Chapter 2 Working with Gateway
This chapter describes Gateway related concepts and information to manage the Gateway. For information on configuring the Gateway, see Chapter 9, Configuring the Gateway.
This chapter covers the following topics:
Introduction to Gateway
The Gateway provides the interface and security barrier between remote user sessions originating from the Internet and your corporate intranet. The Gateway presents content securely from internal web servers and application servers through a single interface to a remote user.
For each Gateway instance you must complete the following tasks:
Creating a Gateway Profile
A gateway profile contains all the information related to gateway configuration, such as the port on which the Gateway listens, SSL options, and proxy options. When you install a Gateway, if you choose the default values, a default gateway profile called "default" is created. A configuration file corresponding to the default profile exists at: /etc/opt/SUNWportal/platform.conf.default.
Where /etc/opt/SUNWportal is the default location for all the platform.conf.* files. For more information on the platform.conf file, see Understanding the platform.conf File.
You can:
-
Create multiple profiles, define attributes for each profile, and assign these profiles to different Gateways as required.
-
Assign a single profile to Gateway installations on different machines.
-
Assign different profiles to instances of a single Gateway running on the same machine.
Do not assign the same profile to different instances of the Gateway running on the same machine. This causes a conflict because the port numbers would be the same.
Do not specify the same port numbers in the different profiles created for the same Gateway. Running multiple instances of the same Gateway with the same port causes a conflict.
 To Create a Gateway Profile
To Create a Gateway Profile
-
Log into the Portal Server administration console as administrator.
-
Click the Secure Remote Access tab and click New Profile.
The New Profile page is displayed.
-
Enter the name of the new gateway profile.
-
Select the profile to use for creating the new profile from the drop-down list.
By default, any new profile that you create is based on the pre-packaged Default profile. If you have created a custom profile, you can select that profile from the drop-down list. The new profile inherits all the attributes of the selected profile.
The existing profile that is copied for the new one, copies the same port. Change the port for the new profile so that it does not conflict with the existing one.
-
Click OK.
The new profile is created and listed in the Profiles page.
 Caution –
Caution – Ensure that you change the port of the instance so that it does not clash with any existing port in use.
-
Telnet to the machine where the instance needs to be created. The default gateway instance is up and running at this machine.
-
Copy the /opt/SUNWportal/template/sra/GWConfig.properties.template file to a temporary location . For example, /tmp.
-
Modify the values as required.
Note –The values should match the port numbers in the gateway instance for the new profile.
-
Once complete, run the following command:
./psadmin create-sra-instance -u amadmin -f <passwordfile> -S <template file location>.template -t gateway
-
Restart the Gateway with this gateway profile name to ensure the changes to take effect:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
For more information on starting and stopping the Gateway, see Starting and Stopping the Gateway Instance. To configure the Gateway, see Chapter 9, Configuring the Gateway
Understanding the platform.conf File
The platform.conf file is located by default at:
/etc/opt/SUNWportal |
The platform.conf file contains the details that the Gateway needs. This section provides a sample platform.conf file and describes all the entries.
The advantage of including all the machine-specific details in the configuration file is that a common profile can be shared by Gateways running on multiple machines.
Here is a sample:
Tue May 30 11:51:23 IST 2006 debug.com.sun.portal.rewriter.original.level=INFO gateway.favicon= gateway.bindipaddress=10.12.154.236 debug.com.sun.portal.sra.rproxy.toFromServer.handler.java.util.logging.FileHandler.pattern= /var/opt/SUNWportal/logs/sra/default/Gateway.toFromServer.%u.%g.log gateway.port=443 rewriterproxy.jvm.flags=-ms64m -mx128m portal.server.instance=default debug.com.sun.portal.handler.java.util.logging.FileHandler.filter= gateway.jdk.dir=/usr/jdk/entsys-j2se gateway.ignoreURIList=/MSOffice/cltreq.asp,/_vti_bin/owssvr.dll debug.com.sun.portal.rewriter.rest.level=INFO gateway.trust_all_server_certs=true debug.com.sun.portal.handler.java.util.logging.FileHandler.append=true gateway.cdm.cacheCleanupTime=300000 gateway.httpurl= debug.com.sun.portal.handler.java.util.logging.FileHandler.count=1 gateway.jvm.classpath= debug.com.sun.portal.setserverlogs=false gateway.protocol=https debug.com.sun.portal.sra.rproxy.toFromServer=java.util.logging.FileHandler rewriterproxy.jvm.classpath= gateway.enable.customurl=false debug.com.sun.portal.sra.rproxy.toFromBrowser=java.util.logging.FileHandler debug.com.sun.portal.handler.java.util.logging.FileHandler.formatter=com.sun.portal. log.common.PortalLogFormatter debug.com.sun.portal.sra.rproxy.toFromBrowser.handler.java.util.logging.FileHandler.pattern= /var/opt/SUNWportal/logs/sra/default/Gateway.toFromBrowser.%u.%g.log debug.com.sun.portal.level=INFO debug.com.sun.portal.rewriter.unaffected.separatefile=true gateway.enable.accelerator=false debug.com.sun.portal.rewriter.original.separatefile=true gateway.virtualhost=nicp236.india.sun.com 10.12.154.236 debug.com.sun.portal.stacktrace=true gateway.host=nicp236.india.sun.com debug.com.sun.portal.handler.java.util.logging.FileHandler.pattern= /var/opt/SUNWportal/logs/sra/default/%logger.%sraComponentType.%u.%g.log gateway.certdir=/etc/opt/SUNWportal/cert/default gateway.sockretries=3 gateway.allow.client.caching=true debug.com.sun.portal.rewriter.unaffected.level=INFO debug.com.sun.portal.rewriter.uriinfo.separatefile=true log.config.check.period=2000 debug.com.sun.portal.rewriter.rewritten.level=INFO gateway.userProfile.cacheSize=1024 debug.com.sun.portal.rewriter.rulesetinfo.level=INFO netletproxy.jvm.classpath= gateway.userProfile.cacheSleepTime=60000 debug.com.sun.portal.rewriter.uriinfo.level=INFO debug.com.sun.portal.rewriter.rest.separatefile=true gateway.notification.url=notification debug.com.sun.portal.rewriter.rulesetinfo.separatefile=true gateway.logdelimiter=&& gateway.ignoreServerList=false gateway.jvm.flags=-ms64m -mx128m debug.com.sun.portal.handler.java.util.logging.FileHandler.limit=5000000 gateway.dsame.agent=http\://sunone216.india.sun.com\:8080/portal/RemoteConfigServlet gateway.httpsurl= gateway.retries=6 gateway.userProfile.cacheCleanupTime=300000 gateway.logging.password=X03MO1qnZdYdgyfeuILPmQ\=\= UX9x0jIua3hx1YOVRG/TLg\=\= netletproxy.jvm.flags=-ms64m -mx128m debug.com.sun.portal.rewriter.rewritten.separatefile=true gateway.user=noaccess gateway.external.ip=10.12.154.236 debug.com.sun.portal.handler=java.util.logging.FileHandler gateway.cdm.cacheSleepTime=60000 rewriterproxy.accept.from.gateways= rewriterproxy.checkacl=false |
Understanding the platform.conf File lists and describes all the fields in the platform.conf file.
