Chapter 3 Federation
Sun Java™ System Access Manager provides an interface for creating, modifying, and deleting authentication domains, service providers, and identity providers. This chapter explains how to use the Federation module to configure these components, allowing for Liberty-based provider federation. It covers the following topics:
Process of Federation
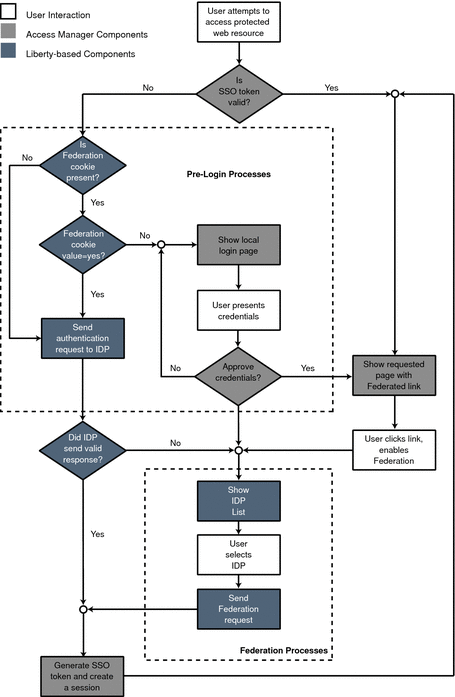
The process of federation begins with authentication. A standard installation of Access Manager provides two options for user authentication: the proprietary Authentication Service and the Liberty-based Federation component. With the proprietary option, users attempting to access a resource protected by Access Manager are redirected to the Authentication Service via an Access Manager login page. After the users provide credentials, the Authentication Service allows or denies access to the resource based on the outcome.
Note –
For more information about the proprietary Authentication Service, see the Sun Java System Access Manager 7.1 Administration Guide.
The second option for user authentication is Liberty-based federation. When a principal attempts to access a web site that belongs to the trusted member provider of a configured authentication domain, the process of user authentication begins with the search for a valid Access Manager session token from the proprietary Authentication Service.
-
If no session token is found, the principal is redirected to a location defined by the pre-login URL to establish a valid session. See Pre-login Process for details.
-
If a session token is found, the principal is granted (or denied) access to the requested page. Assuming access is granted, the requested page contains a link so the principal can federate the Access Manager identity with the identity local to the requested site. If the principal clicks this link, federation begins. See Federation and Single Sign-On for details.
The following figure illustrates these divergent paths.
Note –
The process shown in the figure below is the default process when no application has been deployed. When an application is deployed and using Access Manager, the process will change based on the application's query parameters and preferences. For more information, see The Pre-login URL.
Figure 3–1 Default Process of Federation
Pre-login Process
The pre-login process establishes a valid Access Manager session. When a principal attempts to access a service provider site and no Access Manager session token is found, Access Manager searches for a federation cookie. A federation cookie is implemented by Access Manager and is called fedCookie. It can have a value of either yes or no, based on the principal’s federation status.
Note –
A federation cookie is not defined in the Liberty Alliance Project specifications.
At this point, the pre-login process may take one of the following paths:
-
If a federation cookie is found and its value is no, an Access Manager login page is displayed and the principal submits credentials to the proprietary Authentication Service. When authenticated by Access Manager, the principal is redirected to the requested page, which might contain a link to allow for identity federation. If the principal clicks this link, federation begins. See Federation and Single Sign-On for details.
-
If a federation cookie is found and its value is yes, the principal has already federated an identity but has not been authenticated by an identity provider within the authentication domain for this Access Manager session. Authentication to Access Manager is achieved on the back end by sending a request to the principal’s identity provider. After authentication, the principal is directed back to the requested page.
-
If no federation cookie is found, a passive authentication request (one that does not allow identity provider interaction with the principal) is sent to the principal’s identity provider. If an affirmative authentication is received back from the identity provider, the principal is directed to the Access Manager Authentication Service, where a session token is granted. The principal is then redirected to the requested page. If the response from the identity provider is negative (for example, if the session has timed out), the principal is sent to a common login page to complete either a local login or Liberty-based federation. See Federation and Single Sign-On for details.
Note –
This pre-login process is the default behavior of Access Manager. This process might change based on parameters passed to Access Manager from the participating application. For more details, see the section on The Pre-login URL.
Federation and Single Sign-On
When a principal logs in to access a protected resource or service, Access Manager sends a request to the appropriate identity provider for authentication confirmation. If the identity provider sends a positive response, the principal gains access to all provider sites within the authentication domain. If the identity provider sends a negative response, the principal is directed to authenticate again using the Liberty-based federation process.
In the Liberty-based federation process, a principal selects an identity provider and sends credentials for authentication. After authentication is complete and access is granted, the principal is issued a session token from the Access Manager Authentication Service and redirected to the requested page. As long as the session token remains valid, the principal can access other service providers in the authentication domain without having to authenticate again.
Note –
Common Domain Services for Federation Management are used by a service provider to determine the identity provider used by a principal in an authentication domain that contains multiple identity providers. See Chapter 4, Common Domain Services for Federation Management for details.
Federation Graphical User Interface
The Federation component uses JavaServer Pages™ (JSP™) to define its look and feel. JSP are HTML files that contain additional code to generate dynamic content. More specifically, a JavaServer page contains HTML code to display static text and graphics, as well as application code to generate information. When the page is displayed in a web browser, it contains both the static HTML content and, in the case of the Federation component, dynamic content retrieved through calls to the Federation API. An administrator can customize the look and feel of the interface by changing the HTML tags in the JSP but the invoked APIs must not be changed.
The JSP are located in /AccessManager-base/SUNWam/web-src/services/config/federation/default. The files in this directory provide a default interface to the Federation component. To customize the pages for a specific organization, this default directory can be copied and renamed to reflect the name of the organization (or any value). This directory would then be placed at the same level as the default directory, and the files within this directory would be modified as needed. The following table lists the JSP including details on what each page is used for and the invoked APIs that cannot be modified. For more information about modifying these pages to customize the console, see the Sun Java System Access Manager 7.1 Developer’s Guide.
Entities and Authentication Domains
The Federation component in the Access Manager Console provides an interface for configuring, modifying, and deleting authentication domains, and its member identity providers and service providers. To enable provider federation using Access Manager, create and populate an authentication domain using the following process:
-
Create an entity to hold the metadata (information that defines a particular identity services architecture) for each provider that will become a member of the authentication domain.
See Creating Entities.
-
Configure and save an authentication domain.
-
Add an entity (a configured provider) to the authentication domain by configuring the entity's properties to add the authentication domain and configuring the authentication domain's properties to add the entity.
Information on configuring the entity's properties can be found in To Configure Hosted or Remote Identity Provider Attributes for a Provider Entity or To Configure Hosted or Remote Service Provider Attributes for a Provider Entity. Information on configuring the authentication domain's properties can be found in To Configure or Modify an Authentication Domain.
Note –
The establishment of contractual agreements between providers is beyond the scope of this guide. For information, see the Liberty Trust Model Guidelines.
The following sections contain more detailed information:
Tip –
In a federation setup, all service providers and identity providers must share a synchronized clock. You can implement the synchronization by pointing to an external clock source or by ensuring that, in case of delays in receiving responses, the responses are captured without fail through adjustments of the time outs.
Entities
An entity may be configured with metadata (configuration information that defines a particular identity service architecture) for an individual identity provider, an individual service provider, or one of each. Contrarily, an entity may be configured as an affiliation, a selected group of providers of either type. Both provider and affiliation entities can be configured using the Access Manager Console.
Note –
For general information about entities, see the Liberty Metadata Description and Discovery Specification.
- Provider Entity
-
A provider entity holds the metadata for individual providers of either type. All identity providers and service providers (both hosted and remote) must be configured within a provider entity before they can be associated with an authentication domain, or chosen to be included in an affiliate entity. Using the attributes provided in the Access Manager Console, one individual identity provider, one individual service provider, or one of each can be defined within a provider entity.
- Affiliate Entity
-
A configured affiliation (referenced by an affiliationID) contains a grouping of provider sites. The affiliation is formed and maintained by an affiliation owner who chooses the member providers from already configured provider entities. (An affiliation is formed without regard to the boundaries of any authentication domains which might also include the providers as members.) The affiliation enables a user to federate amongst the group of associated sites. The chosen providers may invoke services either as a member of the affiliation, or individually as a provider. If services are invoked as an affiliation member, a service provider might issue an authentication request for a user on behalf of an affiliation. When authentication is secured, the user can achieve single sign-on with all members of the affiliation.
An affiliate entity holds the metadata that defines the grouping of one or more provider entities that comprise the affiliation. It does not contain the configuration information for any providers (which is defined in a provider entity), only the configuration information for the affiliation itself.
Tip –The name identifier (a single persistent randomized string) is used to achieve single sign-on between an identity provider and a group of service providers acting as a single affiliation. If there are several service providers and identity providers in the same circle of trust, use an affiliate entity to avoid having to generate different name identifiers for commonly shared services.
