9.2 Configuring Protected Resource 2
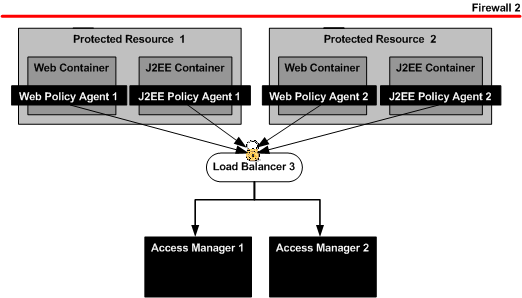
We will install Sun Java™ System Web Server, BEA WebLogic Server, a web policy agent, and a J2EE policy agent on the ProtectedResource–2 host machine. The policy agents are configured to access Load Balancer 3 as illustrated in the following figure.
Figure 9–2 Protected Resources and Policy Agents
Use the following list of procedures as a checklist for configuring Protected Resource 2.
-
9.2.1 Installing Web Container 2 and Web Policy Agent 2 on Protected Resource 2
-
9.2.4 Configuring the J2EE Policy Agent 2 to Communicate Over SSL
9.2.1 Installing Web Container 2 and Web Policy Agent 2 on Protected Resource 2
In this section, you install Sun Java System Web Server and a web policy agent on the ProtectedResource–2 host machine. Use the following list of procedures as a checklist.
-
To Install Sun Java System Web Server as Web Container 2 on Protected Resource 2
-
To Install and Configure Web Policy Agent 2 on Protected Resource 2
-
To Import the Certificate Authority Root Certificate into the Web Server 2 Keystore
-
To Configure Policy for Web Policy Agent 2 on Protected Resource 2
 To Create an Agent Profile for Web Policy
Agent 2
To Create an Agent Profile for Web Policy
Agent 2
You create an agent profile in Access Manager to store authentication and configuration information that will be used by the policy agent to authenticate itself to Access Manager. Creating an agent profile also creates a custom user. The policy agent will, by default, use the account with the user identifier UrlAccessAgent to authenticate to Access Manager.
Note –
Creating an agent profile is not a requirement for web policy agents. You can use the agent's default values and not change the user name; however, in certain cases, you might want to change these default values. For example, if you want to audit the interactions between multiple agents and the Access Manager server, you want be able to distinguish one agent from another. This would not be possible if all the agents used the same default agent user account. For more information, see the Sun Java System Access Manager Policy Agent 2.2 User’s Guide.
-
Access http://AccessManager-1.example.com:1080/amserver/UI/Login from a web browser.
-
Log in to the Access Manager console as the administrator.
- User Name:
-
amadmin
- Password:
-
4m4dmin1
-
Under the Access Control tab, click example, the top-level Realm Name.
-
Click the Subjects tab.
-
Click the Agents tab.
-
Click New to create a new agent profile.
-
On the resulting page, enter the following and click OK.
- ID
-
webagent-2
- Password:
-
web4gent2
- Password Confirm
-
web4gent2
- Device State
-
Choose Active.
The new agent webagent-2 is displayed in the list of agent users.
-
Log out of the console.
 To Install Sun Java System Web Server as Web Container 2 on
Protected Resource 2
To Install Sun Java System Web Server as Web Container 2 on
Protected Resource 2
Download the Sun Java System Web Server bits and install the software on the ProtectedResource–2 host machine.
-
As a root user, log into the ProtectedResource–2 host machine.
-
Install required patches if necessary.
Results for your machines might be different. Read the latest version of the Web Server 7.0 Release Notes to determine if you need to install patches and, if so, what they might be. In this case, the Release Notes indicate that based on the hardware and operating system being used, patch 117461–08 is required.
-
Run patchadd to see if the patch is installed.
# patchadd -p | grep 117461–08
No results are returned which indicates that the patch is not yet installed on the system.
-
Make a directory for downloading the patch you need and change into it.
# mkdir /export/patches # cd /export/patches
-
Download the patches.
You can search for patches directly at http://sunsolve.sun.com. Navigate to the PatchFinder page, enter the patch number, click Find Patch, and download the appropriate patch.
Note –Signed patches are downloaded as JAR files. Unsigned patches are downloaded as ZIP files.
-
Unzip the patch file.
# unzip 117461–08.zip
-
Run patchadd to install the patches.
# patchadd /export/patches/117461–08
-
After installation is complete, run patchadd to verify that the patch was added successfully.
# patchadd -p | grep 117461–08
In this example, a series of patch numbers are displayed, and the patch 117461–08 is present.
-
-
Create a directory into which you can download the Web Server bits and change into it.
# mkdir /export/ws7 # cd /export/ws7
-
Download the Sun Java System Web Server 7.0 software from http://www.sun.com/download/products.xml?id=45ad781d.
Follow the instructions on the Sun Microsystems Product Downloads web site for downloading the software. In this example, the software was downloaded to the /export/ws7 directory.
# ls -al total 294548 drwxr-xr-x 2 root root 512 Aug 7 13:23 . drwxr-xr-x 3 root sys 512 Aug 7 13:16 .. -rw-r--r-- 1 root root 150719523 Aug 7 13:24 sjsws-7_0-solaris-sparc.tar.gz
-
Unpack the Web Server bits.
# gunzip sjsws-7_0-solaris-sparc.tar.gz # tar xvf sjsws-7_0-solaris-sparc.tar
-
Run setup.
# ./setup --console
-
When prompted, provide the following information.
You are running the installation program for the Sun Java System Web Server 7.0. ... The installation program pauses as questions are presented so you can read the information and make your choice. When you are ready to continue, press Enter.
Press Enter. Continue to press Enter when prompted.
Have you read the Software License Agreement and do you accept all the terms?
Enter yes.
Sun Java System Web Server 7.0 Installation Directory [/sun/webserver7]
Enter /opt/SUNWwbsvr
Specified directory /opt/SUNWwbsvr does not exist. Create Directory? [Yes/No]
Enter yes.
Select Type of Installation 1. Express 2. Custom 3. Exit What would you like to do? [1]
Enter 2.
Component Selection 1. Server Core 2. Server Core 64-biy Binaries 3. Administration Command Line Interface 4. Sample Applications 5. Language Pack Enter the comma-separated list [1,2,3,4,5]
Enter 1,3,5.
Java Configuration 1. Install Java Standard Edition 1.5.0_09 2. Reuse existing Java SE 1.5.0_09 or greater 3. Exit What would you like to do? [1]
Enter 1.
Administrative Options 1. Create an Administration Server and a Web Server Instance 2. Create an Administration Node Enter your option. [1]
Enter 1.
Start servers during system startup. [yes/no]
Enter no.
Host Name [ProtectedResource-2.example.com]
Accept the default value.
SSL Port [8989]
Accept the default value.
Create a non-SSL Port? [yes/no]
Enter no.
Runtime User ID [webservd]
Enter root.
Administrator User Name [admin]
Accept the default value.
Administrator Password:
Enter web4dmin.
Retype Password:
Enter web4dmin.
Server Name [ProtectedResource-2.example.com]
Accept the default value.
