2 Deploying the Connector
This chapter is divided into the following sections:
2.1 Preinstallation
Preinstallation information is divided across the following sections:
2.1.1 Files and Directories on the Installation Media
This section lists files and directories on the installation media.
Table 2-1 lists and describes them in detail.
Table 2-1 Files and Directories in the Installation Package
| File in the Installation Package Directory | Description |
|---|---|
|
bundle/org.identityconnectors.genericunix-1.0.0.jar |
This JAR file contains the connector bundle. |
|
configuration/GenericUNIX-CI.xml |
This XML file contains configuration information that is used during the connector installation process. |
|
Files in the resources directory |
Each of these resource bundles contains language-specific information that is used by the connector. During connector installation, these resource bundles are copied to Oracle Identity Manager database. Note: A resource bundle is a file containing localized versions of the text strings that are displayed on the Administrative and User Console. These text strings include GUI element labels and messages. |
|
Files in the test-utility directory:
|
These files are used by the testing utility to identify the cause of problems associated with connecting to the target system and performing basic operations on the target system.
|
|
upgrade/PostUpgradeScriptUnix.sql |
This file is used after upgrading the connector. See Upgrading the Connector for more information. |
|
util/privateKeyGen.sh |
This file is used during SSH key-based authentication. |
|
util/sudoers |
This file contains the SUDO user specifications and configurations. |
|
xml/UNIX-ConnectorConfig.xml |
This XML file contains definitions for the connector components. These components include the following:
|
|
xml/UNIX-RequestDatasets.xml |
This XML file contains request datasets that can be imported using Deployment Manager. It specifies the information to be submitted by the requester during a request-based provisioning operation. See Importing Request Datasets Using Deployment Manager for more information. Note: Use this file only if you are using Oracle Identity Manager release prior to 11.1.2. |
2.1.2 Configuring the Target System
Depending on the target system and your requirements, perform some of the following procedures:
2.1.2.1 Configuring Solaris and Linux
Perform the following steps to configure Solaris and Linux environments:
2.1.2.3 Configuring HP-UX
Perform the following steps for HP-UX environments:
-
If you want to switch to HP-UX Trusted mode, then:
Note:
If you are converting the target system to the trusted system, then please make sure that no shadow file exists on the target after it is converted to trusted system.You can use
pwunconvcommand to get rid of the shadow file, if it exists.-
Log in as root and then run the following command:
/usr/bin/sam
/usr/sbin/sam
-
Select Auditing and Security and then select System Security Policies. A message is displayed asking if you want to switch to the trusted mode.
-
Click Yes. The following message is displayed:
System changed successfully to trusted system
-
-
Ensure that the /etc/passwd and /etc/shadow directories are available on the target server.
-
Create a directory on the target system where the connector can create mirror files for the /etc/passwd and /etc/shadow files.
This directory is specified in the mirrorFilesLocation entry of the Lookup.UNIX.Configuration lookup definition. The default value is
/etc/connector_mirror_files.If the directory path is different from the default value, then you must update the correct path in the lookup.The loginUser (sudo or root user) must have read and write privileges to this directory.
2.1.2.4 Installing OpenSSH
Follow these steps to install OpenSSH on the target system:
For Solaris 9
- If SSH is not installed on the Solaris server, then install the appropriate OpenSSH.
- Create a group with the name
sshdand group ID27. Add a user with the namesshadminto this group. - To enable root logins, change the value of
PermitRootLoginin the /etc/ssh/sshd_config file as follows:PermitRootLogin yes
Note:
Implement this change only if it does not violate local security policies. If Public Key Authentication is enabled, then you can change the value of
PermitRootLogintowithout-password.Instead of using the root account, if you can use a user account with sudo privileges, then you do not need to perform this step.
For Solaris 10 and Later Versions
By default, OpenSSH is installed on Solaris 10 and later versions. If it is not installed, then install the OpenSSH server from the operating system installation CD. To enable SSH, make the following changes in the /etc/ssh/ssh_config file:
- Remove the comment character from the
Host *line. - To enable root logins, change the value of
PermitRootLoginin the /etc/ssh/sshd_config file as follows:PermitRootLogin yes
Note:
Implement this change only if it does not violate local security policies. If Public Key Authentication is enabled, then you can change the value of
PermitRootLogintowithout-password.Instead of using the root account, if you can use a user account with sudo privileges, then you do not need to perform this step.
For HP-UX
If SSH is not installed on the UNIX server, then install the appropriate OpenSSH from the installation media.
For Linux
By default, OpenSSH is installed on Red Hat Linux. If it is not installed, then install the OpenSSH server from the operating system installation CD.
For AIX
If SSH is not installed on the AIX server, then from the installation media:
- Install OpenSSL.
- Install PRNG.
- Install OpenSSH.
- To enable root logins, change the value of
PermitRootLoginin the /etc/ssh/sshd_config file as follows:PermitRootLogin yes
Note:
Implement this change only if it does not violate local security policies. If Public Key Authentication is enabled, then you can change the value of
PermitRootLogintowithout-password.Instead of using the root account, if you can use a user account with sudo privileges, then you do not need to perform this step.
2.1.2.5 Creating a Target System SUDO User Account for Connector Operations
Oracle Identity Manager uses a target system account for performing reconciliation and provisioning operations. On all supported target systems, this account must be either the root user or sudo user.
See Also:
Privileges Required for Performing Provisioning and Reconciliation for information about the privileges required to perform connector operations
To create a target system user account with the minimum permissions required to perform connector operations, perform the following procedure:
-
If SUDO is not installed on the target system, then install it from the installation media.
-
Use the
visudocommand to edit and customize the /etc/sudoers file according to your requirements.Note:
If you cannot use the
visudocommand to edit thesudoersfile, then:-
Enter the following command:
chmod 777 /etc/sudoers
-
Make the required changes in the
sudoersfile. -
Enter the following command:
chmod 440 /etc/sudoers
For example, if you have a group named
mqmon the Linux server and require all members of the group to act as SUDO users with all possible privileges, then thesudoersfile must contain the following line:mqm ALL= (ALL) ALL
This example is only a sample configuration. If you need other group members or individual users to be SUDO users with specific privileges, then edit this file as was done for the sample value
mqm.Therefore, the SUDO user must have the privileges required to run these commands.
Note:
NOPASSWD: ALLoption for any SUDO user or group is supported. To configure this, you may need to add a lookup field. For more information on adding a lookup field, refer Setting up the Lookup Definitions for Connector Configuration. -
-
Edit the same
sudoersfile so that the SUDO user stays validated for 10 minutes after being validated once. You may need to increase the timeout if the reconciliation operation takes longer than 10 minutes and if you encounter errors such as "Permission denied". At the beginning of each operation, the connector validates the user usingsudo -voption so that the operation stays validated for a maximum of 10 minutes. After carrying out the operation, the connector runs thesudo -kto kill the validation.Add the following line under the
# Defaults specificationheader:Defaults timestamp_timeout=10
This is a prerequisite for this connector to work successfully.
-
Create a SUDO user as follows:
-
Enter the following command:
useradd -g group_name -d /home/directory_name -m user_name
In this command:
group_nameis the SUDO users group for which there is an entry in the/etc/sudoersfile.directory_nameis the name of the directory in which you want to create the default directory for the user. -
In the .bash_profile file, which is created in the /home/directory_name directory, add the following lines to set the
PATHenvironment variable:PATH=/usr/sbin:$PATH export PATH
-
-
In the sudo user's .bashrc, .cshrc, or .kshrc file, which is created in the sudo user's home directory, add the following line to change the prompt end character from $ (dollar sign) to # (pound sign):
PS1="[\\u@\\h:\\w]#"
The encrypted passwords in the shadow file contain $ (dollar sign), which matches the default prompt end character. You must change the prompt end character to ensure that changes made to the shadow file are reconciled correctly.
-
Login with the sudo user.
-
Run the
sudo -kcommand on the target system to clear the validation. -
Run the
sudo -vcommand on the target system and ensure that the password prompt is displayed.The connector would not work if the sudo user is not prompted for password at this step.
2.1.2.6 Creating an RBAC User Account for Connector Operations on Solaris
On Solaris, you can either create a sudo user or apply the role-based access control (RBAC) feature to create an account and assign to it the minimum privileges required for connector operations.
Note:
You use the IT resource to specify whether or not you want to use an RBAC user. Parameters of the IT resource are described later in this chapter.
To create an RBAC user account:
-
Run the following command to create a role for the user.
roleadd -d /export/home/ROLE_NAME -m ROLE_NAME
In this command, replace
ROLE_NAMEwith the name that you want to assign to the role, for example,OIMRole. -
Run the following command to assign a password to the role:
passwd ROLE_NAMEAt the prompt, enter a password for the role.
See Also:
Privileges Required for Performing Provisioning and Reconciliation for information about the privileges required to run the commands that are used for provisioning and reconciliation
-
Create a profile for the user as follows:
-
Open the /etc/security/prof_attr file in a text editor and insert the following line in the file:
PROFILE_NAME:::Oracle Identity Manager Profile:In this line, replace
PROFILE_NAMEwith the name that you want to assign to the profile, for example,OIMProf. -
Save and close the file.
-
-
Add execution attribute entries in the /etc/security/exec_attr file. Each entry defines a task to be run and the uid that the role will assume when running the task.
Open the /etc/security/exec_attr file in a text editor, and insert the following lines:
Note:
There are seven fields in this file, and the colon (:) is used as the delimiting character.