Table 2–1 platform.conf File Properties
Creating Multiple Instances of a Gateway
To create multiple instances of a gateway, see Chapter 6, Installing and Configuring a Gateway With Portal Server, in Sun Java System Portal Server 7.1 Configuration Guide
Creating Multi-homed Gateway Instances
If you are creating multi-homed gateway instances, that is multiple gateways on one Portal Server, you must modify the platform.conf file as follows:
gatewaybindipaddress = 0.0.0.0
Creating Gateway Instances Using the Same LDAP
If you are creating multiple gateway instances that use the same LDAP, after creating the first Gateway on all subsequent Gateways:
In /etc/opt/SUNWam/config/, modify the following areas in AMConfig-instance-name.properties to be consistent with the first installed instance of the Gateway:
 To Create Gateway Instances Using the Same LDAP
To Create Gateway Instances Using the Same LDAP
-
Replace the key that is used to encrypt and decrypt passwords with the same string used for the first Gateway.
am.encryption.pwd= string_key_specified_in gateway-install
-
Replace the key that is the shared secret for application authentication module:
com.iplanet.am.service.secret= string_key_specified_in gateway-install
-
In /etc/opt/SUNWam/config/ums modify the following areas in serverconfig.xml to be consistent with the first installed instance of Portal Server:
<DirDN> cn=puser,ou=DSAME Users,dc=sun,dc=net</DirDN>
<DirPassword>string_key_specified_in gateway-install</DirPassword>
<DirDN>cn=dsameuser,ou=DSAME Users,dc=sun,dc=net</DirDN>
<DirPassword>string_key_specified_in gateway-install </DirPassword>
-
Restart Access Manager services.
Starting and Stopping the Gateway Instance
By default, the Gateway starts as user noaccess.
 To Start the Gateway Instances
To Start the Gateway Instances
-
After installing the Gateway and creating the required profile, run the following command to start the Gateway:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
default — is the default gateway profile that is created during installation. You can create your own profiles later, and restart the Gateway with the new profile. See Creating a Gateway Profile.
Note –Replace the <profile name> with an appropriate profile name to start other instances of the Gateway.
Restarting the server (the machine on which the Gateway instances are configured) restarts all instances of the Gateway.
Ensure that no backed up profiles are present in the /etc/opt/SUNWportal directory.
-
Run the following command to check if the Gateway is running on the specified port:
netstat -an | grep port-number
The default Gateway port is 443.
 To Stop the Gateway
To Stop the Gateway
-
Use the following command to stop the Gateway:
./psadmin stop-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
Note –Replace the <profile name> with an appropriate profile name to start other instances of the Gateway.
-
Run the following command to verify if any of the Gateway processes are still running:
/usr/bin/ps -ef | grep entsys
 To Start and Stop Gateway Using Management Console
To Start and Stop Gateway Using Management Console
-
Select the Secure Remote Access tab.
-
Click the Manage Instances submenu.
-
Under SRA Proxy instances, select an instance.
Restarting the Gateway
Normally, you do not need to restart the Gateway. You need to restart only if any of the following events occur:
-
You have created a new profile and need to assign the new profile to the Gateway.
-
You have modified some attributes in the existing profile and need the changes to take effect.
-
Gateway crashes due errors such as OutOfMemory error.
-
Gateway stops responding and does not service any requests.
 To Restart the Gateway with a Different Profile
To Restart the Gateway with a Different Profile
-
Restart the Gateway:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
 To Restart the Gateway
To Restart the Gateway
-
In a terminal window, connect as root and do one of the following:
-
Start the watchdog process:
./psadmin sra-watchdog -u uid -f password-filename -t instance-type on
[--adminuser | -u] uid
Specifies the administrator's distinguished name (DN) or user ID.
[-passwordfile | -f] password-filename
Specifies the administrator's password in the password file.
[--type | -t] instance-type
Specifies the type of the Secure Remote Access instance. Enter: gateway, nlproxy, or rwproxy.
For information on watchdog command, see the Sun Java System Portal Server Command Line Reference Guide.
This creates an entry in the crontab utility and the watchdog process is now active. The watchdog monitors all running instances of a Gateway on a particular machine and Gateway port and restarts the Gateway if it goes down.
-
To Configure the Gateway Watchdog
You can configure the time interval at which the watchdog monitors the status of the Gateway. This time interval is set to 60 seconds by default. To change this, edit the following line in the crontab utility:
0-59 * * * * gateway-install-root/SUNWportal/bin/ /var/opt/SUNWportal/.gw. 5 > /dev/null 2>&1 |
See the crontab man page to configure the crontab entries.
Specifying a Virtual Host
A virtual host is an additional hostname that points to the same machine IP and a host name. For example, if a host name a.b.c points to the host IP address 192.155.205.133, you can add another host name c.d.e which points to the same IP address.
 To Specify a Virtual Host
To Specify a Virtual Host
-
Login as root and edit the platform.conffile of the required Gateway instance:
/etc/opt/SUNWportal/platform.conf.gateway-profile-name
-
Add the following entries:
gateway.virtualhost=fully-qualified-gateway-host gateway-ip-address fully- qualified-reverse-proxyhost
gateway.enable.customurl=true (This value is set to false by default.)
-
Restart the Gateway:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
If these values are not specified, the Gateway defaults to normal behavior.
