Chapter 1 Introduction to Deployment Planning for Directory Server Enterprise Edition
This chapter provides an overview of Sun Java System Directory Server Enterprise Edition, and describes at a high level the deployment planning process.
This chapter covers the following topics:
About Directory Server Enterprise Edition
Directory Server Enterprise Edition provides secure, highly available, scalable directory services for storing and managing identity data. Directory Server Enterprise Edition is the foundation of an enterprise identity infrastructure. It enables mission-critical enterprise applications and large-scale extranet applications to access consistent and reliable identity data.
Directory Server Enterprise Edition provides a central repository for storing and managing identity profiles, access privileges, application and network resource information. Directory Server Enterprise Edition integrates smoothly into multi-platform environments. It also provides secure, on-demand synchronization of passwords, users, and groups with Microsoft Active Directory.
Prior to Directory Server Enterprise Edition, Sun provided these functions in four separate product offerings including Directory Server, Directory Proxy Server, Directory Server Resource Kit and Identity Synchronization for Windows. These and other products are now components of one comprehensive, integrated solution.
Quality of Service Requirements for a Robust Directory Service
The more users and applications in an enterprise, the more critical is the need for a robust directory service. Directory Server Enterprise Edition addresses the challenges faced by a rapidly changing and expanding enterprise by providing the following quality of service requirements:
-
Availability. A measure of how often the system's resources and services are accessible to end users, often expressed as the uptime of the system.
-
Scalability. The ability to add capacity, and users, to a deployed system over time. Scalability typically involves adding resources to the system but should not require changes to the deployment architecture.
-
Security. A complex combination of factors that describe the integrity of a system and its users. Security includes authentication and authorization of users, security of data, and secure access to the deployed system.
-
Interoperability. The ease with which the system operates in conjunction with other systems.
-
Serviceability. The ease with which a deployed system can be maintained. Maintenance tasks include monitoring the system, repairing problems that arise, and upgrading hardware and software components.
This chapter briefly describes how the components of Directory Server Enterprise Edition fill the quality of service requirements. The requirements are discussed in detail in the remainder of this guide.
Directory Server Enterprise Edition Components and Their Capabilities
Directory Server Enterprise Edition includes these separate components:
Each of these components addresses one or more of the quality of service requirements described previously. This section describes the components and illustrates how they fit together to provide a robust directory service.
Directory Server
Directory Server provides a scalable, high-performance data store for identity information. Directory Server supports the Lightweight Directory Access Protocol (LDAP) v3 and the Directory Service Markup Language (DSML) v2 natively for standards-based access. With LDAP and DSML over HTTP or SOAP (Simple Object Access Protocol), clients anywhere on a network are able to securely search and update directory data objects. Clients are also able to receive changes made by other applications and to authenticate users or applications even through firewalls.
Directory Server and Security
Directory Server provides several security features to achieve compliance with information security policies. These features ensure that only users with proper authorization have access to information.
-
Macro-level, dynamic access control instructions (ACIs). Provide a means for defining access down to the level of an LDAP attribute. Access control policies can be defined once, and then reused across the directory tree. Macro ACIs can be used to optimize the number of ACIs in the directory, thereby reducing the complexity of the security framework.
-
Role-based access. Enables you to provide access that is based on information in a user's entry. Roles are defined and administered like groups, but roles provide more efficient grouping mechanisms for applications. Roles can be used in ACIs to control access to data. They can also be used by Class of Service (CoS), a capability of Directory Server to create virtual attributes that can apply to many entries at the same time. These virtual attributes reduce storage requirements on entries. They also allow a single change to update an unlimited number of related entries.
-
Get Effective Rights control. Provides a means for determining what access a user has to a set of information. Administrators who maintain access policies for the directory service can tighten security by auditing the permissions of directory users and applications. This capability can also be used to build applications with adaptive interfaces that are based on the user's rights.
-
Encryption mechanisms. Protect data on the disk and during transfer through communications channels. Directory Server also supports fractional replication and data hiding based on access. These mechanisms can be used to comply with European Union and other international privacy regulations.
-
Multiple password policies. Can be defined on a per-user basis or targeted to certain groups. These policies help to ensure that users change passwords on a regular basis and that unauthorized access to an account is blocked.
Directory Server and Availability
Directory Server natively supports a variety of access protocols and offers a highly flexible, scalable replication environment that helps to ensure availability in distributed environments.
