Implementing a User Activity
This section provides an overview of how to configure the user activity and other components required to implement a user activity. Each step below is described in detail in the following sections. Perform the following steps to create a BP containing a user activity.
Creating the Worklist Manager Database
The Worklist Manager database stores task assignment data, such as the type, priority, and status of the task, as well as who a task is currently assigned to. Before beginning this task, be sure you have database instance created where you can install the Worklist Manager tables.
 To create the Worklist Manager database
To create the Worklist Manager database
-
From the Project Explorer, expand BPM, and then expand WorkListViewer.
-
On the dialog box, click Check Out.
-
Right-click Database Scripts, and then click Properties.
The Database Script Properties dialog box appears.
Figure 1 Worklist Manager Database Properties
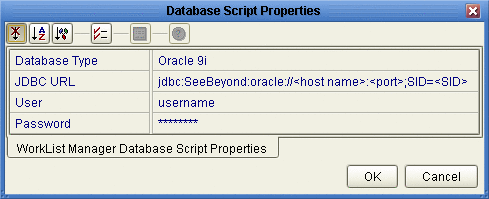
-
Configure the database properties to connect to your database, and then click OK.
See Figure 1 for more information about the values for these properties.
Note –The user whose login information you enter must have DBA privileges to create the new Worklist Manager user.
-
In the Project Explorer, right-click the install script file appropriate for your database, and then click Run.
Configuring Security
The Worklist Manager and task assignment window both require a connection to an LDAP directory for user information and authentication. You can optionally configure SSL on the LDAP server to encrypt information.
Configuring the LDAP Server
If you are already using an LDAP server, you can use your existing directory structure. The primary requirement for the Worklist Manager is a mechanism that clearly defines a user hierarchy so managers and supervisors can view the tasks of their subordinates and users can escalate tasks to their supervisors.
OpenLDAP
The Worklist Manager can adapt to your existing OpenLDAP directory structure. You may need to assign each user an attribute that defines their reporting structure, if this has not been done already. You can use the default attribute, Manager, or you can create a new manager attribute. Each user should have an entry similar to Manager: cn=GSmythe, as shown in the sample directory structure in Figure 2.
Figure 2 Sample OpenLDAP Directory Structure
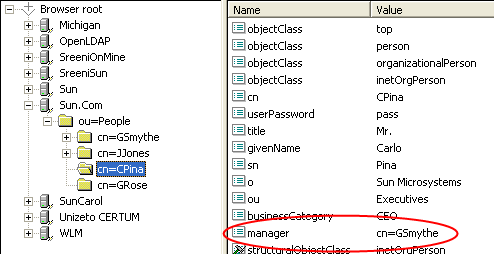
Worklist Manager login credentials for each user are defined by the value of the Naming Attribute used in the distinguished name for each user (typically the cn attribute) and the value of the userpassword attribute. For OpenLDAP, Sun BPM uses an anonymous bind to access the directory server.
You can create custom groups and roles to which Worklist Manager users belong, but this is not required. For information about configuring the Worklist Manager for OpenLDAP, see Configuring an OpenLDAP Connection.
Sun Java System Directory Server
The Worklist Manager can adapt to your existing Sun Java System Directory Server structure. You need to define the reporting structure if this has not been done already. There are a variety of ways to define the reporting structure. Sun provides a default attribute, manager, that you can use to define the upward reporting structure, but you must also use an attribute that defines subordinates. You can also create custom attributes that indicate a user’s managers and subordinates, or define hierarchies in the entrydn attribute of the user. For example, if user “gsmythe” reports to “grose” who in turn reports to “cpina”, the entrydn attribute for “gsmythe” would be similar to:
uid=gsmythe,uid=grose,uid=cpina,ou=people,dc=sun,dc=com
Using the above entrydn, the directory structure would look similar to Figure 3.
Figure 3 Sample Sun Java System Directory Server Structure
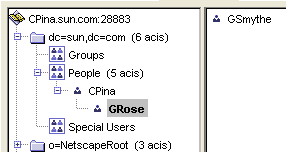
You can create custom groups and roles to which Worklist Manager users belong, but this is not required.
Note –
To enable task escalation and re-assignment on the Worklist Manager, you need to use the manager attribute to define a user’s supervisor and you need to define the reporting structure in each user’s entrydn attribute as described above. In the manager attribute, be sure to enter the full entrydn value for the supervisor.
When you define the LDAP directory structure, note the Naming Attribute used in the distinguished name for each user. This is typically the uid attribute or the cn attribute. This value is specified in the Worklist Manager External System properties in the Environment. Worklist Manager login credentials for each user are defined by the value of the Naming Attribute and the value of the userpassword attribute. You need to create an administrator user that the Worklist Manager will use as the security principal.
For more information about configuring the Worklist Manager for the Sun Java System Directory Server, see Configuring a Sun Java System Directory Server Connection.
