Using the auditreduce Command
Use auditreduce to merge audit records from one or more input audit files or to perform a post selection of audit records. See the auditreduce(1M) man page. To merge the entire audit trail, the system administrator enters the command on the machine on which all the audit file systems for the distributed system are mounted.
When multiple machines running BSM are administered as part of a distributed system, each machine performs auditable events, and each machine writes audit records to its own machine-specific audit file. This procedure simplifies software and is robust in the face of machine failures. However, without auditreduce, you would have to look at every one of the files to determine what a particular user did because each machine produces its own set of audit files.
The auditreduce command makes the job of maintaining the whole audit trail practical. Using auditreduce (or shell scripts you write yourself to provide a higher-level interface), you can read the logical combination of all audit files in the system as a single audit trail without regard to how the records were generated or where they are stored.
The auditreduce program operates on the audit records produced by the audit daemon. Records from one or more audit files are selected and merged into a single, chronologically ordered output file. The merging and selecting functions of auditreduce are logically independent. auditreduce selects messages from the input files as the records are read, before the files are merged and written to disk.
Without options, auditreduce merges the entire audit trail (which consists of all of the audit files in all of the subdirectories in the audit root directory /etc/security/audit) and sends all the audit records to standard output. Making the records human-readable is done by the praudit command.
Following are some of the actions performed by some of the options to the auditreduce command.
-
You can request that the output contain audit records generated by only certain audit flags.
-
You can request audit records generated by one particular user.
-
You can request audit records generated on specific dates.
With no arguments, auditreduce looks in all subdirectories below /etc/security/audit, the default audit root directory, for a files directory in which the date.date.hostname files reside. The auditreduce command is very useful when the audit data for different hosts (Figure 2-1) or for different audit servers (Figure 2-2) reside in separate directories.
Figure 2-1 Audit Trail Separated by Host
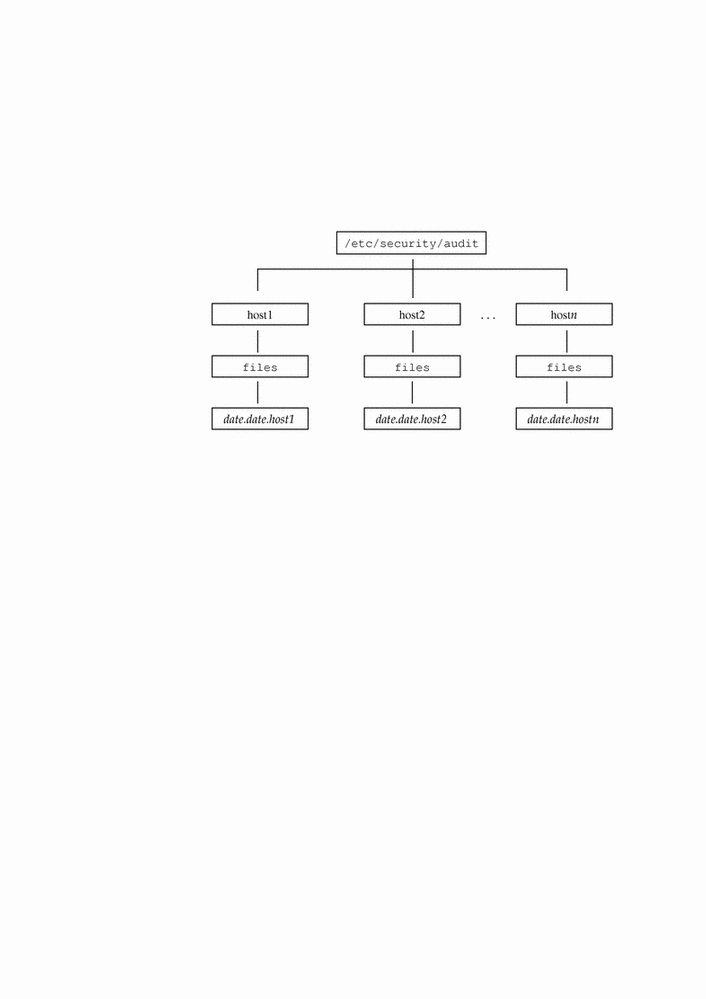
The audit data cannot be in the default directory -- perhaps because the partition for /etc/security/audit is very small or because you want to store audit data on another partition without symbolically linking that partition to /etc/security/audit. You can give auditreduce another directory (-R) to substitute for /etc/security/audit, or you can specify one particular subdirectory (-S):
# auditreduce -R /var/audit-alt # auditreduce -S /var/audit-alt/host1 |
Figure 2-2 Audit Trail Separated by Server
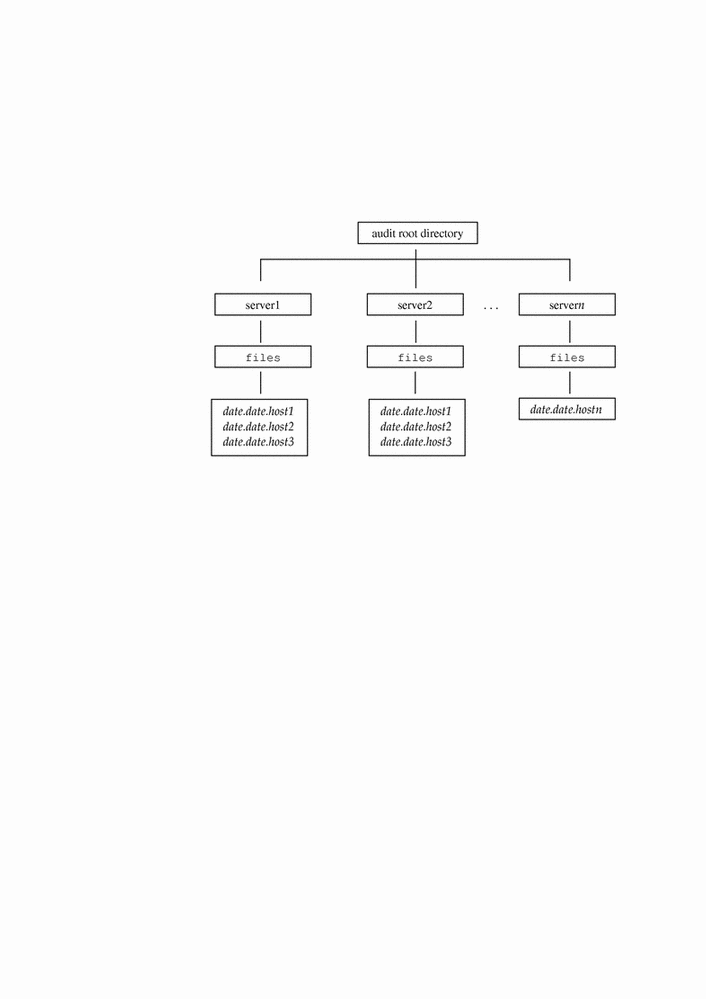
You can direct auditreduce to treat only certain files by specifying them as command arguments:
# auditreduce /var/audit/bongos/files/1993*.1993*.bongos |
The auditreduce(1M) man page for auditreduce lists other options and provides additional examples for using the command.
- © 2010, Oracle Corporation and/or its affiliates
