Audit Commands
This section provides information about the commands that are used with the auditing service.
The Audit Daemon
The following list summarizes what the audit daemon, auditd, does.
-
auditd opens and closes audit log files in the directories that are specified in the audit_control file, in the order in which they are specified.
-
auditd reads audit data from the kernel and writes it to an audit log file.
-
auditd executes the audit_warn script when the audit directories fill past limits that are specified in the audit_control file. The script, by default, sends warnings to the audit_warn mail alias and to the console.
-
By default, when all audit directories are full, processes that generate audit records are suspended. In addition, the auditd command writes a message to the console and to the audit_warn mail alias. The audit policy can be reconfigured with the auditconfig. At this point, only the system administrator can log in to write audit files to tape, delete audit files from the system, or do other cleanup.
The auditd daemon can be started automatically when the machine is brought up to multiuser mode, or you can start it from the command line. When the audit daemon is started, it determines the amount of free space necessary for audit log files.
The daemon uses the list of audit directories in the audit_control file as possible locations for creating audit files. The audit daemon maintains a pointer into this list of directories, starting with the first directory. Every time the audit daemon needs to create an audit file, it puts the file into the first available directory in the list, starting at the audit daemon's current pointer. You can reset the pointer to the beginning of the list by running the audit -s command. When you use the audit -n command to instruct the daemon to switch to a new audit file, the new file is created in the same directory as the current file.
The audit Command
The audit command controls the actions of the audit daemon. The audit command can do the following tasks:
-
Enable and disable auditing
-
Reset the audit daemon
-
Adjust the auditing preselection mask on the local machine
-
Write audit records to a different audit log file
See the audit(1M) man page for a discussion of the available options.
The auditreduce Command
Use the auditreduce command to merge audit records from one or more input audit files or to perform a post selection of audit records. See the auditreduce(1M) man page. To merge the entire audit trail, you can run this command on the machine on which all the audit file systems for the installation are mounted.
The auditreduce command enables you to track all auditable actions on multiple machines from a single location. If you identically configure all machines at an installation for auditing, and create servers and local directories for the audit log files, then the auditreduce command can read the logical combination of all audit files in the installation as a single audit trail. auditreduce ignores how the records were generated or where they are stored. Without options, the auditreduce command merges audit records from all the audit files in all of the subdirectories in the audit root directory (/etc/security/audit) and sends the result to standard output. You can also place it into a single, chronologically ordered output file. The file contains binary data.
The auditreduce command also can select particular types of records for analysis. The merging and selecting functions of auditreduce are logically independent. auditreduce captures data from the input files as the records are read, before the files are merged and written to disk.
The praudit command makes the binary output of auditreduce readable.
By specifying options to the auditreduce command, you can also do the following:
-
Request audit records that were generated by only certain audit flags
-
Request audit records that were generated by one particular user
-
Request audit records that were generated on specific dates
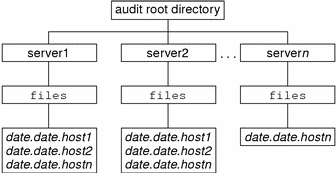
With no arguments, auditreduce checks the subdirectories within the /etc/security/audit directory, the default audit root directory. The command checks for a files directory in which the start-time.end-time.hostname files reside. The auditreduce command is very useful when the audit data for different hosts (Figure 25–1) or for different audit servers (Figure 25–2) reside in separate directories.
Figure 25–1 Audit Trail Storage Sorted by Host
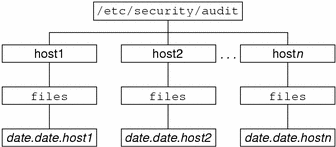
Figure 25–2 Audit Trail Storage Sorted by Server
When you do not store audit data in the default directory, perhaps because the partition for /etc/security/audit is very small, you can pass the auditreduce command another directory by using the -R option:
# auditreduce -R /var/audit-alt |
You can also specify a particular subdirectory by using the -S option:
# auditreduce -S /var/audit-alt/host1 |
You can direct auditreduce to process only certain audit log files by specifying them as command arguments:
# auditreduce /var/audit/egret/files/2001*.2001*egret |
For other options and additional examples, see the auditreduce(1M) man page.
