|
|
| Sun ONE Portal Server 6.0 Administrator's Guide |
Chapter 2 Administering Authentication, Users, and Services
This chapter describes how to use iPlanet™ Directory Server Access Management Edition to administer authentication, users, and services. This chapter does not attempt to explain all aspects of iPlanet Directory Server Access Management Edition. Instead, it focuses on those aspects that pertain to Sun™ ONE Portal Server. See the iPlanet Directory Server Access Management Edition documentation for more information.
This chapter contains these sections:
- Overview of iPlanet Directory Server Access Management Edition
- Logging In to the iPlanet Directory Server Access Management Edition Admin Console
- Viewing Basic Information
- Starting and Stopping Sun ONE Portal Server
- Managing iPlanet Directory Server Access Management Edition Services
- Managing Sun ONE Portal Server Users
- Configuring Authentication
- Overview of How Sun ONE Portal Server Uses Policy Management
- Logging In to the Sun ONE Portal Server Desktop
- Managing Logging
Overview of iPlanet Directory Server Access Management Edition
In Sun™ ONE Portal Server 3.0 (formerly known as iPlanet™ Portal Server 3.0) implementations, you administer authentication methods, create domains, roles and users, and manage other data, such as profile attributes and logs, through the product itself. You also use the iPlanet Portal Server 3.0 APIs to develop custom applications.
Now, with Sun ONE Portal Server 6.0 product, you use iPlanet Directory Server Access Management Edition administrative capabilities and APIs formerly found within iPlanet Portal Server 3.0 itself. iPlanet Directory Server Access Management Edition is a set of tools that leverage the management and security potential of Sun™ ONE Directory Server. The goal of iPlanet Directory Server Access Management Edition is to provide an interface for managing user objects, policies, and services for organizations using Sun ONE Directory Server.
iPlanet Directory Server Access Management Edition enables:
- Sun ONE Directory Server to perform user authentication and single sign-on, increasing data security.
- Administrators to initiate user entry management based on roles, an entry grouping mechanism which appears as an attribute in a user entry.
- Developers to define and manage the configuration parameters of a multitude of default and custom-made services.
You access all three of these functions through a graphical user interface, the web-based iPlanet Directory Server Access Management Edition admin console. In addition, the command-line interface, amadmin, enables you to perform batch administrative tasks on the directory server. For example, you can create, register, and activate new services; and create, delete, and read (get) organizations, people containers, groups, roles, and users.
Summary of iPlanet Directory Server Access Management Edition Features
iPlanet Directory Server Access Management Edition provides the following management components. Previously, these components resided within the Sun ONE Portal Server 3.0 framework itself.
- User Management—Creates and manages user-related objects (user, role, group, people container, organization, sub-organization, and organizational unit objects). These can be defined, modified, or deleted using either the iPlanet Directory Server Access Management Edition console or the command-line interface.
- Authentication—Provides a plug-in solution for user authentication. The criteria needed to authenticate a particular user is based on the authentication service configured for each organization in the Sun ONE Portal Server enterprise. Before being allowed access to a Sun ONE Portal Server session, a user must pass through authentication successfully.
- Single Sign-On—Once the user is authenticated, the iPlanet Directory Server Access Management Edition API for Single Sign-On (SSO) takes over. Each time the authenticated user tries to access a protected page, the SSO API determines whether the user has the permissions required based on their authentication credentials. If the user is valid, access to the page is given without additional authentication. If not, the user will be prompted to authenticate again.
- Service Management—Specifies configuration parameters for default and custom-made services, including those for the Sun ONE Portal Server product itself (Desktop, Rewriter, Search, and NetMail).
- Policy Management—Defines, modifies, or removes the rules that control access to business resources. Collectively, these rules are referred to as policy. Policies can be role-based or organization-based and can offer privileges or define constraints.
Comparison: Portal Server 3.0 and Portal Server 6.0
Table 2-1 provides an overview to the major changes that have taken place to the Portal Server product. Many functions and features that previously were part of the Sun ONE Portal Server 3.0 (formerly iPlanet Portal Server 3.0) product are now part of iPlanet Directory Server Access Management Edition. In the table, the first column lists a concept or term, the second column defines the function or feature for that term in the Sun ONE Portal Server 3.0 product, the third column describes the corresponding feature or function in the Sun ONE Portal Server 6.0 product.
Table 2-1 Sun ONE Portal Server 3.0 to Sun ONE Portal Server 6.0 Comparison
Concept or Term
Sun ONE Portal Server 3.0
Sun ONE Portal Server 6.0
Role tree
A hierarchy you configure within Sun ONE Portal Server 3.0 to organize users and applications. The four levels of the role tree are:
Concept of role tree no longer applies.
Instead, because iPlanet Directory Server Access Management Edition leverages the capability of Sun ONE Directory Server, you use the Directory Information Tree (DIT) to organize your users, organizations, suborganizations, and so on.
Domain/
OrganizationA top-level grouping of users with common interests, such as employees or customers. Note that this is not a DNS domain, but a means that Sun ONE Portal Server 3.0 uses to group users into logical communities.
Concept of domain no longer applies. Instead, the iPlanet Directory Server Access Management Edition organization represents the top level of a hierarchical structure used by an enterprise to manage its departments and resources.
Upon installation, iPlanet Directory Server Access Management Edition dynamically creates a top-level organization (default o=isp) to manage the iPlanet Directory Server Access Management Edition enterprise configurations. Additional organizations can be created after installation to manage separate enterprises. All created organizations fall beneath the top-level organization. Within these sub organizations other suborganizations can be nested. There is no limitation on the depth to the nested structure.
Role
Divides the members of a domain according to function. The role contains a set of attributes and policies that define a user's Desktop policy.
Contains a privilege or set of privileges that can be granted to a user or users. This includes access and management of identity information stored in Sun ONE Directory Server and access to privileges protected by the iPlanet Directory Server Access Management Edition policy module. An iPlanet Directory Server Access Management Edition role also has associated with it a profile, which is stored in the class-of-service template.
Role is defined differently in iPlanet Directory Server Access Management Edition and it includes the ability for a single user to have multiple roles, which was previously not supported.
The privileges for a role are defined in access control instructions (ACIs). The iPlanet Directory Server Access Management Edition includes several predefined roles. The iPlanet Directory Server Access Management Edition Console allows you to edit a role's ACI to assign access privileges within the Directory Information Tree.
Attribute
Supports two types of attributes: global and user-configurable. Global attributes apply to the entire platform and are configured only by the Super Administrator. User-configurable attributes apply to underlying levels of the role tree, as described in the following sections. A delegated Domain Administrator can configure these attributes for the domain, parent role, child role, and user levels. At the user level of the role tree, some attributes can be customized for each user, as needed.
