| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Synchronization for Windows 6.0 Deployment Planning Guide |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Synchronization for Windows 6.0 Deployment Planning Guide |
2. Case Study: Deploying in a Multimaster Replication Environment
3. Case Study: Deploying in a High-Availability Environment Over a Wide Area Network Using SSL
Installation and Configuration Overview
Primary and Secondary Installations
Periodically Linking New Users
Large Deployment Considerations
Increasing Connector Worker Threads
Aligning Primary and Failover Configurations
Setting Multiple Passwords for uid=PSWConnector
Initial idsync resync Operation
Initial idsync resync Operation for Primary Installation
Initial idsync resync Operation for Failover Installation
Periodic idsync resync Operations
Periodic idsync resync Operation for Primary Installation
Periodic idsync resync Operation for Failover Installation
Understanding the Failover Process
Initializing the Connector State
Failover Installation Maintenance
Stopping Synchronization at the Primary Installation
Starting Synchronization at the Failover Installation
Re-enabling the Directory Server Plugins
Changing the PDC FSMO Role Owner
Failing Back to the Primary installation
A. Pluggable Authentication Modules
B. Identity Manager and Identity Synchronization for Windows Cohabitation
Global Telco, a large company with 500,000 employees world-wide, is using Sun Java System Identity Manager (Identity Manager) to provision users between Active Directory, Directory Server, Oracle RDBMS, Novel NDS, and other systems. They have two main data centers: one in the United States, and the other in Europe.
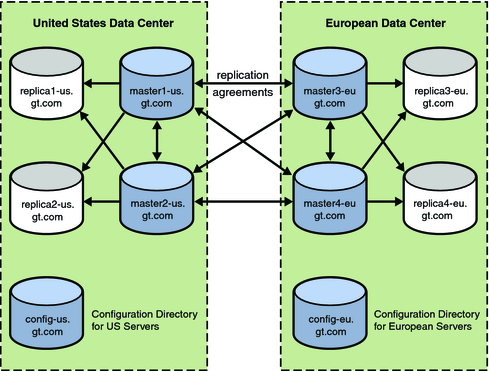
They have a single Active Directory domain (gt.com) with four domain controllers, and a Sun Java System Directory Server Deployment (dc=gt,dc=com) with four masters and four read-only replicas.
The Sun Java System Directory Server topology includes four masters and four read-only replicas. Directory Server is the corporate directory server used to control access to Web-based applications. The directory server has a single root suffix, dc=gt,dc=com; information about the users are stored in the ou=people, dc=gt,dc=example,dc=com container with uid as the naming attribute.
Two masters and two read-only replicas are located in the United States (a separate configuration directory in the United States stores configuration information for these systems).
Two masters and two read-only replicas are located in Europe (a separate configuration directory in Europe stores configuration information for these systems).
All four masters have replication agreements with each other, but the four read-only replicas only have replication agreements with two of the masters as shown in the following figure.
Note - Identity Synchronization for Windows treats hub replicas the same as read-only replicas. In many scenarios, using a hub replica is preferred to using a read-only replica because a hub can be easily promoted to a master.
Figure 3-1 Data Center Information for Directory Server
The Active Directory deployment has a single domain, gt.com, with two domain controllers located in the United States and two in Europe. The user information is stored in the standard cn=users container in Active Directory (cn=users,dc=gt,dc=com).
The Active Directory samaccountname attribute value matches the Directory Server uid attribute, and the Active Directory domain controller with the PDC FSMO role is located in the United States office.
Figure 3-2 Data Center Information for Active Directory
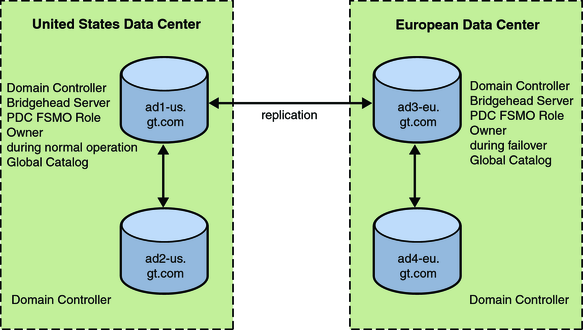
Note - Both ad1-us.gt.com and ad3-eu.gt.com are bridgehead servers which control replication between the two sites.
Global Telco wants to achieve the following:
The users’ passwords for Windows systems must be synchronized with their Directory Server passwords.
The users must be able to change passwords using native mechanisms made in either environment, through the Change Password option in the Task Manager dialog on Windows systems, and a web-based portal for Directory Server.
Identity Synchronization for Windows supports capturing native password changes in Directory Server and Active Directory. Users can continue to change passwords as they always have.
Note - Passwords can be set in Directory Server by passing a pre-hashed password value. However, Identity Synchronization for Windows cannot synchronize passwords from Directory Server to Windows if the password is pre-hashed. Even in installations without Identity Synchronization for Windows, this is not advisable because it circumvents password policy and password history.
Existing Identity Manager functionality must be retained. Identity Manager will continue to provision users to Active Directory and Directory Server.
Identity Synchronization for Windows requires the users’ Directory Server accounts to be explicitly linked to their Windows accounts. This linking is automatically done when Identity Synchronization for Windows is configured to synchronize creations of new users. However, because Identity Manager is provisioning both Active Directory and Directory Server accounts, Identity Synchronization for Windows will not synchronize new users. Global Telco must either run idsync resync command periodically to link newly created users, or Identity Manager must be configured to set the necessary linking attributes when a new Directory Server entry is created.
Support for propagating native password changes made in Directory Server to all systems managed by Identity Manager must be added.
Identity Manager supports synchronizing Active Directory password changes to many other systems because Identity Synchronization for Windows can synchronize password changes from Directory Server to Active Directory. Couple Identity Manager and Identity Synchronization for Windows to synchronize password changes made in Directory Server to any system that Identity Manager supports.
High availability for failover redundancy of all services is required in the European office.
Identity Synchronization for Windows is very robust. Once all components are running, it synchronizes data without losing changes. By default, Identity Synchronization for Windows provides some high availability options such as failover to an alternate Directory Server master, and performing on-demand password synchronization against any Active Directory domain controller. It also includes a watchdog that restarts failed processes.
However, if the machine with the Identity Synchronization for Windows Core or Connector has a hardware failure, then Identity Synchronization for Windows will not synchronize users until it is re-installed on different hardware.
This case study addresses Global Telco's HA requirement by installing a completely separate instance of Identity Synchronization for Windows at the European office.
All communication must use SSL and trusted certificates where possible.
Identity Synchronization for Windows supports SSL communication for all over-the-wire communication. By default, it does not require trusted certificates for SSL communication between connectors and directory sources, but it can be configured to require trusted certificates.