Chapter 1 Solaris for ISPs Overview
Welcome to SolarisTM for ISPsTM. This Solaris overpack builds upon the open architecture and scalability of the Solaris operating system to provide the optimum operating environment for Internet service providers and their customers.
Solaris for ISPs Architecture
Solaris for ISPs is organized into two collections of software. The platform software extends the Solaris foundation, adding features that enable ISP services but are not directly accessed by ISP subscribers. The ISP services provide subscriber functionality such as Internet news, FTP, and World Wide Web access while taking advantage of the extended Solaris environment.
Figure 1-1 Basic architecture of Solaris for ISPs
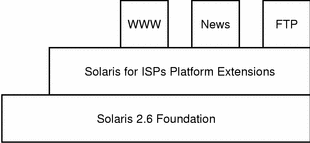
Solaris for ISPs Platform Extensions
Solaris for ISPs includes the following enhancements to the Solaris operating system:
-
SunTM Internet AdministratorTM
-
Host configuration software
-
SunTM Internet Services MonitorTM
-
SunTM Directory Services
-
SunscreenTM SKIP
-
FlexLM License Server
-
HotJavaTM browser
-
Java Development Kit
Sun Internet Administrator
Sun Internet Administrator provides secure central management for distributed ISP services. It gives ISP administrators the following features:
-
Single sign-on for administrators. ISP administrators log onto Sun Internet Administrator once to access all functions for which they have authorization. Services developed according to ISP guidelines and managed from Sun Internet Administrator receive log-on information from it; the user is not subsequently challenged.
-
Secure communications between administrators' client machines and remote service hosts. The optional SKIP software can be installed and configured on all connections to the console, and from the console to the service host machines, making those communications snoop-proof and spoof-proof.
-
Logging of administrator actions for traceability. Each administrator action, from initial log-on attempt through logout, is logged via the syslog utility. This provides both troubleshooting and accountability information.
-
Remote management of existing ISP services. Service components provided with Solaris for ISPs can all be managed from the Sun Internet Administrator, regardless of their location on the network. Additionally, SunTM Internet FTP ServerTM and SunTM Internet News ServerTM are three-tier components and receive all the security benefits built into Sun Internet Administrator. See "Managing Services with Sun Internet Administrator" for more information on service interaction with Sun Internet Administrator.
-
Extensibility for existing services. ISPs can integrate their own applications with Sun Internet Administrator and manage them in the same way as services provided with Solaris for ISPs. See Chapter 7, Integrating Existing Service Applications for instructions on integrating applications with Sun Internet Administrator.
Host Configuration Software
The Solaris for ISPs host configuration software provides the following functionality:
-
Software installation. Administrators install and uninstall all Solaris for ISPs software using the host configuration software. Administrators can save installation scenarios for use in a JumpStart finish script to repeat installations automatically.
-
Solaris foundation configuration. To improve security and conserve resources, unneeded Solaris services are disabled. Security-related components of Solaris are configured appropriately for an ISP environment.
-
Intrusion detection. Periodically, the intrusion detector checks its log file, determining whether any failed log-on attempts have occurred since the last check. If an intrusion attempt has occurred, the detector collects the logged data and passes it to the user-specified notification mechanism (such as electronic mail).
-
Server process management. This cron job ensures that server processes (such as news servers) are indeed running. If any server has stopped abnormally, the server process manager starts that server.
-
Log file management. Audit and syslog logs are cycled daily. The log file management daemon archives logs weekly and deletes any archive older than one month.
The host configuration software is a required software component. It is installed on every Solaris for ISPs host machine.
Sun Internet Services Monitor
The performance monitoring software allows an ISP to set up special client machines that emulate a subscriber's experience with the ISP services. The performance monitoring applet can be set to connect to any combination of Web, mail, news, and directory services servers and collect information on their performance from a subscriber's perspective. This data is collected on the monitoring host machine and viewable with a Web browser.
Sun Internet Services Monitor is a two-tier application. It is manageable through Sun Internet Administrator, but does not receive the benefits of single sign-on or administrator authentication. See "Managing Services with Sun Internet Administrator" for more information on the two-tier architecture.
Sun Directory Services
This Lightweight Directory Access Protocol (LDAP) implementation provides a shared repository for both user (administrator) and service configuration information. Administrators store subscriber information in the repository as well. Features in this release of Sun Directory Services include:
-
Conformance to LDAP v3 Internet standards.
