|
|
| Sun ONE Directory Server 5.2 Getting Started Guide |
Glossaryaccess control instruction (ACI). An instruction that grants or denies permissions to entries in the directory.
The mechanism for controlling access to your directory. In Sun ONE Directory Server, an ACL is an aci attribute in a directory entry.
access rights. In the context of access control, specify the level of access granted or denied. Access rights are related to the type of operation that can be performed on the directory. The following rights can be granted or denied: read, write, add, delete, search, compare, selfwrite, proxy and all. For more information on these rights, see Chapter 6, "Managing Access Control", in the Sun ONE Directory Server Administration Guide.
account inactivation. Disables a single user account, or set of accounts, so that all authentication attempts are automatically rejected.
All IDs Threshold. A size limit which is globally applied to every index managed by the server. When the size of an entry ID list reaches this limit, the server replaces that entry ID list with an All IDs token.
All IDs token. A mechanism which causes the server to assume that all directory entries match the index key. In effect, the All IDs token causes the server to perform an unindexed search to match the index key.
anonymous access. When granted, allows anyone to access directory information without providing credentials, and regardless of the conditions of the bind.
approximate index. Allows for efficient approximate or "sounds-like" searches.
attribute. Holds descriptive information about an entry. Attributes have a type (name) and a set of values. An attribute type also specifies the syntax for the kind of information that can be stored as values of attributes of that type.
attribute list. See optional attribute list and required attribute list.
authenticating Directory Server. In pass-through authentication (PTA), the authenticating Directory Server contains the authentication credentials of the requesting client. A PTA-enabled user directory passes through bind requests to the authenticating directory, which verifies the bind credentials of the requesting client.
authentication. The process of proving the identity of the client user to the Directory Server. Users must provide a bind DN and either the corresponding password or certificate in order to be granted access to the directory. Directory Server allows the user to perform functions or access files and directories based on the permissions granted to that user by the directory administrator. See also server authentication.
authentication certificate. An X.509 digital certificate, issued by a Certification Authority, that is marked as suitable for use in authentication during an SSL connection setup.
base distinguished name (base DN). Base distinguished name. A search operation may be performed on just the entry identified by the base DN, the entries which are immediately subordinate to it, or to the entry and all entries below it in the directory information tree.
bind distinguished name (bind DN). Distinguished name used to authenticate to a Directory Server in the bind request.
bind rule. In the context of access control, the bind rule specifies the credentials and conditions that a particular user or client must satisfy in order to get access to directory information.
browsing index. Also known as a virtual list view (VLV) index. Speeds up the display of entries in the Directory Server Console (or other graphical user interface) if the client with the user interface uses the virtual list view extension. Virtual list view indexes can be created on any branch in the directory tree to improve display performance for specific searches.
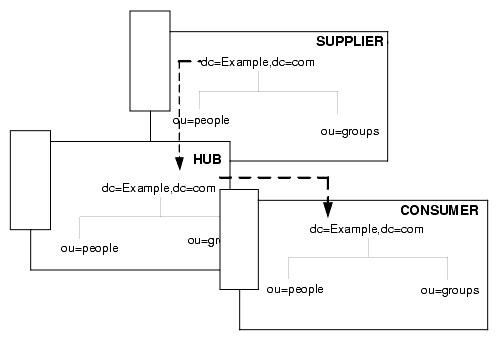
cascading replication. In a cascading replication scenario, one server, often called the hub supplier acts both as a consumer and a supplier for a particular replica. It holds a read-only replica and maintains a change log. It receives updates from the supplier server that holds the master copy of the data, and in turn supplies those updates to the consumer, as shown in the following diagram.
certificate. A certificate strongly associates the public key of a user or CA with the identity, typically a distinguished name, of that user or CA. The certificate is digitally signed by a Certificate Authority, and can be validated during an SSL connection setup to obtain the public key of the other end of the connection. X.509 certificates are stored within the directory in the caCertificate;binary or userCertificate;binary attributes.
