Using a Reverse Proxy
As an application proxy does, a reverse proxy acts as a gateway between a protected HTTP server and requests to the HTTP server that originate from outside the secure intranet. A reverse proxy is installed between the outer internet firewall and the inner intranet firewall - referred to as the demilitarized zone (DMZ) - to prevent direct access to the OpenSSO configuration and user data stores by unauthorized users. A reverse proxy can be implemented as Sun Web Proxy Server 4.0.9 or as Sun Web Server 7.0 Update 3 or later with the reverse proxy plugin. It requires an SSL-enabled port for communication between the external client and the back-end OpenSSO Enterprise server. The following diagram illustrates the deployment.
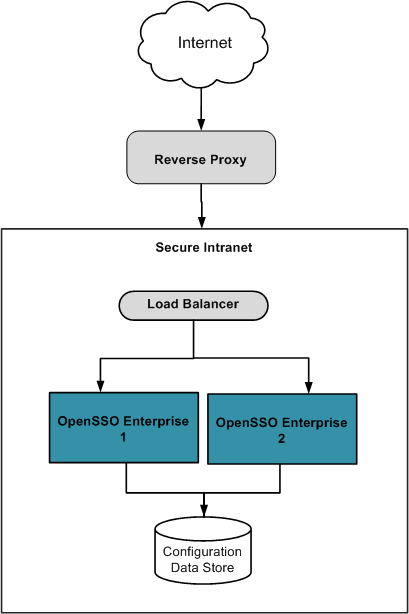
A reverse proxy is best used when the content to be presented is uniform. This is generally the case when there is only one authentication module or authentication chain configured thus only one user interface page is served and that page is hardly changed. Taking advantage of the caching and compression capabilities of the reverse proxy, the page can be served very quickly. Also using a reverse proxy can be an acceptable and efficient way of distributing the load among web servers. Benefits of reverse proxy servers include:
-
Caching for improved performance When static content is cached, the reverse proxy would not forward a request for the content to OpenSSO Enterprise; it would respond to the request by serving the content itself. This could lower the request load, thereby improving performance of the server and potentially lower response times to the client.
-
Additional layer of security By introducing an additional layer of security, access to the OpenSSO Enterprise server is further limited. This additional layer offers the opportunity to monitor traffic, to perform a wider set of checks (for example, malformed URL strings can be stopped at the proxy), and to react to attacks sooner.
-
Persistent load balancing Configure the name of a sticky cookie or sticky URI parameter (in the reverse proxy configuration) to allow subsequent requests to stick to the same OpenSSO server that responded to the first request. Stickiness affects OpenSSO Enterprise performance positively.
-
Compression for speedy load times Outgoing traffic can be transparently compressed thus lowering total bandwidth requirements. A reverse proxy supports various compression levels and fragment sizes, allowing the administrator to select a level of compromise between speed and compression.
-
Spoon feeding dynamic content Dynamically generated content can be returned from the back end server a little at a time.
Note –
As most reverse proxies have limited load balancing capabilities, thought should be put into whether you would use a reverse proxy or a reverse proxy capable load balancer. For example, reverse proxy software would require additional hardware whereas load balancers are fairly common.
See Sun Java System Web Proxy Server 4.0.12 Installation and Migration Guide and chapters 3 and 4 in Using the Java System Web Server as a Reverse Proxy for Improved Security for more information.
- © 2010, Oracle Corporation and/or its affiliates
