Configuring Security
The Worklist Manager and task assignment window both require a connection to an LDAP directory for user information and authentication. You can optionally configure SSL on the LDAP server to encrypt information.
Configuring the LDAP Server
If you are already using an LDAP server, you can use your existing directory structure. The primary requirement for the Worklist Manager is a mechanism that clearly defines a user hierarchy so managers and supervisors can view the tasks of their subordinates and users can escalate tasks to their supervisors.
OpenLDAP
The Worklist Manager can adapt to your existing OpenLDAP directory structure. You may need to assign each user an attribute that defines their reporting structure, if this has not been done already. You can use the default attribute, Manager, or you can create a new manager attribute. Each user should have an entry similar to Manager: cn=GSmythe, as shown in the sample directory structure in Figure 2.
Figure 2 Sample OpenLDAP Directory Structure
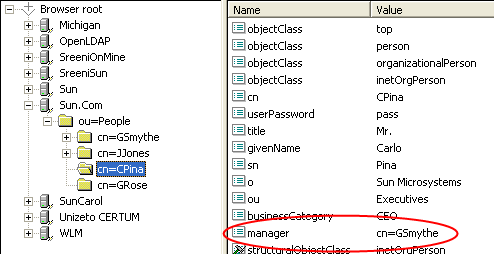
Worklist Manager login credentials for each user are defined by the value of the Naming Attribute used in the distinguished name for each user (typically the cn attribute) and the value of the userpassword attribute. For OpenLDAP, Sun BPM uses an anonymous bind to access the directory server.
You can create custom groups and roles to which Worklist Manager users belong, but this is not required. For information about configuring the Worklist Manager for OpenLDAP, see Configuring an OpenLDAP Connection.
Sun Java System Directory Server
The Worklist Manager can adapt to your existing Sun Java System Directory Server structure. You need to define the reporting structure if this has not been done already. There are a variety of ways to define the reporting structure. Sun provides a default attribute, manager, that you can use to define the upward reporting structure, but you must also use an attribute that defines subordinates. You can also create custom attributes that indicate a user’s managers and subordinates, or define hierarchies in the entrydn attribute of the user. For example, if user “gsmythe” reports to “grose” who in turn reports to “cpina”, the entrydn attribute for “gsmythe” would be similar to:
uid=gsmythe,uid=grose,uid=cpina,ou=people,dc=sun,dc=com
Using the above entrydn, the directory structure would look similar to Figure 3.
Figure 3 Sample Sun Java System Directory Server Structure
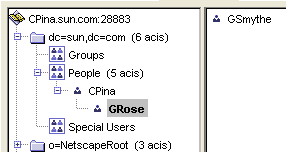
You can create custom groups and roles to which Worklist Manager users belong, but this is not required.
Note –
To enable task escalation and re-assignment on the Worklist Manager, you need to use the manager attribute to define a user’s supervisor and you need to define the reporting structure in each user’s entrydn attribute as described above. In the manager attribute, be sure to enter the full entrydn value for the supervisor.
When you define the LDAP directory structure, note the Naming Attribute used in the distinguished name for each user. This is typically the uid attribute or the cn attribute. This value is specified in the Worklist Manager External System properties in the Environment. Worklist Manager login credentials for each user are defined by the value of the Naming Attribute and the value of the userpassword attribute. You need to create an administrator user that the Worklist Manager will use as the security principal.
For more information about configuring the Worklist Manager for the Sun Java System Directory Server, see Configuring a Sun Java System Directory Server Connection.
Microsoft Active Directory
The Worklist Manager can adapt to your existing Active Directory structure. You need to define the reporting structure if this has not been done already. Active Directory provides two default attributes, manager and directReports, that define the reporting hierarchy. You can also create custom attributes that indicate a user’s supervisors and subordinates. You can create groups and roles to which Worklist Manager users belong, but this is not required.
In Active Directory, a user’s login ID is defined by the sAMAccountName attribute. This attribute is specified in the Worklist Manager External System properties in the Environment. Worklist Manager login credentials for each user are defined by the value of the sAMAccountName attribute and the value of the userPassword attribute. You need to create an administrator user that the Worklist Manager will use as the security principal.
For more information about configuring the Worklist Manager for Microsoft Active Directory, see Configuring a Microsoft Active Directory Connection.
Configuring Secure Sockets Layer
By default, communications between the Repository and the LDAP server are unencrypted. You can configure the LDAP server and Worklist Manager to use Secure Sockets Layer (SSL).
 To encrypt communications between the Repository and
the LDAP server
To encrypt communications between the Repository and
the LDAP server
-
Configure SSL on the LDAP server.
Ensure that the LDAP server is configured to use the Secure Sockets Layer (SSL). For detailed instructions, see the documentation provided with the LDAP server.
-
Export the LDAP server certificate to a file.
-
Import the LDAP server certificate to the Repository’s list of trusted certificates. The following steps use the keytool program. This program is included with the Repository (as well as the Java SDK).
-
From a command prompt, navigate to <JavaCAPS_home>\repository\1.5.0_10\jre\bin.
-
Run the following command:
keytool -import -trustcacerts -alias alias -file certificate_filename -keystore cacerts_filename
For the -alias option, assign any value.
For the -file option, specify the fully qualified name of the LDAP server certificate. For example:
C:\ldap\mycertificate.cer
For the -keystore option, specify the fully qualified name of the cacerts file, located in <Java CAPS_home>\repository\1.5.0_10\jre\lib\security. For example:
C:\JavaCAPS51\repository\1.5.0_10\jre\lib\security\cacerts
-
When prompted, enter the keystore password. The default password is changeit.
-
When prompted whether to trust this certificate, enter yes.
The following message appears:
Certificate was added to keystore
-
In the Realm element of the server.xml file, modify the URL of the LDAP server as follows:
LDAP and UNIX Java CAPS Environments
If the Logical Host of the Java CAPS environment is running on a UNIX system, you must configure the LDAP Provider URL to connect to the LDAP server. The following is common for a Java CAPS environment.
-
Logical Host running on UNIX
-
Java CAPS Repository running on Windows
-
LDAP running on UNIX
In this environment, the LDAP provider URL in the Worklist Manager properties must be set to an exact URL.
 To set an LDAP provider URL
To set an LDAP provider URL
-
From the Environment Explorer tab, right-click the Worklist Manager External System, and then click Properties.
-
In the Configuration list, expand WLMConnector External System Configuration, and then, depending on the LDAP server you are using, click Open Ldap Parameters or Sun Java System Directory Server/ADS.
-
In the LDAP Provider URL property, enter the exact URL to the LDAP server.
The URL for the LDAP server is ldap://host:port
where hostis the name of the machine on which the LDAP server resides, and port is the port number on which the LDAP directory is listening. You can access the port number through the LDAP directory browser or administration tool you are using.
-
Click OK to save the changes.
- © 2010, Oracle Corporation and/or its affiliates