Makes use of iPlanet Directory Server Access Management Edition attributes, which can be one of the following types:
- Global— The values applied to the global attributes are applied across the iPlanet Directory Server Access Management Edition configuration and are inherited by every configured organization.
- Dynamic—A dynamic attribute can be assigned to an iPlanet Directory Server Access Management Edition configured role or organization. When the role is assigned to a user or a user is created in an organization, the dynamic attribute then becomes a characteristic of the user.
- Organization—These attributes are assigned to organizations only. In that respect, they work as dynamic attributes. They differ from dynamic attributes, though, as they are not inherited by entries in the subtrees.
- User—These attributes are assigned directly to each user. They are not inherited from a role or an organization and, typically, are different for each user.
- Policy—Policy attributes are privilege attributes. Once a policy is configured, they may be assigned to roles or organizations. That is the only difference between dynamic and policy attributes; dynamic attributes are assigned directly to a role or an organization and policy attributes are used to configure policies and then applied to a role or an organization.
Policy
Configures portal access policies to applications, the Desktop, NetFile, Netlet, and so on.
Rules that define who can do what to which resource. The iPlanet Directory Server Access Management Edition Policy Service allows an organization to set up these rules or policies. In general, policy is created at the organization (or sub-organization) level to be used throughout the organization's tree. In order to create a named policy, the specific policy service must first be registered to the organization under which the policy will be created.
In iPlanet Directory Server Access Management Edition 5.1, the policy service consists only of lists of URLs that are allowed or denied. This is not sufficient for Portal Server to build a policy-based Desktop for content. This is why policy for channel access is built into the display profile for the Desktop. The Portal Server 6.0 Desktop supports a display profile that allows list of channels to be merged from several roles. If, for example, you have 25 roles, each with a handful of channels associated with that role, users can be configured to have any number of those roles, and the Desktop they get will then provide the aggregation of all those roles. Merge semantics control how channels from the various roles are aggregated or merged. For the purpose of merging display profiles, a hierarchical ordering is imposed on the roles in the Portal Server. The merge begins with the lowest priority document (lowest number) and proceeds in increasing priority number, until it arrives at the user (base), the highest priority profile. See Chapter 5 "Administering the Display Profile," for information on merging display profiles.
Component/
ServiceThe four major components of Portal Server 3.0 are the server itself, the profile server, the gateway, and the firewall.
Component has been replaced by iPlanet Directory Server Access Management Edition service, which is group of attributes defined under a common name. The attributes define the parameters that the service provides to an organization. iPlanet Directory Server Access Management Edition is the service framework.
Sun ONE Portal Server 6.0 relies on iPlanet Directory Server Access Management Edition to provide core services, such as authentication, user management, and policy management, as well as for the framework to run Portal Server specific services (Desktop, NetMail, Rewriter, and Search).
Administrative interfaces
Provides its own admin console to administer only Portal Server 3.0 components.
The command-line interface is ipsadmin.
Uses the iPlanet Directory Server Access Management Edition admin console to administer iPlanet Directory Server Access Management Edition services, users, and policy, as well as Sun ONE Portal Server specific services (Desktop, NetMail, Rewriter, and Search.)
The command-line interfaces that replace ipsadmin are amadmin, dpadmin, and rwadmin.
iPlanet Directory Server Access Management Edition Constraints
When using iPlanet Directory Server Access Management Edition, the following constraints apply:
- The predefined iPlanet Directory Server Access Management Edition roles cannot span multiple parallel organizations; however, a role can be assigned to a user who resides in a child organization of the organization that the role is associated with. In addition, access to resources in multiple domains can also be enabled by creating a custom role and defining the necessary Access Control Instructions (ACIs) to grant the role the privileges required.
- A user must belong to an organization and can only belong to that organization.
- Hierarchical roles are not supported. For example, you cannot create role C as equal to the sum of role A and role B, and have a user with role C have access to the resources in Role A, without being explicitly assigned to role A.
- The access permission for the RoleAdministratorRole can only be configured through editing corresponding ACIs directly.
- When role administrators (delegated administrators) log in to the iPlanet Directory Server Access Management Edition admin console, they can see all the roles and their associated services and properties under the same organization even if the role administrators don't have the permission to modify them.
iPlanet Directory Server Access Management Edition Interfaces
iPlanet Directory Server Access Management Edition Admin Console
This browser-based console provides a graphical user interface to manage the iPlanet Directory Server Access Management Edition enterprise, including Sun ONE Portal Server services. The admin console has default administrators with varying degrees of privileges used to create and manage the services, policies and users. (Additional delegated administrators can be created based on roles.) See Chapter 3 "Configuring Delegated Administration," for more information.
The iPlanet Directory Server Access Management Edition admin console is divided into three sections: the Location pane, the Navigation pane and the Data pane. By using all three panes you navigate the directory, perform user and service configurations, and create policies.
See "Using the iPlanet Directory Server Access Management Edition Console"," for more information.
iPlanet Directory Server Access Management Edition Command-Line
The iPlanet Directory Server Access Management Edition command-line interface is amadmin, to aminister the server, and amserver, to stop and start the server process. amadmin is also used to load XML service files into the directory server and perform batch administrative tasks on the directory tree.The Sun ONE Portal Server 3.0 command-line interfaces, ipsadmin and ipsserver are no longer used.
For more information on amadmin, see the iPlanet Directory Server Access Management Edition documentation.
Logging In to the iPlanet Directory Server Access Management Edition Admin Console
You can log in to the iPlanet Directory Server Access Management Edition console in two ways:
- Using a Specific URL
- Through HTTPS
When you log in to the admin console, the capabilities that are presented to you depend on your access. Access permissions are determined based on the ACIs or roles assigned to you. For example, the superuser sees all of the admin console's functionality; a delegated administrator might only see a subset of this functionality, perhaps for a suborganization; end users see only the user attributes pertaining to their particular user ID.
Currently, there are two URLs available for logging in to the admin console:
- http://host:port/amconsole/
- http://host:port/amserver/
The /amconsole URL explicitly requests the HTML pages for the iPlanet Directory Server Access Management Edition administration console. If you log in using /amconsole, it brings up the admin console and then you'll see the URL change to /amserver/login so the user can authenticate. Regardless of the configuration, this URL can be used to access the admin console.
The /amserver URL requests the HTML pages for the iPlanet Directory Server Access Management Edition service. Although the default set up when Sun ONE Portal Server is installed is to redirect this URL to log in to the admin console, because the /amserver URL accesses the iPlanet Directory Server Access Management Edition service this URL can be used to make other services besides the console available. For example,
- If a user accesses an application with an invalid session, an application may redirect the /amserver URL request to amserver/login with the goto parameter. For example, the Sun ONE Portal Server Desktop does this as well as the iPlanet Directory Server Access Management Edition agent.
