Analyzing the Deployment Architecture
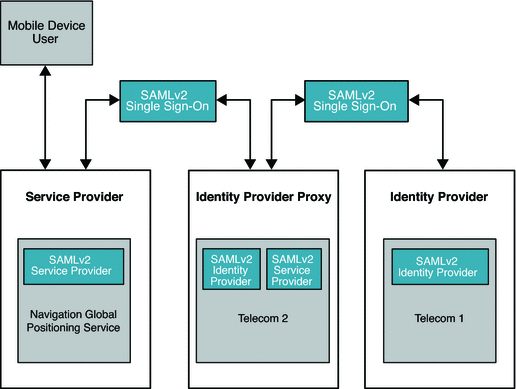
Identity Provider Proxy uses the SAMLv2 protocol to transfer identity data among the communicating entities. The following figure illustrates the major components in a typical deployment using Identity Provider Proxy.
In this deployment, the mobile device user is from France and has an account with Telecom1. The mobile device user travels to the United States and wants to access the global positioning service (GPS) provided by Telecom2 . Telecom2 is a United States service provider . The Telecom2 Identity Provider is the sole identity provider with which Telecom2 has a business affiliation.
Telecom2 receives and processes the authentication requests coming from Telecom2 Global Positioning Service, and responds with the required authentication information. Telecom2, like so many other wireless phone service providers in the world, always maintains the trust relationship with other carriers in different countries. Telecom1 is one such trusted partner which provides roaming services to their customers based on bilateral agreements. In this illustration, because of an established business relationship, Telecom2 doesn't need to know the mobile user at all. Telecom2 can process the authentication request from Telecom2 Global Positioning Service on behalf of Telecom1 based on the following trust relationships:
-
Telecom2 Global Positioning Service trusts Telecom2 for user authentication.
-
Telecom2 and Telecom1 trust each other for authentication and for the roaming services.
Figure 7–1 Deployment Architecture of Identity Provider Proxy
- © 2010, Oracle Corporation and/or its affiliates
