| Previous Contents Index Next |
| iPlanet Certificate Management System Agent's Guide |
Chapter 5 Recovering Encrypted Data
This chapter describes how to process key recovery requests and how to recover stored encrypted data when the encryption key has been lost. This service is available only when the Data Recovery Manager subsystem is installed. The Data Recovery Manager Agent Services page allows certified agents to accomplish these tasks.This chapter has the following sections:
Finding and Recovering Keys
Finding and Recovering Keys
If an end user loses a private encryption key or if a key's owner is unavailable, data encrypted with that key cannot be read unless a copy of the private key was archived when the key was created. The archived key can then be recovered and used to read the data.As a Data Recovery Manager agent, you manage key recovery using the Data Recovery Manager's Agent Services page. You can search through archived keys, either to view them or to initiate a key recovery. Once you have initiated key recovery, a minimum number of designated key recovery agents are required to authorize the recovery. Key recovery agents may or may not also be certified Data Recovery Manager agents.
Finding Archived Keys
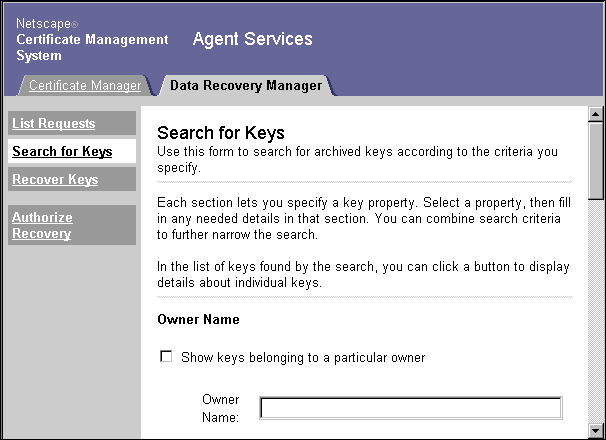
You can search for archived keys to examine them or to initiate recovery. The process of selecting search criteria and selecting a key from the search results is the same in either case.To search for and list archived keys:
Go to the Data Recovery Manager Agent Services page (see Accessing Agent Services).You must submit the proper client certificate to get access to this page.
Click Search for Keys or Recover Keys to display the form in which you specify search criteria.
To search by particular criteria, use one or more of the different sections of the Search for Keys or Recover Keys form. To use a section, select the appropriate checkbox in that section, then fill in any necessary information.
- If you choose Recover Keys, you will have the option of initiating recovery for any key that you find.
- Owner Name. Use this section to find an archived key with a specific owner name. The owner name for a key is much like the subject name for a certificate. It consists of a string that can be used in searches. Select the checkbox and enter the owner name for the key you want to find.
- Key identifiers. Use this section to find an archived key with a specific key identifier or to list all keys within a range of key identifiers.
To find a key with a specific key identifier, enter the key identifier in both the upper limit and lower limit fields. Use decimal or hexadecimal form. Use 0x to indicate the beginning of a hexadecimal number; for example, 0x2A. (Key identifiers are displayed in hexadecimal form in the Search Results and Details pages.)
To find all keys within a range of key identifiers, enter the upper and lower limits of the key identifier range (in decimal or hexadecimal form).
- If you leave either the lower limit or upper limit field blank, all keys before or after the one you specify are displayed.
After entering your search criteria, click Show Key.
- Certificate. Use this section to find the archived key that corresponds to a specific public key. Select the checkbox and paste the certificate containing the corresponding public key (in base-64 encoded form) into the text area. (You must first find and copy the encoded form of the encryption certificate associated with the key pair. Use the Certificate Manager or Registration Manager Agent Services pages to find the certificate; for instructions, see "Examining Certificates," in Chapter 3.)
- Archiver. Use this section to find keys that were archived by a specific server. Select the checkbox and enter the user ID of the Certificate Manager or Registration Manager that submitted the key archival request. Note that this information is available only for archival requests from servers that are remote from the Data Recovery Manager (that is, not installed in the same server root directory).