- A customer may direct users to amserver/login as their starting point into some application or portal. Their default redirect URL could then be some portal application or custom application.
- A custom application could directly call the amserver/login to authenticate.
To log in to the iPlanet Directory Server Access Management Edition Admin Console
- Using a specific URL:
Type http://host:port/amserver/
or
Type http://host:port/amconsole/
- Using HTTPS:
Type https://host:ssl_port/amconsole/Configuring Log in to the Admin Console Using an IP Address
You cannot log in to the iPlanet Directory Server Access Management Edition administration console by using the server's IP address. This is because of the cookie domain settings in iPlanet Directory Server Access Management Edition.
However, you can add the local host's IP address to the list of Cookie Domains on the administration console.
- Select Service Management from the View menu.
- Click Platform.
- Add your local host's IP address to Cookie Domains.
You should now be able to access the administration console with IP address, rather than the domain name.
Viewing Basic Information
A script is available to enable you to display basic information about the product such as the version, build date of the Sun ONE Portal Server as well as the version and build date for the jar file. The version script is installed in BaseDir/SUNWps/bin directory where BaseDir is the server root directory in which you installed the Sun ONE Portal Server. The default is /opt.
To view product information:
- Change directories to the directory where the script is installed. That is:
cd BaseDir/SUNWps/bin
- To view information about the Sun ONE Portal Server, type
./version
- To view information about the jar file on the Sun ONE Portal Server, type
./version JarName
where JarName is the name of the jar file.
Starting and Stopping Sun ONE Portal Server
This section describes how to stop and start Sun ONE Portal Server. Because Sun ONE Portal Server depends on iPlanet Directory Server Access Management Edition, you do not start and stop Sun ONE Portal Server directly. You need to restart the iPlanet Directory Server Access Management Edition server itself.
- To start Sun ONE Portal Server, enter:
/etc/init.d/amserver start
- To start multiple instances Sun ONE Portal Servers, enter:
/etc/init.d/amserver startall
- To stop Sun ONE Portal Server, enter:
/etc/init.d/amserver stop
Note You do not need to stop the server to restart it. If you start a server that is already running, the server is stopped and restarted.
The Sun ONE Portal Server supports various platform locales. To start the Sun ONE Portal Server with a value other than the installed default see the Sun ONE Portal Server 6.0 Developer's Guide.
Managing iPlanet Directory Server Access Management Edition Services
This section provides an introduction to iPlanet Directory Server Access Management Edition services used by Sun ONE Portal Server. See the iPlanet Directory Server Access Management Edition documentation for complete information.
Installation and Sun ONE Web Server Packaging
- The Sun ONE Portal Server installer executes the iPlanet Directory Server Access Management Edition installer if iPlanet Directory Server Access Management Edition has not previously been installed.
- Sun ONE Portal Server shares the web container with iPlanet Directory Server Access Management Edition. The web container specifies a runtime environment for Web components including concurrency, deployment, life cycle management, security, transaction, and other services.
- Sun ONE Portal Server uses the JVM™ and other components that iPlanet Directory Server Access Management Edition provides.
User Management
- Sun ONE Portal Server stores its profile information in iPlanet Directory Server Access Management Edition using the iPlanet Directory Server Access Management Edition APIs.
- Sun ONE Portal Server leverages multi-role support in iPlanet Directory Server Access Management Edition.
- Sun ONE Portal Server uses open and non-proprietary standard schema attributes, for example, givenName.
- iPlanet Directory Server Access Management Edition provides direct access to the LDAP directory.
Single Sign-On/Authentication
- In Sun ONE Portal Server 6.0, the authentication is managed by iPlanet Directory Server Access Management Edition.
- iPlanet Directory Server Access Management Edition provides all the authentication modules.
- Sun ONE Portal Server uses iPlanet Directory Server Access Management Edition policy attributes to restrict access.
Service Management
Sun ONE Portal Server 6.0 defines the following iPlanet Directory Server Access Management Edition services:
- Desktop—Provides the portal front-end and is the primary end user interface to the portal .See Chapter 4 "Administering the Desktop Service" for information on setting up and administering the Desktop.
- NetMail—Accesses the IMAP and SMTP mail servers in the Internet and allows users to access email through the portal. See Chapter 6 "Administering the NetMail Service" for information on setting up and administering NetMail.
- Rewriter—Implements rules set up by the administrator to rewrite URLs to provide appropriate access. See Chapter 7 "Administering the Rewriter Service" for information on setting up and administering the Rewriter.
- Search—Provides a search capability for the Sun ONE Portal Server including basic and advanced search channels of the available documents. See Chapter 8 "Administering the Search Engine Service" for information on setting up and administering the Search service.
Managing Sun ONE Portal Server Users
The Directory Information Tree (DIT) organizes your users, organizations, suborganizations, and so on into a logical or hierarchical structure that enables you to efficiently administer and assign appropriate access to the users assuming those roles or contained within those organizations. This section provides information to help you plan the directory structure or tree underlying your portal server implementation by providing information about the functions and capabilities of organizations, suborganizations, and roles, and also providing procedures for creating and managing organizations, roles, and users.
Note Sun ONE Portal Server 6.0 supports organizations; previously, Sun ONE Portal Server 3.0 used the concept of domains.
The top of the organization tree in iPlanet Directory Server Access Management Edition is called isp by default but can be changed or specified at install time. Additional organizations can be created after installation to manage separate enterprises. All created organizations fall beneath the top-level organization. Within these suborganizations other suborganizations can be nested. There is no limitation on the depth to the nested structure.
Note The top of the tree does not have to be called isp. It can be called anything. But with a tree organized with a generic top, for example, isp, then organizations within the tree can share roles.
Roles are a new grouping mechanism that are designed to be more efficient and easier to use for applications. Each role has members, or entries that possess the role. As with groups, you can specify role members either explicitly or dynamically. The roles mechanism automatically generates the nsRole attribute containing the DN of all role definitions in which the entry is a member. Each role contains a privilege or set of privileges that can be granted to a user or users. In Sun ONE Portal Server 6.0, multiple roles can be assigned to a single user. The privileges for a role are defined in Access Control Instructions (ACIs). The Sun ONE Portal Server includes several predefined roles. The iPlanet Directory Server Access Management Edition console allows you to edit a role's ACI to assign access privileges within the Directory Information Tree. Built-in examples include SuperAdmin Role and TopLevelHelpDeskAdmin roles. You can create other roles that can be shared across organizations.
