
Comment |
An optional comment about the entry |
For network numbers, you can use the conventional IP dot notation used by machine addresses, but leave zeros in place of the machine addresses. For example, this entry
172.31.0.0 255.255.255.0 |
means that class B network 172.31.0.0 should have 24 bits in its subnet field, and 8 bits in its host field.
networks NIS+ Table
The networks table lists the networks of the Internet. This table is normally created from the official network table maintained at the Network Information Control Center (NIC), though you might need to add your local networks to it. It has four columns.
Table 23–11 networks Table|
Column |
Description |
|---|---|
|
Cname |
The official name of the network, supplied by the Internet |
|
Addr |
The official IP number of the network |
|
Name |
An unofficial name for the network |
|
Comment |
An optional comment about the entry |
passwd NIS+ Table
The passwd table contains information about the accounts of users in a domain. These users generally are, but do not have to be, NIS+ principals. Remember though, that if they are NIS+ principals, their credentials are not stored here, but in the domain's cred table. The passwd table usually grants read permission to the world (or to nobody).
Note –
The passwd table should not have an entry for the user root (user ID 0). Root's password information should be stored and maintained in the machine's /etc files.
The information in the passwd table is added when users' accounts are created.
The passwd table contains the following columns.
Table 23–12 passwd Table|
Column |
Description |
|---|---|
|
Name |
The user's login name, which is assigned when the user's account is created; the name can contain no uppercase characters and can have a maximum of eight characters |
|
Passwd |
The user's encrypted password |
|
UID |
The user's numerical ID, assigned when the user's account is created |
|
GID |
The numerical ID of the user's default group |
|
GCOS |
The user's real name plus information that the user wishes to include in the From: field of a mail-message heading; an “&” in this column simply uses the user's login name |
|
Home |
The path name of the user's home directory. |
|
Shell |
The user's initial shell program; the default is the Bourne shell: /usr/bin/sh. |
|
Shadow |
(See Table 23–13.) |
The passwd table shadow column stores restricted information about user accounts. It includes the following information.
Table 23–13 passwd Table Shadow Column|
Item |
Description |
|---|---|
|
Lastchg |
The number of days between January 1, 1970, and the date the password was last modified |
|
Min |
The minimum number of days recommended between password changes |
|
Max |
The maximum number of days that the password is valid |
|
Warn |
The number of days' warning a user receives before being notified that his or her password has expired |
|
Inactive |
The number of days of inactivity allowed for the user |
|
Expire |
An absolute date past which the user's account is no longer valid |
|
Flag |
Reserved for future use: currently set to 0. |
Earlier Solaris releases used a +/- syntax in local /etc/passwd files to incorporate or overwrite entries in the NIS password maps. Since the Solaris 2x release uses the name service switch file to specify a machine's sources of information, this is no longer necessary. All you have to do in Solaris Release 2x systems is edit a client's /etc/nsswitch.conf file to specify files, followed by nisplus as the sources for the passwd information. This effectively adds the contents of the passwd table to the contents of the /etc/passwd file.
However, if you still want to use the +/- method, edit the client's nsswitch.conf file to add compat as the passwd source if you are using NIS. If you are using NIS+, add passwd_compat: nisplus.
protocols NIS+ Table
The protocols table lists the protocols used by the Internet. It has four columns.
Table 23–14 protocols Table|
Column |
Description |
|---|---|
|
Cname |
The protocol name |
|
Name |
An unofficial alias used to identify the protocol |
|
Number |
The number of the protocol |
|
Comments |
Comments about the protocol |
rpc NIS+ Table
The rpc table lists the names of RPC programs. It has four columns.
Table 23–15 rpc Table|
Column |
Description |
|---|---|
|
Cname |
The name of the program |
|
Name |
Other names that can be used to invoke the program |
|
Number |
The program number |
|
Comments |
Comments about the RPC program |
Here is an example of an input file for the rpc table:
# # rpc file # rpcbind 00000 portmap sunrpc portmapper rusersd 100002 rusers nfs 100003 nfsprog mountd 100005 mount showmount walld 100008 rwall shutdown sprayd 100012 spray llockmgr 100020 nlockmgr 100021 status 100024 bootparam 100026 keyserv 100029 keyserver nisd 100300 rpc.nisd # |
services NIS+ Table
The services table stores information about the Internet services available on the Internet. It has five columns.
Table 23–16 services Table|
Column |
Description |
|---|---|
|
Cname |
The official Internet name of the service |
|
Name |
The list of alternate names by which the service can be requested |
|
Proto |
The protocol through which the service is provided (for instance, 512/tcp) |
|
Port |
The port number |
|
Comment |
Comments about the service |
timezone NIS+ Table
The timezone table lists the default timezone of every machine in the domain. The default time zone is used during installation but can be overridden by the installer. The table has three columns.
Table 23–17 timezone Table|
Field |
Description |
|---|---|
|
Name |
The name of the domain |
|
Tzone |
The name of the time zone (for example, US/Pacific) |
|
Comment |
Comments about the time zone |
Additional Default Tables
For information the other default tables:
-
audit_user
-
auth_attr
-
exec_attr
-
prof_attr
-
user_attr
Refer to the appropriate section (4) man pages.
Chapter 24 NIS+ Troubleshooting
In this chapter, problems are grouped according to type. For each problem there is a list of common symptoms, a description of the problem, and one or more suggested solutions.
In addition, Appendix A, NIS+ Error Messages contains an alphabetic listing of the more common NIS+ error messages.
Note –
NIS+ might not be supported in a future release. Tools to aid the migration from NIS+ to LDAP are available as of the Solaris 9 release. For more information, see System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP) and visit NIS+ End-of-Feature (EOF) Announcement FAQ.
NIS+ Debugging Options
The NIS_OPTIONS environment variable can be set to control various NIS+ debugging options.
Options are specified after the NIS_OPTIONS command
separated by spaces with the option set enclosed in double quotes. Each option
has the format name=value. Values can be integers,
character strings, or filenames depending on the particular option. If a value
is not specified for an integer value option, the value defaults to 1.
NIS_OPTIONS recognizes the
following options.