Certificate Authority. Company or organization that sells and issues authentication certificates. You may purchase an authentication certificate from a Certification Authority that you trust. Also known as a CA.
chained suffix. An implementation of chaining. A chained suffix behaves like a normal suffix but has no persistent storage. Instead, it points to data stored remotely.
chaining. A method for relaying requests to another server. Results for the request are collected, compiled and then returned to the client. In the context of replication, chaining occurs when a consumer replica receives an update request, and forwards it to the server that holds the corresponding master replica. Note that this is not the same as a referral.
change log. A change log is a record of the modifications that have occurred on a replica. The supplier server then replays these modifications on the replicas stored on consumer servers, or on other masters, in the case of multi-master replication. Note that this is not the same as the retro changelog, which is not used for replication.
character type. Distinguishes alphabetic characters from numeric or other characters and the mapping of upper-case to lower-case letters.
ciphertext. Encrypted information that cannot be read by anyone without the proper key to decrypt the information.
class definition. Specifies the information needed to create an instance of a particular object.
class of service. (CoS) A method for sharing attributes between entries.
classic CoS. A classic CoS identifies the template entry by both its DN and the value of one of the target entry's attributes.
client. A software entity that requests services or information from a server.
collation order. Provides language and cultural-specific information about how the characters of a given language are to be sorted. This information might include the sequence of letters in the alphabet or how to compare letters with accents to letters without accents.
computed attributes. Attributes that are not stored with the entry itself but are returned to the client application along with normal attributes in operation results.
conflict. A situation that arises when changes are made to the same directory data on different directory servers before replication can synchronize the data between the servers. When the servers do synchronize, they detect that their copies are inconsistent, and may resolve the conflict or log an error.
conflict resolution. Deterministic procedures used to resolve change information. For more information, see "Solving Common Replication Conflicts" in the Sun ONE Directory Server Administration Guide.
consumer. Server containing replicated directory trees or subtrees from a supplier server.
consumer replica. A replica that refers all add, modify, and delete operations to master replicas. A server can hold any number of consumer replicas of different naming contexts.
container entry. An entry that represents the top of a subtree in the directory.
CoS. See class of service.
CoS definition entry. Identifies the type of CoS you are using. It is stored as an LDAP subentry below the branch it affects.
CoS template entry. Contains a list of the shared attribute values.
DAP. Directory Access Protocol. The ISO/ITU-T X.500 protocol that was the basis for LDAP.
default index. When Directory Server is installed, a set of default indexes is created for each database instance. For more information, see "Default Indexes" in the Sun ONE Directory Server Administration Guide.
definition entry. See CoS definition entry.
Directory Access Protocol. See DAP.
directory information tree. The logical representation of the information stored in the directory. It mirrors the tree model used by most file systems, with the tree's root point appearing at the top of the hierarchy. Also known as DIT.
Directory Manager. The privileged database administrator, comparable to the root user in UNIX systems. Access control does not apply to the directory manager.
Directory Server Console. An LDAP client application that provides a graphical user interface to browse, configure, and manage the contents of your directory. The Directory Server Console is a component of the Sun ONE Directory Server product.
directory service. A database application designed to manage descriptive, attribute-based information about people and resources within an organization.
distinguished name. String representation of an entry's name and location in the directory.
DIT. See directory information tree.
DN. See distinguished name.
DNS. Domain Name System. The system used by machines on a network to associate IP addresses (such as 64.124.140.181) with hostnames (such as www.sun.com). Clients usually use DNS to find the IP addresses of servers they wish to contact. The data in DNS is often augmented in local tables, such as from NIS or the /etc/hosts file on UNIX systems.
DNS alias. A DNS alias is a hostname that the DNS server knows points to a different host. The DNS alias is implemented as a DNS CNAME record. Machines always have one real name, but they can have one or more aliases. For example, an alias such as www.[yourdomain].[domain] might point to a real machine called realthing.[yourdomain].[domain] where the server currently exists.
DSA. Directory System Agent (an X.500 term for a Directory Server).
DSE. A DSE, or DSA-specific entry, has additional server-specific information associated with it. Some DSE's such as the Root DSE or schema DSE, have different attributes on each server.
DSML. (Directory Services Markup Language). A family of document formats for representing XML markup language that enables you to represent directory services in XML. Sun ONE Directory Server 5.2 conforms to version 2 of the DSML standard (DSMLv2).
entry. A group of attributes and a unique distinguished name.
entry distribution. Method of distributing directory entries across more than one server in order to scale to support large numbers of entries.
entry ID list. Each index that the directory uses is composed of a table of index keys and matching entry ID lists. The entry ID list is used by the directory to build a list of candidate entries that may match the client application's search request.
equality index. Allows you to search efficiently for entries containing a specific attribute value.
filter. The filter in a search request specifies a pattern which an entry in the scope of the search must match for that entry to be returned in the search response. Filters are also used in constructing role and access control definitions.
filtered role. Allows you to assign entries to the role depending upon the attribute contained by each entry. You do this by specifying an LDAP filter. Entries that match the filter are said to possess the role.
fractional replication. Replication of a filtered subset of attributes.
general access. When granted, indicates that all authenticated users can access directory information.