On Solaris 10, the value
susercan be replaced withsolaris.Some of the entries contain
euid. These instances ofeuidcan be replaced withuid.PROFILE_NAME:suser:cmd:::/usr/sbin/usermod:uid=0 PROFILE_NAME:suser:cmd:::/usr/sbin/useradd:uid=0 PROFILE_NAME:suser:cmd:::/usr/sbin/userdel:uid=0 PROFILE_NAME:suser:cmd:::/usr/bin/passwd:uid=0 PROFILE_NAME:suser:cmd:::/usr/bin/cat:euid=0 PROFILE_NAME:suser:cmd:::/usr/bin/diff:euid=0 PROFILE_NAME:suser:cmd:::/usr/bin/sort:euid=0 PROFILE_NAME:suser:cmd:::/usr/bin/rm:uid=0 PROFILE_NAME:suser:cmd:::/usr/bin/grep:euid=0 PROFILE_NAME:suser:cmd:::/usr/bin/egrep:euid=0 PROFILE_NAME:suser:cmd:::/bin/echo:euid=0 PROFILE_NAME:suser:cmd:::/bin/sed:euid=0
You can add similar entries for other commands if you have customized the pre-configured Solaris scripts to use other commands.
-
Run the following command to associate the profile with the role:
rolemod -P PROFILE_NAME ROLE_NAME
-
Run the following command to create the user:
useradd -d /export/home/USER_NAME -m USER_NAME
-
Run the following command to assign a password to the user:
passwd USER_NAME -
Run the following command to grant the role to the user:
usermod -R ROLE_NAME USER_NAME
-
To verify the changes that you have made, open the /etc/user_attr file in a text editor and verity that the following entries are present in the file:
ROLE_NAME::::type=role;profiles=PROFILE_NAME USER_NAME::::type=normal;roles=ROLE_NAME
2.1.2.7 Configuring Public Key Authentication
To configure Public Key Authentication:
Note:
-
If Public Key Authentication is used, then an RBAC user for a Solaris target system cannot be used.
-
This section contains the procedure to configure Public Key Authentication for a root user. It can also be configured for a SUDO user.
2.1.2.8 Configuring SSH Public Key Authentication
To configure SSH Public Key Authentication:
For Solaris
- Set the following parameters in the /etc/ssh/sshd_config file:
PubKeyAuthorization yes PasswordAuthentication no PermitRootLogin yes
Note:
Change the value of
PermitRootLogintoyesonly if it does not violate local security policies. If Public Key Authentication is enabled, then you can change the value ofPermitRootLogintowithout-password.Instead of using the root account, if you can use a user account with sudo privileges, then you do not need to perform this step.
- To restart the SSH server, enter the following commands:
-
/etc/init.d/sshd stop -
/etc/init.d/sshd start
-
- To test login:
ssh -i /.ssh/id_rsa -l root server_IP_addressThis command prompts you for the passkey before setting up the connection.
- Set the
privateKey[LOADFROMURL]advanced settings parameter to include the complete path of theid_rsafile with the prefixfile://For example:
file:///OIM_HOME/server/ConnectorDefaultDirectory/SSH/config/id_rsa
- Uncomment the following lines in the /etc/ssh/sshd_config file:
PermitRootLogin yes PubkeyAuthentication yes AuthorizedKeysFile .ssh/authorized_keys
Note:
Change the value of
PermitRootLogintoyesonly if it does not violate local security policies. If Public Key Authentication is enabled, then you can change the value ofPermitRootLogintowithout-password.Instead of using the root account, if you can use a user account with sudo privileges, then you do not need to perform this step.
- To restart the SSH Server, enter the following command:
/opt/ssh/sbin/sshd
- To test login, enter the following command:
ssh -i /.ssh/id_rsa -l root server_IP_addressWhen prompted, enter the passkey to connect to the server.
- In Oracle Identity Manager Design Console, create a new entry in the Lookup.UNIX.Configuration lookup definition with the following values:
Code Key:
privateKey[LOADFROMURL]Decode: Add the complete path of the
id_rsafile, with the prefix file://.For example:
file:///OIM_HOME/server/ConnectorDefaultDirectory/SSH/config/id_rsa
For Linux
- Enter the following commands to restart the UNIX server:
/etc/init.d/sshd stop /etc/init.d/sshd start
- Copy the /.ssh/id_rsa file to the following directory:
OIM_HOME/server/ConnectorDefaultDirectory/SSH/config - To check if you can connect to the target system using the SSH protocol, directly from the command prompt and without using a password, enter the following command:
Note:
The account used to run the OIM application server on UNIX should have the ownership of the id_rsa file.
ssh -i OIM_HOME/server/ConnectorDefaultDirectory/SSH/config/id_rsa -l root host_ip_address
- In Oracle Identity Manager Design Console, create a new entry in the Lookup.UNIX.Configuration lookup definition with the following values:
Code Key:
privateKey[LOADFROMURL]Decode: Add the complete path of the
id_rsafile, with the prefix file://.For example:file:///OIM_HOME/server/ConnectorDefaultDirectory/SSH/config/id_rsa
- Use the /etc/ssh/sshd_config file to set the following parameters:
export PATH=$PATH: /usr/sbin Installation path: /etc/ssh/ sshd -- /usr/sbin/
- Open the /etc/ssh/sshd_config file, and uncomment the following lines:
AuthorizedKeysFile .ssh/authorized_keys PermitRootLogin yes PubkeyAuthentication yes
Note:
Change the value of
PermitRootLogintoyesonly if it does not violate local security policies. If Public Key Authentication is enabled, then you can change the value ofPermitRootLogintowithout-password.Instead of using the root account, if you can use a user account with sudo privileges, then you do not need to perform this step.
- To restart the SSH server, enter the following command:
/usr/sbin/sshd - To test the login, enter the following command:
ssh -i /.ssh/id_rsa -l root server_IP_addressWhen prompted, enter the passkey to connect to the server.
- In Oracle Identity Manager Design Console, create a new entry in the Lookup.UNIX.Configuration lookup definition with the following values:
Code Key:
privateKey[LOADFROMURL]Decode: Add the complete path of the
id_rsafile, with the prefix file://.For example:
file:///OIM_HOME/server/ConnectorDefaultDirectory/SSH/config/id_rsa
2.2 Installation
You must install the connector in Oracle Identity Manager. If necessary, you can also deploy the connector in a Connector Server.
Note:
In this guide, the term Connector Installer has been used to refer to the Connector Installer feature of the Oracle Identity Manager Administrative and User Console.
Depending on where you want to run the connector code (bundle), the connector provides the following installation options:
-
To run the connector code locally in Oracle Identity Manager, perform the procedure described in Installing the Connector in Oracle Identity Manager
-
To run the connector code remotely in a Connector Server, perform the procedures described in Installing the Connector in Oracle Identity Manager and Deploying the Connector Bundle in a Connector Server.
2.2.1 Installing the Connector in Oracle Identity Manager
In this scenario, you install the connector in Oracle Identity Manager using the Connector Installer.
Note:
In this guide, the term Connector Installer has been used to refer to the Connector Installer feature of the Oracle Identity Manager Administrative and User Console.
To run the connector code locally in Oracle Identity Manager, perform the following steps:
-
Copy the contents of the connector installation media directory into the following directory:
OIM_HOME/server/ConnectorDefaultDirectory
Note:
In an Oracle Identity Manager cluster, perform this step on each node of the cluster.
-
If you are using Oracle Identity Manager release 11.1.1, perform the following steps:
-
Log in to the Administrative and User Console.
-
On the Welcome to Identity Manager Advanced Administration page, in the System Management region, click Manage Connector.
-
-
If you are using Oracle Identity Manager release 11.1.2.x, perform the following steps:
-
Log in to Oracle Identity System Administration.
-
In the left pane, under System Management, click Manage Connector.
-
-
In the Manage Connector page, click Install.
-
From the Connector List list, select Generic UNIX Connector 11.1.1.7.0. This list displays the names and release numbers of connectors whose installation files you copy into the default connector installation in Step 1.
If you have copied the installation files into a different directory, then:
-
In the Alternative Directory field, enter the full path and name of that directory.
-
To repopulate the list of connectors in the Connector List list, click Refresh.
-
From the Connector List list, select Generic UNIX Connector 11.1.1.7.0.
-
-
Click Load.
-
To start the installation process, click Continue.
The following tasks are performed, in sequence:
-
Configuration of connector libraries
-
Import of the connector XML files (by using the Deployment Manager)
-
Compilation of adapters
On successful completion of a task, a check mark is displayed for the task. If a task fails, then an X mark and a message stating the reason for failure are displayed. Depending on the reason for the failure, make the required correction and then perform one of the following steps:
-
Retry the installation by clicking Retry.
-
Cancel the installation and begin again from Step 1.
-
-
If all three tasks of the connector installation process are successful, then a message indicating successful installation is displayed. In addition, a list of the steps that you must perform after the installation is displayed. These steps are as follows:
-
Ensuring that the prerequisites for using the connector are addressed
Note:
At this stage, run the Oracle Identity Manager PurgeCache utility to load the server cache with content from the connector resource bundle in order to view the list of prerequisites. See Clearing Content Related to Connector Resource Bundles from the Server Cache for information about running the PurgeCache utility.
There are no prerequisites for some predefined connectors.
-
Configuring the IT resource for the connector
Record the name of the IT resource displayed on this page. The procedure to configure the IT resource is described later in this guide.
-
Configuring the scheduled tasks
Record the names of the scheduled tasks displayed on this page. The procedure to configure these scheduled tasks is described later in this guide.
-
When you run the Connector Installer, it copies the connector files and external code files to destination directories on the Oracle Identity Manager host computer. These files are listed in Files and Directories on the Installation Media.