Http Port [8080]
Enter 1080.
Document Root Directory [/opt/SUNWwbsvr/ https-ProtectedResource-2.example.com/docs]
Accept the default value.
Ready To Install 1. Install Now 2. Start Over 3. Exit Installation What would you like to do?
Enter1.
When installation is complete, the following message is displayed:
Installation Successful.
-
Start the Web Server administration server.
# cd /opt/SUNWwbsvr/admin-server/bin # ./startserv server not running Sun Java System Web Server 7.0 B12/04/2006 10:15 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, Version 1.5.0_09] from [Sun M icrosystems Inc.] info: WEB0100: Loading web module in virtual server [admin-server] at [/admingui ] info: WEB0100: Loading web module in virtual server [admin-server] at [/jmxconne ctor] info: HTTP3072: admin-ssl-port: https://protectedresource-2.example.com:8989 ready to accept requests info: CORE3274: successful server startup
-
Run netstat to verify that the port is open and listening.
# netstat -an | grep 8989 *.8989 *.* 0 0 49152 0 LISTEN
-
(Optional) Login to the Web Server administration console at https://protectedresource-2.example.com:8989.
- Username
-
admin
- Password
-
web4dmin
You should see the Web Server console.
-
(Optional) Log out of the Web Server console.
-
Start the Protected Resource 2 Web Server instance.
# cd /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/bin # ./startserv server not running Sun Java System Web Server 7.0 B12/04/2006 10:15 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, Version 1.5.0_09] from [Sun Microsystems Inc.] info: HTTP3072: http-listener-1: http://ProtectedResource-2.example.com:1080 ready to accept requests info: CORE3274: successful server startup
-
Run netstat to verify that the port is open and listening.
# netstat -an | grep 1080 *.1080 *.* 0 0 49152 0 LISTEN
-
Access the Protected Resource 2 instance at https://ProtectedResource-2.example.com:1080 using a web browser.
You should see the default Web Server index page.
-
Log out of the ProtectedResource–2 host machine.
 To Install and Configure Web Policy Agent
2 on Protected Resource 2
To Install and Configure Web Policy Agent
2 on Protected Resource 2
Due to a known problem with this version of the Web Policy Agent, you must start an X-display session on the server host using a program such as Reflections X or VNC, even though you use the command-line installer. For more information about this known problem, see On UNIX-based machines, all web agents require that the X11 DISPLAY variable be set properly. in Sun Java System Access Manager Policy Agent 2.2 Release Notes.
-
As a root user, log into the ProtectedResource–2 host machine.
-
Ensure that your system is properly patched.
This should have been done in To Install Sun Java System Web Server as Web Container 2 on Protected Resource 2.
-
Create a directory into which you can download the Web Server agent bits and change into it.
# mkdir /export/WebPA2 # cd /export/WebPA2
-
Download the web policy agent for Web Server from http://www.sun.com/download/.
# ls -al total 294548 drwxr-xr-x 2 root root 512 Aug 7 13:23 . drwxr-xr-x 3 root sys 512 Aug 7 13:16 .. -rw-r--r-- 1 root root 150719523 Aug 7 13:24 sjsws_v70_SunOS_agent.zip
-
Unzip the downloaded file.
# unzip sjsws_v70_SunOS_agent.zip
-
Change the permissions for the resulting agentadmin binary.
# cd /export/WebPA2/web_agents/sjsws_agent/bin # chmod +x agentadmin
-
Verify that crypt_util has execute permission before running the installer.
# cd /export/WebPA2/web_agents/sjsws_agent/bin # chmod +x crypt_util
-
Create a temporary file for the password that will be required during agent installation.
# echo web4gent2 > /export/WebPA2/pwd.txt # cat /export/WebPA2/pwd.txt
-
Run the agent installer.
# ./agentadmin --install
-
When prompted, do the following.
Do you completely agree with all the terms and conditions of this License Agreement (yes/no): [no]:
Type yes and press Enter.
********************************************* Welcome to the Access Manager Policy Agent for Sun Java System Web Server If the Policy Agent is used with Federation Manager services, User needs to enter information relevant to Federation Manager. ***************************************************
Enter the complete path to the directory which is used by Sun Java System Web Server to store its configuration Files. This directory uniquely identifies the Sun Java System Web Server instance that is secured by this Agent. [ ? : Help, ! : Exit ] Enter the Sun Java System Web Server Config Directory Path [/var/opt/SUNWwbsvr7/ https-ProtectedResource-2.example.com/config]:
Type /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/config and press Enter.
Enter the fully qualified host name of the server where Access Manager Services are installed. [ ? : Help, < : Back, ! : Exit ] Access Manager Services Host:
Type LoadBalancer-3.example.com and press Enter.
Enter the port number of the Server that runs Access Manager Services. [ ? : Help, < : Back, ! : Exit ] Access Manager Services port [80]:
Type 9443 and press Enter.
Enter http/https to specify the protocol used by the Server that runs Access Manager services. [ ? : Help, < : Back, ! : Exit ] Access Manager Services Protocol [http]:
Type https and press Enter.
Enter the Deployment URI for Access Manager Services. [ ? : Help, < : Back, ! : Exit ] Access Manager Services Deployment URI [/amserver]:
Press Enter to accept the default /amserver.
Enter the fully qualified host name on which the Web Server protected by the agent is installed. [ ? : Help, < : Back, ! : Exit ] Enter the Agent Host name:
Type ProtectedResource-2.example.com and press Enter.
Enter the preferred port number on which the Web Server provides its services. [ ? : Help, < : Back, ! : Exit ] Enter the port number for Web Server instance [80]:
Type 1080 and press Enter.
Select http or https to specify the protocol used by the Web server instance that will be protected by Access Manager Policy Agent. [ ? : Help, < : Back, ! : Exit ] Enter the Preferred Protocol for Web Server instance [http]:
Press Enter to accept the default http.
Enter a valid Agent profile name. Before proceeding with the agent installation, please ensure that a valid Agent profile exists in Access Manager. [ ? : Help, < : Back, ! : Exit ] Enter the Agent Profile name [UrlAccessAgent]:
Type webagent-2 and press Enter.
Enter the path to a file that contains the password to be used for identifying the Agent. [ ? : Help, < : Back, ! : Exit ] Enter the path to the password file:
Type /export/WebPA2/pwd.txt and press Enter.
----------------------------------------- SUMMARY OF YOUR RESPONSES ----------------------------------------------- Sun Java System Web Server Config Directory : /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/ config Access Manager Services Host : LoadBalancer-3.example.com Access Manager Services Port : 9443 Access Manager Services Protocol : https Access Manager Services Deployment URI : /amserver Agent Host name : ProtectedResource-2.example.com Web Server Instance Port number : 1080 Protocol for Web Server instance : http Agent Profile name : webagent-2 Agent Profile Password file name : /export/WebPA2/pwd.txt Verify your settings above and decide from the choices below. 1. Continue with Installation 2. Back to the last interaction 3. Start Over 4. Exit Please make your selection [1]:
Type 1 and press Enter.