Configuring an entity using the Access Manager Console is a two-step process. First, you create a provider or affiliate entity. Then, you populate the entity with either remote or hosted provider metadata (either service or identity) or affiliation information. This process is described in the following sections.
-
Creating and Configuring Entities using amadmin
Note –This section contains information on how entities can be created and configured in one step using the amadmin command-line interface and prepared XML files (as opposed to the manual configuration illustrated in the previous sections).
Creating Entities
This section describes the process for creating a provider entity or an affiliate entity.
 To Create a Provider Entity or an Affiliate
Entity
To Create a Provider Entity or an Affiliate
Entity
An entity can be created but it will not be available for assignment to an authentication domain until it has been populated with provider(s). Once created and populated, the entity (and thus the member providers) can be added to an authentication domain.
-
In the Access Manager Console, select the Federation tab.
-
Under Federation, select the Entities tab.
-
Select New.
The new entity attributes are displayed.
-
Type a value for the Entity Name.
This field specifies the uniform resource identifier (URI) of the entity and must be unique. For example, http://shivalik.sun.com or http://provider2.com:875.
-
(Optional) Enter a description of the entity in the Description field.
-
Select one of the following options to define the entity’s type.
-
Select Provider and click OK.
The new entity is now displayed as a provider in the list of configured Entities. To configure the entity, see To Configure a Provider Entity.
-
Select Affiliate, type a value for both Affiliate Name and Affiliate Owner, and click OK.
The Affiliate Name (or affiliationID) specifies a URI that uniquely represents the affiliate entity. For example, http://shivalik.sun.com or http://provider2.com:875. The Affiliate Owner (or providerID) is the value assigned to the Entity Name attribute of the provider entity that is forming the affiliation. After entering these values and clicking OK, the new entity is displayed as an affiliate in the list of configured Entities. To configure the entity, see To Configure an Affiliate Entity.
Note –Defining a service provider as the Affiliate Owner does not automatically include it as a member of the affiliate. If an owner is also a member, the provider ID must be defined as both.
-
Configuring Provider Entities
After you create a provider entity, you populate it with remote or hosted provider information (either service or identity). This section contains the following procedures:
-
To Configure Hosted or Remote Identity Provider Attributes for a Provider Entity
-
To Configure Hosted or Remote Service Provider Attributes for a Provider Entity
 To Configure a Provider Entity
To Configure a Provider Entity
When you configure a provider entity, you are populating it with remote or hosted provider information (either service or identity). You might also be defining values for attributes that were not available when the entity was initially created. Before performing this procedure, you must have completed the steps in To Create a Provider Entity or an Affiliate Entity.
-
In the Access Manager Console, select the Federation tab.
-
Under Federation, select the Entities tab.
-
Select the provider entity that you want to configure.
Ensure that you select an entity marked as type Provider.
-
Define values for the General, Identity Provider or Service Provider attributes by choosing from the View menu.
-
To define values for General attributes, see To Configure General Attributes for a Provider Entity.
-
To define values for Identity Provider attributes, see To Configure Hosted or Remote Identity Provider Attributes for a Provider Entity.
-
To define values for Service Provider attributes, see To Configure Hosted or Remote Service Provider Attributes for a Provider Entity.
-
 To Configure General Attributes for a Provider
Entity
To Configure General Attributes for a Provider
Entity
Before performing this procedure, you must have completed the steps in To Configure a Provider Entity.
-
Choose General from the View menu, and provide information for the Entity Common Attributes.
Entity Common Attributes contain values that define the entity itself.
- Entity Name
-
The static value of this attribute is the name that you provided when creating the entity.
- Type
-
The static value of this attribute is Provider.
- Description
-
The value of this optional attribute is the description that you provided when creating the entity. You can modify the description.
-
Provide information for the Entity Contact Person Profile attributes.
Entity Contact Person Profile attributes contain values that define the administrator of the entity.
- First Name
-
Type the given name of the entity’s contact person.
- Last Name
-
Type the surname of the entity’s contact person.
- Type
-
Choose the type of contact from the drop-down menu:
-
Administrative
-
Billing
-
Technical
-
Other
-
- Company
-
Type the name of the company that employs this person.
- Liberty Principal ID
-
Type a URI that points to an online instance of the contact person’s personal information profile.
- Emails
-
Type one or more email addresses for the contact person in New Value and click Add.
- Telephone Numbers
-
Type one or more telephone numbers for the contact person in New Value and click Add.
-
(Optional) Provide information for the Organization Profiles.
The Organization Profiles attributes contain values that define the organizational name of the entity.
- Names
-
Type the complete legal name of the entity’s organization in New Value and click Add. Use the format locale|organization-name. For example, en|organization-name.com.
Note –If the Names attribute contains a value, it is required to add values to the Display Names and URL attributes.
- Display Names
-
Type a name that is suitable for display in New Value and click Add. Use the format locale|organization-display-name. For example, en|organization-display-name.com.
- URL
-
Type a URL that can be used to direct a principal to additional information on the entity's organization in New Value and click Add. Use the format locale|organization-URL. For example, en|http://www.organization-name.com.
-
Click Save to complete the configuration, or define additional values for the Identity Provider or Service Provider attributes by choosing from the View menu.
-
To define values for Identity Provider attributes, see To Configure Hosted or Remote Identity Provider Attributes for a Provider Entity.
-
To define values for Service Provider attributes, see To Configure Hosted or Remote Service Provider Attributes for a Provider Entity.
-
 To Configure Hosted or Remote Identity Provider
Attributes for a Provider Entity
To Configure Hosted or Remote Identity Provider
Attributes for a Provider Entity
Before performing this procedure, you must have completed the steps in To Configure a Provider Entity.
Note –
Some of the attributes below will only be visible after you have saved the initial provider configuration.
-
Choose Identity Provider from the View menu.
-
Select the type of provider that you are configuring:
-
New Hosted Provider
A hosted provider is installed on the same server as Access Manager.
-
New Remote Provider
A remote provider is not installed on the same server as Access Manager.
-
-
Provide information for the Common Attributes.
Common Attributes contain values that generally define the identity provider.
- Provider Type
-
The static value of this attribute is the type of provider being configured: hosted or remote.
- Description
-
The value of this attribute is a description of the identity provider.
- Protocol Support Enumeration
-
Choose the Liberty ID-FF release that is supported by this provider.
-
urn:liberty:iff:2003-08 refers to the Liberty Identity Federation Framework Version 1.2.
-
urn:liberty:iff:2002-12 refers to the Liberty Identity Federation Framework Version 1.1.
-
- Server Name Identifier Mapping Binding
-
Name identifier mapping allows a service provider to obtain a name identifier for a principal that has federated in the namespace of a different service provider. Implementing this protocol allows the requesting service provider to communicate with the second service provider without an identity federation having been enabled. Type a URI that identifies the communication specifications in New Value and click Add.
Note –Currently, the Name Identifier Mapping profile only supports SOAP. If this attribute is used, its value must be http://projectliberty.org/profiles/nim-sp-http.
- Signing Key: Key Alias
-
Type the key alias that is used to sign requests and responses.
- Encryption Key: Key Alias
-
Type the security certificate alias. Certificates are stored in a Java keystore file. Each specific certificate is mapped to an alias that is used to fetch the certificate.
- Encryption Key: Key Size
-
Type the length for keys that are used by the web service consumer when interacting with another entity.
Note –If the encryption method is DESede, the key size must be 192. If the encryption method is AES, the key size must be 128, 192 or 256.
- Encryption Key: Encryption Method
-
Choose the method of encryption:
-
None
-
AES
-
DESede
-
- Name Identifier Encryption
-
Select the check box to enable encryption of the name identifier.
-
Provide information for the Communication URLs.
Communication URLs attributes contain locations for redirects and sending requests.
- SOAP Endpoint
-
Type a URI to the identity provider’s SOAP message receiver. This value communicates the location of the SOAP receiver in non browser communications.
- Single Sign-On Service URL
-
Type a URL to which service providers can send single sign-on and federation requests.
- Single Logout Service
-
Type a URL to which service providers can send logout requests. Single logout synchronizes the logout functionality across all sessions authenticated by the identity provider.
- Single Logout Return
-
Type a URL to which the identity provider will redirect the principal after completing a logout.
- Federation Termination Service
-
Type a URL to which a service provider will send federation termination requests.
- Federation Termination Return
-
Type a URL to which the identity provider will redirect the principal after completing federation termination.
- Name Registration Service
-
Type a URL to which a service provider will send requests to specify a new name identifier to be used when communicating with the identity provider about a principal. This service can only be used after a federation session is established.
- Name Registration Return
-
Type a URL to which the identity provider will redirect the principal after HTTP name registration has been completed.
-
Provide information for the Communication Profiles.
Communication Profiles attributes define the transmission methods used by the identity provider.