2.2.2 Deploying the Connector Bundle in a Connector Server
To deploy the connector bundle remotely in a Connector Server, you must first deploy the connector in Oracle Identity Manager.
To do so, perform the procedure described in Installing the Connector in Oracle Identity Manager.
Note:
-
You can download the Connector Server from the Oracle Technology Network web page.
-
See Configuring the IT Resource for the Connector Server for related information.
-
See Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for more information about installing, configuring, and running the Connector Server.
To install the connector in the Connector Server:
2.3 Postinstallation
Postinstallation for the connector involves configuring Oracle Identity Manager, enabling logging to track information about all connector events, and configuring the IT resources. It also involves performing some optional configurations such as localizing the user interface, setting up lookup definitions for connection pooling, and so on.
Postinstallation steps are divided across the following sections:
2.3.1 Configuring Oracle Identity Manager 11.1.2 or Later
If you are using Oracle Identity Manager release 11.1.2 or later, you must create additional metadata such as a UI form and an application instance. In addition, you must run entitlement and catalog synchronization jobs.
These procedures are described in the following sections:
2.3.1.1 Creating and Activating a Sandbox
Create and activate a sandbox as follows:
- On the upper navigation bar, click Sandboxes. The Manage Sandboxes page is displayed.
- On the toolbar, click Create Sandbox. The Create Sandbox dialog box is displayed.
- In the Sandbox Name field, enter a name for the sandbox. This is a mandatory field.
- In the Sandbox Description field, enter a description of the sandbox. This is an optional field.
- Click Save and Close. A message is displayed with the sandbox name and creation label.
- Click OK. The sandbox is displayed in the Available Sandboxes section of the Manage Sandboxes page.
- Select the sandbox that you created.
- From the table showing the available sandboxes in the Manage Sandboxes page, select the newly created sandbox that you want to activate.
- On the toolbar, click Activate Sandbox.
The sandbox is activated.
2.3.1.2 Creating a New UI Form
Create a new UI form as follows. For detailed instructions, see Creating Forms By Using the Form Designer in Oracle Fusion Middleware Administering Oracle Identity Manager.
- In the left pane, under Configuration, click Form Designer.
- Under Search Results, click Create.
- Select the resource type for which you want to create the form.
- Enter a form name and click Create.
2.3.1.3 Creating an Application Instance
Create an application instance and associate it with the form created in Creating a New UI Form. Then, publish the application instance to an organization to make the application instance available for requesting and subsequent provisioning to users. See the following sections in Oracle Fusion Middleware Administering Oracle Identity Manager for detailed instructions on creating and publishing application instances:
- In the System Administration page, under Configuration in the left pane, click Application Instances.
- Under Search Results, click Create.
- Enter appropriate values for the fields displayed on the Attributes form and click Save.
- In the Form drop-down list, select the newly created form and click Apply.
- Publish the application instance for a particular organization.
2.3.1.4 Publishing a Sandbox
To publish the sandbox that you created in Creating and Activating a Sandbox:
- Close all the open tabs and pages.
- From the table showing the available sandboxes in the Manage Sandboxes page, select the sandbox that you created in Creating and Activating a Sandbox.
- On the toolbar, click Publish Sandbox. A message is displayed asking for confirmation.
- Click Yes to confirm. The sandbox is published and the customizations it contained are merged with the main line.
2.3.1.5 Harvesting Entitlements and Sync Catalog
To harvest entitlements and sync catalog:
- Run the scheduled jobs for lookup field synchronization listed in Scheduled Tasks for Lookup Field Synchronization.
- Run the Entitlement List scheduled job to populate Entitlement Assignment schema from child process form table. See Predefined Scheduled Tasks in Oracle Fusion Middleware Administering Oracle Identity Manager for more information about this scheduled job.
- Run the Catalog Synchronization Job scheduled job. See Predefined Scheduled Tasks in Oracle Fusion Middleware Administering Oracle Identity Manager for more information about this scheduled job.
2.3.1.6 Updating an Existing Application Instance with a New Form
For any changes you do in the Form Designer, you must create a new UI form and update the changes in an application instance. To update an existing application instance with a new form:
- Create a sandbox and activate it as described in Creating and Activating a Sandbox.
- Create a new UI form for the resource as described in Creating a New UI Form.
- Open the existing application instance.
- In the Form field, select the new UI form that you created.
- Save the application instance.
- Publish the sandbox as described in Publishing a Sandbox.
2.3.2 Configuring the IT Resource for the Target System
Note:
If you have configured your target system as a trusted source, then create an IT resource of type UNIX. For example, UNIX Trusted. The parameters of this IT resource are the same as the parameters of the IT resources described in Table 2-2 of this section. See Creating IT Resources in Fusion Middleware Administering Oracle Identity Manager.
For both provisioning and reconciliation, the connector uses the UNIX Server IT Resource. This IT resource is created with default parameter values as part of the connector installation. You must update the IT resource parameters with information about the target system.
To configure the UNIX Server IT resource:
-
Depending on the Oracle Identity Manager release you are using, perform one of the following steps:
- For Oracle Identity Manager release 11.1.1: Log in to the Administrative and User Console
- For Oracle Identity Manager release 11.1.2.x: Log in to Oracle Identity System Administration
-
If you are using Oracle Identity Manager release 11.1.1, then:
- On the Welcome page, click Advanced in the upper right corner.
- On the Welcome to Oracle Identity Manager Advanced Administration page, in the Configuration region, click Manage IT Resource.
-
If you are using Oracle Identity Manager release 11.1.2.x, then in the left pane under Configuration, click IT Resource.
-
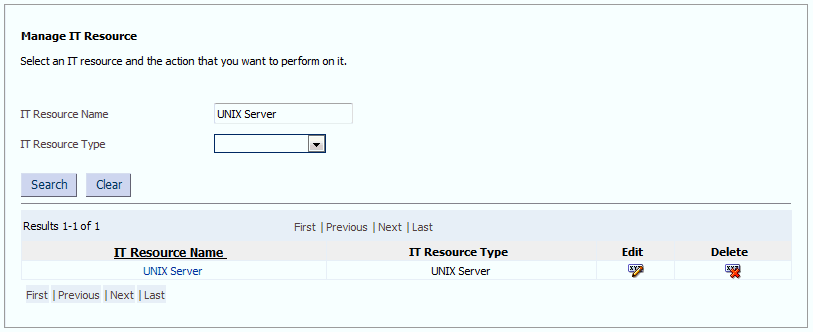
In the IT Resource Name field on the Manage IT Resource page, enter
UNIX Serverand then click Search. Figure 2-1 shows the Manage IT Resource page. -
Click the edit icon corresponding to the UNIX Server IT resource.
-
From the list at the top of the page, select Details and Parameters.
-
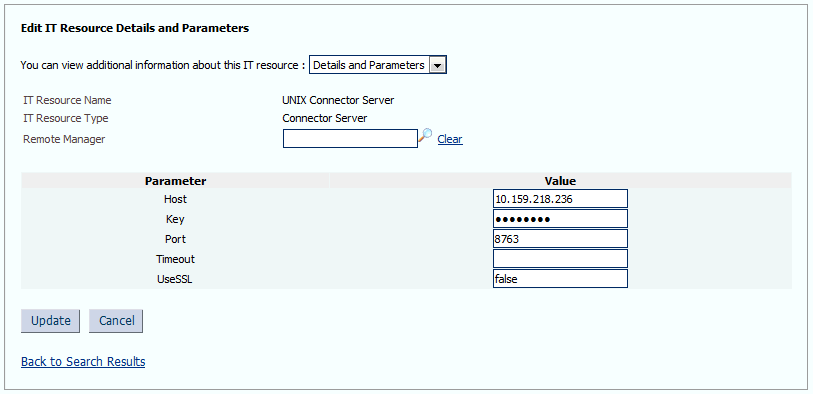
Specify values for the parameters of the UNIX Server IT resource. Figure 2-2 shows the Edit IT Resource Details and Parameters page.
Figure 2-2 Edit IT Resource Details and Parameters Page
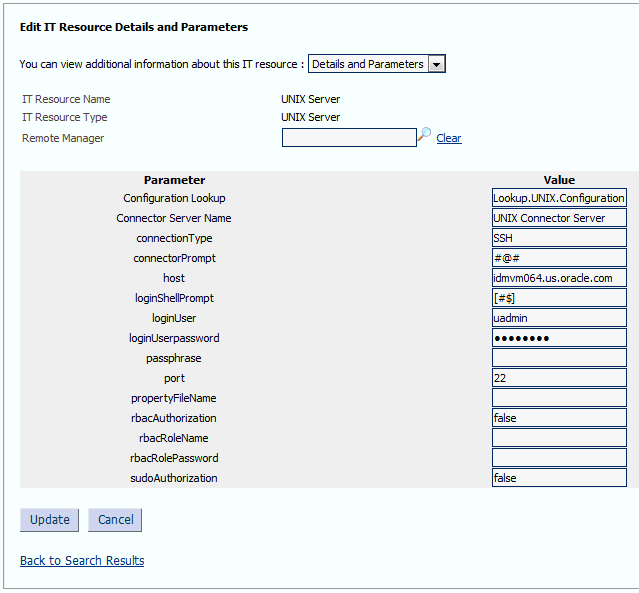
Description of "Figure 2-2 Edit IT Resource Details and Parameters Page"Table 2-2 describes each parameter of the UNIX Server IT resource.
