Home | Book List | Contents | Contact Us |
Go to main content
|
|
This chapter introduces the Database Application Tables connector.
Topics:
Database Application Tables connector (DBAT connector enables the exchange of user data between the database and Oracle Identity Manager.
Oracle Identity Manager (OIM) platform automates access rights management, security, and provisioning of IT resources. Oracle Identity Manager connects users to resources, and revokes and restricts unauthorized access to protect sensitive corporate information. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with external and identity-aware applications such as PeopleSoft and MySQL.
In an enterprise setup, many applications in your organization may use relational database tables as a repository for user data. This guide describes the procedure to dynamically generate the connector based on the underlying schema of the database table user store, and to install and use this connector for managing user lifecycle and entitlements from Oracle Identity Manager. After you integrate the tables with Oracle Identity Manager by using the connector, you can use them either as a managed (target) resource or as an authoritative (trusted) source of user data for Oracle Identity Manager.
The connector that you generate is known as a Database Application Tables connector (DBAT connector). The following sample scenario describes the requirement that can be addressed by a DBAT connector:
Example Inc. has some database-driven custom applications. These applications do not have any APIs for identity administration. The company wants to manage the lifecycle of users in these custom applications by using a centralized identity management system such as OIM.
The DBAT connector is one of the solutions to this business problem. Example Inc. can use this connector to enable the exchange of user data between the database and Oracle Identity Manager.
Note:
In this guide:
The database tables and their relation tables that store user data are collectively referred to as the target system.
The computer on which the database is installed is referred to as the target system host computer.
RELEASE_NUMBER has been used as a placeholder for the current release number of the connector. Therefore, replace all instances of RELEASE_NUMBER with the release number of the connector. For example, 11.1.1.6.0.
Target systems are identity-aware applications such as databases, Microsoft Active Directory, Siebel and so on that can be managed by Oracle Identity Manager connectors.
In general, there are two broad categories of target systems for which Oracle Identity Manager connectors exist:
Predefined target systems: These are target systems that have a static schema and the connector is aware of this schema. This means that connectors for such target systems are shipped with preconfigured metadata or connector artifacts such as IT resource definition, process forms, resource objects, and so on.
Discovered target systems: These are target systems for which the schema is not known in advance. For example, a flat file does not have a fixed schema. Each target system can have a totally different schema. The connector is not initially aware of the schema that it is supposed to integrate with and the attributes available.
The DBAT connector is a connector for a discovered target system.
Connectors for discovered target systems are not shipped with any artifacts. They are shipped only with a set of deployment utilities that help in discovering the schema and then generating the artifacts.
Discovery is the process of identifying the underlying schema of your database. You can discover the schema of your database by configuring a groovy file and running the DBAT Generator. This is discussed later in the guide.
These are the software components and their versions required for installing and using the DBAT connector.
Table 1-1 lists the certified components for this connector.
Table 1-1 Certified Components
| Item | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Governance or Oracle Identity Manager:
|
|
Target systems |
The target system can be database tables from any one of the following RDBMSs:
|
|
JDBC drivers |
Depending on the target system that you use, download one of the following sets of JDBC drivers from the Vendor's Web site: For IBM DB2:
For Microsoft SQL Server:
For MySQL: mysql-connector-java-5.1.12-bin For Oracle Database or Oracle RAC:
For Sybase Adaptive Server Enterprise: jconn3 |
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 or later |
|
Format in which user data is stored in the target system |
You can use a Database Application Tables connector only if user data is stored in the target system in any one of the following formats:
|
|
Other requirements of the target system |
The target system must meet the following requirement: If parent and child tables are not joined by a foreign key (for example, if you are using views), then the names of the foreign key columns in both tables must be the same. |
These are the recommendations for the DBAT connector versions that you can deploy and use depending on the Oracle Identity Governance or Oracle Identity Manager version that you are using.
You must deploy and use one of the following connectors:
If you are using an Oracle Identity Manager release that is earlier than Oracle Identity Manager 11g Release 2 BP10 (11.1.2.0.10), then you must use the 9.1.0.x version of this connector.
If you are using any of the Oracle Identity Manager releases listed in Table 1-1, then you must use the latest 11.1.1.x version of this connector.
The DBAT connector will support the languages that are supported by Oracle Identity Manager.
Resource bundles are not part of the connector installation media as the resource bundle entries vary depending on the target system being used.
Lear more about the data types supported for reconciliation and provisioning.