- Federation Termination
-
Select a profile to notify other providers of a principal’s federation termination:
-
HTTP Redirect
-
SOAP
-
- Single Logout
-
Select a profile to notify other providers of a principal’s logout:
-
HTTP Redirect
-
HTTP Get
-
SOAP
-
- Name Registration
-
Select a profile to notify other providers of a principal’s name registration:
-
HTTP Redirect
-
SOAP
-
- Single Sign-on/Federation
-
Select a profile for sending authentication requests:
-
Browser Post (specifies a browser-based HTTP POST protocol)
-
Browser Artifact (specifies a non-browser SOAP-based protocol)
-
LECP (specifies a Liberty-enabled Client Proxy)
Note –Access Manager can handle requests that come from a Liberty-enabled client proxy profile, but it requires additional configuration that is beyond the scope of this manual.
-
-
Select any of the available authentication domains to assign to the provider.
A provider can belong to one or more authentication domains. However, a provider without a specified authentication domain can not participate in Liberty-based communications. If no authentication domains have been created, you can define this attribute later.
Note –If configuring a remote identity provider, skip to step 11. If configuring a hosted identity provider, continue with step 7.
-
(Hosted Identity Provider Only) Provide mappings for the Authentication Context classes.
This attribute maps the Liberty-defined authentication context classes to authentication methods available from the identity provider.
- Supported
-
Select the check box next to the authentication context class if the identity provider supports it.
- Context Reference
-
The Liberty-defined authentication context classes are:
-
Mobile Contract
-
Mobile Digital ID
-
MobileUnregistered
-
Password
-
Password-ProtectedTransport
-
Previous-Session
-
Smartcard
-
Smartcard-PKI
-
Software-PKI
-
Time-Sync-Token
-
- Key
-
Choose the Access Manager authentication type to which the context is mapped.
Note –See Authentication Types in Sun Java System Access Manager 7.1 Administration Guide for more information.
- Value
-
Type the Access Manager authentication option.
- Priority
-
Choose a priority level for cases where there are multiple contexts.
-
(Hosted Identity Provider Only) Select any of the available provider entities to assign as a Trusted Provider and click Add.
This attribute tallies providers that the identity provider trusts.
-
(Hosted Identity Provider Only) Provide information for the Access Manager Configuration attributes.
Access Manager Configuration attributes define general information regarding the instance of Access Manager being used as an identity provider.
- Provider Alias
-
Type an alias name for the local identity provider.
- Authentication Type
-
Select the provider that should be used for authentication requests from a provider hosted locally:
-
Remote specifies that the provider hosted locally would contact a remote identity provider upon receiving an authentication request.
-
Local specifies that the provider hosted locally should contact a local identity provider upon receiving an authentication request (essentially, itself).
-
- Default Authentication Context
-
Select the authentication context class (method of authentication) to use if the identity provider does not receive this information as part of a service provider request. This value also specifies the authentication context used by the service provider when an unknown user tries to access a protected resource. The options are:
-
Password
-
Mobile Digital ID
-
Smartcard
-
Smartcard-PKI
-
MobileUnregistered
-
Software-PKI
-
Previous-Session
-
Mobile Contract
-
Time-Sync-Token
-
Password-ProtectedTransport
-
- Realm
-
Type a value that points to the realm in which this provider is configured. For example, /sp.
- Liberty Version URI
-
Type the URI of the version of the Liberty Alliance Project specification being used. The default value is http://projectliberty.org/specs/v1.
- Name Identifier Implementation
-
This field defines the class used by a service provider to participate in name registration. Name registration is a profile by which service providers specify a principal’s name identifier that an identity provider will use when communicating with the service provider. The value is com.sun.identity.federation.services.util.FSNameIdentifierImpl.
- Home Page URL
-
Type the URL of the home page of the identity provider.
- Single Sign-on Failure Redirect URL
-
Type the URL to which a principal will be redirected if single sign-on has failed.
- Assertion Issuer
-
Type the name of the host that issues the assertion. This value might be the load balancer's host name if Access Manager is behind one.
- Generate Discovery Bootstrapping Resource Offering
-
Select the check box if you want a Discovery Service Resource Offering to be generated during the Liberty-based single sign-on process for bootstrapping purposes.
- Auto Federation
-
Select the check box to enable auto-federation.
- Auto Federation Common Attribute Name
-
When creating an Auto Federation Attribute Statement, the value of this attribute will be used. The statement will contain the AutoFedAttribute element and this common attribute as its value.
- Attribute Statement Plug-in
-
Specify a pluggable class used for adding attribute statements to an assertion that is generated during the Liberty-based single sign-on process.
- Identity Provider Attribute Mapping
-
Specify values to define the mappings used by the default attribute mapper plug-in. Mappings should be configured in the format:
SAML-attribute=local-attribute
For example, EmailAddress=mail or Address=postaladdress. Type the mapping as a New Value and click Add.
-
(Hosted Identity Provider Only) Provide information for the SAML Attributes.
SAML Attributes define general information regarding SAML assertions that are sent by the identity provider.
- Assertion Interval
-
Type the interval of time (in seconds) that an assertion issued by the identity provider will remain valid. A principal will remain authenticated until the assertion interval expires.
- Cleanup Interval
-
Type the interval of time (in seconds) before assertions stored in the identity provider will be cleared.
- Artifact Timeout
-
Type the interval of time (in seconds) to specify the timeout for assertion artifacts.
- Assertion Limit
-
Type a number to define how many assertions an identity provider can issue, or how many assertions that can be stored.
Note –To continue configuring a hosted identity provider, skip to step 12.
-
(Remote Identity Provider Only) Provide information for the Proxy Authentication Configuration attributes.
Proxy Authentication Configuration attributes define values for dynamic identity provider proxying.
- Proxy Authentication
-
Select the check box to enable proxy authentication for a service provider.
- Proxy Identity Providers List
-
Type an identifier for an identity provider(s) that can be used for proxy authentication in New Value and click Add. The value is a URI defined as the provider's identifier.
- Maximum Number of Proxies
-
Enter the maximum number of identity providers that can be used for proxy authentication.
- Use Introduction Cookie for Proxying
-
Select the check box if you want introductions to be used to find the proxying identity provider.
-
(Optional) Provide information for the Organization Profiles.
The Organization Profiles attributes contain values that define the organizational name of the entity.
- Names
-
Type the complete legal name of the organization in New Value and click Add. Use the format locale|organization-name, for example, en|organization-name.com.
Note –If the Names attribute contains a value, it is required to add values to the Display Names and URL attributes also.
- Display Names
-
Type a name that is suitable for display to a principal in New Value and click Add. The value is defined in the format locale|organization-display-name, for example, en|organization-display-name.com.
- URL
-
Type a URL that can be used to direct a principal to additional information on the entity in New Value and click Add. Use the format locale|organization-URL, for example, en|http://www.organization-name.com.
-
Click New Contact Person to create a contact person for the provider.
The Contact Person attributes contain information regarding a human contact for the identity provider.
- First Name
-
Type the given name of the identity provider’s contact person.
- Last Name
-
Type the surname of the identity provider's contact person.
- Type
-
Choose the contact's role from the drop-down menu:
-
Administrative
-
Billing
-
Technical
-
Other
-
- Company
-
Type the name of the company that employs the contact person.
- Liberty Principal Identifier
-
Type the name identifier that points to an online instance of the contact person’s personal information profile.
- Emails
-
Type one or more email addresses for the contact person in New Value and click Add.
- Telephone Numbers
-
Type one or more telephone numbers for the contact person in New Value and click Add.
-
Click Create to create the contact person.
-
Click Save to complete the configuration, or define values for General or Service Provider attributes by choosing from the View menu:
-
To define values for General attributes, see To Configure General Attributes for a Provider Entity.
-
To define values for Service Provider attributes, see To Configure Hosted or Remote Service Provider Attributes for a Provider Entity.
-
 To Configure Hosted or Remote Service Provider
Attributes for a Provider Entity
To Configure Hosted or Remote Service Provider
Attributes for a Provider Entity
Before performing this procedure, you must have completed the steps in To Configure a Provider Entity.
Note –
Some of the attributes below will only be visible after you have saved the initial provider configuration.
-
Choose Service Provider from the View menu.
-
Select the type of provider that you are configuring:
-
New Hosted Provider
A hosted provider is installed on the same server as Access Manager.
-
New Remote Provider
A remote provider is not installed on the same server as Access Manager.
-
-
Provide information for the Common Attributes.
Common Attributes contain values that generally define the service provider.
- Provider Type
-
The static value of this attribute is the type of provider being configured: hosted or remote. This attribute is visible only after saving your configuration.
- Description
-
The value of this attribute is a description of the service provider.
- Protocol Support Enumeration
-
Select the Liberty ID-FF release that is supported by this provider.
-
urn:liberty:iff:2003-08 refers to the Liberty Identity Federation Framework Version 1.2.
-
urn:liberty:iff:2002-12 refers to the Liberty Identity Federation Framework Version 1.1.
-
- Server Name Identifier Mapping Binding
-
Name identifier mapping allows a service provider to obtain a name identifier for a principal that has federated in the namespace of a different service provider. Implementing this protocol allows the requesting service provider to communicate with the second service provider without an identity federation having been enabled. Type a URI that identifies the communication specifications in New Value and click Add.