Table 2-2 Parameters of the UNIX Server IT Resource for the Target System
Parameter Description Configuration Lookup
Name of the lookup definition that stores configuration information used during reconciliation and provisioning
To use the target system as a target resource, set the following value (default):
Lookup.UNIX.ConfigurationTo use the target system as a trusted source, set the following value:
Lookup.UNIX.Configuration.TrustedConnector Server Name
Name of the IT resource of type "Connector Server"
A default IT resource for the Connector Server is created during the connector installation. See Configuring the IT Resource for the Connector Server for information about modifying the default IT resource.
By default, this field is blank.
If you use a Connector Server, then the default value is:
UNIX Connector ServerconnectionType
Protocol used by the connector to connect to the target system
The connector supports the following connection types:
-
SSH- Used for SSH with password-based authentication. -
SSHPUBKEY- Used for SSH with key-based authentication. -
TELNET- Used for Telnet connection.
Default value:
SSHconnectorPrompt
Shell prompt set by the connector for its operations on the target system
Default value:
#@#Note: If this value occurs in user login names, comment fields, directory names, and so on, some connector operations may be affected.
In such a case, the value for the connector prompt can be changed to a value that does not occur in the names.
host
Host name or the IP address of the target system computer
loginShellPrompt
Shell prompt that you encounter when you login to the target system using the loginUser account
Default value:
[#$]Note: This value is a regular expression. By default, the connector works if the shell prompt on the target system is either
#or$.However, if the shell prompt is different, for example
>, then you must change the value of this parameter to the actual prompt.To know the loginShellPrompt, perform the following steps on the target system:
-
Log in to the target system using the user and the password specified in the loginUser and loginUserPassword parameters.
Note the login prompt. For example,
#. -
Run the
shcommand.Note the shell prompt, if it is different from the previous prompt. For example,
$. -
Run the
sudo -kcommand.Note the shell prompt, if it is different from the previous prompt. For example,
$. -
Run the
sudo -vcommand.This will prompt you for the password if loginUser is a SUDO user. Enter the password and continue. Note the shell prompt, if it is different from the previous prompt. For example,
$. -
Run the
sudo -scommand.Note the shell prompt, if it is different from the previous prompt. For example,
$.
For the values shown in the examples, the loginShellPrompt parameter value should be
[#$].In addition, if the shell prompt displayed in any of the previous steps is similar tohome/jdoe>,then the prompt is>(not the entire string,home/jdoe>).loginUser
User ID of the administrator to perform connector operations
rootorjdoeHere,
jdoecan be the SUDO user ID, for the SUDO Admin mode. Alternatively, on Solaris, it can be the user ID of the account to which you assign the minimum privileges required to perform connector operations. See Creating a Target System SUDO User Account for Connector Operations for more information.loginUserpassword
Password of the administrator
passphrase
Passphrase for the key file to use with key based authentication
Note: You must provide a passphrase if you use key-based authentication.
port
Port at which the SSH or Telnet service is running on the server
Default value for SSH:
22Default value for Telnet:
23propertyFileName
Relative path of the ScriptProperties.properties file of the target system
You can leave this field blank if you want to use the default scripts. However, if you want to use custom scripts other than the OOTB scripts, then you must provide a value for this field.
The connector will try to determine the path of the properties file by running the
uname -acommand on the target system. If the connector is unable to determine an appropriate value (when an exception is encountered), then it will display the following error message:Unable to determine UNIX Type. Please provide property file name in IT Resource.In the case of an error message, enter one of the following values (or a different path if you want to use customized scripts) depending on the target system and the user account:
-
scripts/solaris/sudo/ScriptProperties.properties -
scripts/solaris/nonsudo/ScriptProperties.properties -
scripts/linux/sudo/ScriptProperties.properties -
scripts/linux/nonsudo/ScriptProperties.properties -
scripts/aix/sudo/ScriptProperties.properties -
scripts/aix/nonsudo/ScriptProperties.properties -
scripts/hpux/sudo/ScriptProperties.properties -
scripts/hpux/nonsudo/ScriptProperties.properties
rbacAuthorization
Indicates whether the user provided in the loginUser parameter is a RBAC user
Default value:
falseSee Creating an RBAC User Account for Connector Operations on Solaris for more information.
rbacRoleName
If you specify the rbacAuthorization parameter as
true, then enter the name of the role assigned to the RBAC user. Otherwise, do not specify a value for this parameter.rbacRolePassword
If you specify the rbacAuthorization parameter as
true, then enter the password of the role assigned to the RBAC user. Otherwise, do not specify a value for this parameter.sudoAuthorization
Indicates whether the user provided in the loginUser parameter is a SUDO user
Default value:
false -
-
To save the values, click Update.
2.3.3 Configuring the IT Resource for the Connector Server
Perform the procedure described in this section only if you have installed the connector bundle in a Connector Server.
The procedure to install the connector bundle in a Connector Server is described in Deploying the Connector Bundle in a Connector Server. During the installation of the connector, a default IT resource for the Connector Server for UNIX is created with the name, UNIX Connector Server.
To configure or modify the IT resource for the Connector Server:
2.3.4 Setting up the Lookup Definitions for Connector Configuration
The configuration lookup definitions are created in Oracle Identity Manager when you deploy the connector.
These lookup definitions are either prepopulated with values or you must manually enter values in them after the connector is deployed. The lookup definitions are as follows:
-
Lookup.UNIX.Configuration
This lookup definition holds connector configuration entries that are used during reconciliation and provisioning operations.
-
Lookup.UNIX.Configuration.Trusted
This lookup definition holds connector configuration entries when the target system is configured as a trusted source.
Table 2-4 lists the default entries in these lookup definitions.
Table 2-4 Entries in the UNIX Configuration Lookup Definitions
| Code Key | Decode | Description |
|---|---|---|
|
Bundle Name |
|
Name of the connector bundle package Do not modify this entry. |
|
Bundle Version |
1.0.0 |
Version of the connector bundle class Do not modify this entry. |
|
commandTimeout |
100000 |
Time in milliseconds for which the connector would wait for a response from the target systemAfter this time, the connector will throw timeout exception. You can increase this value if you encounter a 'command timed out' exception for connector operations. |
|
configPropertiesOnScripts |
moveHomeDirContents,shadow,defaultHomeBaseDir, defaultPriGroup,defaultShell,nisPwdDir, nisBuildDirectory,removeHomeDirContents,forceDeleteUserHome,syncToken, mirrorFilesLocation,connectorPrompt |
Lists the properties that are sent to the scripts For example, if during provisioning, you want to set a default shell for the users. To do so:1. Verify that the 'defaultShell' property is a part of this list.2. Add an entry for this property in this lookup.Set the Code Key value to defaultShell.Set the Decode value to If the target-specific script supports the defaultShell property, it would be set. Not all scripts support all the attributes listed in the Decode column. You must manually check the script contents for supported attributes. |
|
Connector Name |
|
Name of the connector class Do not modify this entry. |
|
mirrorFilesLocation |
|
Directory used by the connector to store copies of the /etc/passwd and shadow files Note: This directory has to be manually created on the target before performing reconciliation.If you want to specify a different directory, ensure that the directory exists on the target system and the loginUser has read-write access to the directory. |
|
moveHomeDirContents |
Default value: |
Specifies whether the old home directory contents should be moved to the new directory location when changing the Home Directory. You can enter |
|
passwordExpectExpressions |
Note: The third-party library, Expect4j, matches these expected expressions to the actual contents of the console output on the UNIX target system. Therefore, you must ensure that these fields have correct values. Incorrect values may impact the connector operations. |
Regular expression for the two comma-separated password prompts that are displayed on the target system when a password is set for a user If the regular expression does not work on your target system, then you can specify the exact prompts in this lookup entry. For example, if you set the password for a user and you get the following prompt:
Then, you can set the Decode value as follows:
|
|
prePasswdExpectExpression Note: This entry does not exist by default. You must add it to the configuration lookup if your target displays extra prompts such as the prompt shown in the description column. |
For the example shown in the description column, the sample value for the choice p will be:
|
Some target systems such as HP-UX may display additional options before prompting for passwords while running the For example: Do you want (choose one letter only): pronounceable passwords generated for you (g) a string of letters generated (l) ? to pick your passwords (p)? Enter choice here: In such a case, you can enter these Code Key and Decode entries to the lookup definition. |
|
privateKey[LOADFROMURL] Note: This entry does not exist by default. You must add it to the configuration lookup if you want to enable key-based authentication. |
Sample value:
|
Path to the id_rsa file |
|
rbacRoleExpectExpressions Note: This entry is applicable only to Lookup.UNIX.Configuration. |
Note: The third-party library, Expect4j, matches these expected expressions to the actual contents of the console output on the UNIX target system. Therefore, you must ensure that these fields have correct values. Incorrect values may impact the connector operations. |
Regular expressions for the two comma-separated prompts The first prompt (password:) is the password prompt displayed on the Solaris target system when you enter the SUDO mode for the RBAC role. If the target system displays a different prompt, then you must change this password prompt. The second prompt ([$#]) is the shell prompt displayed after running the previous command in SUDO mode. If the target system displays a different prompt, then you must change this shell prompt. |
|
sudoPasswdExpectExpression |
Note: The third-party library, Expect4j, matches these expected expressions to the actual contents of the console output on the UNIX target system. Therefore, you must ensure that these fields have correct values. Incorrect values may impact the connector operations. |
Regular expression for the password prompt displayed on the target system when you enter the SUDO mode If the target system displays a different prompt, then you must change this password prompt. |
|
supportedLanguage |
Bourne |
Shell script language supported on the target system |
|
targetDateFormat |
yyyy-MM-dd Note: You must ensure that this is the correct Java date format for the target system. An incorrect format may affect provisioning of the Expire Date attribute. For information about the date format, see |
Format of the date on the target system |
|
telnetAuthenticationPrompts Note: This entry is applicable for Telnet connection, when the connectionType parameter of the IT Resource is set to TELNET. |
Note: The third-party library, Expect4j, matches these expected expressions to the actual contents of the console output on the UNIX target system. Therefore, you must ensure that these fields have correct values. Incorrect values may impact the connector operations. |
The login and password prompts on a target system using Telnet connection. |
|
User Configuration Lookup |
|
Name of the lookup definition that contains user-specific configuration properties Do not modify this entry. |
|
whitelistRegex |
|
Specifies characters that are allowed as a part of the field values For example: The regular expression, Note: For information about the supported regular expressions, you can refer to a guide such as This regular expression does not apply to the GECOS field, which can have any characters. |
|
isSudoWithNoPasswd Note: This entry does not exist by default. If you want the support for SUDO user with NoPasswd, then you must add it to the configuration lookup definition. |
true/false |
true: If NoPasswd is configured for SUDO user. If not, false. |
|
defaultConnectorShell |
Note: If you are using RBAC, then the decode value must be changed from |
This is the defaultShell used for connector operations. Do not modify this entry unless you are using RBAC |
2.3.5 Setting up the Lookup Definition for Connection Pooling
By default, this connector uses the ICF connection pooling.
