18 Managing Configurable Actions
Oracle Adaptive Access Manager provides many standard actions that are handled by a web application. These standard actions include block, KBA challenge, password TextPad, and others. The standard actions can also be used as trigger actions for Configurable Actions. Configurable actions are external Java code that is triggered by OAAM Server. Customers can write any java code they wish to perform custom operations without any change to Oracle Adaptive Access Manager. The Configurable Actions feature allows for endless customizations.
This chapter provides an overview on configuring a configurable action and instructions on how to define, view, edit, and delete an action instance, and on how to associate action instances to a Checkpoint.
18.1 Introduction and Concepts
This section introduces you to the concept of configurable actions and how they are used in Oracle Adaptive Access Manager.
18.1.1 Configurable Actions
Configurable actions are actions that are triggered based on the result action or risk scoring or both after a checkpoint execution.
Although some configurable actions are provided with the product, you may have to develop custom configurable actions for your particular requirements.
An example of a configurable action is an email that is sent to you whenever a checkpoint execution returns "block" as an action in the result. In this case, "Send Email" is the configurable action and "block" is the trigger criteria. Similarly, there could be configurable actions that can be based on a "risk score" as the trigger criteria.
Java classes and action templates for certain configurable actions are provided out-of-the-box, but you have the option to create configurable actions based on your needs. For detailed steps on configuring the default configurable actions, see Section 18.20, "Out-of-the-Box Configurable Actions."
18.1.2 Action Templates
Action Templates let you define the common details of the configurable action. You can specify the java class that is tied to the action and also specify default parameter values of the action.
The configurable actions are built using action templates. You can create only one action template per Java class file. You can create custom Java class files and corresponding action templates for your needs.
For example, if you had an action template, "add to a group," you could create four instances of the action template:
-
Add user to a white-list group
-
Add user to black-list group
-
Add IP to IP white-list group
-
Add IP to IP black-list group
Using the action template, you create an action instance based on your scenario. For example, you could have an instance such as "create a case whenever there is a block action" or another instance such as "create a case whenever there is a challenge action."
18.1.3 Deploying a Configurable Action
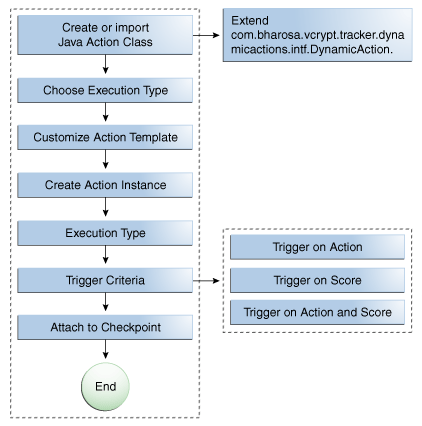
A flow chart illustrating the deployment of a Configuration Action is shown in Figure 18-1.
Note:
Steps to install newly created java class are included in this illustration.The chapter has been organized into sections by topic. If you have configured configurable actions before, use this chapter as a reference.
If you want configurable actions enabled in your system, follow this process:
-
Enable the configurable action property.
Set
dynamicactions.enabledtotrue. -
Make sure the configurable action definitions are configured in the Oracle Adaptive Access Manager database.
Out-of-the-box configurable action templates are imported when you import the snapshot when you are setting up OAAM's base environment.
A user can see the list of available configurable actions before adding a new one.
-
Determine what configurable actions have to be added to which checkpoint and the preconditions for executing those configurable actions.
-
If the existing Configuration Actions are not sufficient, develop and deploy custom ones. See the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager for details on developing a configurable action.
Although some configurable actions are provided with the product, you may have to develop custom templates for your particular requirements.
-
Define the custom action template
-
Load the action template
-
-
Associate the configurable actions to the Checkpoint.
18.2 Creating Configurable Actions
The configurable action creation flow is presented in this section.
You can:
-
Use an existing action template or create a new one to create a configurable action.
-
Define an action instance/create a configurable action
18.2.1 Define New Action Template
If you want to define a new action template, see Section 18.6, "Creating a New Action Template" for detailed information.
18.2.2 Use Existing Action Template
If you want to use an existing action template, see Section 18.4, "Searching for Action Templates."
18.2.3 Create Action Instance
To define an action instance, see Section 18.9, "Creating an Action Instance and Adding it to a Checkpoint" for detailed information.
18.3 Navigating to the Action Templates Search Page
You manage action templates in Oracle Adaptive Access Manager from the Action Templates Search page. From this page, you can search, view, create, export, and delete action templates.
