Home | Book List | Contents | Contact Us |
Go to main content
|
|
You can use the connector for performing reconciliation and provisioning operations after configuring it to meet your requirements.
The following topics discuss information related to using the connector for performing reconciliation and provisioning operations:
Note:
These sections provide both conceptual and procedural information about configuring the connector. It is recommended that you read the conceptual information before you perform the procedures.Guidelines on Using the Microsoft Active Directory User Management Connector
Performing Provisioning Operations in Oracle Identity Manager Release 11.1.1.x
Performing Provisioning Operations in Oracle Identity Manager Release 11.1.2 or Later
Uninstalling the Microsoft Active Directory User Management Connector
These guidelines give information on what to do when using the connector.
You must apply the following guidelines while performing reconciliation and provisioning operations:
The following are guidelines that you must apply while configuring reconciliation:
Before a target resource reconciliation run is performed, lookup definitions must be synchronized with the lookup fields of the target system. In other words, scheduled tasks for lookup field synchronization must be run before user reconciliation runs.
If you are using Oracle Identity Manager release 11.1.2.x or later, then before you perform a reconciliation run, create an application instance.
The scheduled job for user reconciliation must be run before the scheduled job for reconciliation of deleted user data.
In the identity reconciliation mode, if you want to configure group reconciliation, then note that group reconciliation does not cover reconciliation of updates to existing groups on the target system. If you modify the name of a group on the target system, then it is reconciled as a new group in Oracle Identity Manager.
In the identity reconciliation mode, if you want to configure organization reconciliation, then note that:
Organization reconciliation does not cover reconciliation of updates to existing organization names on the target system. If you modify the name of an organization on the target system, then it is reconciled as a new organization in Oracle Identity Manager.
Organization reconciliation events created by the scheduled job for organization reconciliation (Active Directory Organization Recon) must be successfully processed before the scheduled job for trusted source reconciliation (Active Directory User Trusted Recon) is run. In other words, organization reconciliation must be run and the organization records reconciled from the target system must be successfully linked in Oracle Identity Manager.
On the target system, users are created in specific organizations. During trusted source reconciliation of user data, if you want OIM Users to be created in the same organizations on Oracle Identity Manager, then you must set the MaintainHierarchy attribute of the trusted source reconciliation scheduled task to yes. In addition, you must configure organization reconciliation to run before trusted source reconciliation.
In Oracle Identity Manager, the organization namespace is a flat namespace although it allows parent-child hierarchical relationships between organizations. Therefore, two Microsoft Active Directory OUs with the same name cannot be created in Oracle Identity Manager, even if they have different parent OUs on the target system.
The name of an organization in Oracle Identity Manager cannot contain special characters, such as the equal sign (=) and comma (,). However, these special characters can be used in the name of an organization on the target system.
The synchronization of organization lookup fields is independent of whether or not you configure organization reconciliation.
If you are going to configure Microsoft AD LDS as the trusted source, then you must ensure that a value (either true or false) is set for the msDS-UserAccountDisabled field of each user record on the target system. In Microsoft ADAM, the msDS-UserAccountDisabled field does not have a default value.
The Filter attribute must contain only attributes that are present in the Decode column of the lookup definition that holds reconciliation attribute mapping.
The following are guidelines that you must apply while performing provisioning operations:
Before you perform provisioning operations, lookup definitions must be synchronized with the lookup fields of the target system. In other words, scheduled tasks for lookup field synchronization must be run before provisioning operations.
When both Microsoft Active Directory User Management and Microsoft Exchange connectors are deployed in your environment, do not specify a value for the Redirection Mail Id field.
If you specify a value for the Redirection Mail Id field during a user provisioning operation, then a corresponding mail user account is created in Microsoft Exchange. When an Exchange mail user account is created through Active Directory, then some of the fields of an Exchange mail user account such as Maximum Receive Size cannot be updated. This also means that the Microsoft Exchange Connector cannot be used for further provisioning operations of this user. This is because the user is already created in Microsoft Exchange as a Mailuser.
Note that the Microsoft Exchange connector cannot be used to convert Mailuser, mail user accounts created in the manner described in the preceding paragraph, to Mailbox as this is not allowed by the target. Therefore, it is recommended not to specify a value for the Redirection Mail Id field if both Microsoft Active Directory and Microsoft Exchange connector are deployed.
Passwords for user accounts provisioned from Oracle Identity Manager must adhere to the password policy set in Microsoft Active Directory.
Note:
If you install Microsoft ADAM in a domain controller then it acquires all the policies of Microsoft Active Directory installed in the same domain controller. If you install Microsoft ADAM in a workgroup, then the local system policies are applied.
In Microsoft Active Directory, password policies are controlled through password complexity rules. These complexity rules are enforced when passwords are changed or created. While changing the password of a Microsoft Active Directory account by performing a provisioning operation on Oracle Identity Manager, you must ensure that the new password adheres to the password policies on the target system.
See Also:
For more information about password guidelines applicable on the target system, visit the Microsoft TechNet Web site at
Some Asian languages use multibyte character sets. If the character limit for fields on the target system is specified in bytes, then the number of Asian-language characters that you can enter in a particular field may be less than the number of English-language characters that you can enter in the same field. The following example illustrates this point:
Suppose you can enter 50 characters of English in the User Last Name field of the target system. If you have configured the target system for the Japanese language, then you would not be able to enter more than 25 characters in the same field.
The character length of target system fields must be taken into account when specifying values for the corresponding Oracle Identity Manager fields. For example, ensure that the value you specify for the User Login field in Oracle Identity Manager contains no more than 20 characters. This is because the sAMAccountName attribute in the target system (corresponding to the User Login field in Oracle Identity Manager) cannot contain more than 20 characters.
On the target system, the Manager Name field accepts only DN values. Therefore, when you set or modify the Manager Name field on Oracle Identity Manager, you must enter the DN value.
For example:
cn=abc,ou=lmn,dc=corp,dc=com
If the value that you specify for the Manager Name field contains special characters, then you must prefix each special character with a backslash (\). For example, if you want to specify CN=John Doe #2,OU=sales,DC=example,DC=com as the value of the Manager Name field, then you must specify the following as the value:
CN=John Doe \#2,OU=sales,DC=example,DC=com
The following is the list of special characters that must be prefixed with a backslash (\):
Number sign (#)
Backslash (\)
Plus sign (+)
Equal sign (=)
Comma (,)
Semicolon (;)
Less than symbol (<)
Greater than symbol (>)
Quotation mark (")
While specifying a value for the Home Directory field, follow these guidelines:
The value must always begin with two backslashes (\\).