Table 2-5 lists the connection pooling properties, their description, and default values set in ICF:
Table 2-5 Connection Pooling Properties
| Property | Description |
|---|---|
|
Pool Max Idle |
Maximum number of idle objects in a pool. Default value: |
|
Pool Max Size |
Maximum number of connections that the pool can create. Default value: |
|
Pool Max Wait |
Maximum time, in milliseconds, the pool must wait for a free object to make itself available to be consumed for an operation. Default value: |
|
Pool Min Evict Idle Time |
Minimum time, in milliseconds, the connector must wait before evicting an idle object. Default value: |
|
Pool Min Idle |
Minimum number of idle objects in a pool. Default value: |
If you want to modify the connection pooling properties to use values that suit requirements in your environment, then:
2.3.6 Setting up the Lookup Definitions for User Operations
The user management lookup definitions are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed. The lookup definitions are as follows:
2.3.6.1 Lookup.UNIX.UM.Configuration
The Lookup.UNIX.UM.Configuration lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during user management operations.
Table 2-6 lists the default entries in this lookup definition.
Table 2-6 Entries in the Lookup.UNIX.UM.Configuration
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.UNIX.UM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. See Lookup.UNIX.UM.ProvAttrMap for more information about this lookup definition. |
|
Recon Attribute Map |
Lookup.UNIX.UM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.UNIX.UM.ReconAttrMap for more information about this lookup definition. |
|
Recon Transformation Lookup Note: This entry does not exist by default. You must add it if you want to enable transformation during reconciliation. |
Lookup.UNIX.UM.ReconTransformation |
This entry holds the name of the lookup definition that is used to configure transformation of attribute values that are fetched from the target system during user reconciliation. See Configuring Transformation of Data During User Reconciliation for more information about adding entries in this lookup definition. |
|
Recon Validation Lookup Note: This entry does not exist by default. You must add it if you want to enable validation during reconciliation. |
Lookup.UNIX.UM.ReconValidation |
This entry holds the name of the lookup definition that is used to configure validation of attribute values that are fetched from the target system during reconciliation. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition. |
|
Provisioning Validation Lookup Note: This entry does not exist by default. You must add it if you want to enable validation during provisioning. |
Lookup.UNIX.UM.ProvValidation |
This entry holds the name of the lookup definition that is used to configure validation of attribute values entered on the process form during provisioning operations. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition. |
|
Recon Exclusion Lookup Note: This entry does not exist by default. You must add it if you want to enable resource exclusions during reconciliation. |
Lookup.UNIX.UM.ProvExclusionList |
This entry holds the name of the lookup definition that is used to configure resource exclusion lists during reconciliation. See Configuring Resource Exclusion Lists for more information. |
|
Provisioning Exclusion Lookup Note: This entry does not exist by default. You must add it if you want to enable resource exclusions during provisioning. |
Lookup.UNIX.UM.ReconExclusionList |
This entry holds the name of the lookup definition that is used to configure resource exclusion lists during provisioning operations. See Configuring Resource Exclusion Lists for more information about adding entries in this lookup definition. |
2.3.6.2 Lookup.UNIX.UM.Configuration.Trusted
The Lookup.UNIX.UM.Configuration.Trusted lookup definition holds configuration entries that are specific to the user object type when the target system is configured as a trusted source. This lookup definition is used during user management operations.
Table 2-7 lists the default entries in this lookup definition.
Table 2-7 Entries in the Lookup.UNIX.UM.Configuration.Trusted
| Code Key | Decode | Description |
|---|---|---|
|
Recon Attribute Defaults |
Lookup.UNIX.UM.ReconAttrMap.TrustedDefaults |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. See Lookup.UNIX.UM.ReconAttrMap.TrustedDefaults for more information about this lookup definition. |
|
Recon Attribute Map |
Lookup.UNIX.UM.ReconAttrMap.Trusted |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.UNIX.UM.ReconAttrMap.Trusted for more information about this lookup definition. |
2.3.7 Setting up the Lookup Definitions for Attribute Mappings
The attribute mapping lookup definitions are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed. The lookup definitions are as follows:
2.3.7.1 Lookup.UNIX.UM.ProvAttrMap
The Lookup.UNIX.UM.ProvAttrMap lookup definition holds mappings between process form fields (Code Key values) and target system attributes (Decode values) used during provisioning operations.
You can add entries to this lookup if you want to map new target system attributes for provisioning. See Adding Custom Attributes for Provisioning for more information.
Table 2-8 lists the default entries in this lookup definition.
Table 2-8 Entries in the Lookup.UNIX.UM.ProvAttrMap
| Code Key | Decode |
|---|---|
|
Create home directory |
CREATE_HOME_DIR |
|
Expire Date[DATE] |
EXP_DATE##DATE## |
|
GECOS |
COMMENTS##COMMENTS## |
|
Home Directory |
HOME_DIR |
|
Inactive Days |
INACTIVE |
|
Password |
__PASSWORD__ |
|
Primary Group[LOOKUP] |
PGROUP |
|
ReturnValue |
__UID__ |
|
Skeleton Directory |
SKEL_DIR |
|
UD_UNIX_CH~Secondary Group[LOOKUP] |
SECONDARYGROUP |
|
UID |
USID |
|
User Login |
__NAME__ Note: This value is a target system attribute, used by the connector for internal purposes. |
|
User Shell[LOOKUP] |
USER_SHELL |
2.3.7.2 Lookup.UNIX.UM.ReconAttrMap
The Lookup.UNIX.UM.ReconAttrMap lookup definition holds mappings between resource object fields (Code Key values) and target system attributes (Decode values) used during reconciliation operations.
You can add entries to this lookup definition if you want to map new target system attributes for reconciliation. See Adding Custom Attributes for Target Resource Reconciliation for more information.
Table 2-9 lists the default entries in this lookup definition.
Table 2-9 Entries in the Lookup.UNIX.UM.ReconAttrMap
| Code Key | Decode |
|---|---|
|
Create home directory |
CREATE_HOME_DIR |
|
Expire Date[DATE] |
EXP_DATE##DATE## |
|
GECOS |
COMMENTS |
|
Home Directory |
HOME_DIR |
|
Inactive Days |
INACTIVE |
|
Primary Group[LOOKUP] |
PGROUP |
|
ReturnValue |
__UID__ Note: This value is a target system attribute, used by the connector for internal purposes. |
|
Secondary Groups~Secondary Group[LOOKUP] |
SECONDARYGROUP |
|
Status |
__ENABLE__ |
|
UID |
USID |
|
User Login |
__NAME__ |
|
User Shell[LOOKUP] |
USER_SHELL |
2.3.7.3 Lookup.UNIX.UM.ReconAttrMap.Trusted
The Lookup.UNIX.UM.ReconAttrMap.Trusted lookup definition holds mappings between resource object fields (Code Key values) and target system attributes (Decode values) used during reconciliation operations. This lookup definition is used during user management operations when the target system is configured as a trusted source.
Table 2-10 lists the default entries in this lookup definition.
Table 2-10 Entries in the Lookup.UNIX.UM.ReconAttrMap.Trusted
| Code Key | Decode |
|---|---|
|
LastName |
__NAME__ |
|
TrustedStatus[TRUSTED] |
__ENABLE__ |
|
User ID |
__UID__ |
2.3.7.4 Lookup.UNIX.UM.ReconAttrMap.TrustedDefaults
The Lookup.UNIX.UM.ReconAttrMap.TrustedDefaults lookup definition is used when the target system is configured as a trusted source.
These entries are OIM User attributes. The fields are not mapped to any UNIX target system fields. The default values are set for these fields in this lookup.
Table 2-11 lists the default entries in this lookup definition.
Table 2-11 Entries in the Lookup.UNIX.UM.ReconAttrMap.TrustedDefaults
| Code Key | Decode |
|---|---|
|
Organization |
Xellerate Users |
|
Role |
Full-Time |
|
User Type |
End-User |
2.3.7.5 Lookup.UNIX.YesNo.Options
The Lookup.UNIX.YesNo.Options lookup definition is used to set value for a process form field that is boolean in nature, such as true or false. Do not modify the entries in this lookup definition.
This lookup contains the following entries by default:
| Code Key | Decode |
|---|---|
|
false |
false |
|
true |
true |
2.3.8 Enabling Logging
Oracle Identity Manager uses Oracle Java Diagnostic Logging (OJDL) for logging. OJDL is based on java.util.logger. To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
Note:
In an Oracle Identity Manager cluster, perform this procedure on each node of the cluster. Then, restart each node.
