Context Checking
Whereas password-protection grants all-or-nothing access, context checking allows the agent application to filter each management request individually. Context-checking may be associated with password protection to provide multiple levels of security
All management requests that arrive through a connector or protocol adaptor may be inspected by the agent application to determine if they are allowed. The management application may filter requests based on the type of request, the MBean for which they are intended, or the values that are provided in the operation.
For example, context checking could allow an agent to implement a read-only policy which refuses attribute set operations, all operation invocation, and doesn't allow MBean registration or deregistration. A more selective filter could just insure that the agent cannot be disconnected: it would disallow MBean deregistrations, stop operations, and invocations that contain null parameters, but only when applied to connector servers or protocol adaptor MBeans.
In addition, requests through connector clients may be filtered by an operation context field, which could be a password or any other identifying data. The context object is provided by the management application, and it will be sent to the connector server along with each request. The agent can verify this context and potentially reject the request if the context is considered invalid or inappropriate for the operation.
To make this context checking possible, the agent provides:
-
Stackable MBean server objects - You can insert your own code to perform context checking and filtering between the communication component and the MBean server.
-
Thread contexts - Your code can retrieve the remote application's context object which is stored in the thread object which handles the request. The context is an arbitrary object that your code can use to determine whether or not to allow the request.
Figure 2-6 Context Checking Using Stackable MBean Server Objects
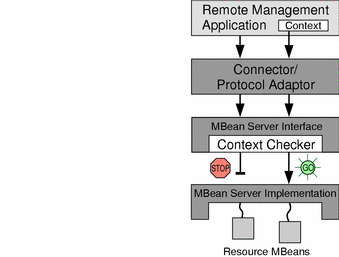
In the figure above, a context checker object has been inserted between the connector and the MBean server. Because a context checker object implements the MBeanServer interface, the connector interacts with it in exactly the same way as it did with the MBean server. This stacked object will retain a reference to the real MBean server, to which it will forward all requests that are allowed. The context checker may also perform any other action, such as log all filtered requests and trigger a notification when an invalid request is received.
For security reasons, only the agent application may insert or remove stackable MBean server objects. This operation is not exposed to management applications, who cannot even know if requests are being filtered. However, the context checker may choose to respond with an exception whose message explains why a request was denied.
- © 2010, Oracle Corporation and/or its affiliates
