|
|
| Sun ONE Identity Server Policy Agent Guide |
Appendix A Configuration Tasks Performed by Installer
This appendix explains how to configure the following application servers to recover from installation failure:
WebLogic 6.1 SP2
The Sun ONE Identity Server Policy Agent for WebLogic 6.1 SP2 Server Installer performs certain configuration tasks. Depending on your system configuration and various other factors, these tasks can occasionally fail resulting in a unusable installation. Fortunately, such failures in most cases are recoverable by manually performing these tasks.The following sections describe how to configure Sun ONE Identity Server Policy Agent for WebLogic 6.1 SP2 Installer.
WebLogic Server Startup Script Modifications
The Installer modifies the WebLogic Server startup script in order to add the newly installed libraries to the CLASSPATH as well as to add certain startup properties for the Java Virtual Machine.
Solaris and HP-UX CLASSPATH Modifications
The following new lines are added to the WebLogic Server startup script, above the line where CLASSPATH variable is defined:
AM_INSTALL_DIR=/opt/SUNWam/wlAgent
AM_SDK_DIR=$AM_INSTALL_DIR/amSDK
AM_SDK_LIB_DIR=$AM_SDK_DIR/lib
AM_SDK_LOCALE_DIR=$AM_SDK_DIR/locale
AM_SDK_JAR1=$AM_SDK_LIB_DIR/am_sdk.jar
AM_SDK_JAR2=$AM_SDK_LIB_DIR/am_services.jar
AM_SDK_JAR3=$AM_SDK_LIB_DIR/am_sso_provider.jar
AM_SDK_JARS=$AM_SDK_JAR1:$AM_SDK_JAR2:$AM_SDK_JAR3
AM_SDK_PATH1=$AM_SDK_DIR:$AM_SDK_LIB_DIR
AM_SDK_PATH2=$AM_SDK_LOCALE_DIR:$AM_SDK_JARS
AM_SDK_CLASSPATH=$AM_SDK_PATH1:$AM_SDK_PATH2
AM_AGT_DIR=$AM_INSTALL_DIR/amAgent
AM_AGT_CONFIG_DIR=$AM_AGT_DIR/config
AM_AGT_LOCALE_DIR=$AM_AGT_DIR/locale
AM_AGT_LIB_DIR=$AM_AGT_DIR/lib
AM_AGT_JAR1=$AM_AGT_LIB_DIR/amagent_core.jar
AM_AGT_JAR2=$AM_AGT_LIB_DIR/amagent_weblogic.jar
AM_AGT_JAR3=$AM_AGT_LIB_DIR/amagent_filter.jar
AM_AGT_JAR4=$AM_AGT_LIB_DIR/amagent_tools.jar
AM_AGT_JARS12=$AM_AGT_JAR1:$AM_AGT_JAR2
AM_AGT_JARS34=$AM_AGT_JAR3:$AM_AGT_JAR4
AM_AGT_JARS=$AM_AGT_JARS12:$AM_AGT_JARS34
AM_AGT_PATH1=$AM_AGT_DIR:$AM_AGT_CONFIG_DIR
AM_AGT_PATH2=$AM_AGT_LOCALE_DIR:$AM_AGT_LIB_DIR:$AM_AGT_JARS
AM_AGT_CLASSPATH=$AM_AGT_PATH1:$AM_AGT_PATH2
AM_CLASSPATH=$AM_SDK_CLASSPATH:$AM_AGT_CLASSPATH
Once these entries have been added, the AM_CLASSPATH is appended to the CLASSPATH variable.
CLASSPATH=$AM_CLASSPATH:$WL_HOME:$WL_HOME/lib/weblogic_sp.jar:$W L_HOME/lib/weblogic.jar:$WL_HOME/samples/eval/cloudscape/lib/clo udscape.jar:./config/examples/serverclasses
Windows CLASSPATH Modifications
The CLASSPATH is modified By adding the following lines to the WebLogic Server startup script immediately after the definition of the CLASSPATH variable.