-
In the Navigation tree, expand Configurable Actions.
-
Click Action Templates.
The Action Templates Search page is displayed.
Alternative methods to open search pages are listed in Section 3.9, "Search, Create, and Import."
18.4 Searching for Action Templates
In the Action Templates Search page, you can narrow down the number of action templates that are shown by specifying criteria in the Search Filter.
To search for action templates:
-
Navigate to the Action Templates Search page, as described in Section 18.3, "Navigating to the Action Templates Search Page."
The Search Results table will display no results when the Action Templates Search page first appears.
-
Specify criteria in the Search Filter to locate the action template.
-
Click Search.
If you do not want to perform the search, click Reset to reset the search parameters to the default setting.
The action templates displayed are those that match the criteria specified in the Name, Java Class Name, and Keyword fields (Table 18-1).
Table 18-1 Action Template Search Filter Criteria
| Filters and Fields | Descriptions |
|---|---|
|
Name |
Name of the action template. You can enter the complete name or part of an action template name. For example, if you enter new, any action template with new in any part of its name is shown. |
|
Java Class Name |
The fully qualified classpath of the java class file. |
|
Keyword |
Keyword in the description. |
Each action template has a name. If the description is too long to be fully shown, you can place the mouse over the text to see the entire description.
By default, action templates are sorted on Action Template Name, but you can sort action templates on Description and Java Class name.
In the Search Results table, click the row for the action template you are interested in to view more details.
18.5 Viewing Action Template Details
In the Results table of the Action Template Search page, click the row of the action template you are interested in to review the details of a specific action template. The Action Template Details page provides such general details about the case as the Java class name, action name, description, and Java class parameters.
To view details about an action template:
-
Search for the action template, as described in Section 18.4, "Searching for Action Templates."
-
In the Results table, click the row of the action template you are interested in. The Action Template Details page appears.
The fields are pre-populated with default values.
You can edit the values of the parameters, action names, and description, but you cannot edit the Java Class name.
18.6 Creating a New Action Template
To define a new action template:
-
Create the Java Class file for the configurable action template.
-
Copy the Java Class file.
Now you are ready to create the action template.
You can create only one action template per class file.
-
Navigate to the Action Templates Search page, as described in Section 18.3, "Navigating to the Action Templates Search Page."
-
From the Action Templates Search page, click New Action Template.
Alternative methods to open create pages are listed in Section 3.9, "Search, Create, and Import."
The New Action Template page appears where you can enter details to create a new action template.
-
In the Java Class Name field, enter the fully qualified classpath of the configurable action.
You will have created the Java Class during the creation of the configurable action. For information on creating a configurable action, see the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager.
An example of a Java Class is com.bharosa.vcrypt.tracker.dynamicactions.impl.AddItemToWatchListAction.
You must enter the fully qualified Java class name.
If you enter an incorrect Java class name, an error occurs when you click Load Parameters.
Also, you must ensure that the Java Class is in the correct directory.
-
Click Load Parameters.
Oracle Adaptive Access Manager obtains the list of parameters and displays the names, labels, types, and values.
Examples of parameters are shown in the following table.
Name Label Type Value Item Type Item Type: String <value> Watch-List Name Enter the Watch-List Name: String <value> White-List Name Enter the White-List Name: String <value> Black-List Name Enter the Black-List Name: String <value> Only one action template can be created per Java Class file. If you try to create an action template using the same Java Class file, a warning appears after you click Load Parameters.
-
In the Action Name field, enter a name for the action.
-
In the Description field, enter a description of the action.
-
Enter values for the parameters.
All parameter values are required. You cannot save the template until all values are entered.
-
Click Apply.
The message, "Action template created successfully," is displayed.
-
Click OK to dismiss the dialog.
After you defined the action templates, the next step is to configure the action instance. A single action template can have multiple instances. For details on configuring the action instance, see Section 18.9, "Creating an Action Instance and Adding it to a Checkpoint."
18.7 Navigating to the Action Instances Search Page
You manage configurable actions in Oracle Adaptive Access Manager from the Action Instances Search page. From this page, you can search, view, create, activate, deactivate, and delete action instances.
-
In the Navigation tree, expand Configurable Actions.
-
Click Action Instances.
The Action Instances Search page is displayed.
Alternative methods to open search pages are listed in Section 3.9, "Search, Create, and Import."