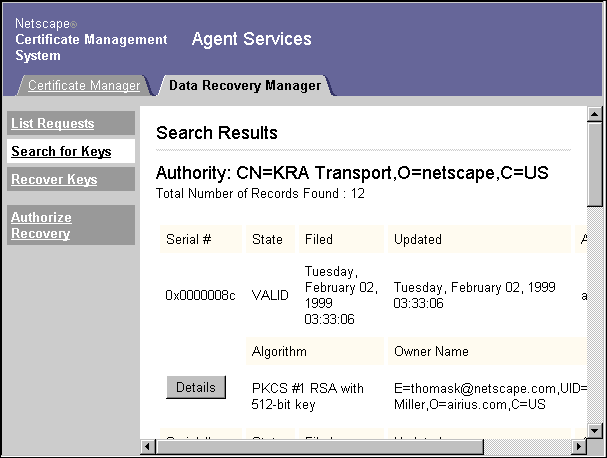
- The Data Recovery Manager displays a list of the keys that match your search criteria. You can select a key in the list and examine it in more detail (described in "Selecting a Key"). If you initiated the search with the Recover Keys button, you have the option of recovering any key returned by the search (described in "Recovering Keys").
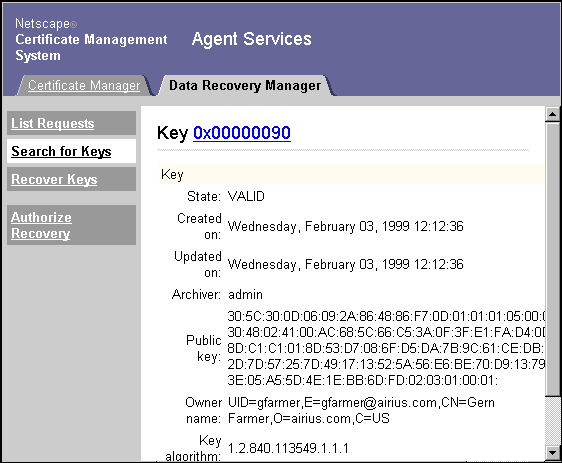
Selecting a Key
To select a key from the list returned by your key search:
On the Data Recovery Manager's Agent Services page, click Search for Keys, specify search criteria, and click Show Key to display a list of archived keys.
On the Search Results form, find a particular key.
- For details, see "Finding Archived Keys."
Click Details next to the key you want to examine.
- If the key you want to see is not shown, scroll to the bottom of the list and select the Next or Previous group of keys.
Recovering Keys
If you perform a search with the Recover Keys button, the Search Results form allows you to initiate the recovery of any key found.
On the Data Recovery Manager's Agent Services page, click Recover Keys, specify search criteria, and click Show Key to display a list of archived keys.
On the Search Results form, find a particular key.
- For details, see "Finding Archived Keys."
Click Recover next to the key you want to examine.
- If the key you want to see is not shown, scroll to the bottom of the list and select the Next or Previous group of keys.
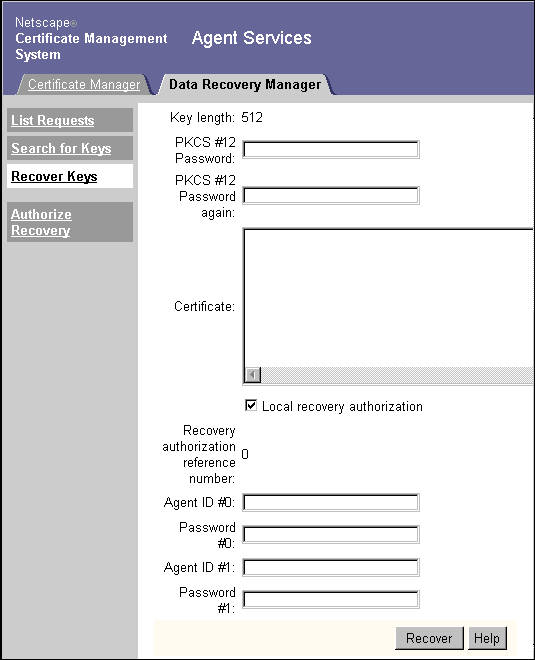
In the Key Recovery form, scroll to the bottom of the key information.
