Subsequent Authentications
After the client has received the initial authentication, each individual authentication follows the pattern shown in Figure 1-2:
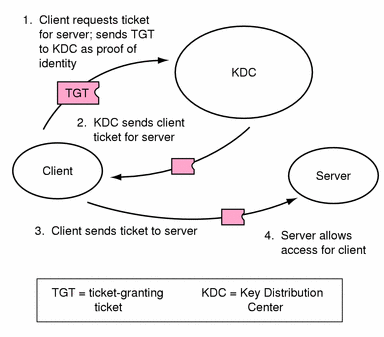
Figure 1-2 Obtaining Access to a Service
-
The client requests a ticket for a particular service (say, to rlogin into another machine) from the KDC, sending the KDC its ticket-granting ticket as proof of identity.
-
The KDC sends the ticket for the specific service to the client.
For example, suppose the user joe uses rlogin on the server boston. Since he is already authenticated (that is, he already has a ticket-granting ticket), he automatically and transparently obtains a ticket as part of the rlogin command. This ticket allows him to rlogin into boston as often as he wants until it expires. If joe wants to rlogin into the machine denver, he obtains another ticket, as in Step 1.
-
The client sends the ticket to the server.
-
The server allows the client access.
Looking at these steps, you might have noticed that the server doesn't appear to ever communicate with the KDC. It does, though; it registers itself with the KDC, just as the first client does. For simplicity's sake we have left that part out.
- © 2010, Oracle Corporation and/or its affiliates