The value must contain at least one backslash (\), but not at the end.
Correct sample values:
\\SOME_MACHINE\SOME_SHARE\SOME_DIRECTORY
\\SOME_MACHINE\SOME_SHARE\SOME_DIRECTORY\SOME_OTHER_DIRECTORY
Incorrect sample values:
\\SOME_MACHINE\SOME_SHARE\
\\SOME_MACHINE
During a provisioning operation, you can specify multiple auxiliary classes to be attached (to the user account being created) by adding the auxiliary class names as an entry to the Lookup.Configuration.ActiveDirectory lookup definition. See Adding Dynamic Auxiliary Object Classes and Their Attributes to Users for more information.
If you want to provision users and groups under the Users container, then include the following entry in the Lookup.ActiveDirectory.OrganizationalUnits lookup definition:
Code Key:
IT_RESOURCE_KEY~CN=Users,DC=childtest,DC=test,DC=idm,DC=central,DC=example,DC=com
Decode:
IT_RESOURCE_NAME~CN=Users,DC=childtest,DC=test,DC=idm,DC=central,DC=example,DC=com
In the Code Key and Decode values, replace:
IT_RESOURCE_KEY with the numeric code assigned to each IT resource in Oracle Identity Manager. You can determine the value of the IT resource key by performing lookup field synchronization of organizational units and then finding the IT resource key from the code key value of the Lookup.ActiveDirectory.OrganizationalUnits lookup definition.
IT_RESOURCE_NAME with the name of the IT resource in Oracle Identity Manager.
Scheduled jobs for lookup field synchronization fetch the most recent values from specific fields in the target system to lookup definitions in Oracle Identity Manager. These lookup definitions are used as an input source for lookup fields in Oracle Identity Manager.
The following are the scheduled jobs for lookup field synchronization:
Note:
The procedure to configure these scheduled tasks is described later in the guide.
Active Directory Group Lookup Recon
This scheduled task is used to synchronize group lookup fields in Oracle Identity Manager with group-related data in the target system.
Active Directory Organization Lookup Recon
This scheduled task is used to synchronize organization lookup fields in Oracle Identity Manager with organization-related data in the target system.
Table 3-1 describes the attributes of both scheduled jobs.
Table 3-1 Attributes of the Scheduled Tasks for Lookup Field Synchronization
| Attribute | Description |
|---|---|
|
Code Key Attribute |
Name of the connector or target system attribute that is used to populate the Code Key column of the lookup definition (specified as the value of the Lookup Name attribute). Depending on the scheduled job you are using, the default values are as follows:
Note: You must not change the value of this attribute. |
|
Decode Attribute |
Enter the name of the connector or target system attribute that is used to populate the Decode column of the lookup definition (specified as the value of the Lookup Name attribute). Depending on the scheduled job you are using, the default values are as follows:
|
|
Filter |
Enter a filter to filter out records to be stored in the lookup definition. For more information about the Filter attribute, see Limited Reconciliation. |
|
IT Resource Name |
Enter the name of the IT resource for the target system installation from which you want to reconcile records. Sample value: |
|
Lookup Name |
Enter the name of the lookup definition in Oracle Identity Manager that must be populated with values fetched from the target system. Note: If the lookup name that you specify as the value of this attribute is not present in Oracle Identity Manager, then this lookup definition is created while the scheduled job is run. Depending on the scheduled job you are using, the default values are as follows:
|
|
Object Type |
This attribute holds the name of the type of object you want to reconcile. Depending on the scheduled job you are using, the default values are as follows:
|
You can configure the connector to specify the type of reconciliation and its schedule.
This section discusses the following topics related to configuring reconciliation:
Full reconciliation involves reconciling all existing user records from the target system into Oracle Identity Manager. After you deploy the connector, you must first perform full reconciliation. In addition, you can switch from incremental reconciliation to full reconciliation whenever you want to ensure that all target system records are reconciled in Oracle Identity Manager.
For performing a full reconciliation run, values for the following attributes of the scheduled jobs for reconciling user records must not be present:
Batch Start
Filter
Latest Token
At the end of the reconciliation run, the Latest Token attribute of the scheduled job for user record reconciliation is automatically set to the highest value of the uSNChanged attribute of a domain controller that is used for reconciliation. From the next run onward, only records created or modified after the value in the latest token attribute are considered for reconciliation. This is incremental reconciliation.
This section discusses the following topics that help you understand limited reconciliation and the ways in which it can be achieved:
By default, all target system records that are added or modified after the last reconciliation run are reconciled during the current reconciliation run. You can customize this process by specifying the subset of added or modified target system records that must be reconciled.
You can perform limited reconciliation the first time you perform a reconciliation run. In other words, by using filters or by specifying a search base while configuring a scheduled job for full reconciliation, you can perform limited reconciliation.
You can perform limited reconciliation by creating filters for the reconciliation module.
This connector provides a Filter attribute (a scheduled task attribute) that allows you to use any of the Microsoft Active Directory resource attributes to filter the target system records. Table 3-2 lists the filter syntax that you can use and the corresponding description and sample values.
Note:
Filters with wildcard characters are not supported.
