Chapter 2 About the OpenSSO Add-On
Based on the open sourceOpenSSO project and the Sun OpenSSO Enterprise (formerly known as Federated Access Manager) product, the OpenSSO Add-On provides enterprise-grade single sign-on and authentication features for Web Space Server portals and portlets.
The Add-On also provides convenience features for mapping OpenSSO and Access Manager users, roles, filtered roles, groups, and realms to Web Space Server users, communities, and organizations. This makes the Add-On particularly useful for migrating existing OpenSSO or Access Manager—based Portal Server user, role, group, and realm configurations to corresponding Web Space Server configurations.
Note –
Most of the concepts and features of the OpenSSO Add-On apply equally to OpenSSO and Access Manager authentication servers. Throughout this document, except where noted, the term OpenSSO can be used interchangeably with the term Access Manager.
Who Should Use the OpenSSO Add-On?
The Web Space Server OpenSSO Add-On is intended for developers who want to implement single sign-on and authentication features in their portals and portlets in general.
In addition, the OpenSSO Add-On is useful for developers and administrators who are migrating from Portal Server to Web Space Server. In this regard, the OpenSSO Add-On is particularly useful in three scenarios:
-
When upgrading a Sun Java System Portal Server 7.x installation to Web Space Server 10.0, the OpenSSO Add-On enables the mapping of user role-based content assignments in Portal Server to analogous community-based content assignments in Web Space Server 10.0.
-
For developers and administrators familiar with Portal Server software, the OpenSSO Add-On enables you to define role-based content privileges in Web Space Server, similar to the functionality provided in Portal Server.
-
When migrating an existing Portal Server user base to Web Space Server, the OpenSSO Add-On makes it possible to perform bulk imports of Portal Server user accounts into Web Space Server.
How Does the OpenSSO Add-On Work?
The OpenSSO Add-On enables the exchange of user authentication data between a Web Space Server site and an OpenSSO server. From the standpoint of a Web Space Server administrator, the OpenSSO Add-On provides a Community Mapper portlet, which is GUI-based administration tool for associating OpenSSO users, roles, filtered roles, groups, and realms with Web Space Server users, communities, and organizations.
Figure 2–1 OpenSSO Add-On Overview
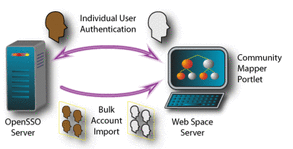
There are two general scenarios through which account information is mapped from an OpenSSO server and a Web Space Server:
-
When an individual user initiates a login to a Web Space Server account
-
When a Web Space Server site administrator performs a bulk import of OpenSSO accounts, often as part of a migration from Portal Server to Web Space Server
These two scenarios are described in more detail below.
Individual User Login Scenario
When an individual user connects to a Web Space Server site:
-
The attempt to connect to the Web Space Server site is redirected to the OpenSSO server for authentication.
-
If access to public pages on the Web Space Server site is allowed, then the public pages are displayed without further authentication.
-
If an attempt is made to access any Web Space Server private pages, or if the user initiates a login request by clicking the Sign In link on the Web Space Server page, the user is redirected to an OpenSSO login page.
-
-
After successful OpenSSO login, the user is redirected back to the Web Space Server page.
-
If a Web Space Server account corresponding to the account used to log in through the OpenSSO server already exists, the user is logged in to Web Space Server and is redirected to his or her home page.
-
If a corresponding Web Space Server account does not exist, a new Web Space Server account is created.
-
If the user belongs to an OpenSSO realm that is mapped to a Web Space Server organization, then his or her account is assigned to that mapped organization.
-
If the user has an OpenSSO membership (role, filtered role, or group) that is mapped to a Web Space Server community, then the user added to the mapped community, and Web Space Server content available to that community is displayed.
-
If the user's OpenSSO membership has been subsequently removed, then the user is also removed from the mapped community.
-
-
-
Once a user has been authenticated through OpenSSO, he or she is also signed on with all applications that use those OpenSSO credentials.
-
Logging out of Web Space Server or any other application that uses OpenSSO causes the user to be logged out of Web Space Server, OpenSSO, and any other application that uses those OpenSSO credentials.
Bulk User Import Scenario
In this scenario, typically performed by a Web Space Server site administrator as part of a migration from Portal Server to Web Space Server, an existing set of OpenSSO user accounts is imported in a single step. Instructions for performing a bulk user import are provided later in this guide, in Performing Bulk Imports of OpenSSO User Accounts.