The data types supported for reconciliation and provisioning operations are listed in the following section:
Note:
Complex data types, such as RAW, Binary File, CLOB, and BLOB, are not supported. Any data type that is not supported and is not a complex data type is treated as a String data type.
For IBM DB2 Database:
SMALLINT
BIGINT
INTEGER
REAL
FLOAT
DOUBLE
DECIMAL
CHARACTER
VARCHAR
DATE
TIMESTAMP
For Microsoft SQL Server:
CHAR
VARCHAR
SMALLINT
INT
BIGINT
DECIMAL
NUMERIC
NVARCHAR
FLOAT
REAL
SMALLDATETIME
DATETIME
For MySQL:
BOOL
SMALLINT
MEDIUMINT
INT
BIGINT
FLOAT
DOUBLE
DECIMAL
CHAR
VARCHAR
TINYTEXT
DATE
DATETIME
TIMESTAMP
For Oracle Database:
VARCHAR2
CHAR
NUMBER
NUMERIC
INTEGER
INT
SMALLINT
DOUBLE
FLOAT
DECIMAL
DEC
REAL
DATE
TIMESTAMP
For Sybase Database:
CHAR
DATE
VARCHAR
TINYINT
SMALLINT
INT
NUMERIC
DECIMAL
FLOAT
REAL
DATETIME
The DBAT connector is implemented by using the Identity Connector Framework (ICF). The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Governance connectors. The ICF is shipped along with Oracle Identity Governance. Therefore, you need not configure or modify it.
Figure 1-1 shows the architecture of the connector.
The Database Application Tables connector is implemented by using the Identity Connector Framework (ICF). The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. The ICF is shipped along with Oracle Identity Manager.
The DBAT connector is not shipped with any metadata as it is a connector for a discovered target. Depending on the database schema, the connector artifacts are generated during connector deployment.
The following is a high-level description of the stages into which the connector deployment and usage procedure is divided into:
Generating the connector
Discovering the schema is one of the important aspects in generating the connector. The DBAT connector includes a groovy file in which you can specify information about your target system. This information is used by the DBAT Generator, one of the deployment utilities shipped with the connector, to discover your schema and generate the connector.
In other words, when you run the DBAT generator on the groovy file, the connector package is generated. This package contains an XML file that contains definitions for connector components such as adapters, process tasks, scheduled tasks, lookup definitions, and IT resource. Connector operations such as provisioning and reconciliation are performed using these connector components.
Installing and configuring the connector
In this stage, you install the generated connector by running the connector installer and then perform configuration tasks such as configuring the IT resource, enabling logging and so on.
Using the connector
In this stage, you start using the connector to perform connector operations such as reconciliation and provisioning.
The DBAT connector can be configured to run in one of the following modes:
Identity reconciliation
In the identity reconciliation mode, the target system is used as the trusted source and users are directly created and modified on it directly outside Oracle Identity Manager.
During reconciliation, a scheduled job establishes a connection with the target system and sends reconciliation criteria to the APIs. The APIs extract user records that match the reconciliation criteria and hand them over to the scheduled task, which brings the records to Oracle Identity Manager. The next step depends on the mode of connector configuration.
Each record fetched from the target system is compared with existing OIM Users. If a match is found, then the update made to the record on the target system is copied to the OIM User attributes. If no match is found, then the target system record is used to create an OIM User.
Note:
Trusted reconciliation does not support multivalued attributes, for example, child table entries.Account Management
In the account management mode, the target system is used as a target resource. The connector enables the target resource reconciliation and provisioning operations. Through provisioning operations performed on Oracle Identity Manager, user accounts are created and updated on the target system for OIM Users. During reconciliation from the target resource, the Database Application Tables connector fetches into Oracle Identity Manager data about user accounts that are created or modified on the target system. This data is used to add or modify resources allocated to OIM Users.
During provisioning operations, adapters carry provisioning data submitted through the process form to the target system. APIs on the target system accept provisioning data from the adapters, carry out the required operation on the target system, and return the response from the target system to the adapters. The adapters return the response to Oracle Identity Manager.
During reconciliation, a scheduled task calls the connector bundle which gets the data from target and handles it and returns to OIM and associates it based on Recon rule.
Note:
It is recommended that you do not configure the target system as both an authoritative (trusted) source and a managed (target) resource.
See Installing Connectors in Oracle Fusion Middleware Administering Oracle Identity Manager for detailed information about connector deployment configurations.