-
A Remote Access Dialup User Service (RADIUS) server that provide authentication for remote users connecting to the network through a Network Access Server (NAS).
-
A Network Information System (NIS) server that integrates into an existing NIS environment to provide an integrated naming service.
-
A complete suite of administration tools, including the Deja directory editor, a Java--implemented administration console for management of the directory, and a Web gateway for access from any browser.
Sun Directory Services is manageable from Sun Internet Administrator as an X-based application.
Sun Directory Services installs with a no-license limitation of 1K (one thousand) entries in the directory. A license certificate for 5K (five thousand) entries ships with Solaris for ISPs and must be redeemed and registered with the FlexLM license server before it takes effect. See the instructions in the Solaris for ISPs Installation Guide for details of redeeming and installing the license certificate.
See Chapter 5, Using Directory Services and Chapter 6, Solaris for ISPs Directory Services Schema of this book for information about the role of Sun Directory Services in Solaris for ISPs. The Sun Directory Services documentation consists of two books, Sun Directory Services 3.1 Administration Guide and Sun Directory Services 3.1 User's Guide, both delivered as AnswerBook2TM packages. The Sun Directory Services Deja tool also has full on-line help.
Sunscreen SKIP
SunscreenTM SKIP is based on the Simple Key-management for Internet Protocols (SKIP) standard of key management for IP encryption. Characteristics of SKIP include:
-
Automatic certificate exchanges
-
Sessionless protocols
-
Multicast and unicast packet protocols for IPv4 and IPv6
-
Certificate Discovery Protocol (CDP)
The full SKIP technology is available only in North America, but a version exists for export to other parts of the world. When SKIP is installed, its manual pages are located at /opt/SUNWicp/man.
FlexLM License Server
The FlexLM license server is used by Sun Directory Services to manage licenses of various sizes. If you already have a license server in your network (version 4.1 or later), you can use it to serve Sun Directory Services licenses.
Sun Directory Services allows 1K (one thousand) entries before requiring a license. This is sufficient to install and initialize the directory. In any reasonable ISP application, however, more entries will quickly be required. Follow the directions in the Solaris for ISPs Installation Guide for acquiring a license key and configuring the server.
After it is installed, the FlexLM manual pages are located at /opt/SUNWste/licene_tools/man.
HotJava Browser
The HotJava browser is provided with Solaris for ISPs to support Sun Internet Administrator and other administration user interfaces in the product. It supports the following Internet standards and protocols:
-
Java Development Kit 1.1.6
-
HTTP 1.1 Protocol
-
HTML 3.2
-
Tables and Frames
-
Persistent Cookies
-
GIF and JPEG Media Formats
-
AU Audio Format
-
FTP and Gopher File Transfer Protocols
-
SMTP and MIME E-mail Protocols
-
SOCKS Protocol
-
Secure Sockets Layer (SSL) 3.0
-
Java Archive (JAR) Format
Java Development Kit
The Java Development Kit (JDK) is provided with Solaris for ISPs to support the use of Java in the product. JDK version 1.1.5 includes the following new capabilities:
-
Internationalization
-
Signed applets
-
JAR file format
-
AWT (window toolkit) enhancements
-
JavaBeansTM component model
-
Networking enhancements
-
Math package for large numbers
-
Remote Method Invocation (RMI)
-
Reflection
-
Database connectivity (JDBC)
ISP Services
Services in this version of Solaris for ISPs include:
-
SunTM WebServerTM (SWS)
-
SunTM Internet News ServerTM
-
SunTM Internet FTP ServerTM
In addition to any graphical user interfaces, all ISP services also provide full command-line access for scripting.
SWS
SWS is a highly reliable, secure, standards-based Web server for accessing, managing, and distributing information over the Internet, extranets, or intranets. Features added in this release of SWS include:
-
Support for HTTP/1.1. SWS supports the latest version of the hypertext transfer protocol, including named virtual hosts and content negotiation.
-
Enhanced scalability. Multiple instances of the server process can run on a single machine and can be managed through the same administration graphical user interface. The number of available virtual hosts is thus raised geometrically.
-
Java servlet support. Using servlets rather than the more usual CGI scripts provides the cross-platform advantages of Java on the server side while improving processing speed.
-
Secure HTTP communications. SWS includes secure-socket layer (SSL) functionality and support for Verisign certificates for safe, encrypted communications.