Creating directory layout and configuring Agent file for Agent_001 instance ...DONE. Reading data from file /export/WebPA2/pwd.txt and encrypting it ...DONE. Generating audit log file name ...DONE. Creating tag swapped AMAgent.properties file for instance Agent_001 ...DONE. Creating a backup for file /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/ config/obj.conf ...DONE. Creating a backup for file /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/ config/magnus.conf ...DONE. Adding Agent parameters to /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/ config/magnus.conf file ...DONE. Adding Agent parameters to /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/ config/obj.conf file ...DONE. SUMMARY OF AGENT INSTALLATION ----------------------------- Agent instance name: Agent_001 Agent Configuration file location: /export/WebPA2/web_agents/sjsws_agent/Agent_001/ config/AMAgent.properties Agent Audit directory location: /export/WebPA2/web_agents/sjsws_agent/Agent_001/ logs/audit Agent Debug directory location: /export/WebPA2/web_agents/sjsws_agent/Agent_001/ logs/debug Install log file location: /export/WebPA2/web_agents/sjsws_agent/logs/audit/ install.log Thank you for using Access Manager Policy Agent
-
Modify the AMAgent.properties file.
Tip –Backup AMAgent.properties before you modify it.
-
Change to the config directory.
# cd /export/WebPA2/web_agents/sjsws_agent/Agent_001/config
-
Set the values of the following properties as shown.
com.sun.am.policy.am.login.url = https://LoadBalancer-3. example.com:9443/amserver/UI/Login?realm=users com.sun.am.load_balancer.enable = true
-
Save the file and close it.
-
-
Restart the Protected Resource 2 Web Server instance.
# cd /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/bin # ./stopserv; ./startserv server has been shutdown Sun Java System Web Server 7.0 B12/04/2006 10:15 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, Version 1.5.0_09] from [Sun Microsystems Inc.] info: HTTP3072: http-listener-1: http://ProtectedResource-2.example.com:1080 ready to accept requests
-
Log out of the ProtectedResource–2 host machine.
 To Import the Certificate Authority Root Certificate
into the Web Server 2 Keystore
To Import the Certificate Authority Root Certificate
into the Web Server 2 Keystore
The web policy agent on Protected Resource 2 connects to Access Manager through Load Balancer 3. The load balancer is SSL-enabled, so the agent must be able to trust the load balancer SSL certificate to establish the SSL connection. For this reason, import the root certificate of the Certificate Authority (CA) that issued the Load Balancer 3 SSL server certificate into the policy agent keystore.
Before You Begin
Import the same CA root certificate used in To Import a Certificate Authority Root Certificate on the Access Manager Load Balancer.
-
As a root user, log into the ProtectedResource–2 host machine.
-
Copy the CA root certificate into a directory.
In this example, the file is /export/software/ca.cer.
-
Import the CA root certificate into the Java keystore.
# /opt/SUNWwbsvr/jdk/jre/bin/keytool -import -trustcacerts -alias OpenSSLTestCA -file /export/software/ca.cer -keystore /opt/SUNWwbsvr/jdk/jre/lib/security/cacerts -storepass changeit Owner: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Issuer: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Serial number: 97dba0aa26db6386 Valid from: Tue Apr 18 07:66:19 PDT 2006 until: Tue Jan 13 06:55:19 PST 2009 Certificate fingerprints: MD5: 9f:57:ED:B2:F2:88:B6:E8:0F:1E:08:72:CF:70:32:06 SHA1: 31:26:46:15:C5:12:5D:29:46:2A:60:A1:E5:9E:26:64:36:80:E4:70 Trust this certificate: [no] yes Certificate was added to keystore.
-
Verify that the CA root certificate was imported into the keystore.
# /opt/SUNWwbsvr/jdk/jre/bin/keytool -list -keystore /opt/SUNWwbsvr/jdk/jre/lib/security/cacerts -storepass changeit | grep -i open openssltestca, Sep 10, 2007, trustedCertEntry,
-
Restart the Protected Resource 2 Web Server instance.
# cd /opt/SUNWwbsvr/https-ProtectedResource-2.example.com/bin # ./stopserv # ./startserv server has been shutdown Sun Java System Web Server 7.0 B12/04/2006 10:15 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, Version 1.5.0_09] from [Sun Microsystems Inc.] info: HTTP3072: http-listener-1: http://ProtectedResource-2. example.com:1080 ready to accept requests info: CORE3274: successful server startup
-
Log out of the ProtectedResource–2 host machine.
 To Configure Policy for Web Policy Agent 2
on Protected Resource 2
To Configure Policy for Web Policy Agent 2
on Protected Resource 2
Use the Access Manager console to configure policy for Web Policy Agent 2. This policy will be used to verify that Web Policy Agent 2 is working properly. You will modify this policy later when we add a load balancer in front of it.
-
Access http://AccessManager-1.example.com:1080/amserver/UI/Login from a web browser.
-
Log in to the Access Manager console as the administrator.
- Username
-
amadmin
- Password
-
4m4dmin1
-
Create a referral policy in the top-level realm.
-
Under the Access Control tab, click the top-level realm, example.
-
Click the Policies tab.
-
Click Referral URL Policy for users realm.
-
On the same page, in the Rules section, click New.
-
On the resulting page, select URL Policy Agent (with resource name) as a Service Type and click Next.
-
Provide the following information on the resulting page.
- Name:
-
URL Rule for ProtectedResource-2
- Resource Name:
-
http://ProtectedResource-2.example.com:1080/*
-
Click Finish.
-
Click Save.
-
On the Edit Policy page, click Back to Policies.
Under the Policies tab for the example realm, you should see the policy named Referral URL Policy for users realm with http://ProtectedResource-2.example.com:1080/* added in the list of protected resources.
-
-
Create a policy in the users realm.
The users realm was previously created in 7.2 Creating and Configuring a Realm for Test Users.
-
Click the Access Control tab.
-
Under Realms, click users.
-
Click the Policies tab.
-
Click New Policy.
-
On the New Policy page, provide the following information:
- Name:
-
URL Policy for ProtectedResource-2
- Active:
-
Mark the Yes checkbox.
-
On the same page, in the Rules section, click New.
-
Select a Service Type for the rule and click Next.
URL Policy Agent (with resource name) is the only choice.
-
On the resulting page, provide the following information:
- Name:
-
URL Rule for ProtectedResource-2
- Resource Name:
-
Click http://ProtectedResource-2.example.com:1080/*, listed in the Parent Resource Name list, to add it to the Resource Name field.
- GET:
-
Mark this checkbox, and select Allow.
- POST:
-
Mark this checkbox, and select Allow.
-
Click Finish.
-
-
Create a new subject in the users realm for testing.
-
On the New Policy page, in the Subjects section, click New.
-
Select Access Manager Identity Subject as the subject type and click Next.
-
Provide the following information on the resulting page.
- Name:
-
Test Subject
- Filter:
-
Choose User and click Search. Two users are added to the Available list.
- Available:
-
In the list, select Test User1 and click Add.