NIS_OPTIONS Options and Values|
Option |
Values |
Actions |
|---|---|---|
|
debug_file |
filename |
Directs debug output to specified file. If this option is not specified, debug output goes to stdout. |
|
debug_bind |
Number |
Displays information about the server selection process. |
|
debug_rpc |
1 or 2 |
If the value is 1, displays RPC calls made to the NIS+ server and the RPC result code. If the value is 2, displays both the RPC calls and the contents of the RPC and arguments and results. |
|
debug_calls |
Number |
Displays calls to the NIS+ API and the results that are returned to the application. |
|
pref_srvr |
String |
Specifies preferred servers in the same format as that generated by the nisprefadm command (see Table 20–1). This will over-ride the preferred server list specified in nis_cachemgr. |
|
server |
String |
Bind to a particular server. |
|
pref_type |
String |
Not currently implemented. |
For example, if you are using a C-Shell:
-
To display many debugging messages, you would enter:
setenv NIS_OPTIONS “debug_calls=2 debug_bind debug_rpc”
-
To obtain a simple list of API calls and store them in the file /tmp/CALLS, you would enter:
setenv NIS_OPTIONS “debug_calls debug_file=/tmp/CALLS”
-
To obtain a simple list of API calls sent to a particular server, you would enter:
setenv NIS_OPTIONS “debug_calls server=sirius”
NIS+ Administration Problems
This section describes problems that may be encountered in the course of routine NIS+ namespace administration work.
Common symptoms include:
-
“Illegal object type” for operation message
-
Other “object problem” error messages
-
Initialization failure
-
Checkpoint failures
-
Difficulty adding a user to a group
-
Logs too large/lack of disk space/difficulty truncating logs
-
Cannot delete groups_dir or org_dir
NIS+ Illegal Object Problems
Symptoms
There are a number of possible causes for this error message:
-
You have attempted to create a table without any searchable columns.
-
A database operation has returned the status of DB_BADOBJECT (see the nis_db man page for information on the db error codes).
-
You are trying to add or modify a database object with a length of zero.
-
You attempted to add an object without an owner.
-
The operation expected a directory object, and the object you named was not a directory object.
-
You attempted to link a directory to a LINK object.
-
You attempted to link a table entry.
-
An object that was not a group object was passed to the nisgrpadm command.
-
An operation on a group object was expected, but the type of object specified was not a group object.
-
An operation on a table object was expected, but the object specified was not a table object.
nisinit Fails
Make sure that:
-
You can ping the NIS+ server to check that it is up and running as a machine.
-
The NIS+ server that you specified with the -H option is a valid server and that it is running the NIS+ software.
-
rpc.nisd is running on the server.
-
The nobody class has read permission for this domain.
-
The netmask is properly set up on this machine.
NIS+ Checkpoint Keeps Failing
If checkpoint operations with a nisping -C command consistently fail, make sure that you have sufficient swap and disk space. Check for error messages in syslog. Check for core files filling up space.
Cannot Add NIS+ User to a Group
A user must first be an NIS+ principal client with a LOCAL credential
in the domain's cred table before
the user can be added as a member of a group in that domain. A DES credential
alone is not sufficient.
NIS+ Logs Grow too Large
Failure to regularly checkpoint your system with nisping -C causes your log files to grow too large. Logs are not cleared on a master until all replicas for that master are updated. If a replica is down or otherwise out of service or unreachable, the master's logs for that replica cannot be cleared. Thus, if a replica is going to be down or out of service for a period of time, you should remove it as a replica from the master as described in Removing an NIS+ Directory. Keep in mind that you must first remove the directory's org_dir and groups_dir subdirectories before you remove the directory itself.
Lack of Disk Space for NIS+
Lack of sufficient disk space will cause a variety of different error messages. (See Insufficient Disk Space in NIS+ for additional information.)
Cannot Truncate NIS+ Transaction Log File
First, check to make sure that the file in question exists and is readable and that you have permission to write to it.
-
You can use ls /var/nis/trans.log to display the transaction log.
-
You can use nisls -l and niscat to check for existence, permissions, and readability.
-
You can use syslog to check for relevant messages.
The most likely cause of inability to truncate an existing log file for which you have the proper permissions is lack of disk space. (The checkpoint process first creates a duplicate temporary file of the log before truncating the log and then removing the temporary file. If there is not enough disk space for the temporary file, the checkpoint process cannot proceed.) Check your available disk space and free up additional space if necessary.
NIS+ Domain Name Confusion
Domain names play a key role in many NIS+ commands and operations. To avoid confusion, you must remember that, except for root servers, all NIS+ masters and replicas are clients of the domain above the domain that they serve. If you make the mistake of treating a server or replica as if it were a client of the domain that it serves, you may get Generic system error or Possible loop detected in namespace directoryname:domainname error messages.
For example, the machine altair might be a client of the subdoc.doc.com. domain. If the master server of the subdoc.doc.com. subdomain is the machine sirius, then sirius is a client of the doc.com. domain.
-
Client machines belong to a given domain or subdomain.
-
Servers and replicas that serve a given subdomain are clients of the domain above the domain they are serving.
-
The only exception to Rule 2 is that the root master server and root replica servers are clients of the same domain that they serve. In other words, the root master and root replicas are all clients of the root domain.
When using, specifying, or changing domains, remember these rules to avoid confusion:
Thus, in the example above, the fully qualified name of the altair machine is alladin.subdoc.doc.com. The fully qualified name of the sirius machine is sirius.doc.com. The name sirius.subdoc.doc.com. is wrong and will cause an error because sirius is a client of doc.com., not subdoc.doc.com.
Cannot Delete org_dir or groups_dir
Always delete org_dir and groups_dir before deleting their parent directory. If you use nisrmdir to delete the domain before deleting the domain's groups_dir and org_dir, you will not be able to delete either of those two subdirectories.
Removal or Dissociation of NIS+ Directory From Replica Fails
When removing or disassociating a directory from a replica server you must first remove the directory's org_dir and groups_dir subdirectories before removing the directory itself. After each subdirectory is removed, you must run nisping on the parent directory of the directory you intend to remove. (See Removing an NIS+ Directory.)
If you fail to perform the nisping operation, the directory will not be completely removed or disassociated.