Planning Organizations, Suborganizations, and Roles
As you plan your DIT structure, you need to decide whether to use a hierarchical or flat tree structure. As a general rule, you should strive to make your tree as flat as possible. However, as the size of your organization grows, a certain amount of hierarchy is important to facilitate granting and managing user access. The three key structural entities in iPlanet Directory Server Access Management Edition for building your DIT structure are organizations (or suborganizations), roles, and users. Before you plan your structure, you should understand the functions, characteristics, and interrelationships of each of these entities.
Organizations and Suborganizations
- Allow creation of hierarchical relationships that can represent or model your enterprise or organization's hierarchy.
- Can contain users created by its corresponding admin. This provides a method of grouping users together for administration and access control purposes. It is typically easier to administer and control access if users with similar needs are grouped together.
- Can be easily created or removed by an admin in a parent organization or suborganization via the admin console. However, when removed, all subordinate organizations and users are also removed, so not suitable when names or structure likely to change.
Roles
- Allow assignment of a privilege or set of privileges to a user or users. Within an organization, multiple roles can be defined to provide specific privilege sets to users.
- Define permissions via Access Control Instructions (ACI), which must be directly edited. Once defined, can be easily assigned or unassigned to an organization, a suborganization or a user. Unassigning a role from one entity only applies to that entity. Roles will still exist and remain assigned and be available for reassignment to other entities, so are more suited for organizations in which access changes will be frequently required.
- Can control visibility of channels and user's ability to overwrite channels. Settings within the XML Display Profile can make channels in the XML document visible or invisible by default. In addition, the default channels in the XML document can be prevented from being overridden.
Users
- Represent the identity of a person. Can be created within an organization or suborganization by its admin.
- Can be associated with multiple roles, but user must be within the roles' scope. In addition users inherit attributes from the suborganization.
- Belong to only one organization or suborganization; however, users can be easily moved from one organization to another if the admin has the privilege to do it.
- Can personalize visibility of channels.
Scenario 1: Hierarchical Structure with Suborganizations and Roles
Although you should strive for as flat a structure as possible, some hierarchy is useful to provide necessary groupings. The high-level steps to create a hierarchical structure are:
- Creating a top-level organization.
- Identifying all the functional or organizational groupings of users in your enterprise and determine for which ones you want to create a DIT structural entity, that is, ones that need to have specific privileges. Typically this should be only the largest subdivisions in your enterprise and the administrators for managing them. Use names that are generic or functional, so reorganizations and name changes will not be problematic.
- For each DIT entity that has some affiliation with the top-level organization, creating either a suborganization (that is, an organization under another organization in the iPlanet Directory Server Access Management Edition world) or a role for that entity.
Use the following guidelines to decide whether to use a suborganization or role:
- Define a suborganization for entities that contain groupings of users with similar access needs. Typically this will be broad functional or organizational entities for which a single set of permissions could be assigned.
- Define a role if it is possible that users in the child organizations need to have this role. All users belong to an organization or suborganization. If they do not have any roles assigned to them, they inherit their permissions from the organization in which they reside. Therefore, if you want a user to have attributes from both the organization they reside in and any parent organizations, you must use the role mechanism and assign them multiple roles.
- For each role, defining a RoleAdministratorRole to manage the role. Then set the ACIs appropriately (management privileges: add or delete users, modify role attributes, and so on.)
- Defining the users who will access your enterprise. If users are inheriting their privileges from their organization, place them in the appropriate organization. If users are receiving their privileges through role assignments, they must be placed so that they are within the role's scope, that is, within the organization or a child of the organization in which the role is defined.
Figure 2-1 illustrates a hierarchical directory structure. In this figure, the top-level organization is Sesta.com. Directly beneath the top-level is the SestaAdminRole to administer the organization and the Corporate and Partners suborganizations. The Corporate organization has three suborganizations: Finance, Operations, and Sales. Because there are multiple types of users within the Sales organization, two roles for are defined: SalesRole1 and SalesRole 2. Within the Partners organization there are three suborganizations: Partner1, Partner2, and Partner3. Each of these organizations, requires its own administrator, so three roles are defined and each one is associated with the appropriate organization.The partner roles are PartnerAdmin1, PartnerAdmin2, and PartnerAdmin3.
Figure 2-1 Hierarchical Directory Structure
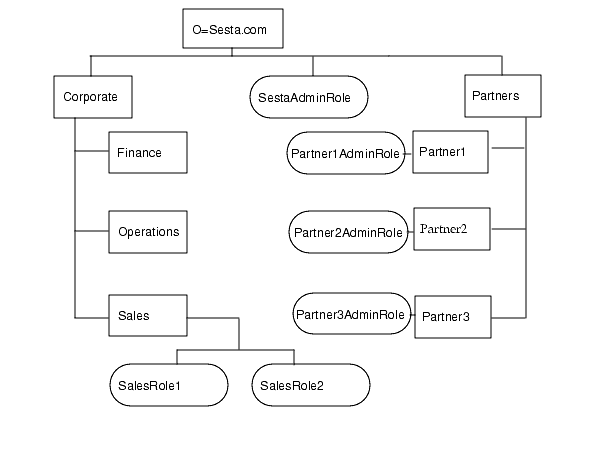
Scenario 2: Flat Tree Structure
If your organization changes often, a flatter or even totally flat tree structure may be appropriate. A structure with one organization, with one People container, and roles all at the same level is often useful if your enterprise changes frequently. With one organization, enterprise changes will not impact your DIT. All access privileges will be defined using roles and since all users are in the single People container and all roles are at the same level, any user can be assigned any role.
Figure 2-2 illustrates a flat directory structure. In this figure, the top-level and only organization is Sesta.com. All entities are defined directly beneath this top-level organization. They include the SestaAdminRole to administer the organization, four roles for the various corporate functions needed by the Finance, Operations, Sales1 and Sales2 users, and six roles for the user functions required by the partners: Partner1Role, Partner2Role, Partner3Role, Partner1AdminRole, Partner2AdminRole and Partner3AdminRole.