Note –Currently, the Name Identifier Mapping profile only supports SOAP. If this attribute is used, its value must be http://projectliberty.org/profiles/nim-sp-http.
- Signing Key: Key Alias
-
Type the key alias that is used to sign requests and responses.
- Encryption Key: Key Alias
-
Type the security certificate alias. Certificates are stored in a Java keystore file. Each specific certificate is mapped to an alias that is used to fetch the certificate.
- Encryption Key: Key Size
-
Type the length for keys that are used by the web service consumer when interacting with another entity.
- Encryption Key: Encryption Method
-
Select the method of encryption:
-
None
-
AES
-
DESede
-
- Name Identifier Encryption
-
Select the check box to enable encryption of the name identifier.
-
Provide information for the Communication URLs.
Communication URLs attributes contain locations for redirects and sending requests.
- SOAP Endpoint
-
Type a URI to the service provider’s SOAP message receiver. This value communicates the location of the SOAP receiver in non browser communications.
- Single Logout Service
-
Type a URL to which identity providers can send logout requests.
- Single Logout Return
-
Type a URL to which the service provider will redirect the principal after completing a logout.
- Federation Termination Service
-
Type a URL to which identity providers will send federation termination requests.
- Federation Termination Return
-
Type a URL to which the service provider will redirect the principal after completing federation termination.
- Name Registration Service
-
Type a URL that will be used when communicating with the identity provider to specify a new name identifier for the principal. (Registration can occur only after a federation session is established.)
- Name Registration Return
-
Type a URL to which the service provider will redirect the principal after HTTP name registration has been completed.
-
Provide information for the Communication Profiles.
Communication Profiles attributes define the transmission methods used by the service provider.
- Federation Termination
-
Select a profile to notify other providers of a principal’s federation termination:
-
HTTP Redirect
-
SOAP
-
- Single Logout
-
Select a profile to notify other providers of a principal’s logout:
-
HTTP Redirect
-
HTTP Get
-
SOAP
-
- Name Registration
-
Select a profile to notify other providers of a principal’s name registration:
-
HTTP Redirect
-
SOAP
-
- Single Sign-on/Federation
-
Select a profile for sending authentication requests:
-
Browser Post (specifies a browser-based HTTP POST protocol)
-
Browser Artifact (specifies a non-browser SOAP-based protocol)
-
LECP (specifies a Liberty-enabled Client Proxy)
Note –Access Manager can handle requests that come from a Liberty-enabled client proxy profile, but it requires additional configuration that is beyond the scope of this manual.
-
-
Select any of the available authentication domains to assign to the provider.
A provider can belong to one or more authentication domains. However, a provider without a specified authentication domain cannot participate in Liberty-based communications. If no authentication domains have been created, you can define this attribute later.
Note –If configuring a hosted service provider, skip to step 9. If configuring a hosted service provider, continue with step 7.
-
(Hosted Service Provider Only) Provide a hierarchy for the Authentication Context classes.
This attribute corresponds to the authentication level defined for an Access Manager authentication module. It will redirect the principal to the authentication type with an authentication level equal to the number defined.
- Context Reference
-
The Liberty-defined authentication context classes are:
-
Password
-
Mobile Digital ID
-
Smartcard
-
Smartcard-PKI
-
MobileUnregistered
-
Software-PKI
-
Previous-Session
-
Mobile Contract
-
Time-Sync-Token
-
Password-ProtectedTransport
-
- Level
-
Type a level for each authentication context class. The number can be any positive number.
-
(Hosted Service Provider Only) Select any of the available provider entities to assign as a Trusted Provider and click Add.
This attribute tallies providers that the service provider trusts.
-
Provide information for the Service Provider attributes.
Service Provider attributes define general information regarding the service provider.
- Assertion Consumer URL
-
Type the URL to the end point that defines where a provider will send SAML assertions.
- Assertion Consumer Service URL ID
-
If the value of the Protocol Support Enumeration common attribute is urn:liberty:iff:2003-08, type the required ID.
- Set Assertion Consumer Service URL as Default
-
Select the check box to use the Assertion Consumer Service URL as the default value when no identifier is provided in the request.
- Sign Authentication Request
-
Select the check box to make the service provider always signs authentication requests.
- Name Registration after Federation
-
Select the check box to enable the service provider to participate in name registration after a principal has been federated.
- Name ID Policy
-
Select the option permitting requester influence over name identifier policy at the identity provider. The options are:
-
None specifies that the identity provider will return the name identifier(s) for the principal corresponding to the federation that exists between the identity provider and the requesting service provider or affiliation group. If no such federation exists, an error will be returned.
-
One-time specifies that the identity provider will issue a temporary, one-time-use identifier for the principal after federation.
-
Federation specifies that the identity provider may start a new identity federation if one does not already exist for the principal.
-
- Affiliation Federation
-
Select the check box to enable affiliation federation.
Note –If configuring a remote service provider, skip to step 11. If configuring a hosted service provider, continue with step 10.
-
(Hosted Service Provider Only) Provide information for the Access Manager Configuration attributes.
Access Manager Configuration attributes define general information regarding the instance of Access Manager being used as a service provider.
- Service Provider Adapter
-
Defines the implementation class for the com.sun.identity.federation.plugins.FederationSPAdapter interface, used to add application-specific processing during the federation process.
- Provider Alias
-
Type an alias name for the local service provider.
- Authentication Type
-
Select the provider that should be used for authentication requests from a provider hosted locally:
-
Remote specifies that the provider hosted locally would contact a remote identity provider upon receiving an authentication request.
-
Local specifies that the provider hosted locally should contact a local identity provider upon receiving an authentication request (essentially, itself).
-
- Default Authentication Context
-
This attribute defines the service provider's default authentication context class (method of authentication). This method will always be called when the service provider sends an authentication request. This value also specifies the authentication context used by the service provider when an unknown user tries to access a protected resource. The options are:
-
Password
-
Mobile Digital ID
-
Smartcard
-
Smartcard-PKI
-
MobileUnregistered
-
Software-PKI
-
Previous-Session
-
Mobile Contract
-
Time-Sync-Token
-
Password-ProtectedTransport
-
- Identity Provider Forced Authentication
-
Select the check box to indicate that the identity provider must reauthenticate (even during a live session) when an authentication request is received. This attribute is enabled by default.
- Request Identity Provider to be Passive
-
Select the check box to specify that the identity provider must not interact with the principal and must interact with the user.
- Realm
-
Type a value that points to the realm in which this provider is configured, for example, /sp.
- Liberty Version URI
-
Type the URI of the version of the Liberty specification being used. The default value is http://projectliberty.org/specs/v1.
- Name Identifier Implementation
-
This field defines the class used by a service provider to participate in name registration. Name registration is a profile by which service providers specify a principal’s name identifier that an identity provider will use when communicating with the service provider. The value is com.sun.identity.federation.services.util.FSNameIdentifierImpl.
- Home Page URL
-
Type the URL of the home page of the service provider.
- Single Sign-on Failure Redirect URL
-
Type the URL to which a principal will be redirected if single sign-on has failed.
- Auto Federation
-
Select the check box to enable auto-federation.
- Auto Federation Common Attribute Name
-
When creating an Auto Federation Attribute Statement, the value of this attribute will be used. The statement will contain the AutoFedAttribute element and this common attribute as its value.
- Attribute Mapper Class
-
The class used to map attributes in the SAML assertion to user attributes defined locally by the service provider. The default class is com.sun.identity.federation.services.FSDefaultAttributeMapper.
- Service Provider Attribute Mapping
-
Specify values to define the mappings used by the default attribute mapper plug-in specified above. Mappings should be configured in the format:
SAML-attribute=local-attribute
For example, EmailAddress=mail or Address=postaladdress. Type the mapping as a New Value and click Add.
-
Provide information for the Proxy Authentication Configuration attributes.
Proxy Authentication Configuration attributes define values for dynamic identity provider proxying.
- Proxy Authentication
-
Select the check box to enable proxy authentication for a service provider.
- Proxy Identity Providers List
-
Add a list of identity providers that can be used for proxy authentication. Type the URI defined as the provider's identifier in New Value and click Add.
- Maximum Number of Proxies
-
Enter the maximum number of identity providers that can be used for proxy authentication.
- Use Introduction Cookie for Proxying
-
Select the check box if you want introductions to be used to find the proxying identity provider.
-
(Optional) Provide information for the Organization Profiles.
The Organization Profiles attributes contain values that define the organizational name of the entity.
- Names
-
Type the complete legal name of the entity’s organization in New Value and click Add. Use the format locale|organization-name, for example, en|organization-name.com.
Note –If the Names attribute contains a value, it is required to add values to the Display Names and URL attributes.
- Display Names
-
Type a name that is suitable for display in New Value and click Add. Use the format locale|organization-display-name, for example, en|organization-display-name.com.
