Home | Book List | Contents | Contact Us |
Go to main content
|
|
The PeopleSoft User Management connector helps you to manage PeopleTools-based PSOPRDEFN user profile records in PeopleSoft applications including Role and Permission List assignments to these records.
This chapter contains the following sections:
Oracle Identity Manager automates access rights management, security, and provisioning of resources to various target systems. Oracle Identity Manager Connectors are used to integrate Oracle Identity Manager with target applications. This guide discusses the connector that enables you to use PeopleSoft Enterprise Applications as a managed (target) source of user profile data for Oracle Identity Manager.
Note:
In this guide, the term Oracle Identity Manager server refers to the computer on which Oracle Identity Manager is installed.
At some places in this guide, PeopleSoft Enterprise Applications has been referred to as the target system.
The PeopleSoft User Management connector helps you to manage PeopleTools-based PSOPRDEFN user profile records in PeopleSoft applications including Role and Permission List assignments to these records. This is done through target resource reconciliation and provisioning.
In the target resource configuration, information about user accounts created or modified directly on the target system can be reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
See Also:
Installing Connectors in Oracle Fusion Middleware Administering Oracle Identity Manager for detailed information about connector deployment configurations
connector.htm#GUID-C78A0044-2A98-4C79-8B7E-8218CB6336AE__CEGGBDFE lists the components certified for use with the connector.
Table 1-1 Certified Components
| Item | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Governance or Oracle Identity Manager:
|
|
Target systems |
The target system can be any one of the following:
Note: If you are using PeopleTools 8.54, full reconciliation operation may not work as expected. Apply PeopleSoft Patch 21109998 using the following URL for this operation to work successfully: |
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 Update 24 or later, or JRockit 1.6 or later If you are using PeopleTools 8.53, PeopleTools 8.54, or PeopleTools 8.55, see JDK Requirement for PeopleTools 8.53, PeopleTools 8.54, and PeopleTools 8.55, for information related to JDK requirement. If you are using PeopleTools 8.56 or PeopleTools 8.57, see JDK Requirement for PeopleTools 8.56 and PeopleTools 8.57, for information related to JDK requirement. |
|
Other Software |
Ensure that the following components are installed and configured in the target system environment:
The following standard PeopleSoft messages are available:
|
|
SoD engine |
If you want to enable and use the Segregation of Duties (SoD) feature of Oracle Identity Manager release 11.1.1.5 BP01 with this target system, then install Oracle Applications Access Controls Governor (OAACG) release 8.6. See SoD Validation of Entitlement Provisioning for more information about the SoD feature. |
Before you deploy the connector, you might want to determine the version of PeopleTools and the target system you are using to check whether you are using the combination supported by this connector.
Depending on the Oracle Identity Manager version that you are using, you must deploy and use one of the following connectors:
If you are using an Oracle Identity Manager release 9.1.0.2 BP05 or later and earlier than Oracle Identity Manager 11g Release 1 BP06 (11.1.1.5.6), then you must use the 9.1.1 version of this connector.
If you are using Oracle Identity Manager 11g Release 1 BP06 (11.1.1.5.6) or later, Oracle Identity Manager 11g Release 2 BP04 (11.1.2.0.4) or later, or Oracle Identity Manager 11g Release 2 PS3 (11.1.2.3.0), then use the latest 11.1.1.x version of this connector.
The connector supports the following languages:
Arabic
Chinese Simplified
Chinese Traditional
Danish
English
French
German
Italian
Japanese
Korean
Portuguese (Brazilian)
Spanish
The architecture of the connector can be explained in terms of the connector operations it supports.
This section contains the following topics:
connector.htm#GUID-88938A47-3BF9-44CE-A25E-88C14EB8E39B__BABJDJBC shows the architecture of the connector.
The target system is configured as a trusted source of identity data for Oracle Identity Manager. In other words, identity data that is created and updated on the target system is fetched into Oracle Identity Manager and used to create and update OIM Users.
The connector is implemented using the Identity Connector Framework (ICF). The ICF provides a container that separates the connector bundle from the application. The ICF also provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering.
For more information about the ICF, see Understanding the Identity Connector Framework in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager.
PeopleSoft Enterprise Application is configured as a target resource of Oracle Identity Manager. Through reconciliation, account data that is created and updated on the target system is fetched into Oracle Identity Manager and stored against the corresponding OIM Users.
Standard PeopleSoft XML files and messages are the medium of data interchange between PeopleSoft Enterprise Applications and Oracle Identity Manager.
The method by which account data is sent to Oracle Identity Manager depends on the type of reconciliation that you configure as follows:
A lookup reconciliation run fetches the records of Email Types, Currency Codes, Language Codes, Permission Lists, and Roles from the target system. Running PeopleSoft's Application Engine process generates these properties files at a specified location. Lookup reconciliation stores the information from these properties files into Oracle Identity Manager as reference data for subsequent use in provisioning.
You must run lookup reconciliation at periodic intervals to ensure that all the lookup data is reconciled into Oracle Identity Manager. See Performing Lookup Reconciliation for instructions to perform Lookup reconciliation.
Note:
To reconcile all existing target system records into Oracle Identity Manager, you must run full reconciliation the first time you perform a reconciliation run after deploying the connector. This is to ensure that the target system and Oracle Identity Manager contain the same data.
PeopleSoft uses its standard message format USER_PROFILE to send user profile data to external applications such as Oracle Identity Manager. Full reconciliation fetches all of these records from the target system to reconcile records in Oracle Identity Manager. Full reconciliation within Oracle Identity Manager is implemented using the USER_PROFILE XML file that PeopleSoft generates. See Support for Standard PeopleSoft Messages for more information about the message.
Full reconciliation involves the following steps:
See Performing Full Reconciliation for instructions to perform full reconciliation.
Incremental reconciliation involves real-time reconciliation of newly created or modified user data. It is achieved by PeopleSoft standard messages, such as USER_PROFILE and DELETE_USER_PROFILE. See Support for Standard PeopleSoft Messages for more information about these messages. You use incremental reconciliation to reconcile individual data changes after an initial, full reconciliation run has been performed. Incremental reconciliation is performed using PeopleSoft application messaging.
Incremental reconciliation involves the following steps:
See Performing Incremental Reconciliation for instructions to perform incremental reconciliation.
Note:
During connector deployment, the PeopleSoft listener is deployed as an EAR file.
PeopleSoft Enterprise Application is configured as a target resource of Oracle Identity Manager. Through provisioning operations performed on Oracle Identity Manager, accounts are created and updated on the target system for OIM Users.
During a provisioning operation, the adapters pass on to PeopleSoft Enterprise Applications user data that are created, modified or deleted in Oracle Identity Manager.
The connector, by default, supports Customer and Vendor ID types in addition to the Employee ID type. The connector is enhanced to support new ID types depending on the PeopleSoft application module being provisioned. The new ID type can then be linked to a user profile for provisioning. See Adding New ID Types for more information.
See SoD Validation of Entitlement Provisioning for information about the process followed for provisioning of role entitlements in an SoD-enabled environment.