Specifying a Proxy to Contact Access Manager
You can specify a proxy host to be used by the Gateway to contact SRA Core (RemoteConfigServlet) that is deployed over the Portal Server. This proxy is used by the Gateway to reach the Portal Server and Access Manager.
 To Specify a Proxy
To Specify a Proxy
-
From the command-line, edit the following file:
/etc/opt/SUNWportal/platform.conf.gateway-profile-name
-
Add the following entries:
http.proxyHost=proxy-host http.proxyPort=proxy-port http.proxySet=true
-
Restart the Gateway to use the specified proxy for requests made to the server:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
Using Web Proxies
You can configure the Gateway to contact HTTP resources using third party web proxies. Web proxies reside between the client and the Internet.
Web Proxy Configuration
Different proxies may be used for different domains and subdomains. These entries tell the Gateway which proxy to use to contact specific subdomains in specific domains. The proxy configuration specified in the Gateway works as follows:
-
Creates a list of domains and subdomains along with the required proxies in the Proxies for Domains and Subdomains field in the Gateway service.
-
With the Use Proxy option enabled:
-
The proxies specified in the Proxies for Domains and Subdomains field are used for the specified hosts.
-
To enable direct connections for certain URLs within the domains and subdomains specified in the Proxies for Domains and Subdomains list, specify these URLs in the Do Not Use Web Proxy URLS field.
With the Use Proxy option disabled:
-
To ensure that proxies are used for certain URLs within the domains and subdomains specified in the Proxies for Domains and Subdomains field, specify these URLs in the Use Webproxy URLs list.
Although the Use Proxy option is disabled, a proxy is used to connect to the URLs listed under Use Webproxy URLs. The proxies for these URLs are obtained from the Proxies for Domains and Subdomains list.
Web Proxy Configuration shows how the web proxy information is resolved based on the proxy configuration in the Gateway service.
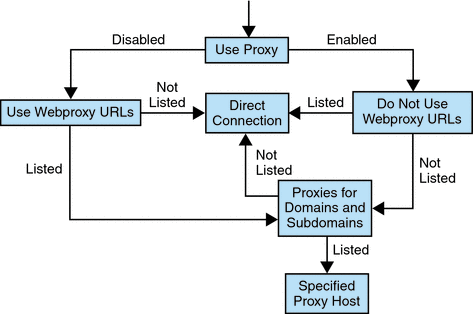
In Web Proxy Configuration, if Use Proxy is enabled, and the requested URL is listed in the Do Not Use Webproxy URLs list, the Gateway connects to the destination host directly.
If Use Proxy is enabled, and the requested URL is not listed in the Do Not Use Webproxy URLs list, the Gateway connects to the destination host through the specified proxy. The proxy, if specified, is looked up in the Proxies for Domains and Subdomains list.
If Use Proxy is disabled, and the requested URL is listed in the Use Webproxy URLs list, the Gateway connects to the destination host using the proxy information in the Proxies for Domains and Subdomains list.
If Use Proxy is disabled, and the requested URL is not listed in the Use Webproxy URLs list, the Gateway connects to the destination host directly.
If none of the above conditions are met, and a direct connection is not possible, the Gateway displays an error saying that connection is not possible.
-
Note –
If you are accessing the URL through the Bookmark channel of the standard Portal Desktop, and none of the above conditions are met, the Gateway sends a redirect to the browser. The browser accesses the URL using its own proxy settings.
Syntax
domainname [web_proxy1:port1]|subdomain1 [web_proxy2:port2]| |
Example
sesta.com wp1:8080|red wp2:8080|yellow|* wp3:8080 |
* is a wild card that matches everything
where,
sesta.com is the domain name and wp1 is the proxy to contact on port 8080.
red is a subdomain and wp2 is the proxy to contact on port 8080.
yellow is a subdomain. Since no proxy is specified, the proxy specified for the domain is used, that is, wp1 on port 8080.
* indicates that for all other subdomains wp3 needs to be used on port 8080.
Note –
Port 8080 is used by default if you do not specify a port.
Processing the Web Proxy Information
When a client tries to access a particular URL, the host name in the URL is matched with the entries in the Proxies for Domains and Subdomains list. The entry that matches the longest suffix of the requested host name is considered. For example, consider that the requested host name is host1.sesta.com
-
The Proxies for Domains and Subdomains is scanned for host1.sesta.com. If a matching entry is found, the proxy specified against this entry is used to connect to this host.
-
Else, the list is scanned for *.sesta.com. If an entry is found, the corresponding proxy is used.
-
Else, the list is searched for sesta.com. If an entry is found, the corresponding proxy is used.
-
Else, the list is searched for *.com. If an entry is found, the corresponding proxy is used.
-
Else the list is searched for com. If an entry is found, the corresponding proxy is used.
-
Else the list is searched for *. If an entry is found, the corresponding proxy is used.
-
Else, a direct connection is attempted.
Consider the following entries in the Proxies for Domains and Subdomains list:
com p1| host1 p2 | host2 | * p3 sesta.com p4 | host5 p5 | * p6 florizon.com | host6 abc.sesta.com p8 | host7 p7 | host8 p8 | * p9 host6.florizon.com p10 host9.sesta.com p11 siroe.com | host12 p12 | host13 p13 | host14 | * p14 siroe.com | host15 p15 | host16 | * p16 * p17 |
The Gateway internally maps these entries into a table as shown in Processing the Web Proxy Information.