-
Make sure that org_dir.domain does not appear in /var/nis/rep/serving_list on the replica.
-
Perform a nisping on domain.
-
From the master server, run nisrmdir -f replica_directory.
If this occurs, you need to perform the following steps to correct the problem:
If the replica server you are trying to dissociate is down or out of communication, the nisrmdir -s command will return a Cannot remove replica name: attempt to remove a non-empty table error message.
In such cases, you can run nisrmdir -f -s replicaname on the master to force the dissociation. Note, however, that if you use nisrmdir -f -s to dissociate an out-of-communication replica, you must run nisrmdir -f -sagain as soon as the replica is back on line in order to clean up the replica's /var/nis file system. If you fail to rerun nisrmdir -f -s replicaname when the replica is back in service, the old out-of-date information left on the replica could cause problems.
NIS+ Database Problems
This section covers problems related to the namespace database and tables.
Common symptoms include error messages with operative clauses such as:
-
Abort_transaction: Internal database error
as well as when rpc.nisd fails.
See also NIS+ Ownership and Permission Problems.
Multiple rpc.nisd Parent Processes
Symptoms:
Various Database and transaction log corruption error messages containing the terms:
Possible Causes:
You have multiple independent rpc.nisd daemons running. In normal operation, rpc.nisd can spawn other child rpc.nisd daemons. This causes no problem. However, if two parentrpc.nisd daemons are running at the same time on the same machine, they will overwrite each other's data and corrupt logs and databases. (Normally, this could only occur if someone started running rpc.nisd by hand.)
Diagnosis:
Run ps -e | grep rpc.nisd. Make sure that you have no more than one parent rpc.nisd process.
Solution:
If you have more than one “parent” rpc.nisd entry, you must kill all but one of them. Use svcadm disable to stop the unwanted services, then run the ps command again to make sure the unwanted daemons have died.
If an NIS+ database is corrupt, you will also have to restore it from your most recent backup that contains an uncorrupted version of the database. You can then use the logs to update changes made to your namespace since the backup was recorded. However, if your logs are also corrupted, you will have to recreate by hand any namespace modifications made since the backup was taken.
rpc.nisd Fails
If an NIS+ table is too large, rpc.nisd may fail.
Diagnosis:
Use nisls to check your NIS+ table sizes. Tables larger than 7k may cause rpc.nisd to fail.
Solution:
Reduce the size of large NIS+ tables. Keep in mind that as a naming service NIS+ is designed to store references to objects, not the objects themselves.
NIS+ and NIS Compatibility Problems
This section describes problems having to do with NIS compatibility with NIS+ and earlier systems and the switch configuration file.
Common symptoms include:
Error messages with operative clauses include:
User Cannot Log In to NIS+ Domain After Password Change
Symptoms:
New users, or users who recently changed their password are unable to log in at all, or able to log in on one or more machines but not on others.
The user may see error messages with operative clauses such as:
First Possible Cause:
Password was changed on NIS machine.
If a user or system administrator uses the passwd command to change a password on a Solaris system machine running NIS in a domain served by NIS+ namespace servers, the user's password is changed only in that machine's /etc/passwd file. If the user then goes to some other machine on the network, the user's new password will not be recognized by that machine. The user will have to use the old password stored in the NIS+ passwd table.
Diagnosis:
Check to see if the user's old password is still valid on another NIS+ machine.
Solution:
Use passwd on a machine running NIS+ to change the user's password.
Second Possible Cause:
Password changes take time to propagate through the domain.
Diagnosis:
Namespace changes take a measurable amount of time to propagate through a domain and an entire system. This time might be as short as a few seconds or as long as many minutes, depending on the size of your domain and the number of replica servers.
Solution:
You can simply wait the normal amount of time for a change to propagate through your domains. Or you can use the nisping org_dir command to resynchronize your system.
nsswitch.conf File Fails to Perform Correctly
A modified (or newly installed) nsswitch.conf file fails to work properly.
Symptoms:
You install a new nsswitch.conf file or make changes to the existing file, but your system does not implement the changes.
Possible Cause:
Each time an nsswitch.conf file is installed or changed, you must reboot the machine for your changes to take effect. This is because nscd caches the nsswitch.conf file.
Solution:
Check your nsswitch.conf file against the information contained in the nsswitch.conf man page. Correct the file if necessary, and then reboot the machine.
NIS+ Object Not Found Problems
This section describes problem in which NIS+ was unable to find some object or principal. Common symptoms include:
Error messages with operative clauses such as:
NIS+ Syntax or Spelling Error
The most likely cause of some NIS+ object not being found is that you mistyped or misspelled its name. Check the syntax and make sure that you are using the correct name.
Incorrect NIS+ Path
A likely cause of an “object not
found” problem is specifying an incorrect path. Make sure that the path
you specified is correct. Also make sure that the NIS_PATH environment
variable is set correctly.
NIS+ Domain Levels Not Correctly Specified
Remember that all servers are clients of the domain above them, not the domain they serve.
There are two exceptions to this rule:
-
The root masters and root replicas are clients of the root domain.
-
NIS+ domain names end with a period. When using a fully qualified name you must end the domain name with a period. If you do not end the domain name with a period, NIS+ assumes it is a partially qualified name. However, the domain name of a machine should not end with a dot in the /etc/defaultdomain file. If you add a dot to a machine's domain name in the /etc/defaultdomain file, you will get Could not bind to server serving domain name error messages and encounter difficulty in connecting to the net on boot up.
NIS+ Object Does Not Exist
The NIS+ object may not have been found because it does not exist, either because it has been erased or not yet created. Use nisls -l in the appropriate domain to check that the object exists.
Lagging or Out-of-Sync NIS+ Replica
When you create or modify an NIS+ object, there is a time lag between the completion of your action and the arrival of the new updated information at a given replica. In ordinary operation, namespace information may be queried from a master or any of its replicas. A client automatically distributes queries among the various servers (master and replicas) to balance system load. This means that at any given moment you do not know which machine is supplying you with namespace information. If a command relating to a newly created or modified object is sent to a replica that has not yet received the updated information from the master, you will get an “object not found” type of error or the old out-of-date information. Similarly, a general command such as nisls may not list a newly created object if the system sends the nisls query to a replica that has not yet been updated.