Microsoft Active Directory
The Worklist Manager can adapt to your existing Active Directory structure. You need to define the reporting structure if this has not been done already. Active Directory provides two default attributes, manager and directReports, that define the reporting hierarchy. You can also create custom attributes that indicate a user’s supervisors and subordinates. You can create groups and roles to which Worklist Manager users belong, but this is not required.
In Active Directory, a user’s login ID is defined by the sAMAccountName attribute. This attribute is specified in the Worklist Manager External System properties in the Environment. Worklist Manager login credentials for each user are defined by the value of the sAMAccountName attribute and the value of the userPassword attribute. You need to create an administrator user that the Worklist Manager will use as the security principal.
For more information about configuring the Worklist Manager for Microsoft Active Directory, see Configuring a Microsoft Active Directory Connection.
Configuring Secure Sockets Layer
By default, communications between the Repository and the LDAP server are unencrypted. You can configure the LDAP server and Worklist Manager to use Secure Sockets Layer (SSL).
 To encrypt communications between the Repository and
the LDAP server
To encrypt communications between the Repository and
the LDAP server
-
Configure SSL on the LDAP server.
Ensure that the LDAP server is configured to use the Secure Sockets Layer (SSL). For detailed instructions, see the documentation provided with the LDAP server.
-
Export the LDAP server certificate to a file.
-
Import the LDAP server certificate to the Repository’s list of trusted certificates. The following steps use the keytool program. This program is included with the Repository (as well as the Java SDK).
-
From a command prompt, navigate to <JavaCAPS_home>\repository\1.5.0_10\jre\bin.
-
Run the following command:
keytool -import -trustcacerts -alias alias -file certificate_filename -keystore cacerts_filename
For the -alias option, assign any value.
For the -file option, specify the fully qualified name of the LDAP server certificate. For example:
C:\ldap\mycertificate.cer
For the -keystore option, specify the fully qualified name of the cacerts file, located in <Java CAPS_home>\repository\1.5.0_10\jre\lib\security. For example:
C:\JavaCAPS51\repository\1.5.0_10\jre\lib\security\cacerts
-
When prompted, enter the keystore password. The default password is changeit.
-
When prompted whether to trust this certificate, enter yes.
The following message appears:
Certificate was added to keystore
-
In the Realm element of the server.xml file, modify the URL of the LDAP server as follows:
LDAP and UNIX Java CAPS Environments
If the Logical Host of the Java CAPS environment is running on a UNIX system, you must configure the LDAP Provider URL to connect to the LDAP server. The following is common for a Java CAPS environment.
-
Logical Host running on UNIX
-
Java CAPS Repository running on Windows
-
LDAP running on UNIX
In this environment, the LDAP provider URL in the Worklist Manager properties must be set to an exact URL.
 To set an LDAP provider URL
To set an LDAP provider URL
-
From the Environment Explorer tab, right-click the Worklist Manager External System, and then click Properties.
-
In the Configuration list, expand WLMConnector External System Configuration, and then, depending on the LDAP server you are using, click Open Ldap Parameters or Sun Java System Directory Server/ADS.
-
In the LDAP Provider URL property, enter the exact URL to the LDAP server.
The URL for the LDAP server is ldap://host:port
where hostis the name of the machine on which the LDAP server resides, and port is the port number on which the LDAP directory is listening. You can access the port number through the LDAP directory browser or administration tool you are using.
-
Click OK to save the changes.
Creating a Web Service Definition
Web Service Definitions, embodied as Web Service Definition Language (WSDL) files, can be used to invoke and operate web services on the Internet and to access and invoke remote applications and databases. WSDL files are used when you are building a web service, and expose the BP as a web service.
Creating the BPs
Once you have created the Worklist Manager database and have the LDAP directory structure in place, you can create the main BP that contains the user activity and the sub-process that defines the user activity logic.
Creating the Sub-process
The sub-process defines the flow of data through the user activity, and defines the access point for users to enter the required information.
 To create the sub-process
To create the sub-process
-
Create the Sun VPD page flows that define the user activity.
-
Create a BP, and add the modeling elements including the Sun VPD page flows.
-
Link the modeling elements together.
-
Create the business rules for the links to define the mapping of data..
-
When you are done configuring the modeling elements, click Save on the Enterprise Designer toolbar.
Creating a Partner
When creating a BP that will be used as a sub-process, you need to create a partner to associate with the receive and reply activities.
 To create a new partner
To create a new partner
-
In the Project Explorer, right-click the sub-process, and then click Properties.
-
On the BP Properties window, click the Partners tab.
-
Click New, and enter a name for the partner.
-
Click OK.
Associating the Partner with Activities
Once you create a partner for the sub-process, you need to associate it with the implement or receive activity and the reply activity of the sub-process. This allows you to connect the components in the Connectivity Map.
 To associate the partner with activities
To associate the partner with activities
-
In the BP, select the receive or implement activity.
-
On the BP Designer toolbar, click Property Sheet.
-
In the Partner property, select the partner you created above.
-
Repeat for the reply activity.
Creating the Main BP
The main BP includes the user activity, and invokes the sub-process created in the previous step.
