| Skip Navigation Links | |
| Exit Print View | |
|
Configuring Oracle Java CAPS for SSL Support Java CAPS Documentation |
| Skip Navigation Links | |
| Exit Print View | |
|
Configuring Oracle Java CAPS for SSL Support Java CAPS Documentation |
Configuring Java CAPS for SSL Support
Secure Sockets Layer (SSL) Overview
Public Keys, Private Keys, and Certificates
Generating a KeyStore and TrustStore
Creating a KeyStore in JKS Format
Creating a KeyStore in PKCS12 Format
Configuring a Oracle Java CAPS JMS IQ Manager to Use SSL
Configuring the Message Server URL
To Configure the Message Server URL
Configuring the Repository to Use SSL
Generating a Key Pair and a Self-Signed Certificate
To Generate a Key Pair and a Self-Signed Certificate
Obtaining a Signed Certificate
To Obtain a Digitally Signed Certificate from a Certificate Authority
To Obtain a Self-Signed Certificate from a Local Keystore
Configuring the server.xml File
To Configure the server.xml File
Testing the New SSL Connection
To Test the New SSL Connection
Configuring Enterprise Manager to Use SSL
Creating the Keystore and Trust Store
To Create the Keystore and Trust Store
Importing the Domain Certificate
To Import the Domain Certificate
Enabling Security on the Application Server
To Enable Security on the Application Server
Logging In to Enterprise Manager
To Log In to Enterprise Manager
Using SSL With the WebSphere MQ Adapter
Creating a Certification Authority
To Create a Certification Authority
To Issue a Certificate to a Queue Manager
To Issue a Certificate to Java CAPS
Using the OpenSSL Utility for the LDAP and HTTPS Adapters
Creating a Sample CA Certificate
To Create a Sample CA Certificate
Signing Certificates With Your Own CA
To Create a CSR with keytool and Generate a Signed Certificate for the Certificate Signing Request
Oracle Java CAPS JMS IQ Manager provides a self-signed server certificate. You can set the authentication mode to Authenticate or TrustAll.
If the mode is Authenticate, then clients authenticate the server certificate that the message server sends. The clients need to use their trust store.
If the mode is TrustAll, then clients always trust the message server that they connect to. The clients do not need to use their trust store.
The default mode is TrustAll. You can replace the Oracle Java CAPS JMS IQ Manager’s self-signed server certificate with your own server certificate.
You can configure SSL for the Oracle Java CAPS JMS IQ Manager by editing an Environment property.
The Properties dialog box appears.
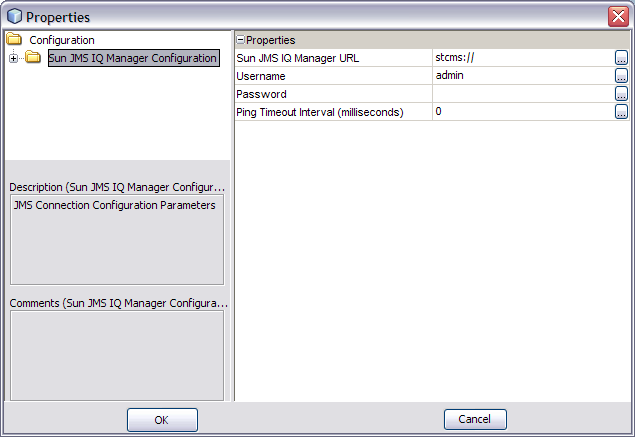
stcmss://localhost:18008
stcmss://localhost:18008?com.stc.jms.ssl.authenticationmode=Authenticate
stcmss://localhost:18008?com.stc.jms.ssl.authenticationmode=TrustAll
By default, JMS clients that are deployed inside the GlassFish Application Server use the default keystore and trust store. External JMS clients must set the following properties in the connection factory:
com.stc.jms.ssl.authenticationmode
javax.net.ssl.trustStore
You can replace the Oracle Java CAPS JMS IQ Manager’s self-signed server certificate with your own server certificate.
This procedure makes the following assumptions:
You have a server certificate in PEM format. The file name is mycacert.pem. The common name of the owner and issuer is mycertuserid. The password is mycertpassword.
You have a private key in PEM format. The file name is mycakey.pem.
keytool -import -alias stcmscert -file mycacert.pem -keystore cacerts.jks
For the -alias option, you can use any value.
openssl pkcs12 -export -in mycacert.pem -inkey mycakey.pem -out mycert.p12 -name "stcmscert"
STCMS.SSL.UserId=mycertuserid STCMS.SSL.Password=mycertpassword
If you want the JMS IQ Manager to install the certificate automatically, then set the value to On.
If you want to install the certificate by using the certmgr tool or Internet Explorer, then set the value to Off.