You can use nisping to resync a lagging or out of sync replica server.
Alternatively, you can use the -M option with most NIS+ commands to specify that the command must obtain namespace information from the domain's master server. In this way you can be sure that you are obtaining and using the most up-to-date information. (However, you should use the -M option only when necessary because a main point of having and using replicas to serve the namespace is to distribute the load and thus increase network efficiency.)
NIS+ Files Missing or Corrupt
One or more of the files in /var/nis/data directory has become corrupted or erased. Restore these files from your most recent backup.
Old /var/nis Filenames
In the Solaris 2 release, the /var/nis directory contained two files named hostname.dict and hostname.log. It also contained a subdirectory named /var/nis/hostname. Starting with the Solaris 2.5 release, the two files were renamed trans.log and data.dict, and the subdirectory is named /var/nis/data.
Do not rename the /var/nis or /var/nis/data directories or any of the files in these directories that were created by nisinit or any of the other NIS+ setup procedures.
In the Solaris 2.5 release, the content of the files were also changed and they are not backward compatible with the Solaris 2 releases. Thus, if you rename either the directories or the files to match the Solaris 2.4 patterns, the files will not work with either the Solaris 2.4 release or current Solaris releases that use the newer version of the rpc.nisd command. Therefore, do not rename either the directories or the files.
Blanks in NIS+ Name
Symptoms:
Sometimes an object is there, sometimes it is not. Some NIS+ or UNIX commands report that an NIS+ object does not exist or cannot be found, while other NIS+ or UNIX commands do find that same object.
Diagnoses:
Use nisls to display the object's name. Look carefully at the object's name to see if the name actually begins with a blank space. (If you accidentally enter two spaces after the flag when creating NIS+ objects from the command line with NIS+ commands, some NIS+ commands will interpret the second space as the beginning of the object's name.)
Solution:
If an NIS+ object name begins with a blank space, you must either rename it without the space or remove it and then recreate it from scratch.
Cannot Use Automounter in NIS+
Symptoms:
You cannot change to a directory on another host.
Possible Cause:
Under NIS+, automounter names must be renamed to meet NIS+ requirements. NIS+ cannot access /etc/auto* tables that contain a period in the name. For example, NIS+ cannot access a file named auto.direct.
Diagnosis:
Use nisls and niscat to determine if the automounter tables are properly constructed.
Solution:
Change the periods to underscores. For example, change auto.direct to auto_direct. (Be sure to change other maps that might reference these.)
Links To or From NIS+ Table Entries Do Not Work
You cannot use the nisln command (or any other command) to create links between entries in tables. NIS+ commands do not follow links at the entry level.
NIS+ Ownership and Permission Problems
This section describes problems related to user ownership and permissions. Common symptoms include:
Error messages with operative clauses such as:
-
Unable to stat NIS+ directory name
Another Symptom:
User or root unable to perform any namespace task.
No NIS+ Permission
The most common permission problem is the simplest: you have not been granted permission to perform some task that you try to do. Use niscat -o on the object in question to determine what permissions you have. If you need additional permission, you, the owner of the object, or the system administrator can either change the permission requirements of the object (as described in Chapter 15, Administering NIS+ Access Rights) or add you to a group that does have the required permissions (as described in Chapter 17, Administering NIS+ Groups).
No NIS+ Credentials
Without proper credentials for you and your machine, many operations will fail. Use nismatch on your home domain's cred table to make sure you have the right credentials. See Corrupted NIS+ Credentials for more on credentials-related problems.
NIS+ Server Running at Security Level 0
A server running at security level 0 does not create or maintain credentials for NIS+ principals.
If you try to use passwd on a server that is running at security level 0, you will get the error message: You name do not have secure RPC credentials in NIS+ domain domainname.
Security level 0 is only to be used by administrators for initial namespace setup and testing purposes. Level 0 should not be used in any environment where ordinary users are active.
User Login Same as NIS+ Machine Name
A user cannot have the same login ID as a machine name. When a machine is given the same name as a user (or a user has the same name as a machine), the first principal can no longer perform operations requiring secure permissions because the second principal's key has overwritten the first principal's key in the cred table. In addition, the second principal now has whatever permissions were granted to the first principal.
For example, suppose a user with the login name of saladin is granted namespace read-only permissions. Then a machine named saladin is added to the domain. The user saladin will no longer be able to perform any namespace operations requiring any sort of permission, and the root user of the machine saladin will only have read-only permission in the namespace.
Symptoms:
-
The user or machine gets “permission denied” type error messages.
-
Either the user or root for that machine cannot successfully run keylogin.
-
Security exception on LOCAL system. UNABLE TO MAKE REQUEST. error message.
-
If the first principal did not have read access, the second principal might not be able to view otherwise visible objects.
Note –
When running nisclient or nisaddcred, if the message Changing Key is displayed rather than Adding Key, there is a duplicate user or host name already in existence in that domain.
Diagnosis:
Run nismatch to find the host and user in the hosts and passwd tables to see if there are identical host names and user names in the respective tables:
nismatch username passwd.org_dir |
Then run nismatch on the domain's cred table to see what type of credentials are provided for the duplicate host or user name. If there are both LOCAL and DES credentials, the cred table entry is for the user; if there is only a DES credential, the entry is for the machine.
Solution:
Change
the machine name. (It is better to change the machine name than to change
the user name.) Then delete the machine's entry from the cred table and use nisclient to
reinitialize the machine as an NIS+ client. (If you wish, you can use nistbladm to create an alias for the machine's old name in the hosts tables.)
If necessary, replace the user's credentials in the cred table.
Bad NIS+ Credentials
See Corrupted NIS+ Credentials.
NIS+ Security Problems
This section describes common password, credential, encryption, and other security-related problems.
NIS+ Security Problem Symptoms
Error messages with operative clauses such as:
-
Password [problems]
User or root unable to perform any namespace operations or tasks. (See also NIS+ Ownership and Permission Problems.)