 To create the main BP
To create the main BP
-
Create a BP, and add the modeling elements including a user activity.
-
Link the modeling elements together.
-
In the Project Explorer, expand the sub-process, and then drag the operation of the sub-process onto the user activity in the BP. This node is named Operation by default, but you can customize the name in the WSD object.
-
Create the business rules for the links to define the mapping of data.
-
Define task assignment for the user activity, as described in Defining Task Assignment.
-
When you are done configuring the modeling elements, click Save on the Enterprise Designer toolbar.
Configuring User Activities Inside While Loops
When creating a BP that includes a user activity inside a while loop, you must take a few extra steps. The following procedure provides the steps for configuring a user activity inside a while loop.
 To configure a user activity inside a while loop
To configure a user activity inside a while loop
-
Create and configure a user activity as normal.
-
Add a business rule to the link leaving the user activity.
-
Open the Business Rule Designer and expand the WLVTask.Input node.
-
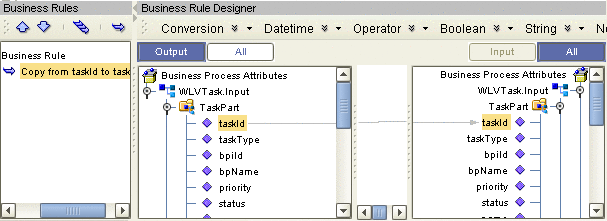
Copy a BP attribute from the Output panel to the All panel, as shown in Figure 4.
This creates an output container.
Figure 4 Copy BP Attribute
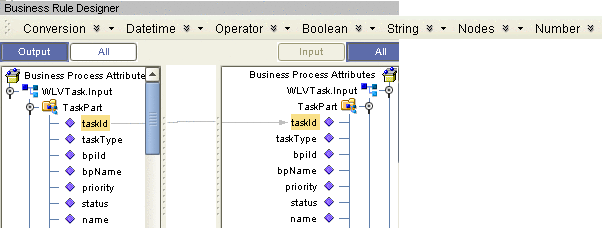
-
Open the Business Rules panel and click Show Single Mapping, as shown in Figure 5.
Figure 5 Business Rules Editor
-
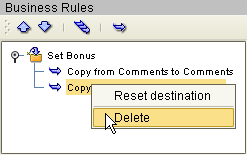
Right-click the Copy rule and click Reset Destination, as shown in Figure 6.
Figure 6 Reset Destination
-
On the Enterprise Designer toolbar, click Save.
Defining Task Assignment
After the BPs are created and configured, you need to connect to the LDAP server and configure the user activity. To configure a user activity, you create expressions that define which users are assigned to a task under specific conditions. You can optionally define automatic task escalation and email notifications for user activities. The task assignment panel also provides a Sun VPD page mapper so you can expose values generated by the user activity to the Sun VPD page flow.
Note –
One default expression is defined in the expression list, which cannot be deleted. This expression is used when no conditions defined for any other expression evaluate to true. At a minimum, you must configure the default expression by assigning a user to the expression; otherwise, BP validation will find a fatal error and you will be unable to deploy.
Creating a Task Assignment Expression
The flow of a specific task is defined by an expression. You can define multiple expressions for each user activity, each defining the conditions under which a task is assigned, the users to whom it is assigned, and what happens once the task is assigned.
 To create a task assignment expression
To create a task assignment expression
-
In the main BP, right-click the user activity to which you want to assign LDAP users, and then click Edit Task Assignment Panel.
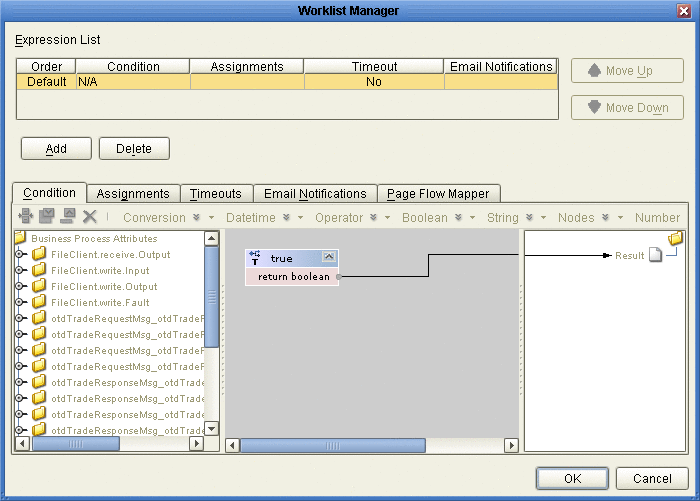
The Worklist Manager window appears, as shown in Figure 7.
Figure 7 Worklist Manager Window: Expression List
-
In the upper section of the window, click Add.
A new expression appears in the expressions list.
-
If necessary, use the Move Up and Move Down buttons to place the expression in the correct order.
-
Configure the expression as described in the following sections.
Defining Task Assignment Conditions
Conditions define how an activity is evaluated for user completion. The Conditions tab of the Worklist Manager window includes a Method Palette, similar to that of the Business Rule Designer. This step is required for all but the default expression.