Figure 2-2 Flat Directory Structure
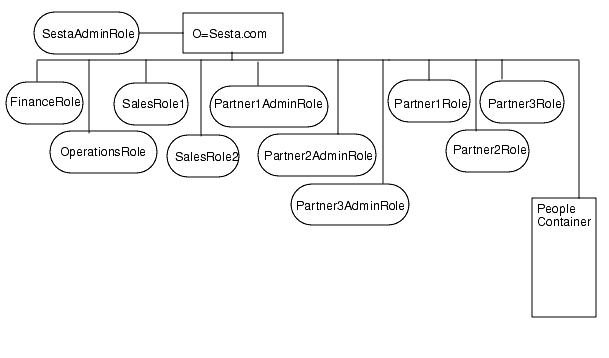
Creating New Organizations and Suborganizations
Organizations and suborganizations allow you to structure and group users for administration and access control purposes. Once you have determined the hierarchy or structure for your enterprise you must create the necessary organizations and suborganizations to implement it. By default, when you create a new organization or suborganization, there are no services, policies, users, or roles defined for it. Therefore, whenever you create a new organization or sub-organization, you need to perform the following high-level steps to configure it:
- Registering all the services you want available to the organization. See "To Register a Service"" for information. Typically, at a minimum you will want to register the following services:
- Authentication. The Core authentication service and any authentication service with which users in the organization will use to authenticate (LDAP, anonymous). See"Configuring Authentication"" for further information.
- URL Policy Agent.
- User.
- Portal Server Configuration. Any Portal Server services you want to enable for users in the organization (Desktop and NetMail).
- Creating templates for each of the registered services. See "To Create a Template for a Service"."
- Creating the policies needed to grant users within the organization access privileges. See "Overview of How Sun ONE Portal Server Uses Policy Management"" for more information on using policies.
- Adding users to the organization. See "To Add a New User"" for information.
- Creating and assigning any roles you want in the organization. See "To Create a New Role"" and "To Assign a Role to a User"" for information.
- Configuring the services enabled for your organization. To configure the Desktop, see Chapter 4 "Administering the Desktop Service." To configure NetMail, see Chapter 6 "Administering the NetMail Service."
For a single linear procedure to create a new organization and configure it to use portal, see "Creating a New Portal Organization".
To Create a New Organization or Suborganization
See "Planning Organizations, Suborganizations, and Roles" for recommendations on how to plan your organizations and suborganizations for use with Sun ONE Portal Server.
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- By default, when you log in, User Management is selected in the View menu, and Organizations is selected in the Show menu.
All created organizations are displayed in the navigation pane.
- If you are creating a suborganization, use the navigation pane to select the organization where the suborganization will be created.
- Click New in the navigation pane.
The Create Organization template displays in the data pane.
- Type a value for the name of the organization or suborganization in the Create Organization template.
- Choose a status of active or inactive.
The default is inactive. This can be changed at any time during the life of the organization or suborganization by selecting the properties arrow. Choosing inactive disables log in to the organization or sub-organization.
- Click Create.
The new organization or suborganization displays in the navigation pane.
To Register a Service
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in User Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization for which you want to register a service.
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Services from the Show menu.
- Click Register.
- Select the service or services to register from the data pane and click Register. Use Select All to register all the services.
To Create a Template for a Service
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in User Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization where the registered service exists.
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Services from the Show menu.
- Click the properties arrow next to the registered service.
- If the No Template Available prompt appears, click Create.
- Accept or modify the default attribute values for the service and click Save.
For information on the setting iPlanet Directory Server Access Management Edition specific service attributes, see the iPlanet Directory Server Access Management Edition Administrator's Guide. For information on the setting Sun ONE Portal Server specific service attributes, see the appropriate appendix in this guide.
To Add a New User
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- By default, when you log in, User Management is selected in the View menu, and Organizations is selected in the Show menu.
- Navigate to the organization or suborganization where the user will be created.
- Choose Users from the Show menu and click New.
The Create User template appears in the data pane.
- Select the services to assign to the user and click Next.
Typically, at a minimum you will want to register the Desktop, NetMail, Session, URL Domain Access, and URL Policy Agent services for most users.
- Enter the user information and click Create.
The new user appears in the navigation pane.
To Create a New Role
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- By default, when you log in, User Management is selected in the View menu, and Organizations is selected in the Show menu.
- Navigate to the organization or suborganization where the role will be created.
- Choose Roles from the Show menu and click New.
The Create Role template appears in the data pane.
- Enter the role information (Name, Description, Type, Permissions) and click Create.
The new role appears in the navigation pane.
Note If you are creating a customized role for delegated administration, you must have previously defined the ACI privileges for the role. See Chapter 3 "Configuring Delegated Administration," for information.
To Assign a Role to a User
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in User Management.
- Navigate to the organization or suborganization where the role will be created.
- Choose Users from the Show menu.
- Click the properties arrow next to the user who will be assigned the role.
The user profile information appears in the data pane.
- In Roles for this User, click Add to display a list of all available roles to assign.
The Add Roles template appears.
- Check the box next to the roles to assign and click Submit.
The Roles for this User box is updated with the assigned roles.
- Click Save to save the changes.
Enabling Existing Users to Access the Sun ONE Portal Server
When you install the Sun ONE Portal Server on an existing instance of iPlanet Directory Server Access Management Edition, users are not registered to use the Sun ONE Portal Server Desktop. In order to allow users to access the Desktop, you must enable them. Use the following procedures to enable users in the default organization or in another organization.
To Enable Users in the Default Organization
Before you start you will need the to obtain some configuration information. If you do not know all the details of the configuration, the information can be retrieved using a script from the /var/sadm/pkg/SUNWps/pkginfo file.
- Determine or retrieve the following information from the /var/sadm/pkg/SUNWps/pkginfo file:
- The distinguished name for the directory manager (referred to as DS_DIRMGR_DN/). Default value is cn=Directory Manager.
- The directory manager password (referred to as DS_DIRMGR_PASSWORD/).
- The fully qualified domain name of the directory server (referred to as DS_HOST/).
- The port on which the directory server runs (referred to as DS_PORT/). Default value is 389.
- The root suffix of the directory tree (referred to as DS_ROOT_SUFFIX/). Default value is o=isp.
- The default organization of the Sun ONE Portal Server installation (referred to as DS_DEFAULT_ORG/). Default value is o=domain-name.
- The base directory of the Sun ONE Portal Server installation (referred to as /BaseDir/). Default value is /opt.
If you do not know the configuration information, run the following script and refer to the output to obtain the information you will need to complete this procedure..
- Change directories to iPlanet Directory Server Access Management Edition utilities directory. For example, if the base directory is /opt, enter:
cd /IDSAME_BaseDir/SUNWam/bin
- If the root suffix of the directory server and the default organization are not the same, execute the following command:
./ldapsearch -h /DS_HOST/ -p /DS_PORT/ -D /DS_DIRMGR_DN/ -w /DS_DIRMGR_PASSWORD/ \ -b "ou=People,/DS_DEFAULT_ORG/,/DS_ROOT_SUFFIX/" "(uid=*)" dn | \ /usr/bin/sed 's/^version.*//' > /tmp/.tmp_ldif_file1
- If the root suffix of the directory server and the default organization are the same, execute the following command:
./ldapsearch -h /DS_HOST/ -p /DS_PORT/ -D /DS_DIRMGR_DN/ -w /DS_DIRMGR_PASSWORD/ \ -b "ou=People,/DS_ROOT_SUFFIX/" "(uid=*)" dn | \ /usr/bin/sed 's/^version.*//' > /tmp/.tmp_ldif_file1
- Execute the following command
grep "^dn" /tmp/.tmp_ldif_file1 | awk '{
print $0
print "changetype: modify"
print "add: objectclass"
print "objectclass: sunPortalDesktopPerson"
print "objectclass: sunPortalNetmailPerson\n" }' >
/tmp/.tmp_ldif_file2
- Execute the following command.