-
Click Finish.
-
-
Back on the New Policy page, click Create.
Under the Policies tab, you should see the policy named URL Policy for ProtectedResource-2.
-
Log out of the console.
 To Verify that Web Policy Agent 2 is Working
Properly
To Verify that Web Policy Agent 2 is Working
Properly
-
Access http://ProtectedResource-2.example.com:1080 from a web browser.
-
Log in to Access Manager as testuser1.
- Username
-
testuser1
- Password
-
password
You should see the default index page for Web Server 2 as testuser1 was configured in the test policy to be allowed to access Protected Resource 2.
-
Log out and close the browser.
-
Once again, access http://ProtectedResource-2.example.com:1080 from a web browser.
Tip –If you are not redirected to the Access Manager login page for authentication, clear your browser's cache and cookies and try again.
-
Log in to Access Manager as testuser2.
- Username
-
testuser2
- Password
-
password
You should see the message, You're not authorized to view this page, (or Your client is not allowed to access the requested object) as testuser2 was not included in the test policy that allows access to Protected Resource 2.
9.2.2 Installing and Configuring the J2EE Container 2 and J2EE Policy Agent 2 on Protected Resource 2
In this section, you will download the BEA WebLogic Server bits and install this application server on the ProtectedResource–2 host machine. Additionally, you will download and install the appropriate J2EE policy agent, deploy the policy agent application, setup up an authentication provider, and modify the Bypass Principal List. Use the following list of procedures as a checklist for installing Application Server 2 and the J2EE Policy Agent 2.
-
To Install BEA WebLogic Server as J2EE Container 2 on Protected Resource 2
-
To Configure BEA WebLogic Server as J2EE Container 2 on Protected Resource 2
 To Install BEA WebLogic Server as J2EE Container
2 on Protected Resource 2
To Install BEA WebLogic Server as J2EE Container
2 on Protected Resource 2
BEA WebLogic Server is the application server used as the J2EE container on Protected Resource 2. After installing the bits in this procedure, see To Configure BEA WebLogic Server as J2EE Container 2 on Protected Resource 2.
-
As a root user, log into the ProtectedResource–2 host machine.
-
Ensure that your system is properly patched.
Refer to the BEA web site to make sure that your system has the recommended patches.
-
Create a directory into which you can download the WebLogic Server bits and change into it.
# mkdir /export/BEAWL92 # cd /export/BEAWL92
-
Download the WebLogic Server bits from http://commerce.bea.com/.
For this deployment, we download the Solaris version.
# ls -al total 294548 drwxr-xr-x 2 root root 512 Aug 7 13:23 . drwxr-xr-x 3 root sys 512 Aug 7 13:16 .. -rw-r--r-- 1 root root 722048346 Aug 7 13:24 portal920_solaris32.bin
-
Run the installer.
# ./portal920_solaris32.bin
-
When prompted, do the following:
Accept the License agreement
Select Yes and click Next.
Create a new BEA Home
Type /usr/local/bea and click Next.
Select "Custom"
Click Next.
Deselect the following: - Workshop for WebLogic Platform - WebLogic Portal
Click Next.
Choose Product Installation Directories
Type /usr/local/bea/weblogic92 and click Next.
Installation Complete
Deselect Run Quickstart and click Done.
-
Verify that the application was correctly installed.
# cd /usr/local/bea # ls -al total 34 drwxr-xr-x 6 root root 512 Sep 13 14:26 . drwxr-xr-x 3 root root 512 Sep 13 14:22 .. -rwxr-xr-x 1 root root 851 Sep 13 14:26 UpdateLicense.sh -rw-r--r-- 1 root root 14 Sep 13 14:26 beahomelist drwxr-xr-x 6 root root 512 Sep 13 14:26 jdk150_04 -rw-r--r-- 1 root root 7818 Sep 13 14:26 license.bea drwxr-xr-x 2 root root 512 Sep 13 14:26 logs -rw-r--r-- 1 root root 947 Sep 13 14:26 registry.xml drwxr-xr-x 3 root root 512 Sep 13 14:26 utils drwxr-xr-x 10 root root 512 Sep 13 14:26 weblogic92
 To Configure BEA WebLogic Server as J2EE Container
2 on Protected Resource 2
To Configure BEA WebLogic Server as J2EE Container
2 on Protected Resource 2
After installing the bits, WebLogic Server must be configured for use as the J2EE container on Protected Resource 2.
Before You Begin
This procedure assumes you have just completed To Install BEA WebLogic Server as J2EE Container 2 on Protected Resource 2.
-
Run the WebLogic Server configuration script.
# cd /usr/local/bea/weblogic92/common/bin # ./config.sh
-
When prompted, do the following:
-
Start the WebLogic administration server.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2 # ./startWebLogic.sh
When prompted, type the following credentials.
- Username
-
weblogic
- Password
-
w3bl0g1c
-
Run the netstat command to verify that the port is open and listening.
# netstat -an | grep 7001 XXX.XX.XX.151.7001 *.* 0 0 49152 0 LISTEN XXX.X.X.1.7001 *.* 0 0 49152 0 LISTEN
Note –You can also access the administration console by pointing a browser to http://protectedresource-2.example.com:7001/console.
-
Change to the AdminServer directory.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2/servers/AdminServer
-
Create a security directory and change into it.
# mkdir security # cd security
-
Create a boot.properties file for the WebLogic Server administration server.
The administrative user and password are stored in boot.properties. Application Server 2 uses this information during startup. WebLogic Server encrypts the file, so there is no security risk even if you enter the user name and password in clear text.
# cat > boot.properties username=weblogic password=w3bl0g1c Hit Control D to terminate the command ^D
-
Restart the WebLogic administration server to encrypt the username and password in boot.properties.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2/bin # ./stopWebLogic.sh # ./startWebLogic.sh
-
Start the ApplicationServer-2 managed instance.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2/bin # ./startManagedWebLogic.sh ApplicationServer-2 t3://localhost:7001
You will be prompted for the following credentials.
- Username
-
weblogic
- Password
-
w3bl0g1c
-
Change to the ApplicationServer-2 directory.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2/ servers/ApplicationServer-2
-
Create a security directory and change into it.
# mkdir security # cd security
-
Create a boot.properties file for the ApplicationServer-2 managed instance.
The administrative user and password are stored in boot.properties. The WebLogic Server managed instance uses this information during startup. WebLogic Server encrypts the file, so there is no security risk even if you enter the user name and password in clear text.
# cat > boot.properties username=weblogic password=w3bl0g1c Hit Control D to terminate the command ^D
-
Restart the managed server.
# cd /usr/local/bea/user_projects/domains/ ProtectedResource-2/bin # ./stopManagedWebLogic.sh ApplicationServer-2 t3://localhost:7001 # ./startManagedWebLogic.sh ApplicationServer-2 t3://localhost:7001 -
Run the netstat command to verify that the port is open and listening.
# netstat -an | grep 1081 XXX.X.X.1.1081 *.* 0 0 49152 0 LISTEN XXX.XX.XX.151.1081 *.* 0 0 49152 0 LISTEN
-
Access http://ProtectedResource-2.example.com:7001/console from a web browser.