HTTP. Hypertext Transfer Protocol
The method for exchanging information between HTTP servers and clients.HTTPD. An abbreviation for the HTTP daemon or service, a program that serves information using the HTTP protocol.
HTTPS. Used in URLs to indicate that HTTP is layered on the Secure Sockets Layer, SSL, and so is protected against eavesdropping while in transit.
hub supplier. In the context of replication, a server that holds a replica that is copied from a different server, and in turn replicates it to a third server. See also cascading replication.
immediate subordinate . In the DIT, an entry is an immediate subordinate of another if its distinguished name is formed by appending its RDN to the distinguished name of the parent entry.
immediate superior. In the DIT, an entry is the immediate superior of another if its distinguished name, followed by the RDN of the other entry, forms the distinguished name of the child entry.
index key. Each index that the directory uses is composed of a table of index keys and matching entry ID lists.
indirect CoS. An indirect CoS identifies the template entry using the value of one of the target entry's attributes.
international index. Speeds up searches for information in a directory information tree in which the attributes have language tags.
LDAP. Lightweight Directory Access Protocol. Directory service protocol designed to run over TCP/IP and across multiple platforms.
LDAPv3. Version 3 of the LDAP protocol.
LDAP URL. Provides the means of locating directory servers using DNS and then completing the query via LDAP. A sample LDAP URL is ldap://ldap.sun.com
LDBM database. A high-performance, disk-based database consisting of a set of large files that contain all of the data in Directory Server.
LDIF. LDAP Data Interchange Format. Format used to represent Directory Server entries a text form using "type: value" pairs.
leaf entry. An entry under which there are no other entries. A leaf entry cannot be a branch point in a directory tree.
Lightweight Directory Access Protocol. See LDAP.
locale. Identifies the collation order, character type, monetary format and date/time format used to present data for users of a specific region, culture, or custom. This includes information on how data of a given language is interpreted, stored, or collated. The locale also indicates which code page should be used to represent a given language. Note that in LDAP all attributes are in UTF-8.
managed object. An SNMP data element that forms part of an MIB. In Sun ONE Directory Server, the managed objects are held in cn=monitor, and the SNMP agent provides to the network management station. As with LDAP attributes, each managed object has a name and object identifier expressed in dot-notation.
managed role. Allow you to create an explicit enumerated list of members.
management information base. See MIB.
mapping tree. A data structure that associates the names of suffixes (subtrees) with databases.
master agent. See SNMP master agent.
matching rule. Provides guidelines for how the server compares strings during a search operation. In an international search, the matching rule tells the server what collation order and operator to use.
MD5. A message digest algorithm by RSA Data Security, Inc., which can be used to produce a short digest of data, that is unique with high probability, and is mathematically extremely hard to produce a piece of data that will produce the same message digest.
MD5 signature. A message digest produced by the MD5 algorithm.
MIB. Management Information Base. The collection of managed objects held by an SNMP agent.
multi-master replication. A replication model in which entries can be written and updated on any of several master replica copies without requiring communication with other master replicas before the write or update is performed. Each server maintains a change log for the replica. Modifications made on one server are automatically replicated to the other servers. In case of conflict, a time stamp is used to determine which server holds the most recent version.
multiplexor. The server containing the database link that communicates with the remote server.
n + 1 directory problem. The problem of managing multiple instances of the same information in directories and databases of different types, resulting in increased hardware and personnel costs.
name collision. A conflict that occurs during replication if multiple entries have been added or renamed, and attempt to use the same distinguished name. The conflicting entries are renamed automatically by the directory servers to ensure DN uniqueness.
nested role. A role that names other role definitions. The set of members of a nested role is the union of all members of the roles it contains. Nested roles may also define extended scope to include the members of roles in other subtrees
Powerful workstation with one or more network management applications installed.