The PeopleSoft Internet Architecture is flexible; this means that you have many options to consider for deploying PeopleSoft across your enterprise. The following section describes a split-deployment scenario where the Jolt listener resides on a different computer than the Integration Broker.
connector.htm#GUID-61297187-A267-4403-AABB-A3251D0D0EA4__CEGIIFCF shows the architecture of the connector that supports a split-deployment scenario.
Figure 1-2 Architecture of the Connector for a Split-Deployment Scenario
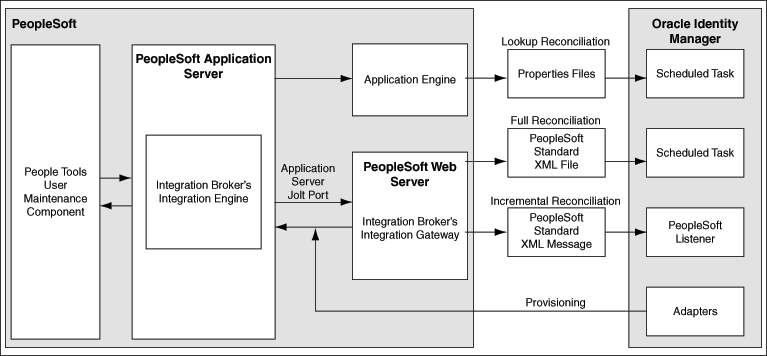
In this configuration:
The following are the features of the connector:
The connector supports reconciliation in two ways:
In a full reconciliation run, all records are fetched from the target system to Oracle Identity Manager in the form of XML files. In incremental reconciliation, records that are added, modified, or deleted are directly sent to the listener deployed on the Oracle Identity Manager host computer. The listener parses the records and sends reconciliation events to Oracle Identity Manager.
PeopleSoft provides standard messages to synchronize user profiles with external applications, such as Oracle Identity Manager. The connector uses these standard PeopleSoft messages that are delivered as part of PeopleSoft installation to achieve full reconciliation and incremental reconciliation. They are listed as follows:
USER_PROFILE
DELETE_USER_PROFILE
The USER_PROFILE message contains information about user accounts that are created or modified. The DELETE_USER_PROFILE message contains information about user accounts that are deleted.
Fetching all the records present in PeopleSoft to Oracle Identity Manager is implemented by running the USER_PROFILE message. Similarly, when a user profile is updated in PeopleSoft, the USER_PROFILE message is triggered. Oracle Identity Manager uses this message for incremental reconciliation. Similarly, when a user profile is deleted in PeopleSoft, the DELETE_USER_PROFILE message is triggered from PeopleSoft to delete the corresponding provisioned resource in Oracle Identity Manager. The DELETE_USER_PROFILE is supported through incremental reconciliation.
To distinguish between the full and incremental reconciliation USER_PROFILE XML messages, you must identify the number of transaction nodes in the message. In case of full reconciliation, the USER_PROFILE message has multiple transaction nodes. But, in incremental reconciliation, the USER_PROFILE message has a single transaction node for a particular user.
Standard messages provided by PeopleSoft are asynchronous. In other words, if a message is not delivered successfully, the PeopleSoft Integration Broker marks that message as not delivered. The message can then be retried manually.
If the connector is not able to process the message successfully, it sends an error code and PeopleSoft Integration Broker marks that message as Failed. A message marked as Failed can be resent to the listener. See Resending Messages That Are Not Received by the PeopleSoft Listener for details.
See Also:
Resubmitting and Canceling Service Operations for Processing topic in the PeopleBook Enterprise PeopleTools 8.49 PeopleBook: PeopleSoft Integration Broker available on Oracle Technology Network:
http://download.oracle.com/docs/cd/E13292_01/pt849pbr0/eng/psbooks/tibr/book.htm
Target authentication is done to validate whether Oracle Identity Manager should accept messages from the target system or not. Target authentication is done by passing the name of the IT resource in the Integration Broker node. You must ensure that the correct value of the IT resource name is specified in the node. See Configuring PeopleSoft Integration Broker for setting up the node.
In addition, the flag IsActive is used to verify whether the IT resource is active or not. The value of this flag is Yes, by default. When this value is Yes, target authentication is carried out. Target authentication fails if it is set to No.
Target authentication is also carried out during a ping request from the PeopleSoft node.
This connector supports the SoD feature in Oracle Identity Manager release 11.1.1.5 BP01.
This section contains the following topics:
The following are the focal points of this feature:
The SoD Invocation Library (SIL) is bundled with Oracle Identity Manager release. The SIL acts as a pluggable integration interface with any SoD engine.
The connector is preconfigured to work with Oracle Applications Access Controls Governor as the SoD engine. To enable this, changes have been made in the provisioning workflows of the connector.
The SoD engine processes role entitlement requests that are sent through the connector. Potential conflicts in role assignments can be automatically detected.
See Also:
Configuring SoD on Oracle Identity Manager in this guide
When you enable SoD, an entitlement is provisioned only after the SoD validation clears the request for the entitlement. Users can create entitlement requests for themselves. Alternatively, administrators can submit entitlement requests on behalf of users.
Note:
The connector supports the scenario in which a single request is created for multiple roles and a single approver is assigned the entire request.
The SoD validation process is asynchronous. The response from the SoD engine must be brought to Oracle Identity Manager by a scheduled task.
Request-based provisioning of roles involves the following steps:
You can configure validation and transformation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning.
Lookup.PSFT.UM.ReconValidation and Configuring Validation of Data During Reconciliation provide information about setting up the validation feature during reconciliation.
Configuring Transformation of Data During Reconciliation provides information about setting up the transformation feature.
Lookup.PSFT.UM.ProvValidation and Configuring Validation of Data During Provisioning provide information about setting up the validation feature during provisioning.
A connection pool is a cache of objects that represent physical connections to the target. Oracle Identity Manager connectors can use these connections to communicate with target systems. At run time, the application requests a connection from the pool. If a connection is available, then the connector uses it and then returns it to the pool. A connection returned to the pool can again be requested for and used by the connector for another operation. By enabling the reuse of connections, the connection pool helps reduce connection creation overheads such as network latency, memory allocation, and authentication.
One connection pool is created for each IT resource. For example, if you have three IT resources for three installations of the target system, then three connection pools are created, one for each target system installation.
Setting up the Lookup.PSFT.Configuration Lookup Definition for Connection Pooling provides information about connection pooling.
Note:
The connector does not support connection pooling for provisioning multiple versions of the target system. In other words, connection pooling is supported only when provisioning is done for one version of the target system. In this case, the Multiple Version Support parameter is set to No in the Lookup.PSFT.Configuration lookup definition.
You can configure the connector to support additional ID types effortlessly. The connector by default supports the following ID types other than the Employee (EMP) ID type:
Customer (CST)
Vendor (VND)
The following additional attributes are provided in the Oracle Identity Manager process form to support these ID types:
For Customer:
Customer ID
Customer Set ID
For Vendor:
Vendor ID
Vendor Set ID
The Adding New ID Types for Provisioning describes the procedure to add ID types.