- URL
-
Type a URL that can be used to direct a principal to additional information on the entity's organization in New Value and click Add. Use the format locale|organization-URL, for example, en|http://www.organization-name.com.
-
Click New Contact Person to create a contact person for the provider.
The Contact Person attributes contain information regarding a human contact for the identity provider.
- First Name
-
Type the given name of the identity provider’s contact person.
- Last Name
-
Type the surname of the identity provider's contact person.
- Type
-
Choose the contact's role from the drop-down menu:
-
Administrative
-
Billing
-
Technical
-
Other
-
- Company
-
Type the name of the company that employs the contact person.
- Liberty Principal Identifier
-
Type the name identifier that points to an online instance of the contact person’s personal information profile.
- Emails
-
Type one or more email addresses for the contact person in New Value and click Add.
- Telephone Numbers
-
Type one or more telephone numbers for the contact person in New Value and click Add.
-
Click Create to create the contact person.
-
Click Save to complete the configuration, or define values for General or Identity Provider attributes by choosing from the View menu:
-
To define values for General attributes, see To Configure General Attributes for a Provider Entity.
-
To define values for Identity Provider attributes, see To Configure Hosted or Remote Identity Provider Attributes for a Provider Entity.
-
Configuring Affiliate Entities
After you create an affiliate entity, you populate it with affiliation information. This section contains the following procedures:
 To Configure an Affiliate Entity
To Configure an Affiliate Entity
Before performing this procedure, you must have completed the steps in To Create a Provider Entity or an Affiliate Entity.
-
In the Access Manager Console, select the Federation tab.
-
Under Federation, select the Entities tab.
-
Select the entity that you want to configure.
Ensure that you select an entity marked as type Affiliate.
-
Define values for the General or Affiliate attribute groupings by choosing from the View menu:
-
To define values for General attributes, see To Configure General Attributes for an Affiliate Entity
-
To define values for Affiliate attributes, see To Configure Affiliate Attributes for an Affiliate Entity
-
 To Configure General Attributes for an Affiliate
Entity
To Configure General Attributes for an Affiliate
Entity
Before performing this procedure, you must have completed the steps in To Configure an Affiliate Entity.
-
Choose General from the View menu, and provide information for the Entity Common Attributes.
Entity Common Attributes contain values that define the entity.
- Entity Name
-
The static value of this attribute is the name that you provided when creating the entity.
- Type
-
The static value of this attribute is Affiliate.
- Description
-
The value of this optional attribute is the description that you provided when creating the entity. You can modify the description.
-
Provide information for the Entity Contact Person Profile attributes.
Entity Contact Person Profile attributes contain values that define the administrator of the entity.
- First Name
-
Type the given name of the entity’s contact person.
- Last Name
-
Type the surname of the entity’s contact person.
- Type
-
Choose the type of contact from the drop-down menu:
-
Administrative
-
Billing
-
Technical
-
Other
-
- Company
-
Type the name of the company that employs this person.
- Liberty Principal ID
-
Type a URI that points to an online instance of the contact person’s personal information profile.
- Emails
-
Type one or more email addresses for the contact person in New Value and click Add.
- Telephone Numbers
-
Type one or more telephone numbers for the contact person in New Value and click Add.
-
(Optional) Provide information for the Organization Profiles.
The Organization Profiles attributes contain values that define the organizational name of the entity.
- Names
-
Type the complete legal name of the organization in New Value and click Add. Use the format locale|organization-name, for example, en|organization-name.com.
Note –If the Names attribute contains a value, it is required to add values to the Display Names and URL attributes also.
- Display Names
-
Type a name that is suitable for display to a principal in New Value and click Add. The value is defined in the format locale|organization-display-name. For example, en|organization-display-name.com.
- URL
-
Type a URL that can be used to direct a principal to additional information on the entity in New Value and click Add. Use the format locale|organization-URL, for example, en|http://www.organization-name.com.
-
Click Save to complete the configuration, or choose Affiliate from the View menu to configure the Affiliate attributes.
To define values for Affiliate attributes, see To Configure Affiliate Attributes for an Affiliate Entity.
 To Configure Affiliate Attributes for an Affiliate
Entity
To Configure Affiliate Attributes for an Affiliate
Entity
Before performing this procedure, you must have completed the steps in To Configure an Affiliate Entity.
-
Select any of the available provider entities to add to the affiliation.
A provider must be a member of an authentication domain as, without a specified authentication domain, it cannot participate in Liberty-based communications. The provider can belong to one or more affiliations. Also, be sure that the selected provider has the Affiliation Federation attribute enabled and the Protocol Support Enumeration attribute set to urn:liberty:iff:2003-08 to enable the Liberty ID-FF version 1.2.
-
Choose Affiliate from the View menu and provide information for the Common Attributes.
Common Attributes contain values that generally define the affiliation.
- Name
-
The value of this attribute is the name of the affiliation.
- Owner
-
The value of this attribute is the owner of the affiliation.
- Signing Key: Key Alias
-
Type the key alias that is used to sign requests and responses.
- Encryption Key: Key Alias
-
Type the security certificate alias. Certificates are stored in a JKS keystore file. Each specific certificate is mapped to an alias that is used to fetch the certificate.
- Encryption Key: Key Size
-
Type the length for keys used by the web service consumer when interacting with another entity.
- Encryption Key: Encryption Method
-
Select the method of encryption:
-
None
-
AES
-
DESede
-
-
Click Save to complete the configuration.
-
Click OK to complete the configuration, or choose General from the View menu to configure the General attributes.
To define values for General attributes, see To Configure General Attributes for an Affiliate Entity.
Deleting Entities
If an entity is to be deleted from the console, it first needs to be manually removed from the Trusted Providers list (if the provider is hosted) or the Available Providers list (if part of an affiliation).
 To Delete a Provider or Affiliate Entity
To Delete a Provider or Affiliate Entity
-
In the Access Manager Console, click the Federation tab.
-
Under Federation, select the Entities tab.
-
Select the check box next to the entity that you want to delete.
No warning message is displayed when performing a delete.
-
Click Delete.
Creating and Configuring Entities using amadmin
The previous sections detailed how to create and configure entities using the Access Manager console. But entities can also be created and configured in one step using the amadmin command-line interface and prepared XML files. Rather than filling in provider attribute values manually, you would create an XML file containing the provider attributes and corresponding values and import it using amadmin. Alternatively, you can modify the sample provider metadata XML files included with Access Manager. See sample1 Directory for information.
The format of the XML file used as input is based on the sms.dtd, located in /AccessManager-base/SUNWam/dtd. Alterations to the DTD files may hinder the operation of Access Manager.
There are two types of provider metadata (formatted in XML files) that can be used as input to amadmin:
-
Standard metadata properties are defined in the Liberty ID-FF specification.
-
Extended metadata properties are proprietary and used by features specific to Access Manager.
Note –
amadmin uses different options to load the different types of metadata XML files. Information on how to use amadmin can be found in Using amadmin for Federation Management in Sun Java System Access Manager 7.1 Administration Reference. Information regarding the attributes and possible values can be found in the online help of the Access Manager console or in the following sections:
Following are instructions to load the provider metadata:
Loading Standard Metadata Using amadmin
To load metadata compliant with the Liberty ID-FF use the following command:
amadmin --runasdn userdn --password password --import metadata_filename |
This option is usually used to load provider metadata sent from a trusted partner in an XML file compliant with the Liberty ID-FF. Here is an example of a service provider metadata XML file compliant with the Liberty ID-FF.
Example 3–1 Service Provider Standard Metadata XML File for amadmin
<!--
Copyright (c) 2005 Sun Microsystems, Inc. All rights reserved
Use is subject to license terms.
