Chapter 10 Securing Web Services Using ID-WSF (Liberty Alliance Specifications)
This chapter provides information about developing identity-based web services using the Identity Web Services Framework (ID-WSF) developed in OpenSSO Enterprise. OpenSSO Enterprise provides an implementation for the Liberty Personal Profile Service and typically uses the default OpenSSO Enterprise configuration store for the Personal Profile Service configuration. However, this chapter describes a new use case. With OpenSSO Enterprise 8.0, you can develop a custom, identity-based web service using the OpenSSO Enterprise infrastructure instead of using the Personal Profile Service as a data service.
The following topics are contained in this chapter:
About the Identity Web Services Framework
Identity Web Services Framework (ID-WSF) is a set of specifications created by the Liberty Alliance to promote secure web services. ID-WSF is part of Liberty's Phase 2 specifications which augment the initial Identity Federation Framework (ID-FF) specifications. The ID-FF focuses on federating the user's authentication and single sign-on. The ID-WSF defines specifications for web services in a federated environment. The federated environment establishes a trust between all the participating entities without revealing the end user's identity. The following diagram illustrates the relationship between entities in such an environment, known as a circle of trust.
Figure 10–1 Major Components in a Circle of Trust
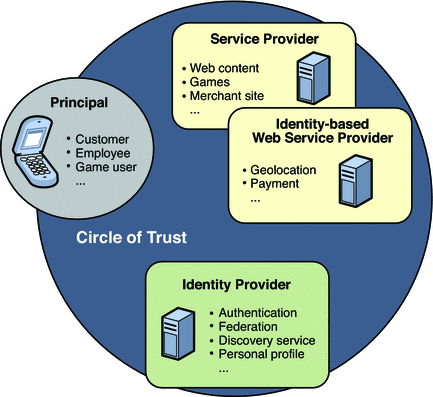
The ID-WSF defines specifications for the following Liberty components:
-
Discovery Service
-
SOAP Binding
-
Authentication Service
-
Security Mechanisms
-
Interaction Service
-
PAOS Binding
-
Data Service Template
The ID-WSF defines a concrete trust authority called the Liberty Discovery Service. The framework is built around the Liberty Discovery Service. The Liberty Discovery Service not only enables a web service to register, but also helps in generating security credentials for web service clients that may be doing lookups for a specific service type.
The Liberty Interaction Service allows the user to interact during web services communication for any authorization. Liberty Authentication Service allows the web services clients to authenticate the principal in non-browsed based environments. As part of the Phase 2 specifications, Liberty Alliance also defined specifications for additional identity services such as Liberty Personal Profile Service, Liberty Employee Personal Profile Service and others. These Phase 2 specifications form the Liberty Service Instance Specifications (SIS) Specifications.
OpenSSO Enterprise fully implements ID-WSF1.x specifications and exposes the ID-WSF as a pluggable framework which the user can leverage for increased security. OpenSSO Enterprise is a self-contained, single WAR file built to industry standard specifications. The Identity Web Services Framework in OpenSSO Enterprise enables developers to focus on the business logic of their service while leaving the security aspect to OpenSSO Enterprise.
The following diagram represents the OpenSSO Enterprise ID-WSF framework from an implementation point of view.
Figure 10–2 OpenSSO Enterprise Identity Web Service Framework Implementation
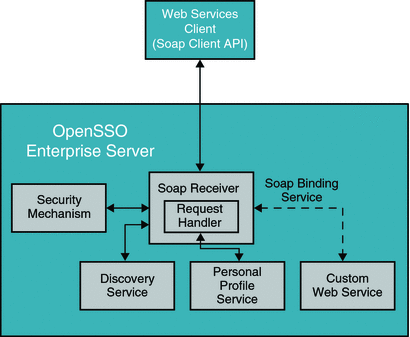
The OpenSSO Enterprise ID-WSF uses a simple servlet-based extension framework that any identity based web service can plug into. OpenSSO Enterprise provides tools and APIs for two distinct classes of developers: Identity Web Service Implementors (WSPs), and application developers (WSCs) who use these web services . OpenSSO Enterprise also provides the hooks required to quickly integrate the existing infrastructure with Liberty-enabled infrastructure.