-
SEVERE.intValue()+100
This level enables logging of information about fatal errors.
-
SEVERE
This level enables logging of information about errors that might allow Oracle Identity Manager to continue running.
-
WARNING
This level enables logging of information about potentially harmful situations.
-
INFO
This level enables logging of messages that highlight the progress of the application.
-
CONFIG
This level enables logging of information about fine-grained events that are useful for debugging.
-
FINE, FINER, FINEST
These levels enable logging of information about fine-grained events, where FINEST logs information about all events.
These log levels are mapped to ODL message type and level combinations as shown in
Table 2-12 Log Levels and ODL Message Type:Level Combinations
| Log Level | ODL Message Type:Level |
|---|---|
| SEVERE.intValue()+100 | INCIDENT_ERROR:1 |
| SEVERE | ERROR:1 |
| WARNING | WARNING:1 |
| INFO | NOTIFICATION:1 |
| CONFIG | NOTIFICATION:16 |
| FINE | TRACE:1 |
| FINER | TRACE:16 |
| FINEST | TRACE:32 |
The configuration file for OJDL is logging.xml, which is located at the following path:
DOMAIN_HOME/config/fmwconfig/servers/OIM_SERVER/logging.xml
Here, DOMAIN_HOME and OIM_SERVER are the domain name and server name specified during the installation of Oracle Identity Manager.
To enable logging in Oracle WebLogic Server:
-
Edit the logging.xml file as follows:
-
Add the following blocks in the file:
<log_handler name='unix-handler' level='[LOG_LEVEL]' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='[FILE_NAME]'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler>
<logger name="ORG.IDENTITYCONNECTORS.GENERICUNIX" level="[LOG_LEVEL]" useParentHandlers="false"> <handler name="unix-handler"/> <handler name="console-handler"/> </logger> -
Replace both occurrences of
[LOG_LEVEL]with the ODL message type and level combination that you require. Table 2-12 lists the supported message type and level combinations.Similarly, replace
[FILE_NAME]with the full path and name of the log file in which you want log messages to be recorded.The following blocks show sample values for
[LOG_LEVEL]and[FILE_NAME]:<log_handler name='unix-handler' level='NOTIFICATION:1' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='F:\MyMachine\middleware\user_projects\domains\base_domain1\servers\oim_server1\logs\oim_server1-diagnostic-1.log'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler> <logger name="ORG.IDENTITYCONNECTORS.GENERICUNIX" level="NOTIFICATION:1" useParentHandlers="false"> <handler name="telnetssh-handler"/> <handler name="console-handler"/> </logger>
With these sample values, when you use Oracle Identity Governance, all messages generated for this connector that are of a log level equal to or higher than the
NOTIFICATION:1level are recorded in the specified file. -
-
Save and close the file.
-
Set the following environment variable to redirect the server logs to a file:
For Microsoft Windows:
set WLS_REDIRECT_LOG=FILENAMEFor UNIX:
export WLS_REDIRECT_LOG=FILENAMEReplace FILENAME with the location and name of the file to which you want to redirect the output.
-
Restart the application server.
2.3.9 Changing to the Required Input Locale
Changing to the required input locale (language and country setting) involves installing the required fonts and setting the required input locale.
Note:
In an Oracle Identity Manager cluster, you must perform this step on each node of the cluster. Then, restart each node.
You may require the assistance of the system administrator to change to the required input locale.
2.3.10 Clearing Content Related to Connector Resource Bundles from the Server Cache
When you deploy the connector, the resource bundles are copied from the resources directory on the installation media into the Oracle Identity Manager database. Whenever you add a new resource bundle to the connectorResources directory or make a change in an existing resource bundle, you must clear content related to connector resource bundles from the server cache.
Note:
In an Oracle Identity Manager cluster, you must perform this step on each node of the cluster. Then, restart each node.
To clear content related to connector resource bundles from the server cache:
2.3.11 Localizing Field Labels in UI Forms
You can localize UI form field labels by using the resource bundle corresponding to the language you want to use. The resource bundles are available in the connector installation package.
Note:
Perform the procedure described in this section only if you are using Oracle Identity Manager release 11.1.2.x or later and you want to localize UI form field labels.
To localize field label that you add to in UI forms:
-
Log in to Oracle Enterprise Manager.
-
In the left pane, expand Application Deployments and then select oracle.iam.console.identity.sysadmin.ear.
-
In the right pane, from the Application Deployment list, select MDS Configuration.
-
On the MDS Configuration page, click Export and save the archive to the local computer.
-
Extract the contents of the archive, and open the following file in a text editor:
-
For Oracle Identity Manager 11g Release 2 PS2 (11.1.2.2.0) or later releases:
SAVED_LOCATION\xliffBundles\oracle\iam\ui\runtime\BizEditorBundle_en.xlf
-
For releases prior to Oracle Identity Manager 11g Release 2 PS2 (11.1.2.2.0):
SAVED_LOCATION\xliffBundles\oracle\iam\ui\runtime\BizEditorBundle.xlf
-
-
Edit the BizEditorBundle.xlf file in the following manner:
-
Search for the following text:
<file source-language="en" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">
-
Replace with the following text:
<file source-language="en" target-language="LANG_CODE" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">In this text, replace LANG_CODE with the code of the language that you want to localize the form field labels. The following is a sample value for localizing the form field labels in French:
<file source-language="en" target-language="fr" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">
-
Search for the application instance code. This procedure shows a sample edit for UNIX application instance. The original code is:
<trans-unit id="${adfBundle['oracle.adf.businesseditor.model.util.BaseRuntimeResourceBundle']['persdef.sessiondef.oracle.iam.ui.runtime.form.model.user.entity.userEO.UD_UNIX_GRPNAME__c_description']}"> <source>Primary Group</source> </target> </trans-unit> <trans-unit id="sessiondef.oracle.iam.ui.runtime.form.model.UNIX.entity.UNIXEO.UD_UNIX_GRPNAME__c_LABEL"> <source>Primary Group</source> </target> </trans-unit> -
Open the resource file from the connector package, for example UNIX_fr.properties, and get the value of the attribute from the file, for example, global.udf.UD_UNIX_GRPNAME= Groupe principal.
-
Replace the original code shown in Step 6.c with the following:
<trans-unit id="${adfBundle['oracle.adf.businesseditor.model.util.BaseRuntimeResourceBundle']['persdef.sessiondef.oracle.iam.ui.runtime.form.model.user.entity.userEO.UD_UNIX_GRPNAME__c_description']}"> <source> Primary Group</source> <target> Groupe principal</target> </trans-unit> <trans-unit id="sessiondef.oracle.iam.ui.runtime.form.model.UNIX.entity.UNIXEO.UD_UNIX_GRPNAME__c_LABEL"> <source> Primary Group</source> <target> Groupe principal</target> </trans-unit> -
Repeat Steps 6.a through 6.d for all attributes of the process form.
-
Save the file as BizEditorBundle_LANG_CODE.xlf. In this file name, replace LANG_CODE with the code of the language to which you are localizing.
Sample file name: BizEditorBundle_fr.xlf.
-
-
Repackage the ZIP file and import it into MDS.
See Also:
Deploying and Undeploying Customizations in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance for more information about exporting and importing metadata files
-
Log out of and log in to Oracle Identity Governance.
2.4 Upgrading the Connector
If you have already deployed an earlier release of this connector, then upgrade the connector to the current release 11.1.1.7.0.
Note:
Before you perform the upgrade procedure:
-
It is strongly recommended that you create a backup of the Oracle Identity Manager database. Refer to the database documentation for information about creating a backup.
-
As a best practice, first perform the upgrade procedure in a test environment.
-
If you have added custom attributes to an earlier release of the connector, you must retain and configure all the custom attributes after the upgrade procedure.
The following sections discuss the procedure to upgrade the connector:
2.4.1 Preupgrade Steps
Perform the following preupgrade steps:
- Perform a reconciliation run to fetch all latest updates to Oracle Identity Manager.
- Perform the preupgrade procedure documented.
- Define the source connector (an earlier release of the connector that must be upgraded) in Oracle Identity Manager. You define the source connector to update the Deployment Manager XML file with customization changes made to the connector.
2.4.2 Upgrade the UNIX Connector from Release 11.1.1.6.0 to 11.1.1.7.0
You can upgrade the UNIX connector from release 11.1.1.6.0 to this release of the connector.