Table 3-2 Keywords and Syntax for the Filter Attribute
| Filter Syntax | Description |
|---|---|
|
String Filters |
|
|
startsWith('ATTRIBUTE_NAME','PREFIX') |
Records whose attribute value starts with the specified prefix are reconciled. Example: In this example, all records whose userPrincipalName begins with 'John' are reconciled. |
|
endsWith('ATTRIBUTE_NAME','SUFFIX') |
Records whose attribute value ends with the specified suffix are reconciled. Example: In this example, all records whose last name ends with 'Doe' are reconciled. |
|
contains('ATTRIBUTE_NAME','STRING') |
Records where the specified string is contained in the attribute's value are reconciled. Example: In this example, all records whose display name contains 'Smith' are reconciled. |
|
containsAllValues('ATTRIBUTE_NAME',['STRING1','STRING2', . . . ,'STRINGn']) |
Records that contain all the specified strings for a given attribute are reconciled. Example: In this example, all records whose objectClass contains both "top" and "person" are reconciled. |
|
Equality and Inequality Filters |
|
|
equalTo('ATTRIBUTE_NAME','VALUE') |
Records whose attribute value is equal to the value specified in the syntax are reconciled. Example: In this example, all records whose sAMAccountName is Sales Organization are reconciled. |
|
greaterThan('ATTRIBUTE_NAME','VALUE') |
Records whose attribute value (string or numeric) is greater than (in lexicographical or numerical order) the value specified in the syntax are reconciled. Example 1: In this example, all records whose common name is present after the common name 'bob' in the lexicographical order (or alphabetical order) are reconciled. Example 2: In this example, all records whose employee number is greater than 1000 are reconciled. |
|
greaterThanOrEqualTo('ATTRIBUTE_NAME','VALUE') |
Records whose attribute value (string or number) is lexographically or numerically greater than or equal to the value specified in the syntax are reconciled. Example 1: In this example, all records whose sAMAccountName is equal to 'S' or greater than 'S' in lexicographical order are reconciled. Example 2: In this example, all records whose employee number is greater than or equal to 1000 are reconciled. |
|
lessThan('ATTRIBUTE_NAME','VALUE') |
Records whose attribute value (string or numeric) is less than (in lexicographical or numerical order) the value specified in the syntax are reconciled. Example 1: In this example, all records whose last name is present after the last name 'Smith' in the lexicographical order (or alphabetical order) are reconciled. Example 2: In this example, all records whose employee number is less than 1000 are reconciled. |
|
lessThanOrEqualTo('ATTRIBUTE_NAME','VALUE') |
Records whose attribute value (string or numeric) is lexographically or numerically less than or equal to the value specified in the syntax are reconciled. Example 1: In this example, all records whose sAMAccountName is equal to 'A' or less than 'A' in lexicographical order are reconciled. Example 2: In this example, all records whose employee number is less than or equal to 1000 are reconciled. |
|
Complex Filters |
|
|
<FILTER1> & <FILTER2> |
Records that satisfy conditions in both filter1 and filter2 are reconciled. In this syntax, the logical operator & (ampersand symbol) is used to combine both filters. Example: In this example, all records whose common name starts with John and last name ends with Doe are reconciled. |
|
<FILTER1> | <FILTER2> |
Records that satisfy either the condition in filter1 or filter2 are reconciled. In this syntax, the logical operator | (vertical bar) is used to combine both filters. Example: In this example, all records that contain 'Andy' in the sAMAccount Name attribute or records that contain 'Brown' in the last name are reconciled. |
|
not(<FILTER>) |
Records that do not satisfy the given filter condition are reconciled. Example: In this example, all records that does not contain the common name 'Mark' are reconciled. |
You can perform limited reconciliation by using the Search Base parameter of the reconciliation job.
By specifying a value for the Search Base parameter, you can limit the container from which the user, group, or organization records must be reconciled. This is the starting point for the search in the hierarchial structure for objects in Microsoft Active Directory.
This section discusses the Batch Size, Batch Start, Sort By, and Sort Direction attributes of the scheduled jobs for target resource reconciliation (Active Directory User Target Recon) and trusted source reconciliation (Active Directory User Trusted Recon).
By default, all target system records that are added or modified after the last reconciliation run are reconciled during the current reconciliation run. Depending on the number of records to be reconciled, this process may require a large amount of time. In addition, if the connection breaks during reconciliation, then the process would take longer to complete. You can configure batched reconciliation to avoid such problems.
To configure batched reconciliation, specify values for the following attributes:
Batch Size: Use this attribute to specify the number of records that must be included in each batch.
Batch Start: Use this attribute to specify the record number from which batched reconciliation must begin.
Number of Batches: Use this attribute to specify the total number of batches that must be reconciled. The default value of this attribute is All. If you do not want to implement batched reconciliation, then accept the default value. When you accept the default value, the values of the Batch Size, Batch Start, Sort By, and Sort Direction attributes are ignored.
Sort By: Use this attribute to specify the name of the target system field by which the records in a batch must be sorted.
Sort Direction: Use this attribute to specify the whether records being fetched must be sorted in ascending or descending order. The value of this attribute can be either asc or desc.
If batched reconciliation fails, then you only need to rerun the scheduled task without changing the values of the task attributes.
After completing batched reconciliation, if you want to perform incremental reconciliation, then specify the value of the highestCommittedUSN attribute (see Step 3 of Preupgrade Steps) as the value of the Latest Token attribute. From the next reconciliation run onward, the reconciliation engine automatically enters a value for the Latest Token attribute.
Note:
Sorting large number of records on the target system fails during batched reconciliation. Therefore, it is recommended that you use the PageSize entry of the Lookup.Configuration.ActiveDirectory or Lookup.Configuration.ActiveDirectory.Trusted lookup definitions to tune fetching of records from the target system.
When you run the Connector Installer, the following reconciliation scheduled tasks are automatically created in Oracle Identity Manager:
Depending on whether you want to implement trusted source or target resource reconciliation, you must specify values for the attributes of one of the following user reconciliation scheduled jobs:
See Active Directory User Target Recon to implement target resource reconciliation.
See Active Directory User Trusted Recon to implement trusted source reconciliation.
This scheduled job is used to reconcile user data in the target resource (account management) mode of the connector. Table 3-3 describes the attributes of this scheduled job.
