Chapter 1 Introduction to Portal Server Secure Remote Access
This chapter describes Sun Java System Portal Server Secure Remote Access and the relationship between Sun Java System Portal Server (Portal Server) software and Sun Java System Portal Server Secure Remote Access components.
This chapter covers the following topics:
Overview of Secure Remote Access
Secure Remote Access software enables remote users to securely access their organization’s network and its services over the Internet. Additionally, it gives your organization a secure internet portal, providing access to content, applications, and data to any targeted audience—employees, business partners, or the general public.
Secure Remote Access software offers browser-based secure remote access to portal content and services from any remote device. Secure Remote Access is a secure access solution that is accessible to users from any device with a Java™ technology-enabled browser, eliminating the need for client software. Integration with Portal Server ensures that users receive secure encrypted access to the content and services that they have permission to access.
Secure Remote Access software is targeted toward enterprises deploying highly secure remote access portals. These portals emphasize security, protection, and privacy of intranet resources. The architecture of Secure Remote Access is well suited to these types of portals. Secure Remote Access software enables users to securely access intranet resources through the Internet without exposing these resources to the Internet.
Portal Server can function in two modes:
Open Mode
In open mode, Portal Server is installed without Secure Remote Access. Although HTTPS communication is possible in this mode, secure remote access is not possible. This means that users cannot access secure remote file systems and applications.
The main difference between an open portal and a secure portal is that the services presented by the open portal typically reside within the demilitarized zone (DMZ) and not within the secured intranet. A DMZ is a small protected network between the public Internet and a private intranet, usually demarcated with a firewall on both ends.
If the portal does not contain sensitive information (deploying public information and allowing access to free applications), then responses to access requests by a large number of users is faster than using secure mode.
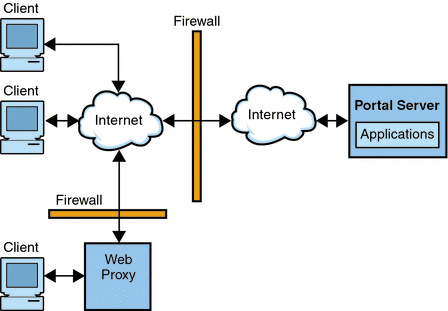
Open Mode shows Portal Server in open mode. Here, Portal Server is installed on a single server behind the firewall. Multiple clients access Portal Server across the Internet through the single firewall.
Figure 1–1 Portal Server in Open Mode
Secure Mode
Secure mode provides users with secure remote access to required intranet file systems and applications.
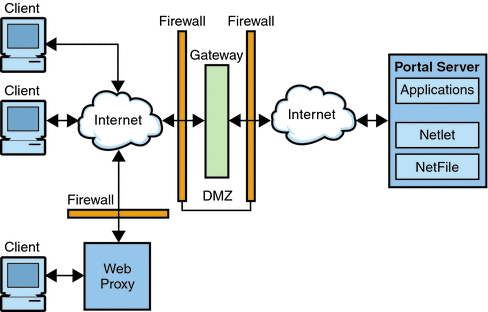
The Gateway resides in the demilitarized zone (DMZ). The Gateway provides a single secure access point to all intranet URLs and applications, thus reducing the number of ports to be opened in the firewall. All other Portal Server services such as Session, Authentication, and the standard Portal Desktop reside behind the DMZ in the secured intranet. Communication from the client browser to the Gateway is encrypted using HTTP over Secure Sockets Layer (SSL). Communication from the Gateway to the server and intranet resources can be either HTTP or HTTPS.
Secure Mode shows Portal Server with Secure Remote Access software. SSL is used to encrypt the connection between the client and the Gateway over the Internet. SSL can also be used to encrypt the connection between the Gateway and the server. The presence of the Gateway between the intranet and the Internet extends the secure path between the client and the Portal Server.
Figure 1–2 Portal Server in Secure Mode with Secure Remote Access
Additional servers and gateways can be added for site expansion. Secure Remote Access software can be configured in various ways based on the business requirement.
Secure Remote Access Services
Secure Remote Access software has five major components:
Gateway
The SRA Gateway provides the interface and security barrier between remote user sessions originating from the Internet and a corporate intranet. Gateway presents content securely from internal web servers and application servers through a single interface to a remote user.
Web servers use web-based resources such as HTML, JavaScript and XML to communicate between the client and Gateway. Rewriter is the Gateway component used to make web content available.