-->
<EntityDescriptor meta:providerID="http://sp10.com" meta:cacheDuration="360"
xmlns:meta="urn:liberty:metadata:2003-08" xmlns="urn:liberty:metadata:2003-08">
<SPDescriptor cacheDuration="180" xmlns:meta="urn:liberty:metadata:2003-08"
aaa="aaa" protocolSupportEnumeration="urn:liberty:iff:2003-08">
<KeyDescriptor use="signing">
<EncryptionMethod>http://something/encrypt</EncryptionMethod>
<KeySize>4567</KeySize>
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Certificate xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
MIIC1DCCApICBD8poYwwCwYHKoZIzjgEAwUAMFAxCzAJBgNVBAYTAlVTMQwwCgYDVQQKEwNTdW4x
IDAeBgNVBAsTF1NVTiBPTkUgSWRlbnRpdHkgU2VydmVyMREwDwYDVQQDEwhzdW4tdW5peDAeFw0w
MzA3MzEyMzA5MDBaFw0wNDAxMjcyMzA5MDBaMFAxCzAJBgNVBAYTAlVTMQwwCgYDVQQKEwNTdW4x
IDAeBgNVBAsTF1NVTiBPTkUgSWRlbnRpdHkgU2VydmVyMREwDwYDVQQDEwhzdW4tdW5peDCCAbcw
ggEsBgcqhkjOOAQBMIIBHwKBgQD9f1OBHXUSKVLfSpwu7OTn9hG3UjzvRADDHj+AtlEmaUVdQCJR
+1k9jVj6v8X1ujD2y5tVbNeBO4AdNG/yZmC3a5lQpaSfn+gEexAiwk+7qdf+t8Yb+DtX58aophUP
BPuD9tPFHsMCNVQTWhaRMvZ1864rYdcq7/IiAxmd0UgBxwIVAJdgUI8VIwvMspK5gqLrhAvwWBz1
AoGBAPfhoIXWmz3ey7yrXDa4V7l5lK+7+jrqgvlXTAs9B4JnUVlXjrrUWU/mcQcQgYC0SRZxI+hM
KBYTt88JMozIpuE8FnqLVHyNKOCjrh4rs6Z1kW6jfwv6ITVi8ftiegEkO8yk8b6oUZCJqIPf4Vrl
nwaSi2ZegHtVJWQBTDv+z0kqA4GEAAKBgCNS1il+RQAQGcQ87GBFde8kf8R6ZVuaDDajFYE4/LNT
Kr1dhEcPCtvL+iUFi44LzJf8Wxh+eA5K1mjIdxOo/UdwTpNQSqiRrm4Pq0wFG+hPnUTYLTtENkVX
IIvfeoVDkXnF/2/i1Iu6ttZckimOPHfLzQUL4ldL4QiaYuCQF6NfMAsGByqGSM44BAMFAAMvADAs
AhQ6yueX7YlD7IlJhJ8D4l6xYqwopwIUHzX82qCzF+VzIUhi0JG7slSpyis=
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<SingleLogoutServiceURL>http://www.sun.com/slo"</SingleLogoutServiceURL>
<SingleLogoutServiceReturnURL>http://www.sun.com/sloservice
</SingleLogoutServiceReturnURL>
<FederationTerminationServiceURL>http://www.sun.com/fts
</FederationTerminationServiceURL>
<FederationTerminationServiceReturnURL>http://www.sun.com/ftsr
</FederationTerminationServiceReturnURL>
<FederationTerminationNotificationProtocolProfile>http://projectliberty.org/profiles/
fedterm-sp-http</FederationTerminationNotificationProtocolProfile>
<SingleLogoutProtocolProfile>http://projectliberty.org/profiles/slo-sp-http
</SingleLogoutProtocolProfile>
<RegisterNameIdentifierProtocolProfile>http://projectliberty.org/profiles/
rni-sp-http</RegisterNameIdentifierProtocolProfile>
<RegisterNameIdentifierServiceURL>http://www.sun2.com/risu
</RegisterNameIdentifierServiceURL>
<RegisterNameIdentifierServiceReturnURL>http://www.sun2.com/rstu
</RegisterNameIdentifierServiceReturnURL>
<RelationshipTerminationNotificationProtocolProfile>http://projectliberty.org/
profiles/rel-term-soap</RelationshipTerminationNotificationProtocolProfile>
<NameIdentifierMappingBinding AuthorityKind="ppp:AuthorizationDecisionQuery"
Location="http://eng.sun.com" Binding="http://www.sun.com"
xmlns:ppp="urn:oasis:names:tc:SAML:1.0:protocol"></NameIdentifierMappingBinding>
<AdditionalMetaLocation namespace="abc">http://www.aol.com</AdditionalMetaLocation>
<AdditionalMetaLocation namespace="efd">http://www.netscape.com</AdditionalMetaLocation>
<AssertionConsumerServiceURL id="jh899" isDefault="true">
http://www.iplanet.com/assertionurl</AssertionConsumerServiceURL>
<AuthnRequestsSigned>true</AuthnRequestsSigned>
</SPDescriptor>
<ContactPerson xmlns:meta="urn:liberty:metadata:2003-08" contactType="technical"
meta:libertyPrincipalIdentifier="myid">
<Company>SUn Microsystems</Company>
<GivenName>Joe</GivenName>
<SurName>Smith</SurName>
<EmailAddress>joe@sun.com</EmailAddress>
<EmailAddress>smith@sun.com</EmailAddress>
<TelephoneNumber>45859995</TelephoneNumber>
</ContactPerson>
<Organization xmlns:xml="http://www.w3.org/XML/1998/namespace">
<OrganizationName xml:lang="en">sun com</OrganizationName>
<OrganizationName xml:lang="en">sun micro com</OrganizationName>
<OrganizationDisplayName xml:lang="en">sun.com</OrganizationDisplayName>
<OrganizationURL xml:lang="en">http://www.sun.com/liberty</OrganizationURL>
</Organization>
</EntityDescriptor>
|
Loading Proprietary Metadata Using amadmin
Access Manager provides proprietary attributes that are not a specific part of the Liberty ID-FF. To load Access Manager proprietary metadata use the following command:
amadmin --runasdn userdn --password password --data proprietary_metadata_filename |
After loading the metadata, the --export option can be used to export metadata compliant with the Liberty ID-FF. This file can then be exchanged with trusted partners. Here is an example of an identity provider metadata XML file for proprietary attributes.
Example 3–2 Identity Provider Proprietary Metadata XML File for amadmin
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE Requests PUBLIC "-//iPlanet//Sun Java System Access Manager 2005Q4 Admin CLI
DTD//EN" "jar://com/iplanet/am/admin/cli/amAdmin.dtd">
<Requests>
<OrganizationRequests DN="dc=companyA,dc=com">
<CreateHostedProvider id="http://sp.companyA.com" role="SP"
defaultUrlPrefix="http://sp.companyA.com:80">
<AttributeValuePair>
<Attribute name="iplanet-am-provider-name"/>
<Value>sp</Value>
</AttributeValuePair>
<AttributeValuePair>
<Attribute name="iplanet-am-provider-alias"/>
<Value>sp.companyA.com</Value>
</AttributeValuePair>
<AttributeValuePair>
<Attribute name="iplanet-am-list-of-authenticationdomains"/>
<Value>samplecot</Value>
</AttributeValuePair>
<AttributeValuePair>
<Attribute name="iplanet-am-certificate-alias"/>
<Value>cert_alias</Value>
</AttributeValuePair>
<AttributeValuePair>
<Attribute name="iplanet-am-trusted-providers"/>
<Value>http://idp.companyB.com</Value>
<Value>http://idp.companyC.com</Value>
</AttributeValuePair>
<SPAuthContextInfo AuthContext="Password" AuthLevel="1"/>
<AttributeValuePair>
<Attribute name="iplanet-am-provider-homepage-url"/>
<Value>http://sp.companyA.com:80/idff/index.jsp</Value>
</AttributeValuePair>
</CreateHostedProvider>
</OrganizationRequests>
</Requests>
|
Authentication Domains
An authentication domain is a federation of any number of service providers (and at least one identity provider) with whom principals can transact business in a secure and apparently seamless environment. (The members of the domain must have previously established a circle of trust based on the Liberty Alliance Project architecture and operational agreements.)
Note –
An authentication domain is not a domain in the domain name system (DNS) sense of the word.
The following procedures describe how to create, configure, and delete authentication domains using the Access Manager Console.
 To Create An Authentication Domain
To Create An Authentication Domain
-
In the Access Manager Console, click the Federation tab.
-
Under Federation, select the Authentication Domains tab.
-
Select New.
The New Authentication Domain attributes are displayed.
-
Type a name for the authentication domain.
-
(Optional) Type a description of the authentication domain in the Description field.
-
(Optional) Type a value for the Writer Service URL.
The Writer Service URL specifies the location of the service that writes the common domain cookie. Use the format http://common-domain-host:port/common/writer. For more information about the Common Domain Services, see Chapter 4, Common Domain Services for Federation Management.
-
(Optional) Type a value for the Reader Service URL.
The Reader Service URL specifies the location of the service that reads the common domain cookie. Use the format http://common-domain-host:port/common/transfer. For more information about the Common Domain Services, see Chapter 4, Common Domain Services for Federation Management.
-
Select Active or Inactive.
The default status is Active. Selecting Inactive disables communication within the authentication domain.
-
Click OK.
The new authentication domain is now displayed in the list of configured Authentication Domains.
 To Configure or Modify an Authentication Domain
To Configure or Modify an Authentication Domain
-
In the Access Manager Console, click the Federation tab.
-
Under Federation, select the Authentication Domains tab.
All created Authentication Domains are displayed.
-
Click the name of the authentication domain that you want to modify.
The General and Providers properties for the authentication domain are displayed.
-
(Optional) Enter or modify a description of the authentication domain in the Description field.
-
(Optional) Enter or modify the value for the Writer Service URL.
The Writer Service URL specifies the location of the service that writes the common domain cookie. Use the format http://common-domain-host:port/common/writer. For more information on the Common Domain Services, see Chapter 4, Common Domain Services for Federation Management.
-
(Optional) Enter or modify the value for the Reader Service URL.
The Reader Service URL specifies the location of the service that reads the common domain cookie. Use the format http://common-domain-host:port/common/transfer. For more information on the Common Domain Services, see Chapter 4, Common Domain Services for Federation Management.