To do so, perform the following procedures:
2.4.2.1 Setting Entitlement Tagging
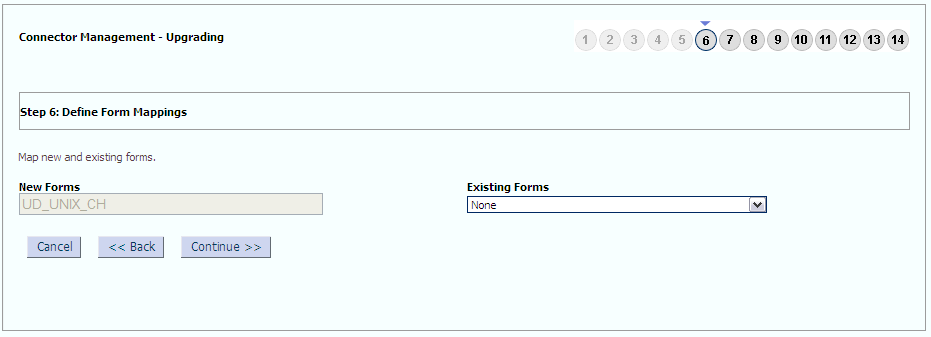
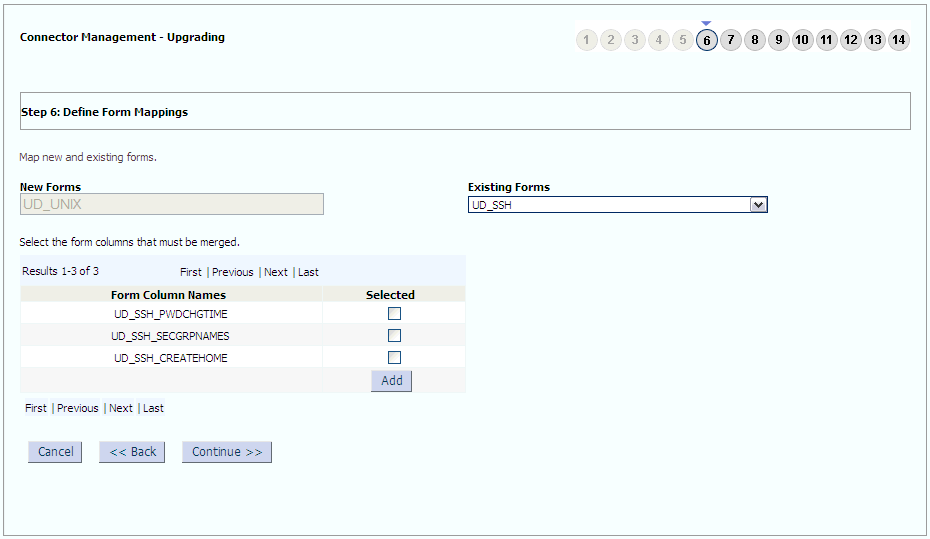
To set entitlement tagging for secondary groups child form (UD_UNIX_CH), do the following:
- Log in to the Oracle Identity Manager Design Console.
- Expand Development Tools and then double-click Form Designer.
- Enter the name of the UNIX child form,
UD_UNIX_CH,in the Table Name field and click the Query for records button. - Click Create New Version.
- In the Create a New Version dialog box, specify the version name in the Label field, save the changes, and then close the dialog box.
- From the Current Version list, select the newly created version.
- Click the Properties tab.
- Select the Secondary Group field, and click Add Property.
- From the Property Name list, select Entitlement.
- In the Property Value field, enter
true. - Click Make Version Active.
2.4.2.2 Setting IT Resource, Account ID, and Account Name Tagging
To set IT resource, Account ID, and Account Name tagging in the process form (UD_UNIX), do the following:
- In the Oracle Identity Manager Design Console, expand Development Tools and then double-click Form Designer.
- Enter the name of the parent form,
UD_UNIX,in the Table Name field and click the Query for records button. - Click Create New Version.
- In the Create a New Version dialog box, specify the version name in the Label field, save the changes, and then close the dialog box.
- From the Current Version list, select the newly created version.
- Click the Properties tab.
- Select the IT Resource field, and click Add Property.
- From the Property Name list, select ITResource.
- In the Property Value field, enter
true. - Select the User Login field, and click Add Property.
- From the Property Name list, select AccountName.
- In the Property Value field, enter
true. - Select the User Login field, and click Add Property.
- From the Property Name list, select AccountID.
- In the Property Value field, enter
true. - Update the parent form to add the child form created in Step 1.
- Click Make Version Active.
- Recreate the form in the user interface (UI) and update the application instance with the new form as described in Updating an Existing Application Instance with a New Form.
2.4.2.3 Setting the Status of Task to Object Status Mapping of the Secondary Group Update Process Task to None
To set the status of task to object status mapping of the secondary group update process task to none, do the following:
- In the Oracle Identity Manager Design Console, expand Process Management and then double-click Process definition.
- In the Name field, enter
UNIXand then click the Query for records button. - Under Tasks, open the Secondary Group Update task.
- In the Task to Object Status Mapping tab, change the Object Status of status C from Provisioned to
None.
2.4.3 Upgrade Steps
Depending on the environment in which you are upgrading the connector, perform one of the following steps:
-
Staging Environment
Perform the upgrade procedure by using the wizard mode.
-
Production Environment
Perform the upgrade procedure by using the silent mode.
See Procedure to Upgrade a Connector in Oracle Fusion Middleware Administering Oracle Identity Manager for detailed information about the wizard and silent modes.
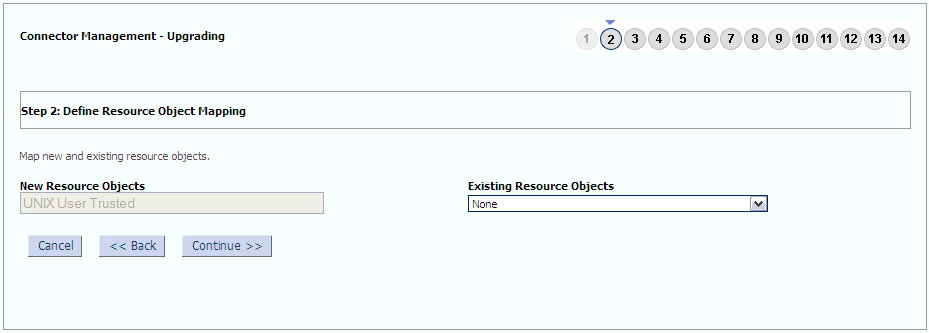
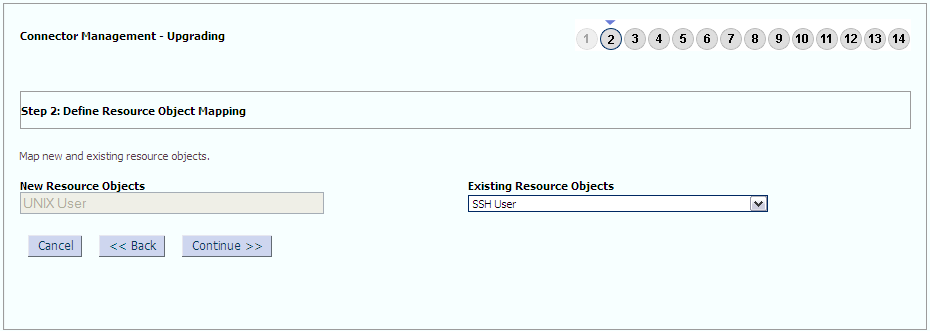
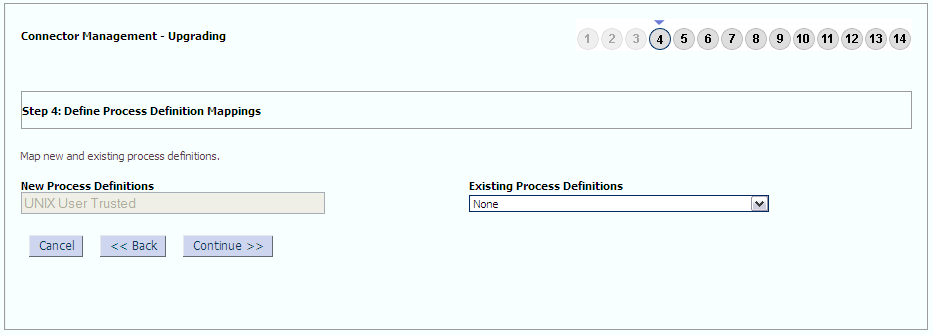
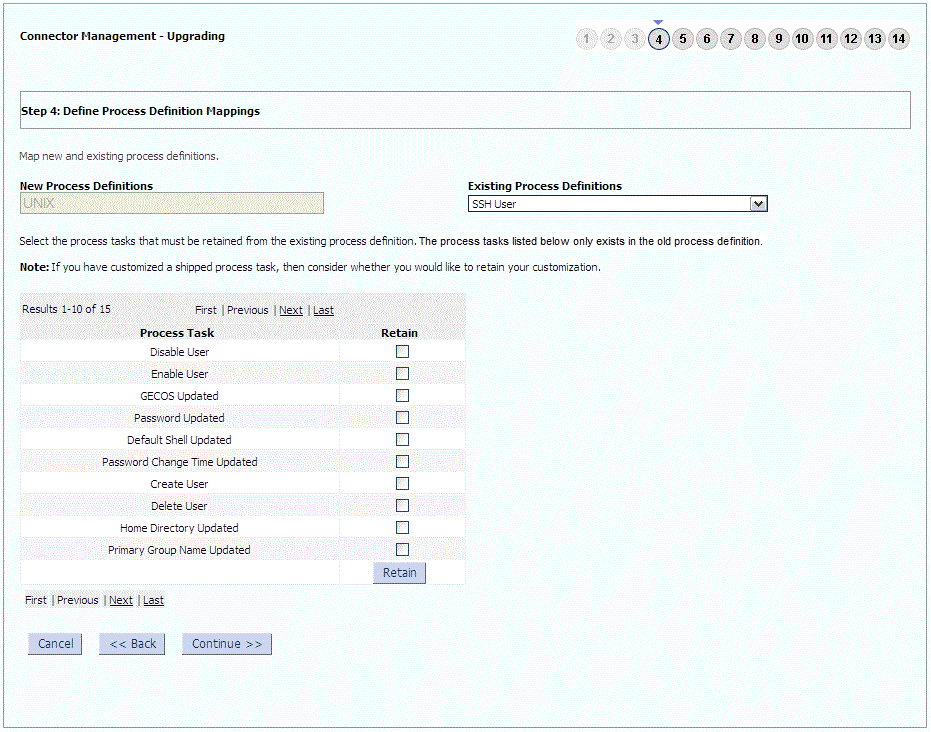
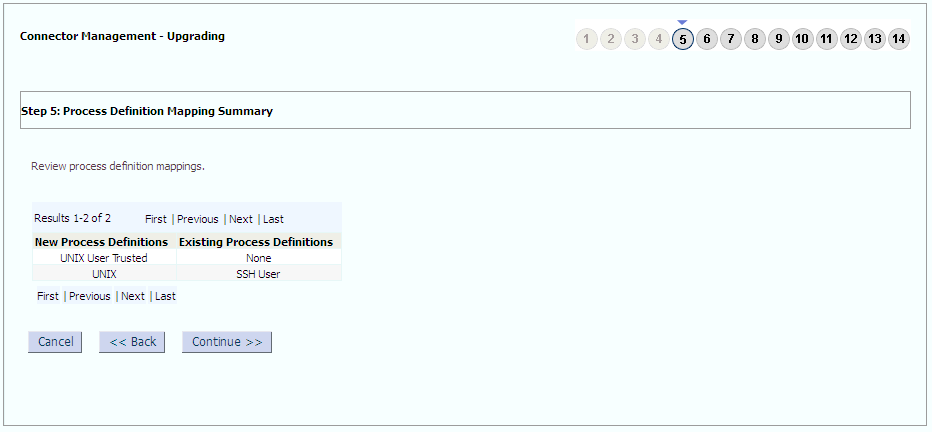
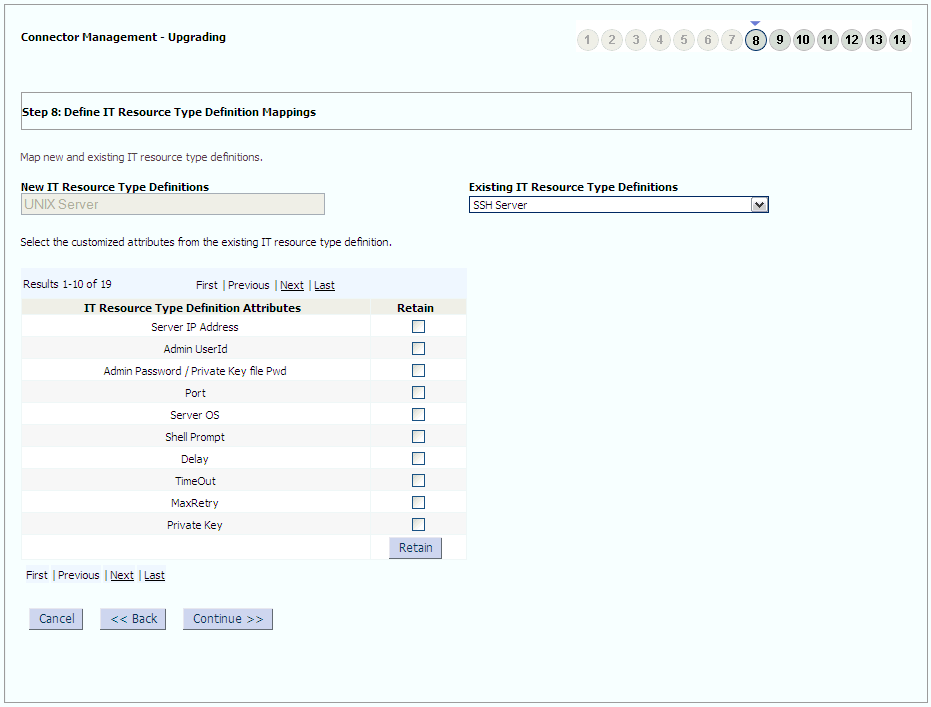
The following sample screenshots show the connector artifacts to be mapped between the new and the old connectors:
2.4.4 Postupgrade Steps
Perform the following postupgrade steps:
-
If you are using Oracle Identity Manager release 11.1.2.x or later, you must create a new UI form and attach it to an existing application instance to view the user-defined fields (UDFs or custom attributes). For more information about UDFs, see Configuring Custom Attributes in Oracle Fusion Middleware Administering Oracle Identity Manager.
-
Modify the parent form and the child form as follows:
-
Create a new version of the parent form, UD_UNIX, and make it active.
For example: v_11.1.1.7.2
-
Ensure that the child form, UD_UNIX_CH, is linked to the parent form UD_UNIX in the Design Console.
Note:
You must perform these steps as a workaround for the known issue where the parent form is not linked to the child form after upgrading the connector. This issue is also described under Bug 13690646 in Known Issues.
-
-
Re-configure the IT resource of the source connector (an earlier release of the connector that must be upgraded). See Configuring the IT Resource for the Target System for information.
-
Run the Form Version Control (FVC) utility to manage data changes on a form after an upgrade operation. To do so:
-
In a text editor, open the fvc.properties file located in the OIM_DC_HOME directory and include the following entries:
FormName;UD_UNIX FromVersion;3 ToVersion;v_11.1.1.7.2 ParentParent;UD_UNIX_USERLOGIN;UD_UNIX_RETURNVALUE Parent;UD_UNIX_CREATE_HOME_DIR;false
Note:
