Configuring SunScreen SKIP
You can configure only one interface at a time using skiptool. If you have more than one network interface, you must configure each separately.
Configuring SunScreen SKIP requires completing several steps:
-
Adding authorized systems ("Adding Authorized Systems")
-
Communicating in the clear (Off) ("Communicating In the Clear (Off)")
-
Communicating using SKIP Version 1 ("Communicating Using SKIP Version 1")
-
Communicating using SKIP ("Communicating Using SKIP")
-
Communicating using ESP/AH ("Communicating Using ESP/AH". This is typically used in test mode.)
-
-
Adding excluded systems, if any ("Adding Excluded Systems")
-
Setting up the behavior for unauthorized systems ("Behavior for Authorized Systems")
-
Enabling SKIP (Access control button is enabled) ("Enabling SKIP")
-
Verifying the installation and set up ("Verifying the SKIP Installation and Set Up")
There are two optional steps that are helpful in troubleshooting and in tuning key usage, respectively.
-
Viewing SunScreen SKIP statistics ("Viewing SunScreen SKIP Statistics ")
-
Key management with skiptool ("Key Management with skiptool")
Each step is described in further detail in the following sections.
When skiptool is started just after the initial installation of the software, the following defaults are in effect:
-
Access control is disabled
-
Unauthorized systems are set at No Access
-
Starting skiptool
To start skiptool, complete the following steps:
-
Open a window, and type
% xhost +mysun
-
Become root, and type
# skiptool&
If you are configuring a system that has multiple network interfaces, you can specify the interface following the skiptool command; for example, skiptool le1.
The main window of skiptool appears, as shown in Figure 3-1.
Figure 3-1 skiptool Main Window

The skiptool Main Window
The skiptool main window has several important features:
-
The File button
-
The Access Control buttons
-
The Authorized and Excluded Systems lists
-
The Add and Delete (Management) buttons
File Menu
The file menu has five submenus:
Load--Loads current ACL from the kernel. This is useful if you have modified the ACL through other tools and want to update the configuration in skiptool.
Key Management--Defines the parameters for key usage, including when to delete an unused key (in seconds) and how much to transmit per key (in Kbytes).
SKIP Statistics--Brings up one of six statistics windows: (1) Network Interface Stats, (2) SKIP Header Stats, (3) Encryption Stats (Version 1), (4) Encryption Stats (Version 2), (5) Key Stats, or (6) Authentication Stats.
Save--Makes the configuration permanent. Before saving, it prompts you to add any systems that are in use, that have access, and that are not currently on the authorized list. The next time that you reboot this configuration is used. Quitting and restarting skiptool will not affect either saved or unsaved changes in configuration. (Another way to save the current ACL is to use the command-line tool skipif with the -s option.)
Note -
If you do not save the changes in the configuration, you can use them until the next time you reboot your machine when they will no longer be in effect.
Exit--Closes all open windows and quits SunScreen SKIP. The Statistics window will not close when you quit skiptool.
Access Control Buttons
Access Control button--This button toggles to enable or disable SKIP. When SKIP is enabled, the ACL rules apply. (For example, you could have only the "default" entry in the authorized systems list and some entries in the excluded systems list. In this case, any host except those that are in the excluded systems list could connect.) When SKIP is disabled, any system can connect, if the "default" entry is configured in the clear.
Unauthorized System button--This button is used to set the policy regarding unauthorized systems.
Note -
If a default authorized host entry exists, this policy does not take effect. The default entry has the name "default" and the ACL looks for this entry (in authorized or excluded host lists) if it cannot find a given entry that matches the host or network criteria.
The policy can be
No Access--Does not allow unauthorized hosts to connect.
Ask For Confirmation--Every time an unauthorized host connects, a pop-up window appears on which the user determines whether or not that particular connection should be allowed.
Add Automatically--Any host that sends packets to this system is automatically added to the authorized systems list.