The DELETE_USER_PROFILE component interface definition is used to delete user profile definitions. The delCompIntfcKey key is defined in the PeopleSoft Component Interface map definition file, PeopleSoftComponentInterfaces.xml.
The Lookup.PSFT.Configuration lookup definition contains a mapping for the delCompIntfcKey key to determine the user profile to be used for delete operations.
You can specify a list of accounts that must be excluded from all reconciliation and provisioning operations. Accounts whose user IDs you specify in the exclusion list are not affected by reconciliation and provisioning operations.
Lookup Definitions for Exclusion Lists describes the lookup definitions where you specify the user IDs to be excluded during reconciliation and provisioning operations. Setting Up the Lookup Definitions for Exclusion Lists describes the procedure to add entries in these lookup definitions.
Note:
See Certified Components for information about the supported PeopleTools versions. If you are using a PeopleTools version that is not supported, then you are likely to encounter issues that might be difficult to resolve.
The connector can be configured to work with different versions of the target system at the same time without any custom class loader. The connector uses the Identity Connector Framework (ICF) connector class loader for this feature. For example, you can use a single instance of the connector to integrate Oracle Identity Manager with a PeopleTools 8.48 installation and a PeopleTools 8.49 installation.
See Configuring the Connector to Support Multiple Versions of the Target System for more information.
The Identity Connector Framework (ICF) is a component that provides basic provisioning, reconciliation, and other functions that all Oracle Identity Manager connectors require. The ICF also uses classpath isolation, which allows the PeopleSoft connector to co-exist with legacy versions of the connector.
For more information, see Understanding the Identity Connector Framework in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager.
If required by your deployment, you can deploy the connector in the Connector Server. For more information, see Installing and Configuring the Connector Server.
Lookup definitions used during connector operations can be categorized as follows:
During a provisioning operation, you use a lookup field to specify a single value from a set of values. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to the target system lookup fields into the lookup definitions in Oracle Identity Manager.
Note:
As an implementation best practice, lookup fields should be synchronized before you perform reconciliation or provisioning operations.
connector.htm#GUID-7D6714A8-19BA-4B23-BF1C-EE9C86A42E81__CHDHACHF lists the lookup fields that are synchronized with their corresponding lookup definitions in Oracle Identity Manager.
Table 1-2 Lookup Fields That Are Synchronized
| Lookup Definition | Target System Lookup Field | Synchronization Method |
|---|---|---|
|
Lookup.PSFT.UM.LanguageCode |
Language Code |
You use the Language Code Lookup Reconciliation scheduled task to synchronize this lookup definition. |
|
Lookup.PSFT.UM.CurrencyCode |
Currency Code |
You use the Currency Code Lookup Reconciliation scheduled task to synchronize this lookup definition. |
|
Lookup.PSFT.UM.PermissionList |
Permission Lists |
You use the Permission List Lookup Reconciliation scheduled task to synchronize this lookup definition. |
|
Lookup.PSFT.UM.EmailType |
Email Type |
You use the Email Type Lookup Reconciliation scheduled task to synchronize this lookup definition. |
|
Lookup.PSFT.UM.Roles |
Role Name |
You use the Roles Lookup Reconciliation scheduled task to synchronize this lookup definition. |
This section describes the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. Either lookup definitions are prepopulated with values or values must be manually entered in them after the connector is deployed.
The predefined lookup definitions can be categorized as follows:
The Lookup.PSFT.Configuration lookup definition is used to store configuration information that is used by the connector. See Configuring the IT Resource for information about the entries in this lookup definition.
The Lookup.PSFT.Configuration lookup definition has the following entries:
| Code Key | Decode | Description |
|---|---|---|
|
Bundle Name |
org.identityconnectors.peoplesoftintfc |
Name of the connector bundle package. Do not modify this entry. |
|
Bundle Version |
1.0.5963 |
Version of the connector bundle class. Do not modify this entry. |
|
Connector Name |
org.identityconnectors.peoplesoft.compintfc.PeopleSoftCompIntfcConnector |
Name of the connector class. Do not modify this entry. |
|
Constants Lookup |
Lookup.PSFT.UM.Constants |
Name of the lookup definition that is used to store constants used by the connector. |
|
delCompIntfcKey |
DELETE_USER_PROFILE |
Name of the component interface used for delete operations. |
|
DELETE_USER_PROFILE |
Lookup.PSFT.Message.DeleteUserProfile.Configuration |
Name of the lookup definition for the DELETE_USER_PROFILE message. |
|
Ignore Root Audit Action |
No |
Use this value if the Root PSCAMA audit action is required to be considered while parsing the XML message. Use Use |
|
mappingFactoryClassName |
org.identityconnectors.peoplesoft.common.mapping.idm.IDMSAXComponentInterfacesFactory |
TBD |
|
maxFindItems |
300 |
TBD |
|
Recon Exclusion List |
Lookup.PSFT.UM.Recon.ExclusionList |
Name of the lookup for specifying exclusions during reconciliation |
|
rwCompIntfcKey |
USER_PROFILE_8_4X Note: If you want to support a different component interface, you must change this value. See Connector Component Interfaces for the PeopleSoft User Management for more information. |
Name of the component interface used for create and update operations. |
|
Target Date Format |
yyyy-MM-dd |
Data format of the Date type data in the XML file and messages Do not modify this entry. |
|
USER_PROFILE.VERSION_84 |
Lookup.PSFT.Message.UserProfile.Configuration |
Name of the lookup definition for the USER_PROFILE message See Lookup.PSFT.Message.UserProfile.Configuration for more information about this lookup definition. |
|
User Configuration Lookup |
Lookup.PSFT.UM.Prov.Configuration |
Name of the lookup definition that contains user-specific configuration properties for provisioning. Do not modify this entry. |
|
xmlMapping[LOADFROMURL] |
Enter the path to the PeopleSoft Component Interface map definition file. Sample value: |
This file contains the definitions used by the connector for various operations. By default, the file is located in the /xml of the connector package. Note: See Connector Component Interfaces for the PeopleSoft User Management for more information about this definition file. If you deploy the connector on a cluster, you must copy this file to the same location on all the nodes. |
The combination of the following fields form the Identity Connector Framework (ICF) connector key used for identifying the right connector bundle:
Bundle Name
Bundle Version
Connector Name
You can configure the message names, such as USER_PROFILE and DELETE_USER_PROFILE defined in this lookup definition. See Setting Up the Lookup.PSFT.Configuration Lookup Definition for instructions on configuring these message names in the lookup definition.
The following lookup definitions are used to process the USER_PROFILE messages:
The Lookup.PSFT.Message.UserProfile.Configuration lookup definition provides configuration-related information for the USER_PROFILE message.
