| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Directory Server Enterprise Edition Deployment Planning Guide 11g Release 1 (11.1.1.5.0) |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Directory Server Enterprise Edition Deployment Planning Guide 11g Release 1 (11.1.1.5.0) |
Part I Overview of Deployment Planning for Directory Server Enterprise Edition
1. Introduction to Deployment Planning for Directory Server Enterprise Edition
2. Business Analysis for Directory Server Enterprise Edition
Part II Technical Requirements
3. Usage Analysis for Directory Server Enterprise Edition
4. Defining Data Characteristics
5. Defining Service Level Agreements
6. Tuning System Characteristics and Hardware Sizing
7. Identifying Security Requirements
Determining Authentication Methods
Simple Password Authentication
Simple Password Authentication Over a Secure Connection
Certificate-Based Client Authentication
SASL-Based Client Authentication
Preventing Authentication by Account Inactivation
Preventing Authentication by Using Global Account Lockout
External Authentication Mappings and Services
Password Policies in a Replicated Environment
Password Synchronization With Windows
Determining Encryption Methods
Attribute Encryption Implementation
Attribute Encryption and Performance
Designing Access Control With ACIs
Obtaining Effective Rights Information
Designing Access Control With Connection Rules
8. Identifying Administration and Monitoring Requirements
9. Designing a Basic Deployment
10. Designing a Scaled Deployment
11. Designing a Global Deployment
12. Designing a Highly Available Deployment
Part IV Advanced Deployment Topics
13. Using LDAP-Based Naming With Solaris
14. Deploying a Virtual Directory
Directory Proxy Server connection handlers provide a method of access control that enables you to classify incoming client connections. In this way, you can restrict the operations that can be performed based on how the connection has been classified.
You can use this functionality, for example, to restrict access to clients that connect from a specified IP address only. The following figure shows how you can use Directory Proxy Server connection handlers to deny write operations from specific IP addresses.
Figure 7-2 Directory Proxy Server Connection Handler Logic
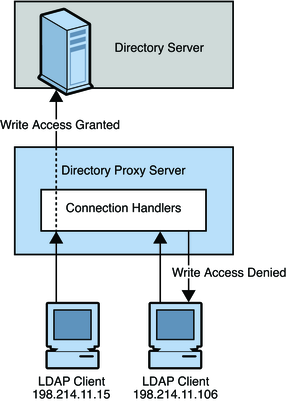
A connection handler consists of a list of criteria and a list of policies. Directory Proxy Server determines a connection's class membership by matching the origination attributes of the connection with the criteria of the class. When the connection has been matched to a class, Directory Proxy Server applies the policies that are contained in that class to the connection.
Connection handler criteria can include the following:
Client physical address
Domain name or host name
Client DN pattern
Authentication method
SSL
The following policies can be associated with a connection handler:
Administrative limits policy. Enables you to set certain limits on, for example, the number of open connections from clients of a specific class.
Content adaptation policy. Enables you to restrict the kind of operations a connection can perform, for example, attribute renaming.
Data distribution policy. Enables you to use a specific distribution scheme for a connection.
For more information about Directory Proxy Server connection handlers and how to set them up, see Chapter 20, Connections Between Clients and Directory Proxy Server, in Oracle Directory Server Enterprise Edition Reference.