Any custom web service that is developed using the OpenSSO Enterprise ID-WSF must register with the SOAP Binding Service. The SOAP Binding Service provides the validation of SOAP message with respect to security such as XML Digital Signature and Encryption and other Liberty processing rules. The Soap Binding Service then generates the OpenSSO Enterprise single sign-on token for further authorization of the client by the web service.
Analyzing the Deployments
The Identity Web Services Framework can be used in either browser-based mode or desktop mode. The browser-based client uses SAMLv2 or ID-FF protocols to find the Liberty Discovery Service Resource Offering of an authenticated user, or bootstrap, into the ID-WSF framework. The desktop clients can leverage the Liberty Authentication Service to bootstrap into the ID-WSF. OpenSSO Enterprise supports ID-WSF boot strapping through the SAMLv2, ID-FF, or ID-WSF -based authentication service, depending upon the client needs. This chapter describes deployments for both browser-based clients and desktop clients
Browser-based ID-WSF Deployment
The following diagram represents the deployment architecture for ID-WSF using OpenSSO Enterprise for browsed-based clients.
Figure 10–3 Deployment Architecture for Browser-based Identity Web Services
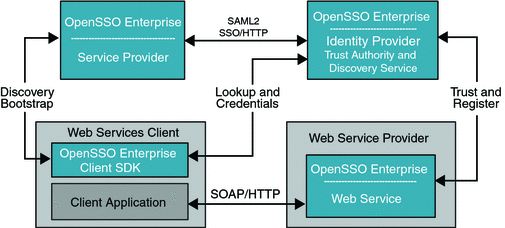
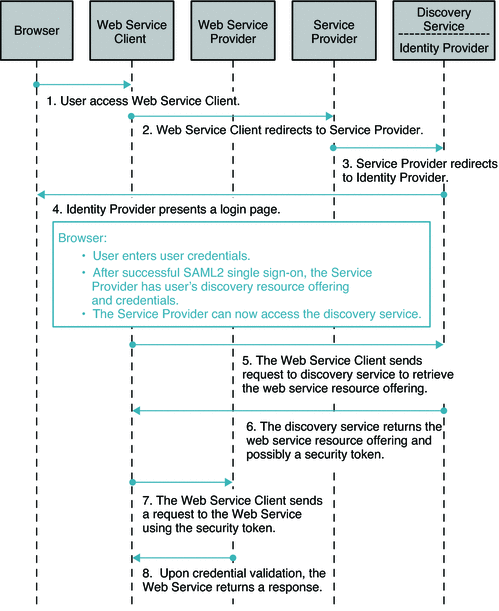
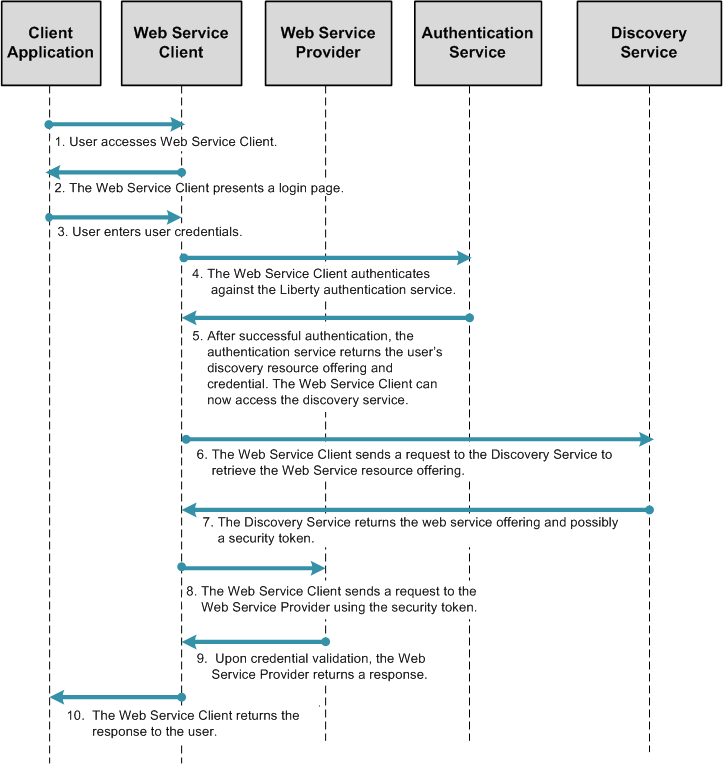
Both Service Provider and Identity Provider are used for authenticating the user's identity using SAMLv2 protocols. OpenSSO Enterprise can be an Identity Provider or a Service Provider or a hosting web service in this deployment. The Service Provider and Web Services Client are in the same domain in this deployment. The Web Service Provider registers its service resource offering with the Discovery Service before it offers services to various clients. The registration can be done through either the Discovery Service protocol or out of band. The OpenSSO Enterprise can be deployed in various roles for this deployment as illustrated in the deployment architecture diagram. The following figures shows the process flow among various entities in the browser-based identity web services deployment.
Figure 10–4 Process Flow for Browser-based Identity Web Services
