Extended User Attributes Database (user_attr)
The /etc/user_attr database supplements the passwd and shadow databases. It contains extended user attributes such as authorizations and execution profiles. It also allows roles to be assigned to a user.
A role is a special type of user account that is intended for performing a set of administrative tasks. It is like a normal user account in most respects except that users can gain access to it only through the su command; it is not accessible for normal logins, for example, through the CDE login window. From a role account, a user can access commands with special attributes, typically root user ID, that are not available to users in normal accounts.
The fields in the user_attr database are separated by colons:
user:qualifier:res1:res2:attr |
The fields are described in the following table.
|
Field Name |
Description |
|---|---|
|
user |
The name of the user as specified in the passwd(4) database. |
|
qualifier |
Reserved for future use. |
|
res1 |
Reserved for future use. |
|
res2 |
Reserved for future use. |
|
attr |
An optional list of semicolon-separated (;) key-value pairs that describe the security attributes to be applied when the user runs commands. There are four valid keys: auths, profiles, roles, and type.
|
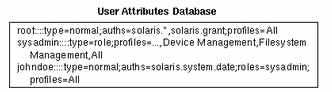
A user_attr database with typical values is shown in the following example.
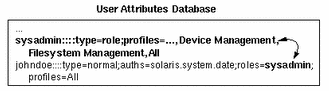
A typical role assignment is illustrated in the following user_attr database. In this example, the sysadmin role has been assigned to the user johndoe. When assuming the sysadmin role, johndoe has access to such profiles as Device Management, Filesystem Management, and the All profile.
- © 2010, Oracle Corporation and/or its affiliates