The praudit Command
The praudit command reads audit records in binary format from standard input and displays the records in a presentable format. The input can be piped from the auditreduce command or from a single audit file. Input can also be produced with the cat command to concatenate several files, or the tail command for a current audit file.
The praudit command can generate four output formats:
-
Default – The default option displays one audit token per line. The default option displays the audit event by its description, such as ioctl(2), and displays any value that could be text in text format. For example, a user is displayed as the user name, not as the user ID.
-
–l option – The long option displays one audit record per line. The -d option changes the delimiter used between token fields, and between tokens. The default delimiter is a comma.
-
–r option – The raw option displays any value that could be numeric as a number. For example, a user is displayed by user ID, Internet addresses are in hexadecimal format, and modes are in octal format. The audit event is displayed as its event number, such as 158.
-
–s option – The short option displays the audit event by its table name, for example, AUE_IOCTL. The option displays the other tokens as the default option displays them.
In the default output format of praudit, each record is easily identified as a sequence of audit tokens where each token is on a separate line. Each record begins with a header token. You could, for example, further process the output with the awk command.
Here is the default output from the praudit command for a header token:
header,240,1,ioctl(2),es,Tue Sept 7 16:11:44 1999, + 270 msec |
Here is the output from the praudit -r command for the same header token:
20,240,1,158,0003,699754304, + 270 msec |
Sometimes, you might want to manipulate output from the praudit command as lines of text. For example, you might want to select records that the auditreduce command cannot select. You can use a simple shell script to process the output of praudit. The following simple example script marks the header tokens by prefixing them with Control-A, combines all the audit tokens for one record onto one line while preserving the line breaks as Control-A, runs the grep command, and restores the original newline breaks.
#!/bin/sh praudit | sed -e '1,2d' -e '$s/^file.*$//' -e 's/^header/^aheader/' \\ | tr '\\012\\001' '\\002\\012' \\ | grep "$1" \\ | tr '\\002' '\\012' |
Note that the ^a in the script is Control-A, not the two characters ^ and a. The prefix distinguishes the header token from the string header that might appear as text.
The auditconfig Command
The auditconfig command provides a command-line interface to retrieve and set audit configuration parameters. See the auditconfig(1M) man page. Options to the auditconfig command include the following:
- -chkconf
-
Checks the configuration of kernel event-to-class mappings and reports any inconsistencies
- -conf
-
Reconfigures kernel event-to-class mappings at runtime to match the current mappings in the audit_event file.
- -getcond
-
Retrieves the state of auditing on the machine. The following table shows the possible responses.
Table 25–1 Possible Auditing ConditionsResponse
Meaning
auditing
Auditing is enabled and turned on.
no audit
Auditing is enabled, but the audit daemon is not running.
disabled
Auditing is not enabled.
- -setcond condition
-
Sets the state of auditing on the machine to one of auditing or noaudit.
- -getclass event_number
-
Retrieves the preselection classes to which the specified event is mapped.
- -setclass event_number audit_flags
-
Sets the preselection classes to which the specified event is mapped.
- -lsevent
-
Displays the currently configured (runtime) kernel and user audit event information.
- -getpinfo pid
-
Retrieves the audit ID, preselection mask, terminal ID, and audit session ID of the specified process.
- -setpmask pid flags
- -setsmask asid flags
-
Sets the preselection mask of all processes with the specified audit session ID.
- -setumask auid flags
-
Sets the preselection mask of all processes with the specified user audit ID.
- -lspolicy
-
Displays the list of audit policies with a short description of each policy.
- -getpolicy
- -setpolicy policy_flag[,policy_flag]
-
Sets the audit policy flags to the specified policies (see Determining Which Audit Policies to Use).
- © 2010, Oracle Corporation and/or its affiliates