Table 3-3 Attributes of the Scheduled Job for Reconciliation of User Data from a Target Resource
| Attribute | Description |
|---|---|
|
Batch Size |
Enter the number of records that must be included in each batch fetched from the target system. Default value: This attribute is used in conjunction with the Batch Start, Number of Batches, Sort By, and Sort Direction attributes. All these attributes are discussed in Batched Reconciliation. |
|
Batch Start |
Enter the number of the target system record from which a batched reconciliation run must begin. Default value: This attribute is used in conjunction with the Batch Size, Number of Batches, Sort By, and Sort Direction attributes. All these attributes are discussed in Batched Reconciliation. |
|
Filter |
Expression for filtering records. See Performing Limited Reconciliation By Using Filters for more information. Default value: None |
|
Incremental Recon Attribute |
Enter the name of the target system attribute that holds last update-related number, non-decreasing value. For example, The value in this attribute is used during incremental reconciliation to determine the newest or most youngest record reconciled from the target system. Default value: Note: For example, if you want to change the Incremental Recon attribute to whenChanged while using the latest Active Directory Connector 11.1.1.6.0W patch 31377499 or later, then:
|
|
IT Resource Name |
Name of the IT resource instance that the connector must use to reconcile data. Sample value: |
|
Latest Token |
This attribute holds the value of the configured incremental recon attribute (for example: uSNChanged or whenChanged) of a domain controller that is used for reconciliation. Note: The reconciliation engine automatically enters a value for this attribute. If you manually specify a value for this attribute, then only user accounts whose incremental recon attribute value is greater than the Latest Token attribute value are reconciled. |
|
Number of Batches |
Enter the number of batches that must be reconciled. Default value: Sample value This attribute is used in conjunction with the Batch Size, Batch Start, Sort By, and Sort Direction attributes. All these attributes are discussed in Batched Reconciliation. If you accept the default value ( |
|
Object Type |
This attribute holds the type of object you want to reconcile. Default value: Note: If you configure the connector to provision users to a custom class (for example, InetOrgPerson) then enter the value of the object class here. |
|
Resource Object Name |
Enter the name of the resource object against which reconciliation runs must be performed. Default value: |
|
Scheduled Task Name |
This attribute holds the name of the scheduled task. Default value: |
|
Search Base |
Enter the container in which the search for user records must be performed during reconciliation. Sample Value: Note: If you do not specify a value for this attribute, then the value specified as the value of the Container parameter of the IT resource is used as the value of this attribute. |
|
Search Scope |
Enter Enter Note: If you want to enter onelevel, then remember that you must not include a space between "one" and "level." Default value: |
|
Sort By |
Enter the name of the target system field by which the records in a batch must be sorted. Default value: Note: If you are using AD LDS as the target system, then change the default value of this attribute to some other attribute (for example, |
|
Sort Direction |
Use this attribute to specify whether records being fetched must be sorted in ascending or descending order. The value of this attribute can be either Default value: |
This scheduled job is used to reconcile user data in the trusted resource (identity management) mode of the connector. Table 3-4 describes the attributes of this scheduled job.
Table 3-4 Attributes of the Scheduled Job for Reconciliation of User Data from a Trusted Source
| Attribute | Description |
|---|---|
|
Batch Size |
Enter the number of records that must be included in each batch fetched from the target system. Default value: This attribute is used in conjunction with the Batch Start, Number of Batches, Sort By, and Sort Direction attributes. All these attributes are discussed in Batched Reconciliation. |
|
Batch Start |
Enter the number of the target system record from which a batched reconciliation run must begin. Default value: This attribute is used in conjunction with the Batch Size, Number of Batches, Sort By, and Sort Direction attributes. All these attributes are discussed in Batched Reconciliation. |
|
Filter |
Expression for filtering records. See Performing Limited Reconciliation By Using Filters for more information. Default value: None |
|
Incremental Recon Attribute |
Enter the name of the target system attribute that holds last update-related number, non-decreasing value. For example, The value in this attribute is used during incremental reconciliation to determine the newest or most youngest record reconciled from the target system. Default value: Note: For example, if you want to change the Incremental Recon attribute to whenChanged while using the latest Active Directory Connector 11.1.1.6.0W patch 31377499 or later, then:
|
|
IT Resource Name |
Enter the name of the IT resource instance that you create for trusted source reconciliation in Configuring the IT Resource for Microsoft AD and AD LDS. Sample value: |
|
Latest Token |
This attribute holds the value of the configured incremental recon attribute (for example: uSNChanged or whenChanged) of a domain controller that is used for reconciliation. Note: The reconciliation engine automatically enters a value for this attribute. If you manually specify a value for this attribute, then only user accounts whose incremental recon attribute value is greater than the Latest Token attribute value are reconciled. |
|
Maintain Hierarchy |
Enter Default value: Note: If you set this attribute to |
|
Manager Id |
Enter the decode value of the User Id Code Key in the lookup definition that holds mappings between resource object fields and target system attributes for trusted source reconciliation. If you are using Microsoft Active Directory as the target system, then the default value of this attribute is If you are using Microsoft AD LDS as the target system, then set the value of this attribute to Default value: |
|
Number of Batches |
Enter the number of batches that must be reconciled. Default value: Sample value This attribute is used in conjunction with the Batch Size, Batch Start, Sort By, and Sort Direction attributes. All these attributes are discussed in Batched Reconciliation. If you accept the default value ( |
|
Object Type |
This attribute holds the type of object you want to reconcile. Default value: Note: If you configure the connector to provision users to a custom class (for example, InetOrgPerson) then enter the value of the object class here. |
|
OIM Employee Type |
Enter the employee type that must be set for OIM Users created through reconciliation. Default value: |
|
OIM Organization Name |
Enter the name of the Oracle Identity Manager organization in which reconciled users must be created. The OIM Organization attribute is taken into account only if you set the MaintainHierarchy attribute to Default value: |
|
OIM User Type |
Enter the role that must be set for OIM Users created through reconciliation. You must select one of the following values:
Default value: |
|
Resource Object Name |
Enter the name of the resource object against which reconciliation runs must be performed. Default value: |
|
Scheduled Task Name |
This attribute holds the name of the scheduled task. Default value: |
|
Search Base |
Enter the container in which the search for user records must be performed during reconciliation. Sample Value: Note: If you do not specify a value for this attribute, then the value specified as the value of the Container parameter of the IT resource is used as the value of this attribute. |
|
Search Scope |
Enter Enter Note: If you want to enter onelevel, then remember that you must not include a space between "one" and "level." Default value: |
|
Sort By |
Enter the name of the target system field by which the records in a batch must be sorted. Default value: Note: If you are using AD LDS as the target system, then change the default value of this attribute to some other attribute (for example, |
|
Sort Direction |
Use this attribute to specify whether records being fetched must be sorted in ascending or descending order. The value of this attribute can be either Default value: |
Depending on whether you want to implement trusted source or target resource delete reconciliation, you must specify values for the attributes of one of the following scheduled jobs:
Note:
To ensure that the target system user account that you create for performing connector operations has access to the Deleted Objects container in the target system, perform the procedure described in Assigning Permissions to Perform Delete User Reconciliation Runs.
Active Directory User Target Delete Recon
This scheduled job is used to reconcile data about deleted users in the target resource (account management) mode of the connector. During a reconciliation run, for each deleted user account on the target system, the Active Directory resource is revoked for the corresponding OIM User.
