1.2 System Architecture
In this system architecture, a Service Provider and a Identity Provider form a circle of trust in order to exchange user authentication information using SAMLv2. For these instructions, the circle of trust contains one identity provider, a service that maintains and manages identity information. Once the circle of trust is established, single sign-on is enabled between both providers.
The Service Provider domain is siroe.com. In this deployment, two Federation Managers are load-balanced for high availability, and each is configured for the SAMLv2 protocol. Each Federation Manager server uses a Directory Server user instance for user data.
The Identity Provider domain is example.com. Two Access Manager servers are configured for the SAMLv2 protocol and load-balanced for high availability.
Table 1–1 Software Products Used in Examples|
Component |
Versions |
|---|---|
|
Sun Java Access Manager |
7.0 JES 2005Q4 |
|
Sun Java Access Manager Patch |
7.0_Patch_5 |
|
Sun Java Directory Server |
5.2 JES 2005Q4 |
|
Sun Java Directory Server Patch |
5.2_Patch_4 |
|
Sun Java System Federation Manager |
7.0 |
|
Sun Java Web Server |
6.1SP5 JES 2005Q4 |
|
Web Policy Agent (for Sun Java WebServer v6.1) |
2.2 |
|
Web Policy Agent Patch |
HotPatch_5 |
|
Sun Java Application Server |
8.1 JES 2005Q4 |
|
Sun Java Application Server Patch |
Enterprise Ed 8.1 2005Q1 |
|
J2EE Policy Agent (for Sun Java Application server 8.1 2005Q1) |
2.2 |
|
SAML plug-in |
2 |
|
SAML v2 plug-in Patch |
2 |
|
Sun Solaris |
10, Update 5 |
Figure 1–1 on the next page illustrates the Service Provider Site described in this document, Deployment Example 2: Federation Using SAMLv2.
Figure 1–1 Physical Architecture for Federation Using SAMLv2
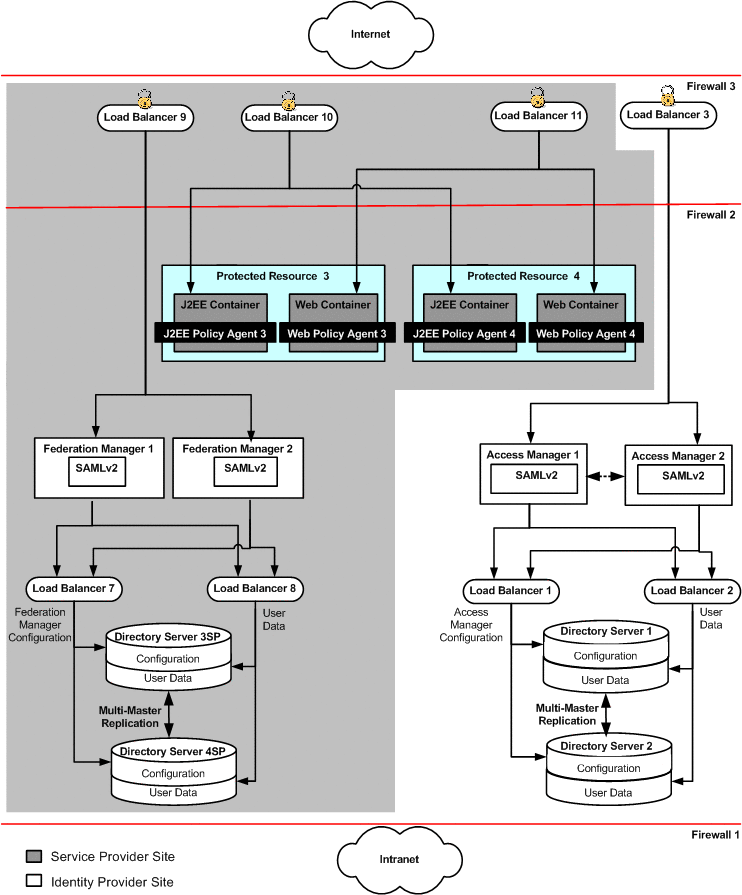
The Identity Provider Site shown here is a subset of a larger deployment example described in a companion document, Deployment Example: Access Manager Load Balancing, Distributed Authentication, and Session Failover. Use the two companion documents together to build both the Service Provider Site and the Identity Provider Site. See 2.12 Obtaining Instructions for Deploying the Identity Provider Site.
Figure 1–2 From Access Manager Load Balancing, Distributed Authentication UI, and Session Failover
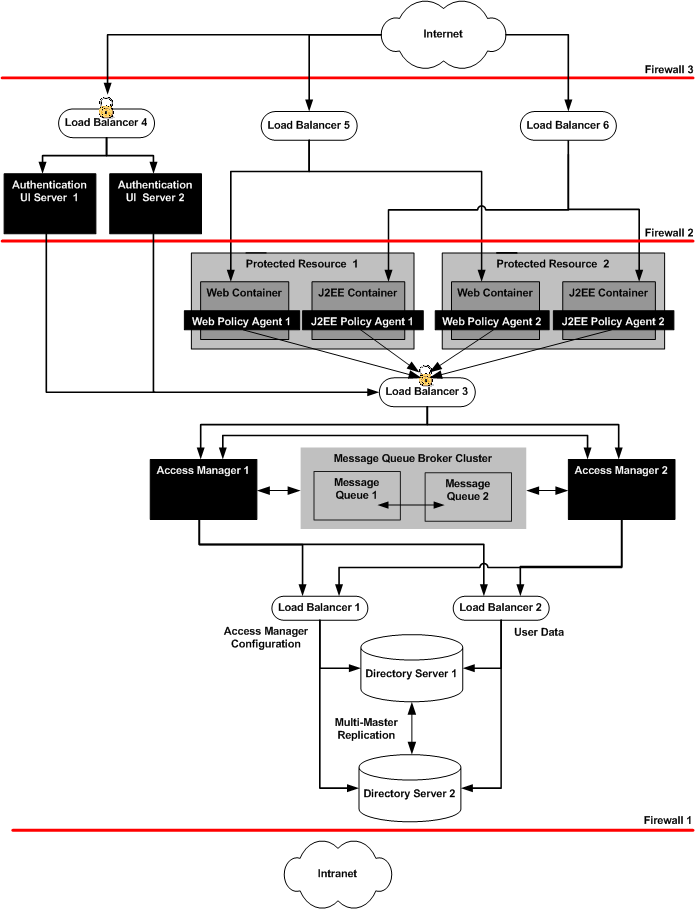
To set up the Identity Provider Site, see Deployment Example: Access Manager Load Balancing, Distributed Authentication, and Session Failover. Follow the detailed instructions for setting up the Directory Servers, the Access Manager Servers, their respective load balancers, and session failover. For the Federation Using SAMLv2 deployment example, it is not necessary to implement the Distributed Authentication UI or the Protected Resources and policy agents pictured here.
- © 2010, Oracle Corporation and/or its affiliates