Note -
It is recommended that you do not change the value from "No Access."
Authorized Systems/Excluded Systems Lists
Authorized Systems--A list of systems that are authorized to have access to this host. System types are host, network, or nomadic. Secure systems are denoted by a padlock or the Sun Microsystems' logo next to the system name, depending on the type of security being used.
Excluded Systems--A list of systems that are specifically denied access to your system. When you move or add a system to the excluded list, it is immediately excluded.
skiptool allows you to move systems from the list of authorized systems to the list of excluded systems and vice versa with the arrows between the two lists.
Management Buttons
These buttons enable you to add or delete a system from the access list. The buttons are available for both authorized and excluded systems.
Add--Brings up the Add pop-up menu where the system type to be added to the ACL is selected:
Host--Adds an individual host, either with or without security.
Network--Adds a network, either with or without security.
Nomadic--Adds a nomadic identity, with SKIP Version 1 or SKIP Version 2 security.
Delete--Deletes the selected system from the list. When an item is deleted, the deletion occurs immediately and cannot be undone.
You may also move ACL entries from one list to another with the arrow buttons. These arrow buttons make it easy to add or delete system when troubleshooting.
If you add or delete ACL entries from one list to another, the addition or deletion takes effect immediately.
Adding Authorized Systems
Any remote host with which you want to communicate (send or receive data) must be configured using the Add pop-up window.
An authorized host may or may not be using encryption. The Add pop-up window provides four options:
-
Off or not using encryption
-
Using SKIP encryption
-
Using SKIP Version 1 encryption
-
Using ESP/AH (manual keying)
You add hosts to the authorized systems list using the Add button, located at the bottom left of the main window of skiptool.
The valid types of remote hosts that you can add to your ACL are
-
Host
-
Network
-
Nomadic
When setting up SunScreen SKIP, be sure to include any NFS servers and NIS or DNS name servers on the authorized systems list, otherwise your system may hang.
Note -
To avoid problems such as this, a safe approach at the beginning is to add the clear "default" entry. Once you become more comfortable with SKIP configuration, you can remove it.
To determine the servers your system communicates with, use the following commands:
-
For NFS servers, type
mount
-
For NIS servers, type
ypwhich
-
For DNS servers, consult your system administrator
-
It might be useful to verify the current routing entries used by the local system. To verify the current routing entries, type netstat -rn and add specific network ACL entries.
If you do not specify a system that you currently have in use when you enable access control, a menu will come up and ask if you want to add the system. It also checks for multicast routers that are being used for others and adds them to the proposed list of systems to add.
Regardless of the type of system that you are adding to the ACL, you must implement the same policy on both your machine and the entity with which you wish to communicate securely over the intranetworks or internetworks. If you do not configure both systems properly, the packets are silently dropped and it appears as if that particular host does not exist. skiplog is useful in diagnosing this situation.
When you click on the Add button, the Add pop-up window appears. From the menu in this window, you select the type of connection: Host, Network, or Nomadic. Next, use the pull-right menu to set the security level. After you have selected the level of security, the appropriate Properties window becomes available. The Add System Properties window is used to set up the options for the type of encryption used by the host, network, or nomadic system being authorized. Table 3-1shows what type of encryption can be used with hosts, networks, or nomadic systems. The procedures in the sections following the table detail how to set up each encryption option.
Table 3-1 Type of Security Available, by Type of System|
Type of System |
Type of Security |
|||
|---|---|---|---|---|
|
Off (none) |
SKIP |
SKIP (Version 1) |
ESP/AH (manual keying) |
|
|
Host |
X |
X |
X |
X |
|
Network |
X |
X |
X |
X |
|
Nomadic |
-- |
X |
X |
-- |
Adding a Host or Network with No Encryption
This procedure is used to allow a host or network access to your system without using any encryption.
-
Click and hold on the Add button at the bottom of the authorized systems list on the skiptool main window.