-
Login to the BEA WebLogic Server as the administrator.
- Username
-
weblogic
- Password
-
w3bl0g1c
-
Click servers.
On the Summary of Servers page, verify that both AdminServer (admin) and ApplicationServer-2 are running and OK.
-
Log out of the console.
-
Log out of the ProtectedResource–2 host machine.
 To Create an Agent Profile for the J2EE Policy
Agent 2
To Create an Agent Profile for the J2EE Policy
Agent 2
This new agent profile will be used by J2EE Policy Agent 2 to authenticate to Access Manager.
-
Access http://LoadBalancer-3.example.com:7070/amserver/UI/Login, the Access Manage load balancer, from a web browser.
-
Log in to the Access Manager console as the administrator.
- Username
-
amadmin
- Password
-
4m4dmin1
-
On the Access Control tab, click the top-level realm, example.
-
Click the Subjects tab.
-
Click the Agents tab.
-
On the Agent page, click New.
-
On the New Agent page, provide the following information and click OK.
- ID:
-
j2eeagent-2
- Password:
-
j2ee4gent2
- Password Confirm:
-
j2ee4gent2
- Device State:
-
Choose Active.
The new agent j2eeagent–2 is displayed in the list of Agent Users.
-
Log out of the Access Manager console.
-
As a root user, log into the ProtectedResource–2 host machine.
-
Create a directory into which you can download the J2EE policy agent bits and change into it.
# mkdir /export/J2EEPA2 # cd /export/J2EEPA2
-
Create a text file that contains the Agent Profile password.
The J2EE Policy Agent installer requires this file for installation.
# cat > agent.pwd j2ee4gent2 Hit Control D to terminate the command ^D
-
Log out of the ProtectedResource–2 host machine.
 To Install the J2EE Policy Agent 2 on Application
Server 2
To Install the J2EE Policy Agent 2 on Application
Server 2
Before You Begin
You must stop both the WebLogic Server 2 managed instance and the WebLogic Server 2 administration server before beginning the installation process.
-
As a root user, log into the ProtectedResource–2 host machine.
-
Stop the WebLogic Server 2 administration server and the WebLogic Server 2 managed instance.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2/bin # ./stopManagedWebLogic.sh ApplicationServer-2 t3://localhost:7001 # ./stopWebLogic.sh
-
Ensure that your system is properly patched.
Read the appropriate policy agent Release Notes for your web container to determine the latest patches you might need to install before beginning installation. In this case, no patch is required.
Note –You can search for patches directly at http://sunsolve.sun.com. Navigate to the PatchFinder page, enter the patch number, click Find Patch, and download the appropriate patch.
-
Change into the J2EEPA2 directory.
# cd /export/J2EEPA2
-
Download the J2EE policy agent bits for WebLogic Server from http://www.sun.com/download/index.jsp.
# ls -al total 8692 drwxr-xr-x 2 root root 512 Sep 13 13:19 . drwxr-xr-x 5 root sys 512 Aug 13 17:08 .. -rw-r--r-- 1 root root 4433920 Sep 13 13:19 SJS_Weblogic_92_agent_2.2.tar
-
Unpack the J2EE policy agent bits.
# /usr/sfw/bin/gtar -xvf /export/J2EEPA2/SJS_Weblogic_92_agent_2.2.tar
Tip –Use the gtar command and not the tar command.
-
Run the J2EE policy agent installer.
# cd /export/J2EEPA2/j2ee_agents/am_wl92_agent/bin # ./agentadmin --install
-
When prompted, provide the following information.
Please read the following License Agreement carefully:
Press Enter to continue. Continue to press Enter until you reach the end of the License Agreement.
Enter startup script location.
Enter .
/usr/local/bea/user_projects/domains/ ProtectedResource-2/bin/ startwebLogic.sh
Enter the WebLogic Server instance name: [myserver]
Enter ApplicationServer-2.
Access Manager Services Host:
Enter LoadBalancer-3.example.com.
Access Manager Services port: [80]
Enter 7070.
Access Manager Services Protocol: [http]
Accept the default value.
Access Manager Services Deployment URI: [/amserver]
Accept the default value.
Enter the Agent Host name:
ProtectedResource-2.example.com
Enter the WebLogic home directory: [/usr/local/bea/weblogic92]
Accept the default value.
Enter true if the agent is being installed on a Portal domain:
Accept false, the default value.
Enter the port number for Application Server instance [80]:
Enter 1081.
Enter the Preferred Protocol for Application instance [http]:
Accept the default value.
Enter the Deployment URI for the Agent Application [/agentapp]
Accept the default value.
Enter the Encryption Key [j8C9QteM1HtC2OhTTDh/f1LhT38wfX1F]:
Accept the default value.
Enter the Agent Profile Name:
j2eeagent-2
Enter the path to the password file:
Enter /export/J2EEPA2/agent.pwd.
Are the Agent and Access Manager installed on the same instance of Application Server? [false]:
Accept the default value.
Verify your settings and decide from the choices below: 1. Continue with Installation 2. Back to the last interaction 3. Start Over 4. Exit Please make your selection [1]:
Accept the default value.
The installer runs and, when finished, creates a new file in the bin directory called setAgentEnv_ApplicationServer-2.sh.
-
Modify the startup script setDomainEnv.sh to reference setAgentEnv_ApplicationServer-2.sh.
Tip –Backup setDomainEnv.sh before you modify it.
-
Change permissions for setAgentEnv_ApplicationServer-2.sh.
# chmod 755 setAgentEnv_ApplicationServer-2.sh
-
Start the WebLogic Server administration server.
# ./startWebLogic.sh &
Watch for startup errors.
-
Log out of the ProtectedResource–2 host machine.
 To Deploy the J2EE Policy Agent 2 Application
To Deploy the J2EE Policy Agent 2 Application
The agent application is a housekeeping application bundled with the agent binaries and used by the agent for notifications and other internal functionality. In order for the agent to function correctly, this application must be deployed on the agent-protected deployment container instance using the same URI that was supplied during the agent installation process. For example, during the installation process, if you entered /agentapp as the deployment URI for the agent application, use that same context path in the deployment container.
-
Access http://ProtectedResource-2.example.com:7001/console from a web browser.
-
Log in to the WebLogic Server console as the administrator.
- Username
-
weblogic
- Password
-
w3bl0g1c
-
Under Domain Structure, click Deployments.
-
On the Summary of Deployments page, in the Change Center, click Lock & Edit.
-
Under Deployments, click Install.
-
On the Install Application Assistant page, click the protectedresource-2.example.com link.
-
In the field named Location: protectedresource-2.example.com, click the root directory.
-
Navigate to /export/J2EEPA2/j2ee_agents/am_wl92_agent/etc, the application directory.
-
Select agentapp.war and click Next.
-
In the Install Application Assistant page, choose Install this deployment as an application and click Next.
-
In the list of Servers, mark the checkbox for ApplicationServer-2 and click Next.
-
In the Optional Settings page, click Next.