Desktop ID-WSF Deployment
The desktop mode ID-WSF deployment supports desktop mode clients, so they do not require an application container. Desktop ID-WSF is useful for standalone Web Service Clients. The custom Web Service Clients can leverage the OpenSSO Enterprise Client SDK to enable a secure connection for a given payload. The Web Services Client bundles the OpenSSO Enterprise Client SDK that accesses the local OpenSSO Enterprise instance to secure web service requests.
Figure 10–5 Desktop ID-WSF Deployment
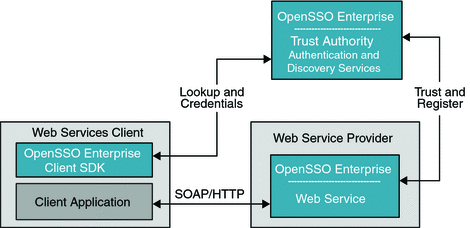
The Web Services package is contained in the OpenSSO Enterprise WAR file and must be deployed along with the OpenSSO Enterprise server to leverage the ID-WSF security framework. The configuration and user data is not required to be same data store as that of OpenSSO Enterprise. The trust authority for ID-WSF is the Discovery Service. The Discovery Service end point is exposed the same way as any data web service, and can fully leverage OpenSSO Enterprise infrastructure components such as authentication, policies, and so forth to serve web service clients and as well as web services. OpenSSO Enterprise is independent in all these roles and can be deployed appropriately based on the customer or application requirements. The following figure illustrates the process flow for desktop ID-WSF.
Figure 10–6 Process Flow for Desktop Identity Web Services
Considering Assumptions, Dependencies and Constraints
As you plan your deployment, consider the following assumptions, dependencies, and constraints to determine if your environment is appropriate for using the ID-WSF.
Assumptions and Dependencies
The fundamental difference between ID-WSF and generic web services is that the ID-WSF defines a security framework around user identity. The ID-WSF allows an end user to register his service offerings with their trusted trust authorities. Generic web services advertise their offerings through either a Web Service Description Language (WSDL) file or by the Enterprise Universal Description, Discovery, and Integration (UDDI) registry. These use cases are driven through Liberty ID-WSF and thus have a dependency on other Liberty protocols such as ID-FF and SAMLv2.