-
Select the type of connection being authorized: Host or Network. (Nomadic does not offer this option.)
-
Pull right on the type of connection and select Off.
The Add Host properties or Add Network properties dialog box will appear (Figure 3-2).
Figure 3-2 Add Host/Properties--No Encryption
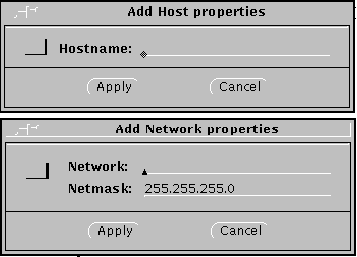
-
In the Add Host or Network properties window, enter the name or IP address of the host system to be added to your ACL.
In the case of a network, you must define the network with the IP address and the netmask.
Setting Up Security for a Host, Network, or Nomadic System
These procedures enable a host, network, or nomadic system access to your system according to the encryption rules set up using one of the procedures below. Remember, both your system and the other system need to use the same properties in order to communicate.
Explanations of the Dialog Box Parameters
The three encryption dialog boxes (SKIP, SKIP Version 1, and ESP/AH) use common set-up parameters, as you can see in Figure 3-3 through Figure 3-10. Explanations of the parameters follow the figures. The procedure follows the explanations.
Figure 3-3 Host--Add SKIP Host Properties

Figure 3-4 Host--Add SKIP Version 1 Properties
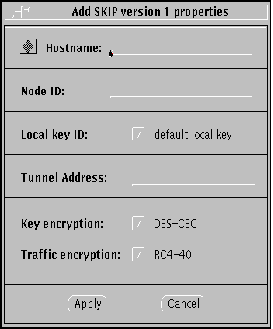
Figure 3-5 Host--Add ESP/AH Host Properties
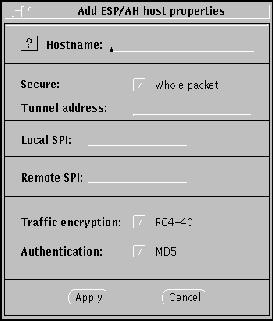
Figure 3-6 Network--Add SKIP Network Properties
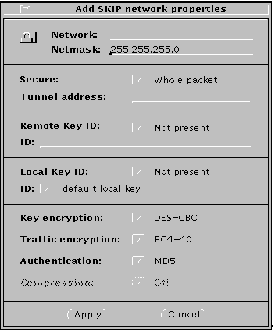
Figure 3-7 Network--Add SKIP Version 1 Properties
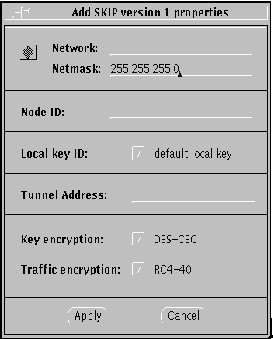
Figure 3-8 Network--Add ESP/AH (Manual Keying) Network Properties
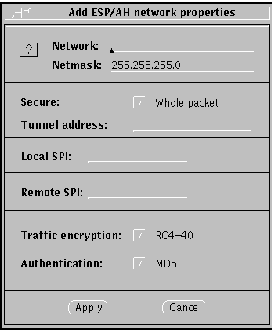
Figure 3-9 Nomadic--Add SKIP Properties (Nomadic)

Figure 3-10 Nomadic--Add SKIP Version 1 (Nomadic)

-
Hostname/Network/Nomadic. Enter the name of the host or nomadic system, or the IP address of the host or network.
-
Netmask. (network only) Enter the netmask of the network. The default (255.255.255.0) is already entered.
-
Secure button. (SKIP and ESP/AH only) Set to either Whole packet ("tunnel mode") or Data only ("transport mode"). Whole packet is recommended because it offers a greater degree of security.
-
Node ID. (SKIP Version 1 only) This is the IPv4 key ID.