The Lookup.PSFT.Message.UserProfile.Configuration lookup definition has the following entries:
| Code Key | Decode | Description |
|---|---|---|
|
Attribute Mapping Lookup |
Lookup.PSFT.UM.UserProfile.ReconAttrMap |
Name of the lookup definition that maps Oracle Identity Manager attributes with the attributes in the USER_PROFILE message during reconciliation operations. See Lookup.PSFT.UM.UserProfile.ReconAttrMap for more information about this lookup definition. |
|
Child Table Lookup Definition |
Lookup.PSFT.UM.UserProfile.ChildTables |
Name of the lookup definition that maps resource object fields and multivalued target system attributes during reconciliation operations. |
|
Custom Query |
Enter a Value |
If you want to implement limited reconciliation, then enter the query condition that you create by following the instructions given in Limited Reconciliation. |
|
Data Node Name |
Transaction |
Name of the node in the XML files to run a transaction Default value: You must not change the default value. |
|
IT Resource Name |
PSFT User |
Name of the IT resource |
|
Message Handler Class |
oracle.iam.connectors.psft.common.handler.impl.PSFTUserProfileReconMessageHandlerImpl |
Name of the Java class that accepts the XML payload, configuration information, and a handle to Oracle Identity Manager. Depending on the message type, it retrieves the appropriate configuration from Oracle Identity Manager and processes the message. To parse a specific message type, it relies on a Message Parser factory. If you want a customized implementation of the message, then you must extend the |
|
Message Parser |
oracle.iam.connectors.psft.common.parser.impl.UserMessageParser |
Name of the parser implementation class that contains the logic for message parsing If you want a customized implementation of the message, then you must extend the |
|
Primary Email Lookup |
Lookup.PSFT.UM.PrimaryEmail |
Name of the lookup definition used to specify whether an e-mail ID is primary or not |
|
Recon Lookup Definition |
Lookup.PSFT.UM.UserProfile.Recon |
Name of the lookup definition that maps the Oracle Identity Manager attributes with the Resource Object attributes |
|
Resource Object |
Peoplesoft User |
Name of the resource object |
|
Transformation Lookup Definition |
Lookup.PSFT.UM.UserProfile.Transformation |
Name of the transformation lookup definition See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition. |
|
User Status Lookup |
Lookup.PSFT.UM.UserProfile.UserStatus |
Name of the lookup definition that provides the user status See Lookup.PSFT.UM.UserProfile.UserStatus for more information about this lookup definition. |
|
Use Transformation |
No |
Use this parameter to perform transformation. |
|
Use Validation |
No |
Use this parameter to perform validation. |
|
Validation Lookup Definition |
Lookup.PSFT.UM.ReconValidation |
Name of the validation lookup definition for reconciliation See Configuring Validation of Data During Reconciliation for more information about adding entries in this lookup definition. |
The Lookup.PSFT.UM.UserProfile.ReconAttrMap lookup definition maps OIM User attributes with the attributes defined in the USER_PROFILE message XML. The following is the format of the values stored in this lookup definition:
| Code Key | Decode |
|---|---|
|
Currency Code |
CURRENCY_CD~PSOPRDEFN |
|
Customer ID |
CUST_ID~PSOPRALIAS~OPRALIASTYPE=CST |
|
Customer Set ID |
SETID~PSOPRALIAS~OPRALIASTYPE=CST |
|
Email ID |
EMAILID~PSUSEREMAIL~None~None~CHILD=Email IDs |
|
Email Type |
EMAILTYPE~PSUSEREMAIL~None~None~CHILD=Email IDs |
|
Employee ID |
EMPLID~PSOPRALIAS~OPRALIASTYPE=EMP |
|
Language Code |
LANGUAGE_CD~PSOPRDEFN |
|
Multi Language Code |
MULTILANG~PSOPRDEFN |
|
Navigator Home Permission List |
DEFAULTNAVHP~PSOPRDEFN |
|
Primary Email |
EMAILID~PSUSEREMAIL~PRIMARY_EMAIL=Y |
|
Primary Permission List |
OPRCLASS~PSOPRDEFN |
|
Process Profile Permission List |
PRCSPRFLCLS~PSOPRDEFN |
|
Return ID |
OPRID~PSOPRDEFN~None~None~PRIMARY |
|
Role |
ROLENAME~PSROLEUSER_VW~None~None~CHILD=Roles |
|
Row Security Permission List |
ROWSECCLASS~PSOPRDEFN |
|
Symbolic ID |
SYMBOLICID~PSOPRDEFN |
|
User Description |
OPRDEFNDESC~PSOPRDEFN |
|
User ID |
OPRID~PSOPRDEFN~None~None~PRIMARY |
|
User ID Alias |
USERIDALIAS~PSOPRDEFN |
|
User Status |
ACCTLOCK~PSOPRDEFN |
|
Vendor ID |
VENDOR_ID~PSOPRALIAS~OPRALIASTYPE=VND |
|
Vendor Set ID |
SETID~PSOPRALIAS~OPRALIASTYPE=VND |
Code Key: Name of the OIM User field
Decode: Combination of the following elements separated by the tilde (~) character:
NODE~PARENT NODE~TYPE NODE=Value~EFFECTIVE DATED NODE~PRIMARY or CHILD=Multivalued Child Table RO Field
In this format:
NODE: Name of the node in the USER_PROFILE message XML from which the value is read. You must specify the name of the NODE in the lookup definition. It is a mandatory field.
PARENT NODE: Name of the parent node for the NODE. You must specify the name of the parent node in the lookup definition. It is a mandatory field.
TYPE NODE=Value: Type of the node associated with the Node value. Value defines the type of the Node.
EFFECTIVE DATED NODE: Effective-dated node for the NODE element, if any.
PeopleSoft supports effective-dated events. The value refers to the name of the node that provides information about the date on which the event becomes effective.
The USER_PROFILE message does not support effective-dated information. Therefore, the value of this parameter in the preceding syntax is None.
PRIMARY or Child=Multivalued Child Table RO Field: Specifies whether the node is a mandatory field or a multivalued attribute on Oracle Identity Manager.
In case of multivalued attribute data, CHILD specifies that this is a Child data followed by the name of the table defined in the resource object to which the data corresponds.
The following scenario illustrates how to map the entries in the lookup definition.
You want to retrieve the value for the Email Type Code Key that is defined as a multivalued attribute in Oracle Identity Manager. In PeopleSoft, the PSUSEREMAIL rowset lists the e-mail IDs assigned to a user. The NODE will be EMAILTYPE as depicted in the XML file. See the sample XML file in connector.htm#GUID-F18F4890-FE62-47E6-8627-EF660E2636C6__CEGEGFBG for more information about each node in the USER_PROFILE message.