./ldapmodify -c -h DS_HOST -p DS_PORT \ -D DS_DIRMGR_DN -w DS_DIRMGR_PASSWORD -f /tmp/.tmp_ldif_file2
- Remove all temporary files.
rm /tmp/.tmp_ldif_file1 /tmp/.tmp_ldif_file2
To Enable Users in a Non-Default Organization
- Determine or retrieve the following information from the /var/sadm/pkg/SUNWps/pkginfo file:
- The distinguished name for the directory manager (referred to as DS_DIRMGR_DN/). Default value is cn=Directory Manager.
- The directory manager password (referred to as DS_DIRMGR_PASSWORD/)
- The fully qualified domain name of the directory server (referred to as DS_HOST/)
- The port on which the directory server runs (referred to as DS_PORT/). Default value is 389.
- The root suffix of the directory tree (referred to as DS_ROOT_SUFFIX/). Default value is o=isp.
- The organization of the Sun ONE Portal Server installation for which you want to update the users (referred to as DS_ORG_TO_UPDATE/). Default value is ".
- The base directory of the Sun ONE Portal Server installation (referred to as /BaseDir/). Default value is /opt.
- Register services for the organization or suborganization containing the existing users you want to enable. See "To Register a Service"" for information on the procedure.
- Create a template for each service you register. See "To Create a Template for a Service"" for information on the procedure.
- Create and assign policies for each service. See "To Create a Desktop Policy"," "To Create a NetMail Policy"," and "To Assign a Policy to an Organization"" for information.
- Set the URL to which to redirect successfully authenticated users from the organization. See "To Redirect Successful Login User to the Desktop URL".
- Change directories to iPlanet Directory Server Access Management Edition utilities directory. For example, if the base directory is /opt, enter
cd /IDSAME_BaseDir/SUNWam/bin
- Enable users within the organization or organizations, do one of the following:
- To enable users only within a particular organization, defined as DS_ORG_TO_UPDATE/, then use the following command:
./ldapsearch -h /DS_HOST/ -p /DS_PORT/ -D /DS_DIRMGR_DN/ -w /DS_DIRMGR_PASSWORD/ \ -b "ou=People,/DS_ORG_TO_UPDATE/,/DS_ROOT_SUFFIX/" "(uid=*)" dn | \ /usr/bin/sed 's/^version.*//' > /tmp/.tmp_ldif_file1
- To enable users in all organizations, then use the following command:
./ldapsearch -h /DS_HOST/ -p /DS_PORT/ -D /DS_DIRMGR_DN/ -w /DS_DIRMGR_PASSWORD/ \ -b "/DS_ROOT_SUFFIX/" "(uid=*)" dn | \ /usr/bin/sed 's/^version.*//' > /tmp/.tmp_ldif_file1
- Execute the following command:
grep "^dn" /tmp/.tmp_ldif_file1 | awk '{
print $0
print "changetype: modify"
print "add: objectclass"
print "objectclass: sunPortalDesktopPerson"
print "objectclass: sunPortalNetmailPerson\n" }' > /tmp/.tmp_ldif_file2
- Execute the following command:
./ldapmodify -c -h DS_HOST -p DS_PORT \ -D "DS_DIRMGR_DN" -w DS_DIRMGR_PASSWORD -f /tmp/.tmp_ldif_file2
- Remove all temporary files.
rm /tmp/.tmp_ldif_file1 /tmp/.tmp_ldif_file2
- Change directory to Portal Server utilities directory.
cd /IDSAME_BASEDIR/SUNWps/bin
- Execute the following to load the display profile for your non-default organization.
./dpadmin modify -u "uid=amadmin,ou=people,DS_DEFAULT_ORG,DS_ROOT_SUFFIX" -w DS_DIRMGR_PASSWORD -d "NON_DEFAULT_ORG,DS_DEFAULT_ORG,DS_ROOT_SUFFIX" \ IDSAME_BASEDIR/SUNWps/samples/desktop/dp-org.xml
- To enable users in another organization, repeat steps Step 7 through Step 13.
Creating a New Portal Organization
The following task describes all the steps to create a new organization and enable it for portal use.
- Create the new organization.
- Select User Management from the View menu.
- Select Organizations from the Show menu.
- Click New.
The Create Organization template opens in the data pane.
- Type the new organization name. The Organization Status should be Active. Click Create.
The newly created organization appears in the navigation page.
- Register services for the organization.
- Select User Management from the View menu and select the newly created organization.
- Select Services from the Show menu.
- Click Register.
The Register Services template appears in the data pane. Click the check box for the to the following minimum services, then click Register.
- Core
- LDAP
- URL Policy Agent
- User
- Desktop
- NetMail
The newly registered services appear in the navigation pane.
- Create templates for the registered services.
- Select User Management from the View menu.
The newly created organization should still be selected.
- Select Services from the Show menu.
- One by one, click the properties arrow icon next to the services and create the templates.
For the Core service, change the value for User's Default Redirect URL to /portal/dt (to cause the sample portal to be displayed.) The default might be /amconsole/base/AMAdminFrame. Also, select the appropriate authentication means for the Authentication menu.
- Create the Desktop policy.
- Select Policy Management from the View menu.
- Select Policies from the Show menu.
- Click New to create new policy.
The Create Policy template appears in the data pane.
- For Name, type Desktop Access Policy. Choose Desktop as the Service. Then click Create.
- Click Add Rule. Make sure Has Privilege to Execute Desktop is checked and click Save.
- Assign the newly created Desktop policy.
- Select User Management from the View menu.
The newly created organization should still be selected.
- Select Policies from the Show menu.
- Click Assign.
The Assign Policies template appears in the data pane.
- Click the check box for the newly created Desktop Access Policy and click Assign.
The navigation pane is updated with the assigned policy.
- Create the NetMail policy.
- Select Policy Management from the View menu.
- Select Policies from the Show menu.
- Click New to create new policy.
The Create Policy template appears in the data pane.
- For Name, type NetMail Access Policy. Choose NetMail as the Service. Then click Create.