Table 2–2 Mapping of Entries in the Proxies for Domains and Subdomains List|
Number |
Entry in Proxies for Domains and Subdomains List |
Proxy |
Description |
|---|---|---|---|
|
1 |
com |
p1 |
As specified in the list. |
|
2 |
host1.com |
p2 |
As specified in the list. |
|
3 |
host2.com |
p1 |
The proxy for the domain is used as no proxy is specified against host2. |
|
4 |
*.com |
p3 |
As specified in the list. |
|
5 |
sesta.com |
p4 |
As specified in the list. |
|
6 |
host5.sesta.com |
p5 |
As specified in the list. |
|
7 |
*.sesta.com |
p6 |
As specified in the list. |
|
8 |
florizon.com |
Direct |
See the description for entry 14 for details. |
|
9 |
host6.florizon.com |
– |
See the description for entry 14 for details. |
|
10 |
abc.sesta.com |
p8 |
As specified in the list. |
|
11 |
host7.abc.sesta.com |
p7 |
As specified in the list. |
|
12 |
host8.abc.sesta.com |
p8 |
As specified in the list. |
|
13 |
*.abc.sesta.com |
p9 |
As specified in the list. For all hosts other than host7 and host8 under the abc.sesta.com domain, p9 is used as the proxy. |
|
14 |
host6.florizon.com |
p10 |
This entry is the same as entry 9. Entry 9 indicates a direct connection, whereas this entry indicates that proxy p10 should be used. In a case with two entries such as this, the entry with the proxy information is considered as the valid entry. The other entry is ignored. |
|
15 |
host9.sesta.com |
p11 |
As specified in the list. |
|
16 |
siroe.com |
Direct |
A direct connection is attempted because no proxy is specified for siroe.com, . |
|
17 |
host12.siroe.com |
p12 |
As specified in the list. |
|
18 |
host13.siroe.com |
p13 |
As specified in the list. |
|
19 |
host14.siroe.com |
Direct |
A direct connection is attempted because no proxy is specified for host14. |
|
20 |
*.siroe.com |
p14 |
See the description for entry 23. |
|
21 |
host15.siroe.com |
p15 |
As specified in the list. |
|
22 |
host16.siroe.com |
Direct |
A direct connection is attempted because no proxy is specified for host16 or siroe.com. |
|
23 |
*.siroe.com |
p16 |
Similar to entry 20. But the proxies specified are different. In such a case, the exact behavior of the Gateway is not known. Either of the two proxies may be used. |
|
24 |
* |
p17 |
If no other entry matches the requested URL, p17 is used as the proxy. |
Note –
Instead of separating the proxy entries in the Proxies for Domains and Subdomains list with the | symbol, it may be simpler to have individual entries in the list. For example, instead of an entry such as:
sesta.com p1 | red p2 | * p3 |
you can specify it as:
sesta.com p1 red.sesta.com p2 *.sesta.com p3 |
This makes it easier to trap repeated entries or any other ambiguities.
Rewriting Based on the Proxies for Domains and Subdomains List
The entries in the Proxies for Domains and Subdomains list are also used by Rewriter. Rewriter rewrites all URLs whose domains match the domains listed in the Proxies for Domains and Subdomains list.
The * entry in the Proxies for Domains and Subdomains list is not considered for rewriting. For example, in the sample provided in Processing the Web Proxy Information, entry 24 is not considered.
For information on Rewriter, see Chapter 3, Working with Proxylet and Rewriter .
Default Domain and Subdomain
When the destination host in the URL is not a fully qualified host name, the default domain and subdomain are used to arrive at the fully qualified name.
Assume that the entry in the Default Domains field of the administration console is:
red.sesta.com |
Note –
You need to have the corresponding entry in the Proxies for Domains and Subdomains list.
In the example above, sesta.com is the default domain and the default subdomain is red.
If the requested URL is host1, this is resolved to host1.red.sesta.com using the default domain and subdomain. The Proxies for Domains and Subdomains list is then looked up for host1.red.sesta.com.
Using Automatic Proxy Configuration
To ignore the information in the Proxies for Domains and Subdomains list, enable the Automatic Proxy Configuration feature.
Please note the following when using a Proxy Auto Configuration (PAC) file:
-
Portal Server, Gateway, Netlet, and Proxylet use Rhino software to parse the PAC file. You can install the SUNWrhino package from the Java Enterprise System Accessory CD.
This package contains the js.jar file which must be present in the /usr/share/lib directory. Add this directory to the webserver/appserver class path on the Gateway and Portal Server machine, otherwise the Portal Server, Gateway, Netlet, and Proxylet cannot parse the PAC file.
-
The js.jar must be present in the $JRE_HOME/lib/ext directory on the Gateway machine, otherwise the Gateway cannot parse the PAC file.
-
Gateway fetches the PAC file at bootup from the location specified in the gateway profile Automatic Proxy Configuration File location field.
-
Gateway uses the URLConnection API to reach this location. If the proxy needs to be configured to reach the Gateway, the proxy needs to be configured in the following way:
-
From the command-line, edit the following file:
/etc/opt/SUNWportal/platform.conf.gateway-profile-name
-
Add the following entries:
http.proxyHost=web-proxy-hostname
http.proxyPort=web-proxy-port
http.proxySet=true
-
Restart the Gateway to use the specified proxy:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
-
-
If PAC file initialization fails, then the Gateway uses the information in the Proxies for Domains and Subdomains list.
-
If "" (empty string) or "null" is returned from the PAC file, then the Gateway assumes that the host does not belong to the intranet. This is similar to the host not being in the Proxies for Domains and Subdomains list.
If you want the Gateway to use a direct connection to the host, return "DIRECT". See Example with Either DIRECT or NULL Return.
-
Gateway only uses the first proxy returned when multiple proxies are specified. It does not try to failover or loadbalance among the various proxies specified for a host.
-
Gateway ignores SOCKS proxies and attempts a direct connection and assumes that the host is part of the intranet.
-
To specify a proxy to be used to reach any host not part of the intranet, use the proxy type STARPROXY. This is an extension of the PAC file format and is similar to the entry * proxyHost:port in Proxies for Domains and Subdomains section of the gateway profile. See Example with STARPROXY Return
Sample PAC File Usage
The following examples show the URLs listed in the Proxies for Domains and Subdomains list and the corresponding PAC file.
Example with Either DIRECT or NULL Return
Using these proxies for domains and subdomains:
*intranet1.com proxy.intranet.com:8080
intranet2.com proxy.intranet1.com:8080
the corresponding PAC file is:
// Start of the PAC File
function FindProxyForURL(url, host) {
if (dnsDomainIs(host, ".intranet1.com")) {
return "DIRECT";
}
if (dnsDomainIs(host, ".intranet2.com")) {
return "PROXY proxy.intranet1.com:8080";
}
return "NULL";
}
//End of the PAC File
|
Example with STARPROXY Return
Using these proxies for domains and subdomains:
intranet1.com
intranet2.com.proxy.intranet1.com:8080
internetproxy.intranet1.com:80
the corresponding PAC file is:
// Start of the PAC File
function FindProxyForURL(url, host) {
if (dnsDomainIs(host, ".intranet1.com")) {
return "DIRECT";
}
if (dnsDomainIs(host, ".intranet2.com")) {
return "PROXY proxy.intranet1.com:8080;" +
"PROXY proxy1.intranet1.com:8080";
}
return "STARPROXY internetproxy.intranet1.com:80";
}
//End of the PAC File
|
In this case, if the request is for a host in .intranet2.com domain, the Gateway contacts proxy.intranet1.com:8080. If proxy.intranet1.com:8080 is down, the request fails. The Gateway does not failover and contacts proxy1.intranet1.com:8080.