Active Directory User Trusted Delete Recon
This scheduled job is used to reconcile data about deleted users in the trusted source (identity management) mode of the connector. During a reconciliation run, for each deleted target system user account, the corresponding OIM User is deleted.
Table 3-5 describes the attributes of both scheduled jobs.
Table 3-5 Attributes of the Scheduled Jobs for Delete User Reconciliation
| Attribute | Description |
|---|---|
|
Delete Recon |
Specifies whether delete reconciliation must be performed. Default value: Note: Do not change the value of this attribute. |
|
IT Resource Name |
Name of the IT resource instance that the connector must use to reconcile user data. The default value of this attribute in the Active Directory User Target Delete Recon scheduled job is The default value of this attribute in the Active Directory User Trusted Delete Recon scheduled job is none. Note: If you have configured your target system as trusted source, then ensure that you specify the name of the IT resource in which the Configuration Lookup parameter is set to |
|
Object Type |
This attribute holds the type of object you want to reconcile. Default value: |
|
Resource Object Name |
Enter the name of the resource object against which reconciliation runs must be performed. The default value of this attribute in the Active Directory User Target Delete Recon scheduled job is The default value of this attribute in the Active Directory User Trusted Delete Recon scheduled job is |
|
Scheduled Task Name |
This attribute holds the name of the scheduled task. The default value of this attribute in the Active Directory User Target Delete Recon scheduled job is The default value of this attribute in the Active Directory User Trusted Delete Recon scheduled job is |
|
Sync Token |
This attribute must be left blank when you run delete reconciliation for the first time. This ensures that data about all records that are deleted from the target system are fetched into Oracle Identity Manager. After the first delete reconciliation run, the connector automatically enters a value for this attribute in an XML serialized format. From the next reconciliation run onward, only data about records that are deleted since the last reconciliation run ended are fetched into Oracle Identity Manager. This attribute stores values in the following format:
A value of A value of |
Depending on your requirement, you must specify values for the attributes of one of the following scheduled jobs:
Active Directory Group Recon
This scheduled job is used to reconcile group data from the target system.
Active Directory Organization Recon
This scheduled job is used to reconcile organization data from the target system.
See Also:
The following sections for information about running group and organization reconciliation:
Table 3-6 describes the attributes of both scheduled jobs.
Table 3-6 Attributes of the Scheduled Task for Reconciliation of Group and Organization Data
| Attribute | Description |
|---|---|
|
Filter |
Expression for filtering records. See Performing Limited Reconciliation By Using Filters for more information. Default value: Note: While creating filters, ensure to use attributes specific to Groups or Organizational Units. |
|
Incremental Recon Attribute |
Enter the name of the target system attribute that holds last update-related number, non-decreasing value. For example, The value in this attribute is used during incremental reconciliation to determine the newest or most youngest record reconciled from the target system. Default value: Note: Do not change the value of this attribute. |
|
IT Resource Name |
Enter the name of the IT resource for the target system installation from which you want to reconcile group or organization data. Default value: |
|
Latest Token |
This attribute holds the value of the uSNChanged attribute of a domain controller that is used for reconciliation. Sample value: Note: The reconciliation engine automatically enters a value for this attribute. It is recommended that you do not change the value of this attribute. If you manually specify a value for this attribute, then only groups or organizational units whose uSNChanged value is greater than the Latest Token attribute value are reconciled. |
|
Object Type |
Type of object to be reconciled. The default value of this attribute in the Active Directory Group Recon scheduled job is The default value of this attribute in the Active Directory Organization Recon scheduled job is |
|
Organization Name |
Enter the name of the organization to which all groups fetched from the target system is linked. See Configuring and Running Group Reconciliation for more information on the usage of this attribute. Note: This attribute is present only in the Active Directory Group Recon scheduled job. |
|
Organization Type |
Type of organization to be created in Oracle Identity Manager. Default value: Note: This attribute is present only in the Active Directory Group Recon scheduled job. |
|
Resource Object Name |
Name of the resource object that is used for reconciliation. The default value of this attribute in the Active Directory Group Recon scheduled job is The default value of this attribute in the Active Directory Organization Recon scheduled job is |
|
Scheduled Task Name |
Name of the scheduled task used for reconciliation. The default value of this attribute in the Active Directory Group Recon scheduled job is The default value of this attribute in the Active Directory Organization Recon scheduled job is |
|
Search Base |
Enter the container in which the search for group or organization records must be performed during reconciliation. Sample Value: Note: If you do not specify a value for this attribute, then the value specified as the value of the Container parameter of the IT resource is used as the value of this attribute. |
|
Search Scope |
Enter Enter Note: If you want to enter onelevel, then remember that you must not include a space between "one" and "level." Default value: |
The Active Directory Group Delete Recon is used to reconcile data about deleted groups.
Table 3-7 describes the attributes of this scheduled job.
Table 3-7 Attributes of the Active Directory Group Delete Recon Scheduled Job
| Attribute | Description |
|---|---|
|
Delete Recon |
Specifies whether delete reconciliation must be performed. Default value: Note: Do not change the value of this attribute. |
|
IT Resource Name |
Name of the IT resource instance that the connector must use to reconcile group data. Default value: |
|
Object Type |
This attribute holds the type of object you want to reconcile. Default value: |
|
Resource Object Name |
Enter the name of the resource object against which reconciliation runs must be performed. Default value: |
|
Scheduled Task Name |
This attribute holds the name of the scheduled task. Default value: |
|
Sync Token |
This attribute must be left blank when you run delete reconciliation for the first time. This ensures that data about all records that are deleted from the target system are fetched into Oracle Identity Manager. After the first delete reconciliation run, the connector automatically enters a value for this attribute in an XML serialized format. From the next reconciliation run onward, only data about records that are deleted since the last reconciliation run ended are fetched into Oracle Identity Manager. This attribute stores values in the following format:
A value of A value of |
|
Organization Name |
Enter the name of the organization to which data about all deleted groups fetched from the target system is linked. There are two scenarios in which group reconciliation is performed. These scenarios are described in Configuring and Running Group Reconciliation. If you have configured the connector to perform group reconciliation in scenario 1, then you need not specify a value for this attribute. In case you specify a value, it is ignored by the connector. If you have configured the connector to perform group reconciliation in scenario 2, then enter the same organization name specified for the Organization Name attribute of the Active Directory Group Recon scheduled job. |
There are two scenarios in which group reconciliation can be performed.