Note –
Bulk import only imports basic OpenSSO user account credentials, and does not map memberships to communities or organizations.
Default Mapping Tables
This section provides reference tables that list the default mappings used by the OpenSSO Add-On. In most cases, you will not need to refer to these tables because the Community Mapper Portlet provided by the OpenSSO Add-On uses these mappings in mostly automatic ways.
Primary Entity Mappings
Table 2–1 lists the primary entity mappings between OpenSSO and Web Space Server.
Table 2–1 Entity Mappings Between OpenSSO (SSO) and Web Space Server (WSS)|
SSO Entity |
WSS Entity |
Comments |
|---|---|---|
|
Realm |
Org |
Org is the “Regular” type of org in Web Space Server. Users inherit permissions/roles from the Organization and Location to which they belong. |
|
User |
User |
|
|
(Static) Role |
Community |
Map to a private community. Users can belong to any number of Communities and inherit permissions/roles from them. |
|
Filtered Role |
Community |
Map to a private community. |
|
Group |
Community |
Map to a private community. |
|
N/A |
Locations |
This is another type of org in Web Space Server. An Organization to which a User belongs must be the parent of the Location to which that User belongs. |
|
N/A |
User Groups |
User Groups are arbitrary collections of Users. Users can belong to any number of User Groups, and can inherit permissions/roles from User Groups. This is a grouping of users that can be used for bulk operations in Web Space Server. |
|
N/A |
Role |
Roles in Web Space Server are containers for permissions. |
Default User Attribute Mappings
Table 2–2 lists the user attribute mappings use to import OpenSSO (SSO) user accounts into Web Space Server (WSS). These default mappings can be changed prior to installing the OpenSSO Add-On by modifying the portal-ext.properties file, located in the webspace_dir/webspace/opensso/templates/ directory.
Table 2–2 Default User Attribute Mappings|
WSS Attribute |
SSO Attribute |
|---|---|
|
firstName |
cn |
|
lastName |
sn |
|
screenName |
givenName |
|
emailAddress |
|
Default Configuration Files
This section lists the properties and default values in the portal-ext.properties and AMConfig.properties files, which are the primary configuration files for the OpenSSO Add-On. All customization of the OpenSSO Add-On is performed through these two files. You may find it useful to refer to the tables in this section as you configure the OpenSSO for your particular Web Space Server site.
As described in Installing the OpenSSO Add-On, there are several site-specific modifications you must make to the portal-ext.properties and AMConfig.properties files before installing the OpenSSO Add-On. In addition, these are also the files you will need to modify if you want to make any post-installation customizations to the OpenSSO Add-On. Note that any customizations made to these files after the OpenSSO Add-On has been installed require that you also rebuild the Web Space Server WAR files, as described in Customizing the OpenSSO Add-On.
Locations of the portal-ext.properties and AMConfig.properties Files
The location of the portal-ext.properties and AMConfig.properties files that you should modify varies depending on whether you are performing the modifications before or after the OpenSSO Add-On has been installed.
-
Before installing the OpenSSO Add-On
Before installation of the OpenSSO Add-On, the portal-ext.properties and AMConfig.properties files you need to modify are located in the glassfish_dir/webspace/opensso/templates directory.
When you first download the OpenSSO Add-On, there are two sample versions of these two files, named portal-ext.properties.template and AMConfig.properties.template. It is strongly recommended that you make copies of these template files and then only make modifications to the copies. After modifying the copies, make sure that the copies are named portal-ext.properties and AMConfig.properties (no .template extension) before proceeding with the OpenSSO Add-On installation.
-
After installing the OpenSSO Add-On
After the OpenSSO Add-On has been installed, any additional customizations you want to make must only be made to the portal-ext.properties and AMConfig.properties files that are located in the webspace_dir/var/webspace/war-workspace/customs/webspace/WEB-INF/classes directory.
portal-ext.properties Properties File
Listed below are the properties and default values in the portal-ext.properties file.