18.8 Searching for Action Instances
In the Action Instances Search page, you can narrow down the number of configurable action instances that are shown by specifying criteria in the Search Filter.
To search for action instances:
-
Navigate to the Action Instances Search page, as described in Section 18.7, "Navigating to the Action Instances Search Page."
-
Specify criteria in the Search Filter to locate the action instance.
-
Click Search.
The action instances shown are those that match the criteria specified in the Name, Checkpoint, Keyword, and Execution Type fields (Table 18-2).
Table 18-2 Action Instances Search Filter Criteria
Each action instance has a name. If the description is too long to be fully shown, you can place the mouse over the text to see the entire description.
In the Results table, click the row for the action instance you are interested in to view the Action Instance Details page.
18.9 Creating an Action Instance and Adding it to a Checkpoint
To create an action instance, follow the procedure in this section.
Create Action Instance and Associate it to a Checkpoint
-
Navigate to the Action Instance Search page, as described in Section 18.7, "Navigating to the Action Instances Search Page."
-
Click New Action Instance.
Alternative methods to open create pages are listed in Section 3.9, "Search, Create, and Import."
The New Action Instance page is displayed.
-
Next to Action Instance Template Details, click Choose Action Template.
-
In the Existing Action Templates page, select a template and click OK.
-
In the Action Instance section, enter values for the action instance.
-
Name
-
Description
-
Log Level
The log level indicates whether the execution status of instance should be recorded.
-
Disable turns off logging
-
Enable turns on logging
-
Log if error turns on logging when errors occur
Only if there is an error will the execution status be recorded in the logs. Otherwise, the instance triggering is not recorded in the logs.
-
-
Checkpoint to associate the configurable actions to
For example, a checkpoint could be Pre-Transaction (a custom checkpoint)
-
Choose Execution Type for the Configurable Action
-
Select from two Execution Types: "Synchronous" or "Asynchronous."
Synchronous actions are executed in the order of their priority in the ascending order.
Synchronous is selected as the execution type so that the action is executed immediately after the rules action is triggered.
For the synchronous execution type, if actions are executing in sequential order and one of the actions in the sequence does not trigger, the other actions will still trigger.
Synchronous actions can also be used to pass/share data across the configurable actions. This is useful when developing custom configurable actions. Refer to "Configurable Actions" in the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager for details.
Asynchronous actions are queued for execution and are executed not in any particular sequence.
-
Enter the execution order if execution type is Synchronous.
Priority is unique within a checkpoint. An error is displayed when the execution order is not unique.
-
Select Action Priority and Time to Live if execution type is Asynchronous.
Actions are aligned in different queues based on the action priority. When it is time to execute the next action from the queue, the highest-priority action is executed first.
Time to Live denotes the maximum time to wait before the action can be discarded.
Enter Preconditions for the Configurable Action
-
Select the trigger criteria.
Trigger criteria determines when to trigger the action in the session.
The criteria should be either a score or an action or both. These are compared against the values for the selected checkpoint.
-
If the evaluated action matches the action provided, the configurable action is triggered.
-
If the Rules Engine returns a score in the range provided, the configurable action is executed.
For example, if you want to create a case whenever the action type is block, Oracle Adaptive Access Manager will create a case whenever there is an action, "block," in the policy. If you want to create a case whenever the score is greater than 500, Oracle Adaptive Access Manager will create a case when the score is greater than 500 in that particular session.
When both action and score are specified, the configurable action is executed only if both of criteria match with the outcome from the Rules Engine.
-
-
Enter the values for the action.
Choose an action. For example, the trigger criteria may be that if the Rules Engine returns "Allow" as the action, the action instance is executed.
Typical actions from the Rules Engine are "Allow," "Block," "PasswordTextPad," and others.
In the example, Challenge is selected as the action trigger. When a KBA challenge is returned as a rules result, the configurable action is triggered.
-
Select Only if this is the final action if you want the action to be the final action.
In the example, "Only if this is the final action" is not selected so that the configurable action is triggered for the challenge even though it may not be a final action.
-
Select the score range
A typical score from the Rules Engine is a numeric value between 0 and 1000.
Select a range. For example, if the Rules Engine returns a score between "x" and "y," the configurable action is executed.
-
Enter values for all the parameters related to the action.
For the example, the Watch-List Name is changed to AmtTransferSuspectedList.
To apply the changes:
-
Click Apply.
If the action instance is created successfully, a confirmation appears.
-
Click OK to dismiss the dialog.