Application servers use binary protocol such as telnet and FTP to communicate between the client and Gateway. Netlet, which resides on the Gateway, is used for this purpose. See Chapter 2, Working with Gateway for more detail.
Rewriter
Rewriter enables end users to browse the intranet and makes links and other URL references on those pages operate correctly. Rewriter prepends the Gateway URL in the location field of the web browser, thereby redirecting content requests through the Gateway. See Chapter 3, Working with Proxylet and Rewriter for details.
NetFile
NetFile is a file manager application that allows remote access and operation of file systems and directories. NetFile includes a Java based user interface. See Chapter 4, Working with NetFile for details.
Netlet
Netlet facilitates the running of popular or company-specific applications on remote desktops in a secure manner. After you implement Netlet at your site, users can securely run common TCP/IP services, such as Telnet and SMTP, and HTTP-based applications such as pcANYWHERE or Lotus Notes. See Chapter 5, Working with Netlet for details.
Proxylet
Proxylet is a dynamic proxy server that runs on a client machine. Proxylet redirects a URL to the Gateway. It does this by reading and modifying the proxy settings of the browser on the client machine so that they point to the local proxy server or Proxylet.
Administering the Secure Remote Access
SRA software has two interfaces for administration:
-
Portal Server administration console
-
Psadmin command line
Most administration tasks are performed through the web-based Portal Server console. The Portal Server console can be accessed locally or remotely using a web browser. However, tasks such as file modification must be administered through the UNIX command-line interface.
Configuring the Secure Remote Access Attributes
Most attributes can be set using the options available under the Secure Remote Access tab in the Portal Server administration console. Any new organization or user that is created inherits these values, by default.
You can configure attributes related to Secure Remote Access at the organization, role, and user levels, with the following exceptions:
-
Conflict Resolution Level cannot be set at the user level. See Setting Conflict Resolution.
-
MIME types Configuration File Location attribute can be set only at the organization level.
Values set at the organization level are inherited by all roles and users under that organization. Values set at the user level override the values set at the organization or role levels.
You can make changes to the attribute values at the Service Configuration level. These new values are reflected only when new organizations are added.
You configure Secure Remote Access attributes on the Portal Server administration console using the following services:
-
Access Control
This service enables you to allow or restrict access to specific URLs and to manage the single sign-on feature. For more information, see Chapter 8, Configuring Access Control.
-
Gateway
Profiles (Gateway Instances) This service enables you to configure all Gateway related attributes such as Enabling components, cookie management, proxy management, security settings, performance tuning, rewriter mapping management. For more information, see Chapter 9, Configuring the Gateway .
-
NetFile
This service enables you to configure all NetFile related attributes such as common hosts, MIME types, and access to different types of hosts. For more information, see Chapter 10, Configuring NetFile.
-
Netlet
This service enables you to configure all Netlet related attributes such as Netlet rules, access to required rules, organizations and hosts, and the default algorithm. For more information, see Chapter 11, Configuring Netlet.
-
Rewriter
This service enables you to download, upload and delete all rewriter rulesets.
-
Proxylet
This service enables you to configure Proxylet related attributes such as Proxylet Applet Bind IP address and port number. For more information, see Chapter 12, Configuring Proxylet.
The Gateway does not receive notifications for attribute changes that are made while Gateway is running. Restart Gateway to ensure that updated profile attributes (belonging to the Gateway or any other service) are used by Gateway. For more information, see Configuring Gateway Attributes Using the Command Line Options.
Setting Conflict Resolution
 To Set the Conflict Resolution Level
To Set the Conflict Resolution Level
-
Log into the Portal Server administration console as administrator.
-
Select the Secure Remote Access Tab and select the required service tab: Netlet, Netfile, or Proxylet.
-
Select the Organization or Role from Select DN option.
-
Select the required Conflict Resolution Level from COS Priority drop-down box.
-
Click Save to complete.
Supported Applications
SRA supports the following applications:
Before You Begin
 To Enable the enableSRAforPortal.xml File
To Enable the enableSRAforPortal.xml File
-
Go to the /opt/SUNWportal/export/request and edit the enableSRAforPortal.xml file.
-
Modify the Host Name, port number, Portal deploy URI appropriately and save the file.
-
Execute the file from amadmin as follows:
/SUNWam/bin/amadmin -u amadmin -w -t /SUNWportal/export/request/enableSRAforPortal.xml
-
After installing the Portal Server, for example, to configure Netfile, you must enable the enableSRAforPortal.xml file.
-
Restart the Gateway.
- © 2010, Oracle Corporation and/or its affiliates