Specifying PAC File Location
The format for specifying the location of the PAC file depends upon it’s location as follows:
-
If the PAC file resides on a Webserver, enter the PAC URL as:
http://hostname/pacfile_name.pac
-
If the pacfile is a local file (for example, c:\\pacfile\\sample.pac), for Java 1.4.1_x, enter the PAC URL as:
file://c:/pacfile/sample.pac
-
If the PAC file is a local file (for example, c:\\pacfile\\sample.pac), for Java 1.4.2_x, enter the PAC URL as:
file:///c:/pacfile/sample.pac
Adding Services in Separate Sessions
When you add Portal Server services in separate sessions, ensure that:
-
All Portal Servers are listed under Gateway > Core in the Portal Server administration console.
-
All Portal Server URLs are listed in the Non-authenticated URLs under Gateway > Security.
Using a Netlet Proxy
Netlet packets are decrypted at the Gateway and sent to the destination servers. However, the Gateway needs to access all Netlet destination hosts through the firewall between the demilitarized zone (DMZ) and the intranet. This requires opening a large number of ports in the firewall. The Netlet proxy can be used to minimize the number of open ports in the firewall.
The Netlet proxy enhances the security between the Gateway and the intranet by extending the secure tunnel from the client, through the Gateway to the Netlet proxy that resides in the intranet. With the proxy, Netlet packets are decrypted by the proxy and then sent to the destination.
The advantages of using Netlet proxy are:
-
To add an additional layer of security.
-
To minimize the use of extra IP addresses and ports from the Gateway through an internal firewall in a significantly sized deployment environment.
-
To restrict the number of open ports between the Gateway and the Portal Server to 1. This port number can be configured during installation.
-
To extend the secure channel between the client and the Gateway, up to the Portal Server as shown in the "With a Netlet Proxy Configured" section of Using a Netlet Proxy. The Netlet proxy offers improved security benefits through data encryption but may increase the use of system resources. See the Sun Java System Installation Guide for information on installing the Netlet proxy.
You can:
-
Choose to install the Netlet proxy on the Portal Server node or on a separate node.
-
Install multiple Netlet proxies and configure them for a single Gateway using the administration console. This is useful in load balancing.
-
Configure multiple instances of the Netlet proxy on a single machine.
-
Point multiple instances of the Gateway to a single installation of the Netlet proxy.
-
Tunnel Netlet through a web proxy.
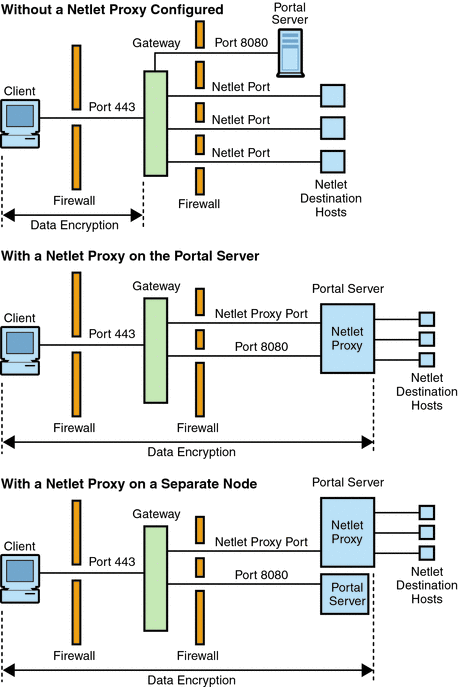
Using a Netlet Proxy shows three sample implementations of the Gateway and the Portal Server with and without a Netlet proxy installed. The components include a client, two firewalls, the Gateway that resides between the two firewalls, Portal Server, and Netlet destination servers.
The first scenario shows the Gateway and Portal Server without a Netlet proxy installed. Here the data encryption extends only from the client to the Gateway. A port is opened in the second firewall for each Netlet connection request.
The second scenario shows the Gateway and Portal Server with a Netlet proxy installed on Portal Server. In this case, the data encryption extends from the client all the way to the Portal Server. Since all Netlet connections are routed through a Netlet proxy, only one port needs to be opened in the second firewall for Netlet requests.
The third scenario shows the Gateway and the Portal Server with a Netlet proxy installed on a separate node. Installing a Netlet proxy on a separate node reduces the load on the Portal Server node. Here again, only two ports need to be opened in the second firewall. One port services requests to the Portal Server, and the other port routes Netlet requests to the Netlet proxy server.
Figure 2–1 Implementation of Netlet Proxy
Creating Instances of a Netlet Proxy
 To create a Netlet Proxy instance
To create a Netlet Proxy instance
-
Telnet to the machine where the instance needs to be created. The default gateway instance is up and running at this machine.
-
Copy the /opt/SUNWportal/template/sra/NLPConfig.properties.template file to a temporary location . For example, /tmp.
-
Modify the values as required in the file for the new profile.
-
Once complete, run the following command:
./psadmin create-sra-instance -u amadmin -f <passwordfile> -S <template file location>.template -t nlproxy
-
Start the new instance of the Netlet proxy with the required gateway profile name to ensure that the changes take effect:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t nlproxy
Enabling a Netlet Proxy
You enable a Netlet proxy through the Gateway service using the Portal Server administration console. .
Restarting a Netlet Proxy
You can configure a Netlet proxy to restart whenever the proxy is killed accidentally. You can schedule a watchdog process to monitor a Netlet proxy and restart it if it goes down.
You can also restart a Netlet proxy manually.
 To Restart a Netlet Proxy
To Restart a Netlet Proxy
-
In a terminal window, connect as root and do one of the following:
-
Start the watchdog process:
psadmin sra-watchdog -u uid -f password-filename -t instance-type on
Enter nlproxy in place of the instance-type. For more information on this command, see the Sun Java Portal Server Command Line Reference Guide.
This creates an entry in the crontab utility and the watchdog process is now active. The watchdog monitors the Netlet proxy port and brings up the proxy if it goes down.