Directory Server replication prevents a single point of failure for applications that are using these protocols to access identity data. Directory Server supports a theoretically unlimited number of masters and read-only consumers in a replicated environment across both local and wide area networks. Special features of the replication protocol allow for optimizations when replicating data over high-latency networks. For more information, see Using Replication and Redundancy for High Availability.
On Solaris platforms, Directory Server supports clustering, a pre-packaged high availability hardware and software solution. For more information, see Using Clustering for High Availability.
Directory Server and Scalability
Directory Server provides for both vertical and horizontal growth without major deployment redesign. This level of scalability becomes increasingly critical as deployment grows.
Depending on the hardware, Directory Server can provide sustained search performance of 20,000 entries per second on a single machine and horizontal scalability to several thousand searches per second. For information about how to deploy Directory Server for read scalability, see Chapter 10, Designing a Scaled Deployment.
The requirement to store and update information constantly increases with the expansion of use across the organization. Update performance of Directory Server is close to relational database-write performance. For information about how to deploy Directory Server for write scalability, see Chapter 10, Designing a Scaled Deployment.
Directory Server provides linear CPU scalability to up to 28 CPUs for “read from cache” operations. It allows access to maximum memory capacity and delivers high performance that accommodates large directories on a single system for maximum hardware benefit.
Directory Server and Serviceability
Directory Server provides a comprehensive set of management tools for administering individual servers as well as the entire directory service.
A centralized, web-based administration console can be used to configure and manage multiple Directory Servers. The interface includes all the tools required for effective, day-to-day server administration and service from configuration to monitoring. In addition, the dsadm and dsconf command-line utilities can be used dynamically while the servers are running. These management features mean that most management operations can be performed while the directory is online, thus maximizing availability.
Management flexibility simplifies the deployment of the directory service into many different environments. The command-line utilities make remote management as easy as if the service were in a local data center.
Directory Proxy Server
Directory Proxy Server is an LDAP application-layer protocol gateway. It is designed to deliver enhanced directory access control, schema compatibility, and high availability.
Directory Proxy Server and Availability
With features such as configurable load balancing, failover, and failback, Directory Proxy Server ensures that systems have access to required data.
Directory Proxy Server works with Directory Server to ensure reliability and to protect against denial-of-service attacks. Directory Proxy Server automatically routes requests appropriately and provides secure firewall-like services for Directory Server.
To prevent a single point of failure for mission-critical applications, Directory Proxy Server detects outages and routes traffic around affected areas, effectively load balancing requests across systems. When the affected areas are restored to operation, Directory Proxy Server detects the restored servers automatically.
For more information, see Using Directory Proxy Server as Part of a Redundant Solution.
Directory Proxy Server and Security
Directory Proxy Server accommodates large numbers of users who are accessing the directory and minimizes the security risks associated with providing this level of access. Security features enable administrators to determine where a request is coming from, whether the request is allowed, and what type of authentication is required. In the event of a search request, Directory Proxy Server can also ensure that the request meets minimum requirements.
Directory Proxy Server uses groups to define how to identify an LDAP client and what restrictions to enforce on clients that match a particular group. Groups can be defined using a variety of criteria.
To protect private directory information from unauthorized access, Directory Proxy Server can configure a fine-grained access control policy on LDAP directories. Such a policy can include controlling who can perform different types of operations on different parts of directories. Directory Proxy Server can be configured to prevent certain kinds of operations typically performed by web trawlers and robots in search of information.
Identity Synchronization for Windows
Identity Synchronization for Windows provides basic synchronization of identity data between Directory Server Enterprise Edition and Microsoft Active Directory.
Identity Synchronization for Windows fulfills the requirement of interoperability. Synchronization of key identity data such as passwords eliminates the need for users to modify passwords several times to accommodate different application authentication mechanisms.
Use of a non intrusive implementation for synchronizing key identity data eliminates the time-consuming and maintenance-intensive need to install a client component on Active Directory servers.
Identity Synchronization for Windows enables users to change passwords and other identity data in either the Windows environment or the web-based application environment. In this way, Identity Synchronization for Windows maintains synchronization between Active Directory and Directory Server. Disabled accounts can also be synchronized between Active Directory and Directory Server. This synchronization ensures conformance of access policies to applications and data between the Windows desktops and web-based applications.