Constraints
The majority of identity web services are deployed in the Mobile Communications industry. For server-side web service providers OpenSSO Enterprise provides a comprehensive solution for ID-WSF. However, solutions for Liberty enabled clients do not provide the same degree of coverage. For example, the Client SDK is not J2ME-compatible and will not work with mobile devices that typically use Midlets to invoke Identity Web Services. Also, the OpenSSO Enterprise ID-WSF does not implement all profiles for the Liberty-enabled user agent or device (LUAD) clients.
Understanding Typical Business Use Cases
The adoption of identity web services is widespread especially in mobile communications-based businesses. Many of the telecommunication industries in Europe have invested heavily in ID-WSF based architectures, although the adoption in US is relatively smaller.
The following figure illustrates a simple E-commerce deployment using OpenSSO Enterprise.
Figure 10–7 Identity Web Services Business Use Case
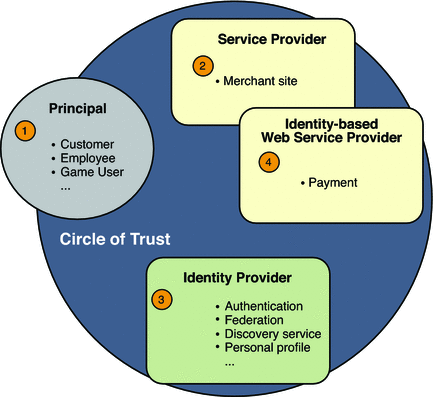
-
The customer is browsing the merchant site and initiates a purchase of some item.
-
The merchant who needs to authenticate the customer can request authentication through one of the trusted Identity Providers. The authentication happens here through ID-FF or SAMLv2, masking the real identity of the customer. This helps preserve the customer's privacy.
-
The merchant requests the payment service to guarantee the transaction. First the merchant site discovers the customer payment service through the Discovery Service. Then the merchant site requests the payment services on behalf of the principal. This step leverages the fact that the Liberty discovery mechanism is per principal-oriented, allowing merchants to request payments without having to know the real customer identity.
-
The payment service validates the transaction. Before charging the customer, the payment service may take a user consent. The payment service uses the Liberty Interaction Service for doing this. With successful purchase, the merchant returns the confirmation of purchase and delivers the service.
Setting Up and Configuring ID-WSF
For demonstration purposes, this section describes the high-level setup of a simple web-based service which was used as the basis for this chapter. OpenSSO Enterprise plays various roles in this environment depending:
-
OpenSSO Enterprise is installed in the Web Services Client Domain.
-
OpenSSO Enterprise is installed in the Web Services Provider Domain.
-
OpenSSO Enterprise acts as a Trust Authority Service.
For browser-based deployment, the Liberty Personal Profile Web Service that is shipped with OpenSSO Enterprise is used. The user profile information is stored in the LDAP user data store.
For desktop based deployment, a simple weather service web service is developed to demonstrate the developer aspect.
Evaluating Benefits and Tradeoffs
The following lists are useful in helping you determine whether ID-WSF is suitable for your environment.
Benefits
-
OpenSSO Enterprise provides an extensive, customizable framework for ID-WSF.
-
ID-WSF consumers can leverage not only use Identity Web Services security, but can also leverage the OpenSSO Enterprise policy and access control features.
-
Processing a custom web service payload can totally be independent of the OpenSSO Enterprise infrastructure.
Tradeoffs
-
Developers must develop and deploy their web services along with OpenSSO Enterprise.
-
If web services already exist in the environment, the developers must integrate them with OpenSSO Enterprise.
OpenSSO Enterprise ID-WSF framework is tested in interoperable environments and certified by the Liberty Alliance. So the web services are almost certain to work in multi-vendor environments as long as the remote party is also a certified implementation.
-
The lack of mobile client support with the OpenSSO Enterprise Client SDK may be a limitation. However, the primary use for OpenSSO Enterprise is in enterprise web service deployments.
Finding More Information
- © 2010, Oracle Corporation and/or its affiliates