- Click Add Rule. Make sure Has Privilege to Execute NetMail is checked and click Save.
- Assign the newly created NetMail policy.
- Select User Management from the View menu.
The newly created organization should still be selected.
- Select Policies from the Show menu.
- Click Assign.
The Assign Policies template appears in the data pane.
- Click the check box for the newly created NetMail Access Policy and click Assign.
The navigation pane is updated with the assigned policy.
- Load the display profile for the new organization.
- Select User Management from the View menu.
The newly created organization should still be selected.
- Select Services from the Show menu.
- Click the properties arrow icon next to Desktop.
The Desktop template appears in the data pane.
- Use the Download XML and Upload XML links to load the display profile to LDAP. Click Save when done.
Note You could also use the dpadmin command if desired to load the display profile to LDAP. See the Sun ONE Portal Server 6.0 Administrator's Guide for more information.
- Create a new user in the new organization to use for test purposes.
- Select User Management from the View menu.
- Select Organizations from the Show menu.
- Select the newly created organization.
- Select Users from the Show menu.
- Click New.
The Create User template appears in the data pane.
- Click the check boxes beside the services and click Next.
- Fill in the user information and click Create.
- Access the new organization's Desktop.
- Log out of the administration console.
- Open a browser window and type:
http://server:port/amserver/login?org=neworg
The users's Desktop should appear.
Configuring Authentication
This section describes how to configure Sun ONE Portal Server authentication. iPlanet Directory Server Access Management Edition provides a framework for authentication. Authentication is implemented through plug-in modules that validate the user's identity. iPlanet Directory Server Access Management Edition provides seven different authentication modules as well as a Core authentication module. The iPlanet Directory Server Access Management Edition admin console is used to set the default values, to register authentication services, to create an organization's authentication template, and to enable the service. Because the Core authentication module provides the overall configuration for authentication, the Core authentication module must be registered and a template for it created for each organization before you can configure any of the specific authentication modules.
During installation the Core authentication is registered and a template is created for it in the default organization. In addition, the installation also registers and creates templates for the following authentication modules:
- LDAP—LDAP authentication allows any valid user within the search base of the directory tree to log in to the Sun ONE Portal Server. This will automatically assign a user to a specific role.
- Membership—Membership authentication allows a user to create an account and personalizes it without the aid of an administrator. With this new account, the user can access it as a registered user.
- Anonymous—Anonymous authentication allows a user to log in and be granted access without providing a user name or password. Anonymous access can be limited to specific types of access (for example, access for read or access for search) or to specific subtrees or individual entries within the directory.
The high-level steps to configure an authentication module are as follows:
- Registering the Core authentication service for each organization. See "To Register a Service"" for the steps to register a service.
- Creating a template for the Core authentication service. See "To Create a Template for a Service"" for the steps to create template for a service.
- Registering the authentication services to support for each organization. See "To Register a Service"" for the steps to register a service.
- Creating service templates for the authentication services to support for the organization. See "To Create a Template for a Service"" for the steps to create a template for an authentication service. For information on the setting the service attributes, see the iPlanet Directory Server Access Management Edition Administrator's Guide, Chapter 5, "Authentication Options."
- Configuring the authentication menu. See "To Configure the Authentication Menu"" for the steps to configure the menu.
To Configure the Authentication Menu
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in User Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization that you want to configure authentication for.
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Services from the Show menu.
- Click the properties arrow next to Core.
- Enable the appropriate authentication modules by selecting them in the Authentication Menu field of the Organization section.
By default, Sun ONE Portal Server installation enables LDAP and Membership.
- Click Save.
- Use the following URL to verify that the authentication menu appears with the appropriate choices by logging in to the admin server.
To Configure LDAP Authentication to an External Directory
When you install the Sun ONE Portal Server, the installation program configures LDAP authentication to directory instance automatically. The installation program allows you to install an internal instance of the directory on the local server and configure LDAP authentication to that internal directory or to configure LDAP authentication to a pre-existing external instance of the directory. Once you have your initial configuration, there are some scenarios where you might want to configure authentication to an external LDAP directory. For example, you may want to isolate authentication information for particular organization onto a dedicated LDAP server for performance or security reasons..
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in User Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization that you want to configure authentication for.
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Services from the Show menu.
- Click the properties arrow next to Core.
- Check Dynamic User Profile Creation and click Save.
- Click the properties arrow next to LDAP.
- Set the appropriate LDAP Attributes for your server. The following example sets up access to the LDAP server ds-sesta1.sesta.com on port 389 with a search start point of ou=people,dc=sesta,dc=com and using an anonymous bind:
Primary LDAP Server and Port: ds-sesta1.sesta.com:389
Secondary LDAP server and port: ds-sesta1.sesta.com:389
DN to Start User Search: ou=people,dc=sesta,dc=com
DN for Root User Bind: blank
Password for Root User Bind: blank
User Naming Attribute: uid
User Entry Search Attributes: employeenumber
User Search Filter: blank
Search Scope: subtree
Enable SSL to LDAP Server: off
Return User DN to Auth: off
Authentication Level: 0
- Click Save.
Configuring Anonymous Authentication
The Sun ONE Portal Server supports two methods for implementing anonymous authentication:
- Using the Authentication-less User ID attributes. Users accessing the Desktop URL are automatically authenticated and granted access to the Desktop.
- Using an Anonymous user session. Users select Anonymous from the Authentication menu, log in as anonymous,and are granted access to the Desktop.
When you install the Sun ONE Portal Server product, by default the installation program enables anonymous authentication to the Desktop of the default organization using the Authentication-less User ID attributes. To implement this feature, the Sun ONE Portal Server installation program creates a user account, authlessanonymous, and sets up access for this user within the following two Desktop Services global attributes:
- Authorized Authentication-less User IDs
- Default Authentication-less User ID
Sun ONE Portal Server can support both authless and anonymous authentication to be configured at the same in the sense that you can do the following:
- Configure the Desktop to work in authless mode.
- Configure the authentication menu so that Anonymous is one of the displayed choices.
- Access the Desktop with browser A, thereby accessing it in authless mode.
- Access http:/server/amserver/login with browser B, and select Anonymous, and see the Desktop.
At this point you are using authless mode in browser A and anonymous mode in browser B.
The way in which the Desktop is accessed occurs in two different ways. One, authless, was through a direct reference to /portal/dt and the other (anonymous) was indirectly through /amserver/login.
The iPlanet Directory Server Access Management Edition Login menu could be avoided by configuring iPlanet Directory Server Access Management Edition to only have anonymous login in the menu.