-
Start a Netlet proxy manually:
psadmin start-sra-instance -u uid -f password-filename -N sra-instance-name -t instance-type
Enter nlproxy in place of the instance-type. This the profile name corresponding to the required Netlet Proxy instance. For more information on this command, see the Sun Java Portal Server Command Line Reference Guide.
-
To Configure a Netlet Proxy Watchdog
You can configure the time interval at which the watchdog monitors the status of a Netlet proxy. This time interval is set to 60 seconds by default. To do this, edit the following line in the crontab utility:
0-59 * * * * netlet-install-dir/bin/checkgw /var/opt/SUNWportal/.gw 5 > /dev/null 2>&1
Using a Rewriter Proxy
Rewriter proxy is installed in the intranet. Instead of trying to retrieve the contents directly, the Gateway forwards all the requests to Rewriter proxy which fetches and returns the contents to the Gateway.
The advantages of using a Rewriter proxy are:
-
If a firewall exists between the Gateway and server, the firewall needs to open only two ports - one between the Gateway and Rewriter proxy, and another between the Gateway and the Portal Server.
-
HTTP traffic is now secure between the Gateway and the intranet even if the destination server only supports HTTP protocol (no HTTPS).
If you do not specify a Rewriter proxy, the Gateway component makes a direct connection to intranet computers when a user tries to access one of those intranet computers.
If you are using the Rewriter proxy as a load balancer, be sure that the platform.conf.instance_name for Rewriter points to the load balancer URL. Also ensure that the load balancer host is specified in the Portal Servers list.
If you have multiple instances of Rewriter proxies for each Gateway instance (not necessarily on the portal node), enter the details for each Rewriter proxy in the form of host-name:port in the platform.conf file, rather than a single port entry for the Rewrite proxy.
Creating Instances of a Rewriter Proxy
Use the rwpmultiinstance script to create a new instance of a Rewriter proxy on the Portal Server node. Run this script after the gateway profile has been created.
 To Create a Rewriter Proxy Instance
To Create a Rewriter Proxy Instance
-
Telnet to the machine where the instance needs to be created. The default gateway instance is up and running at this machine.
-
Copy the /opt/SUNWportal/template/sra/GWConfig.properties.template file to a temporary location . For example, /tmp.
-
Modify the values as required in the file for the new profile.
-
Once complete, run the following command:
./psadmin create-sra-instance -u amadmin -f <passwordfile> -S <template file location>.template -t rwproxy
-
Start the new instance of the Rewirter Proxy with the required gateway profile name to ensure that the changes take effect:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t rwproxy
Enabling a Rewriter Proxy
Enable a Rewriter proxy through the Gateway service under SRA Configuration in the Access Manager administration console.
Restarting a Rewriter Proxy
You can configure to restart Rewriter proxy whenever the proxy is killed accidentally. You can schedule a watchdog process to monitor and restart it if this happens.
You can also restart a Rewriter proxy manually.
 To Restart a Rewriter Proxy
To Restart a Rewriter Proxy
-
In a terminal window, connect as root and do one of the following:
-
Start the watchdog process:
psadmin sra-watchdog -u uid -f password-filename -t instance-type on
Enter rwproxy in place of the instance-type. For more information on this command, see the Sun Java Portal Server Command Line Reference Guide.
This creates an entry in the crontab utility and the watchdog process is now active. The watchdog monitors the Rewriter Proxy port and brings up the proxy if it goes down.
-
Start a Rewriter Proxy manually:
start-sra-instance -u uid -f password-filename -N sra-instance-name -t instance-type
Enter rwproxy in place of the instance-type. This the profile name corresponding to the required Rewritter Proxy instance. For more information on this command, see the Sun Java Portal Server Command Line Reference Guide.
-
To Configure a Rewriter Proxy Watchdog
You can configure the time interval at which the watchdog monitors the status of the Rewriter proxy. This time interval is set to 60 seconds by default. To do this, edit the following line in the crontab utility:
0-59 * * * * rewriter-proxy-install-root/bin/checkgw /var/opt/SUNWportal/.gw 5 > /dev/null 2>&1
Using a Reverse Proxy with the Gateway
A proxy server serves Internet content to the intranet, while a reverse proxy serves intranet content to the Internet. Deployments of reverse proxies can be configured to serve the Internet content to achieve load balancing and caching.
If the deployment has a third-party reverse proxy in front of the Gateway, the response has to be rewritten with the reverse proxy's URL instead of the Gateway's URL. For this, the following configurations are needed.
 To Enable a Reverse Proxy
To Enable a Reverse Proxy
-
Log in as root and edit the platform.conf file of the required Gateway instance:
/etc/opt/SUNWportal/platform.conf.gateway-profile-name
-
Add the following entries:
gateway.virtualhost=fully-qualified-gateway-host gateway-ip-address fully- qualified-reverse-proxyhost
gateway.enable.customurl=true (This value is set to false by default.)
gateway.httpurl=http reverse-proxy-URL
gateway.httpsurl=https reverse-proxy-URL
gateway.httpurl is used to rewrite the response for the request received at the port which is listed as HTTP port in the gateway profile.
gateway.httpsurl is used to rewrite the response for the request received at the port which is listed as HTTPS port in the gateway profile.
-
Restart the Gateway:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
If these values are not specified, the Gateway defaults to normal behavior.
Obtaining Client Information
When the Gateway forwards a client request to any internal server, it adds HTTP headers to the HTTP request. You can use these headers to obtain additional client information and detect the presence of the Gateway.
To view the HTTP request headers, set the entry in the platform.conf file to gateway.error=message, then use the request.getHeader() from the servlet API. The following table lists the information in the HTTP headers.
Table 2–3 Information in HTTP Headers
Using Authentication Chaining
Authentication chaining provides a higher level of security over the regular mechanism of authentication. You can enable users to be authenticated against more than one authentication mechanism.
The procedure described here is only for enabling authentication chaining along with a Personal Digital Certificate (PDC) authentication at the Gateway. For information on authentication chaining without PDC authentication at the Gateway, see the Access Manager Administration Guide.
For example, if you chain the PDC and Radius authentication modules, the user will have to authenticate against all three modules to access the standard Portal Desktop.
Note –
When enabled, PDC is always the first authentication module to be presented to the user.