-
Tunnel Address. Use the tunnel address as the destination IP address. Tunnel address is generally used for clients of encrypted gateways where the IP address of the host entered here serves as the intermediary for any or all hosts on a network whose topography must remain unknown or hidden from the rest of the world. This is called topology hiding. This field is not available if you select Data only.
-
Local/Remote SPI. (ESP/AH only) You need to provide some sort of identifier for the local and remote systems when using manual keying. These are converted to hexadecimal numbers by SKIP. The Local security parameters index (SPI) is your machine, and the Remote SPI is the destination machine. Alternatively, you can enter the Local/Remote SPI values directly in hexadecimal by typing an eight-digit hexadecimal quantity with the prefix "0x."
-
Remote Key ID button. (SKIP only) Select whether you want the remote system's key ID included in SKIP packets and, if so, the namespace that key ID occupies. Selecting Not Present means that the receiver key ID will not be sent.
The following namespaces are listed in this menu:
-
Not Present
-
IPv4 Address
-
MD5 (DH Public Value)
Not Present is the default. It uses the IP address of the remote system to identify its certificate. If a remote system has a key ID other than that identified by its IP address, set the namespace and indicate the remote system's key ID in the ID field.
-
-
Remote Key ID field. (SKIP only) The namespace indicated in the Remote Key ID field is determined by the type of certificate (Table 3-2) that you are using or have obtained for this system:
Table 3-2 Remote Key ID FieldCertificate Type
Remote Key ID Field
CA (Sun or other)
IPv4
Self-generated unsigned key
MD5 (DH Public Value)
If the Remote Key ID field has been set to other than Not Present, enter the key ID in hexadecimal format in the ID field (such as 0x0a000000). It must contain the appropriate key ID for the system being authorized based upon the selection made with the Remote Key ID button. Depending on the type of certificate, this information may be obtained from the master key ID on the diskette or from the local key ID field of the other host.
-
Local Key ID and ID buttons. Use the Local Key ID button to indicate whether you want your local system to send its key ID in the SKIP packet and, if so, the namespace that key occupies. If you select Not Present, the sender's key ID is not sent in the packet and the remote system uses the local system's IP address to decide what key to use.
Note -If you have installed new local keys after you have started skiptool, skiptool will not list them. You must restart the key manager with the skipd_restart command to list them and rerun skiptool.
All the local-key times installed for this host are listed. Select the namespace for the local key that is to be used for communication with the above host. Once you have selected the namespace, click on the ID field to select the key to be used, in hexadecimal, for communication with this host.
-
Key Encryption button. Selecting this button lists the available key encryption algorithms. The algorithms available are determined by the system type and the selected encryption method selected.
-
Traffic Encryption button. Select the algorithm for encrypting the traffic between your system and the remote system. The algorithms available are determined by the system type, the version of SunScreen SKIP, and the method of encryption selected.
-
Authentication button. Use the authentication button to select the type of authentication for the packets. Currently, SunScreen SKIP supports only one type of authentication--MD5. You can also select None for no authentication.
-
Compression button. Compression is not available at this time.
Adding Authorized Systems with Encryption
-
Click and hold on the Add button at the bottom of the authorized systems list on skiptool's Main Window.
-
Select the type of connection being authorized: Host, Network, or Nomadic.
-
Pull right on the type of connection and select the type of encryption that you want to use.
-
If the remote host system also uses SKIP and the traffic between your systems is to be encrypted, select SKIP.
-
For systems using Sun Microsystems' SunScreen SPF-100, select SKIP Version 1.
-
If ESP/AH (manual keying) is to be used, click on ESP/AH.
-
-
On the Add properties window, enter the name or IP address of the host system to be added to your ACL.
-
Determine whether Whole packet ("tunnel mode") or Data only ("transport mode") is secure by clicking on the appropriate selection for the Secure button.
-
Each type of encryption requires that certain options be set.