Depending on the scenario in which you want to perform group reconciliation, perform one of the following procedures:
See Reconciling Target System Groups into Individual Organizations to reconcile each target system group into an organization of its own.
See Reconciling Target System Groups a Single Organization to reconcile each target system group into a single organization.
Create an organizational unit in Oracle Identity Manager with the name of the group (available in the target system), and then reconcile groups to this newly created organizational unit. In other words, suppose a scenario in which you want every target system group to be reconciled into an organization of its own.
To perform group reconciliation in this scenario:
This section discusses the procedure to perform group reconciliation when all groups available on the target system must be reconciled under the same organizational unit in Oracle Identity Manager. In other words, suppose a scenario in which you want all target system groups to be reconciled into a single organization.
To perform group reconciliation in this scenario:
You can configure and run the scheduled job for organization reconciliation.
The following is the procedure to run the scheduled job for organization reconciliation:
Note:
OIM created Organizations do not relate to the OU objects on the Directory Resources of Microsoft Active Directory. The connector does not support the creation of any OU objects in OIM which can then be provisioned to Microsoft Active Directory. Instead, OUs can be created directly on the Directory Services of Microsoft Active Directory.
In addition, as a best practice, ensure that all newly created OUs and other objects are fetched into OIM from the target system by performing a trusted resource reconciliation run.
Configure scheduled jobs to perform reconciliation runs that check for new information on your target system periodically and replicates the data in Oracle Identity Manager.
You can apply this procedure to configure the scheduled jobs for lookup field synchronization and reconciliation.
To configure a scheduled job:
If you are using Oracle Identity Manager release 11.1.1:
Log in to the Administrative and User Console.
On the Welcome to Oracle Identity Manager Self Service page, click Advanced in the upper-right corner of the page.
On the Welcome to Oracle Identity Manager Advanced Administration page, in the System Management region, click Search Scheduled Jobs.
If you are using Oracle Identity Manager release 11.1.2.x:
Log in to Oracle Identity System Administration.
In the left pane, under System Management, click Scheduler.
Search for and open the scheduled task as follows:
On the left pane, in the Search field, enter the name of the scheduled job as the search criterion. Alternatively, you can click Advanced Search and specify the search criterion.
In the search results table on the left pane, click the scheduled job in the Job Name column.
On the Job Details tab, you can modify the parameters of the scheduled task:
Retries: Enter an integer value in this field. This number represents the number of times the scheduler tries to start the job before assigning the Stopped status to the job.
Schedule Type: Depending on the frequency at which you want the job to run, select the appropriate schedule type.
Note:
See Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for detailed information about schedule types.
In addition to modifying the job details, you can enable or disable a job.
On the Job Details tab, in the Parameters region, specify values for the attributes of the scheduled task.
Note:
Attribute values are predefined in the connector XML file that you import. Specify values only for those attributes that you want to change.
Values (either default or user-defined) must be assigned to all the attributes. If even a single attribute value is left empty, then reconciliation is not performed.
See Reconciliation Scheduled Jobs for the list of scheduled tasks and their attributes.
Click Apply to save the changes.
Note:
The Stop Execution option is available in the Administrative and User Console. You can use the Scheduler Status page to either start, stop, or reinitialize the scheduler.
Actions are scripts that you can configure to run before or after the create, update, or delete an account provisioning operations.
For example, you can configure a script to run before every user creation. Similarly, you can run custom PowerShell scripts before or after creating, updating, or deleting a mailbox.
The following are topics pertaining to action scripts:
The following is a summary of the procedure to configure action scripts:
On the computer hosting the connector server, create the custom script (for example, PowerShell) in a directory. This script should be self-sufficient, that is, it should be able to create, maintain, and delete sessions with the target AD server and complete all actions against it.
On the computer hosting Oracle Identity Manager, create a batch (.bat) file. This batch file runs on the computer hosting the connector server, which in turn calls the custom script (for example, PowerShell) available on the connector server host computer. Even if Oracle Identity Manager is installed on a UNIX-based computer, create a batch file.
For a custom PowerShell script, the batch file runs the custom PowerShell script using the Powershell.exe program. For more information on Powershell.exe, see http://technet.microsoft.com/en-us/library/hh847736.aspx.
Add entries to the Lookup.ActiveDirectory.UM.Configuration lookup definition.
Table 3-8 describes the entries to be added to the Lookup.ActiveDirectory.UM.Configuration lookup definition for running actions scripts.
Table 3-8 Lookup Entries for Running Action Scripts
| Code Key | Decode |
|---|---|
|
TIMING Action Language |
Scripting language of the script you want to run. For a custom shell script, enter |
|
TIMING Action File |
Full path and name to the file containing the script to be run. Note that the file containing the script must be located on the computer on which Oracle Identity Manager is running. |
|
TIMING Action Target |
Context in which the script must be run. Enter |
In the preceding table, TIMING defines when an action must be performed. An action can be invoked either before or after a create, update, or delete provisioning operation. Therefore, TIMING can be replaced with any of the following values:
Before Create
Before Update
Before Delete
After Create
After Update
After Delete
All the entries in Table 3-8 define an action together. Therefore, to configure action scripts, all the entries must be defined. Otherwise, no action is performed.
As an example, the following procedure describes the steps to run a custom PowerShell script before a create operation:
Note that you can pass process form fields to scripts that call the before or after action scripts. These process form fields must be present in the Lookup.ActiveDirectory.UM.ProvAttrMap lookup definition and be mapped to a corresponding target system attribute. For example, you can pass the First Name process form field (present in the Lookup.ActiveDirectory.UM.ProvAttrMap lookup definition) to an action script by specifying "givenName," which is the name of the corresponding attribute in the target system.
Note:
Process form fields marked as IGNORE are not sent to the connector.
The following is an example procedure for running a script before a create provisioning operation:
You can also configure actions by using Visual Basic scripts. Although Visual Basic scripts are not directly supported, a Visual Basic script can be called using a shell script.
The following is an example procedure for running actions using Visual Basic scripts that consumes data dynamically from the process form. This is an example procedure for an After Create action, which requires creating a user in an organizational unit in addition to the one in which the user is provisioned to.
The following are important notes on running actions scripts:
Any errors encountered while running action scripts are ignored and are not propagated to Oracle Identity Manager.
During create operations, all attributes part of process form are available to the script.
During update operations, only the attribute that is being updated is available to the script.