The value of the ToVersion field must match the version of the child form created in Step 3.a.
-
Run the FVC utility. This utility is copied into the following directory when you install the design console:
For Microsoft Windows:
OIM_DC_HOME/fvcutil.bat
For UNIX:
OIM_DC_HOME/fvcutil.sh
When you run this utility, you are prompted to enter the login credentials of the Oracle Identity Manager administrator, and the logger level and log file location.
-
-
Run the PostUpgradeScriptUnix.sql script as follows:
-
Connect to the Oracle Identity Manager database by using the OIM User credentials.
-
Run the PostUpgradeScriptUnix.sql located in the OIM_HOME/server/ConnectorDefaultDirectory/UNIX_Package/Upgrade directory.
-
-
Setup incremental reconciliation as follows:
-
On the target system, copy the password mirror file (
/etc/passwd1), the shadow mirror file (/etc/shadow1), and the group file (/etc/group) to the location specified by the mirrorFilesLocation attribute (/etc/connector_mirror_files) in the configuration lookup definition (Lookup.UNIX.Configuration). -
Get the current date and time on the target system by running one of the following commands:
For Linux, use
$(date '+%d%m%Y%s%N')For Solaris, use
(date '+%m%d%y%H%M%S'$random)For HPUX and AIX, use
($(date '+%m%d%Y%S')$RANDOM) -
Save this value as syncToken.
For example,
syncToken = '090420121333955808939929000' -
Rename the /etc/connector_mirror_files/passwd1 file to SYNCTOKEN.passwd.
For example:
/etc/connector_mirror_files/090420121333955808939929000.passwd. -
Rename the /etc/connector_mirror_files/shadow1 file to SYNCTOKEN.shadow.
For example:
/etc/connector_mirror_files/090420121333955808939929000.shadow. -
Rename the /etc/connector_mirror_files/group file to SYNCTOKEN.group.
For example:
/etc/connector_mirror_files/090420121333955808939929000.group. -
Log in to the Oracle Identity Manager Administrative and User Console.
-
On the Welcome to Oracle Identity Manager Self Service page, click Advanced in the upper-right corner of the page.
-
Search for and open the UNIX Target Incremental Resource User Reconciliation scheduled task.
-
On the Job Details tab, in the Parameters region, specify the following value for the Sync Token attribute of the scheduled task:
<String>090420121333955808939929000</String>Note:
For other flavors of Unix, you can use the same syncToken format for the Sync Token attribute of the incremental reconciliation scheduled task.
-
After specifying the attribute, click Apply to save the changes.
-
2.5 Postcloning Steps
You can clone the connector by setting new names for some of the objects that comprise the connector. The outcome of the process is a new connector XML file. Most of the connector objects, such as Resource Object, Process Definition, Process Form, IT Resource Type Definition, IT Resource Instances, Lookup Definitions, Adapters, Reconciliation Rules and so on in the new connector XML file have new names.
See Also:
Cloning Connectors in Oracle Fusion Middleware Administering Oracle Identity Manager for information about the privileges required to perform connector operations
After a copy of the connector is created by setting new names for connector objects, some objects might contain the details of the old connector objects. Therefore, you must modify the following Oracle Identity Manager objects to replace the base connector artifacts or attribute references with the corresponding cloned artifacts or attributes:
-
Lookup Definition
If the lookup definition contains the old lookup definition details, then you must modify it to provide the new cloned lookup definition names. If the Code Key and Decode values are referring the base connector attribute references, then replace these with new cloned attributes.
-
Scheduled Task
You must replace the base connector resource object name in the scheduled task with the cloned resource object name. If the scheduled task parameter has any data referring to the base connector artifacts or attributes, then these must be replaced with the new cloned connector artifacts or attributes.
-
Child Table
You must reassign the adapter and add a new literal value to the childTableName variable of a child table after cloning the connector.
To update a child table:
- Log in to Design Console.
- Open the process task and click Integrations tab.
- Click Remove to unassign the adapter to the process task.
- Click Add to assign the same adapter to the process task.
- Assign a new literal value to the childTableName variable.
- Map the other adapter variables as per the previous mappings.
-
Localization Properties
You must update the resource bundle of a user locale with new names of the process form attributes for proper translations after cloning the connector. You can modify the properties file of your locale in the resources directory of the connector bundle.
For example, the process form attributes are referenced in the Japanese properties file, UNIX_ja.properties, as
global.udf.UD_UNIX_ALIASNAME.During cloning, if you change the process form name fromUD_UNIXtoUD_UNIX1,then you must update the process form attributes toglobal.udf.UD_UNIX1_ALIASNAME.