set AM_SDK_DIR=%AM_INSTALL_DIR%\amSDK
set AM_SDK_LIB_DIR=%AM_SDK_DIR%\lib
set AM_SDK_LOCALE_DIR=%AM_SDK_DIR%\locale
set AM_SDK_JAR1=%AM_SDK_LIB_DIR%\am_sdk.jar
set AM_SDK_JAR2=%AM_SDK_LIB_DIR%\am_services.jar
set AM_SDK_JAR3=%AM_SDK_LIB_DIR%\am_sso_provider.jar
set AM_SDK_JARS=%AM_SDK_JAR1%;%AM_SDK_JAR2%;%AM_SDK_JAR3%
set AM_SDK_PATH1=%AM_SDK_DIR%;%AM_SDK_LIB_DIR%
set AM_SDK_PATH2=%AM_SDK_LOCALE_DIR%;%AM_SDK_JARS%
set AM_SDK_CLASSPATH=%AM_SDK_PATH1%;%AM_SDK_PATH2%
set AM_AGT_DIR=%AM_INSTALL_DIR%\amAgent
set AM_AGT_CONFIG_DIR=%AM_AGT_DIR%\config
set AM_AGT_LOCALE_DIR=%AM_AGT_DIR%\locale
set AM_AGT_LIB_DIR=%AM_AGT_DIR%\lib
set AM_AGT_JAR1=%AM_AGT_LIB_DIR%\amagent_core.jar
set AM_AGT_JAR2=%AM_AGT_LIB_DIR%\amagent_weblogic.jar
set AM_AGT_JAR3=%AM_AGT_LIB_DIR%\amagent_filter.jar
set AM_AGT_JAR4=%AM_AGT_LIB_DIR%\amagent_tools.jar
set AM_AGT_JARS12=%AM_AGT_JAR1%;%AM_AGT_JAR2%
set AM_AGT_JARS34=%AM_AGT_JAR3%;%AM_AGT_JAR4%
set AM_AGT_JARS=%AM_AGT_JARS12%;%AM_AGT_JARS34%
set AM_AGT_PATH1=%AM_AGT_DIR%;%AM_AGT_CONFIG_DIR%
set AM_AGT_PATH2=%AM_AGT_LOCALE_DIR%;%AM_AGT_LIB_DIR%;%AM_AGT_JARS%
set AM_AGT_CLASSPATH=%AM_AGT_PATH1%;%AM_AGT_PATH2%
set AM_CLASSPATH=%AM_SDK_CLASSPATH%;%AM_AGT_CLASSPATH%
set CLASSPATH=%AM_CLASSPATH%;%CLASSPATH%
The last line in the added text modifies the CLASSPATH to include the libraries provided by the Agent.
Adding Parameters to Java Virtual Machine
For the installation platforms Solaris 8, Windows 2000, and HP-UX 11 the following parameters are added to the Java Virtual Machine invocation command that loads the WebLogic Server:
-D"com.iplanet.coreservices.configpath=/opt/SUNWam/wlAgent/amSDK /config/ums"
-D"max_conn_pool=10"
-D"min_conn_pool=1"
The resulting command on Solaris and HP-UX:
java $JAVA_OPTIONS -classpath $CLASSPATH -Dweblogic.Domain=examples -Dweblogic.Name=examplesServer -Dweblogic.management.password=$WLS_PW -Dbea.home=/bea -Dcloudscape.system.home=./samples/eval/cloudscape/data -Djava.security.policy==$WL_HOME/lib/weblogic.policy -D"com.iplanet.coreservices.configpath=/opt/SUNWam/wlAgent/amSDK /config/ums" -D"max_conn_pool=10" -D"min_conn_pool=1" weblogic.Server
On Windows:
"%JAVA_HOME%\bin\java" -hotspot -ms64m -mx64m -classpath "%CLASSPATH%" -Dweblogic.Domain=examples -Dweblogic.Name=examplesServer -Dweblogic.management.password=%WLS_PW% -Dbea.home="C:\bea" -Dcloudscape.system.home=./samples/eval/cloudscape/data -Djava.security.policy=="C:\bea\wlserver6.1/lib/weblogic.policy" -D"com.iplanet.coreservices.configpath=C:/Sun/SUNWam/wlAgent/amS DK/config/ums" -D"max_conn_pool=10" -D"min_conn_pool=1" weblogic.Server
Installation of JCE 1.2.1 and JSSE 1.0.2 Extensions
The Installer also performs the installation of JCE 1.2.1 and JSSE 1.0.2 extensions which result in the modification of the file JAVA_HOME/jre/lib/secrurity/java.security and the copying of various jar files in the JAVA_HOME/jre/lib/ext directory. If the installation of any of these extensions fails, you can manually install them. For obtaining these extensions and documentation on how to install them, refer to the product website at:
http://java.sun.com/products/jce and
http://java.sun.com/products/jsse
WebSphere 4.0.4 AE
The Sun ONE Identity Server Policy Agent for WebSphere Server Installer performs certain configuration tasks. Depending on your system configuration and various other factors, these tasks may occasionally fail resulting in a unusable installation. Fortunately, such failures in most cases are recoverable by manually performing these tasks. The following sections describe how to configure Sun ONE Identity Server Policy Agent for WebSphere manually.
Modifications to Admin Server Configuration File
The following configuration changes are performed in the WebSphere Admin Server configuration file located at WAS_root_dir/bin/admin.config.
- Update the property com.ibm.ejs.sm.adminserver.classpath and add all the SDK and AGENT related directories that contain property files.