Figure 1-3 Sample XML File for USER_PROFILE Message
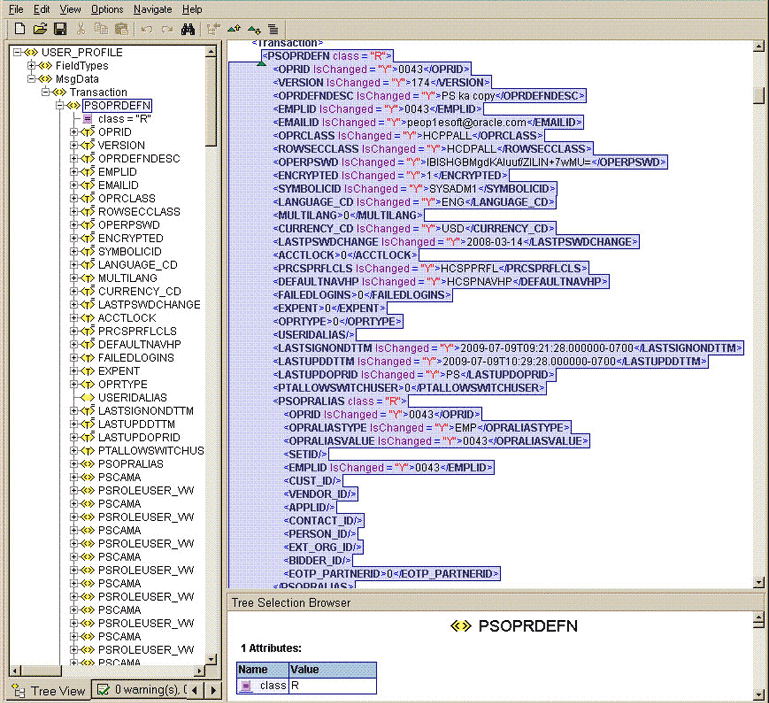
The parent node for the EMAILTYPE node will be PSUSEREMAIL. Now suppose, you have a scenario where want to retrieve the e-mail IDs that are not defined as Primary. In this case, you must identify the TYPE NODE value for the parent node that has the value N. In this example, the type node is PRIMARY_EMAIL with the value N.
The effective-dated node will be None, because the USER_PROFILE message does not provide this information.
The Multivalued Child Table RO Field in this scenario is Email IDs. It is the name of the table defined in the Resource Object for the Email ID child attribute.
If you do not want to provide any element in the Decode column, then you must specify None. This is implemented for the User ID attribute.
Now, you can concatenate the various elements of the syntax by using a tilde (~) to create the Decode entry for Email Type, as follows:
NODE: EMAILTYPE
PARENT NODE: PSUSEREMAIL
TYPE NODE=Value: PRIMARY_EMAIL=N
EFFECTIVE DATED NODE: None
Child=Multivalued Child Table RO Field: CHILD=Email IDs
So, the Decode column for Email Type is as follows:
EMAILTYPE~PSUSEREMAIL~PRIMARY_EMAIL=N~None~CHILD=Email IDs
The Lookup.PSFT.UM.UserProfile.Recon lookup definition maps the resource object field name with the value fetched from the Lookup.PSFT.UM.UserProfile.ReconAttrMap lookup.
The Lookup.PSFT.UM.UserProfile.Recon lookup definition has the following entries:
| Code Key | Decode |
|---|---|
|
Currency Code |
Currency Code~None~LKF |
|
Customer ID |
Customer ID |
|
Customer Set ID |
Customer Set ID |
|
Email Address |
Email ID~None~None~Child |
|
Email Type |
Email Type~None~LKF~Child |
|
Employee ID |
Employee ID |
|
ITResource Name |
IT Resource Name |
|
Language Code |
Language Code~None~LKF |
|
MultiLanguage code |
Multi Language Code |
|
Navigator Home Page |
Navigator Home Permission List~None~LKF |
|
Primary Email Address |
Primary Email ID |
|
Primary Email Type |
Primary Email Type~None~LKF |
|
Primary Permission |
Primary Permission List~None~LKF |
|
Process Profile |
Process Profile Permission List~None~LKF |
|
Role Name |
Role~None~LKF~Child |
|
Row Security |
Row Security Permission List~None~LKF |
|
Symbolic ID |
Symbolic ID |
|
User Description |
User Description |
|
User ID |
User ID |
|
User ID Alias |
User ID Alias |
|
User Status |
User Status~User Status Lookup |
|
Vendor ID |
Vendor ID |
|
Vendor Set ID |
Vendor Set ID |
Code Key: Name of the resource object field in Oracle Identity Manager
Decode: Combination of the following elements separated by a tilde (~) character:
ATTRIBUTE ~ LOOKUP DEF ~LKF
In this format:
ATTRIBUTE: Refers to the Code Key of the Lookup.PSFT.UM.UserProfile.ReconAttrMap lookup definition
LOOKUP DEF: Name of the lookup definition, if the value of the attribute is retrieved from a lookup. This lookup is specified in the message-specific configuration lookup.
LKF: Specifies that the attribute is a lookup field on the process form.
Consider the scenario discussed in Mapping Entries in the Lookup.PSFT.UM.UserProfile.ReconAttrMap Lookup Definition. In that example, you fetched the Email Type in the Code Key column from the EMAILTYPE node of the XML file.
Now, you must map this Email Type defined in the Lookup.PSFT.UM.UserProfile.ReconAttrMap lookup definition with the resource object attribute Email Type defined in the Lookup.PSFT.UM.UserProfile.Recon lookup definition Code Key.
For example, if the name of the Code Key column in the Lookup.PSFT.UM.UserProfile.ReconAttrMap lookup definition is E_Type then you define the mapping in the Lookup.PSFT.UM.UserProfile.Recon lookup definition as follows:
Code Key: Email Type
Decode: E_Type~None~LKF
In other words, this implies that the value for Email Type in the Lookup.PSFT.UM.UserProfile.Recon lookup definition is fetched from E_Type defined in the attribute mapping lookup definition.
The same process holds true for other attributes defined in the lookup.
However, to fetch the value of the User Status resource object field, you must consider the User Status lookup definition. User Status is defined in the message-specific attribute lookup, Lookup.PSFT.UM.UserProfile.ReconAttrMap, which has a value 0 that is fetched from the ACCTLOCK node in the XML.
Now, the User Status Lookup lookup definition is defined in the message-specific configuration, Lookup.PSFT.Message.UserProfile.Configuration lookup definition. The mapping is as follows:
Code Key: User Status Lookup
Decode: Lookup.PSFT.UM.UserProfile.UserStatus
In other words, you must search for the value 0 in the Lookup.PSFT.UM.UserProfile.UserStatus lookup definition. The mapping in Lookup.PSFT.UM.UserProfile.UserStatus lookup definition is defined as follows:
Code Key: 0
Decode: Enabled
The resource is updated with the user status as Enabled.
The Lookup.PSFT.UM.UserProfile.UserStatus lookup definition maps the value of the ACCTLOCK node in the USER_PROFILE message XML with the status to be shown in Oracle Identity Manager for the user.
The Lookup.PSFT.UM.UserProfile.UserStatus lookup definition has the following entries:
| Code Key | Decode |
|---|---|
|
0 |
Enabled |
|
1 |
Disabled |
Setting Up the Lookup.PSFT.UM.UserProfile.UserStatus Lookup Definition describes the procedure to modify the Decode values in this lookup definition.
The Lookup.PSFT.UM.UserProfile.ChildTables lookup definition maps the resource object fields with the multivalued target system attributes.