Both authless and anonymous authentication are not supported simultaneously in that when you access /portal/dt without an iPlanet Directory Server Access Management Edition session, only one of two things happens:
- The Desktop will redirect to /amserver/login, which may automatically do an Anonymous login and redirect you back to /portal/dt.
- The Desktop will run in authless mode.
You do not have to disable anonymous authentication to use authless. But if you want the above item a to work, you have to disable authless mode.
To Configure Anonymous Authentication (Anonymous User Session Method)
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Navigate to Service Management by choosing View Service Management.
- Click the properties arrow next to the Desktop service.
The Desktop attributes appear in the data pane.
- Click the value listed in the Authorized Authentication-less User IDs attribute and click Remove.
- Delete the value in the Default Authentication-less User ID attribute.
- Click Save.
- Choose User Management from the View Menu
- Choose Organizations from the Show menu in User Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization that you want to configure authentication for.
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Services from the Show menu.
- Register and configure the Anonymous service.
- Add Anonymous to the Authentication menu.
- Create an anonymous user account.
See "To Add a New User"."
To Configure Anonymous Authentication (Authentication-less User ID Method)
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Create an authlessanonymous user account with the password authlessanonymous.
See "To Add a New User"".
- Navigate to Service Management by choosing View Service Management.
- Click the properties arrow next to the Desktop service.
The Desktop attributes appear in the data pane.
- Add the fully distinguished name for the authlessanonymous user to the Authorized Authentication-less User IDs attribute. For example:
uid=authlessanonymous, ou=People, o=sesta.com, o=isp
- Specify the fully distinguished name for the authlessanonymous user in the Default Authentication-less User ID attribute.
- Click Save.
You must close and restart your browser to access the Desktop using the newly configured Authentication-less User ID method. The Authentication-less User ID method allows you to specify the UID of the user account in the query string. For example, to access the Desktop from the default organization of sestat.com, use the following URL:
http://server:port/portal/dt?dt.suid=uid= authlessanonymous, ou=People,o=sesta.com, o=isp
To Configure UNIX Authentication
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in User Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization that you want to configure authentication for.
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Services from the Show menu.
- Click Register.
- Check UNIX in the data pane and click Register.
- Click the properties arrow next to UNIX.
- Click Create.
- Set the appropriate UNIX Attributes for your server.
- Click Save.
- Click the properties arrow next to Core.
- Add UNIX to the Authentication menu.
Overview of How Sun ONE Portal Server Uses Policy Management
This section describes how to use iPlanet Directory Server Access Management Edition Policy Management feature. See the iPlanet Directory Server Access Management Edition documentation for the actual steps to use to create, modify, and delete policies.
The iPlanet Directory Server Access Management Edition Policy Service enables you to define rules or access to resources. Policies can be role-based or organization-based and can offer privileges or define constraints. Sun ONE Portal Server ships with two policies:
- Ability to execute SunONE Desktop - Enables users to display the Desktop
- Ability to execute SunONE NetMail - Enables user to run NetMail
Note Chapter 4 "Administering the Desktop Service" and Chapter 6 "Administering the NetMail Service" provide detailed descriptions on assigning their specific policies.
The high-level steps to use policies are:
- Registering the Policy service for an organization. (This will be done automatically for the organization specified at installation.) Suborganizations do not inherit their parent's services, so you need to register a suborganization's Policy service. See "To Register a Service"" for information.
- Creating the policy. Policies are created through the Policy Management interface. Once a named policy is created, it can be assigned to roles or organizations via the User Management interface. If you use the default Desktop and NetMail policies, you can skip this step. See "To Create a Desktop Policy"" and "To Create a NetMail Policy"" for information.
- Assigning the policy to users. Once a policy has been named and created, it can be assigned to the organization or role. This is done using the User Management interface. Assigning a policy at the organization level makes its attributes available to all entries in the organization. Assigning policy to a role makes its attributes available to all users who contain the role attribute. See "To Assign a Policy to an Organization"" for information.
To Create a Desktop Policy
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in Policy Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization that you want to create a policy
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Policies from the Show menu.
- Click New.
- Type "Ability to execute Portal Server Desktop" in the Name field.
- Select Desktop as the Service type.
- Click Create.
- Set the Conflict Resolution level.
See Appendix C "Desktop Attributes" for information on setting Conflict Resolution level.
- Click Add Rule and Save.
To Create a NetMail Policy
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in Policy Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization that you want to create a policy
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Policies from the Show menu.
- Click New.
- Type "Ability to execute Portal Server NetMail" in the Name field.
- Select NetMail as the Service type.
- Click Create.
- Set the Conflict Resolution level.
See Appendix C "Desktop Attributes" for information on setting Conflict Resolution level.
- Click Add Rule and Save.
To Assign a Policy to an Organization
- Log in to the iPlanet Directory Server Access Management Edition admin console as administrator.
- Choose Organizations from the Show menu in User Management.
All created organizations display in the navigation pane.
- Navigate to the organization or suborganization that you want to assign a policy.
Use the Show menu in the navigation pane and the Location path in the location pane.
- Choose Policies from the Show menu.
- Click Assign.
- Check the checkbox next to the policy to assign and click Assign.
Logging In to the Sun ONE Portal Server Desktop
If you installed the sample portal, users will be able to log in to the sample Desktop. In addition, the Sun ONE Portal Server supports a variety of other user logins. This section describes some of the other user ways users can log in to the Sun ONE Portal Server.
To Log In to the Sample Desktop
To access the sample Desktop, type the following URL:
http://server:port/portal/dt
To Log In to a Suborganization
If users have access privileges to an organization, they can also log in to suborganizations within the organization. For example, if a user has access to the organization A which has a suborganization B, type the the following URL to log in to suborganization B:
http://server:port/amserver/login?org=B
To Log On Using Anonymous Authentication
Note You must register the anonymous authentication module to support anonymous authentication. See "Configuring Anonymous Authentication" for information on registering and enabling anonymous authentication modules.
- Log on using the following URL:
http://server:port/portal/dt
- At the iPlanet Directory Server Access Management Edition authentication page, click Anonymous.
- The sample Desktop appears.
- If desired, and if the Membership authentication module has been register, use the Login screen to create and register a user ID.
Managing Logging
Sun ONE Portal Server uses the iPlanet Directory Server Access Management Edition logging and debugging APIs.
By default, the Sun ONE Portal Server log and debug files are located in:
- /var/opt/SUNWam/logs
- /var/opt/SUNWam/debug
The iPlanet Directory Server Access Management Edition admin console allows you to define the following logging attributes:
- Max Log Size
- Number Of History Files
- Log Location
- Logging Type
- Database User Name
- Database User Password
- Database Driver Name
See the iPlanet Directory Server Access Management Edition Administrator's Guide for further information.