 To define task assignment conditions
To define task assignment conditions
-
On the Worklist Manager window, click the Condition tab.
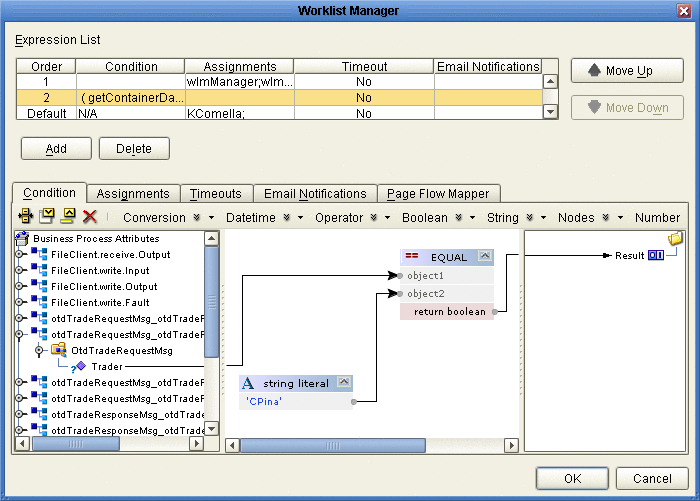
The Condition page appears, as shown in Figure 8.
-
Define the conditions under which a task will be assigned.
Figure 8 illustrates an example of using methods on the Condition page.
Figure 8 Worklist Manager Window: Condition Tab
-
Once the conditions are defined, continue to Assigning Users to the Activity.
Assigning Users to the Activity
In this step, you can create either static or dynamic assignments for the user activity. With static assignments, you specify the users to whom tasks will be assigned when the conditions you defined on the Condition page have been met. To do this, you must connect to a running LDAP server. With dynamic assignments, you specify a field in the incoming data that contains the name of the user to whom that task is assigned. You do not need to connect to the LDAP server to create this assignment. This step is required for all expressions. If a user activity includes an expression with no users assigned, the BP will fail validation.
 To assign users to an activity
To assign users to an activity
-
On the Worklist Manager window, click the Assignments tab.
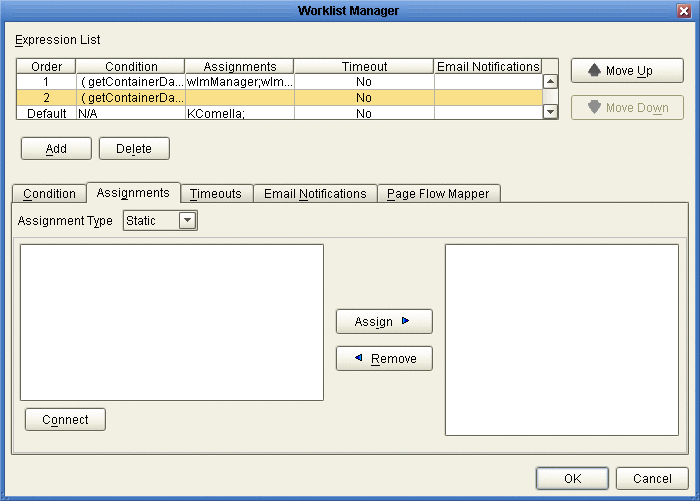
The Assignments page appears, as shown in Figure 9.
Figure 9 Worklist Manager Window: Static Assignments
-
To create static assignments, do the following:
-
On the Assignments page, make sure the Assignment Type is Static, and then click Connect.
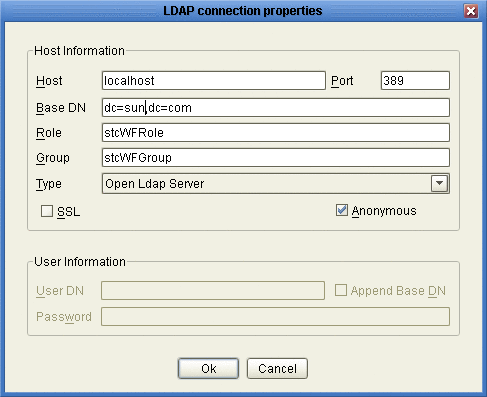
The LDAP connection properties dialog box appears.
Figure 10 LDAP connection properties Dialog Box
-
Enter the values in Figure 10, and then click OK.
The left panel of the Assignments page is populated with the roles, groups, and users defined in your LDAP directory.
-
From the list in the left panel , select the roles, groups, or users you want to include for this task assignment, and then click Assign.
-
To create dynamic assignments, do the following:
-
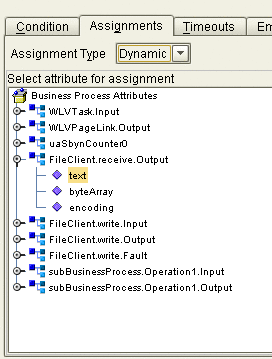
In the Assignment Type field, select Dynamic.
The Assignments page changes to display attributes, as shown in Figure 11.
