16 Configuring SSL for JDENET (Release 9.1 Update 2.1)
This chapter contains the following topics:
16.1 Understanding SSL for JDENET
Secure Sockets Layer (SSL) is a cryptographic protocol that enables secure communication between applications across a network. Enabling SSL communication provides several benefits, including message encryption, data integrity, and authentication. An encrypted message ensures confidentiality in that only authorized users have access to it. Data integrity ensures that a message is received intact without any tampering. Authentication guarantees that the person sending the message is who he or she claims to be.
Starting with JD Edwards EnterpriseOne Tools 9.1 Update 2.1, you can configure EnterpriseOne to use SSL to encrypt all JDENET message data passed between the Enterprise Server and clients. In this context, a client would include an HTML Server, the Deployment Server, or any other client that makes requests to the EnterpriseOne Enterprise Server.
16.2 Installing SSL Programs on IBM System i
For the IBM System i platform, EnterpriseOne provides two SSL-based components within a save file. You have to extract these components to the system foundation IFS folder (such as E910SYS) before you can create and use SSL certificates as described in the following section, "Generating an SSL Certificate and Key File."
The following steps describe how to use the command to extract the components for SSL Programs on IBM System i:
-
Ensure the system foundation library is in your library list. If it is not in the list, you can add it by entering this command:
ADDLIBLE E910SYS
Where E910SYS is the name of the system foundation library.
-
From an IBM System i command line, enter the following command:
INSTALLSSL -
Press F4 to prompt the command.
-
Enter the name of your system foundation library, and then press Enter.
16.3 Generating an SSL Certificate and Key File
To use secure sockets, the server must have an SSL certificate and private key. This information is used by the SSL library functions to generate unique encryption keys for each connection and negotiate the secure connection with the client. EnterpriseOne provides a script file that can be used to generate a combination certificate/key file for use with SSL.
On Windows servers, the gencert.cmd file is used to generate a combination SSL certificate/private key file that is suitable for use with JDENET SSL. On UNIX and Linux systems, the file is called gencert.sh. On IBM System i, the command is GENCERT, which must be run from QSHELL. These files can be found in the system/bin32 directory on the enterprise server and also on the deployment server. The following illustration shows an example of running the script to generate a certificate. Notice that the system prompts you to enter data that is unique to your site to create the certificate/key file:
Figure 16-1 Example of Running Script to Generate an SSL Certificate
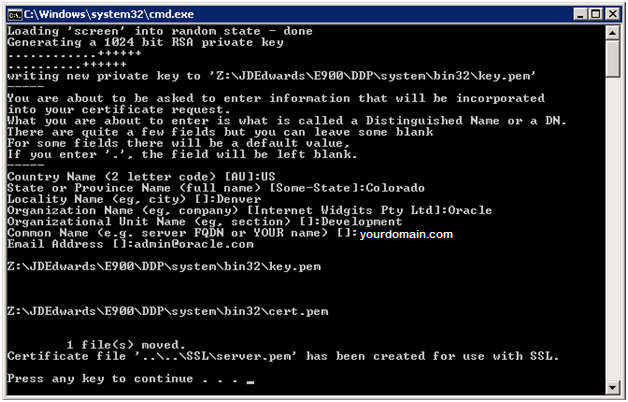
Description of ''Figure 16-1 Example of Running Script to Generate an SSL Certificate''
The file generated by this script should be entered as the sslKeyFile parameter in the enterprise server JDE.INI file when using SSL. See Configuring the Enterprise Server JDE.INI File in this chapter. By default, the file is created in a directory outside the main system directory to ensure that the certificate/key file is preserved during an EnterpriseOne Tools release upgrade.
It is not required to generate the certificate/key file on the server that will use it. You could, for example, generate a certificate/key file on the deployment server and move it to your enterprise server when you are ready to start using SSL.
You can also use commercially signed certificates, such as certificates validated by a company like Verisign or Cybertrust, to set up SSL for JDENET, with some caveats. The EnterpriseOne enterprise server currently requires a combination certificate and key file in PEM format. In addition, the file must not be pass-phrase protected. Currently, using a commercially signed certificate with the JDENET server does not offer any advantage over using the self-signed, internally generated certificate as described in this section.
16.4 Configuring the Enterprise Server JDE.INI File
Starting with JD Edwards EnterpriseOne Tools 9.1 Update 2.1, the "Network and Queue Settings (JDENET Configuration)" section of the enterprise server JDE.INI file contains three settings for SSL support. These settings are used only by the enterprise server. Clients that connect to the enterprise server do not have any related settings, as the enterprise server tells the client the type of connection to be used. Because of this architecture, older EnterpriseOne clients that do not support SSL cannot connect with an EnterpriseOne server that is enabled with SSL. Therefore, SSL support for JDENET requires that the release level of EnterpriseOne clients matches the release level of EnterpriseOne servers.
The SSL settings in the "Network and Queue Settings (JDENET Configuration)" section of the jde.ini include:
-
useSSL
Valid values are
Enable SSLorDisable SSL. Enabling this option specifies that JDENET messages will be exchanged using secure sockets (SSL). The setting is only set on the server, but does require that clients accessing the server can process SSL messages (that is, all clients must be running with a matching EnterpriseOne Tools release). Starting with EnterpriseOne Tools 9.1 Update 2.1, Disable SSL is the default setting in EnterpriseOne Tools 9.1 Update 2.1. -
sslRetries
This setting specifies the maximum number of times the server or client will attempt to complete an SSL handshake. If the handshake is not completed within the retry limit, the SSL connection fails. The retry limit prevents the server from hanging on an SSL connection that may never complete. The default value of 1000 for this setting should be appropriate for most installations, but may need to be increased to allow for slow clients or high network latency.
-
sslKeyFile
You must set this parameter to the fully qualified path of the file containing the server's SSL certificate and private key. The server must have a valid certificate/key file in PEM format in order to use secure sockets. See Generating an SSL Certificate and Key File in this chapter for more information.
The following is an example of a typical SSL setup viewed from Server Manager:
Figure 16-2 SSL Settings in the JDE.INI File
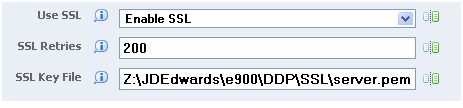
Description of ''Figure 16-2 SSL Settings in the JDE.INI File''