Login Incorrect Message
The most common cause of a “login incorrect” message is the user mistyping the password. Have the user try it again. Make sure the user knows the correct password and understands that passwords are case-sensitive and also that the letter “o” is not interchangeable with the numeral “0,” nor is the letter “l” the same as the numeral “1.”
Other possible causes of the “login incorrect” message are:
-
The password has been locked by an administrator. See Locking a Password in NIS+ and Unlocking a Password in NIS+.
-
The password has been locked because the user has exceeded an inactivity maximum. See Specifying Maximum Number of Inactive Days for Users in NIS+.
-
The password has expired. See Password Privilege Expiration in NIS+.
See Chapter 16, Administering NIS+ Passwords for general information on passwords.
Password Locked, Expired, or Terminated
A common cause of a Permission denied, password expired, type message is that the user's password has passed its age limit or the user's password privileges have expired. See Chapter 16, Administering NIS+ Passwords for general information on passwords.
Stale and Outdated NIS+ Credential Information
Occasionally, you may find that even though you have created the proper credentials and assigned the proper access rights, some client requests still get denied. This may be due to out-of-date information residing somewhere in the namespace.
Storing and Updating NIS+ Credential Information
Credential-related information, such as public keys, is stored in many locations throughout the namespace. NIS+ updates this information periodically, depending on the time-to-live values of the objects that store it, but sometimes, between updates, it gets out of sync. As a result, you may find that operations that should work, don't work. Table 24–2 lists all the objects, tables, and files that store credential-related information and how to reset it.
Table 24–2 Where NIS+ Credential-Related Information Is Stored|
Item |
Stores |
To Reset or Change |
|---|---|---|
|
cred table |
NIS+ principal's secret key and public key. These are the master copies of these keys. |
Use nisaddcred to create new credentials; it updates existing credentials. An alternative is chkey. |
|
Directory object |
A copy of the public key of each server that supports it. |
Run the /usr/lib/nis/nisupdkeys command on the directory object. |
|
Keyserver |
The secret key of the NIS+ principal that is currently logged in. |
Run keylogin for a principal user or keylogin -r for a principal machine. |
|
NIS+ daemon |
Copies of directory objects, which in turn contain copies of their servers' public keys. |
Stop the rpc.nisd daemon and the cache manager by disabling the NIS+ service, and then remove NIS_SHARED_DIRCACHE from /var/nis. Then restart the NIS+ service. |
|
Directory cache |
A copy of directory objects, which in turn contain copies of their servers' public keys. |
Restart the NIS+ cache manager with the -i option. |
|
Cold-start file |
A copy of a directory object, which in turn contains copies of its servers' public keys. |
Stop the NIS+ service. Remove the NIS_COLD_START and NIS_SHARED_DIRCACHE files from /var/nis. Restart the NIS+ service. |
|
passwd table |
A user's password or a machine's superuser password. |
Use the passwd -r nisplus command. It changes the password in the NIS+ passwd table and updates it in the cred table. |
|
passwd file |
A user's password or a machine's superuser password. |
Use the passwd -r nisplus command, whether logged in as superuser or as yourself, whichever is appropriate. |
|
(NIS) |
A user's password or a machine's superuser password. |
Use passwd -r nisplus. |
Updating Stale Cached NIS+ Keys
The most commonly encountered out-of-date information is the existence of stale objects with old versions of a server's public key. You can usually correct this problem by running nisupdkeys on the domain you are trying to access. (See Chapter 12, Administering NIS+ Credentials for information on using the nisupdkeys command.)
Because some keys are stored in files or caches, nisupdkeys cannot always correct the problem. At times you might need to update the keys manually. To do that, you must understand how a server's public key, once created, is propagated through namespace objects. The process usually has five stages of propagation. Each stage is described below.
Stage 1: Server's Public Key Is Generated
An NIS+ server is first an NIS+ client. So, its public key is generated in the same way as any other NIS+ client's public key: with the nisaddcred command. The public key is then stored in the cred table of the server's home domain, not of the domain the server will eventually support.
Stage 2: Public Key Is Propagated to Directory Objects
Once you have set up an NIS+ domain and an NIS+ server, you can associate the server with a domain. This association is performed by the nismkdir command. When the nismkdir command associates the server with the directory, it also copies the server's public key from the cred table to the domain's directory object. For example, assume the server is a client of the doc.com. root domain, and is made the master server of the sales.doc.com. domain.
Figure 24–1 Public Key Is Propagated to NIS+ Directory Objects

Its public key is copied from the cred.org_dir.doc.com. domain and placed in the sales.doc.com. directory object. This can be verified with the niscat -o sales.doc.com. command.
Stage 3: Directory Objects Are Propagated Into Client Files
All NIS+ clients are initialized with the nisinit utility or with the nisclient script.
Among other things, nisinit (or nisclient) creates a cold-start file /var/nis/NIS_COLDSTART. The cold-start file is used to initialize the client's directory cache /var/nis/NIS_SHARED_DIRCACHE. The cold-start file contains a copy of the directory object of the client's domain. Since the directory object already contains a copy of the server's public key, the key is now propagated into the cold-start file of the client.
In addition when a client makes a request to a server outside its home domain, a copy of the remote domains directory object is stored in the client's NIS_SHARED_DIRCACHE file. You can examine the contents of the client's cache by using the nisshowcache command, described on page 184.
This is the extent of the propagation until a replica is added to the domain or the server's key changes.
Stage 4: When a Replica is Added to the Domain
When a replica server is added to a domain, the nisping command (described in nisping Command) is used to download the NIS+ tables, including the cred table, to the new replica. Therefore, the original server's public key is now also stored in the replica server's cred table.
Stage 5: When the Server's Public Key Is Changed
If you decide to change DES credentials for the server (that is, for the root identity on the server), its public key will change.
As a result, the public key stored for that server in the cred table will be different from those stored in:
-
The cred table of replica servers (for a few minutes only)
-
The main directory object of the domain supported by the server (until its time-to-live expires)
-
The NIS_COLDSTART and NIS_SHARED_DIRCACHE files of every client of the domain supported by server (until their time-to-live expires, usually 12 hours)
-
The NIS_SHARED_DIRCACHE file of clients who have made requests to the domain supported by the server (until their time-to-live expires)
Most of these locations will be updated automatically within a time ranging from a few minutes to 12 hours. To update the server's keys in these locations immediately, use the commands.