Figure 11 Worklist Manager Window: Dynamic Assignments
-
In the attributes list, expand the list and select the field that will contain the name of the user to whom a task will be assigned.
-
-
Continue to Defining Task Escalation, or click OK if you are done defining the expression.
Note –Modify the properties to suit your LDAP implementation.
Description
The name of the computer on which the LDAP server resides.
The port number on which the LDAP server listens for requests.
The root Distinguished Name of the users directory; for example, dc=sun,dc=com.
The name of the role to which Worklist Manager users are assigned, if any. This field is not required.
The name of the group to which Worklist Manager users are assigned, if any. This field is not required.
The type of LDAP server you are using.
An indicator of whether to encrypt data shared between the LDAP server and the Repository. Select this option if SSL is configured.
An indicator of whether to create an anonymous bind to the LDAP server or to use specific login credentials. If you deselect this check box, the fields below become enabled.
The distinguished name of the user to use to connect to the directory server.
An indicator of whether to append the value of Base DN to the User DN for authentication.
The password associated with the User DN above.
Defining Task Escalation
The Worklist Manager provides the ability to automatically escalate tasks based on either a duration of time or a deadline. When escalation is based on duration, the task can be escalated repeatedly. When it is based on a deadline, the task is only escalated once.
For duration-based escalation, the timer starts when a task is added and when a user checks in, reassigns, or escalates a task. If the specified duration passes without the timer stopping, the task is escalated to all unique managers of the assignee. The timer stops when a task is checked out or completed and when the task has been escalated as high as it can go.
For deadline-based escalation, the timer starts when a task is inserted. The task is only escalated if the timer does not stop prior to the deadline. The timer stops when a task is checked out, completed, or manually escalated. The timer also stops when the deadline is reached and the task is escalated.
Defining task escalation is optional.
 To define task escalation
To define task escalation
-
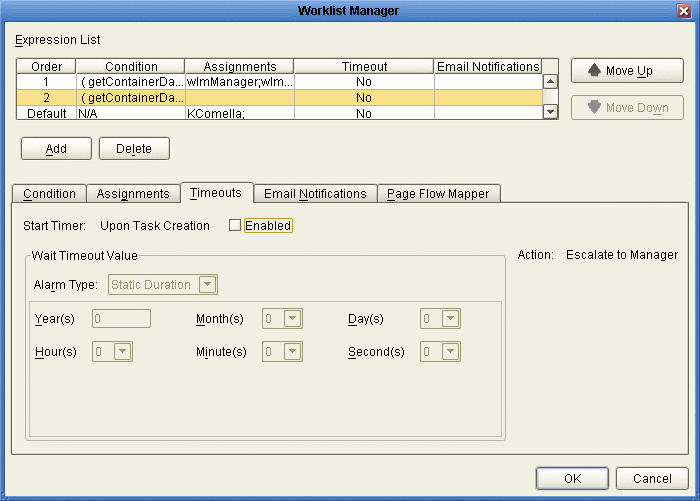
On the Worklist Manager window, click the Timeouts tab.
The Timeouts page appears, as shown in Figure 12.
Figure 12 Worklist Manager Window: Timeouts Tab
-
Click the Enabled checkbox.
-
To set a duration for escalation, do the following:
-
Enter the duration in the fields provided.
Figure 13. specifies that the task must be completed in just under one week before it is escalated.
Figure 13 Static Duration Fields
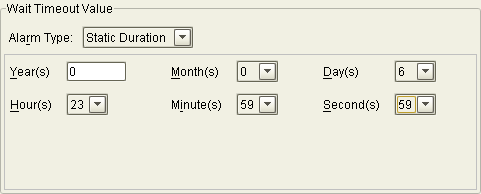
-
To set a deadline for the escalation, do the following:
-
Enter the deadline in the fields provided.
Figure 14 specifies that the task must be completed before midnight on the last day of February, 2007.
Figure 14 Static Deadline Fields
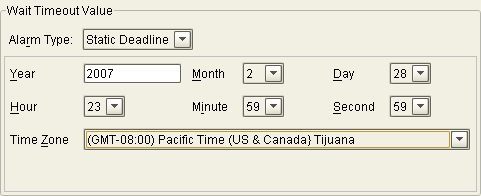
-
Continue to Exposing User Activity Values to Sun VPD Pages, or click OK if you are done defining the expression.
Exposing User Activity Values to Sun VPD Pages
Using the Page Flow Mapper, you can expose values generated by the user activity to the associated Sun VPD pages. For example, if you map the assignedTo field, pages can be built that display the name of the task assignee.
The mapper has a Method Palette from which you can select methods to manipulate the data in the mapping.
Exposing user activities to Sun VPD pages is optional.
 To expose user activity values to Sun VPD pages
To expose user activity values to Sun VPD pages
-
On the Worklist Manager window, click the Page Flow Mapper tab.
The Page Flow Mapper page appears, as shown in Figure 15.
