Initial Authentication: the Ticket-Granting Ticket
Kerberos authentication has two phases: an initial authentication that allows for all subsequent authentications, and the subsequent authentications themselves.
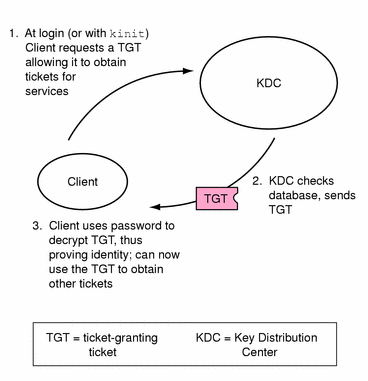
Figure 1-1 shows how the initial authentication takes place:
Figure 1-1 Initial Authentication for SEAM Session
-
A client (a user, or a service such as NFS) begins a SEAM session by requesting a ticket-granting ticket (TGT) from the Key Distribution Center. This is often done automatically at login.
A ticket-granting ticket is needed to obtain other tickets for specific services. One analogy is to think of the ticket-granting ticket as similar to a passport. Like a passport, the ticket-granting ticket identifies you and allows you to obtain numerous "visas" -- where the "visas" (tickets) are not for foreign countries but for remote machines or network services. Like passports and visas, the ticket-granting ticket and the other various tickets have limited lifetimes. The difference is that "Kerberized" commands notice that you have a passport and obtain the visas for you -- you don't have to perform the transactions yourself.
-
The KDC creates a ticket-granting ticket and sends it back, in encrypted form, to the client. The client decrypts the ticket-granting ticket using the client's password.
-
Now in possession of a valid ticket-granting ticket, the client can request tickets for all sorts of network operations, such as rlogin or telnet, for as long as the ticket-granting ticket lasts. This is usually a few hours. Each time the client performs a unique network operation, it requests a ticket for that operation from the KDC.
- © 2010, Oracle Corporation and/or its affiliates
