Chapter 1 Introduction to Deployment Planning for Access Manager
Sun JavaTM System Access Manager (Access Manager) is part of the Sun Identity Management infrastructure that allows an organization to manage secure access to Web applications and other resources both within an enterprise and across business-to-business (B2B) value chains. This chapter introduces the basic Access Manager deployment planning principles, including:
About Access Manager
Access Manager is a component of Sun JavaTM Enterprise System (Java ES), a set of software components that provide services that support enterprise applications distributed across a network or Internet environment. Access Manager provides these major functions:
-
Centralized authentication and authorization services using both role-based and rule-based access control
-
Single sign-on (SSO) for access to an organization’s Web-based applications
-
Federated identity support with the Liberty Alliance Project and Security Assertions Markup Language (SAML)
-
Logging of critical information including administrator and user activities by Access Manager components for subsequent analysis, reporting, and auditing. Logging is based on the J2SE logging APIs (java.util.logging).
Access Manager is also part of the Sun Identity Management Suite, which provides the functions required to use, share, and manage identity information, including directory services, access management, provisioning, and federation. The products in the Identity Management Suite include:
-
Sun Java System Access Manager
-
Sun Java System Directory Server Enterprise Edition
-
Sun Java System Federation Manager
-
Sun Java System Identity Auditor
-
Sun Java System Identity Manager
-
Sun Java System Identity Manager Service Provider Edition
For more information about each component, see the Sun Software web site: http://www.sun.com/software/.
The following figure shows the Access Manager, Identity Manager, and Directory Server identity management components.
Figure 1–1 Sun Identity Management Components
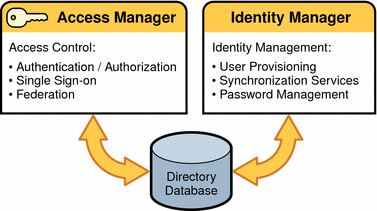
Sun Java System Identity Manager provides user provisioning, password management, synchronization services, comprehensive audit and reporting, and delegated administration. Identity Manager is not a component of Sun Java Enterprise System. To use Identity Manager in your deployment or to obtain more information, contact your Sun Microsystems technical representative or a Sun sales office: http://www.sun.com/sales-n-service/WWSales.html.
For a detailed description of Access Manager, see the Sun Java System Access Manager 7 2005Q4 Technical Overview.
Access Manager Deployment Planning
Deployment planning is a critical step in the successful implementation of an identity management solution. Each enterprise has its own set of goals, requirements, and priorities to consider. Successful deployment planning is the result of careful preparation, analysis, and design. Errors and missteps that occur anywhere during the planning process can result in a system that can misfire in many ways. Significant problems can arise from a poorly planned system. For example, the system could under-perform, be difficult to maintain, be too expensive to operate, could waste resources, or could be unable to scale to meet increasing needs.
Access Manager deployment planning as described in this guide follows the solution life cycle. The solution life cycle includes the process of planning, designing, and implementing an Access Manager enterprise software solution based on Java Enterprise System.
Solution Life Cycle
The solution life cycle, shown in the following figure, is a useful tool for planning and tracking a deployment project. The life cycle structures the preparation, analysis, and design necessary for successful deployment planning into a series of ordered phases. Each phase consists of related tasks that result in outputs that are carried forward as inputs to subsequent phases. The tasks within each phase are iterative, requiring thorough analysis and design before generating the outputs for that phase.
Figure 1–2 Solution Life Cycle
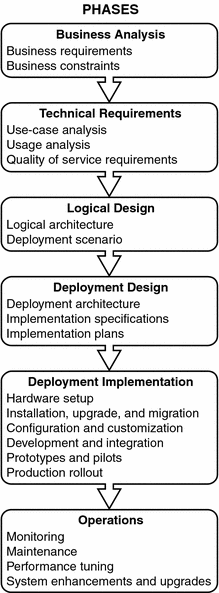
The organization of this manual is based on phases within the solution life cycle. The following sections in this chapter briefly describe each life cycle phase. For a more detailed description of these phases, see Sun Java Enterprise System 2005Q4 Deployment Planning Guide.
Business Analysis Phase
During business analysis, you define the business goals of a deployment project and state the business requirements that must be met to achieve those goals. When stating the business requirements, consider any business constraints that might affect the ability to achieve the business goal. Without proper business analysis, you run the risk of an incomplete solution.
During the business analysis phase you create business requirements documents that you later use as inputs to the technical requirements phase.
See Chapter 2, Business Analysis for Access Manager.
Technical Requirements Phase
The technical requirements phase starts with the business requirements and business constraints defined during the business analysis phase and translates them into technical specifications that can be used to subsequently design the deployment architecture. The technical requirements specify quality of service (QoS) features, such as performance, availability, security, and others.
During the technical requirements phase, you create documents that contain the following information:
-
Analysis of user tasks and usage patterns
-
Use cases that model user interaction with the planned system
-
Quality of service requirements derived from the business requirements, possibly taking into consideration the analysis of user tasks and usage patterns
The resulting usage analysis, use cases, and QoS requirements documents are inputs to the logical design phase of the solution life cycle. The usage analysis also plays a significant role in the deployment design phase.
See Chapter 3, Technical Requirements.
Logical Design Phase
During logical design, using use cases from the technical requirements phase as inputs, you identify the Access Manger components necessary to implement a solution. You also identify components that provide support to those Java ES components, and any additional custom-developed components necessary to meet the business requirements. You then map the components within a logical architecture that shows the interrelationships among the components. The logical architecture does not specify any hardware required to implement the solution.
The output of the logical design phase is the logical architecture. The logical architecture and the QoS requirements from the technical requirements phase form a deployment scenario, which is the input to the deployment design phase.
See Chapter 4, Logical Design with Access Manager.
Deployment Design Phase
During deployment design, you map the components specified in the logical architecture to a physical environment, producing a high-level deployment architecture. You also create an implementation specification, which provides low-level details specifying how to build the deployment architecture. Additionally, you create a series of plans and specifications that detail different aspects of implementing the software solution.
Project approval occurs during the deployment design phase. During project approval, the cost of the deployment is assessed. If approved, contracts for implementation of the deployment are signed, and resources to build the project are acquired. Often, project approval occurs after the implementation specification has been detailed. However, approval can also occur upon completion of the deployment architecture.
The outputs of the deployment design phase include the following:
-
Deployment architecture. A high-level design document that represents the mapping of components to network hardware and software.
-
Implementation specifications. Detailed specifications used as blueprints for building the deployment.
-
Implementation plans. A group of plans and specifications that cover various aspects of implementing an enterprise software solution. Implementation plans include a migration plan, installation plan, user management plan, test plan, and others.
See Chapter 5, Deployment Design with Access Manager
Implementation Phase
During the implementation phase, you work from specifications and plans created during deployment design to build the deployment architecture and implement the solution. Depending on the nature of your deployment project, this guide documents the following tasks:
-
Installing Access Manager on multiple host servers
-
Configuring an Access Manager deployment as a site
-
Using a Load Balancer with Access Manager
-
Implementing Access Manager session failover
-
Setting session quota constraints
-
Enabling session property change notifications
-
Tuning a deployment
- © 2010, Oracle Corporation and/or its affiliates