Figure 15 Worklist Manager Window: Page Flow Mapper
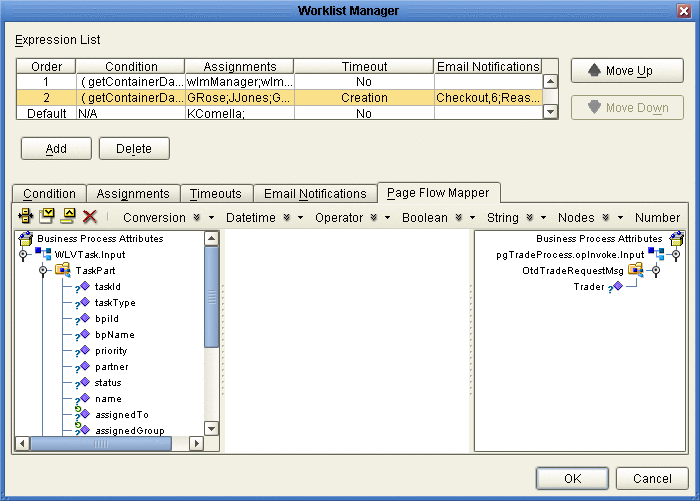
-
In the mapper, map any user activity fields in the left panel to nodes in the right panel.
-
Continue to Define Email Notifications for Tasks, or click OK if you are done defining the expression.
Define Email Notifications for Tasks
You can specify that certain users receive email notifications during different stages of task completion. For example, you might want to notify both the assignee and their managers when they are assigned a task. You can define email notifications for all types of task activities, including assignment, reassignment, escalation, check-ins, checkouts, and completion. This task is optional.
To define email notifications, complete the following tasks:
-
Make sure that the LDAP entry for each user assigned to user activity tasks includes an attribute that defines their email address.
-
Define email notification for tasks as described below (under Define Email Notifications for Tasks).
-
Configure the Worklist Manager External System in the Environment:
-
Define the email properties (described under Defining Email Notification Properties).
-
When configuring the LDAP connection properties, specify the name of the LDAP directory attribute that contains each user’s email address (this is described in Configuring an OpenLDAP Connection, Configuring a Sun Java System Directory Server Connection, or Configuring a Microsoft Active Directory Connection).
-
 To define email notification for tasks
To define email notification for tasks
-
On the Worklist Manager window, click the Email Notifications tab.
The Email Notifications page appears, as shown in Figure 15.
Figure 16 Worklist Manager Window: Email Notifications Tab
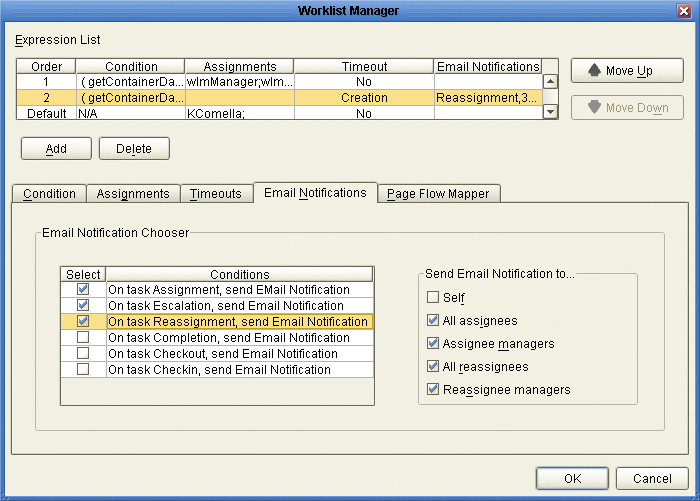
-
For each action for which you want to generate email notifications, do the following:
-
Click OK.
-
In the Environment Explorer, configure the Worklist Manager External System properties by doing the following:
-
Specify the email server connection properties, as described in Defining Email Notification Properties.
-
In the properties for the LDAP server, enter the name of the LDAP user attribute that contains the email address (for example, “mail”).
For more information about this property, see Figure 21, , or Figure 23 (depending on the type of LDAP directory you are using).
Configuring the WorkList Manager
When you create the Environment for a user activity BP, you need to create and configure a Worklist Manager External System. The properties you configure for the external system define the Worklist Manager database connectivity, LDAP server and directory information, and custom labels for flex attributes. Perform the following steps to configure the Worklist Manager.
In addition, you must perform one of the following tasks:
Creating the Worklist Manager External System
The Worklist Manager External System is created from the Environment Explorer.
 To create the Worklist Manager External System
To create the Worklist Manager External System
-
In the Environment Explorer, right-click the Environment for the user activity Project.
-
Point to New, and then click Worklist Manager.
-
Enter a name for the Worklist Manager External System, and then click OK.
The Properties window appears.
-
Configure the Worklist Manager, as described in the following sections.
Defining Configuration Properties
The configuration properties of the Worklist Manager define information about the Worklist Manager database and application.
 To define configuration properties
To define configuration properties
-
On the Worklist Manager Properties window, click WLMConnector External System Configuration (shown in Figure 17).