Code Key: Multivalued Child Table resource object field
Decode: Child Table attributes defined in the resource object separated by the tilde (~) character
The following screenshot displays the link between the table and the resource object attribute:
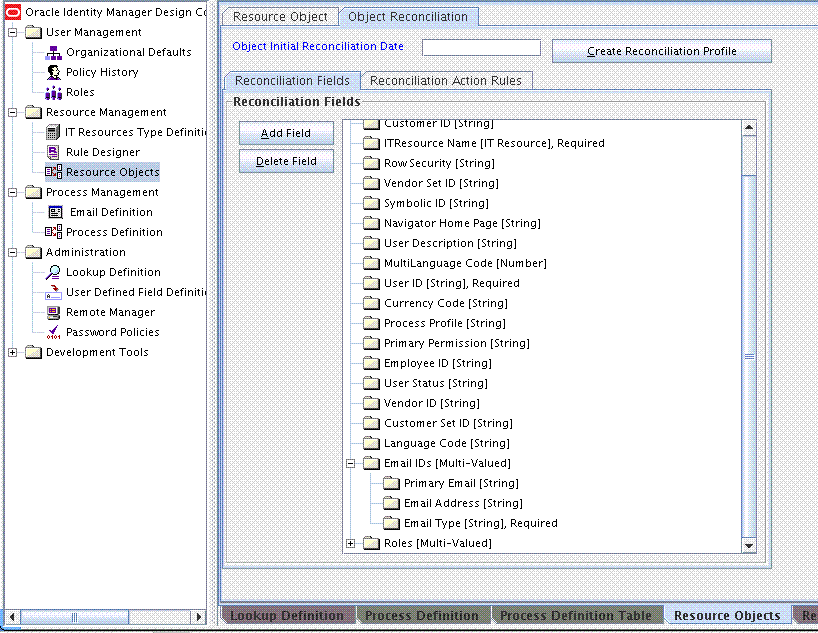
The Lookup.PSFT.UM.UserProfile.ChildTables lookup definition has the following entries:
| Code Key | Decode |
|---|---|
|
Email IDs |
Email Address~Email Type~Primary Email |
|
Roles |
Role Name |
The Lookup.PSFT.UM.UserProfile.Transformation lookup definition is used to store the mapping between the attribute for which transformation has to be applied and the transformation implementation class.
The Lookup.PSFT.UM.UserProfile.Transformation lookup definition is empty, by default.
See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition.
The following lookup definitions are used to process DELETE_USER_PROFILE messages:
The Lookup.PSFT.Message.DeleteUserProfile.Configuration lookup definition provides configuration-related information for the DELETE_PROFILE message.
The Lookup.PSFT.Message.DeleteUserProfile.Configuration lookup definition has the following entries:
| Code Key | Decode | Description |
|---|---|---|
|
Attribute Mapping Lookup |
Lookup.PSFT.UM.DeleteUserProfile.AttributeMapping |
Name of the lookup definition that maps Oracle Identity Manager attributes with attributes in the DELETE_PROFILE message See Lookup.PSFT.UM.DeleteUserProfile.AttributeMapping for more information about this lookup definition. |
|
Data Node Name |
Transaction |
Name of the node in the XML files to run a transaction Default value: You must not change the default value. |
|
IT Resource Name |
PSFT User |
Name of the IT resource |
|
Message Handler Class |
oracle.iam.connectors.psft.common.handler.impl.PSFTDeleteUserReconMessageHandlerImpl |
Name of the Java class that accepts the XML payload, configuration information, and a handle to Oracle Identity Manager. Depending on the message type, it retrieves the appropriate configuration from Oracle Identity Manager and processes the message. To parse a specific message type, it relies on a Message Parser factory. If you want a customized implementation of the message, then you must extend the |
|
Message Parser |
oracle.iam.connectors.psft.common.parser.impl.DeleteUserMessageParser |
Name of the parser implementation class that contains the logic for message parsing If you want a customized implementation of the message, then you must extend the |
|
Recon Lookup Definition |
Lookup.PSFT.UM.DeleteUserProfile.Recon |
Name of the lookup definition that maps the Oracle Identity Manager attributes with the Resource Object attributes See Lookup.PSFT.UM.DeleteUserProfile.Recon for more information about this lookup definition. |
|
Resource Object |
Peoplesoft User |
Name of the resource object |
The Lookup.PSFT.UM.DeleteUserProfile.AttributeMapping lookup definition maps OIM User attributes with the attributes defined in the DELETE_PROFILE message XML.
The following is the format of the values stored in this lookup definition:
| Code Key | Decode |
|---|---|
|
User ID |
Note: If you are using PeopleTools 8.52, replace the preceding default Decode value with the following value:
|
Code Key: Name of the OIM User field
Decode: Combination of the following elements separated by a tilde (~) character:
NODE~PARENT NODE~TYPE NODE=Value~EFFECTIVE DATED NODE~PRIMARY
For more information about the preceding syntax, see Lookup.PSFT.UM.UserProfile.ReconAttrMap.
The Lookup.PSFT.UM.DeleteUserProfile.Recon lookup definition maps the resource object field name with the value fetched from the Lookup.PSFT.UM.DeleteUserProfile.AttributeMapping lookup definition.
The following is the format of the values stored in this table:
| Code Key | Decode |
|---|---|
|
User ID |
User ID |
|
ITResource Name |
IT Resource Name |
The following are the predefined generic lookup definitions:
The Lookup.PSFT.UM.Prov.Configuration lookup definition maps the provisioning configurations with the lookups.
The Lookup.PSFT.UM.Prov.Configuration lookup definition has the following entries:
| Code Key | Decode |
|---|---|
|
Provisioning Attribute Map |
Lookup.PSFT.UM.ProvAttrMap |
|
Provisioning Exclusion List |
Lookup.PSFT.UM.Prov.ExclusionList |
|
Provisioning Validation Lookup |
Lookup.PSFT.UM.ProvValidation |
You can enable exclusions and validations during provisioning by adding the entries as shown in this lookup. To disable exclusions or validations, remove the corresponding entries in this lookup.
The Lookup.PSFT.UM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes. These lookup definitions are used during provisioning.
The Lookup.PSFT.UM.ProvAttrMap lookup definition has the following entries:
| Code Key | Decode |
|---|---|
|
Currency Code[Lookup] |
CurrencyCode |
|
Customer ID |
IDTypes~UM_IDTypes[IDType=CST]~Attributes~UM_Attributes[AttributeName=Customer ID]~AttributeValue |
|
Customer Set ID |
IDTypes~UM_IDTypes[IDType=CST]~Attributes~UM_Attributes[AttributeName=Set ID]~AttributeValue Note: For People Tools 8.48, the AttributeName is |
|
Employee ID |
IDTypes~UM_IDTypes[IDType=EMP]~Attributes~UM_Attributes[AttributeName=Empl ID]~AttributeValue Note: For People Tools 8.48, the AttributeName is |
|
Language Code[Lookup] |
LanguageCode |
|
Multi Language Code |
MultiLanguageEnabled |
|
Navigator Home Permission List[Lookup] |
NavigatorHomePermissionList |
|
Password |
__PASSWORD__ |
|
Primary Permission List[Lookup] |
PrimaryPermissionList |
|
Process Profile Permission List[Lookup] |
ProcessProfilePermissionList |
|
Return ID |
__UID__ |
|
Row Security Permission List[Lookup] |
RowSecurityPermissionList |
|
Symbolic ID |
SymbolicID |
|
UD_PS_EMAIL~Email Address |
EmailAddresses~UM_EmailAddresses~EmailAddress |
|
UD_PS_EMAIL~Email Type[Lookup] |
EmailAddresses~UM_EmailAddresses~EmailType |
|
UD_PS_EMAIL~Primary Email |
EmailAddresses~UM_EmailAddresses~PrimaryEmail |
|
UD_PSROLES~Role Name[Lookup] |
Roles~UM_Roles~RoleName |
|
User Description |
UserDescription |
|
User ID |
__NAME__ |
|
User ID Alias |
UserIDAlias |
|
Vendor ID |
IDTypes~UM_IDTypes[IDType=VND]~Attributes~UM_Attributes[AttributeName=Vendor ID]~AttributeValue |
|
Vendor Set ID |
IDTypes~UM_IDTypes[IDType=VND]~Attributes~UM_Attributes[AttributeName=Set ID]~AttributeValue Note: For People Tools 8.48, the AttributeName is |
The mappings in this lookup definition follow the Identity Connector Framework (ICF) conventions. The following is the format of the Code Key and Decode values in this lookup definition:
SUFFIX[Lookup] means that the value of the attribute is retrieved from a lookup. For example, the value of the CurrencyCode attribute is retrieved from the Currency Code[Lookup] Code Key.
