Chapter 6 Configuring Solaris Bandwidth Manager with a Directory Service
Solaris Bandwidth Manager configuration information and policy information can be stored in a directory service such as Sun Directory Services 3.1. Some advantages of this approach are:
-
It is possible to update the configuration of multiple instances of Solaris Bandwidth Manager from a single point, the directory.
-
The configuration can be dynamically updated upon detection of user connections or traffic flows, for example when using the RADIUS protocol for remote access.
Sun Directory Services 3.1 Configuration
To enable Solaris Bandwidth Manager to operate with Sun Directory Services, you must carry out a certain amount of configuration on the directory itself. Do this first. You must then save the Solaris Bandwidth Manager configuration into the directory. This operation automatically creates the necessary entries for policy information in the directory.
Configuring the Sun Directory Services Server
On the Sun Directory Services server, you must perform the following operations:
-
Add the Solaris Bandwidth Manager schema files to the Sun Directory Services schema.
-
Declare the policy agent as a replica of the subtrees containing Solaris Bandwidth Manager information.
If you modify the Solaris Bandwidth Manager configuration in the directory, you must replicate the subtree containing the configuration. You must replicate all entries.
The bind Distinguished Name (DN) to use in the replication is of the form uid=login, etc, where login is the login defined in the agent.properties file of the policy agent. The password to use in the replication is the password defined in the agent.properties file. Replication mode must be push.
-
Set a replication schedule for the replication of information between the directory and the policy agents. You can set replication to immediate, which means that whenever modifications are made to entries that are within the scope of the replica, they are automatically pushed to the appropriate policy agent. Doing so is mandatory if you are working with the RADIUS protocol.
-
Define Access Control Lists (ACLs) for Solaris Bandwidth Manager information: for remote user connections, you must give the policy agent read access to at least the policyRef attribute of the entries in the remote user subtree. To enable updates to the configuration stored in the directory from batool, you must provide write access to the policy agent on all entries and attributes in the subtree containing the Solaris Bandwidth Manager configuration.
To Add the Solaris Bandwidth Manager Schema Files to the Directory Server Configuration
-
Copy the Solaris Bandwidth Manager schema files to the directory server. By default, the Solaris Bandwidth Manager schema files, policy.at.conf and policy.oc.conf, are located under /etc/opt/SUNWconn/ba/include.
-
Open the configuration file for Sun Directory Services, dsserv.conf, in a text editor. By default, this file is located under /etc/opt/SUNWconn/ldap/current.
-
In the main configuration section of dsserv.conf, include the schema files for Solaris Bandwidth Manager:
# - Main Configuration Section - # include /etc/opt/SUNWconn/ldap/current/dsserv.at.conf include /etc/opt/SUNWconn/ldap/current/dsserv.oc.conf include /etc/opt/SUNWconn/ldap/current/dsserv.acl.conf include /opt/SUNWconn/ba/include/policy.at.conf include /opt/SUNWconn/ba/include/policy.oc.conf
This include statement must contain the absolute path to the Solaris Bandwidth Manager schema files on the directory server.
-
Restart the directory server daemon, dsservd, to reload the directory configuration. This task is described in the Sun Directory Services 3.1 Administration Guide. The Schema section of the Directory Services Admin Console now lists the Solaris Bandwidth Manager object classes and attributes.
These tasks are described in detail in the Sun Directory Services 3.1 Collection.
Saving the Bandwidth Manager Configuration
Save the Solaris Bandwidth Manager configuration into the directory using the
graphical tool batool. To do so, select the Save As option from the File
menu, and choose URL. The URL dialog appears. Enter either the complete URL
in the URL location field or the individual parts of the URL in the relevant
fields in the lower pane. If you enter the complete URL, do so in this format: ldap://username:password@hostname:portnumber/distinguishedname.
If you fill in the fields in the lower pane, do so like this: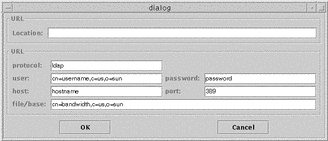
-
Enter the username as a Distinguished Name.
