1.1 System Components and Architecture
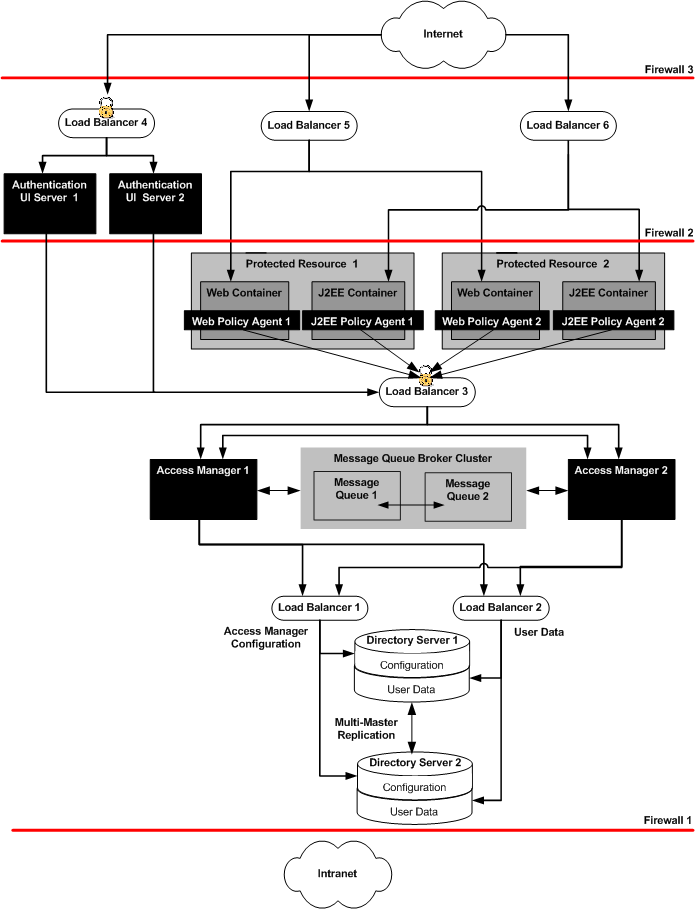
The following components comprise the system environment of the deployment example. Figure 1–1 follows the list and illustrates the components as they will be situated when the deployment is complete.
- Sun Java System Access Manager
-
Two Access Manager servers provide core Access Manager functionality. Both servers share the same configuration data, accessed through a single load balancer deployed in front of two instances of Directory Server.
- Sun Java System Directory Server
-
Two instances of Directory Server provide storage for the Access Manager configuration data and user entries. Configuration data includes information about Access Manager services, realms, policies, and more. User entries will be created and used for testing the deployment. Both Directory Server instances are master replicas that engage in multi-master replication (MMR). MMR allows data to be synchronized in real time between two directories, providing high availability to the Access Manager layer.
Note –No Directory Server Administration Console is installed with the bits downloaded for this deployment example. The command line is used for all Directory Server configurations.
- Protected Resources
-
The protected resources are host machines that contain content for which you want to restrict access. Towards this end, web servers, application servers, and policy agents will be installed. For example, a Human Resources Department might use Sun Java System Web Server to host content and applications. Some of the hosted information must be made available to benefits administration vendors (such as health care providers or stock administrators) that need to access employee information in order to coordinate benefits. These external vendors access the protected resources through an external-facing load balancer. Other information must be restricted to internal Human Resources administrators who access the protected resources through an internal-facing load balancer.
- Sun Java System Access Manager Policy Agents 2.2
-
Both Web Policy Agents and J2EE Policy Agents are used to restrict access to content or applications hosted on the protected resources. The policy agents intercept HTTP requests from external users and redirect the request to Access Manager for authentication. The agent communicates with the Access Manager servers through an internal-facing load balancer.
- Distributed Authentication User Interface
-
The Distributed Authentication User Interface is a component of Access Manager that provides a thin presentation layer for user authentication. During user authentication, a Distributed Authentication Module retrieves the user's credentials and passes them to Access Manager for verification. Thus, the user does not have direct network access to any Access Manager servers.
- Sun Java System Message Queue Broker Cluster
-
Access Manager uses two Message Queue broker instances to form a cluster for distributing client connections and message delivery. The Berkeley Database by Sleepycat Software, Inc. is the session store database. When an Access Manager server goes down and session failover is enabled, the user's session token can be retrieved from one of the Message Queues by the available Access Manager server. This ensures that the user remains continuously authenticated, allowing access to the protected resources without having to reauthenticate.
- Load Balancers
-
The load balancer hardware and software used for this deployment is BIG-IP® manufactured by F5 Networks. They are deployed as follows:
Distributed Authentication User Interface Load Balancer. This external-facing load balancer exposes the remote, web-based Distributed Authentication User Interface for user authentication and self-registration.
Access Manager Load Balancer. This internal-facing load balancer exposes the web-based Access Manager administration console to internal administrators. Alternatively, internal administrators can bypass this load balancer and log in directly to an Access Manager administration console.
Directory Server Load Balancer. The load balancers in front of the Directory Server instances provide round-robin load balancing for Directory Server access, and detects individual Directory Server failures and recovery. Failed servers are taken out of the load balancer list. The load balancer also provides a single virtual Directory Server host name for the Access Manager servers.
Figure 1–1 System Architecture
Note –
Actual firewalls are not set up in this example deployment although they are referred to in this illustration. For information on specific firewall rules, see 2.5 Firewall Rules.
- © 2010, Oracle Corporation and/or its affiliates
