How SEAM Works
The following is an overview of the SEAM authentication system. For a more detailed description, see How the Authentication System Works.
From the user's standpoint, SEAM is mostly invisible after the SEAM session has been started. Commands such as rsh or ftp work pretty much in their usual fashion. Initializing a SEAM session often involves no more than logging in and providing a Kerberos password.
The SEAM system revolves around the concept of a ticket. A ticket is a set of electronic information that serves as identification for a user or a service such as the NFS service. Just as your driver's license identifies you and indicates what driving permissions you have, so a ticket identifies you and your network access privileges. When you perform a SEAM-based transaction (for example, if you rlogin in to another machine), you transparently send a request for a ticket to a Key Distribution Center, or KDC. The KDC accesses a database to authenticate your identity and returns a ticket that grants you permission to access the other machine. “Transparently” means that you do not need to explicitly request a ticket; it happens as part of the rlogin command. Because only the authenticated client can get a ticket for a specific service, another client cannot use rlogin under an assumed identity.
Tickets have certain attributes associated with them. For example, a ticket can be forwardable (which means that it can be used on another machine without a new authentication process), or postdated (not valid until a specified time). How tickets are used (for example, which users are allowed to obtain which types of ticket) is set by policies that are determined when SEAM is installed or administered.
Note –
You will frequently see the terms credential and ticket. In the greater Kerberos world, they are often used interchangeably. Technically, however, a credential is a ticket plus the session key for that session. This difference is explained in more detail in Gaining Access to a Service Using SEAM.
The following sections further explain the SEAM authentication process.
Initial Authentication: the Ticket-Granting Ticket
Kerberos authentication has two phases: an initial authentication that allows for all subsequent authentications, and the subsequent authentications themselves.
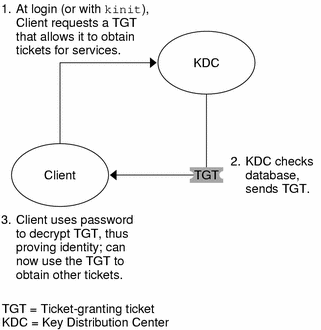
The following figure shows how the initial authentication takes place.
Figure 13–1 Initial Authentication for SEAM Session
-
A client (a user, or a service such as NFS) begins a SEAM session by requesting a ticket-granting ticket (TGT) from the Key Distribution Center (KDC). This request is often done automatically at login.
A ticket-granting ticket is needed to obtain other tickets for specific services. Think of the ticket-granting ticket as similar to a passport. Like a passport, the ticket-granting ticket identifies you and allows you to obtain numerous “visas,” where the “visas” (tickets) are not for foreign countries but for remote machines or network services. Like passports and visas, the ticket-granting ticket and the other various tickets have limited lifetimes. The difference is that “Kerberized” commands notice that you have a passport and obtain the visas for you. You don't have to perform the transactions yourself.
Another analogy for the ticket-granting ticket is that of a three-day ski pass which is good at four different ski resorts. You show the pass at whichever resort you decide to go to (until it expires) and you receive a lift ticket for that resort. Once you have the lift ticket, you can ski all you want at that resort. If you go to another resort the next day, you once again show your pass, and you get an additional lift ticket for the new resort. The difference is that the SEAM-based commands notice that you have the weekend ski pass, and get the lift ticket for you, so you don't have to perform the transactions yourself.
-
The KDC creates a ticket–granting ticket and sends it back, in encrypted form, to the client. The client decrypts the ticket-granting ticket by using the client's password.
-
Now in possession of a valid ticket-granting ticket, the client can request tickets for all sorts of network operations, such as rlogin or telnet, for as long as the ticket-granting ticket lasts. This ticket usually lasts for a few hours. Each time the client performs a unique network operation, it requests a ticket for that operation from the KDC.
Subsequent Authentications
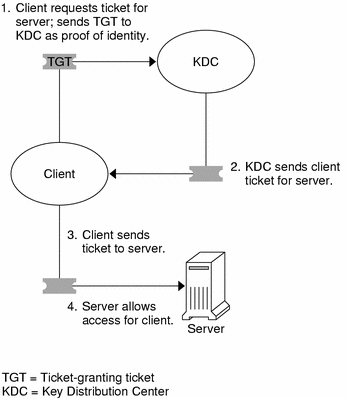
After the client has received the initial authentication, each individual authentication follows the pattern that is shown in the following figure.
Figure 13–2 Obtaining Access to a Service
-
The client requests a ticket for a particular service (say, to rlogin into another machine) from the KDC by sending the KDC its ticket-granting ticket as proof of identity.
-
The KDC sends the ticket for the specific service to the client.