-
The Distinguished name of the subtree to which you want to save the file must begin with a common name. If this common name does not already exist in the directory, it is created for you.
Directory Tree for Solaris Bandwidth Manager
When you save the Solaris Bandwidth Manager configuration to the directory, a dedicated subtree is created in the directory. This section explains the structure of the entries in the Solaris Bandwidth Manager subtree.
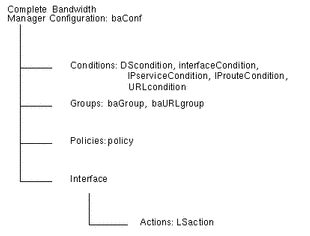
Figure 6-1 shows the tree structure and the different types of entries allowed at each level in the tree. Refer to "Object Classes" for a definition of each type of entry.
A complete configuration is stored under an entry of type baConf. The subentries stored under the baConf entry describe conditions, groups, policies, and interfaces.
A policy entry usually associates a list of conditions with a list of actions. When all the conditions are satisfied, the associated actions are performed.
Figure 6-1 Directory Information Tree Structure
There is not a one-to-one mapping between the elements of the Solaris Bandwidth Manager configuration file and the way that those elements are stored in the Directory Tree. The diagram below summarizes the way in which the mapping is carried out:
Figure 6-2 Mapping Between Solaris Bandwidth Manager and a Directory
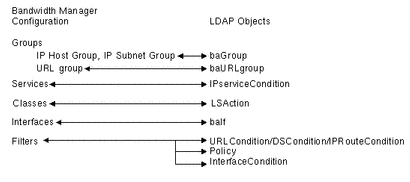
In particular, note that Filters are handled using a combination of Conditions and Policies. The condition type used depends on the content of the filter. The condition name is suffixed with -R, -I,-U, or -D, depending on the condition type.
Pre-defined services are not saved into the directory structure. Instead, if the policy agent finds a reference to a nonexistent Condition, it is assumed to be a pre-defined service.
Table 6-1 shows the allowed containment relationships for entries stored below baConf. There are no constraints on the superior class for baConf.
Table 6-1 Containment Relationships Under baConf|
Entry |
Valid Superiors |
|---|---|
|
Policy |
baConf |
|
URLCondition |
baConf, baContainer |
|
IPRouteCondition |
baConf, baContainer |
|
DSCondition |
baConf, baContainer |
|
IPServiceCondition |
baConf, baContainer |
|
IfCondition |
baConf, baContainer |
|
Group |
baConf, baContainer |
|
Classes |
baIf, baConf, baContainer |
|
baIf |
baConf |
|
baContainer |
baConf, baContainer |
Example Directory Tree
When you save the example configuration file shown in "Configuration Examples", the entry is structured like this:
Figure 6-3 Example Directory Tree
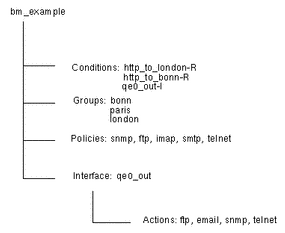
Note -
The pre-configured services, such as ftp, do not appear as conditions, as pre-configured services are not saved to the directory.
Working With a RADIUS Server
The RADIUS server provided with Sun Directory Services 3.1 offers an authentication service for remote users. For full information on the RADIUS server, refer to the documentation delivered with Sun Directory Services 3.1.
Overview
The RADIUS server provided with Sun Directory Services 3.1 is an authentication and authorization information server for a Network Access Server (NAS). A NAS is a device that provides an access point to the network for remote users connecting using SLIP, PPP or any other remote access protocol. The NAS transmits the information provided in the connection request from the remote user to the RADIUS server. The RADIUS server checks this information against the entry for the remote user in the directory. It then returns to the NAS an authorization or denial for the remote user connection. It can also provide the appropriate connection parameters for the remote user connection.
Note -
A NAS is also often referred to as a Remote Access Server (RAS) or as a RADIUS client.
Figure 6-4 summarizes the way in which RADIUS operates with Solaris Bandwidth Manager.
