Execution Attributes
An execution attribute associated with a profile is a command (with any special security attributes) that can be run by those users or roles to whom the profile is assigned. Special security attributes refer to such attributes as UID, EUID, GID, EGID that can be added to a process when the command is run.
The definitions of the execution attributes are stored in the exec_attr database.
The fields in the exec_attr database are separated by colons:
name:policy:type:res1:res2:id:attr |
The fields are described in the following table.
|
Field Name |
Description |
|---|---|
|
name |
The name of the profile. Profile names are case-sensitive. |
|
policy |
The security policy associated with this entry. Currently, suser (the superuser policy model) is the only valid policy entry. |
|
type |
The type of entity whose attributes are specified. Currently, the only valid type is cmd (command). |
|
res1 |
Reserved for future use. |
|
res2 |
Reserved for future use. |
|
id |
A string identifying the entity; the asterisk wild card can be used. Commands should have the full path or a path with a wild card. To specify arguments, write a script with the arguments and point the id to the script. |
|
attr |
An optional list of semicolon (;) separated key-value pairs that describe the security attributes to apply to the entity upon execution. Zero or more keys may be specified. The list of valid key words depends on the policy being enforced. There are four valid keys: euid, uid, egid, and gid. euid and uid contain a single user name or a numeric user ID. Commands designated with euid run with the effective UID indicated, which is similar to setting the setuid bit on an executable file. Commands designated with uid run with both the real and effective UIDs. egid and gid contain a single group name or numeric group ID. Commands designated with egid run with the effective GID indicated, which is similar to setting the setgid bit on an executable file. Commands designated with gid run with both the real and effective GIDs. |
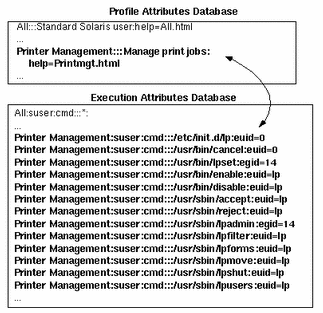
An exec_attr database with some typical values is shown in the following example.

The relationship between the exec_attr and the prof_attr databases is illustrated in the following example. The Printer Management profile is defined in the prof_attr database. It has 13 execution attributes with the appropriate security attributes assigned to it in the exec_attr database.
- © 2010, Oracle Corporation and/or its affiliates