NIS. Network Information Service. A system of programs and data files that UNIX systems use to collect, collate, and share specific information about machines, users, file systems, and network parameters throughout a network of computers.
ns-slapd. On UNIX systems, this is the process or service responsible for all actions of the Directory Server. On Windows systems, the equivalent is slapd.exe.
ns-slapd.exe. The slapd process watchdog on Windows systems.
object class. Defines an entry type in the directory by defining which attributes are contained in the entry.
object identifier. (OID) A string representation of an object identifier consists of a list of decimal numbers separated by periods, e.g. "1.3.6.1.4.1". In LDAP, object identifiers are used to uniquely identify schema elements, including object classes and attribute types. The top levels of an object identifier hierarchy are managed by standards bodies and are delegated to organizations who wish to construct their own schema definitions.
operational attribute. An operational attribute contains information used internally by the directory to keep track of modifications and subtree properties. Operational attributes are not returned in response to a search unless explicitly requested.
optional attribute list. A list of optional attributes for a specified object class. Optional attributes are preceeded by the keyword MAY.
parent access. When granted, indicates that users have access to entries below their own in the directory tree, that is, if the bind DN is the parent of the targeted entry.
pass-through authentication. See PTA.
pass-through subtree. In pass-through authentication, the PTA Directory Server will pass through bind requests to the authenticating Directory Server from all clients whose DN is contained in this subtree.
password policy. A set of rules that govern how passwords are used in a given directory.
permission. In the context of access control, the permission states whether access to the directory information is granted or denied, and the level of access that is granted or denied. See also access rights.
pointer CoS. A pointer CoS identifies the template entry using the template DN only.
presence index. Enables efficient searching for entries that contain an attribute of a specified type, regardless of the value of the attribute in the entry.
propagation behaviour. The synchronization process between a consumer and a supplier.
protocol. A set of rules that describes how devices on a network exchange information.
proxy authorization. A special form of authentication where a user binds to the directory with its own identity but is granted the access rights of another user on a per operation basis. This other user is referred to as the proxy user, and its DN the proxy DN.
proxy DN. Used with proxied authentication. The proxy DN is the DN of an entry that has access permissions to the target on which the client application is attempting to perform an operation.
PTA. Pass-through authentication. Mechanism by which one Directory Server consults another to check bind credentials.
PTA Directory Server. In pass-through authentication (PTA), the PTA Directory Server sends (passes through) bind requests it receives to the authenticating Directory Server.
PTA LDAP URL. In pass-through authentication, the URL that defines the authenticating Directory Server, pass-through subtree(s) and optional parameters.
RDN. Relative distinguished name. The name of the actual entry itself, before the entry's ancestors have been appended to the string to form the full distinguished name. Most RDNs consist of a single attribute type and value from the entry.
referential integrity. Mechanism that ensures that relationships between entries expressed by DN-valued attributes are maintained within the directory.
referral. When a server receives a search or update request from a client that it cannot process, it sends back to the client a pointer to the Directory Server that can process the request.
referral hop limit. The maximum number of referrals that a client should follow in a row.
relative distinguished name. See RDN.
replica. An instance of an area of replication on a server. See also consumer replica and supplier replica.
replica cycle. See replication cycle.
replica group. The servers that hold instances of a particular area of replication. A server may be part of several replica groups.
replication. The process of synchronizing data distributed across Directory Servers and rectifying update conflicts.
replication agreement. Set of configuration parameters that are stored on the supplier server and identify the suffixes to replicate, the consumer servers to which the data is pushed, the times during which replication can occur, the DN and credentials used by the supplier to bind to the consumer, and how the connection is secured.
replication base entry. The DN of the root of a replicated area.
replication cycle. The interval during which update information is exchanged between two or more replicas. The replication cycle begins during an attempt to push data to, or pull data from, another replica or set of replicas, and ends when the data has successfully been exchanged or when an error is encountered.
replication session. A session set up between two servers in a replica group to pass update information as part of a replica cycle.
required attribute list. A list of required attributes for a specified object class. Required attributes are preceeded by the keyword MUST.
retro changelog. Provides backward compatibility with 4.x releases of Directory Server. The retro changelog stores changes in the order of arrival on the local server and not in the order in which these changes were applied to the system. The retro changelog was not designed to function in a multi-master replication environment. Note that this is not the same as the change log, as the retro changelog is not used in replication.
role. An entry grouping mechanism. Each role has members, which are the entries that possess the role.
role-based attributes. Attributes that appear on an entry because it possesses a particular role within an associated CoS template.
root DN. The distinguished name of the Directory Manager (the superuser for the Directory Server).
