| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Directory Server Enterprise Edition Administration Guide 11g Release 1 (11.1.1.5.0) |
| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Directory Server Enterprise Edition Administration Guide 11g Release 1 (11.1.1.5.0) |
Part I Directory Server Administration
2. Directory Server Instances and Suffixes
3. Directory Server Configuration
6. Directory Server Access Control
Creating, Viewing, and Modifying ACIs
To Create, Modify, and Delete ACIs
To View ACIs at the Root Level
Permissions for Typical LDAP Operations
To Allow Normal Users to Manage User Accounts Using dsutil Command
Granting Write Access to Personal Entries
Granting Access to a Certain Level
Restricting Access to Key Roles
Granting a Role Full Access to an Entire Suffix
Granting a Group Full Access to a Suffix
Granting Rights to Add and Delete Group Entries
Allowing Users to Add or Remove Themselves From a Group
Granting Conditional Access to a Group or Role
Setting a Target Using Filtering
Defining Permissions for DNs That Contain a Comma
Restricting Access to the Get Effective Rights Control
Using the Get Effective Rights Control
Advanced Access Control: Using Macro ACIs
Matching for ($dn) in the Target
Substituting ($dn) in the Subject
Logging Access Control Information
Client-Host Access Control Through TCP Wrapping
7. Directory Server Password Policy
8. Directory Server Backup and Restore
9. Directory Server Groups, Roles, and CoS
10. Directory Server Replication
13. Directory Server Attribute Value Uniqueness
15. Directory Server Monitoring
Part II Directory Proxy Server Administration
16. Directory Proxy Server Tools
17. Directory Proxy Server Instances
19. Directory Proxy Server Certificates
20. Directory Proxy Server Load Balancing and Client Affinity
21. Directory Proxy Server Distribution
22. Directory Proxy Server Virtualization
23. Virtual Data Transformations
24. Connections Between Directory Proxy Server and Back-End LDAP Servers
25. Connections Between Clients and Directory Proxy Server
26. Directory Proxy Server Client Authentication
27. Directory Proxy Server Logging
28. Directory Proxy Server Monitoring and Alerts
Part III Directory Service Control Center Administration
Organizations that use repeating directory tree structures can optimize the number of ACIs used in the directory by using macros. When you reduce the number of ACIs in your directory tree, it is easier to manage your access control policy. In addition, the efficiency of your ACI memory usage is improved.
Macros are placeholders that are used to represent a DN or a portion of a DN in an ACI. You can use a macro to represent a DN in the target portion of the ACI, in the bind rule portion, or in both. In practice, when Directory Server gets an incoming LDAP operation, the ACI macros are matched against the resource targeted by the LDAP operation. The matching occurs in order to determine a matching substring, if any matching substring exists. If a match exists, the bind rule-side macro is expanded using the matched substring, and access to the resource is determined by evaluating that expanded bind rule.
This section contains an example of a macro ACI and information about macro ACI syntax.
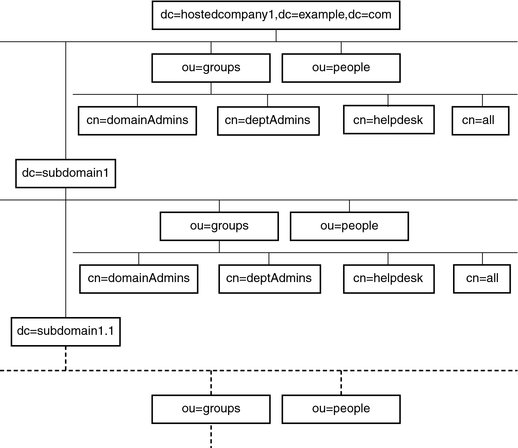
The benefits of macro ACIs and how they work are best explained by using an example. Figure 6-1 shows a directory tree in which using macro ACIs is an effective way of reducing the overall number of ACIs.
In this illustration, note the repeating pattern of subdomains with the same tree structure (ou=groups,ou=people). This pattern is also repeated across the tree because the Example.com directory tree stores the two suffixes dc=hostedCompany2,dc=example,dc=com, and dc=hostedCompany3,dc=example,dc=com, which are not shown in the figure.