Figure 17 Worklist Manager External System Configuration
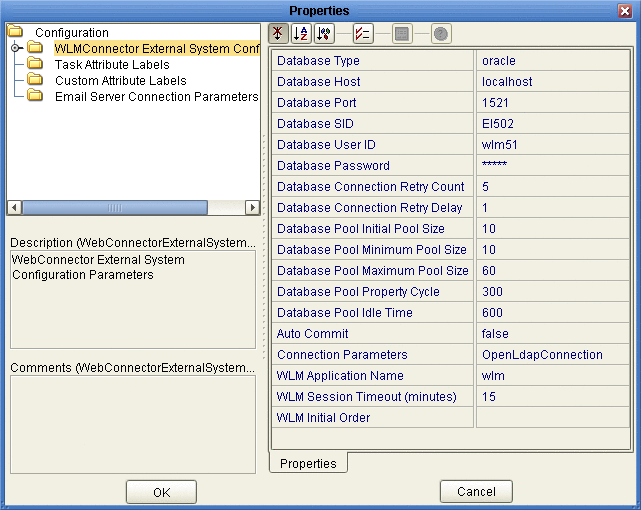
-
Enter values for the properties described in Figure 17.
-
Click OK.
Customizing Flex Attribute Labels
Flex attributes are customizable attributes that aid in task assignment. The attributes appear in the Business Rule Designer (as shown in Figure 18) as well as in columns of the Worklist Manager.
You can map values to these attributes in the Business Rule Designer so the values appear in the Worklist Manager. You can also label the attributes to make them easy to identify in the Worklist Manager.
Figure 18 Flex Attributes in the Business Rule Designer
 To customize flex attribute labels
To customize flex attribute labels
-
From the Environment Explorer, right-click the Worklist Manager External System.
-
Click Properties.
The Properties dialog box appears.
-
Click Custom Attribute Labels, as shown in Figure 19.
Figure 19 Flex Attributes
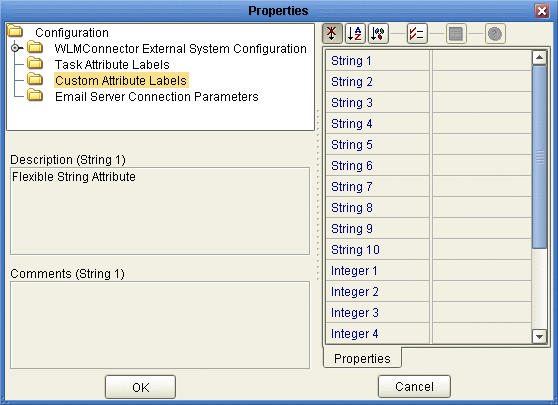
-
Define labels for as many attributes as necessary.
-
Click OK.
Defining Email Notification Properties
If you defined email notifications on the Worklist Manager window for a user activity (see Define Email Notifications for Tasks), you need to define the connection properties for the email server in the Worklist Manager External System properties. You also need to modify the LDAP properties for the directory server you are using by specifying the name of the attribute that contains the users’ email addresses.
 To define email notification properties
To define email notification properties
-
On the Worklist Manager Properties window, click Email Server Connection Parameters (shown in Figure 17).
Figure 20 Email Server Connection Properties
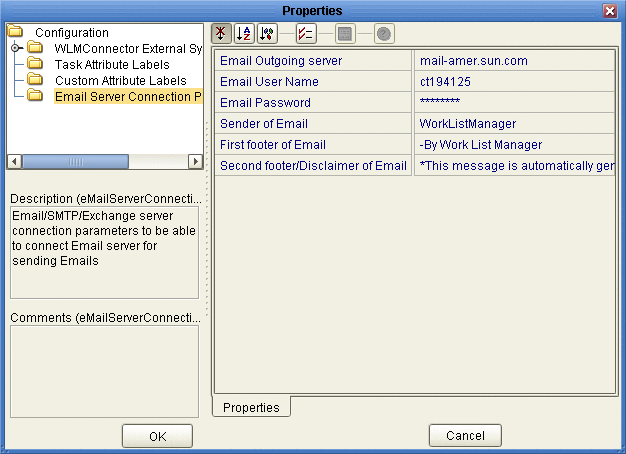
-
Enter values for the properties described in Figure 20.
-
Click OK.
Property
Description
The name of the email server on which the Worklist Manager email notifications are sent.
The login ID for the email account used by the Worklist Manager.
The password for the email account.
The name that should appear in the email as the sender. This property is used to create a URL, so it cannot contain any spaces.
A footer for the email notifications.
A second footer or disclaimer for the email notifications.
Configuring an OpenLDAP Connection
To use OpenLDAP with the Worklist Manager, you must specify certain information about the LDAP directory structure so the Worklist Manager knows where to find the user information defined in the directory. You can use your existing directory structure as long as there is a mechanism for defining a user reporting hierarchy.
The Worklist Manager uses an anonymous bind with OpenLDAP, so you do not need to specify credentials for the security principal.
