How to Use Solaris Secure Shell Port Forwarding
You can specify that a local port be forwarded to a remote host. Effectively, a socket is allocated to listen to the port on the local side. The connection from this port is made over a secure channel to the remote host. For example, you might specify port 143 to obtain email remotely with IMAP4. Similarly, a port can be specified on the remote side.
Note –
Secure Shell port forwarding must use TCP connections. Secure Shell does not support UDP connections.
To set a local port to be forwarded, specify two ports. Specify the local port to listen to, and specify the remote host and port to forward to.
myLocalHost% ssh -L localPort:remoteHost:remotePort |
To set a remote port to receive a secure connection, specify two ports. Specify the remote port to listen to, and specify the local host and port to forward to.
myLocalHost% ssh -R remotePort:localHost:localPort |
Example—Using Local Port Forwarding to Receive Mail
The following example demonstrates how you can use local port forwarding to receive mail securely from a remote server.
myLocalHost% ssh -L 9143:myRemoteHost:143 myRemoteHost |
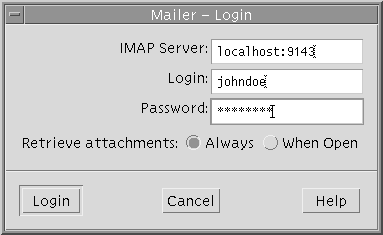
This command forwards connections to port 9143 on myLocalHost to port 143, which is the IMAP v2 server port on myRemoteHost. When the user launches a mail application, the user needs to specify the local port number. An example that uses the dtmail command is shown in Figure 11–1.
Note that the term localhost in this case and in Example—Using Remote Port Forwarding to Communicate Outside of a Firewall refers to the keyword that designates the user's local host. The localhost keyword should not be confused with myLocalHost. The myLocalHost variable is the hypothetical host name that identifies a local host in the examples in this chapter.
Figure 11–1 Specifying Port Forwarding for Email
Example—Using Remote Port Forwarding to Communicate Outside of a Firewall
This example demonstrates how a user in an enterprise environment can forward connections from a host on an external network to a host inside a corporate firewall.
myLocalHost% ssh -R 9022:myLocalHost:22 myOutsideHost |
This command forwards connections to port 9022 on myOutsideHost to port 22, the sshd server, on the local host.
myOutsideHost% ssh -p 9022 localhost myLocalHost% |
This command demonstrates how after the remote forwarding connection has been established, the user can use the ssh command to connect securely from the remote host.
- © 2010, Oracle Corporation and/or its affiliates