- The details of the selected key are displayed in the Authorize Key Recovery form, which allows you to specify authorization information.
Specify the password that the requester will use in importing the recovered certificate/key pair package.
- The number of key recovery agent authorizations required to recover a key is configured by the system administrator using the CMS window in Netscape Console. The Key Recovery form has space for the required number of authorizations.
Paste the base-64 encoded certificate that corresponds to the archived key into the text area.
Choose whether to authorize recovery locally.
- Use the Certificate Manager or Registration Manager Agent Services pages to find and copy the certificate; see "Examining Certificates," in Chapter 3.
- If you searched for the archived key by using the corresponding public key, the certificate information is automatically transferred here.
If you select this option, assemble the required number of key recovery agents and have each agent fill in his or her user name and password.
Click Recover Now.If you deselect this option, notify the key recovery agents that a recovery has been initiated, giving them the recovery authorization reference number indicated on this form. (For information on how to provide a remote authorization, see "Remote Recovery Authorization.")
If you chose local authorization, the recovery is completed immediately, and the recovered certificate and key pair are sent to your browser in the form of a PKCS #12 package.
In the dialog box that appears, specify the path and filename for saving the encrypted file that contains the recovered certificate and key pair.If you chose remote authorization, you must wait for the recovery agents to enter their authorizations. As they do so, a status page informs you of the progress. When the required number of recovery agents have completed their authorizations, the recovery is completed and the recovered certificate/key pair package is sent to your browser.
Send the encrypted file to the requesting party.
Inform the requesting party of the recovery password in a secure manner.
- The recovering party must use this password to import the recovered certificate/key pair package into his or her client software.
Remote Recovery Authorization
By default, recovery authorization is local. That is, when you initiate the recovery, you assemble the required number of recovery agents, and all of them enter their IDs and passwords on the same Authorize Key Recovery form on your system. When you click Recover Now, the recovery is completed, and you receive the encrypted file that contains the recovered key and certificate.If you deselect the local authorization option, you are choosing remote authorization. When you click Recover Now, the key recovery agents must each access the Data Recovery Manager Agent Services pages at their own locations, and use the Authorize Recovery button to enter each authorization separately. You are informed of the status of the authorizations. When all the authorizations have been entered, the recovery is completed and you receive the encrypted file that contains the recovered key and certificate.
To use the remote authorization feature, the designated key recovery agents must also be designated Data Recovery Manager agents, so that they are privileged to access the Agent Services pages directly. If you are using only local authorization, anyone can be designated as a recovery agent, since only you will need to access the recovery authorization form.
If you are a designated key recovery agent as well as a Data Recovery Manager agent, and another Data Recovery Manager agent informs you that a remote key recovery authorization has been initiated, enter your authorization as follows:
Go to the Data Recovery Manager Agent Services page (see Accessing Agent Services). You must submit the proper client certificate to get access to this page.
The initiating agent is informed that you have completed your authorization.Enter the recovery authorization reference number that was part of the notification.
Click Examine.
- This number identifies the particular key recovery request that you are to authorize.
Viewing Key Service Requests
Key service requests are of two kinds:
Key archival requests, made by remote or local Certificate Managers or Registration Managers
As a Data Recovery Manager agent, you can view these requests. You can search for and list key service requests with a particular status, such as completed or rejected. You can select a key service request from the returned list and examine it in detail.Key service requests are usually handled internally. You do not need to take any action on them unless your system is specially configured.