Figure 6-4 RADIUS Operation with Solaris Bandwidth Manager
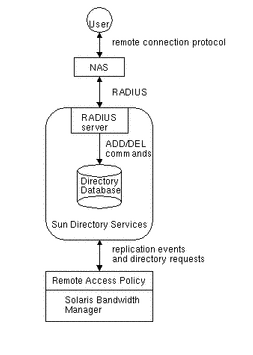
The user is an entity requesting access to network resources. In the directory database, a user is identified by a unique uid attribute. This and all other attributes describing a remote user are defined in the remoteUser object class.
The NAS is the device to which remote users connect. The NAS queries the RADIUS server for authentication status, user profiles, and authorizations. In the directory database, each NAS is identified by a unique ipHostNumber attribute. This and all other attributes describing a RADIUS client are defined in the nas object class.
The RADIUS server authenticates the NAS, then checks the remote user's identity and authorization in the directory database. It returns the user's status and configuration information to the NAS. If the RADIUS server cannot authenticate the NAS, it ignores the request -- there is no connection rejection.
Once the authentication process is complete, the NAS sends accounting information on the remote connection to the RADIUS server. This is logged dynamically in the user's directory entry. The information logged is contained in the dynamicIPaddress, dynamicSessionId, dynamicSessionCounter, and dynamicAddressBinding attributes.
This information is then replicated to the Solaris Bandwidth Manager configuration using a Replication Event.
An exchange of information between Solaris Bandwidth Manager and Sun Directory Services then takes place, in which the Solaris Bandwidth Manager configuration is updated with the dynamic information. The filters and classes that are created, are named using the relevant uid and sessionId names. If the action LSaction has the attribute queueName, no class is created.
Note -
When interoperating with Solaris Bandwidth Manager, dynamic accounting is used. Refer to the documentation delivered with Sun Directory Services for information on other approaches.
Configuration
To be able to use the RADIUS protocol, you must carry out configuration on Solaris Bandwidth Manager and on Sun Directory Services. Refer to the documentation delivered with Sun Directory Services for configuration instructions and schema information.
-
Edit the /opt/SUNWconn/ba/html/beans/QRasPolicy.html file so that Solaris Bandwidth Manager can reply to replication events.
On Sun Directory Services:
-
Enable dynamic accounting for the RADIUS server.
-
In the database, create the necessary entries for NAS devices and remote users. For each user, in addition to an object class of type remoteUser, you must create an object class of type policyAux. The policyAux object class must have the same Distinguished Name (DN) as the remoteUser object class. This is because the remoteUser object class cannot contain a policyRef attribute. The policyRef attribute must point to a valid policy.
-
Set a replication schedule for the replication of information between the directory and the policy agents. Set replication to immediate, so that whenever modifications are made to entries that are within the scope of the replica, they are automatically pushed to the policy agent.
-
Replicate the subtree containing remote user entries. If you do not want to replicate all attributes in the remote user entries, make sure that you include at least the following attributes: dynamicIPaddress, dynamicSessionID, dynamicSessionCounter.
-
Insure that Replication Events contain a Replication Password. This is the password you set when installing the Solaris Bandwidth Manager packages and is defined in the /etc/opt/SUNWconn/ba/agent.properties file. You will be prompted for this when configuring the DN of the administrator of the remote system. The DN itself is ignored.
Policy Behavior
The policyRef attribute contained in the policyAux object class for a user must point to an entry of type Policy. This can do one of the following:
-
Create a filter containing the IP address of the newly connected user.
-
Create a class and a filter containing the IP address of the newly connected user.
Creating a Filter Only
A service provider offers three classes of service: Standard, StandardPlus, and Premium. Each has a different level of guaranteed bandwidth. Administrative and other incidental traffic is handled by the root class:
|
Class Name |
Guaranteed Bandwidth |
|---|---|
|
Premium |
50% |
|
StandardPlus |
30% |
|
Standard |
10% |
User Fred Smith has a subscription to the Premium class.
On receiving traffic from Fred Smith, the policyRef attribute in the policyAux class is checked. It points to the policy "Premium." The "Premium" policy contains an LSaction "ActionPremiumClass" with the attribute queueName "Premium."
A filter is created containing Fred Smith's IP address and is added to the Premium class. Traffic from Fred Smith is then filtered into the Premium class. The filter name is the UID of Fred Smith's user entry in the directory, plus the sessionID.