Table 24–3 Updating an NIS+ Server's Keys|
Location |
Command |
See |
|---|---|---|
|
Cred table of replica servers (instead of using nisping, you can wait a few minutes until the table is updated automatically) |
nisping | |
|
Directory object of domain supported by server |
nisupdkeys | |
|
NIS_COLDSTART file of clients |
nisinit -c | |
|
NIS_SHARED_DIRCACHE file of clients |
nis_cachemgr |
Note –
You must stop the existing nis_cachemgr before restarting nis_cachemgr. To stop nis_cachemgr, disable the NIS+ service by using svcadm disable /network/rpc/nisplus:default.
Corrupted NIS+ Credentials
When a principal (user or machine) has a corrupt credential, that principal is unable to perform any namespace operations or tasks, not even nisls. This is because a corrupt credential provides no permissions at all, not even the permissions granted to the nobody class.
Symptoms:
User or root cannot perform any namespace tasks or operations. All namespace operations fail with a “permission denied” type of error message. The user or root cannot even perform a nisls operation.
Possible Cause:
Corrupted keys or a corrupt, out-of-date, or otherwise incorrect /etc/.rootkey file.
Diagnosis:
Use snoop to identify the bad credential.
Or, if the principal is listed, log in as the principal and try to run an NIS+ command on an object for which you are sure that the principal has proper authorization. For example, in most cases an object grants read authorization to the nobody class. Thus, the nisls object command should work for any principal listed in the cred table. If the command fails with a “permission denied” error, then the principal's credential is likely corrupted.
Solution
-
Ordinary user. Perform a keylogout and then a keylogin for that principal.
-
Root or superuser. Run keylogout -f followed by keylogin -r.
Keyserv Failure
The keyserv is unable to encrypt a session. There are several possible causes for this type of problem:
Possible Causes and Solutions:
-
The client has not keylogged in. Make sure that the client is keylogged in. To determine if a client is properly keylogged in, have the client run nisdefaults -v (or run it yourself as the client). If
(not authenticated)is returned on the Principal Name line, the client is not properly keylogged in. -
The client (host) does not have appropriate LOCAL or DES credentials. Run niscat on the client's cred table to verify that the client has appropriate credentials. If necessary, add credentials as explained in Creating Credential Information for NIS+ Principals.
-
The keyserv daemon is not running. Use the ps command to see if keyserv is running. If it is not running, restart keyserv and then do a keylogin.
-
While keyserv is running, other long running processes that make secure RPC or NIS+ calls are not. For example, automountd, rpc.nisd, and sendmail. Verify that these processes are running correctly. If they are not, restart them.
Machine Previously Was an NIS+ Client
If this machine has been initialized before as an NIS+ client of the same domain, try keylogin -r and enter the root login password at the Secure RPC password prompt.
No Entry in the NIS+ cred Table
To make sure that an NIS+ password for the principal (user or host) exists in the cred table, run the following command in the principal's home domain
nisgrep -A cname=principal cred.org_dir.domainname |
If you are running nisgrep from another domain, the domainname must be fully qualified.
Changed NIS+ Domain Name
Do not change a domain name.
If you change the name of an existing domain you will create authentication problems because the fully qualified original domain name is embedded in objects throughout your network.
If you have already changed a domain name and are experiencing authentication problems, or error messages containing terms like “malformed” or “illegal” in relation to a domain name, change the domain name back to its original name. The recommended procedure for renaming your domains is to create a new domain with the new name, set up your machines as servers and clients of the new domain, make sure they are performing correctly, and then remove the old domain.
When Changing a Machine to a Different NIS+ Domain
If this machine is an NIS+ client and you are trying to change it to a client of a different domain, remove the /etc/.rootkey file, and then rerun the nisclient script using the network password supplied by your network administrator or taken from the nispopulate script.
NIS+ and Login Passwords in /etc/passwd File
Your NIS+ password is stored in the NIS+ passwd table. Your user login password may be stored in NIS+ passwd table or in your /etc/passwd file. (Your user password and NIS+ password can be the same or different.) To change a password in an /etc/passwd file, you must run the passwd command with the nsswitch.conf file set to files or with the -r files flag.
The nsswitch.conf file specifies which password is used for which purpose. If the nsswitch.conf file is directing system queries to the wrong location, you will get password and permission errors.
Secure RPC Password and NIS+ Login Passwords Are Different
When a principal's login password is different from his or her Secure RPC password, keylogin cannot decrypt it at login time because keylogin defaults to using the principal's login password, and the private key was encrypted using the principal's Secure RPC password.
When this occurs the principal can log in to the system, but for NIS+ purposes is placed in the authorization class of nobody because the keyserver does not have a decrypted private key for that user. Since most NIS+ environments are set up to deny the nobody class create, destroy, and modify rights to most NIS+ objects this results in “permission denied” types errors when the user tries to access NIS+ objects.
Note –
In this context network password is sometimes used as a synonym for Secure RPC password. When prompted for your “network password,” enter your Secure RPC password.
To be placed in one of the other authorization classes, a user in this situation must explicitly run the keylogin program and give the principal's Secure RPC password when keylogin prompts for password. (See Keylogin With NIS+.)
But an explicit keylogin provides only a temporary solution that is good only for the current login session. The keyserver now has a decrypted private key for the user, but the private key in the user's cred table is still encrypted using the user's Secure RPC password, which is different than the user's login password. The next time the user logs in, the same problem reoccurs. To permanently solve the problem the user needs to change the private key in the cred table to one based on the user's login ID rather than the user's Secure RPC password. To do this, the user need to run the chkey program as described in Changing Keys for an NIS+ Principal.
-
Log in using the login password.
-
Run the keylogin program to temporarily get a decrypted private key stored in the keyserver and thus gain temporary NIS+ access privileges.
-
Run chkey -pto permanently change the encrypted private key in the cred table to one based on the user's login password.
Thus, to permanently solve a Secure RPC password different than login password problems, the user (or an administrator acting for the user) must perform the following steps:
Preexisting /etc/.rootkey File
Symptoms:
Various insufficient permission to and permission denied error messages.