-
access.manager.auth.enabled
Default: true
Enable the OpenSSO Add-On
-
access.manager.sync.enabled
Default: true
Enable automatic synchronization of users from OpenSSO to Web Space Server
-
access.manager.import.enabled
Default: true
Enable the automatic import of the OpenSSO user account if the corresponding account does not already exist in Web Space Server
-
access.manager.allow.public.pages
Default: true
Allow access to Web Space Server public pages with first being redirected to OpenSSO server for user authentication
-
access.manager.email.attr
Default: mail
Web Space Server user email property corresponding to OpenSSO email property
-
access.manager.first.name.attr
Default: givenName
Web Space Server user first name property corresponding to OpenSSO first name property
-
access.manager.last.name.attr
Default: sn
Web Space Server user last name property corresponding to OpenSSO last name property
-
access.manager.screen.name.attr
Default: uid
Web Space Server user ID property corresponding to OpenSSO user ID property
-
access.manager.login.url
Default: http://localhost:8080/opensso/UI/Login?goto=http://localhost:8080/c/portal/login
URL for OpenSSO authentication login redirect; use only when authenticating through OpenSSO; enabled by default
-
access.manager.logout.url
Default: http://localhost:8080/opensso/UI/Logout?goto=http://localhost:8080/portal
URL for OpenSSO authentication logout redirect; use only when authenticating through OpenSSO; enabled by default
-
access.manager.login.url
Default: http://localhost:8080/amserver/UI/Login?goto=http://localhost:8080/c/portal/login
URL for Access Manger authentication login redirect; use only when authenticating through Access Manager; disabled by default
-
access.manager.logout.url
Default: http://localhost:8080/amserver/UI/Logout?goto=http://localhost:8080/portal
URL for Access Manager authentication logout redirect; use only when authenticating through Access Manager; disabled by default
-
auto.login.hooks
Default: com.sun.portal.security.auth.AccessManagerAutoLogin, com.liferay.portal.security.auth.CASAutoLogin, com.liferay.portal.security.auth.NtlmAutoLogin, com.liferay.portal.security.auth.OpenIdAutoLogin, com.liferay.portal.security.auth.OpenSSOAutoLogin, com.liferay.portal.security.auth.ParameterAutoLogin, com.liferay.portal.security.auth.RememberMeAutoLogin
Classes required to enable OpenSSO autologin features; you should not need to modify these properties
-
application.startup.events
Default: com.sun.portal.opensso.startup.OpenssoAddonStartupAction
Parameter passed to the Sun GlassFish Enterprise Server to start the OpenSSO Add-On
AMConfig.properties Properties File
Listed below are the properties and default values in the AMConfig.properties file.
-
com.iplanet.am.cookie.encode
Default: true
Allows authentication server to URLencode the cookie value, converting characters to ones that are understandable by HTTP
-
com.iplanet.am.cookie.name
Default: iPlanetDirectoryPro
Name of the persistent cookie
-
com.iplanet.am.cookie.secure
Default: false
Set secure mode in which browser will only return the cookie when a secure protocol like HTTP(s) is used
-
com.iplanet.am.naming.url
Default: http://localhost:8080/opensso/namingservice
URI for the authentication server naming service; use with OpenSSO
-
com.iplanet.am.notification.url
Default: http://localhost:8080/opensso/notificationservice
URI of the authentication server notification service; allows authentication server to send notifications to registered applications when an event has occurred, and enables single sign-on cache to stay up to date; use with OpenSSO
-
com.iplanet.am.naming.url
Default: http://localhost:8080/amserver/namingservice
URI for the authentication server naming service; use with Access Manager; disabled by default
-
com.iplanet.am.notification.url
Default: http://localhost:8080/amserver/notificationservice
URI of the authentication server notification service; use with Access Manager; disabled by default
-
com.iplanet.am.service.password
Default: anonymous
Specifies the password of the user with permission to read OpenSSO Enterprise configuration data.
-
com.iplanet.security.encryptor
Default: com.iplanet.services.util.JCEEncryption
Specifies the encrypting class implementation; available classes are com.iplanet.services.util.JCEEncryption and com.iplanet.services.util.JSSEncryption
-
com.iplanet.services.debug.directory
Default: /var/opt/sun/identity/debug
Directory in which debug messages are stored
-
com.iplanet.services.debug.level
Default: error
Severity of debug messages recorded in server log; possible values are: off | error | warning | message
-
com.sun.identity.agents.app.username
Default: anonymous
Defines a user with permission to read the OpenSSO Enterprise configuration data
- © 2010, Oracle Corporation and/or its affiliates
