| C H A P T E R 7 |
|
Configuring VLANs |
This chapter describes how to configure virtual local area networks (VLANs).
This chapter contains the following sections:
With multiple VLANs on a card, a server with a single card can have a logical presence on multiple IP subnets. By default, 128 VLANs can be defined for each VLAN-aware card on your server. However, this number can be increased by changing the system parameters.
If your network does not require multiple VLANs, you can use the default configuration, in which case no further configuration is necessary.
VLANs enable you to split your physical LAN into logical subparts, providing an essential tool for increasing the efficiency and flexibility of your network.
VLANs are commonly used to separate groups of network users into manageable broadcast domains, to create logical segmentation of workgroups, and to enforce security policies among each logical segment. Each defined VLAN behaves as its own separate network, with its traffic and broadcasts isolated from the others, increasing the bandwidth efficiency within each logical group.
Although VLANs are commonly used to create individual broadcast domains or separate IP subnets, it can be useful for a server to have a presence on more than one VLAN simultaneously. Several Sun products support multiple VLANs on a per-port or per-interface basis, allowing very flexible network configurations.
FIGURE 7-1 shows an example network that uses VLANs.
FIGURE 7-1 Example of Servers Supporting Multiple VLANs With Tagging Adapters
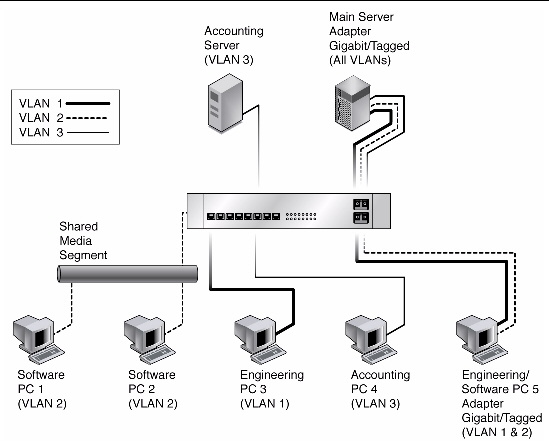
The example network has the following features:
The physical LAN network consists of a switch, two servers, and five clients. The LAN is logically organized into three different VLANs, each representing a different IP subnet.
The Main Server is a high-use server that needs to be accessed from all VLANs and IP subnets. The server has a Sun 10GbE XFP SR PCI Express Card installed. All three IP subnets are accessed by means of the single physical Ethernet adapter interface. The server is attached to one of the switch’s Gigabit Ethernet ports, which is configured for VLANs 1, 2, and 3. Both the Ethernet adapter and the connected switch port have tagging turned on. Because of the tagging VLAN capabilities of both devices, the server is able to communicate on all three IP subnets in this network, but continues to maintain broadcast separation between all of those subnets. The following list describes the components of this network:
VLAN tagging is only required to be enabled on switch ports that create trunk links to other VLAN-aware Ethernet switches, or on ports connected to tag-capable end-stations, such as servers or workstations with VLAN-aware Ethernet adapters.
VLANs can be created according to various criteria, but each VLAN must be assigned a VLAN tag or VLAN ID (VID). The VID is a 12-bit identifier between 1 and 4094 that identifies a unique VLAN. For each network interface (ixgbe0, ixgbe1, ixgbe2, and so on), 4094 possible VLAN IDs can be selected for each port.
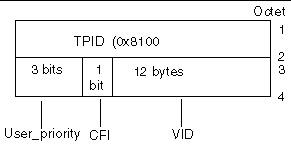
Tagging an Ethernet frame requires the addition of a tag header to the frame. The header is inserted immediately following the destination MAC address and the source MAC address. The tag header consists of two bytes of Ethernet Tag Protocol identifier (TPID, 0x8100) and two bytes of tag control information (TCI). FIGURE 7-2 shows the Ethernet tag header format.
FIGURE 7-2 Ethernet Tag Header Format
By default, a single VLAN is configured for every port, which groups all ports into the same broadcast domain, just as if there were no VLANs at all. This means that VLAN tagging for the switch port is turned off.
| Note - If you configure a VLAN virtual device for an Ethernet adapter, all traffic sent or received by that Ethernet adapter must be in VLAN-tagged format. |
|
1. Create one /etc/hostname.ixgbe# file for each VLAN that will be configured for each adapter on the server.
Use the following naming format, which includes both the VID and the physical point of attachment (PPA):
VLAN logical PPA = 1000 * VID + Device PPA
123000 = 1000*123 + 0
So the VLAN interface will be ixgbe123000.
This format limits the maximum number of PPAs (instances) you can configure to 1000 in the /etc/path_to_inst file.
For example, if the virtual ID is 123 and physical adapter is instance 2:
VLAN logical PPA = 1000 * VID + [Device PPA]
123002 = 123000 + 2
So the VLAN interface is ixgbe123002. This format limits the maximum number of PPAs (instances) that can be configured in the /etc/path_to_inst file to 1000 .
For example, on a server with the Sun PCI Express card having an instance of 2, belonging to a member of two VLANs, with VID 123 and 224, you would use ixgbe123002 and ixgbe224002, respectively, as the two VLAN PPAs.
2. Use the ifconfig command to configure each VLAN virtual device.
Include the IP address in the command you type. For example, if the IP address is 192.2.2.84, type:
3. Type the ifconfig -a command to see details about the VLAN devices.
This example shows the output of ifconfig -a on a system having VLAN devices ixgbe123002 and ixgbe224002:
Refer to the documentation that came with your switch for specific instructions for setting VLAN tagging and ports.
|
1. Ensure that the ixgbe module is loaded:
2. Plumb the Sun 10GbE XFP SR PCI Express Card interface:
where xxx.xxx.xx.xxx = the IP address of the interface.
3. Add the VLAN instance (VID).
where eth6 is the interface and 5 is the VID.
| Note - In Linux systems, you can use any single digit as the VID. |
4. Configure the ixgbe VLAN (eth2 in this example):
where xxx.xxx.xx.xxx = the IP address of the interface.
|
3. Click the folder icon from the sub-manual bar.
4. Right-click the Sun 10GbE XFP SR PCI Express Card port, then select Properties.
6. Click VLAN, then click on New.
7. Type VLAN with ID (for example, type Vlan10).
8. Click Internet Protocol (TCP/IP).
9. Click Use the following IP address.
The value 255.255.255.0 is displayed.
13. Repeat Step 3 through Step 10 until all the network ports are VLAN configured.
| Note - Ensure that the firewall is configured to allow VLAN traffic. Otherwise, the VLAN might not operate properly. |
|
1. Use the modprobe command to configure the mode:
2. Use the ifconfig command to create the bond:
In this command bond0 is the bonding device.
3. Configure the bondn interfaces.
In this example, two bonds (bond0 and bond1) are configured:
Refer to Linux documentation for more information.
|
 Use the rmmod command to remove bonding:
Use the rmmod command to remove bonding:
Copyright © 2010, Oracle and/or its affiliates. All rights reserved.