Managing Services with Sun Internet Administrator
Sun Internet Administrator provides secure centralized management for all ISP services, both locally and across a network of hosts. It launches the administration GUIs (where present) of individual services upon request from an authorized administrator. Command-line interfaces can also be accessed where appropriate.
Features for a Secure Environment
Sun Internet Administrator provides the following security features:
-
Administrator authentication. Administrators are required to supply a valid user name and password when accessing the GUI.
-
Administrator access control. Access is controlled per ISP service. An administrator allowed to manage FTP servers on the network may or may not also have access to news servers. Console administrators (those who can manage Sun Internet Administrator processes) have access to all services managed by Sun Internet Administrator.
-
Central auditing. Administrators' actions are logged for traceability and accountability.
-
Privacy and integrity protection for all network traffic. The optional SKIP software can be configured to protect all connections to and from Sun Internet Administrator. SSL can also be used for secure HTTP traffic.
Sun Internet Administrator supports services in two architectures: three-tier and two-tier. Only the three-tier architecture receives all of the above-listed security benefits. Four types of service UIs are supported:
-
Three-tier, browser-based applications receive all security benefits offered by Sun Internet Administrator.
-
Two-tier, browser-based applications cannot make use of the single sign-on feature, but are manageable through the Sun Internet Administrator. If they use SWS to support the administration application, they can configure it to provide administrator authentication. (See Chapter 7, Integrating Existing Service Applications for details on this configuration.) The two-tier architecture is included to support legacy applications.
-
X-based applications receive all the benefits of a three-tier application.
-
Command-line functions (scripts, programs, or in combination) receive all the benefits of three-tier applications. Any number of them can be registered for a given service and managed by Sun Internet Administrator, which constructs a Web interface to the command-line programs.
Three-Tier Application Architecture
The recommended three-tier browser-based application architecture receives all Sun Internet Administrator security benefits.
Figure 1-3 Three-Tier ISP Service Architecture

As shown in Figure 1-3, an administrator uses the following steps to access a service's administration functions:
-
From a browser, the administrator requests a specific URL (the location of the main Sun Internet Administrator GUI page).
The AWC is downloaded to the client browser, where the administrator can choose a service to manage.
-
Sun Internet Administrator prompts the administrator for user name and password. The administrator need not use a UNIX account for access to the console GUI; a directory services repository (Sun Directory Services) manages administrator information for Sun Internet Administrator. This connection should be secured by using secure HTTP.
The selected service resolves to an URL, designating the services's ASCA. The server agent GUI is downloaded in response. At this step, control passes to the service's administration program.
-
Subsequent access is directly between the client browser and the component's server agent on the AWS.
The AWS authenticates the administrator against the directory services, and logs each administrator request. If the administrator has appropriate access, requests are passed to the ASRA.
-
The ASCA communicates with the ASRA via a protocol chosen by the developer of the service. Appropriate IP-level security measures should be taken to protect this connection and its traffic.
The ASRA again authenticates and logs each administrator action. To protect the network communications, the ISP can add IP-level encryption, if that is desired, by using SKIP.
ASCA and ASRA modules for command line and X-based programs are provided in Solaris for ISPs. Sun Internet Administrator uses them automatically when you register these applications.
Two-Tier Application Architecture
For some applications, especially existing services, a two-tier architecture for access via Sun Internet Administrator is more practical. These services can be managed from Sun Internet Administrator, but do not receive the security benefits of single sign-on and logging.
Figure 1-4 Two-Tier ISP Service Architecture
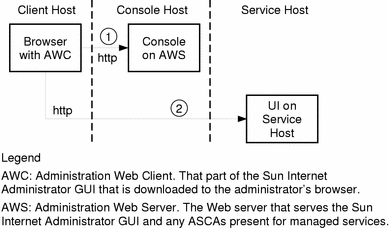
As shown in Figure 1-4, an administrator uses the following steps to access a service's administration functions:
-
From a browser, the administrator requests a specific URL (the location of the main console GUI page).
This step is the same as for the three-tier architecture. The AWC is downloaded to the client browser, where the administrator can choose a service to manage.
-
The selected service resolves to a URL, designating the component's ASRA. If the service's administration GUI is not browser-based, other protocols may be used at the developer's option.
-
Subsequent access is directly between the client browser and the service's remote agent. Appropriate IP-level security measures should be taken to protect this connection and its traffic.
In a two-tier architecture, services are not able to take advantage of the single sign-on feature.
- © 2010, Oracle Corporation and/or its affiliates