Directory Editor
Directory Editor is a Java web application that provides efficient, cost-effective management of directory data.
Directory Editor fulfills the requirement of serviceability by enabling users to manage identity data within the directory service. Administrators can create a forms-based web interface with which users can perform everyday tasks. Directory Editor supports extensive customization, branding, and embedding for the interface. Customization is done using a form-based interface for configuration rather than writing code. To ensure data security and privacy, built-in authorization controls limit visibility of menus and actions. In this way, users see only what they are authorized to see within the application.
Directory Server Resource Kit
The Directory Server Resource Kit provides tools and application programming interfaces (APIs) for deploying, accessing, tuning, and maintaining Directory Server Enterprise Edition. These utilities help to implement and maintain more robust LDAP-based solutions.
Performance testing and capacity planning tools help administrators to measure performance and to perform capacity planning on installations of Directory Server Enterprise Edition. Debugging and maintenance tools help with troubleshooting as well as daily maintenance of Directory Server Enterprise Edition. Deployment utilities and tools facilitate the rollout of new installations of Directory Server Enterprise Edition and migration to new releases. LDAP productivity tools include sample LDAP applications that were developed using Directory Server Enterprise Edition.
In addition, Sun has developed SLAMD, a powerful load-generation testing application that includes all the tests needed to thoroughly performance-test Directory Server Enterprise Edition applications. SLAMD is available free of charge at http://www.slamd.com.
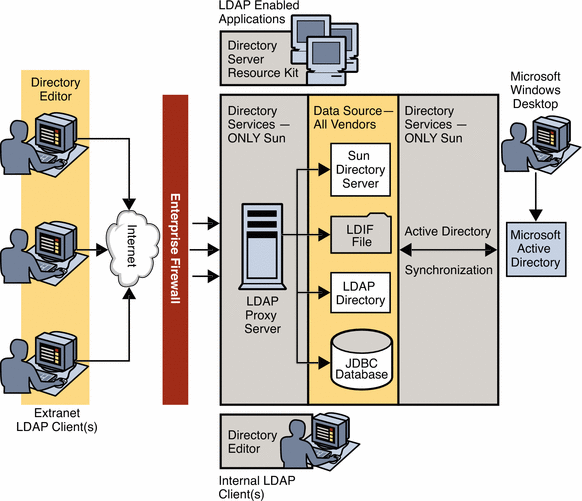
Directory Server Enterprise Edition Components in a Deployment
The combination of Directory Server Enterprise Edition components that you deploy depends on the requirements of your organization. The following figure shows a typical deployment scenario using the components described previously.
Figure 1–1 Directory Server Enterprise Edition Components
About Deployment Planning
Deployment planning is a critical step in the successful implementation of a Directory Server Enterprise Edition solution. Each enterprise has its own set of goals, requirements, and priorities to consider. Successful planning starts with analyzing the goals of an enterprise and determining the business requirements to meet those goals. The business requirements must then be converted into technical requirements. The technical requirements can be used as a basis for designing and implementing a system that meets the goals of the enterprise.
Successful deployment planning is the result of careful preparation, analysis, and design. Errors and missteps that occur anywhere during the planning process can result in a system that can be problematic in many ways. Significant problems can arise from a poorly planned system. For example, the system could under perform or be difficult to maintain, expensive to operate, or unable to scale.
The principles of deployment planning are discussed in depth in the Sun Java Enterprise System Deployment Planning Guide. This guide refers to the solution life cycle, which addresses deployment planning in clearly defined steps.
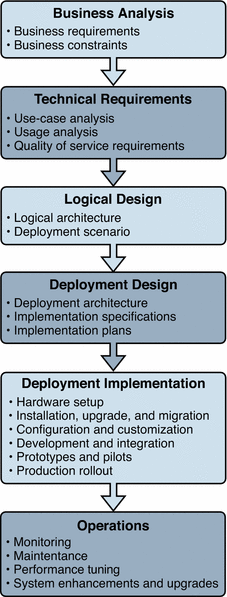
Solution Life Cycle
The solution life cycle shown in the following figure depicts the steps in the planning, design, and implementation of an enterprise software solution based on Java Enterprise System. The life cycle is a useful tool for keeping a deployment project on track. The solution life cycle is described in detail in the Sun Java Enterprise System Deployment Planning Guide.
Figure 1–2 Solution Life Cycle
- © 2010, Oracle Corporation and/or its affiliates