18.10 Creating a Custom Action Instance
To add a custom action instance, you will need to:
-
Develop the action instance by implementing the com.bharosa.vcrypt.tracker.dynamicactions.intf.DynamicAction java interface.
Note:
Implementing means writing java code based on the contract specified by the Java interface com.bharosa.vcrypt.tracker.dynamicactions.intf.DynamicAction. -
Test the implementation of the action instance thoroughly.
-
Compile the Java class and create a jar file of the compiled class files.
-
Extend/customize Oracle Adaptive Access Manager to add the custom jar.
Refer to the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager for steps on adding the custom jar to Oracle Adaptive Access Manager.
-
Restart OAAM Server and OAAM Admin Server.
-
Log in to OAAM Admin and create an action definition entry for the newly deployed configurable action.
-
Make sure all the parameters required for the configurable action are displayed in the user interface.
-
Use the newly available configurable action by adding it to the required checkpoints.
18.11 Editing an Action Template
To edit details about a specific action template:
-
Search for the action template, as described in Section 18.4, "Searching for Action Templates."
-
In the Results table, click the row of the action template you are interested in. The Action Template Details page appears.
The default values are pre-populated in the Action Template Details page.
-
Edit the values of the parameters, action name, and description in the action template.
18.12 Exporting Action Templates
-
Search for the action template, as described in Section 18.4, "Searching for Action Templates."
-
Select the row for each action template you want to export.
-
Click the Export button or select Export Selected from the Actions menu.
-
In the Export Action Template dialog, click Export.
-
In the Save dialog, click OK.
18.13 Importing Action Templates
-
Navigate to the Action Templates Search page, as described in Section 18.3, "Navigating to the Action Templates Search Page."
-
In the Action Templates Search page, click Import.
-
In the Action Templates Import dialog, click Browse and locate the action templates file you want to import.
-
Click OK.
18.14 Moving an Action Template from a Test Environment
To move an action template from a test environment to a production environment, perform the tasks listed:
-
Export the action template from the test environment. Refer to Section 18.12, "Exporting Action Templates."
-
Import the action template into the target system. Refer to Section 18.13, "Importing Action Templates."
-
If the configurable action is a customized one, skip Steps 1 and 2. Use the OAAM Extensions Shared Library (oracle.oaam.extensions.war) to package the configurable action and related jars and deployed the war into the target system.
For information on adding custom jars, see "Add Customizations/Extensions using Oracle Adaptive Access Manager Extensions Shared Library" in the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager.
Note:
From 11g, do not copy the custom jars to OAAM webapp folders.
Migrating 10g Action Templates to 11g
In the 11g user interface for Action Templates, the Notes field has been removed. If the Notes field contains text in the 10g Action Templates, after migration to 11g, these notes will be appended (combined) with the description text.
18.15 Deleting Action Templates
-
Search for the action template, as described in Section 18.4, "Searching for Action Templates."
-
Select the row for each action template you want to delete and click Delete Action Templates from the Actions menu.
If you select an action template to delete that is used in a checkpoint, an error about the configurable action currently being used by checkpoints is displayed.
When multiple action templates are selected for deletion and if there are checkpoints that contain the instances of some of the action templates selected, a warning message is provided, stating that the instances are linked to Checkpoints and cannot be deleted. You have the option to delete the unlinked action templates.
18.16 Viewing a List of Configurable Action Instances
-
Navigate to the Action Instances Search page, as described in Section 18.7, "Navigating to the Action Instances Search Page."
-
In the Search Filter, select a checkpoint to see all the action instances for that checkpoint or select All to see all action instances for the checkpoints.
-
Click Search.
In the Results table, a list of action instances is displayed.
If you want to view a particular instance, click the row of the action instance you are interested in. The Action Instance Details page appears.
18.17 Viewing the Details of an Action Instance
To view the details of an action instance:
-
Navigate to the Action Instance Search page, as described in Section 18.7, "Navigating to the Action Instances Search Page."
-
Click the row of the action instance you are interested in viewing.
The details page of the action instance is displayed.
18.18 Editing an Action Instance
-
Navigate to the Action Instance Search page, as described in Section 18.7, "Navigating to the Action Instances Search Page."
-
Click the action instance you are interested in editing.
-
In the Action Instance section, change the values for the action instance.
-
Name
-
Description
-
Log Level
-
Checkpoint
-
-
Change the execution type.
-
Change the trigger criteria.
-
Enter values for all the parameters related to the action.
-
Apply the changes.