It would also be possible to add conditions to the policy, specifying a service, for example.
Creating a Class and a Filter
A service provider offers three classes of service: Standard, StandardPlus, and Premium. Each has a different level of guaranteed bandwidth. Administrative and other incidental traffic is handled by the root class. From time to time, however, the service's administrators need to send high priority messages to each other. To do so, they send email from an account called admin-urgent. Doing so creates a class with a priority of 1 and a guaranteed bandwidth of 10% so that these messages are dealt with immediately.
Jane Brown needs to send an urgent message to the other administrators. To do so, she logs in as admin-urgent. On receiving traffic from admin-urgent, the policyRef atribute of the policyAux class is checked. It points to the policy Urgent. The Urgent policy contains an LSaction with the attributes ceilingRate, guaranteedRate, and queuePriority. The absence of the queueName attribute tells the Solaris Bandwidth Manager software to create a class called urgent with the specified maximum and guaranteed bandwidth and priority. A filter is then created containing the IP address from which the admin-urgent message was sent. The filter's name is composed of the UID and sessionID.
Schema Objects for Solaris Bandwidth Manager
The directory schema determines what information can be stored in the directory. See Sun Directory Services 3.1 Administration Guide for details of the default schema and how to modify it. Figure 6-5 summarizes the schema structure.
Figure 6-5 Solaris Bandwidth Manager Schema

Table 6-2 lists the attributes for each object class. (M) indicates that the attribute is mandatory and (O) that it is optional. Refer to the alphabetical list of object classes below for a detailed description of each object class. Refer to the alphabetical list of attributes for a detailed description of each attribute.
Table 6-2 Object Class Summary|
Object Class |
Attributes |
Allowed value(s) |
|---|---|---|
|
baConfState(M) |
valid/invalid |
|
|
commonName(M) |
common name |
|
|
baClConfRef(O) |
DN of generic configuration |
|
|
baTimeout(O) |
timeout in seconds |
|
|
baIfName(M) |
device name with suffix _in or _out |
|
|
baIfRate(M) |
bandwidth in bits per second |
|
|
commonName(M) |
common name |
|
|
baIfNetwork(O) |
device name |
|
|
baIfActivate(O) |
enabled, stats, tos, disabled |
|
|
none/all/direct |
||
|
baIfNonIP(O) |
ipqos/direct |
|
|
baIfRtrMac(O) |
MAC address |
|
|
baIfRtrAddr(O) |
list of IP addresses or hostnames |
|
|
commonName(M) |
common name |
|
|
groupMember(M) |
IP address |
|
|
networkMask(O) |
subnet mask in dot format |
|
|
commonName(M) |
common name |
|
|
URL |
||
|
Mask:Match expressed in binary |
||
|
device:direction, where direction is INCOMING, OUTGOING or BOTH |
||
|
sourceIPHost(O) |
IP address or hostname |
|
|
IP address or hostname |
||
|
name:mask |
||
|
name:mask |
||
|
sourceGroup(O) |
DN of entry of type baGroup |
|
|
DN entry of type baGroup |
||
|
port number(s) |
||
|
port number(s) |
||
|
source:destination |
||
|
ANY or the name of any protocol defined in the /etc/protocols file. |
||
|
ceilingRate(O) |
1:bps or 2:percentage |
|
|
1:bps or 2:percentage |
||
|
parent(O) |
classname |
|
|
previous(O) |
classname |
|
|
queueName(O) |
classname |
|
|
integer between 1 and 7 |
||
|
tosWrite(O) |
integer between 0 and 255 |
|
|
commonName(M) |
common name |
|
|
policyName(M) |
policy name |
|
|
reference to a set of policyCondition objects |
||
|
TRUE/FALSE |
||
|
reference to a set of policyAction objects |
||
|
list of keywords |
||
|
policyUsage(O) |
distinguished name |
|
|
commonName (M) |
common name |
|
|
policyActionName(M) |
name |
|
|
policyRef(M) |
reference to policy |
|
|
commonName (M) |
common name |
|
|
policy condition name |
||
|
URLmatch(O) |
URL |
|
|
pointer to baURLgroup entry |
Object Classes
This section contains an alphabetical list of the object classes that are used by Solaris Bandwidth Manager.