The parameters selected are determined by the type of system being authorized and your security policies. The options to be considered are based on the method of encryption selected. They are
-
For systems using SKIP: Tunnel address, Remote Key ID, Local Key ID. If you leave the tunnel address blank, it will default to the peer's address.
-
For SKIP Version 1: Key ID, Tunnel address.
-
For ESP/AH systems: Tunnel address, Local SPI, Remote SPI.
-
-
Select the appropriate algorithms buttons for Key encryption, Traffic encryption, and Authentication.
The options available for each system are based upon the method of encryption selected from the Security pop-up menu:
-
Key Encryption button: Selecting this button lists the available key encryption algorithms. The algorithm available is determined by the type of system and selected method of encryption.
-
Traffic Encryption button: Selecting this button lists the algorithms available for encryption between your system and the remote system. The algorithms that are available for key and traffic encryption depend on the packages that were installed on the system, such as core product and key upgrades. The algorithms available determine the type of system and the method of encryption selected.
-
Authentication button: Use this button to select the type of authentication for the packets.
-
Compression button: Compression is not currently supported.
-
-
Click Apply to add the host to the authorized systems list.
Refer to the previous section for descriptions of the fields and buttons.
Repeat Steps 1 though 8 for all encrypted hosts. Remember that your policy options for each system entered on your ACL must be the same as those entered on the system entity with which you wish to communicate through encrypted channels. If the configuration on your system does not match that of the party with which you wish to communicate, the packets are silently dropped. It will simply appear as though that host no longer exists.
Default System Entry
The default system entry is used when no other more specific ACL entry matches a host. Often, this entry is set to clear to allow hosts that are not listed in the ACL to communicate in the clear. It may, however, be used to create a default encryption rule.
Note -
If the default ACL remains and is set to Off, it is unnecessary to add any entity with the Off security option. Further, if the default ACL remains and is set to Off, the option set by the Unauthorized Systems button never goes into effect because all systems are considered as authorized.
Communicating In the Clear (Off)
Typically, the NIS and DNS servers to which your servers have access are set up as communicating with your system in the clear or unencrypted. In addition, any host that does not use an encryption package must be set up to communicate with you in the clear.
Communicating Using SKIP Version 1
Complete the following steps to set these fields for encrypted traffic between your server and the system to be authorized.
-
After selecting the type of system and setting the security to SKIP, enter the Hostname.
-
Enter the Node ID.
This is the IPv4 key ID.
-
Local Key ID and ID buttons.
Use the Local Key ID button to indicate whether you want your local system to send its key ID in the SKIP packet.
-
Set the Tunnel Address, if you are using topology hiding.
Tunnel addressing is generally used for clients of encrypted gateways where the IP address of the host entered here serves as the intermediary for any or all hosts on a network whose topography is to remain unknown or hidden from the rest of the world.
-
Select the appropriate key and traffic algorithms for the Key and Traffic encryption buttons. Available Key encryption algorithms are DES-CBC and RC2-40. Available Traffic encryption algorithms are RC4-40 and RC2-40.
Communicating Using SKIP
Complete the following steps to set these fields for encrypted traffic between your server and the system to be authorized.
-
After selecting the type of system and setting the security to SKIP, enter the Hostname.
-
Set the Secure button to either Whole packet (`tunnel mode") or Data only ("transport mode").
Whole packet is recommended because it offers a greater degree of security.
-
Set the Tunnel address, if you are using topology hiding.
Tunnel addressing is generally used for clients of encrypted gateways where the IP address of the host entered here serves as the intermediary for any or all hosts on a network whose topography is to remain unknown or hidden from the rest of the world.
-
Use the Remote Key ID button to select whether you would like the remote system's keyID included in SKIP packets.
If so, what namespace does that key occupy. By selecting Not Present, the receiver key ID is not sent.