For the Employee ID Code Key, Decode is the combination of the following elements separated by a tilde (~) character:
IDTypes~UM_IDTypes[IDType=EMP]~Attributes~UM_Attributes[AttributeName=Empl ID]~AttributeValue
In this format:
IDTypes: Refers to the ICF Parent Attribute Name
UM_IDTypes: Refers to the embedded ICF object class that contains IDType and Attributes. The default value of IDType is EMP.
Attributes: Refers to the ICF embedded object class that contains AttributeName and AttributeValue. The default value of AttributeName is Empl ID. The value of AttributeValue is retrieved from the form field.
The following ICF hierarchy is created for the lookup:
IDTypes [Objectclass UM_IDTypes]
IDType : EMP
Attributes [Objectclass UM_Attributes]
AttributeName : Empl ID
Attribute Value : <Form field mapping>
This hierarchy is similar to the definition in PeoplesoftComponentInterfaces.xml, which is the default component interface map definition file.
The same format holds true for the Customer ID, Customer Set ID, Vendor ID, and Vendor Set ID Code Keys.
For the child form mappings, Code Key is the combination of the child form name and the child form attribute separated by a tilde (~) character.
Decode is the combination of the following elements separated by a tilde (~) character:
ICF Parent Attribute Name~ICF Embedded Object Class Name~Embedded Object Class Attribute
The following ICF hierarchy is created for the email lookups:
EmailAddresses (Objectclass UM_EmailAddresses)
EmailAddress
EmailType
PrimaryEmail
The same format holds true for the roles lookups.
The following Code Keys are used for special configurations:
User ID: Refers to the key identifier for operations
Return ID: Refers to the UID returned after a create operation. This UID is used for further provisioning operations such as update and delete. This connector returns the User ID.
Password: Refers to the password field.
The Lookup.PSFT.UM.ProvValidation lookup definition is used to store the mapping between the attribute for which validation during provisioning has to be applied and the validation implementation class.
The Lookup.PSFT.UM.ProvValidation lookup definition is empty, by default.
See Configuring Validation of Data During Provisioning for more information about adding entries in this lookup definition.
The Lookup.PSFT.UM.ReconValidation lookup definition is used to store the mapping between the attribute for which validation during reconciliation has to be applied and the validation implementation class.
The Lookup.PSFT.UM.ReconValidation lookup definition is empty, by default.
See Configuring Validation of Data During Reconciliation for more information about adding entries in this lookup definition.
The Lookup.PSFT.UM.Prov.ExclusionList and Lookup.PSFT.UM.Recon.ExclusionList lookup definitions hold user IDs of target system accounts for which you do not want to perform provisioning and reconciliation operations, respectively.
The following is the format of the values stored in these lookups:
| Code Key | Decode | Sample Values |
|---|---|---|
|
User ID resource object field name |
User ID of a user |
Code Key: User ID Decode: User001 |
|
User ID resource object field name with the [PATTERN] suffix |
A regular expression supported by the representation in the |
Code Key: User ID[PATTERN] To exclude users matching any of the user ID 's User001, User002, User088, then: Decode: User001|User002|User088 To exclude users whose user ID 's start with 00012, then: Decode: 00012* See Also: For information about the supported patterns, visit |
Setting Up the Lookup Definitions for Exclusion Lists describes the procedure to add entries in these lookup definitions.
Target resource reconciliation involves fetching the data of newly created or modified users on the target system and using this data to add or modify resources assigned to OIM Users.
See Also:
Managing Reconciliation in Oracle Fusion Middleware Administering Oracle Identity Manager for conceptual information about target resource reconciliation
This section discusses the following topics:
connector.htm#GUID-00551BA6-10A5-480E-8B81-FBF17EEB45EF__CHDCGGFG lists the target system attributes whose values are fetched during a target resource reconciliation run.
Table 1-3 Attributes Used for Reconciliation
| Resource Object Field | Target System Attribute | Description |
|---|---|---|
|
Single-Valued Fields |
||
|
User Id |
PSOPRDEFN.OPRID |
Login ID of the user profile This is a mandatory field. |
|
Employee Id |
PSOPRDEFN.EMPLID |
Employee ID of the employee linked with the user profile |
|
User Description |
PSOPRDEFN.OPRDEFNDESC |
Description of the user profile |
|
Multi Language Code |
PSOPRDEFN.MULTILANG |
Multilanguage code |
|
Language Code |
PSOPRDEFN.LANGUAGE_CD |
Language code |
|
Currency Code |
PSOPRDEFN.CURRENCY_CD |
Currency code |
|
User Id Alias |
PSOPRDEFN.USERIDALIAS |
Alias of user login ID |
|
Row Security Permission List |
PSOPRDEFN.ROWSECCLASS |
Row security parameter |
|
Process Profile Permission List |
PSOPRDEFN.PRCSPRFLCLS |
Process profile parameter |
|
Navigator Home Permission List |
PSOPRDEFN.DEFAULTNAVHP |
Navigator home page address |
|
Primary Permission List |
PSOPRDEFN.OPRCLASS |
Primary permission list |
|
Multivalued Fields |
||
|
RoleName |
PSROLEUSER_VW.ROLENAME |
The role name that is assigned to the user profile |
|
Email Address Email Type Primary Email Note: To specify the e-mail address for an account, you must also specify the e-mail type of that e-mail address. You must have only one primary e-mail address if you provide e-mail addresses. |
PSUSEREMAIL.EMAILID PSUSEREMAIL.EMAILTYPE PSUSEREMAIL.PRIMARYEMAIL |
E-mail address E-mail type Specifies if the e-mail address is primary |
|
User Profile Type Note: PeopleSoft stores values corresponding to a user profile type, such as Employee ID, Customer ID, and Vendor ID in the |
PSOPRALIAS. OPRALIASTYPE |
A user profile can be attached to several user profile types, such as Employee (EMP), Customer (CST), and Vendor (VND) |
The following sections provide information about the reconciliation rules for this connector:
The following reconciliation rule is used for target resource reconciliation:
Rule Name: PSFT UM Target Recon Rule
Rule Element: User Login Equals User ID
In this rule:
User Login represents the User ID field on the OIM User form.