baConf
Mandatory attributes: baConfState, commonName (cn)
Optional attributes: baClConfRef, baTimeout
Description: Top entry of a subtree that holds a complete configuration for Solaris Bandwidth Manager
baIf
Mandatory attributes: baIfName, baIfRate, commonName (cn)
Optional attributes: baIfNetwork, baIfMulticast, baIfNonIP, baIfRtrMac, baIfRtrAddr, baIfActivate
Description: Contains the configuration parameters for an interface controlled by Solaris Bandwidth Manager
baGroup
Mandatory attributes: commonName (cn), groupMember
Optional attributes: networkMask
Description: Contains the configuration parameters for a group of hosts or subnets controlled by Solaris Bandwidth Manager
baURLGroup
Mandatory attributes: commonName (cn), URLgroupMember
Description: Contains the configuration parameters for a group of URLs controlled by Solaris Bandwidth Manager
DSCondition
Inherits from policyCondition
Mandatory attributes: none
Optional attributes: receivedDSByteCheck
Description: In the context of differentiated services, describes a condition applicable to behavior aggregate
interfaceCondition
Inherits from policyCondition
Mandatory attributes: none
Optional attributes: interfaceName
Description: Describes a condition applicable to an interface
IProuteCondition
Inherits from policyCondition
Mandatory attributes: none
Optional attributes: sourceIPHost, destinationIPHost, sourceNetwork, destinationNetwork, sourceGroup, destinationGroup
Description: Describes a condition applicable to an IP source or IP destination
IPserviceCondition
Inherits from policyCondition
Mandatory attributes: none
Optional attributes: sourcePortNumberRanges, destinationPortNumberRanges, portNumberPairs, protocolNumber
Description: Describes a condition applicable to an IP service
LSaction
Inherits from policyAction
Mandatory attributes: none
Optional attributes: ceilingRate, guaranteedRate, parent, previous, queueName, queuePriority, tosWrite
Description: Describes an action to be performed in the context of link sharing
policy
Mandatory attributes: commonName, policyName, policyConditionList, policyEnabled
Optional attributes: policyActionList, PolicyKeywords, policyUsage
Description: Describes the interaction between two or more objects
policyAction
Mandatory attributes: commonName (cn), policyActionName
Optional attributes: None
Description: Describes a set of actions to be performed when all the conditions listed by a policy have been met
policyAux
Mandatory attributes: policyRef
Optional attributes: None
Description: This object class is used to associate a policy with a remote user entry. It is an auxiliary object class which means that it can be used in conjunction with any other object class to create an entry.
policyCondition
Mandatory attributes: commonName (cn), policyConditionName
Optional attributes: None
Description: Describes a set of conditions to be met to satisfy a policy. This object class is not used as such in the Solaris Bandwidth Manager DIT. Instead, the object classes derived from it are used to create entries that describe actual conditions. These object classes are DScondition, interfaceCondition, IProuteCondition, IPserviceCondition, URLCondition.
URLcondition
Inherits from policyCondition
Optional attributes: URLmatch, URLgroupMember
Description: Describes a condition applicable to a URL
Attributes
This section contains an alphabetical list of the attributes used by Solaris Bandwidth Manager. It gives the attribute syntax, possible values, and a short definition of the attribute's purpose.
This section does not include attributes that are not specific to Solaris Bandwidth Manager such as top or common name (cn).
Table 6-3 shows the possible syntaxes for attributes, with their definitions.