 To configure an OpenLDAP connection
To configure an OpenLDAP connection
-
From the Environment Explorer tab, right-click the Worklist Manager External System, and then click Properties.
-
On the properties page that appears, verify that the Connection Parameters property is set to OpenLdapConnection.
-
Expand WLMConnector External System Configuration, and then click Open Ldap Parameters.
The Properties dialog box appears, as shown in Figure 21.
Figure 21 OpenLDAP Configuration Properties
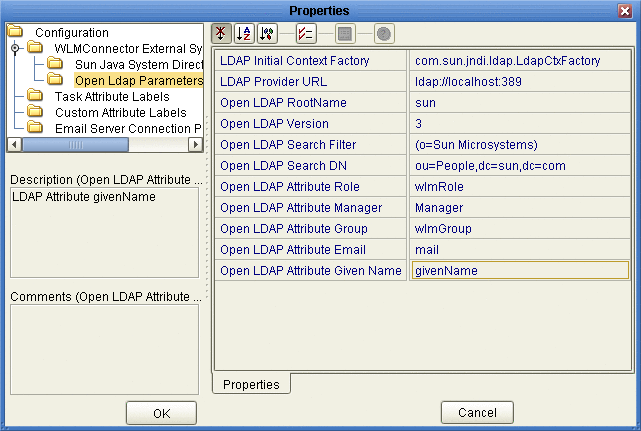
-
Enter values for the properties in Figure 21.
Note –Modify these values to suit your existing directory structure and attributes.
-
Click OK.
Configuring a Sun Java System Directory Server Connection
To use the Sun Java System Directory Server with the Worklist Manager, you must specify certain information about the LDAP directory structure so the Worklist Manager knows where to find the user information defined in the directory. You can use your existing directory structure as long as there is a mechanism for defining a user reporting hierarchy.
 To configure a Sun Java System Directory Server connection
To configure a Sun Java System Directory Server connection
-
From the Environment Explorer tab, right-click the Worklist Manager External System, and then click Properties.
-
On the properties page that appears, verify that the Connection Parameters property is set to Sun Java System Directory Server.
-
Expand WLMConnector External System Configuration, and then click Sun Java System Directory Server/ADS.
The Properties dialog box appears, as shown in Figure 21.
Figure 22 Sun Java System Directory Server Configuration Properties
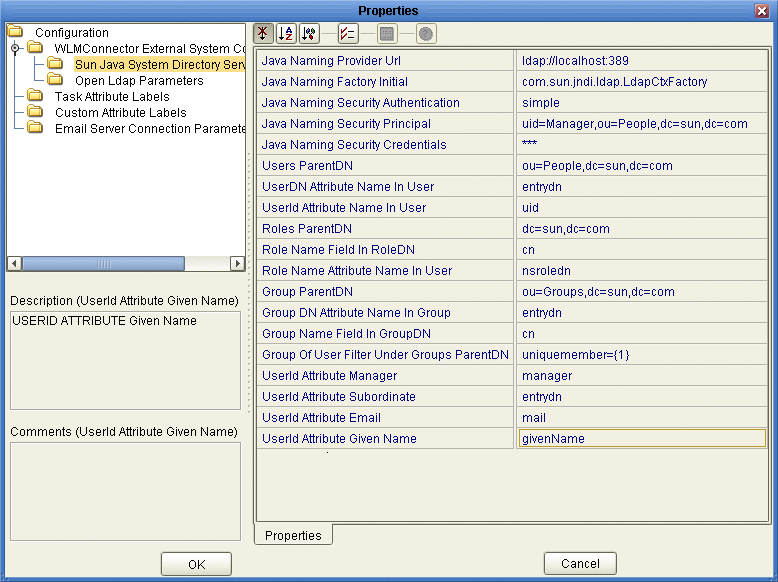
-
Enter the property values for the properties described in .
Note –Depending on how your LDAP directory is set up, not all of these fields are required. The default configuration is not necessarily illustrative of an actual implementation.
-
Click OK to close the Properties dialog box.
Configuring a Microsoft Active Directory Connection
To use Microsoft Active Directory with the Worklist Manager, you must specify certain information about the LDAP directory structure so the Worklist Manager knows where to find the user information defined in the directory. You can use your existing directory structure as long as there is a mechanism for defining a user reporting hierarchy.
 To configure a Microsoft Active Directory connection
To configure a Microsoft Active Directory connection
-
From the Environment Explorer tab, right-click the Worklist Manager External System, and then click Properties.
-
On the properties page that appears, verify that the Connection Parameters property is set to ActiveDirectoryConnection.
-
Expand WLMConnector External System Configuration, and then click Sun Java System Directory Server/ADS.
The Properties dialog box appears, as shown in Figure 21.
Figure 23 Microsoft Active Directory Configuration Properties

-
Enter the property values for the properties described in Figure 23.
Note –Depending on how your LDAP directory is set up, not all of these fields are required. The default configuration is not necessarily illustrative of an actual implementation.
-
Click OK to close the Properties dialog box.
- © 2010, Oracle Corporation and/or its affiliates