-
Click Finish.
-
On the Settings for agentapp page, click Save.
-
In the Change Center, click Activate Changes.
 To Start the J2EE Policy Agent 2 Application
To Start the J2EE Policy Agent 2 Application
Before You Begin
This procedure assumes that you have just completed To Deploy the J2EE Policy Agent 2 Application.
-
In the WebLogic Server console, on the Settings for agentapp page, click Deployments.
-
On the Summary of Deployments page, mark the agentapp checkbox and click Start > Servicing all requests.
-
On the Start Application Assistant page, click Yes.
Note –You may encounter a JavaScript error as the agent application will not start until you start the WebLogic Server. In this case start the ApplicationServer-2 managed instance and perform the steps again.
 To Set Up the J2EE Policy Agent 2 Authentication
Provider
To Set Up the J2EE Policy Agent 2 Authentication
Provider
Before You Begin
This procedure assumes that you have just completed To Start the J2EE Policy Agent 2 Application.
-
In the WebLogic Server console, on the Summary of Deployments page, under Domain Structure, click Security Realms.
-
On the Summary of Security Realms page, click Lock & Edit.
-
Click the myrealm link.
-
On the Settings for myrealm page, click the Providers tab.
-
Under Authentication Providers, click New.
-
On the Create a New Authentication Provider page, provide the following information and click OK.
- Name:
-
Agent-2
- Type:
-
Select AgentAuthenticator from the drop down list.
Agent-2 is now included in the list of Authentication Providers.
-
In the list of Authentication Providers, click Agent-2.
-
In the Settings for Authentication Providers page, verify that the Control Flag is set to OPTIONAL.
-
In the navigation tree near the top of the page, click Providers.
-
In the list of Authentication Providers, click DefaultAuthenticator.
-
In the Settings for DefaultAuthenticator page, set the Control Flag to OPTIONAL and click Save.
-
In the navigation tree near the top of the page, click Providers again.
-
In the Change Center, click Activate Changes.
-
(Optional) If indicated by the console, restart the servers.
-
Log out of the WebLogic Server console.
-
As a root user, log into the ProtectedResource–2 host machine.
-
Restart the administration server and the managed instance.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2/bin # ./stopManagedWebLogic.sh ApplicationServer-2 t3://localhost:7001 # ./stopWebLogic.sh # ./startWebLogic.sh # ./startManagedWebLogic.sh ApplicationServer-2 t3://localhost:7001
-
Log out of the ProtectedResource–2 host machine.
-
 To Edit the J2EE Policy Agent 2 AMAgent.properties File
To Edit the J2EE Policy Agent 2 AMAgent.properties File
-
As a root user, log into the ProtectedResource–2 host machine.
-
Change to the directory that contains the AMAgent.properties file.
# cd /export/J2EEPA2/j2ee_agents/am_wl92_agent/agent_001/config
Tip –Backup AMAgent.properties before you modify it.
-
Make the following modifications to AMAgent.properties.
-
Set the following property.
com.sun.identity.agents.config.bypass.principal[0] = weblogic
This ensures that the WebLogic administrator will be authenticated against WebLogic itself and not Access Manager.
-
At end of the file, insert the following new property.
com.sun.identity.session.resetLBCookie=true
You must add this property if session failover has been configured for Access Manager. If session failover is not configured and this property is added, it could negatively impact performance. If session failover is enabled for Access Manager and this property is not added, the session failover functionality will work properly but, the stickiness to the Access Manager server will not be maintained after failover occurs. This property is not required for web policy agents.
 Caution –
Caution – This property must be also be added to the Access Manager file, AMConfig.properties if added here.
-
-
Save and close the file.
-
Log out of the ProtectedResource–2 host machine.
9.2.3 Setting Up a Test for the J2EE Policy Agent 2
Use the following list of procedures as a checklist for setting up a test for the J2EE Policy Agent 2.
-
To Create a Test Referral Policy in the Access Manager Root Realm
-
To Configure Properties for the J2EE Policy Agent 2 Sample Application
 To Deploy the J2EE Policy Agent 2 Sample Application
To Deploy the J2EE Policy Agent 2 Sample Application
The BEA Policy Agent comes with a sample application created to help test policies. For more information, see the file readme.txt in the /export/J2EEPA2/j2ee_agents/am_wl92_agent/sampleapp directory.
-
Access http://ProtectedResource-2.example.com:7001/console from a web browser.
-
Log in to the WebLogic Server console as the administrator.
- Username
-
weblogic
- Password
-
w3bl0g1c
-
On the Summary of Deployments page, click Lock & Edit.
-
Under Domain Structure, click Deployments.
-
Under Deployments, click Install.
-
On the Install Application Assistant page, click the protectedresource-2.example.com link.
-
In the list for Location: protectedresource-2.example.com, click the root directory.
-
Navigate to the application directory (/export/J2EEPA2/j2ee_agents/am_wl9_agent/sampleapp/dist), select agentsample and click Next.
-
In the Install Application Assistant page, choose Install this deployment as an application and click Next.
-
In the list of Servers, mark the checkbox for ApplicationServer-2 and click Next.
-
On the Optional Settings page, click Next to accept the default settings.
-
On the Review Your Choices page, click Finish.
The Target Summary section indicates that the module agentsample will be installed on the target ApplicationServer-2.
-
On the Settings for agentsample page, click Save.
-
On the Settings for agentsample page, click Activate Changes.
-
Under Domain Structure, click Deployments.
-
In the Deployments list, mark the checkbox for agentsample and click Start > Servicing All Requests.
-
On the Start Application Assistant page, click Yes.
The state of the deployment changes from Prepared to Active.
-
Log out of the console.
 To Create a Test Referral Policy in the Access Manager Root
Realm
To Create a Test Referral Policy in the Access Manager Root
Realm
-
Access http://LoadBalancer-3.example.com:7070/amserver/UI/Login, the Access Manager load balancer, from a web browser.
-
Log in to the Access Manager console as the administrator.
- Username
-
amadmin
- Password
-
4m4dmin1
-
Under the Access Control tab, click the example realm link.
-
Click the Policies tab.
-
Under Policies, click the Referral URL Policy for users realm link.
-
On the Edit Policy page, under Rules, click New.
-
On the resulting page, select URL Policy Agent (with resource name) and click Next.
-
On the resulting page, provide the following information and click Finish.
- Name:
-
URL Policy for ApplicationServer-2
- Resource Name:
-
http://protectedresource-2.example.com:1081/agentsample/*
Note –Make sure the hostname is typed in lowercase.
-
On the resulting page, click Save.
 To Create a Test Policy in the Access Manager User Realm
To Create a Test Policy in the Access Manager User Realm
Before You Begin
This procedure assumes you have just completed To Create a Test Referral Policy in the Access Manager Root Realm.
-
In the Access Manager console, under the Access Control tab, click the users realm link.
-
Click the Policies tab.
-
Under Policies, click New Policy.
-
In the Name field, enter URL Policy for ApplicationServer-2.
-
Under Rules, click New.