Possible Cause:
An /etc/.rootkey file already existed when you set up or initialized a server or client. This could occur if NIS+ had been previously installed on the machine and the .rootkey file was not erased when NIS+ was removed or the machine returned to using NIS or /etc files.
Diagnosis:
Run ls -l on the /etc directory and nisls -l org_dir and compare the date of the /etc/.rootkey to the date of the cred table. If the /etc/.rootkey date is clearly earlier than that of the cred table, it may be a preexisting file.
Solution:
Run keylogin -r as root on the problem machine and then set up the machine as a client again.
Root Password Change Causes Problem in NIS+
Symptoms:
You change the root password on a machine, and the change either fails to take effect or you are unable to log in as superuser.
Possible Cause:
Note –
For security reasons, you should not have User ID 0 listed in the passwd table.
You changed the root password, but root's key was not properly updated. Either because you forgot to run chkey -p for root or some problem came up.
Solution
Log in as a user with administration privileges (that is, a user who is a member of a group with administration privileges) and use passwd to restore the old password. Make sure that old password works. Now use passwd to change root's password to the new one, and then run chkey -p.
Once your NIS+ namespace is set up and running, you can change the root password on the root master machine. But do not change the root master keys, as these are embedded in all directory objects on all clients, replicas, and servers of subdomains. To avoid changing the root master keys, always use the -p option when running chkey as root.
NIS+ Performance and System Hang Problems
This section describes common slow performance and system hang problems.
NIS+ Performance Problem Symptoms
Error messages with operative clauses such as:
Other common symptoms:
-
You issue a command and nothing seems to happen for far too long.
-
Your system, or shell, no longer responds to keyboard or mouse commands.
-
NIS+ operations seem to run slower than they should or slower than they did before.
NIS+ Checkpointing Operations
Someone has issued an nisping or nisping -C command. Or the rpc.nisd daemon is performing a checkpoint operation.
Do not reboot! Do not issue any more nisping commands.
When performing a nisping or checkpoint, the server will be sluggish or may not immediately respond to other commands. Depending on the size of your namespace, these commands may take a noticeable amount of time to complete. Delays caused by checkpoint or ping commands are multiplied if you, or someone else, enter several such commands at one time. Do not reboot. This kind of problem will solve itself. Just wait until the server finishes performing the nisping or checkpoint command.
During a full master-replica resync, the involved replica server will be taken out of service until the resync is complete. Do not reboot – just wait.
NIS+ Variable NIS_PATH
Make sure that your NIS_PATH variable is set to something clean and simple. For example, the default: org_dir.$:$. A complex NIS_PATH, particularly one that itself contains a variable, will slow your system and may cause some operations to fail. (See NIS+ NIS_PATH Environment Variable for more information.)
Do not use nistbladm to set nondefault table paths. Nondefault table paths will slow performance.
NIS+ Table Paths
Do not use table paths because they will slow performance.
Too Many NIS+ Replicas
Too many replicas for a domain degrade system performance during replication. There should be no more than 10 replicas in a given domain or subdomain. If you have more than five replicas in a domain, try removing some of them to see if that improves performance.
Recursive NIS+ Groups
A recursive group is a group that contains the name of some other group. While including other groups in a group reduces your work as system administrator, doing so slows down the system. You should not use recursive groups.
Large NIS+ Database Logs at Startup
When rpc.nisd starts up it goes through each log. If the logs are long, this process could take a long time. If your logs are long, you may want to checkpoint them using nisping -C before starting rpc.nisd.
Master rpc.nisd Daemon Died
Symptoms:
If you used the -M option to specify that your request be sent to the master server, and the rpc.nisd daemon has died on that machine, you will get a “server not responding” type error message and no updates will be permitted. (If you did not use the -M option, your request will be automatically routed to a functioning replica server.)
Possible Cause:
Using uppercase letters in the name of a home directory or host can sometimes cause rpc.nisd to die.
Diagnosis:
First make sure that the server itself is up and running. If it is, run ps -ef | grep rpc.nisd to see if the daemon is still running.
Solution:
If the daemon has died, restart the NIS+ service by using svcadm enable /network/rpc/nisplus:default. If rpc.nisd frequently dies, contact your service provider.
No nis_cachemgr
Symptoms:
It takes too long for a machine to locate namespace objects in other domains.
Possible Cause:
You do not have nis_cachemgr running.
Diagnosis:
Run ps -ef | grep nis_cachemgr to see if it is still running.
Solution
Start nis_cachemgr on that machine by enabling the NIS+ service.
NIS+ Server Very Slow at Startup After NIS+ Installation
Symptoms:
A server performs slowly and sluggishly after using the NIS+ scripts to install NIS+ on it.
Possible Cause:
You forgot to run nisping -C -a after running the nispopulate script.
Solution:
Run nisping -C -a to checkpoint the system as soon as you are able to do so.
niscat Returns: Server busy. Try Again
Symptoms:
You run niscat and get an error message indicating that the server is busy.
Possible Cause:
-
The server is busy with a heavy load, such as when doing a resync.
-
The server is out of swap space.
Diagnosis:
Run swap -s to check your server's swap space.
Solution:
You must have adequate swap and disk space to run NIS+. If necessary, increase your space.
NIS+ Queries Hang After Changing Host Name
Symptoms:
Setting the host name for an NIS+ server to be fully qualified is not recommended. If you do so, and NIS+ queries then just hang with no error messages, check the following possibilities:
Possible Cause:
Fully qualified host names must meet the following criteria:
-
The domain part of the host name must be the same as the name returned by the domainname command.
-
After the setting the host name to be fully qualified, you must also update all the necessary /etc and /etc/inet files with the new host name information.
-
The host name must end in a period.
Solution:
Stop the NIS+ service and any associated processes that are hanging on that host or server. Rename the host to match the two requirements listed above. Then reinitialize the server with nisinit. (If queries still hang after you are sure that the host is correctly named, check other problem possibilities in this section.)
NIS+ System Resource Problems
This section describes problems having to do with lack of system resources such as memory, disk space, and so forth.