For example, suppose user joe wants to access an NFS file system that has been shared with krb5 authentication required. Since he is already authenticated (that is, he already has a ticket-granting ticket), as he attempts to access the files, the NFS client system automatically and transparently obtains a ticket from the KDC for the NFS service.
For example, suppose the user joe uses rlogin on the server boston. Since he is already authenticated (that is, he already has a ticket-granting ticket), he automatically and transparently obtains a ticket as part of the rlogin command. This ticket allows him to rlogin into boston as often as he wants until it expires. If joe wants to rlogin into the machine denver, he obtains another ticket, as in Step 1.
-
The client sends the ticket to the server.
When using the NFS service, the NFS client automatically and transparently sends the ticket for the NFS service to the NFS server.
-
The server allows the client access.
These steps make it appear that the server doesn't ever communicate with the KDC. The server does, though; it registers itself with the KDC, just as the first client does. For simplicity's sake, we have left that part out.
The SEAM Remote Applications
What are the SEAM-based (or “Kerberized”) commands that a user such as joe can use? They are:
-
ftp
-
rcp
-
rlogin
-
rsh
-
telnet
These applications are the same as the Solaris applications of the same name, except that they use Kerberos principals to authenticate transactions, thereby providing Kerberos-based security. (See Principals for information on principals.)
Principals
A client in SEAM is identified by its principal. A principal is a unique identity to which the KDC can assign tickets. A principal can be a user, such as joe, or a service, such as nfs or telnet.
By convention, a principal name is divided into three parts: the primary, the instance, and the realm. A typical SEAM principal would be, for example, joe/admin@ENG.EXAMPLE.COM, where:
-
joe is the primary. The primary can be a user name, as shown here, or a service, such as nfs. The primary can also be the word host, which signifies that this principal is a service principal that is set up to provide various network services (ftp, rcp, rlogin, and so on).
-
admin is the instance. An instance is optional in the case of user principals, but it is required for service principals. For example: if the user joe sometimes acts as a system administrator, he can use joe/admin to distinguish himself from his usual user identity. Likewise, if joe has accounts on two different hosts, he can use two principal names with different instances (for example, joe/denver.example.com and joe/boston.example.com). Notice that SEAM treats joe and joe/admin as two completely different principals.
In the case of a service principal, the instance is the fully qualified host name. bigmachine.eng.example.com is an example of such an instance so that the primary/instance might be, for example, ftp/bigmachine.eng.example.com or host/bigmachine.eng.example.com.
-
ENG.EXAMPLE.COM is the SEAM realm. Realms are discussed in Realms.
The following are all valid principal names:
-
joe
-
joe/admin
-
joe/admin@ENG.EXAMPLE.COM
-
ftp/host.eng.example.com@ENG.EXAMPLE.COM
-
host/eng.example.com@ENG.EXAMPLE.COM
Realms
A realm is a logical network, similar to a domain, which defines a group of systems under the same master KDC. Figure 13–3 shows how realms can relate to one another. Some realms are hierarchical (one realm being a superset of the other realm). Otherwise, the realms are non-hierarchical (or “direct”) and the mapping between the two realms must be defined. A feature of SEAM is that it permits authentication across realms. Each realm only needs to have a principal entry for the other realm in its KDC. The feature is called cross-realm authentication.
Figure 13–3 Realms
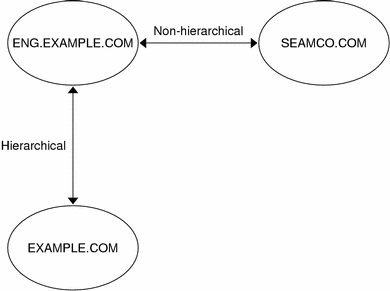
Realms and Servers
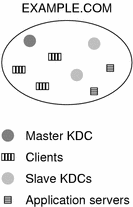
Each realm must include a server that maintains the master copy of the principal database. This server is called the master KDC server. Additionally, each realm should contain at least one slave KDC server, which contains duplicate copies of the principal database. Both the master KDC server and the slave KDC server create tickets that are used to establish authentication.
The realm can also include two additional types of SEAM servers. A SEAM network application server is a server that provides access to Kerberized applications (such as ftp, telnet and rsh). Realms can also include NFS servers, which provide NFS services by using Kerberos authentication. If you have installed SEAM 1.0 or 1.0.1, the realm might include a SEAM network application server, which provides access to Kerberized applications (such as ftp, telnet, and rsh).
The following figure shows what a hypothetical realm might contain.
Figure 13–4 A Typical Realm
- © 2010, Oracle Corporation and/or its affiliates