-
On the resulting page, make sure the default URL Policy Agent (with resource name) is selected and click Next.
-
On the resulting page, provide the following information and click Finish.
- Name:
-
agentsample
- Parent Resource Name:
-
From the list, select http://protectedresource-2.example.com:1081/agentsample/*
- Resource Name:
-
The value of this property is populated when you select the Parent Resource Name. It should read http://protectedresource-2.example.com:1081/agentsample/*.
- GET
-
Mark this check box and verify that Allow is selected.
- POST
-
Mark this check box and verify that Allow is selected.
The rule agentsample is now added to the list of Rules.
-
Under Subjects, click New.
-
On the resulting page, select Access Manager Identity Subject and click Next.
-
On the resulting page, provide the following information and click Search.
- Name:
-
agentsampleGroup
- Filter:
-
Select Group.
Manager-Group and Employee-Group are displayed in the Available list.
-
Select Manager-Group and Employee-Group and click Add.
The groups are now displayed in the Selected list.
-
Click Finish.
-
Click OK.
The new policy subject is included in the list of Policies.
-
Log out of the Access Manager console.
 To Configure Properties for the J2EE Policy
Agent 2 Sample Application
To Configure Properties for the J2EE Policy
Agent 2 Sample Application
Modify AMAgent.properties.
-
Log in as a root user to the ProtectedResource–2 host machine.
-
Change to the config directory.
# cd /export/J2EEPA2/j2ee_agents/am_wl92_agent/agent_001/config
Tip –Backup AMAgent.properties before you modify it.
-
Modify these properties in AMAgent.properties as follows.
com.sun.identity.agents.config.notenforced.uri[0] = /agentsample/public/* com.sun.identity.agents.config.notenforced.uri[1] = /agentsample/images/* com.sun.identity.agents.config.notenforced.uri[2] = /agentsample/styles/* com.sun.identity.agents.config.notenforced.uri[3] = /agentsample/index.html com.sun.identity.agents.config.notenforced.uri[4] = /agentsample com.sun.identity.agents.config.access.denied.uri = /agentsample/authentication/accessdenied.html com.sun.identity.agents.config.login.form[0] = /agentsample/authentication/login.html com.sun.identity.agents.config.login.url[0] = http://LoadBalancer-3.example.com:7070/ amserver/UI/Login?realm=users com.sun.identity.agents.config.privileged.attribute. type[0] = group com.sun.identity.agents.config.privileged.attribute. tolowercase[group] = false
-
Set these remaining properties as follows.
Note –This is specific to this deployment example. For more information see The agentadmin -getUuid command fails for amadmin user on Access Manager 7 with various agents (6452713) in Sun Java System Access Manager Policy Agent 2.2 Release Notes.
-
Retrieve the Universal IDs.
They were saved in To Create Manager and Employee Groups Using Access Manager for J2EE Policy Agent Test.
-
Convert all uppercase to lowercase and append a back slash (\) in front of each equal sign (=).
-
Set the properties.
com.sun.identity.agents.config.privileged.attribute. mapping[id\=manager-group,ou\=group,o\=users,ou\=services, dc\=example,dc\=com] = am_manager_role com.sun.identity.agents.config.privileged.attribute. mapping[id\=employee-group,ou\=group,o\=users,ou\=services, dc\=example,dc\=com] = am_employee_role
-
-
Save AMAgent.properties and close the file.
-
Restart the Application Server 2 administration server and managed server.
-
Change to the bin directory.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2/bin
-
Stop the managed server.
# ./stopManagedWebLogic.sh ApplicationsServer-2 t3://localhost:7001
-
Stop the administration server.
# ./stopWebLogic.sh
-
Start the administration server.
# ./startWebLogic.sh &
-
Start the managed server.
# ./startManagedWebLogic.sh ApplicationServer-2 t3://localhost:7001 &
-
-
Log out of the ProtectedResource–2 host machine.
 To Verify that J2EE Policy Agent 2 is Configured
Properly
To Verify that J2EE Policy Agent 2 is Configured
Properly
Use these steps to access the agent sample application and test policies against it.
-
Access http://ProtectedResource-2.example.com:1081/agentsample/index.html, the sample application URL, from a web browser.
The Sample Application welcome page is displayed.
-
Click the J2EE Declarative Security link.
-
On the resulting page, click Invoke the Protected Servlet.
You are redirected to the Access Manager login page.
-
Log in to the Access Manager console as testuser1.
- Username
-
testuser1
- Password
-
password
If you can successfully log in as testuser1 and the J2EE Policy Agent Sample Application page is displayed, the first part of the test has succeeded and authentication is working as expected.
-
Click the J2EE Declarative Security link again.
-
On the resulting page, click Invoke the Protected Servlet.
If the Success Invocation message is displayed, the second part of the test has succeeded as the sample policy for the manager role has been enforced as expected.
-
Click the J2EE Declarative Security link to return.
-
On the resulting page, click Invoke the Protected EJB via an Unprotected Servlet.
If the Failed Invocation message is displayed, the third part of the test has succeeded as the sample policy for the employee role has been enforced as expected.
-
Log out and close the browser.
-
In a new browser session, access http://ProtectedResource-2.example.com:1081/agentsample/index.html, the sample application URL, again.
The Sample Application welcome page is displayed.
-
Click the J2EE Declarative Security link.
-
On the resulting page, click Invoke the Protected EJB via an Unprotected Servlet.
You are redirected to the Access Manager login page.
Tip –If you are not redirected to the Access Manager login page for authentication, clear your browser's cache and cookies and try again.
-
Log in to the Access Manager console as testuser2
- Username
-
testuser2
- Password
-
password
The Failed Invocation message is displayed. This is a known issue.
-
Click the J2EE Declarative Security link.
-
On the resulting page, click Invoke the Protected EJB via an Unprotected.
The Successful Invocation message is displayed as the sample policy for the employee role has been enforced as expected.
-
Click the J2EE Declarative Security link to return.
-
On the resulting page, click Invoke the Protected Servlet.
If the Access to Requested Resource Denied message is displayed, this part of the test has succeeded as the sample policy for the manager role has been enforced as expected.
-
Log out and close the browser.
9.2.4 Configuring the J2EE Policy Agent 2 to Communicate Over SSL
Use the following list of procedures as a checklist to configure the policy agent to point to the secure port of the Access Manager Load Balancer 3.
-
To Import the CA Root Certificate into the Application Server 2 Keystore
-
To Configure the J2EE Policy Agent 2 to Access the Distributed Authentication User Interface
 To Configure the J2EE Policy Agent 2 for SSL
Communication
To Configure the J2EE Policy Agent 2 for SSL
Communication
-
Log in as a root user to the ProtectedResource–2 host machine.
-
Change to the config directory.
# cd /export/J2EEPA2/j2ee_agents/am_wl92_agent/agent_001/config
Tip –Backup AMAgent.properties before you modify it.