This topic provides a flowchart of the DBAT connector deployment process. Each of the steps in this deployment process is discussed in the subsequent chapters.
Figure 1-2 Overall Flow of the Connector Deployment Process
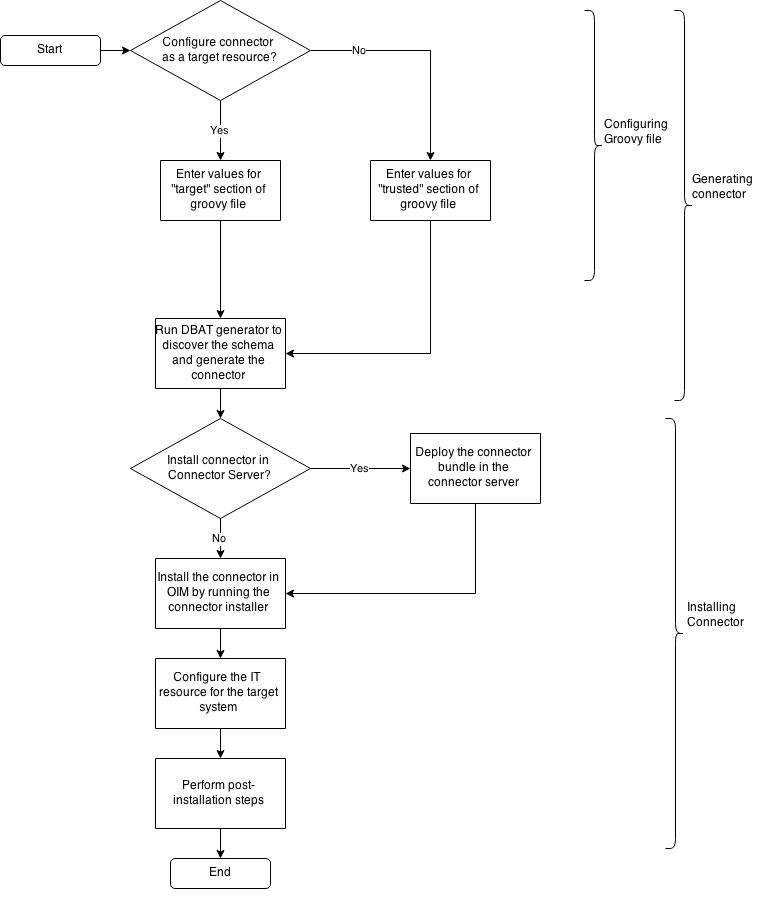
Features in DBAT connector include full reconciliation, incremental reconciliation, limited reconciliation, validation of account data, and so on.
The following are features of the connector:
After you create the connector, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Manager. After the first full reconciliation run, you can configure your connector for incremental reconciliation. In incremental reconciliation, only records that are added or modified after the last reconciliation run are fetched into Oracle Identity Manager.
See About Performing Full Reconciliation and Incremental Reconciliation for more information on full and incremental reconciliation.
To limit or filter the records that are fetched into Oracle Identity Manager during a reconciliation run, you add conditions in the Filter attribute of the scheduled job or in the customizedQuery parameter of the IT resource.
See About Performing Limited Reconciliation for more information.
You can use the connector to configure your target system as either a target resource or trusted source of Oracle Identity Manager.
See Understanding Reconciliation Scheduled Jobs for more information.
Apart from the scheduled jobs for user records reconciliation, there are independent scheduled jobs for reconciliation of deleted user records. In target resource mode, if a record is deleted on the target system, then the corresponding Database Application Tables resource is revoked from the OIM User. In trusted source mode, if a record is deleted on the target system, then the corresponding OIM User is deleted.
See Scheduled Jobs for Reconciliation of Deleted Users Records for more information about the scheduled jobs used for reconciling deleted user records.
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning. In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation. The following sections provide more information:
You can create mappings for OIM User fields that are not included in the list of default mappings. These fields can be either a part of the standard set of OIM User fields provided on the target system or user-defined fields that you add to Oracle Identity Manager.
The following sections provide more information:
The connector runs default SQL queries and statements when you use it to perform reconciliation and provisioning operations. The connector supports calling custom stored procedures to perform connector operations. Instead of these default SQL queries and statements, you can configure the connector to call a script written in the Groovy scripting language, which runs the custom stored procedures.
See Configuring the Connector for Stored Procedures and Groovy Scripts for more information.