Table 6-3 Attribute Syntax Definitions|
Attribute syntax |
Syntax Definition |
|---|---|
|
bin |
Stands for binary. |
|
ces |
Stands for case exact string. A case-sensitive alphanumeric string. |
|
cis |
Stands for case ignore string. A non-case-sensitive alphanumeric string. |
|
dn |
A distinguished name |
|
int |
An integer |
|
protected |
A value that has been encrypted using crypt(1) |
|
tel |
A telephone number |
|
utctime |
UTC time |
baClConfRef
Used in baConf
Description: Provides a pointer to a generic configuration.
baConfState
Used in baConf
Description: Indicates whether the configuration described by the entry is a valid one, or if it is currently being modified. This attribute can have only one of the following values: invalid, valid. When a configuration is saved to the directory, this attribute is set to invalid, any previous version of the configuration is deleted, the new one is saved, and the attribute is set back to valid.
baIfActivate
Used in baIf
Description: Indicates the status of an interface controlled by Solaris Bandwidth Manager. This attribute can have only one of the following values: enabled, stats, tos ordisabled. The meaning of these values is described in "Interface Definition".
baIfMulticast
Used in baIf
Description: Specifies how multicast packets are forwarded. This attribute can have only one of the following values: none, all or direct. The meaning of these values is described in "IP-Transparent Mode". This attribute is required if Solaris Bandwidth Manager is working in IP transparent mode.
baIfName
Used in baIf
Description: Specifies the device name of the interface described by the entry. Suffixed with _in or _out to indicate the direction of traffic handled.
baIfNetwork
Used in baIf
Description: Specifies the name of the device used to communicate with the network. This attribute is required if Solaris Bandwidth Manager is working in IP transparent mode.
baIfNonIP
Used in baIf
Description: Specifies how non-IP packets are forwarded. This attribute can have only one of the following values: ipqos or direct. The meaning of these values is described in "IP-Transparent Mode". This attribute is required if Solaris Bandwidth Manager is working in IP transparent mode.
baIfRate
Used in baIf
Description: Indicates the operating bandwidth rate associated with the interface described by the entry. Enter in bits per second.
baIfRtrAddr
Used in baIf
Description: Gives the list of IP addresses or the hostname of the router. If you specify several IP addresses, they must be separated by commas. This attribute is required if Solaris Bandwidth Manager is working in IP transparent mode.
baIfRtrMac
Used in baIf
Description: Specifies the MAC address of the router described by the entry. Can be either a hexadecimal address or a hostname listed in the ethers table. This attribute is required if Solaris Bandwidth Manager is working in IP transparent mode.
baTimeout
Used in baConf
Description: Specifies a timeout on the configuration. Expressed in seconds.
ceilingRate
Used in LSaction
Description: Indicates the maximum bandwidth allocated across a link. The value of this attribute can be expressed in bytes per second (bps) or as a percentage of bandwidth. If expressed in bytes per second, the syntax is 1:x. If expressed as a percentage, the syntax is 2:x, where x is the value in bps or a percentage.
destinationGroup
Used in IProuteCondition
Description: Provides a pointer to an entry of type baGroup.
destinationIPHost
Used in IProuteCondition
Description: Specifies the name of the destination host in an entry describing an IP route condition.
destinationNetwork
Used in IProuteCondition
Description: Specifies the name of the destination network in an entry describing an IP route condition.
destinationPortNumberRanges
Used in IPserviceCondition
Description: Specifies the port or range of ports to which the condition described by the entry applies.
flowEvent
Used in LSaction
Description: Indicates that "flow added" events are generated when a new flow is detected in the class. The value is a string used by the directory M-bean when searching for a quality of service.
groupMember
Used in baGroup
Description: Provides the address of a host or subnet to include in a group described by a baGroup entry.
guaranteedRate
Used in LSaction
Description: Indicates the guaranteed bandwidth across a link. The value of this attribute can be expressed in bytes per second (bps) or as a percentage of bandwidth. If expressed in bytes per second, the syntax is 1:x. If expressed as a percentage, the syntax is 2:x, where x is the value in bps or a percentage.
interfaceName
Used in interfaceCondition
Description: Specifies the name of the interface to which the condition described by the entry applies. The syntax is device:direction. Where device is expressed in local terms, for example hme0, eth0 and direction is INCOMING, OUTGOING or BOTH.
networkMask
Used in baConf
Description: Specifies the subnet mask of the subnet group described by the entry. The subnet mask is specified in dot format, or by the name of a subnet mask defined in the hosts file or the networks file. You cannot use the + style of specifying a netmask. When this attribute is not present, the group described by the entry is a host group. This attribute is mandatory to describe a subnet group.