- Update the -Dws.ext.dirs value for com.ibm.ejs.sm.util.process.Nanny.adminServerJvmArgs, to include SDK and AGENT related directories and jars.
- Add the following arguments to com.ibm.ejs.sm.util.process.Nanny.adminServerJvmArgs property:
- Djava.protocol.handler.pkgs=com.ibm.net.ssl.internal.www.protocol
- Dcom.iplanet.coreservices.configpath=<Agent_Install_Dir>/SUNWam/wasAgent/amSDK/config/ums
Modifications to trustedserver.properties
- Comment out all the lines that are not commented, and add the following lines to WAS_root_dir/properties/trustedservers.properties file:
com.ibm.websphere.security.trustassociation.enabled=true
com.ibm.websphere.security.trustassociation.types=amagent
com.ibm.websphere.security.trustassociation.amagent.interceptor=com .sun.amagent.websphere.interceptor.AgentInterceptor
com.ibm.websphere.security.trustassociation.amagent.config=AMAgent
Modifications to sas.client.props
- Update the following properties in the file: WAS_root_dir/properties/sas.client.props
com.ibm.CORBA.securityEnabled = true
com.ibm.CORBA.loginSource = properties
com.ibm.CORBA.loginUserid = <Realm Administrator>
com.ibm.CORBA.loginPassword = <Realm Administrator Password>
com.ibm.CORBA.principalName = <Realm Name>/<Realm Administrator>
- Restart the Administration Server and the Application Server instance.
Configurations Through Administrative Console
Setting System Properties for the Application Server Instance
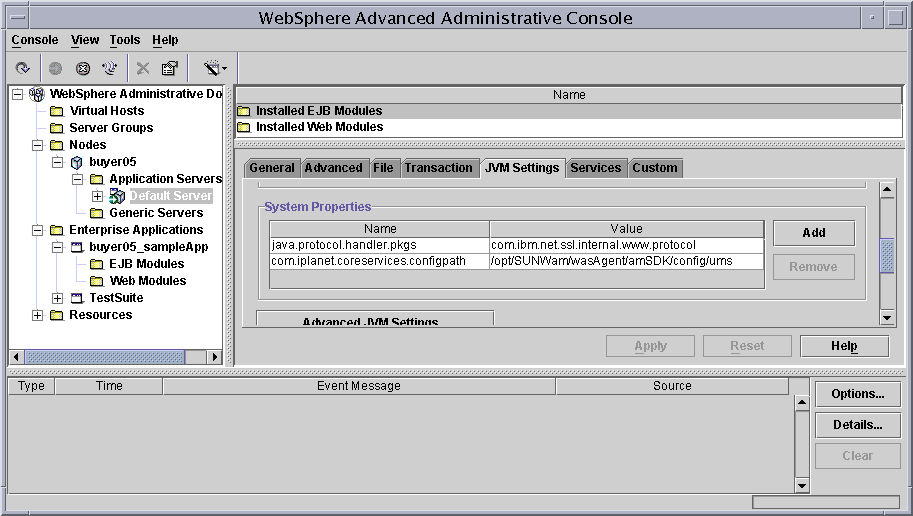
The following properties must be added to each Application server instance, through the Administrative console as shown in Figure A-1.
- Djava.protocol.handler.pkgs=com.ibm.net.ssl.internal.www.protocol
- Dcom.iplanet.coreservices.configpath= Agent_Install_Dir/SUNWam/wasAgent/amSDK/config/ums
Figure A-1 Setting System Properties
Agent Realm Configuration
The Agent Realm can be configured from the Security Center of Administrative Console. Follow the steps given below:
- Start the WebSphere Administrative console using the following command:
# WAS_roor_dir/bin/adminclient.sh
- In the Administrative Console window, choose Console > Security Center.
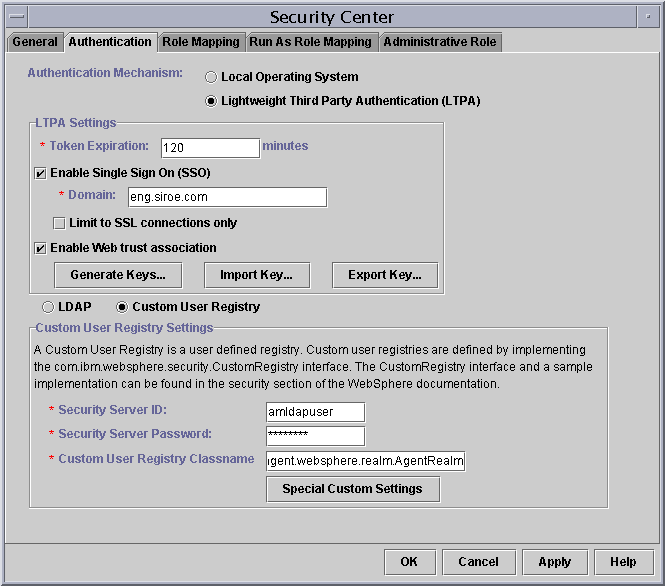
- In the Security Center window, click on Authentication tab. See Figure A-2.