User ID represents the OPRID field of the user on the target system.
After you deploy the connector, you can view the reconciliation rule by performing the following steps:
Note:
Perform the following procedure only after the connector is deployed.
Application of the matching rule on reconciliation events would result in one of multiple possible outcomes. The action rules for reconciliation define the actions to be taken for these outcomes.
Note:
For any rule condition that is not predefined for this connector, no action is performed and no error message is logged.
The following sections provide information about the reconciliation action rules for this connector:
connector.htm#GUID-864EC584-BB15-4A8A-ACD9-13F1DA5A72F0__CHDJDDIC lists the reconciliation action rules for this connector.
Table 1-4 Action Rules for Target Resource Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Assign to Administrator With Least Load |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Provisioning involves creating, modifying, or deleting a user's account information on the target system through Oracle Identity Manager.
See Also:
Managing Provisioning Tasks in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Manager for conceptual information about provisioning
This section discusses the following topics:
connector.htm#GUID-86BE7257-D6B8-447A-87AC-8CFAC2D58970__CEGFFBDG lists the supported user provisioning functions and the adapters that perform these functions. The functions listed in the table correspond to either a single or a multiple process tasks.
See Also:
Developing Provisioning Processes and Using the Adapter Factory in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for generic information about process tasks and adapters
Table 1-5 User Provisioning Functions Supported by the Connector
| Function | Adapter |
|---|---|
|
Create a user |
PSFT UM Create User |
|
Update the password of a user |
PSFT UM Update Password |
|
Update the description of a user |
PSFT UM Update User |
|
Update the multilanguage code of a user |
PSFT UM Update User |
|
Update the language code of a user |
PSFT UM Update User |
|
Update the currency code of a user |
PSFT UM Update User |
|
Update the Primary Permission list of a user |
PSFT UM Update User |
|
Update the Employee Id |
PSFT UM Update ID Types |
|
Update the Vendor Set Id |
PSFT UM Update ID Types |
|
Update the Vendor Id |
PSFT UM Update ID Types |
|
Update the Customer Set Id |
PSFT UM Update ID Types |
|
Update the Customer Id |
PSFT UM Update ID Types |
|
Update the Process Profile Permission list of a user |
PSFT UM Update User |
|
Update the Navigator Home Permission list of a user |
PSFT UM Update User |
|
Update the Row Security Permission list of a user |
PSFT UM Update User |
|
Update the User Id alias of a user |
PSFT UM Update User |
|
Add a role to a user |
PSFT UM Modify Multiple Attr Data |
|
Revoke a role from a user |
PSFT UM Modify Multiple Attr Data |
|
Update Role |
PSFT UM Modify Multiple Attr Data |
|
Add an e-mail address |
PSFT UM Modify Multiple Attr Data |
|
Revoke an e-mail address |
PSFT UM Modify Multiple Attr Data |
|
Update an e-mail address |
PSFT UM Modify Multiple Attr Data |
|
Lock or disable a user |
PSFT UM Modify Lock Unlock User |
|
Unlock or enable a user |
PSFT UM Modify Lock Unlock User |
|
Delete a user |
PSFT UM Delete User |
connector.htm#GUID-FEAAD212-A89C-4772-B71A-9EA227833F6B__CEGEAJEI lists the user attributes for which you can specify or modify values during provisioning operations.
Table 1-6 User Attributes for Provisioning
| OIM PeopleSoft UM Resources Process Form Field | Target System Attribute | Description | Adapter |
|---|---|---|---|
|
Single-Valued Fields |
|||
|
User ID |
PSOPRDEFN.OPRID |
Login Id of the user profile |
PSFT UM Create User |
|
User Description |
PSOPRDEFN.OPRDEFNDESC |
Description of the user profile |
PSFT UM Create User |
|
Employee ID |
PSOPRDEFN.EMPLID |
Employee Id of the employee to which the user profile is assigned |
PSFT UM Create User |
|
Multi Language Code |
PSOPRDEFN.MULTILANG |
Multilanguage code |
PSFT UM Create User |
|
Language Code |
PSOPRDEFN.LANGUAGE_CD |
Language code |
PSFT UM Create User |
|
Currency Code |
PSOPRDEFN.CURRENCY_CD |
Currency code |
PSFT UM Create User |
|
User Id Alias |
PSOPRDEFN.USERIDALIAS |
Alias of user login Id |
PSFT UM Create User |
|
Row Security Permission List |
PSOPRDEFN.ROWSECCLASS |
Row security parameter |
PSFT UM Create User |
|
Process Profile Permission List |
PSOPRDEFN.PRCSPRFLCLS |
Process profile parameter |
PSFT UM Create User |
|
Navigator Permission List |
PSOPRDEFN.DEFAULTNAVHP |
Navigator home page address |
PSFT UM Create User |
|
Primary Permission List |
PSOPRDEFN.OPRCLASS |
Primary permission list |
PSFT UM Create User |
|
Customer ID |
CUST_AL_SRCH.CUST_ID (CRM Table) |
Customer ID Note: A user profile can be attached to several ID types, such as None (NON), Employee (EMP), Customer (CST), and Vendor (VND). |
PSFT UM Create User |
|
Customer Set ID |
SETID_TBL.SETID (CRM Table) |
Customer's SetID |
PSFT UM Create User |
|
Vendor ID |
VENDOR.VENDOR_ID (FSCM Table) |
Vendor ID |
PSFT UM Create User |
|
Vendor Set ID |
SETID_TBL.SETID (FSCM Table) |
Vendor's Set ID |
PSFT UM Create User |
|
Multivalued Fields |
|||
|
Role Name |
PSROLEUSER_VW.ROLENAME |
The role name that is assigned to the user profile |
PSFT UM Update Child Table Values |
|
Email Address |
PSUSEREMAIL.EMAILID |
E-mail address (e-mail account) |
PSFT UM Update Child Table Values |
|
Email Type |
PSUSEREMAIL.EMAILTYPE |
Email type (e-mail account) |
PSFT UM Update Child Table Values |
|
Primary Email |
PSUSEREMAIL.PRIMARY_EMAIL |
Specifies if the e-mail address is primary |
PSFT UM Update Child Table Values |
Note:
The name of the process form in the first column of the preceding table is UD_PSFT_BAS.
The following shows how information is organized in the rest of the guide:
Deploying the Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
Using the Connector describes guidelines on using the connector and the procedure to configure reconciliation runs.
Extending the Functionality of the Connector describes procedures that you can perform to extend the functionality of the connector.
Testing and Troubleshooting describes the procedure to use the connector testing utility for testing the connector.
Known Issues and Workarounds lists known issues associated with this release of the connector.
Determining the Root Audit Action Details provides information about root audit action.
Setting Up SSL on Oracle WebLogic Server describes how to configure SSL on Oracle WebLogic Server for PeopleTools 8.50.
Changing Default Message Versions describes how to activate and deactivate message versions.