-
Microsoft FrontPage support. SWS supports popular FrontPage extensions in the areas of authoring, administration, and dynamic content.
SWS is a two-tier application. It is manageable through the Sun Internet Administrator, but does not receive the benefit of single sign-on. It has been configured to share administrator data with Sun Internet Administrator. See Chapter 7, Integrating Existing Service Applications for details on this configuration and "Managing Services with Sun Internet Administrator" for more information on the two-tier architecture.
Sun Internet News Server
Sun Internet News Server is a high-performance, highly-scalable news server. Significant features include:
-
High performance and client-connection scalability. A multithreaded, multi-process daemon handles client connections, taking advantage of multiprocessor Solaris servers to provide scalability in handling large numbers of simultaneous news reader connections.
-
Full-featured news feed handling. Based on INN from the Internet Software Consortium (INN release 1.5 sec. 2), Sun Internet News Server maintains all the usability improvements of that implementation in the area of news feed handling.
-
Separate feed handling and news reader service functionality. The service for news readers is separable from the feed handling functions to enable horizontal scalability in handling news reader connections.
-
Centralized, browser-based management. Sun Internet News Server is a three-tier service that integrates with Sun Internet Administrator for centralized administration and full security benefits. See "Managing Services with Sun Internet Administrator" for more information on the three-tier architecture.
Sun Internet FTP Server
This scalable, high-performance FTP server offers the following enhancements:
-
Multiple domains on a single host. Sun Internet FTP Server supports IP-based virtual hosting. Each virtual host has its own configuration files that tune the server for that particular domain.
-
Configurable user authentication. Sun Internet FTP Server can use either UNIX accounts or entries in the SunDS registry to authenticate administrators.
-
Centralized, browser-based management. Sun Internet FTP Server is a three-tier service that integrates with Sun Internet Administrator for centralized administration and full security benefits. See "Managing Services with Sun Internet Administrator" for more information on the three-tier architecture.
How Solaris for ISPs Installs
Because the typical UNIX server must run a variety of applications, the default Solaris installation assumes that most UNIX services are needed. ISPs focus more narrowly on providing specific services in a public environment. They have heavy performance and security requirements.
To configure Solaris to their needs, ISP administrators typically perform elaborate hardening and tuning tasks. They stop unneeded Solaris services and change file permissions to close security vulnerabilities. This process can take hours.
The host configuration software in Solaris for ISPs automates this hardening and tuning process for the administrator. In addition to copying the necessary software packages to their proper locations, it hardens the underlying Solaris 2.6 foundation, changing file owners and modes where appropriate as well as configuring Solaris security and logging mechanisms. A final step in this process is selectively disabling standard Solaris services (such as finger or rlogin) when they do not support the purpose of a given host machine.
Solaris for ISPs host configuration can be performed interactively by using its graphical user interface, or repeatably and non-interactively using JumpStart.
Host Configuration Model
The configuration process works by building a scenario of the current state of the system, what software components are available to be installed, and what the user has selected for install or uninstall.
Figure 1-2 Solaris for ISPs Host Configuration Process
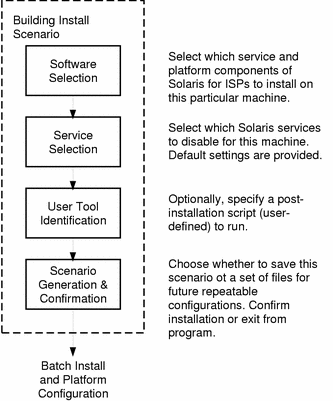
The host configuration software can also be used to reconfigure a host after installation, adding and removing services as needed.
Repeatable Configuration
Interactive host configuration (using the graphical user interface) provides the option to save a configuration scenario (in the form of a binary and some associated files). By creating and saving a scenario, the ISP administrator can use it in a JumpStartTM finish script, forming a non-interactive, one-step installation. Such JumpStart installations are repeatable and can be used to configure identically.
JumpStart is a part of the Solaris operating system that can perform customized, repeatable installations of Solaris both locally and remotely. See the Solaris Advanced Installation Guide for details on how to create a custom JumpStart installation. See Chapter 2 of this guide for information on how to use a scenario file in a finish script for a custom JumpStart installation.
Managing Services with Sun Internet Administrator
Sun Internet Administrator provides secure centralized management for all ISP services, both locally and across a network of hosts. It launches the administration GUIs (where present) of individual services upon request from an authorized administrator. Command-line interfaces can also be accessed where appropriate.