18.19 Deleting an Existing Action Instance
To delete an action instance:
-
Navigate to the Action Instances Search page, as described in Section 18.7, "Navigating to the Action Instances Search Page."
-
In the Search Filter, select a checkpoint to see all the action instances for that checkpoint or select All to see all action instances for the checkpoints.
-
Click Search.
-
Select the checkbox next to an existing action definition you want to delete.
-
Click Delete.
If an action is associated with a checkpoint, you cannot delete it.
18.20 Out-of-the-Box Configurable Actions
The following configurable actions are available out of the box:
-
CaseCreationAction - Used to create a case
-
AddItemToWatchListAction - Used to add item to a watch list.
Before these configurable actions can be configured for checkpoints, the definitions of these should be added.
Note:
To use system provided configurable actions, you must import the configurable action definition. Refer to Section 2.6, "Importing the OAAM Snapshot."18.20.1 Defining CaseCreationAction
-
Create a case.
Customer care cases need an owner.
For information on case creation, see Section 4.8, "Creating a CSR Case."
-
Navigate to the Action Templates Search page, as described in Section 18.3, "Navigating to the Action Templates Search Page."
-
From the Action Templates Search page, click New Action Template.
The New Action Template page appears where you can enter details to create a new action template.
-
Enter the java class name as
com.bharosa.vcrypt.tracker.dynamicactions.impl.CaseCreationAction
-
In the Action Name field, enter a name for CaseCreationAction.
-
In the Description field, enter a description for CaseCreationAction.
-
For the Case Type parameter, enter 1 for "CSR Case."
-
For the Severity parameter, enter 1 for "Low", 2 for "Medium", 3 for "High."
-
Enter a value for the Case Description that should be set while creating the case.
-
Enter the userId for Case Creator UserId. Make sure that userId has a proper role and access permissions for creating the case.
18.20.2 Defining AddItemtoListAction
To define AddItemToListAction:
-
Navigate to the Action Templates Search page, as described in Section 18.3, "Navigating to the Action Templates Search Page."
-
From the Action Templates Search page, click New Action Template.
The New Action Template page appears where you can enter details to create a new action template.
-
Enter the Java class name as com.bharosa.vcrypt.tracker.dynamicactions.impl.AddItemToWatchListAction
-
In the Action Name field, enter a name for AddItemToWatchList.
-
In the Description field, enter a description for the action.
-
For the Item Type parameter, enter any one of the following:
-
vtusers - If UserId of current session has to be added to the Watch List
-
devices - If DeviceId of current session has to be added to the Watch List
-
ips - If IP Address of current session has to be added to the Watch List
-
countries - If Country ID of current session has to be added to the Watch List
-
states - If State ID of current session has to be added to the Watch List
-
cities - If City ID of current session has to be added to the Watch List
-
userLogin - If LoginId of current session has to be added to the Watch List
-
-
For the Watch-List Name parameter, enter the name of the Watch List. Make sure there is a group with the same name.
-
For the White-List Name parameter, enter the name of the White List. Make sure there is a group with the same name. Action checks this list before adding an item to Watch List.
If the item is present in the white list, it will not be added to the watch list.
-
For the Black-List Name parameter, enter the name of the Watch List. Make sure there is a group with the same name. Action checks this list before adding an item to Watch List
If the item is present in the blacklist, it will not be added to the watch list.
18.21 Use Cases
This section describes example use cases for configurable actions
18.21.1 Use Case: Add Device to Black List
Jeff is a Security Administrator at Dollar Bank. He must configure an action to add a device to a black list group whenever there is a device that has more than three failed login attempts from a blacklisted country within a month.
For example, if there were two login attempts from a device in blacklisted country today and two login attempts two weeks ago from the same device, it would be automatically added to the group by the configurable action.
To configure the action:
-
Search for a device rule that evaluates in-group membership.
Look for a rule with a maximum count or authentication status check.
-
If a rule does not exist, create one.
-
Find an existing post-authentication policy used for general security rules.
-
Create and add the rule.
-
-
Configure a new trigger action enumeration named add device to black list and an action group for it.
-
In the group, add a block action.
-
Configure a configurable action to trigger on add device to black list which will add the device to a black list group.