The ACIs in the directory tree also have a repeating pattern. For example, the following ACI is located on the dc=hostedCompany1,dc=example,dc=com node:
aci: (targetattr="*") (targetfilter=(objectClass=nsManagedDomain))(version 3.0; acl "Domain access"; allow (read,search) groupdn= "ldap:///cn=DomainAdmins,ou=Groups,dc=hostedCompany1, dc=example,dc=com";)
This ACI grants the domainAdmins group read and search rights to any entry in the dc=hostedCompany1,dc=example,dc=com tree.
Figure 6-1 Example Directory Tree for Macro ACIs
The following ACI is located on the dc=hostedCompany1,dc=example,dc=com node:
aci: (targetattr="*") (targetfilter=(objectClass=nsManagedDomain)) (version 3.0; acl "Domain access"; allow (read,search) groupdn="ldap:///cn=DomainAdmins,ou=Groups,dc=hostedCompany1,dc=example,dc=com";)
The following ACI is located on the dc=subdomain1,dc=hostedCompany1, dc=example,dc=com node:
aci: (targetattr="*") (targetfilter=(objectClass=nsManagedDomain)) (version 3.0; acl "Domain access"; allow (read,search) groupdn="ldap:///cn=DomainAdmins,ou=Groups,dc=subdomain1,dc=hostedCompany1, dc=example,dc=com";)
The following ACI is located on the dc=hostedCompany2,dc=example,dc=com node:
aci: (targetattr="*") (targetfilter=(objectClass=nsManagedDomain)) (version 3.0; acl "Domain access"; allow (read,search) groupdn="ldap:///cn=DomainAdmins,ou=Groups,dc=hostedCompany2, dc=example,dc=com";)
The following ACI is located on the dc=subdomain1,dc=hostedCompany2, dc=example,dc=com node:
aci: (targetattr="*") (targetfilter=(objectClass=nsManagedDomain)) (version 3.0; acl "Domain access"; allow (read,search) groupdn="ldap:///cn=DomainAdmins,ou=Groups,dc=subdomain1,dc=hostedCompany2, dc=example,dc=com";)
In the preceding four ACIs, the only difference is the DN that is specified in the groupdn keyword. By using a macro for the DN, it is possible to replace these ACIs with a single ACI at the root of the tree, on the dc=example,dc=com node. This macro ACI reads as follows:
aci: (target="ldap:///ou=Groups,($dn),dc=example,dc=com") (targetattr="*")(targetfilter=(objectClass=nsManagedDomain)) (version 3.0; acl "Domain access"; allow (read,search) groupdn="ldap:///cn=DomainAdmins,ou=Groups,[$dn],dc=example,dc=com";)
Note that the target keyword which was not previously used needs to be introduced.
In the preceding example, the number of ACIs is reduced from four to one. However, the real benefit is a factor of how many repeating patterns you have down and across your directory tree.
To simplify the discussion in this section, the ACI keywords such as userdn, roledn, groupdn, and userattr that are used to provide bind credentials are collectively called the subject of the ACI. The subject determines to whom the ACI applies.
The following table shows which macros can be used to replace specific ACI keywords.
Table 6-3 Macro ACI Keywords
|
The following restrictions apply to macro ACI keywords:
When using the ($dn) and [$dn] macros in a subject, you must define a target that contains the ($dn) macro.
You can combine the ($dn) macro (but not the [$dn] macro) with the ($attr.attrName) macro in a subject.
The ($dn) macro in the target of an ACI determines the substitution value by comparing it to the entry targeted by the LDAP request. For example, you have an LDAP request targeted at this entry:
cn=all,ou=groups,dc=subdomain1, dc=hostedCompany1,dc=example,dc=com
In addition, you have an ACI that defines the target as follows:
(target="ldap:///ou=Groups,($dn),dc=example,dc=com")
The ($dn) macro matches with “dc=subdomain1, dc=hostedCompany1”. This substring is then used for substitutions in the subject of the ACI.