 To Add Authentication Modules to an Existing PDC Instance
To Add Authentication Modules to an Existing PDC Instance
-
Login to the Access Manager administration console as administrator.
-
Select the required organization.
-
Select Services from the View drop-down box.
The services are displayed.
-
Click Authentication Configuration.
The Service Instance List is displayed.
-
Click Gatewaypdc.
The Gatewaypdc properties page is displayed.
-
Click Edit.
The Add Module page is displayed.
-
Select Module Name and set Flag to Required.
-
Click OK.
-
Click Save after adding one or more modules.
-
Click Save in the gatewaypdc properties page.
-
Restart the Gateway for the changes to take effect:
gateway-install-location/SUNWportal/bin/psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
Using Wild Card Certificates
A wild card certificate accepts a single certificate with a wild card character in the fully-qualified DNS name of the host.
With the certificate multiple hosts within the same domain are secured. For example, a certificate for *.domain.com can be used for abc.domain.com, and abc1.domain.com. This certificate is valid for any host in the domain.com domain.
Disabling Browser Caching
As the Gateway component provides secure access to back end corporate data from any location using just a web browser, it may be necessary that the information not be cached locally by the client.
You can disable caching of pages redirected through the Gateway by modifying the attribute in the platform.conf file of the specific Gateway.
Disabling this option can have an impact on the Gateway performance. Every time the standard Portal Desktop is refreshed, the Gateway has to retrieve everything referenced by the page, such as images which may have been previously cached by the browser. However, by enabling this feature, remotely accessing secure content will not leave a cached footprint on the client site. This could outweigh performance implications if the corporate network is being accessed from an Internet cafe or similar remote location that is not under corporate IT control.
 To Disable Browser Caching
To Disable Browser Caching
-
Login as root and edit the platform.conf file of the required Gateway instance:
/etc/opt/SUNWportal/platform.conf.gateway-profile-name
-
Edit the following line:
gateway.allow.client.caching=true
This value is set to true by default. Change the value to false to disable browser caching at the client side.
-
Restart the Gateway:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
Customizing the Gateway Service User Interface
This section discusses the various property files that can be edited.
Modifying the srapGateway.properties File
You can edit this file for the following purposes:
-
Customize the error messages that may appear when the Gateway is running.
-
HTML-CharSets=ISO-8859-1 specifies the character set that was used to create this file.
-
The number in braces (for example, {0}) indicates that the value displayed at run time. You can change the label associated with this number, or rearrange the labels as required. Ensure that the label corresponds to the message that to be displayed since the number and the message are associated.
Customize the log information.
By default the srapGateway.properties file is located under the portal-server-install-root/SUNWportal/locale directory. All messages that appear on the Gateway machine (Gateway related messages) are located in this file, irrespective of the language of the messages.
If you need to change the language of the messages that appear on the client standard Portal Desktop, copy this file into the respective locale directory, for example portal-server-install-root/SUNWportal/locale_en_US.
-
Modifying the srapgwadminmsg.properties File
You can edit this file for the following reasons:
-
Customize the labels that appear on buttons for the Gateway service on the administration console.
-
Customize the status messages and error messages that appear when you are configuring the Gateway.
Sharing LDAP Directories
When two instances of Portal Server and Access Manager servers share the same LDAP directories, please use this workaround for all subsequent Portal Server, Access Manager, and Gateways:
 To Share LDAP Directories
To Share LDAP Directories
-
Modify the following areas in AMConfig.properties to synchronize with the first installed instance of Portal Server and Access Manager servers:
# The key that will be used to encrypt and decrypt passwords. am.encryption.pwd=t/vnY9Uqjf12NbFywKuAaaHibwlDFNLO <== REPLACE THIS STRING WITH THE ONE FROM FIRST PORTAL INSTALL
/* The following key is the shared secret for application auth module */ com.iplanet.am.service.secret=AQICxIPLNc0WWQRVlYZN0PnKgyvq3gTU8JA9 <== REPLACE THIS STRING WITH THE ONE FROM FIRST PORTAL INSTALL
-
In /etc/opt/SUNWam/config/ums modify the following areas in serverconfig.xml to be insync with the first installed instance of Portal Server and Access Manager server:
<DirDN> cn=puser,ou=DSAME Users,dc=sun,dc=net </DirDN> <DirPassword> AQICxIPLNc0WWQT22gQnGgnCp9rUf+FuaqpY <== REPLACE THIS STRING WITH THE ONE FROM FIRST PORTAL INSTALL </DirPassword> <DirDN> cn=dsameuser,ou=DSAME Users,dc=sun,dc=net </DirDN> <DirPassword> AQICxIPLNc0WWQT22gQnGgnCp9rUf+FuaqpY <== REPLACE THIS STRING WITH THE ONE FROM FIRST PORTAL INSTALL </DirPassword> -
Restart the Access Manager services.
Using Federation Management
Federation Management enables users to aggregate their local identities so that they have one network identity. Federation Management uses the network identity to allow users to login at one service provider’s site and access other service provider’s sites without having to re-authenticate their identity. This is referred to as single sign-on.
Federation management can be configured in open mode and secure mode on the Portal Server. The Portal Server Administration Guide describes how to configure federation management in open mode. Before configuring Federation management in secure mode, using Portal Server Secure Remote Access, ensure that it works in open mode. If you want your users to use Federation Management from the same browser in both open and secure mode, they must clear the cookies and cache from the browser.
For detailed information on Federation Management, see the Access Manager Federation Management Guide.
Federation Management Scenario
A user authenticates to an initial service provider. Service providers are commercial or not-for-profit organizations that offer web-based services. This broad category can include internet portals, retailers, transportation providers, financial institutions, entertainment companies, libraries, universities, and governmental agencies.
The service provider uses a cookie to store the user’s session information in the client browser. The cookie also includes the user’s identity provider.
Identity providers are service providers that specialize in providing authentication services. As the administrating service for authentication, they also maintain and manage identity information. Authentication accomplished by an identity provider is honored by all service providers with whom they are affiliated.
When the user attempts to access a service that is not affiliated with the identity provider, the identity provider forwards the cookie to the unaffiliated service provider. This service provider can then access the identity provider called out in the cookie.
However, cookies cannot be read across different DNS domains. Therefore a Common Domain Cookie Service is used to redirect the service provider to the correct identity provider thus enabling single sign-on for the user.