Not Present is the default. It uses the IP address of the remote system to identify its certificate. If a remote system has a key ID other than identified by its IP address, set the namespaces and indicate the remote system's key ID in the ID Field. The namespace indicated in the Remote Key ID field is determined by the type of certificate that is used or obtained for this system. The type of certificate and the Remote Key ID field for that certificate is shown below
Certificate Type
Remote Key ID Field
CA (Sun or other)
IPv4
Self-generated unsigned key
MD5 (DH Public Value)
-
The following namespaces are used in this menu:
Not present
IPv4 Address
MD5 (DH public Value)
-
If the Remote Key ID field has been set to something other than Not Present, enter the key ID in hexadecimal format in the ID field (0x0a000000).
It must contain the appropriate key ID for the system that is being authorized based upon the selection made in the Remote Key ID field. Depending on the type of certificate, this information may be obtained from the master keyID on the diskette or from the Local key ID field of the other host.
-
Select the appropriate key and traffic algorithms for the Key and Traffic encryption buttons.
Available Key encryption is None, DES_CBC, and RC2-40. Available Traffic encryption is None, RC4-40, and RC2-40.
-
Authentication button.
Use the authentication button to select the type of authentication for the packets. Currently, SunScreen SKIP supports only one type of authentication--MD5. You can also select None for no authentication.
-
Compression button.
Compression is not available at this time.
Communicating Using ESP/AH
ESP/AH (also called manual keying) is typically used in test mode only. It is not recommended for day-to-day operations. To configure a host with which you are using manual keying, both skiptool and the raw_keys files must be configured.
Adding Excluded Systems
If the default entry remains on the authorized systems list, then any remote host with which you want to prevent communication must be configured using the Add button located under the excluded systems list. When setting up an excluded system, you only need to enter the hostname for hosts and network number for networks. For nomadic systems you need to specify the key IDs.
If the state of the host or network changes to an authorized system, you must delete the system from the excluded systems list and add it to the authorized systems list.
The easiest way to exclude a system is to move it from the authorized systems list with the arrow button to the excluded systems list. The arrow buttons make it easy to add or delete systems when troubleshooting and the host is already present in the authorized systems list. If the host does not already exist on one of the lists, it is simpler to add it directly on the excluded systems list so that you can move it easily with the arrow button when you wish to add it to the authorized systems list.
Note -
If you move an encrypted host from the authorized systems list to the excluded systems list with the arrow button, SunScreen SKIP retains the encryption parameters so that if you later move this host back to the authorized systems list, its parameters are restored.
You can also complete the following steps to exclude a system:
-
Click on the Add button at the bottom of the excluded systems list on skiptool's main window.
-
Select the system type: Host, Network, or Nomadic.
-
In the Hostname field on the Exclude System window, enter the name or IP address of the host system that you want to deny access to your system.
If you are excluding a nomadic system, also enter the key ID.
-
Click Apply on the Exclude System window.
 Caution -
Caution - If you add or delete ACL entries from one list to another, the addition or deletion takes effect immediately.
Behavior for Authorized Systems
Once you have entered the authorized systems and the excluded systems, you need to determine what should happen when unidentified systems attempt to obtain access to your system. An unidentified system is unrecognized by SKIP; that is, it is not on either the authorized systems list or the excluded systems list.
Use the Unauthorized Systems button on the main window to select the action SKIP should take when an unidentified system attempts access. When you remove a default entry from these lists, SKIP will take one of the following three actions:
-
No Access
-
Ask for confirmation
-
Add automatically
It is recommended that you leave this entry in the default selection of No Access for greater security.
If you quit skiptool or if you reboot your system, the selection will revert to No Access.
Note -
If a default ACL entry is on the authorized systems list, this option does not take effect.
Once you have configured SunScreen SKIP on your system, you are ready to configure it on the other systems with which you will be communicating either in the clear or through one of the methods of encryption available in SunScreen SKIP. Once both parties have installed and configured SKIP, SKIP should be enabled and your data protected.
- © 2010, Oracle Corporation and/or its affiliates