- Choose Lightweight Third Party Authentication (LTPA) for authentication mechanism.
- Choose Custom Registry Option.
- Enter the Administrator's user ID for Security Server Id. For example, amAdmin for o=siroe.com.
- Enter the password for the Administrative User for "Security Server Password."
- Enter the value com.sun.amagent.websphere.realm.AgentRealm for Custom Registry Class.
- Click on check box Enable Web trust association.
- Click Apply. A message "Changes will take effect only after Administration Server is restarted" will be displayed. Click OK
- Click on General tab and enable the check box Enable Security.
- Stop all Application Server instances.
- Stop the Administration Server.
- Restart Administration Server and Application Server instances for changes to take effect.
Figure A-2 Agent Realm Configuration
Sun ONE Application Server 7.0
The following sections describe the configuration tasks performed by Sun ONE Identity Server Policy Agent Installer.
Application Server Config Files
The following configuration files are modified by the Installer:
S1AS_Install_Dir/SUNWappserver7/domains/domain1/server-instance/config/serve r.xml
S1AS_Install_Dir/SUNWappserver7/domains/domain1/server-instance/config/ login.conf
S1AS_Install_Dir/SUNWappserver7/domains/domain1/server-instance/config/ server.policy
Modifications in server.xml
Installer modifies server.xml in order to add all the newly installed libraries to the classpath as well as to add certain properties for the Java Virtual Machine. Also, it adds Agent Realm and makes it default to be used.
classpath Modifications
The classpath is modified by adding the following lines to the Application Server startup script immediately after the definition of the classpath variable.
Agent_Install_Dir/SUNWam/asAgent/amSDK;
Agent_Install_Dir/SUNWam/asAgent/amSDK/lib;
Agent_Install_Dir/SUNWam/asAgent/amSDK/locale;
Agent_Install_Dir/SUNWam/asAgent/amSDK/lib/am_sdk.jar;
Agent_Install_Dir/SUNWam/asAgent/amSDK/lib/am_services.jar;
Agent_Install_Dir/SUNWam/asAgent/amSDK/lib/am_sso_provider.jar;
Agent_Install_Dir/SUNWam/asAgent/amAgent;
Agent_Install_Dir/SUNWam/asAgent/amAgent/config;
Agent_Install_Dir/SUNWam/asAgent/amAgent/locale;
Agent_Install_Dir/SUNWam/asAgent/amAgent/lib;
Agent_Install_Dir/SUNWam/asAgent/amAgent/lib/amagent_core.jar;
Agent_Install_Dir/SUNWam/asAgent/amAgent/lib/amagent_as.jar;
Agent_Install_Dir/SUNWam/asAgent/amAgent/lib/amagent_filter.jar;
Agent_Install_Dir/SUNWam/asAgent/amAgent/lib/amagent_tools.jar
You can verify the modifications by invoking the Admin Console:
- Click the server-instance under Application Server Instances.
- On the right pane, click JVM Settings > Path Settings.
- Check the values of Classpath Suffix, which includes the above values.
Adding Parameters to Java Virtual Machine
The following parameters are added to the Java Virtual Machine invocation command that loads the Application Server:
-Dcom.iplanet.coreservices.configpath=Agent_Install_Dir/SUNWam/asAgen t/amSDK/config/ums
-Dmax_conn_pool=10
-Dmin_conn_pool=1
Adding Agent Realm
The following lines are added under <security-service> element:
<auth-realm name="agentRealm" classname="com.sun.amagent.as.realm.AgentRealm">
<property name="jaas-context" value="agentRealm"/>
</auth-realm>
Here name=agentRealm is value provided at installation time.
You can verify this using the Admin Console.
- Choose Security > Realms and verify the Agent Realm.
Making Agent Realm as Default
default-realm attribute of <security-service> element is modified as follows:
<security-service default-realm="agentRealm" anonymous-role="ANYONE" audit-enabled="false">
You can verify this using the Admin Console.
- Click Security and verify the value of Default Realm.
Modifications in login.conf
Installer modifies login.conf to define LoginModule for the jaas-context as follows:
agentRealm {
com.sun.amagent.as.realm.AgentLoginModule required;
};
Modifications in server.policy
Installer modifies server.policy to give Programmatic Login permission to agent-filter.jar as follows:
// ProgrammaticLoginPermission to Sun(TM) ONE Identity Server Policy Agent Filter
grant codeBase "file:Agent_Install_Dir/SUNWam/asAgent/amAgent/lib/amagent_filter.jar " {
permission com.sun.appserv.security.ProgrammaticLoginPermission "login";
};