In the subject of the ACI, the ($dn) macro is replaced by the entire substring that matches in the target. For example:
groupdn="ldap:///cn=DomainAdmins,ou=Groups,($dn),dc=example,dc=com"
The subject becomes this:
groupdn="ldap:///cn=DomainAdmins,ou=Groups, dc=subdomain1,dc=hostedCompany1,dc=example,dc=com"
After the macro has been expanded, Directory Server evaluates the ACI following the normal process to determine whether access is granted.
Note - Unlike a standard ACI, an ACI that uses macro substitution does not necessarily grant access to the child of the targeted entry. This is because when the child DN is the target, the substitution might not create a valid DN in the subject string.
The substitution mechanism for [$dn] is slightly different than for ($dn). The DN of the targeted resource is examined several times, each time dropping the left-most RDN component, until a match is found.
For example, suppose that you have an LDAP request targeted at the cn=all,ou=groups, dc=subdomain1,dc=hostedCompany1,dc=example,dc=com subtree, and the following ACI:
aci: (targetattr="*") (target="ldap:///ou=Groups,($dn),dc=example,dc=com") (version 3.0; acl "Domain access"; allow (read,search) groupdn="ldap:///cn=DomainAdmins,ou=Groups,[$dn], dc=example,dc=com";)
The server proceeds as follows to expand this ACI:
The server verifies that the ($dn) in target matches dc=subdomain1,dc=hostedCompany1.
The server replaces [$dn] in the subject with dc=subdomain1,dc=hostedCompany1.
The resulting subject is groupdn="ldap:///cn=DomainAdmins,ou=Groups, dc=subdomain1,dc=hostedCompany1,dc=example,dc=com". If access is granted because the bind DN is a member of that group, the macro expansion stops, and the ACI is evaluated. If the bind DN is not a member, the process continues.
The server replaces [$dn] in the subject with dc=hostedCompany1.
The resulting subject is groupdn="ldap:///cn=DomainAdmins,ou=Groups, dc=hostedCompany1,dc=example,dc=com". Again, the bind DN is tested as a member of this group and if it is, the ACI is evaluated fully. If the bind DN is not a member, macro expansion stops with the last RDN of the matched value, and ACI evaluation is finished for this ACI.
The advantage of the [$dn] macro is that it provides a flexible way to grant domain-level administrators access to all the subdomains in the directory tree. Therefore, the [$dn] macro is useful for expressing a hierarchical relationship between domains.
For example, consider the following ACI:
aci: (target="ldap:///ou=*,($dn),dc=example,dc=com") (targetattr="*") (targetfilter=(objectClass=nsManagedDomain)) (version 3.0; acl "Domain access"; allow (read,search) groupdn= "ldap:///cn=DomainAdmins,ou=Groups,[$dn],dc=example,dc=com";)
The ACI grants access to the members of cn=DomainAdmins,ou=Groups, dc=hostedCompany1,dc=example,dc=com to all of the subdomains under dc=hostedCompany1. Thus, an administrator who belongs to that group could access, for example, the subtree ou=people,dc=subdomain1.1,dc=subdomain1.
However, at the same time, members of cn=DomainAdmins,ou=Groups, dc=subdomain1.1 would be denied access to the ou=people,dc=subdomain1, dc=hostedCompany1 and ou=people,dc=hostedCompany1 nodes.
The ($attr.attrname) macro is always used in the subject part of a DN. For example, you could define the following roledn:
roledn = "ldap:///cn=DomainAdmins,($attr.ou),dc=HostedCompany1,dc=example,dc=com"
Now, assume that the server receives an LDAP operation that is targeted at the following entry:
dn: cn=Babs Jensen,ou=People,dc=HostedCompany1,dc=example,dc=com cn: Babs Jensen sn: Jensen ou: Sales ...
To evaluate the roledn part of the ACI, the server reads the value of the ou attribute stored in the targeted entry. The server then substitutes this value in the subject to expand the macro. In the example, the roledn is expanded as follows:
roledn = "ldap:///cn=DomainAdmins,ou=Sales,dc=HostedCompany1,dc=example,dc=com"
Directory Server then evaluates the ACI according to the normal ACI evaluation algorithm.
When the attribute that is named in the macro is multivalued, each value is used in turn to expand the macro. The first value that provides a successful match is used.