NIS+ Resource Problem Symptoms
Error messages with operative clauses such as:
Insufficient Memory in NIS+
Lack of sufficient memory or swap space on the system you are working with will cause a wide variety of NIS+ problems and error messages. As a short-term, temporary solution, try to free additional memory by killing unneeded windows and processes. If necessary, exit your windowing system and work from the terminal command line. If you still get messages indicating inadequate memory, you will have to install additional swap space or memory, or switch to a different system that has enough swap space or memory.
Under some circumstances, applications and processes may develop memory leaks and grow too large. you can check the current size of an application or process by running:
ps -el |
The sz (size) column shows the current memory size of each process. If necessary, compare the sizes with comparable processes and applications on a machine that is not having memory problems to see if any have grown too large.
Insufficient Disk Space in NIS+
Lack of disk space will cause a variety of error messages. A common cause of insufficient disk space is failure to regularly remove tmp files and truncate log files. log and tmp files grow steadily larger unless truncated. The speed at which these files grow varies from system to system and with the system state. log files on a system that is working inefficiently or having namespace problems will grow very fast.
Note –
If you are doing a lot of troubleshooting, check your log and tmp files frequently. Truncate log files and remove tmp files before lack of disk space creates additional problems. Also check the root directory and home directories for core files and delete them.
The way to truncate log files is to regularly checkpoint your system (Keep in mind that a checkpoint process may take some time and will slow down your system while it is being performed, checkpointing also requires enough disk space to create a complete copy of the files before they are truncated.)
To checkpoint a system, run nisping -C.
Insufficient Processes in NIS+
On a heavily loaded machine it is possible that you could reach the maximum number of simultaneous processes that the machine is configured to handle. This causes messages with clauses like “unable to fork”. The recommended method of handling this problem is to kill any unnecessary processes. If the problem persists, you can reconfigure the machine to handle more processes as described in your system administration documentation.
NIS+ User Problems
This section describes NIS+ problems that a typical user might encounter.
NIS+ User Problem Symptoms
NIS+ User Cannot Log In
There are many possible reasons for a user being unable to log in:
-
User forgot password. To set up a new password for a user who has forgotten the previous one, run passwd for that user on another machine (naturally, you have to be the NIS+ administrator to do this).
-
Mistyping password. Make sure the user knows the correct password and understands that passwords are case-sensitive and that the letter “o” is not interchangeable with the numeral “0,” nor is the letter “l” the same as the numeral “1.”
-
“Login incorrect” type message. For causes other than simply mistyping the password, see Login Incorrect Message.
-
The user's password privileges have expired (see Password Privilege Expiration in NIS+).
-
An inactivity maximum has been set for this user, and the user has passed it (see Specifying Maximum Number of Inactive Days for Users in NIS+).
-
The user's nsswitch.conf file is incorrect. The passwd entry in that file must be one of the following five permitted configurations:
-
passwd: files
-
passwd: files nis
-
passwd: files nisplus
-
passwd: compat
-
passwd: compat passwd_compat: nisplus
Any other configuration will prevent a user from logging in.
-
(See nsswitch.conf File Requirements for Passwords for further details.)
NIS+ User Cannot Log In Using New Password
Symptoms:
Users who recently changed their password are unable to log in at all, or are able to log in on some machines but not on others.
Possible Causes:
-
It may take some time for the new password to propagate through the network. Have users try to log in with the old password.
-
The password was changed on a machine that was not running NIS+ (see NIS+ User Cannot Log In Using New Password).
NIS+ User Cannot Remote Log In to Remote Domain
Symptoms:
User tries to rlogin to a machine in some other domain and is refused with a “Permission denied” type error message.
Possible Cause:
To rlogin to a machine in another domain, a user must have LOCAL credentials in that domain.
Diagnosis:
Run nismatch username.domainname. cred.org_dir in the other domain to see if the user has a LOCAL credential in that domain.
Solution:
Go to the remote domain and use nisaddcred to create a LOCAL credential for the user in the that domain.
NIS+ User Cannot Change Password
The most common cause of a user being unable to change passwords is that the user is mistyping (or has forgotten) the old password.
Other possible causes:
-
The password Min value has been set to be greater than the password Max value. See Setting Minimum Password Life in NIS+.
-
The password is locked or expired. See Login Incorrect Message and Password Locked, Expired, or Terminated.
Other NIS+ Problems
This section describes problems that do not fit any of the previous categories.
How to Tell if NIS+ Is Running
You may need to know whether a given host is running NIS+. A script may also need to determine whether NIS+ is running.
There are two methods for checking if NIS+ is running.
-
By using the svcs \*nisplus\* command to verify that NIS+ is online
-
By verifying the following items
-
nis_cachemgr is running.
-
The host has a /var/nis/NIS_COLD_START file.
-
nisls succeeds.
-
NIS+ Replica Update Failure
Symptoms:
Error messages indicating that the update was not successfully complete. (Note that the message: replica_update: number updates number errors indicates a successful update.)
Possible Causes:
Any of the following error messages indicate that the server was busy and that the update should be rescheduled:
-
replica_update error result was Master server busy full dump rescheduled, full dump rescheduled
-
replica_update: nis dump result Master server busy, full dump rescheduled
(These messages are generated by, or in conjunction with, the NIS+ error code constant: NIS_DUMPLATER one replica is already resyncing.)
These messages indicate that there was some other problem:
-
replica_update: error result was ...
-
rootreplica_update: update failed nis dump result nis_perror string-variable: could not fetch object from master
(If rpc.nisd is being run with the -C (open diagnostic channel) option, additional information may be entered in either the master server or replica server's system log.
These messages indicate possible problems such as:
-
The server is out of child processes that can be allocated.
-
A read-only child process was requested to dump.
-
Another replica is currently resynching.
Diagnosis:
Check both the replica and server's system log for additional information. How much, if any, additional information is recorded in the system logs depends on your system's error reporting level, and whether or not you are running rpc.nisd with the -C option (diagnostics).
Solution:
In most cases, these messages indicate minor software problems which the system is capable of correcting. If the message was the result of a command, simply wait for a while and then try the command again. If these messages appear often, you can change the threshold level in your /etc/syslog.conf file. See the syslog.conf man page for details.
- © 2010, Oracle Corporation and/or its affiliates