-
Select Active or Inactive.
The default status is Active. Selecting Inactive disables communication within the authentication domain.
-
Click Add to populate the authentication domain with providers.
The Trusted Providers page is displayed.
-
Choose from the list of Available Providers and click Add.
-
Click OK to save the providers to the authentication domain.
The authentication domain's attribute page is displayed.
-
Click Save to complete the configuration.
 To Delete an Authentication Domain
To Delete an Authentication Domain
Deleting an authentication domain does not delete the providers that belong to it although it will impact the trusted relationship.
-
In the Access Manager Console, click the Federation tab.
-
Under Federation, select the Authentication Domains tab.
All created Authentication Domains are displayed.
-
Select the check box next to the authentication domain that you want to delete.
-
Click Delete.
The Pre-login URL
The pre-login process is the entry point for applications participating in Liberty-based single sign-on. As described in Process of Federation, the principal would be redirected to the location defined by the pre-login URL if no Access Manager session token is found. This default process, though, can be modified based on the values of query parameters passed to Access Manager by the service provider via a URL.
A query parameter is a name/value pair appended to the end of a URL. The parameter starts with a question mark (?) and takes the form name=value. A number of parameters can be combined in one URL; when more than one parameter exists, they are separated by an ampersand (&). Use the format http://hostname:port/deploy-uri/preLogin?metaAlias=metaAlias. Additional parameters are appended to the URL as ¶m1=value1¶m2=value2 and so on. These parameters and their usage and values are described in the following table.
Table 3–1 Pre-login URL Parameters for Federation|
Parameter |
Description |
|---|---|
|
actionOnNoFedCookie |
The actionOnNoFedCookie parameter provides the flexibility to redirect a user when the fedCookie is not present in the browser, and when there is only one identity provider. It takes the following values:
|
|
anonymousOnetime |
The anonymousOnetime parameter can be used by service providers that authenticate users with anonymous, one time federation sessions. A value of true enables the service provider to issue a one time federation request and generate an anonymous session after successful verification of the authentication assertion from the identity provider. This feature is useful when the service provider doesn't have a user repository (for example, http://www.weather.com) but would like to depend on an identity provider for authentication. When the service provider receives a successful authentication assertion from an identity provider, they would generate an anonymous, temporary session. |
|
authlevel |
The authlevel parameter takes as a value a positive number that maps to an authentication level defined in the Access Manager Authentication Framework. The authentication level indicates how much to trust a method of authentication. Note – More information on the authentication framework can be found in Sun Java System Access Manager 7.1 Administration Guide. In this framework, each service provider is configured with a default authentication context (preferred method of authentication). However, the provider might like to change the assigned authentication context to one that is based on the defined authentication level. For example, provider B would like to generate a local session with an authentication level of 3 so it requests the identity provider to authenticate the user with an authentication context assigned that level. The value of this query parameter determines the authentication context to be used by the identity provider. |
|
goto |
The goto parameter takes as a value a URL to which the principal will be redirected after a successful SSO. If the value is not specified, default redirection will occur based on the value of the Provider Home Page URL attribute defined in the service provider configuration. The value of this URL can be configured by changing the iplanet-am-provider-homepage-url attribute in the amProviderConfig.xml file. |
|
gotoOnFedCookieNo |
The gotoOnFedCookieNo parameter takes as a value a URL to which the principal is redirected if a fedCookie with a value of no is found. The default behavior is to redirect the user to the Access Manager login page. |
In order to modify the pre-login URL, edit the relevant properties in either the AMConfig.properties file or the AMAgent.properties file, dependant on your deployment. See the following procedures for more information:
 To Configure for Pre-login
To Configure for Pre-login
In a federation setup, Access Manager acts as a service provider and manages an application that runs on a separate instance of Sun Java System Web Server. You must configure the agent that is protecting this application as follows:
-
Point the com.sun.am.policy.loginURL property in the AMAgent.properties file to the pre-login service URL running on Access Manager.
For example: com.sun.am.policy.loginURL = http://www.sp1.com:58080/amserver/preLogin?metaAlias=www.sp1.com
-
Point the com.sun.am.policy.am.library.loginURL in the AMAgent.properties file to the login URL of the instance of Access Manager acting as the service provider.
For example: com.sun.am.policy.am.library.loginURL = http://www.sp1.com:58080/amserver/UI/Login
 To Configure for Global Logout
To Configure for Global Logout
To implement the logout process for all service providers using the Liberty Logout method, do the following:
-
Copy the AMClient.properties file to the service provider's web container.
-
Revise the Logout method, as follows:
ResourceBundle rsbu =ResourceBundle.getBundle("AMClient"); String logouturl = rsbu.getString ("com.sun.identity.federation.client.samples.logoutURL"); response.sendRedirect(logouturl);
This revision is equivalent to a redirection to http://www.sp1.com:58080/amserver/liberty-logout?metaAlias=www.sp1.com.
Federation API
The following packages form the Federation API.
com.sun.identity.federation.plugins
The com.sun.identity.federation.plugins package contains the FederationSPAdapter interface which can be implemented to allow applications to customize their actions before and after invoking the federation protocols. For example, a service provider may want to choose to redirect to a specific location after single sign-on. For more detailed information, see the Java API Reference in /AccessManager-base/SUNWam/docs or on Sun Java System Access Manager 7.1 Java API Reference.
com.sun.identity.federation.services
The com.sun.identity.federation.services package provides interfaces for writing custom plug-ins that can be used during the federation or single sign-on process. The interfaces are described in the following table. For more detailed information, see the Java API Reference in /AccessManager-base/SUNWam/docs or on Sun Java System Access Manager 7.1 Java API Reference.
Table 3–2 com.sun.identity.federation.services Interfaces|
Interface |
Description |
|---|---|
|
FSAttributeMapper |
Plug-in for mapping the attributes passed from the identity provider to local attributes on the service provider side during the single sign-on. |
|
FSAttributePlugin |
Plug-in for an identity provider to add AttributeStatements into a SAML assertion during the single sign-on process. |
|
FSIDPProxy |
Interface used to find a preferred identity provider to which an authentication request can be proxied. |
com.sun.liberty
The com.sun.liberty package contains the LibertyManager class which must be instantiated by web applications that want to access the Federation component. It also contains the methods needed for account federation, session termination, log in, log out and other actions. Some of these methods are described in the following table. For more detailed information, see the Java API Reference in /AccessManager-base/SUNWam/docs or on Sun Java System Access Manager 7.1 Java API Reference.
Table 3–3 com.sun.liberty Methods|
Method |
Description |
|---|---|
|
getFederatedProviders(String userName) |
Returns a specific user’s federated providers. |
|
getIDPFederationStatus(String user, String provider) |
Retrieves a user’s federation status with a specified identity provider. This method assumes that the user is already federated with the provider. |
|
getIDPList() |
Returns a list of all trusted identity providers. |
|
getIDPList(java.lang.String hostedProviderID) |
Returns a list of all trusted identity providers for the specified hosted provider. |
|
getProvidersToFederate(java.lang.String providerID, java.lang.String userName) |
Returns a list of all trusted identity providers to which the specified user is not already federated. |
|
getSPList() |
Returns a list of all trusted service providers. |
|
getSPList(java.lang.String hostedProviderID) |
Returns a list of all trusted service providers for the specified hosted provider. |
|
getSPFederationStatus(java.lang.String user, java.lang.String provider) |
Retrieves a user’s federation status with a specified service provider. This method assumes that the user is already federated with the provider. |
Liberty ID-FF Operations
This section contains procedures illustrating how to use Access Manager to configure interactions based on the Liberty ID-FF. They are:
Auto-Federation
The auto-federation feature in Access Manager will automatically federate a user's disparate provider accounts based on a common attribute. This common attribute will be exchanged in a single sign-on assertion so that the consuming service provider can identify the user and create account federations. If auto-federation is enabled and it is deemed that a user at provider A and a user at provider B have the same value for the defined common attribute (for example, emailaddress), the two accounts will be federated automatically without principal interaction.
Note –
Auto-federating a principal's two distinct accounts at two different providers requires each provider to have agreed to implement support for this functionality beforehand.
 To Enable Auto Federation
To Enable Auto Federation
Ensure that each local service and identity provider participating in auto federation is configured for it. Remote providers would not be configured in your deployment.
-
In the Access Manager Console, click the Federation tab.
-
Under Federation, select the Entities tab.
-
Select the name of a hosted provider entity to edit its profile.
Whether an entity is configured to hold hosted or remote providers is not information that is disclosed on this screen.
-
Select Identity Provider or Service Provider from the View menu.
-
Select Access Manager Configuration.
-
Enable Auto Federation by checking the box.
-
Type a value for the Auto Federation Common Attribute Name attribute.
For example, enter emailaddress or userID. You should be sure that each participating user profile (at both providers) has a value for this attribute.
-
Click Save to complete the configuration.
Bulk Federation
Access Manager provides a script for federating user accounts in bulk. It is called ambulkfed and is located in /opt/SUNWam/bin. The script assumes that the user database is LDAPv3–compliant.