If other attributes are also required, then a new adapter calling ICProvisioningManager# updateAttributeValues(String objectType, String[] labels) must be created and used. During adapter mapping in process task, add the form field labels of the dependent attributes.
During delete operations, only the __UID__ (GUID) attribute is available to the script.
The following are the guidelines that you must apply or be aware of while configuring action scripts:
Your script file can contain scripts that include attributes present in the decode column of any of the following lookup definitions:
Lookup.ActiveDirectory.UM.ProvAttrMap
Lookup.ActiveDirectory.GM.ProvAttrMap
Lookup.ActiveDirectory.OM.ProvAttrMap
All field names used in the scripts must be enclosed within %%.
You can call any VB script from a shell and pass the process form fields.
You cannot include the Password field in the script. This is because password is stored as a guarded string. Therefore, we do not get the exact password when we fetch values for the Password field.
Addition of child table attributes belongs to the 'Update' category and not 'Create.'
Provisioning a resource for an OIM user involves using Oracle Identity Manager to create a Microsoft Active Directory account for the user.
Information pertaining to performing provisioning operations is discussed in the following topics:
When you install the connector on Oracle Identity Manager, the direct provisioning feature is automatically enabled. This means that the process form is enabled when you install the connector.
If you configure the connector for request-based provisioning, then the process form is suppressed and the object form is displayed. In other words, direct provisioning is disabled when you configure the connector for request-based provisioning. If you want to revert to direct provisioning, then perform the steps described in Switching Between Request-Based Provisioning and Direct Provisioning.
This following are types of provisioning operations:
Direct provisioning
Request-based provisioning
See Also:
Manually Completing a Task in Performing Self Service Tasks with Oracle Identity Manager for information about the types of provisioning
To provision a resource by using the direct provisioning approach:
Log in to the Administrative and User Console.
If you want to first create an OIM User and then provision a target system account, then:
On the Welcome to Identity Administration page, in the Users region, click Create User.
On the user details page, enter values for the OIM User fields, and then click Save. Figure 3-2 shows this page.
If you want to provision a target system account to an existing OIM User, then:
On the Welcome to Identity Administration page, search for the OIM User by selecting Users from the list on the left pane.
From the list of users displayed in the search results, select the OIM User. The user details page is displayed on the right pane.
On the user details page, click the Resources tab.
From the Action menu, select Add Resource. Alternatively, you can click the add resource icon with the plus (+) sign. The Provision Resource to User page is displayed in a new window.
On the Step 1: Select a Resource page, select AD User from the list and then click Continue. Figure 3-3 shows the Step 1: Select a Resource page.
Figure 3-3 Step 1: Select a Resource Page
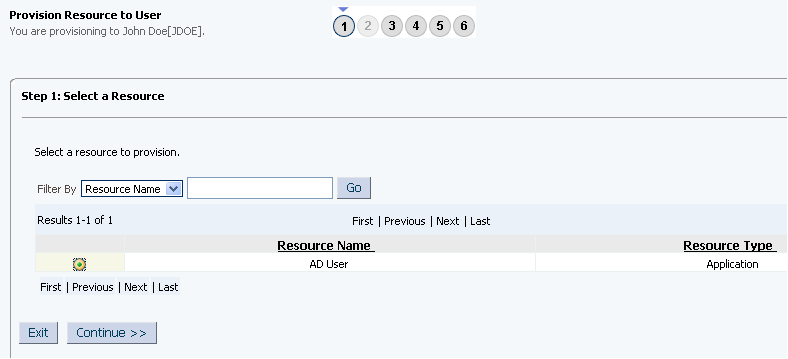
On the Step 2: Verify Resource Selection page, click Continue. Figure 3-4 shows the Step 2: Verify Resource Selection page.
Figure 3-4 Step 2: Verify Resource Selection Page
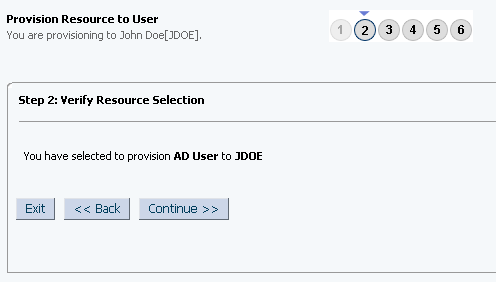
On the Step 5: Provide Process Data for Active Directory Users Form page, enter the details of the account that you want to create on the target system and then click Continue. Figure 3-5 shows the user details added.
Figure 3-5 Step 5: Provide Process Data for AD User Form Page
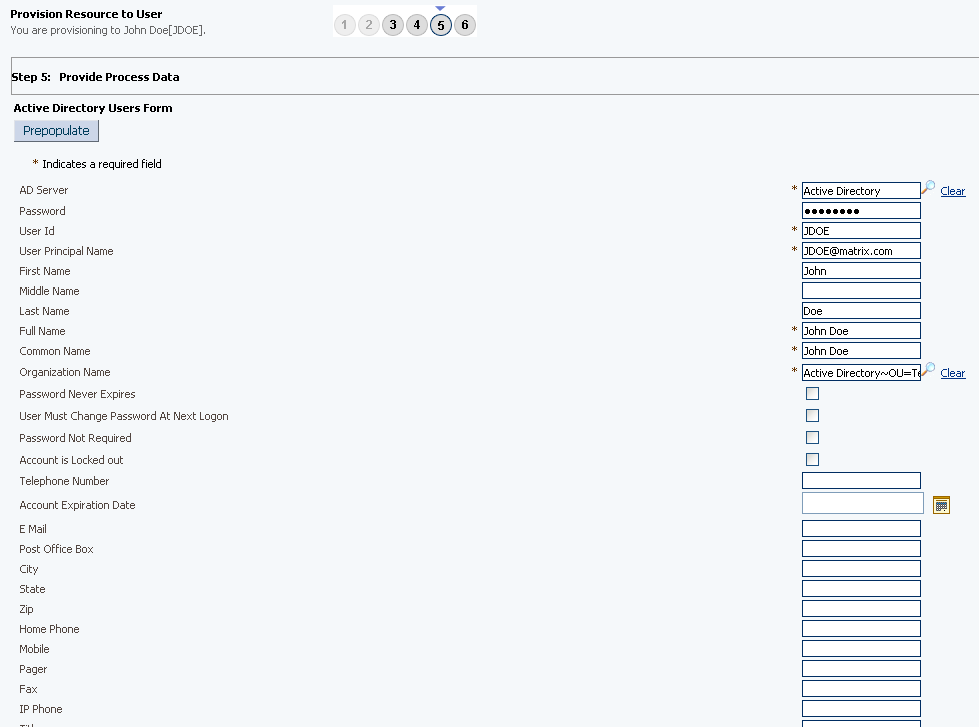
If required, on the Step 5: Provide Process Data for Assigned Groups Form page, search for and select a group for the user on the target system and then click Continue. Figure 3-6 shows this page.