-
Modify these properties in AMAgent.properties as follows.
com.sun.identity.agents.config.login.url[0] = https://LoadBalancer-3.example.com:9443/amserver/UI/Login?realm=users com.sun.identity.agents.config.cdsso.cdcservlet.url[0] = https://LoadBalancer-3.example.com:9443/amserver/cdcservlet com.sun.identity.agents.config.cdsso.trusted.id.provider[0] = https://LoadBalancer-3.example.com:9443/amserver/cdcservlet com.iplanet.am.naming.url= https://LoadBalancer-3.example.com:9443/amserver/namingservice com.iplanet.am.server.protocol=https com.iplanet.am.server.port=9443
-
Save AMAgent.properties and close the file.
 To Import the CA Root Certificate into the
Application Server 2 Keystore
To Import the CA Root Certificate into the
Application Server 2 Keystore
The Certificate Authority (CA) root certificate enables the J2EE policy agent to trust the certificate from the Access Manager Load Balancer 3, and to establish trust with the certificate chain that is formed from the CA to the certificate. Import the same CA root certificate used in To Import a Certificate Authority Root Certificate on the Access Manager Load Balancer.
Before You Begin
This procedure assumes you have just completed To Configure the J2EE Policy Agent 2 for SSL Communication. In this example, the root certificate is a file named /export/software/ca.cer.
-
Change to the directory where the cacerts keystore is located.
# cd /usr/local/bea/jdk150_04/jre/lib/security
Tip –Backup cacerts before you modify it.
-
Import the root certificate.
# /usr/local/bea/jdk150_04/bin/keytool -import -trustcacerts -alias OpenSSLTestCA -file /export/software/ca.cer -keystore /usr/local/bea/jdk150_04/jre/lib/security/cacerts -storepass changeit Owner: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun, L=Santa Clara, ST=California, C=US Issuer: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun, L=Santa Clara, ST=California, C=US Serial number: 97dba0aa26db6386 Valid from: Tue Apr 18 07:55:19 PDT 2006 until: Tue Jan 13 06:55:19 PST 2009 Certificate fingerprints: MD5: 9F:57:ED:B2:F2:88:B6:E8:0F:1E:08:72:CF:70:32:06 SHA1: 31:26:46:15:C5:12:5D:29:46:2A:60:A1:E5:9E:28:64:36:80:E4:70 Trust this certificate? [no]: yes Certificate was added to keystore
-
Verify that the certificate was successfully added to the keystore.
# /usr/local/bea/jdk150_04/bin/keytool -list -keystore /usr/local/bea/jdk150_04/jre/lib/security/cacerts -storepass changeit | grep -i openssl openssltestca, Sept 19, 2007, trustedCertEntry,
-
Restart the Application Server 1 administration server and managed instance.
-
Change to the bin directory.
# cd /usr/local/bea/user_projects/domains/ProtectedResource-2/bin
-
Stop the managed instance.
# ./stopManagedWebLogic.sh ApplicationsServer-2 t3://localhost:7001
-
Stop the administration server.
# ./stopWebLogic.sh
-
Start the administration server.
# ./startWebLogic.sh &
-
Start the managed instance.
# ./startManagedWebLogic.sh ApplicationServer-2 t3://localhost:7001 &
-
-
Log out of the ProtectedResource–2 host machine.
 To Verify that J2EE Policy Agent 2 is Configured
Properly
To Verify that J2EE Policy Agent 2 is Configured
Properly
Use these steps to access the agent sample application and test policies against it.
-
Access http://ProtectedResource-2.example.com:1081/agentsample/index.html, the sample application URL, from a web browser.
The Sample Application welcome page is displayed.
-
Click the J2EE Declarative Security link.
-
On the resulting page, click Invoke the Protected Servlet.
You are redirected to the Access Manager login page.
-
Log in to the Access Manager console as testuser1.
- Username
-
testuser1
- Password
-
password
If you can successfully log in as testuser1 and the J2EE Policy Agent Sample Application page is displayed, this first part of the test has succeeded and authentication is working as expected.
-
Click the J2EE Declarative Security link to return.
-
On the resulting page, click Invoke the Protected Servlet.
If the Success Invocation message is displayed, this second part of the test has succeeded as the sample policy for the manager role has been enforced as expected.
-
Click the J2EE Declarative Security link to go back.
-
On the resulting page, click Invoke the Protected EJB via an Unprotected Servlet.
If the Failed Invocation message is displayed, this third part of the test succeeded as the sample policy for the employee role has been enforced as expected.
-
Log out and close the browser.
-
In a new browser session, access http://ProtectedResource-2.example.com:1081/agentsample/index.html, the sample application URL.
The Sample Application welcome page is displayed.
-
Click the J2EE Declarative Security link.
-
On the resulting page, click Invoke the Protected EJB via an Unprotected Servlet.
You are redirected to the Access Manager login page.
Tip –If you are not redirected to the Access Manager login page for authentication, clear your browser's cache and cookies and try again.
-
Log in to the Access Manager console as testuser2.
- Username
-
testuser2
- Password
-
password
The Failed Invocation message is displayed. This is a known issue.
-
Click the J2EE Declarative Security link.
-
On the resulting page, click Invoke the Protected EJB via an Unprotected Servlet.
The Successful Invocation message is displayed. The sample policy for the employee role has been enforced as expected.
-
Click the J2EE Declarative Security link to return.
-
On the resulting page, click Invoke the Protected Servlet.
If the Access to Requested Resource Denied message is displayed, this part of the test is successful as the sample policy for the manager role has been enforced as expected.
-
Log out and close the browser.
 To Configure the J2EE Policy Agent 2 to Access
the Distributed Authentication User Interface
To Configure the J2EE Policy Agent 2 to Access
the Distributed Authentication User Interface
Modify AMAgent.properties.
-
Log in as a root user to the ProtectedResource–2 host machine.
-
Change to the config directory.
# cd /export/J2EEPA2/j2ee_agents/am_wl92_agent/agent_001/config
Tip –Backup AMAgent.properties before you modify it.
-
Set the following property.
com.sun.identity.agents.config.login.url[0] = https://LoadBalancer-4.example.com:9443/distAuth/UI/Login?realm=users
-
Save AMAgent.properties and close the file.
-
Restart the Application Server 1 managed server.
-
Log out of the ProtectedResource–2 host machine.
-
Verify that the agent is configured properly.
-
Access http://ProtectedResource-2.example.com:1081/agentsample/index.html, the sample application URL, form a web browser.
The Sample Application Welcome page is displayed.
-
Click the J2EE Declarative Security link.
-
On the resulting page, click Invoke the Protected Servlet.
You are redirected to the Distributed Authentication User Interface at https://loadbalancer-4.example.com:9443/distAuth/UI/Login.
-
(Optional) Double-click the gold lock in the lower left corner of the browser.
In the Properties page, you see the certificate for LoadBalancer–4.example.com.
-
Log in to the Access Manager console as testuser1.
- Username
-
testuser1
- Password
-
password
If you can successfully log in as testuser1 and the J2EE Policy Agent Sample Application page is displayed, user authentication worked through the Distributed Authentication User Interface.
-
Log out of the console.
-
- © 2010, Oracle Corporation and/or its affiliates