Features for a Secure Environment
Sun Internet Administrator provides the following security features:
-
Administrator authentication. Administrators are required to supply a valid user name and password when accessing the GUI.
-
Administrator access control. Access is controlled per ISP service. An administrator allowed to manage FTP servers on the network may or may not also have access to news servers. Console administrators (those who can manage Sun Internet Administrator processes) have access to all services managed by Sun Internet Administrator.
-
Central auditing. Administrators' actions are logged for traceability and accountability.
-
Privacy and integrity protection for all network traffic. The optional SKIP software can be configured to protect all connections to and from Sun Internet Administrator. SSL can also be used for secure HTTP traffic.
Sun Internet Administrator supports services in two architectures: three-tier and two-tier. Only the three-tier architecture receives all of the above-listed security benefits. Four types of service UIs are supported:
-
Three-tier, browser-based applications receive all security benefits offered by Sun Internet Administrator.
-
Two-tier, browser-based applications cannot make use of the single sign-on feature, but are manageable through the Sun Internet Administrator. If they use SWS to support the administration application, they can configure it to provide administrator authentication. (See Chapter 7, Integrating Existing Service Applications for details on this configuration.) The two-tier architecture is included to support legacy applications.
-
X-based applications receive all the benefits of a three-tier application.
-
Command-line functions (scripts, programs, or in combination) receive all the benefits of three-tier applications. Any number of them can be registered for a given service and managed by Sun Internet Administrator, which constructs a Web interface to the command-line programs.
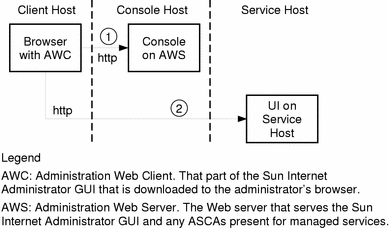
Three-Tier Application Architecture
The recommended three-tier browser-based application architecture receives all Sun Internet Administrator security benefits.
Figure 1-3 Three-Tier ISP Service Architecture

As shown in Figure 1-3, an administrator uses the following steps to access a service's administration functions:
-
From a browser, the administrator requests a specific URL (the location of the main Sun Internet Administrator GUI page).
The AWC is downloaded to the client browser, where the administrator can choose a service to manage.
-
Sun Internet Administrator prompts the administrator for user name and password. The administrator need not use a UNIX account for access to the console GUI; a directory services repository (Sun Directory Services) manages administrator information for Sun Internet Administrator. This connection should be secured by using secure HTTP.
The selected service resolves to an URL, designating the services's ASCA. The server agent GUI is downloaded in response. At this step, control passes to the service's administration program.
-
Subsequent access is directly between the client browser and the component's server agent on the AWS.
The AWS authenticates the administrator against the directory services, and logs each administrator request. If the administrator has appropriate access, requests are passed to the ASRA.
-
The ASCA communicates with the ASRA via a protocol chosen by the developer of the service. Appropriate IP-level security measures should be taken to protect this connection and its traffic.
The ASRA again authenticates and logs each administrator action. To protect the network communications, the ISP can add IP-level encryption, if that is desired, by using SKIP.
ASCA and ASRA modules for command line and X-based programs are provided in Solaris for ISPs. Sun Internet Administrator uses them automatically when you register these applications.
Two-Tier Application Architecture
For some applications, especially existing services, a two-tier architecture for access via Sun Internet Administrator is more practical. These services can be managed from Sun Internet Administrator, but do not receive the security benefits of single sign-on and logging.
Figure 1-4 Two-Tier ISP Service Architecture
As shown in Figure 1-4, an administrator uses the following steps to access a service's administration functions:
-
From a browser, the administrator requests a specific URL (the location of the main console GUI page).
This step is the same as for the three-tier architecture. The AWC is downloaded to the client browser, where the administrator can choose a service to manage.
-
The selected service resolves to a URL, designating the component's ASRA. If the service's administration GUI is not browser-based, other protocols may be used at the developer's option.
-
Subsequent access is directly between the client browser and the service's remote agent. Appropriate IP-level security measures should be taken to protect this connection and its traffic.
In a two-tier architecture, services are not able to take advantage of the single sign-on feature.
- © 2010, Oracle Corporation and/or its affiliates