Listing Key Service Requests
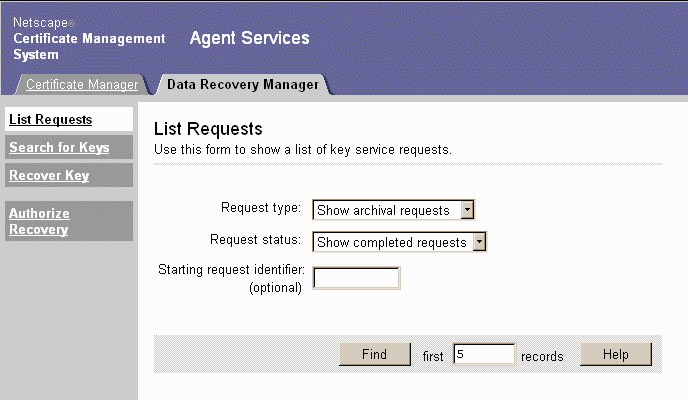
To list key service requests:
Go to the Data Recovery Manager Agent Services page (see Accessing Agent Services). You must submit the proper client certificate to get access to this page.
Click List Requests to display the List Requests form.
Choose the type of requests you want to see from the "Request type" pull-down menu. You can choose to see requests to archive keys, to recover keys, or both.
- Use the List Requests form to specify which key service requests to list.
Choose the statsu of requests you want to see by selecting one of the following choices from the "Request status" pull-down menu:
Show canceled requests. Unless your system is specially configured for it, there will be no cancelled requests.
To start the list at a specific place in the queue, enter the starting request identifier in decimal or hexadecimal form.Show rejected requests. Rejected requests do not comply with your company's archival or recovery policies. Unless your system is specially configured for it, there will be no rejected requests.
Show completed requests. Completed requests include archival requests for which proof of archival has been sent and completed recovery requests.
Show all requests. All requests stored in the system.
Choose the number of matching requests you want to see.
- Use 0x to indicate the beginning of a hexadecimal number; for example, 0x2A. (Key identifiers are displayed in hexadecimal form in the Search Results and Details pages.)
Click Find.
- When you specify a number n, the system displays the first n requests after the starting request identifier that match your specified criteria.
Selecting a Request
To select a request from the queue:
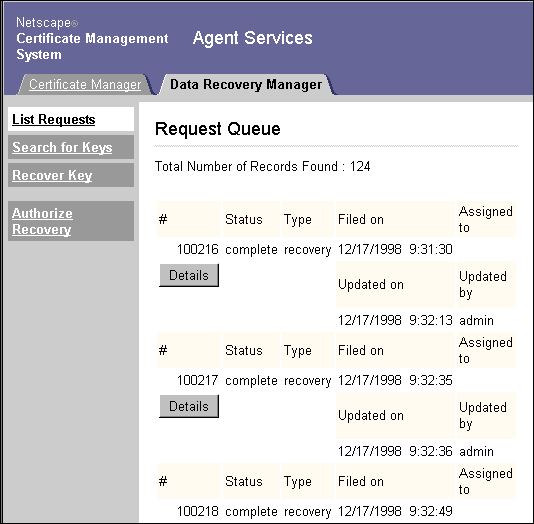
On the Data Recovery Manager's Agent Services page, click List Requests, specify search criteria, and click Find to display a list of key service requests.
On the Key Service Request Queue form, find a particular request.
- For details, see "Listing Key Service Requests."
Click Details next to the selected request.
- If the request you want to see is not shown, scroll to the bottom of the list and select the Next or Previous group of requests.
- The details of the selected key service request appear in the Request details form. You cannot manipulate the request in any way.
- If the system changes the state of the displayed request, and if you use your browser's Back or Forward buttons or the Go (history) menu to move to another page, the data shown can become out of date. To refresh the data, click the highlighted key identifier at the top of the page.
Previous Contents Index Next
Copyright © 2001 Sun Microsystems, Inc. Some preexisting portions Copyright © 2001 Netscape Communications Corp. All rights reserved.
Last Updated April 02, 2001