18.21.2 Use Case: Add Device to Watch-list Action
Jeff is a Security Administrator at Dollar Bank. He needs to configure an action to add a device to a watch list group whenever there is a device that has more than three failed login attempts within a month. He starts with the rule he will need. He searches for a device rule that evaluates in-group membership. He finds one for device in-group but it does not have a max count or authentication status check. Jeff decides he must create one. He finds an existing post-authentication policy used for general security rules, and then creates and adds the rule. Jeff also configures a new trigger action enumeration named "add device to watch list" and an action group for it. In the group he also adds a block action. Next Jeff configures a configurable action to trigger on "add device to watch list" action which will add the device to a watch list group. Today there were two login attempts from a device in North Korea and two weeks ago the same device so it was automatically added to the group by the configurable action.
Implementation Notes:
The above requirement can be implemented by following these steps:
-
Create a group called Device Watch List that will store the devices that have to be monitored before they can be classified as white-listed or black-listed.
-
Similarly create groups called Device While List , Device Black List.
-
Create a custom rule action called add_device_to_watch_list.
-
Add a rule with the rule condition "USER: Check login count" to a policy for the "PreAuthentication" checkpoint. Configure it such a way that it will trigger and return the action add_device_to_watch_list whenever there are more than three failed login attempts within last 30 days.
-
Now create an action instance of the action template AddItemToWatchListAction and associate it to the Pre-Authentication checkpoint.
-
Set the trigger criteria as the action by selecting add_device_to_watch_list action and set the score range as 0 to 1000.
-
Set the Item Type parameter value as devices since deviceid needs to be added to the list.
-
Set the Watch List Name parameter value as Device Watch List.
-
Set the Black List Name parameter value as Device White List.
-
Set the White List Name parameter value as Device Black List.
-
Save the action instance
Simulate logins so that the rule triggers and returns add_device_to_watch_list as the rule action. Whenever that happens you will see the current device added to the Device Watch List.
18.21.3 Use Case: Custom Configuration Action
Jeff is a Security Administrator. He has defined a custom configurable action in the test environment. Now he has to export the custom action template from test and import it into Production. (Tip: He has to manually link the custom jar (custom class) before the import action, if not import would fail. In 11g, he does this by adding his custom jars to the OAAM Extensions Shared Library. The server should be restarted for the changes to take effect)
Implementation Notes:
The above can be achieved by following these steps:
-
Jeff implements his custom configurable action by writing a java class that implements
com.bharosa.vcrypt.tracker.dynamicactions.intf.DynamicActionjava interface. -
He can compile his class by linking the Oracle Adaptive Access Manager jars from
$IDM_ORACLE_HOME\oaam\native\java\libfolder. -
He should then test his custom configurable action to make sure it is working correctly.
-
He should then package his class as a jar file and create the shared library by following the structure of the OAAM Extensions Shared Library that is available in
$IDM_ORACLE_HOME\oaam\oaam_extensions\genericfolder -
He should then overwrite the existing oracle.oaam.extensions shared library or deploy his extensions shared library with a different implementation version.
-
He can then create action template and an action instance for the custom configurable action.
-
He should test it by creating an action instance and attach it to a checkpoint and set the trigger criteria and then simulate logins/sessions from OAAM Server to trigger the custom configurable action.
-
Once he is done with testing, he can export his custom action template.
-
Now he has export file that has the custom action template and also the shared library that has custom java code related to his custom configurable action.
-
He can deploy his custom configurable action by redeploying the OAAM Extensions Shared Library using his shared library and then import his custom configurable action template from his export file.
18.21.4 Use Case: Create Case
Matt is a Security Administrator. He needs a configurable action such that an Agent case is created automatically, whenever a user is blocked more than 3 times in the last one month. The Fraud investigator will work on these cases to determine if the user is a risky user.
Implementation Notes:
The above requirement can be implemented by following these steps:
-
Create a custom rule action called create_agent_case.
-
Add a rule with the rule condition "USER: Check login count" to a policy for the Post-Authentication checkpoint. Configure it such a way that it will trigger and return the action create_agent_case whenever there are more than three blocks for the user within last 30 days.
-
Now create an action instance of the action template CaseCreationAction and associate it to the Post-Authentication checkpoint.
-
Set the trigger criteria as the action by selecting create_agent_case action and set the score range as 0 to 1000.
-
Set the parameters of CaseCreationAction as follows:
-
Enter "2" as value of Case Type parameter
-
Enter "2" (for Medium) or "3" (for High) as Severity parameter value
-
Enter "Case Description" parameter value.
-
Enter the userId for "Case Creator UserId" parameter. Make sure that userId has a proper role and access permissions for creating the case
-
-
Save the action instance.
-
Try few logins for a user so that it triggers and returns at least three blocks
-
After third block, you should see automatic creation of an agent case by the configurable action.