Figure 3-6 Step 5: Provide Process Data for Assigned Groups Form Page
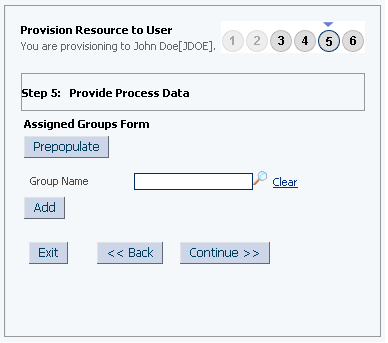
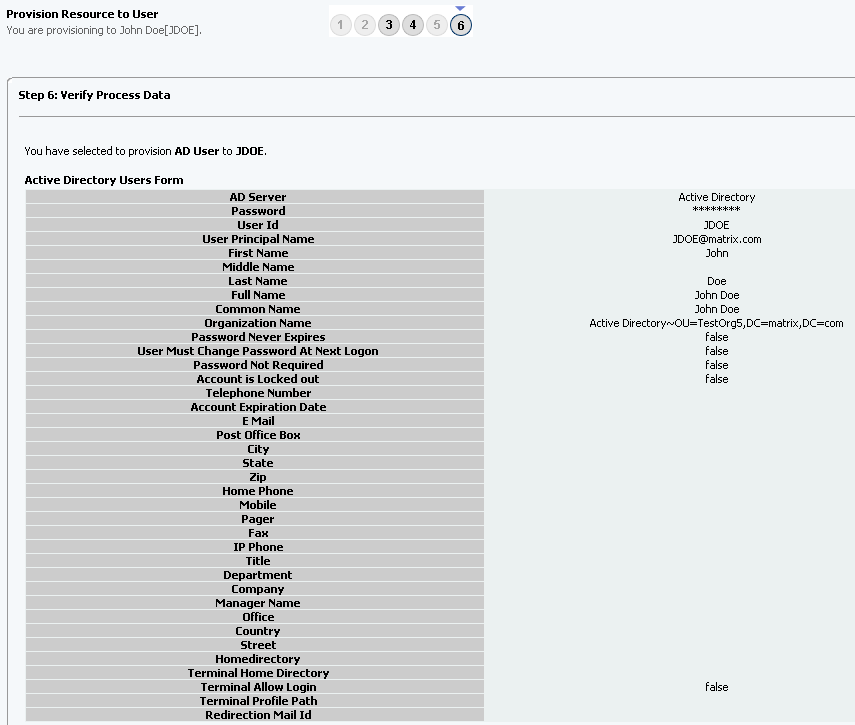
On the Step 6: Verify Process Data page, verify the data that you have provided and then click Continue. Figure 3-7 shows Step 6: Verify Process Data page.
Figure 3-7 Step 6: Verify Process Data Page
Close the window displaying the "Provisioning has been initiated" message.
On the Resources tab, click Refresh to view the newly provisioned resource.
A request-based provisioning operation involves both end users and approvers. Typically, these approvers are in the management chain of the requesters. The following sections discuss the steps to be performed by end users and approvers during a request-based provisioning operation:
Note:
The procedures described in these sections are built on an example in which the end user raises or creates a request for provisioning a target system account. This request is then approved by the approver.
The following steps are performed by the end user in a request-based provisioning operation:
If you have configured the connector for request-based provisioning, you can always switch to direct provisioning. Similarly, you can always switch back to request-based provisioning any time. This section discusses the following topics:
Note:
It is assumed that you have performed the procedure described in Configuring Oracle Identity Manager for Request-Based Provisioning.
If you want to switch from request-based provisioning to direct provisioning, then:
Log in to the Design Console.
Disable the Auto Save Form feature as follows:
Expand Process Management, and then double-click Process Definition.
Search for and open the AD User process definition.
Deselect the Auto Save Form check box.
Click the Save icon.
If the Self Request Allowed feature is enabled, then:
Expand Resource Management, and then double-click Resource Objects.
Search for and open the AD User resource object.
Deselect the Self Request Allowed check box.
Click the Save icon.
If you want to switch from direct provisioning back to request-based provisioning, then:
Log in to the Design Console.
Enable the Auto Save Form feature as follows:
Expand Process Management, and then double-click Process Definition.
Search for and open the AD User process definition.
Select the Auto Save Form check box.
Click the Save icon.
If you want to enable end users to raise requests for themselves, then:
Expand Resource Management, and then double-click Resource Objects.
Search for and open the AD User resource object.
Select the Self Request Allowed check box.
Click the Save icon.
Provisioning a resource for an OIM User involves using Oracle Identity Manager to create a Microsoft Active Directory account for the user.
To perform provisioning operations in Oracle Identity Manager release 11.1.2 or later:
Log in to Oracle Identity Administrative and User console.
Create a user. See Managing Users in Performing Self Service Tasks with Oracle Identity Manager for more information about creating a user.
On the Account tab, click Request Accounts.
In the Catalog page, search for and add to cart the application instance created in Creating an Application Instance, and then click Checkout.
Specify value for fields in the application form and then click Ready to Submit.
Click Submit.
If you want to provision entitlements, then:
On the Entitlements tab, click Request Entitlements.
In the Catalog page, search for and add to cart the entitlement, and then click Checkout.
Click Submit.
Uninstalling the connector deletes all the account related data associated with resource objects of the connector.
If you want to uninstall the connector for any reason, see Uninstalling Connectors in Administering Oracle Identity Manager.
Note:
The connector cannot be uninstalled if a valid access policy is present in Oracle Identity Manager. As a workaround, create a dummy resource type by using the design console. Remove the dependent access policy by directing it to a dummy resource type and then remove the dependency from the resource type that must be deleted.
Uninstalling the connector removes only those IT resource definitions (and its IT resources) that are attached with the process form. However, the IT resource of the Connector Server IT Resource Type Definition is not removed for Oracle Identity Manager.