Root DSE. An entry that is automatically generated by the Directory Server and is returned from a baseObject search with a DN that is empty (zero bytes long). The Root DSE provides information to clients about the server's configuration, such as a pointer to the subschema entry, a list of the DNs of the naming contexts held by the server, and a list of the LDAPv3 controls and extensions which the server supports. See also DSE.
root suffix. The parent of one or more sub suffixes. A directory tree can contain more than one root suffix.
RTT. Round Trip Time (also called the round-trip delay time). The elapsed time for transit of a signal over a closed circuit (from the server to the client and back). This delay is important in systems that require two-way interactive communication where the RTT directly affects the throughput rate. In the context of Sun ONE Directory Server, the RTT and the TCP window can have a significant impact on replication performance over WAN.
schema. Definitions describing what types of information can be stored as entries in the directory. When information that does not match the schema is stored in the directory, clients attempting to access the directory may be unable to display the proper results.
schema checking. Ensures that entries added or modified in the directory conform to the defined schema. Schema checking is on by default and users will receive an error if they try to save an entry that does not conform to the schema.
See SSL.
self access. When granted, indicates that users have access to their own entries, that is, if the bind DN matches the targeted entry.
server authentication. Allows a client to make sure that it is connected to a secure server, preventing another computer from impersonating the server or attempting to appear secure when it is not.
server root. Also known as ServerRoot. A directory on the server machine dedicated to holding the server program and configuration, maintenance, and information files.
Simple Network Management Protocol. See SNMP.
single-master replication. A replication model in which only one server, the master, allows LDAP write access to the replicated data. In a single-master replication model, the supplier or master server maintains a change log.
slapd.exe. On Windows systems, this is the process or service responsible for all actions of the Directory Server. On UNIX systems, the equivalent is ns-slapd.
SNMP. Simple Network Management Protocol. Used to monitor and manage application processes running on the servers, by exchanging data about network activity.
SNMP master agent. Software that exchanges information between the various subagents and the NMS.
SNMP subagent. Software that gathers information about the managed device and passes the information to the master agent.
SOAP. Simple Object Access Protocol. A lightweight, XML-based protocol for the exchange of information in a decentralized, distributed environment. In the context of Sun ONE Directory Server, SOAP is used with HTTP to provide a framework for describing the contents of messages and how to process them.
SSL. Secure Sockets Layer. A software library establishing a secure connection between two parties (client and server) used to implement HTTPS, the secure version of HTTP.
standard index. Indexes that are maintained by default.
subagent. See SNMP subagent.
subschema entry. An entry containing all the schema definitions (definitions of object classes, attributes, matching rules, and so on) used by entries in part of a directory tree.
substring index. Allows for efficient searching against substrings within entries. Substring indexes are limited to a maximum of three characters per index key.
sub suffix. A branch underneath a root suffix.
suffix. The name of the entry in the directory tree, below which data is stored. Multiple suffixes are possible within the same directory. Each database only has one suffix.
supplier. Server containing the master copy of directory trees or subtrees that are replicated to consumer servers.
supplier replica . A replica that contains a master copy of directory information and can be updated. A server can hold any number of master replicas.
supplier server. In the context of replication, a server that holds a replica that is copied to a different server is called a supplier for that replica.
symmetric encryption. Encryption that uses the same key for both encrypting and decrypting. The Data Encryption Standard (DES) is an example of a symmetric encryption algorithm.
system index. An index that cannot be deleted or modified as it is essential to Directory Server operations.
target. In the context of access control, the target identifies the directory information to which a particular ACI applies.
target entries. The entries within the scope of a CoS.
TCP/IP. Transmission Control Protocol/Internet Protocol. The main network protocols for the Internet and for enterprise networks.
template entry. See CoS template entry.
TLS. Transport Layer Security. The standard for Secure Socket Layers (SSL), a public key based protocol.
topology. The way a directory tree is divided among physical servers and how these servers link with one another.
Transport Layer Security. See TLS.
virtual list view index . (VLV) See browsing index.
X.500 standard. The set of ISO/ITU-T documents outlining the recommended information model, object classes and attributes used by Directory Server implementation. LDAP is a "lightweight" version of the Directory Access Protocol (DAP) used by the X.500 standard.
XML. Extensible Markup Language. XML is an underlying format for structured textual document exchange on the web.