Note –
The ambulkfed script is the primary script for bulk federation. It uses two other Perl scripts, amGenerateLDIF.pl and amGenerateNI.pl, behind the scenes.
As input, the script takes a file that maps the user distinguished name (DN) of the identity provider to the user DN of the service provider. Each line of the file must place the mappings in the following order and separated by a pipe (”|”): uid=spuser,dc=iplanet,dc=com | uid=idpuser,dc=iplanet,dc=com. The script generates unique random identifiers for each mapping and creates four files:
-
spnameidentifiers.txt
-
idpnameidentifiers.txt
-
spuserdata.ldif
-
idpuserdata.ldif
These files contain the data for bulk federation. The LDIFs are used for instances of Access Manager. ambulkfed generates and loads the LDIF data into Access Manager based on its given provider role. For example, it will load spuserdata.ldif if Access Manager acts as a service provider and it will load idpuserdata.ldif if Access Manager acts as an identity provider. The LDIFs will also be stored locally and can be used with ldapmodify to load the data into a remote instance of Access Manager. If the remote provider is not an instance of Access Manager, the generated text files spnameidentifiers.txt and idpnameidentifiers.txt can be used to generate federation data based on the input needs of the provider.
Configuring Trust Between Providers
In order to complete interactions based on the Liberty ID-FF, trust must exist between all communicating providers. Each provider that wishes to be part of a federated trust model does so after complex business negotiations, the exchange of provider configuration metadata, and the configuration of trust. Using the Access Manager console, trusted providers are configured using the metadata and are then grouped (as entities) into an authentication domain. To accomplish this, you load the provider metadata, and assign the configured providers to the same authentication domain. The following procedure explains how to configure trust using either the command line interface or the Access Manager console. Additional information can be found in Entities and Authentication Domains.
 To Configure Trust Between Service Providers
and Identity Providers
To Configure Trust Between Service Providers
and Identity Providers
Before You Begin
You must have metadata files specific to each provider you are configuring. Access Manager includes sample metadata XML files that you can modify for your purposes. See sample1 Directory for more information.
-
Load the hosted and remote provider metadata XML files to Access Manager using the amadmin command line interface.
See Creating and Configuring Entities using amadmin for information.
-
Login to the Access Manager console as amadmin, the default administrator.
-
Under Federation, click the Authentication Domains tab.
-
Select New.
The new Authentication Domain attributes are displayed.
-
Create the authentication domain and click OK.
See To Create An Authentication Domain for information.
-
Under Federation, click the Entities tab.
-
Select the name of a provider.
The provider was created when the metadata was loaded. The General attributes for the chosen provider are displayed.
-
Select the appropriate provider type from the View pull down menu.
-
Scroll down to Authentication Domains, select the authentication domain just created and click Add.
The authentication domain will be moved under Selected.
-
Click Save to store the change.
Repeat this configuration for all providers (remote and hosted) with which you want to establish trust.
-
Under Federation, click the Authentication Domains tab.
-
Select the name of the authentication domain which was previously created.
The General attributes are displayed.
-
Under Providers, click Add.
The Select Trusted Partner Type and Profile page is displayed.
-
Select the appropriate provider(s) as trusted members of the authentication domain and click Add.
The provider(s) will be moved under Selected.
-
Click OK to save the change.
-
Click Save to store the change.
Trust is now established between the appropriate providers.
Signing Liberty ID-FF Requests and Responses
Federation-based communications passing between identity providers and service providers are generally required to be digitally signed and verified. Signing and verifying messages provides data integrity, data origin authentication, and a basis for non-repudiation. To turn on signing for all Liberty ID-FF requests and responses emanating from your instance of Access Manager, set the value of the com.sun.identity.federation.services.signingOn property in AMConfig.properties to true and restart Access Manager and its web container. This allows for signing of Liberty ID-FF requests being sent and verification of signature validity for Liberty ID-FF responses received. If set to false, signing is disabled. If set to optional, requests and responses will be signed or verified only if required by the federation profile being used. After installation, AMConfig.properties is located in the etc/opt/SUNWam/config directory.
Note –
More information on com.sun.identity.federation.services.signingOn and the other identity federation properties in AMConfig.properties can be found in the Chapter 6, amConfig.properties Reference, in Sun Java System Access Manager 7.1 Administration Reference.
Additionally, you can enable the signing of an authentication request from a service provider configured on your instance of Access Manager, use the following procedure.
 To Enable Signing of Service Provider Authentication
Requests
To Enable Signing of Service Provider Authentication
Requests
Before You Begin
A keystore must be set up before turning on the signing properties. See Appendix B, Key Management information on how to do this.
-
Log in to the Access Manager console as the top-level administrator, by default, amadmin.
-
Select the Federation tab.
-
Select the Entities tab.
-
Select the name of the entity that contains the service provider configuration for which you want to enable the signing of an authentication request.
-
Select Service Provider from the View pull-down menu.
-
Enable the Sign Authentication Request property under the Service Provider configuration and click Save.
-
Log out of the Access Manager console.
Dynamic Identity Provider Proxying
An identity provider that is asked to authenticate a principal that has already been authenticated with another identity provider may proxy the authentication request, on behalf of the requesting service provider, to the authenticating identity provider. This is called dynamic identity provider proxying. When the first identity provider receives an authentication request regarding a principal, it prepares a new authentication assertion on its own behalf by referencing the relevant information from the original assertion and sending the assertion to the authenticating identity provider.
Note –
The service provider requesting authentication may control this proxy behavior by setting a list of preferred identity providers or by defining the amount of times the identity provider can proxy the request.
 To Configure and Test Dynamic Identity Provider
Proxying
To Configure and Test Dynamic Identity Provider
Proxying
The following steps describe the procedure to enable three machines for identity provider proxying and test the configuration. The procedure assumes the three machines have Access Manager installed and are configured as follows:
|
Machine |
Authentication Function |
Federation Function |
|---|---|---|
|
Machine 1 |
Authenticating Identity Provider |
Identity Provider |
|
Machine 2 |
Proxying Identity Provider |
Identity Provider and Service Provider |
|
Machine 3 |
Requesting Service Provider |
Service Provider |
All of the WAR files and metadata used in the following procedure can be found in /AccessManager-base/samples/liberty/sample1.
-
To configure machine 3, deploy the SP1 WAR files and load sp1Metadata.xml.
Ensure that the metadata defines machine 2 as an identity provider and machine 3 as a service provider.
-
To configure machine 1, deploy the IDP1 WAR files and load idp1Metadata.xml.
Ensure that the metadata defines machine 1 as an identity provider and machine 2 as a service provider.
-
To configure machine 2, do the following:
-
To configure machine 2 as a service provider, deploy the SP1 WAR files.
Modify AMClient.properties to reflect this.
-
To configure machine 2 as an identity provider, load a second, modified idp1Metadata.xml.
Ensure that idp1Metadata.xml contains only data that defines machine 1 as an identity provider. Remove all other metadata.
-
-
Log in to machine 2 and modify the following metadata:
-
Change the value of the Authentication Type attribute to Local.
This attribute can be found in the Access Manager Configuration section of the entity describing machine 2 as a service provider.
-
Add machine 1 and machine 3 to the list of Trusted Providers configured for machine 2.
This attribute can be found in the Trusted Provider section of the entity describing machine 2 as a service provider.
-
Save the configuration.
-
-
Also on machine 2, modify the following metadata regarding machine 3.
-
Select the check box next to Enable Proxy Authentication.
This attribute can be found in the Proxy Authentication Configuration section of the entity that defines machine 3 as an identity provider.
-
Add machine 1 to the list of Proxy Identity Providers List.
This attribute can be found in the Proxy Authentication Configuration section of the entity that defines machine 3 as an identity provider. The value is a URI defined as the provider's identifier.
-
Set Maximum Number of Proxies to 1.
-
Save the configuration.
-
-
Federate a user between machine 3 (acting as a service provider) and machine 2 (acting as an identity provider).
-
Federate a user between machine 2 (acting as a service provider) and machine 1 (acting as an identity provider).
-
Close the browser and attempt single sign-on.
You will be redirected to machine 1 rather than machine 2 if you enter the username and password used to federate with machine 1.
Sample Federation Environment
Access Manager provides a collection of samples based on the Liberty Alliance Project specifications. They are located in the /AccessManager-base/SUNWam/samples/liberty/ directory. Appendix A, Liberty-based and SAML Samples includes information about these samples.
Sample 1, located in /AccessManager-base/SUNWam/samples/liberty/Sample1, can be used to configure an environment for creating and managing a federation. The sample demonstrates the basic use of various Liberty-based federation protocols including account federation, single sign-on, single logout, and federation termination. Completing the procedures in the sample Readme.txt or Readme.html will help to give you a more complete understanding of how federation works.
Note –
The Readme file also contains instructions for configuring a common domain. For information about common domains, see Chapter 4, Common Domain Services for Federation Management.
- © 2010, Oracle Corporation and/or its affiliates