parent
Used in LSaction
Description: The name of a class's parent class.
policyActionList
Used in policy
Description: Provides references to a set of policyAction objects. The actions described by the policyAction entries are performed when all the conditions defined by the policy entry have been satisfied.
policyActionName
Used in policyAction
Description: The user friendly name of the policy action described by the entry.
policyConditionList
Used in policy
Description: Provides references to a set of policyCondition objects. The policy described by the entry is applicable when this set of conditions is satisfied.
policyConditionName
Used in policyCondition
Description: The user friendly name of the policy condition described by the entry. This attribute is not a naming attribute, and therefore cannot be used in the RDN of an entry.
policyEnabled
Used in policy
Description: Indicates whether the policy described by the entry is currently enabled. This attribute can have only one of the following values: TRUE or FALSE.
policyKeywords
Used in policy
Description: Provides a list of keywords that can be used in a search for the policy entry.
policyName
Used in policy
Description: The user friendly name of the policy described by the entry. This attribute is not a naming attribute, and therefore cannot be used in the RDN of an entry.
policyRef
Used in policyAux
Description: Provides a reference to a policy. This attribute is used to associate a policy with other types of entries, for example a remote user entry.
policyUsage
Used in policy
Description: Provides guidelines for using the policy described by the entry.
portNumberPairs
Used in IPserviceCondition
Description: Indicates pairs of source and destination ports, with the following syntax: source:destination.
previous
Used in LSaction
Description: Specifies the name of the class that was verified before the current one. If the previous class was root, this is blank.
protocolNumber
Used in IPserviceCondition
Description: Provides the name of the protocol described in the condition. This attribute can have only one value and can be either ANY or the name of any protocol defined in the /etc/protocols file.
queueName
Used in LSaction
Description: Specifies the classname of the queue to which the actions described by the entry apply.
queuePriority
Used in LSaction
Description: As part of the actions described by the entry, it indicates the priority assigned to the flow.
receivedDSByteCheck
Used in DScondition
Description: Specifies a condition for traffic based on the contents of the differentiated services (DS) byte of the received packet's IP header. The format is a string of the form xxxxxxxx:xxxxxxxx, where x is 0 or 1. The left substring is a Mask, and the right substring a Match. The DS byte of the received packet's IP header is ANDed with Mask, and the result is compared against Match. Therefore, the condition can be expressed as follows:
(receivedPacketTOSbyte & Mask == Match)?
where & indicates the bitwise AND operation, and == the bitwise compare operation.
The combination of Mask and Match makes it possible to define DS byte-based profiles where certain bits in the DS byte may be ignored for the purpose of comparison.
sourceGroupRef
Used in IProuteCondition
Description: Provides a pointer to an entry of type baGroup.
sourceIPHost
Used in IProuteCondition
Description: Specifies the name of the source host in an entry describing an IP route condition.
sourceNetwork
Used in IProuteCondition
Description: Specifies the name of the source network in an entry describing an IP route condition.
sourcePortNumberRanges
Used in IPserviceCondition
Description: Specifies the port or range of ports to which the condition described by the entry applies.
tosWrite
Used in LSaction
Description: As part of the actions described by the entry, specifies the type of service provided. The value of this attribute is an integer between 0 and 255.
URLgroupMember
Used in baURLgroup
Description: Provides a pointer to a baURLgroup entry.
URLmatch
Used in URLcondition
Description: Specifies a URL used to construct a filter for the URL condition described by the entry. This URL can contain wildcards.
Naming Conventions for Solaris Bandwidth Manager
When you create a Solaris Bandwidth Manager configuration either by editing the configuration file ba.conf or by using the configuration tool batool and then saving it to a directory, naming conventions are handled automatically for you. When creating a configuration in a directory service, you must observe the following conventions:
-
policyNames, groupNames and serviceNames must be unique within a configuration. The policyName becomes the filter name when the configuration is run in Solaris Bandwidth Manager.
-
classNames must be unique within an interface. As each class is associated with a particular interface, more than one class with the same name can exist as long as they are associated with different interfaces.
- © 2010, Oracle Corporation and/or its affiliates