Configuring Federation Management Resources
The Federation resources, the service providers, identity providers, and the Common Domain Cookie Service (CDCS), are configured in the gateway profile based on where they reside. This section describes how to configure three scenarios:
 To Configure Federation Management Resources
To Configure Federation Management Resources
-
When all resources are inside the corporate intranet
-
When all resources are not inside the corporate intranet or the identity provider resides in the Internet
-
When all resources are not inside the corporate intranet or the service provider is a third party residing in the Internet while the identity provider is protected by the Gateway.
Configuration 1
In this configuration the service providers, identity providers and the Common Domain Cookie Service are deployed in the same corporate intranet and the identity providers are not published in the Internet Domain Name Server (DNS). The CDCS is optional.
In this configuration the Gateway points to the service provider, which is the Portal Server. This configuration is valid for multiple instances of the Portal Server.
 To Configure Gateway to a Service Provider (Portal
Server)
To Configure Gateway to a Service Provider (Portal
Server)
-
Log into the Portal Server administration console as administrator.
-
Select the Secure Remote Access tab and select the appropriate gateway profile to modify its attributes.
The Edit Gateway Profile page is displayed.
-
Select the Core tab.
-
Select the Enable Cookie Management checkbox to enable cookie management.
-
Select the Security tab.
-
In the Portal Servers field, enter Portal Server names to use the relative URLs such as: /amserver or /portal/dt listed in the Non-Authenticated URLs list. For example:
http://idp-host:port/amserver/js
http://idp-host:port/amserver/UI/Login
http://idp-host:port/amserver/css
http://idp-host:port/amserver/SingleSignOnService
http://idp-host:port/amserver/UI/blank
http://idp-host:port/amserver/postLogin
http://idp-host:port/amserver/login_images
-
In the Portal Servers field, enter the Portal Server name. For example, /amserver.
-
Click Save.
-
Select the Security tab.
-
In the Non-Authenticated URLs list, add the federation resources. For example:
/amserver/config/federation
/amserver/IntersiteTransferService
/amserver/AssertionConsumerservice
/amserver/fed_images
/amserver/preLogin
/portal/dt
-
Click Add.
-
Click Save.
-
If web proxies are needed to reach the URLs listed in the Non-authenticated URLs list, select the Deployment tab.
-
In the Proxies for Domains and Subdomains field, enter the necessary web proxies.
-
Click Add.
-
Click Save.
-
From a terminal window, restart the Gateway:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
Configuration 2
In this configuration the identity providers, identity providers and the Common Domain Cookie Provider (CDCP) are not deployed in the corporate intranet or the identity provider is a third party provider residing the in Internet.
In this configuration the Gateway points to the service provider, which is the Portal Server. This configuration is valid for multiple instances of the Portal Server.
 To Configure Gateway to a Service Provider (Portal
Server)
To Configure Gateway to a Service Provider (Portal
Server)
-
Log into the Portal Server administration console as administrator.
-
Select the Secure Remote Access tab and select the appropriate gateway profile to modify its attributes.
-
Select the Core tab.
-
Select the Enable Cookie Management checkbox to enable cookie management.
-
In the Portal Servers field, enter portal server names of the service provider to use the relative URLs such as: /amserver or /portal/dt listed in the Non-Authenticated URLs list.
http://idp-host:port/amserver/js
http://idp-host:port/amserver/UI/Login
http://idp-host:port/amserver/css
http://idp-host:port/amserver/SingleSignOnService
http://idp-host:port/amserver/UI/blank
http://idp-host:port/amserver/postLogin
http://idp-host:port/amserver/login_images
-
Click Save.
-
Click the Security tab.
-
In the Non-Authenticated URLs list, add the Federation resources. For example:
/amserver/config/federation
/amserver/IntersiteTransferService
/amserver/AssertionConsumerservice
/amserver/fed_images
/amserver/preLogin
/portal/dt
-
Click Add.
-
Click Save.
-
If web proxies are needed to reach the URLs listed in the Non-authenticated URLs list, select the Deployment tab.
-
In the Proxies for Domains and Subdomains field, enter information about the web proxies.
-
Click Add.
-
Click Save.
-
From a terminal window, restart the Gateway:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
Configuration 3
In this configuration the identity providers, identity providers and the Common Domain Cookie Provider (CDCP) are not deployed in the corporate intranet or the service provider is a third party provider residing the in Internet and the identity provider is protected by the Gateway.
In this configuration the Gateway points to the identity provider, which is the Portal Server.
This configuration is valid for multiple instances of the Portal Server. This configuration is unlikely on the Internet, however, some corporate networks may have such a configuration within their intranet, that is the identity provider may reside in a subnet this is protected by a firewall and the service providers are directly accessible from within the corporate network.
 To Configure Gateway to an Identity Provider (Portal
Server)
To Configure Gateway to an Identity Provider (Portal
Server)
-
Log into the Portal Server administration console as administrator.
-
Select the Secure Remote Access tab and select the appropriate gateway profile to modify its attributes.
-
Select the Core tab.
-
Select the Enable Cookie Management checkbox to enable cookie management.
-
In the Portal Servers field, enter the portal server name of the identity provider to use the relative URLs such as: /amserver or /portal/dt listed in the Non-Authenticated URLs list.
http://idp-host:port/amserver/js
http://idp-host:port/amserver/UI/Login
http://idp-host:port/amserver/css
http://idp-host:port/amserver/SingleSignOnService
http://idp-host:port/amserver/UI/blank
http://idp-host:port/amserver/postLogin
http://idp-host:port/amserver/login_images
-
Click Save.
-
Select the Security tab.
-
In the Non-authenticated URLs list, add the federation resources. For example:
/amserver/config/federation
/amserver/IntersiteTransferService
/amserver/AssertionConsumerservice
/amserver/fed_images
/amserver/preLogin
/portal/dt
-
Click Add.
-
Click Save.
-
If web proxies are needed to reach the URLs listed in the Non-authenticated URLs list, select the Deployment tab.
-
In the Proxies for Domains and Subdomains field, enter information about the web proxies.
-
Click Add.
-
Click Save.
-
From a terminal window, restart the Gateway:
./psadmin start-sra-instance –u amadmin – f <password file> –N <profile name>– t <gateway>
- © 2010, Oracle Corporation and/or its affiliates
